En Sandworm descubrimos una vulnerabilidad SSTI en Flask lo que nos permitio obtener credenciales y acceso a la maquina. Tras manipular codigo rust ejecutado por un cronjob logramos el acceso a un siguiente usuario. Finalmente para escalar privilegios explotamos una vulnerabilidad presente en firejail.
| Nombre | Sandworm |
|---|---|
| OS | Linux |
| Puntos | 30 |
| Dificultad | Media |
| IP | 10.10.11.218 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http/s (80, 445) y ssh (22).
|
|
Web Site
El sitio web nos redirige al dominio ssa.htb.
|
|
Observamos informacion del sitio, en el footer indica que es una aplicacion escrita en Flask.
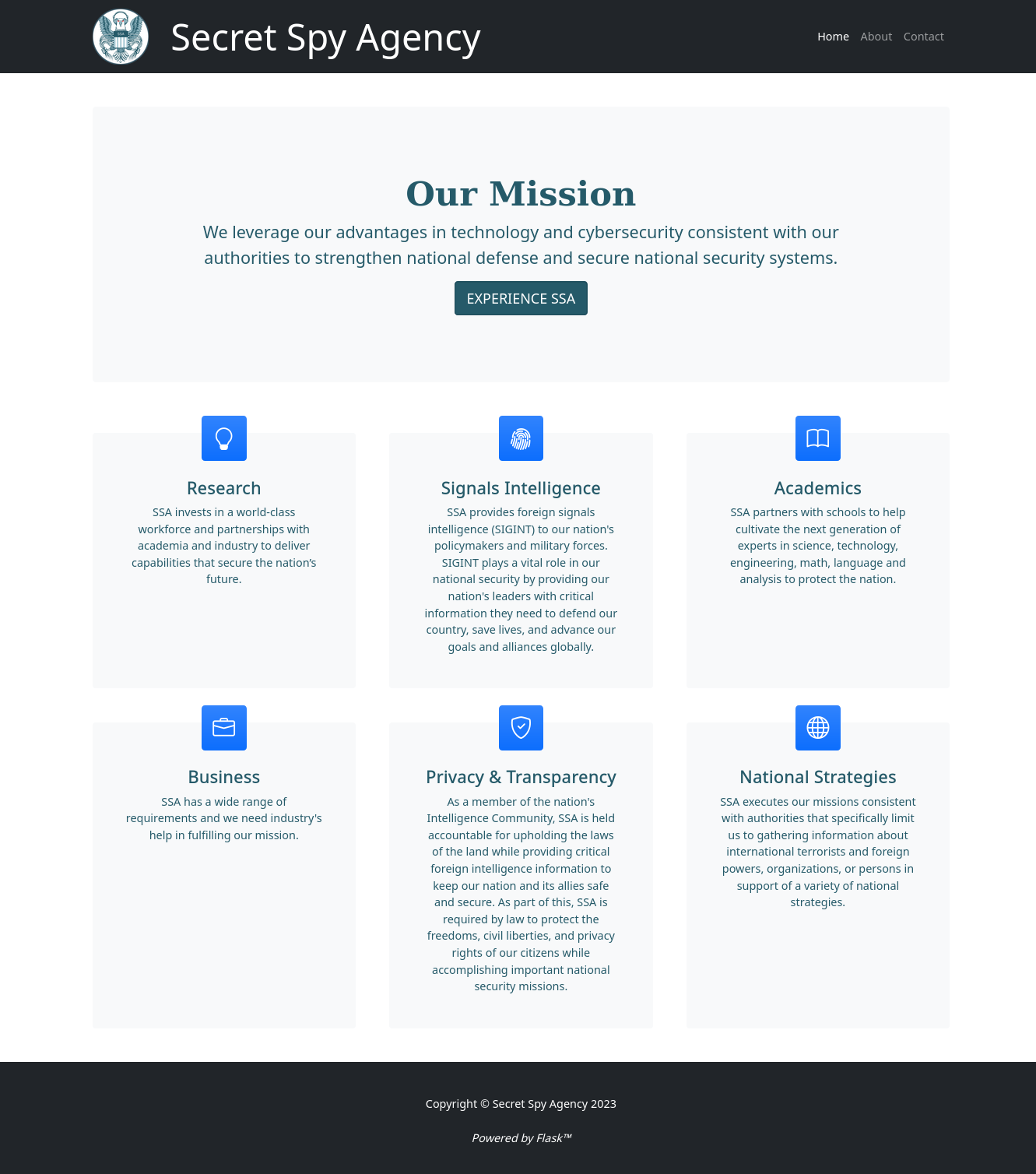
En /contact encontramos un formulario en el que indica que los mensajes enviados deben de estar encriptados, tambien, nos muestra una direccion sobre el uso de PGP.
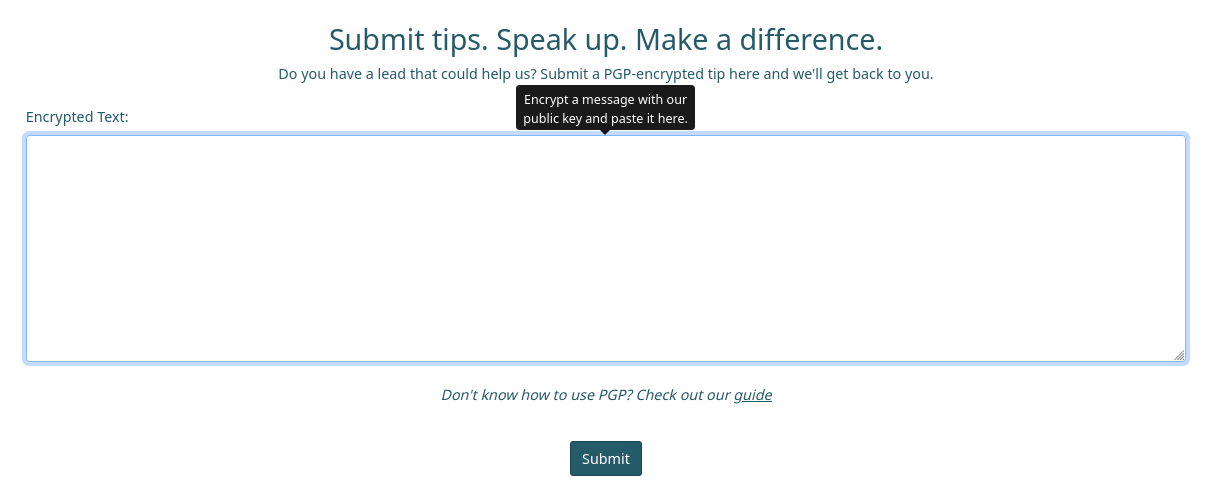
Site PGP
En /guide encontramos multiples opciones; desencriptar, encriptar y verificar firma, y, al final encontramos un ejemplo de un mensaje firmado. Las dos primeras opciones utilizan la clave publica que encontramos en /pgp.
Utilizando la clave publica que ofrece el sitio, utilizamos la opcion de encriptar, vemos la salida.
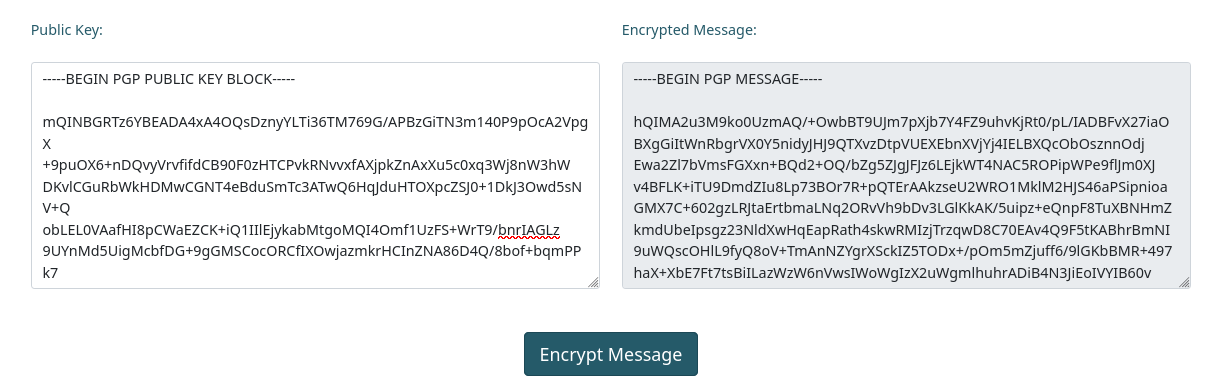
Con la opcion de desencriptar observamos el mensaje desencriptado.
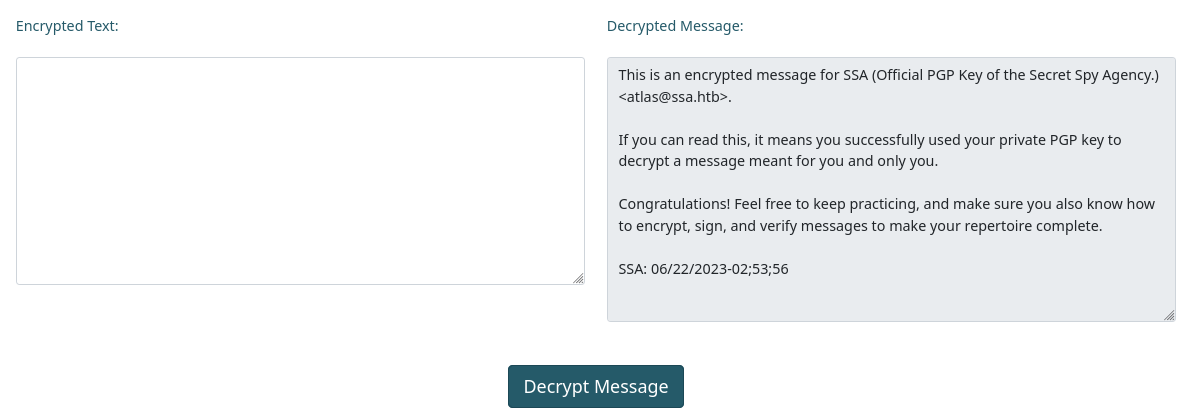
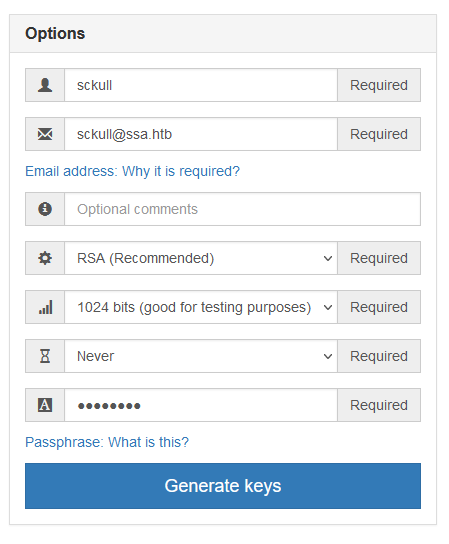
La clave privada no esta disponible en el sitio por lo que para verificar la firma es necesario crear una llave propia. Utilizamos el sitio PGP Tool para crear nuestra llave rellenando los valores necesarios.
Utilizamos la llave privada para firmar un mensaje.
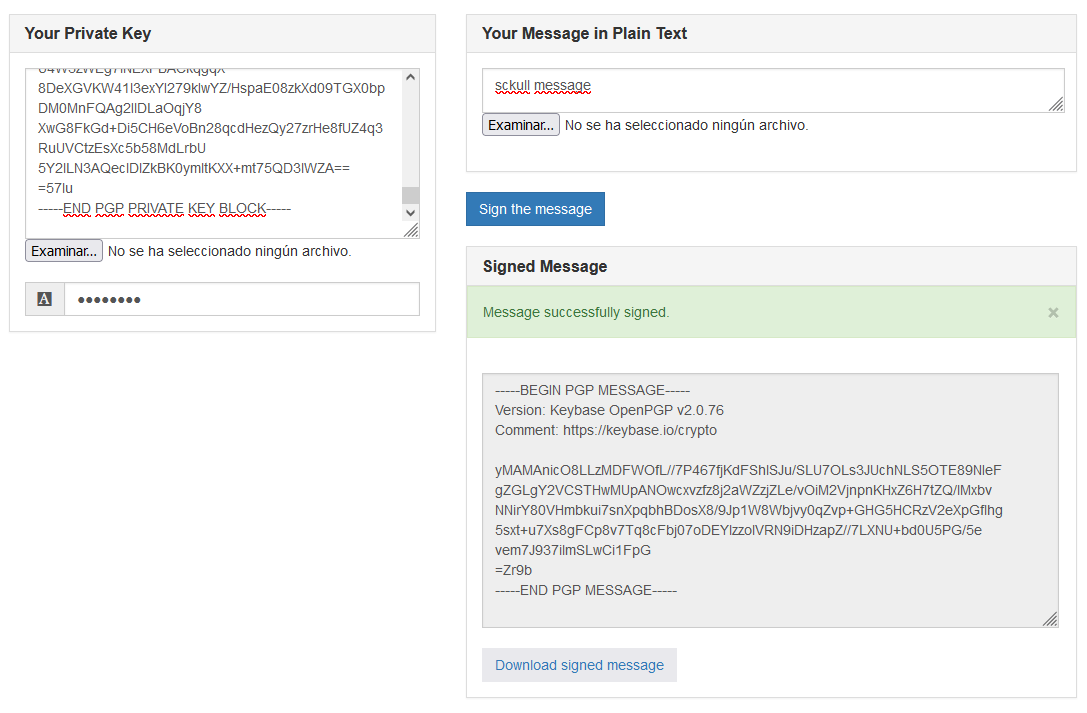
Utilizando la llave publica y el mensaje firmado verificamos la firma en el sitio.
Observamos que la firma es valida, y se muestra informacion de la verificacion.
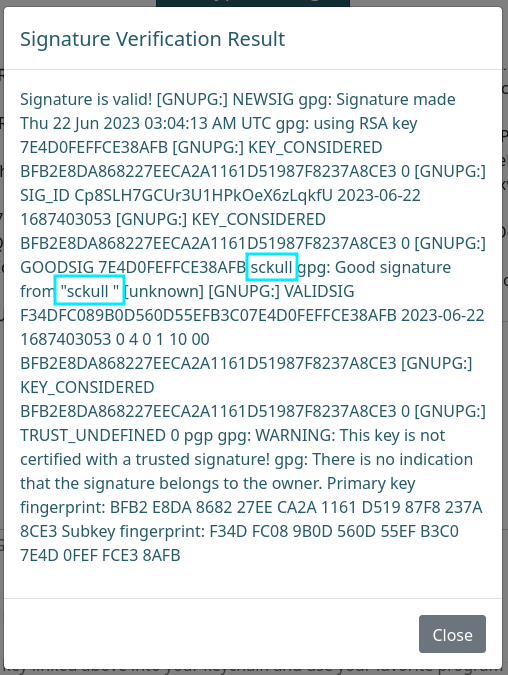
En la salida se muestran los valores del nombre y correo, estos dos valores son los unicos valores manipulables del sitio.
|
|
SSTI - Flask
Creamos una llave propia con la configuracion dentro del archivo config.txt utilizando pgp ya que el sitio no nos permite manipular el valor del email.
|
|
Utilizamos la clave para firmar el mensaje en msg.txt el cual se guarda en sign_msg.txt.
|
|
Mostramos nuestra clave publica.
|
|
Y verificamos en el sitio el cual se muestra como valido.
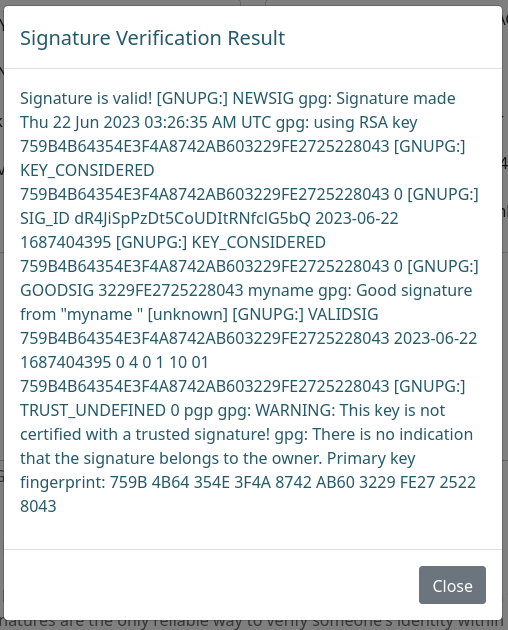
Payloads
Como sabemos el sitio esta escrito en python con flask, utilizamos distintos payloads para verificar si en el valor de email o name existe algun tipo de vulnerabilidad del tipo SSTI.
|
|
Firmamos nuestro mensaje y “exportamos” nuestra clave publica.
|
|
Observamos en el resultado de verificacion que el tercer payload es funcional y que la vulnerabilidad se encuentra tanto en name y email.
|
|
Python GNUPG
Ya que estariamos probando distintos payloads para verificar hasta donde podemos llegar con esta vulnerabilidad creamos un script que realice los pasos anteriores utilizando la libreria python-gnupg.
|
|
El payload {{ config.items() }} nos dio informacion sobre la aplicacion, observamos credenciales de la base e datos MySQL.
|
|
User - SiletObserver
Uno de los payloads nos permitio ejecutar comandos dentro de la maquina, vemos que el usuario es atlas.
|
|
Creamos una shell inversa para ejecutarla dentro de la maquina.
|
|
La agregamos en nuestro payload.
|
|
Limited Shell - Atlas
Sin embargo tras obtener una shell como atlas observamos que la shell esta limitada a ciertos comandos.
|
|
Explorando los directorios encontramos el codigo fuente de la aplicacion web.
Destacamos la ruta process_form la cual hace uso de render_template_string vulnerable a SSTI.
|
|
Luego de explorar los diferentes directorios encontramos credenciales para el usuario silentobserver el cual esta registrado en la maquina. Segun el archivo parecen ser credenciales para el sitio tambien.
|
|
Shell
Utilizamos estas credenciales por SSH logrando acceder y obtener nuestra flag user.txt.
|
|
Al ingresar enumeramos los ficheros con permisos SUID, vemos que existen tres los cuales son propiedad de Atlas, ademas observamos firejail y un proceso ejecutado por atlas que seguramente es por donde logramos obtener una shell.
|
|
Observando los cronjobs en ejecucion con pspy, se muestra uno interesante, la ejecucion de cargo dentro del directorio /opt/tipnet el cual ejecutaria el proyecto.
|
|
Encontramos que en /opt existen dos carpetas, crates/ cuyo contenido parece ser la libreria logger propia y editable por el usuario siletobserver.
|
|
Y, en tipnet/ observamos una libreria/proyecto que permite la busqueda de informacion en una base de datos MySQL. En el codigo se muestra el uso de logger la libreria a la cual tenemos acceso.
User - Atlas
Agregamos codigo dentro del archivo lib.rs de logger/, para le ejecucion del archivo /dev/shm/ex el cual contiene una shell inversa.
|
|
El archivo contiene lo siguiente y al que tambien le dimos permisos de ejecucion chmod +x /dev/shm/ex.
|
|
Shell
Esperamos unos segundos a la ejecucion del archivo, logrando obtener una shell como Atlas, esta vez sin limites.
|
|
Generamos una clave SSH para el usuario silentobserver y utilizando la shell de atlas agregamos esta en el archivo authorized_keys.
|
|
Logrando asi obtener una shell mas comoda.
|
|
Privesc
Como sabemos unicamente el grupo jailer tiene permitido la ejecucion de firejail al cual Atlas pertenece. Si observamos la version es 0.9.68 la cual el sitio web de firejail marca como vulnerable mostrando el CVE-2022-31214.
|
|
El CVE permite escalar privilegios y en el reporte existe un PoC.
Tras ejecutar el exploit nos muestra el pid del sandbox al cual podemos ingresar.
|
|
Tras ingresar a este unicamente ejecutamos su - logrando obtener una shell como root y la flag root.txt.
|
|