En Devvortex inicialmente realizamos la explotacion de una vulnerabilidad en Joomla que nos dio acceso como Administrador y posteriormente la posibilidad de ejecucion de una shell inversa tras modificar el template. Dentro, enumeramos la base de datos donde descubrimos credenciales para un segundo usuario. Finalmente escalamos privilegios tras ejecutar una shell en el ‘pager’ de apport.
| Nombre | Devvortex |
|---|---|
| OS | Linux |
| Puntos | 20 |
| Dificultad | Facil |
| IP | 10.10.11.242 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
|
|
Web Site
El sitio web nos redirige al dominio devvortex.htb el cual agregamos al archivo /etc/hosts.
|
|
El sitio muestra multiples enlaces, y, aparentemente es un sitio estatico.
Directory Brute Forcing
feroxbuster muestra los archivos y recursos del sitio.
|
|
Subdomain Discovery
Tras ejecutar ffuf este muestra el subdominio dev.
|
|
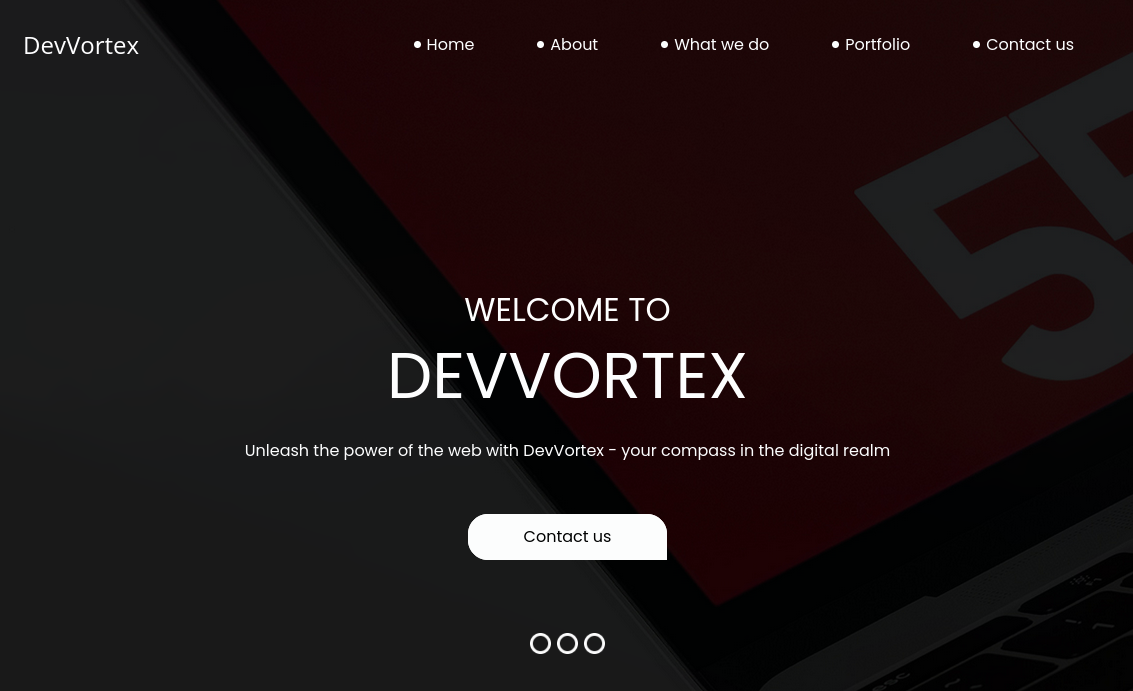
Joomla
El subdominio muestra un sitio nuevo, parece ser el sitio de una compania de desarrollo web.
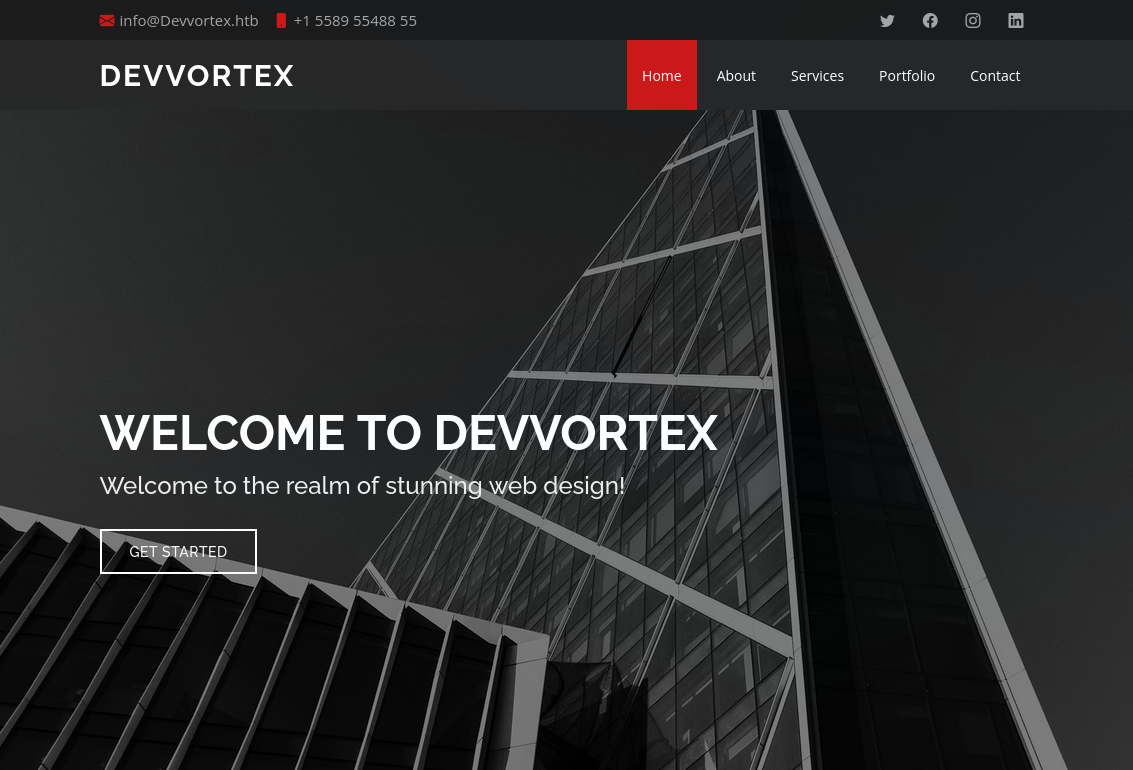
Wappalyzer muestra multiples tecnologias utilizadas por el sitio.
Intentamos generar un error para verificar la existencia de alguna tecnologia en el backend. Observamos que el favico pertenece a Joomla, y, ademas Wappalyzer muestra el CMS Joomla.
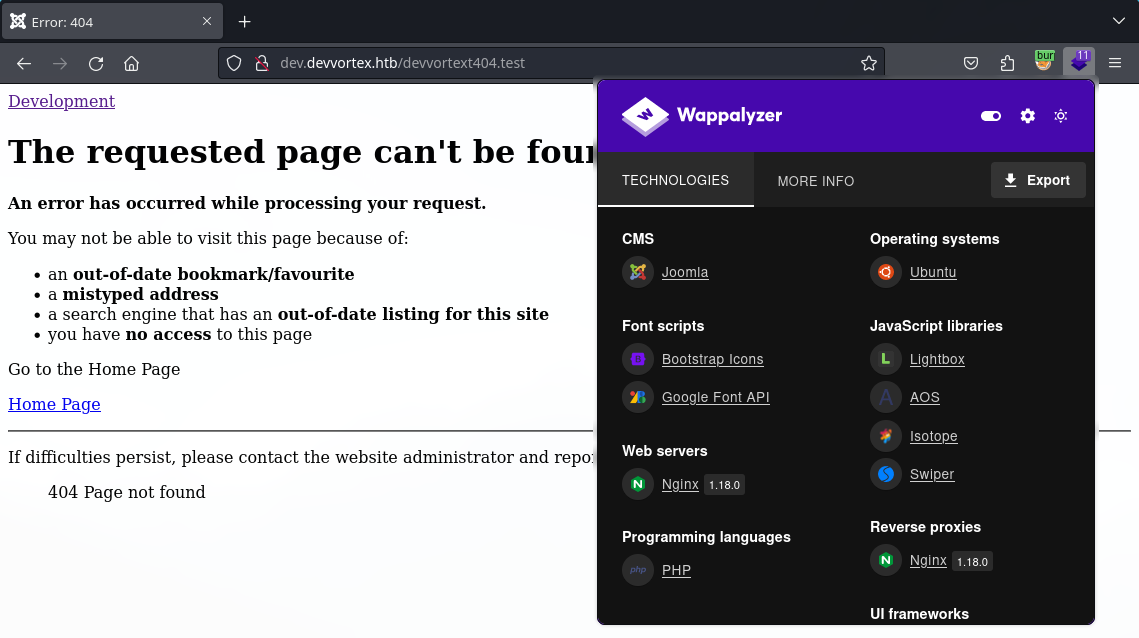
Identificamos la version como Joomla 4.2.6.
|
|
Joomla - CVE-2023-23752
Realizamos una busqueda de vulnerabilidades/exploits y observamos que existe una que afecta a esta version.
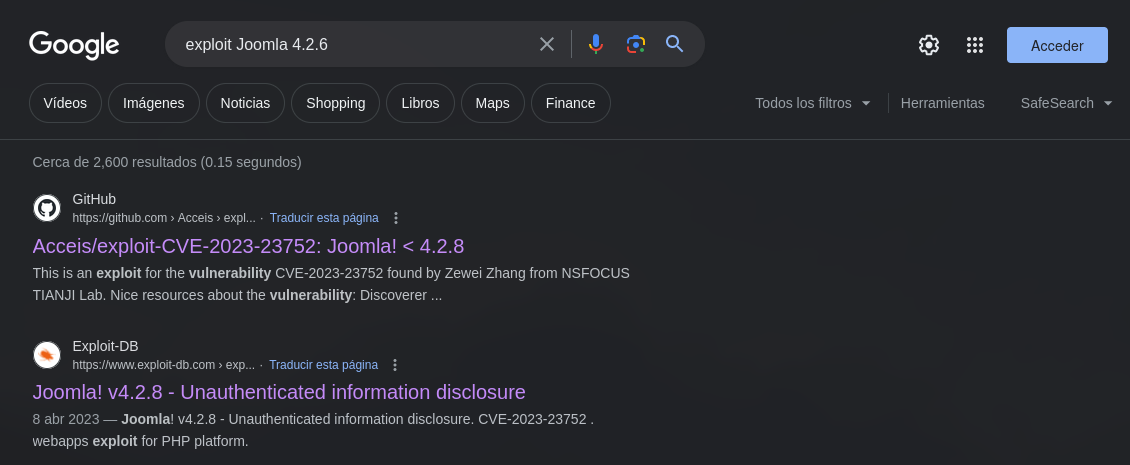
Segun el codigo de Joomla! v4.2.8 - Unauthenticated information disclosure este realiza dos solicitudes a dos direcciones de la API, una para los usuarios y otra para la configuracion.
|
|
Si observamos los usuarios, muestra dos unicos usuarios: lewis y logan. El primero como super user y el otro como registrado.
|
|
Luego, tenemos la configuracion, donde podemos destacar la contrasena P4ntherg0t1n5r3c0n##.
|
|
|
|
Joomla - Access
Logramos acceder al panel de Joomla con la contrasena y el usuario lewis.
User - www-data
Intentamos ejecutar codigo en System -> Templates -> Site Templates -> Cassiopeia -> error.php.
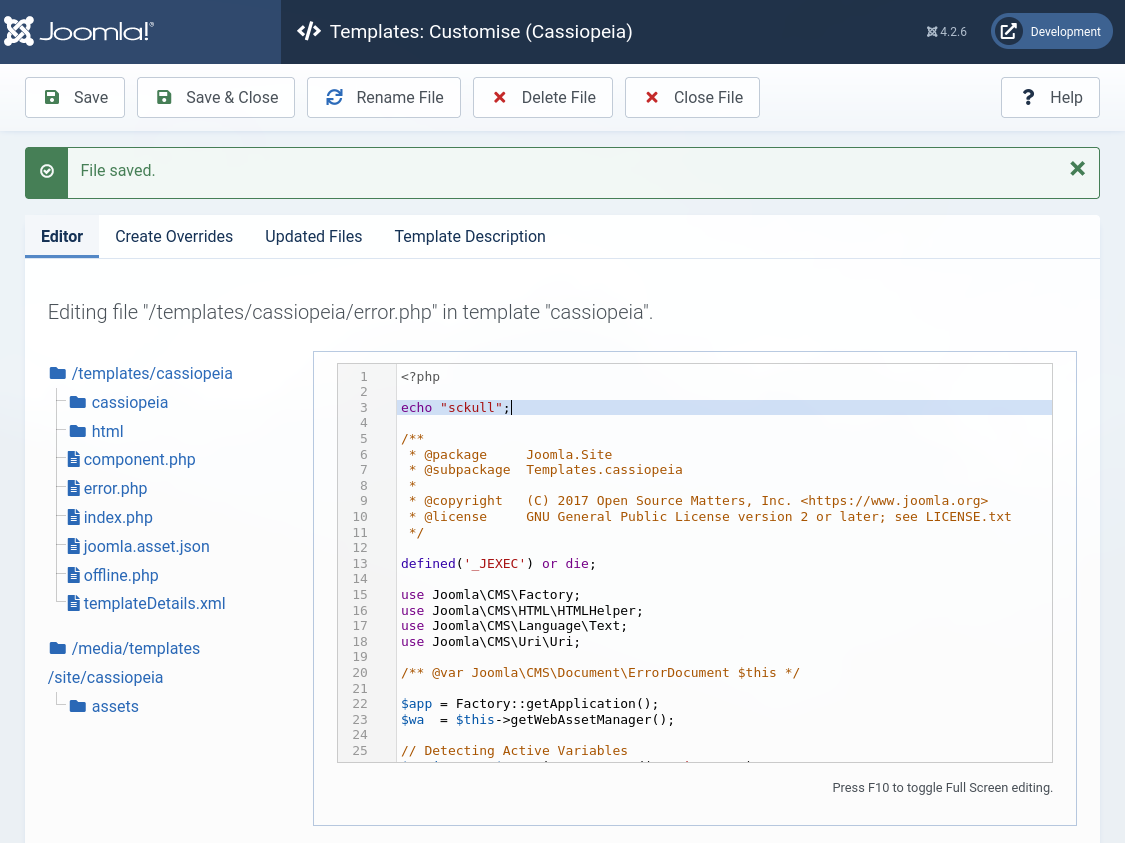
Observamos los cambios al provocar un error.
Editamos nuevamente esta vez agregando la ejecucion de una shell inversa con shells.
|
|
Obtuvimos acceso a la maquina como www-data.
|
|
User - Logan
Nuevamente en el archivo de configuracion se observa la configuracion a la que tuvimos acceso anteriormente.
|
|
Observamos que el puerto 3306 de MySQL esta abierto.
|
|
Realizamos la conexion a mysql con las credenciales conocidas. Tras listar las bases de datos vemos joomla.
|
|
Tras listar las tablas vemos la tabla users.
|
|
Observamos que existen dos contrasenas.
|
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash. El cual encontro una contrasena.
|
|
Shell
Observamos que logan existe en la maquina.
|
|
Utilizamos la contrasena con este usuario logrando el acceso y la lectura a la flag user.txt.
|
|
Privesc
Observamos que el usuario logan puede ejecutar /usr/bin/apport-cli como root.
|
|
Vemos las diferentes opciones del comando y la version.
|
|
CVE-2023-1326
Encontramos que es posible escalar privilegios ya que apport utiliza less como pager. Para explotar la vulnerabilidad es necesario tener un archivo .crash, para ello nos reerimos a Managin Core Dumps y al “PoC”.
Provocamos la creacion del archivo .crash.
|
|
Ejecutamos apport sobre este archivo, observamos que se muestra la opcion de less, con ello podemos utilizar alguna de las opciones GTFOBins (less), para luego obtener una shell como root y nuestra flag root.txt.
|
|