El sitio web de Zipping permite la subida de archivos Zip aceptando PDFs dentro de este, realizamos la lectura de archivos atraves de Zip Symlik lo que nos permitio el acceso al codigo fuente del sitio. Posteriormente logramos la subida de una shell inversa tras realizar Bypass a la subida de archivos mediante Null Byte Injection. Finalmente, escalamos privilegios tras crear una libreria personalizada para la ejecucion de un fichero.
| Nombre | Zipping |
|---|---|
| OS | Linux |
| Puntos | 30 |
| Dificultad | Media |
| IP | 10.10.11.229 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
|
|
Web Site
No muestra ninguna redireccion a algun dominio, pero si se muestra un Apache como servidor.
|
|
El sitio web muestra informacion sobre la empresa.
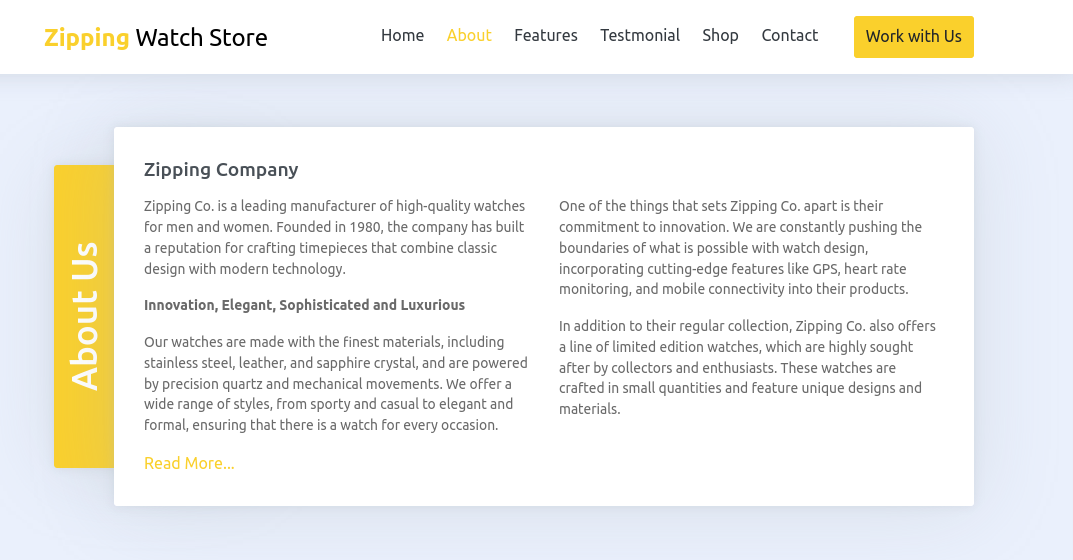
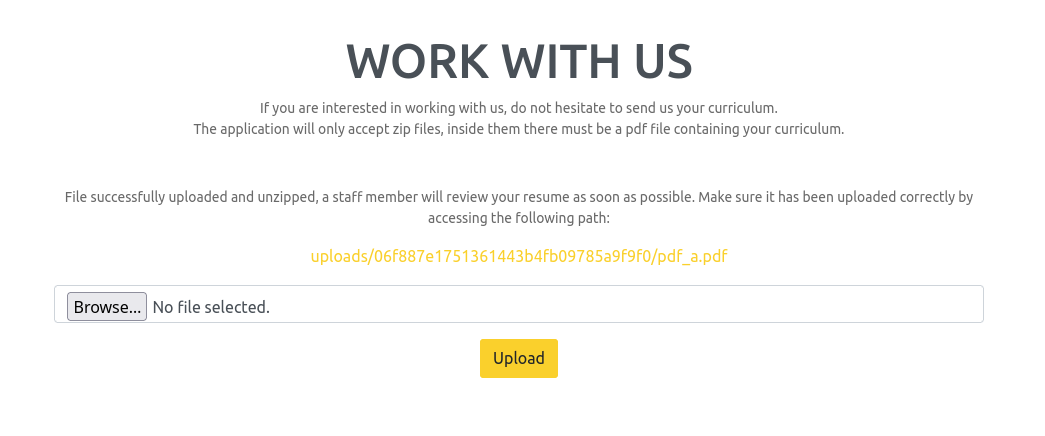
En ‘work with us’ se muestra un formulario para subida de archivos.
Encontramos una tienda funcional en shop/.
Zip Symlink
El formulario de subida de archivos unicamente acepta archivos .ZIP y dentro debe de existir un archivo PDF. Creamos un PDF y lo comprimimos en un archivo zip.
|
|
Al subirlo nos retorna un link el cual muestra el pdf dentro del archivo zip.
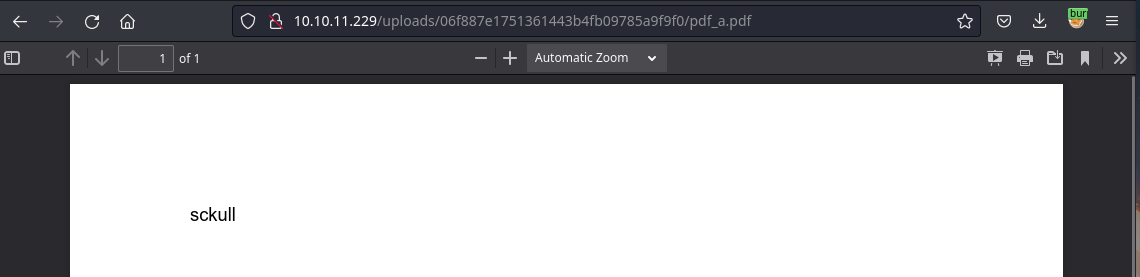
Investigando sobre sobre vulnerabilidades en ZIP nos topamos con ZIP Symlink. Esto permite acceder a archivos representados por enlaces simbolicos dentro del archivo zip. Simplemente creamos un enlace simbolico apuntando a un archivo, lo comprimimos y al observar el archivo comprimido este tendria el contenido del enlace simbolico.
En este caso el archivo /etc/passwd esta representado como un enlace simbolico por nombre file.pdf el cual comprimimos.
|
|
Como sabemos el archivo es descomprimido y el pdf puesto en un directorio, file.pdf al ser un enlace simbolico apuntaria a /etc/passwd y podriamos ver el contenido de este como se esperaba.
|
|
Source Code
Creamos un pequeno script para crear un archivo zip. En este caso logramos adivinar el directorio donde el sitio web esta almacenado.
|
|
Observamos el codigo fuente de upload.php.
Si observamos, verifica que el archivo extraido tenga la extension PDF en caso contrario muestra un mensaje.
|
|
Tambien, logramos obtener el codigo fuente de la tienda.
Null Byte Injection
Intentamos realizar bypass a la restriccion de archivos unicos PDF utilizando null byte. Primero, creamos un archivo con codigo PHP en este caso un simple echo, el nombre lo identificamos como file.phpA.pdf tomamos en cuenta la letra A la cual cambiamos adelante. Comprimimos el archivo en un ZIP.
|
|
Utilizando Burpsuite interceptamos la subida del archivo, nos dirigimos a la pestana Hex, en la ultima columna buscamos file.phpA.pdf y nos ubicamos en la letra A con valor 41 en la tabla Hex y lo modificamos a un valor null 00. Tras realizar el cambio enviamos la solicitud.
Nos retorna la direccion con el archivo file.php .pdf hay que notar que la direccion contiene un espacio, tras visitar esta direccion esta aparece como no disponible, sin embargo si eliminamos el espacio y la extension pdf nos devuelve la ejecucion del codigo php.
|
|
Ref. 1
User - Rektsu
Con lo anterior, creamos un archivo para la ejecucion de una shell inversa utilizando shells.
|
|
Tras la ejecucion logramos obtener una shell como rektsu y nuestra flag user.txt.
|
|
Privesc
Encontramos que rektsu puede ejecutar el fichero /usr/bin/stock como root.
|
|
Tras ejecutar el archivo requiere una contrasena.
|
|
Pasamos strings sobre el fichero vemos una direccion de un archivo .csv y dos strings interesantes: Hakaize y St0ckM4nager.
|
|
Tras ingresar St0ckM4nager es aceptada como contrasena. Sin embargo no encontramos algun valor manipulable.
|
|
strace nos muestra mas informacion sobre el fichero, vemos que este intenta acceder a /home/rektsu/.config/libcounter.so el cual no existe.
|
|
Creamos y compilamos la libreria libcounter.so a la carpeta /home/rektsu/.config/ la cual ejecuta /bin/sh. (2)
|
|
Tras ejecutar nuevamente el fichero con sudo obtuvimos una shell como root y nuestra flag root.txt.
|
|