Environment expone una aplicacion Laravel en modo debug, esto permitio conocer la logica de autenticacion de un valor en la variable de entorno y, con una vulnerabilidad que permite realizar cambios a este logramos el acceso. Tambien, descubrimos un manejador de archivos vulnerable a code injection que posteriormente nos dio acceso inicial. Las claves privadas GPG y un archivo encriptado facilitaron las credenciales para un segundo usuario. Escalamos privilegios con un comando que mantiene el valor de BASH_ENV para la ejecucion de comandos como root.
| Nombre | Environment |
|---|---|
| OS | Linux |
| Puntos | 30 |
| Dificultad | Medium |
| Fecha de Salida | 2025-05-03 |
| IP | 10.10.11.67 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
|
|
Web Site
El sitio web nos redirige al dominio environment.htb el cual agregamos al archivo /etc/hosts.
|
|
Se presenta una tematica de medio ambiente.
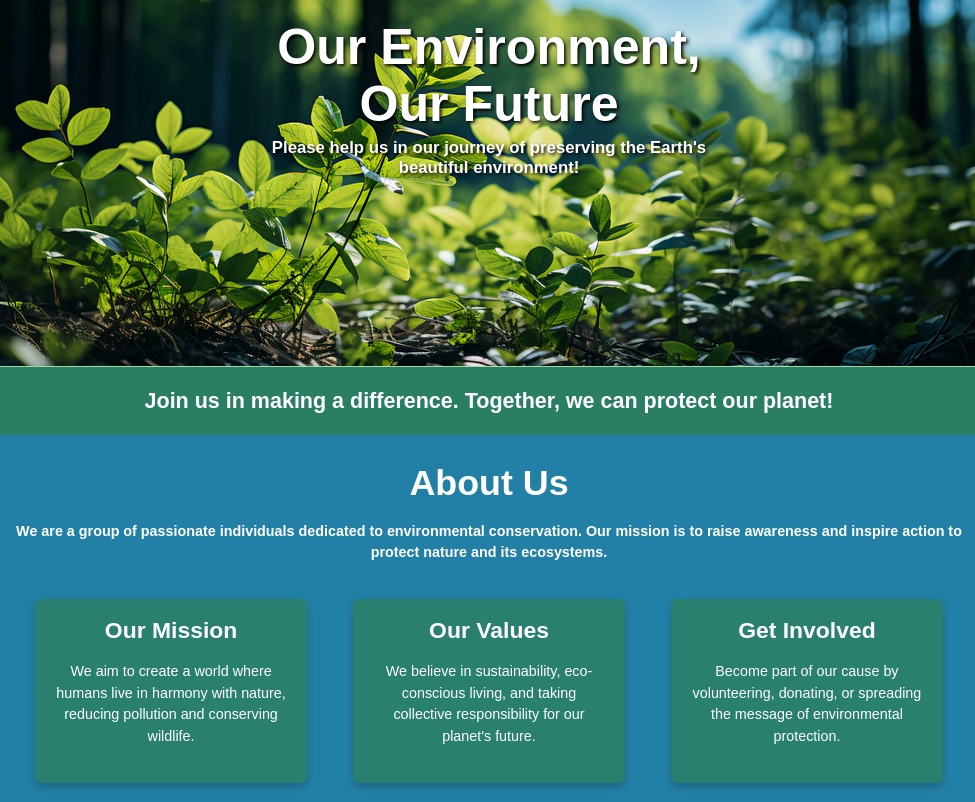
Encontramos un un formulario para emails.
Tras el envio de una direccion email se muestra que se agrego exitosamente. Tambien, se observa que se agrego una cookie a nuestra sesion, se muestra laravel como tecnologia.
|
|
Directory Brute Forcing
feroxbuster muestra los recursos estaticos y paginas php que no existen por lo que se filtro por codigo 404. Entre las direcciones se listan dos con codigo 405: /mailing y /upload.
|
|
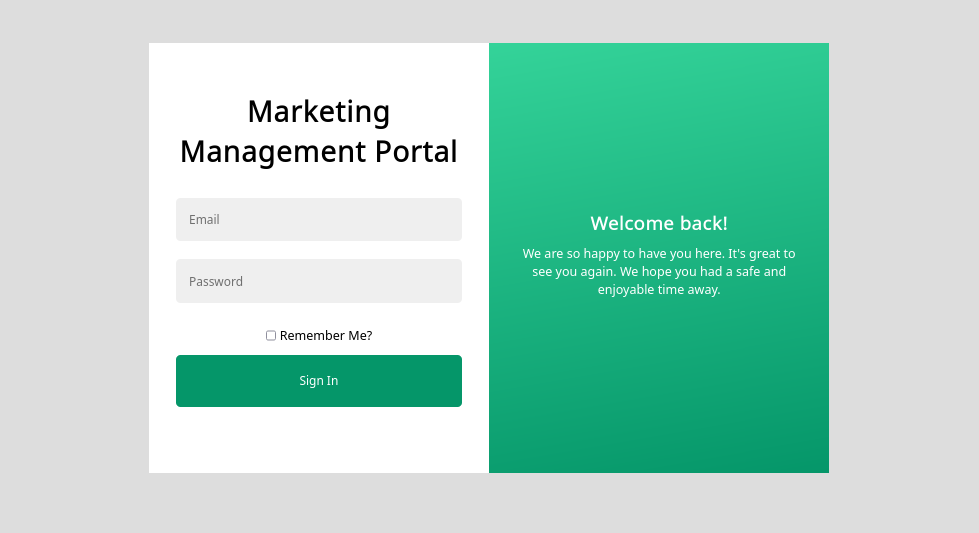
/login muestra un formulario de autenticacion.
/up muestra si la aplicacion esta funcionando.
Laravel Application
La direccion /mailing no acepta peticiones con el metodo GET, se muestra la version de PHP 8.2.28 y laravel 11.30.0, codigo e informacion de la peticion. Esto indicaria que la aplicacion esta siendo ejecutada en modo Debug.
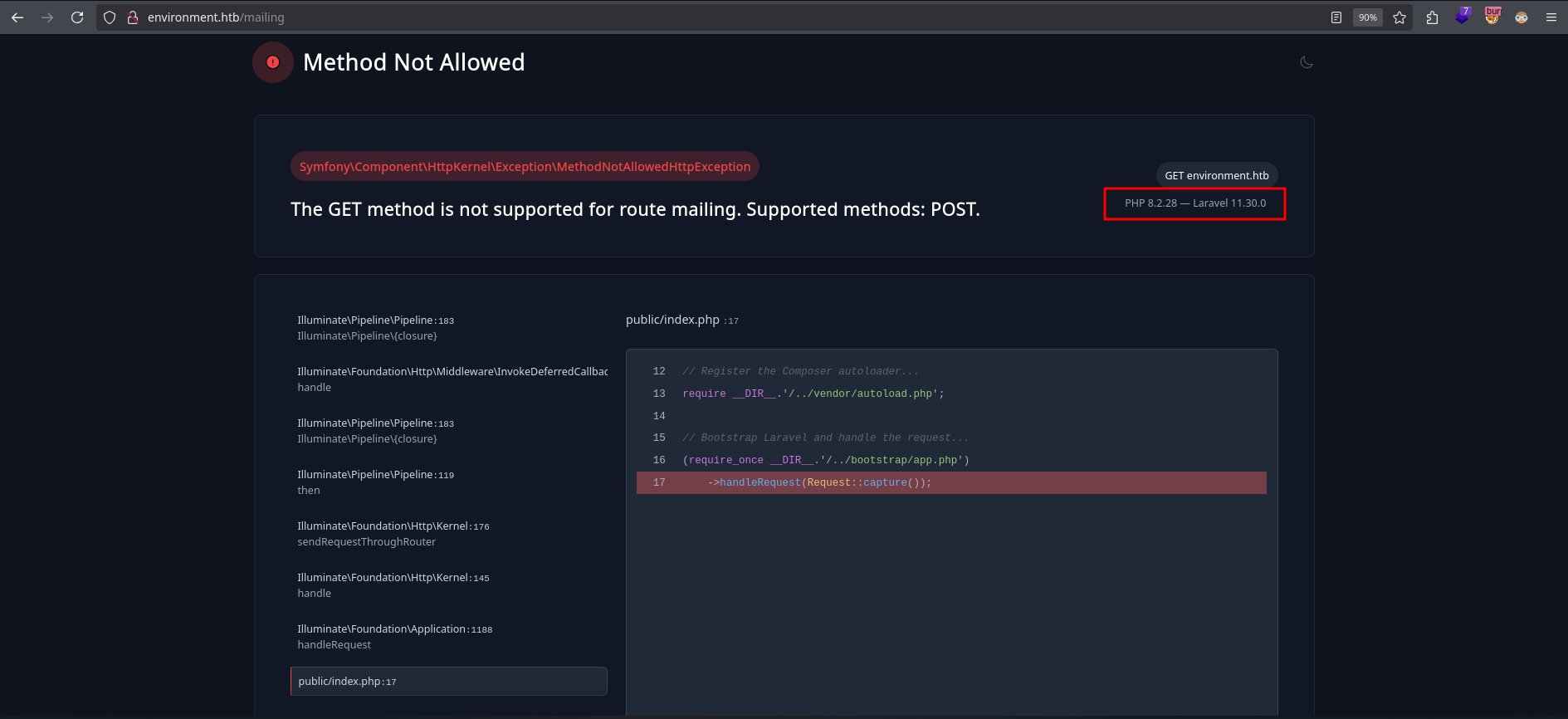
Observamos que /mailing unicamente acepta peticiones POST.
|
|
El mismo caso se observa en /upload.
|
|
Trigger Error
La aplicacion esta en modo Debug, intentamos generar un error en el login cambiando el nombre del parametro enviado en burpsuite, interceptando y modificando la solicitud. El valor email paso a emil, con esto se genero un error y se muestra parte del codigo donde la aplicacion fallo.
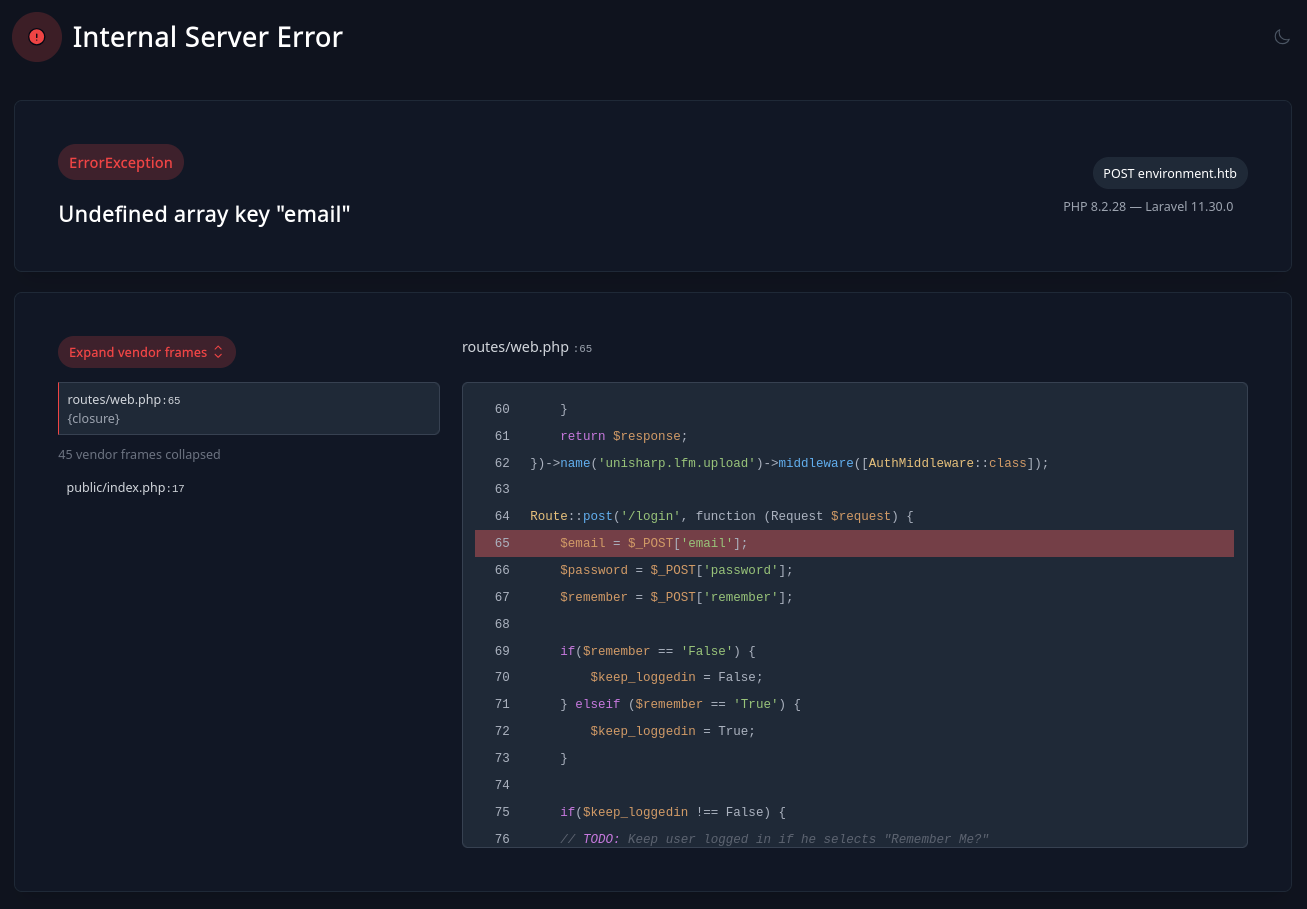
Generamos nuevamente el error cambiando el valor del parametro remember a 0. Esto nos permitiria ver un poco mas de codigo.
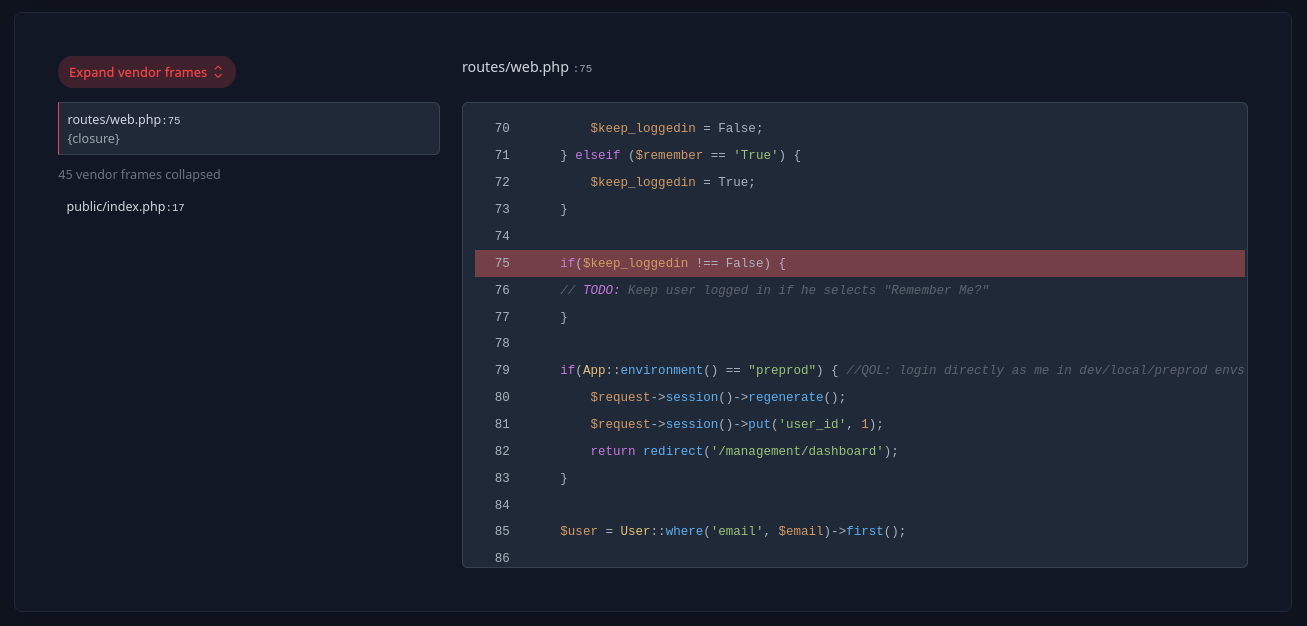
Analysis
Tras analizar el codigo descubrimos dos cosas:
- posible uso de laravel-filemanager lo indica
unisharp.lfm.upload. - Parece existir una opcion unica para desarrolladores, si el valor de APP_ENV tiene el valor
preprodal realizar una solicitud de autenticacion sin importar las credenciales, este autenticaria directamente al usuario conID 1y daria acceso directo al dashboard de la aplicacion.
|
|
CVE-2024-52301
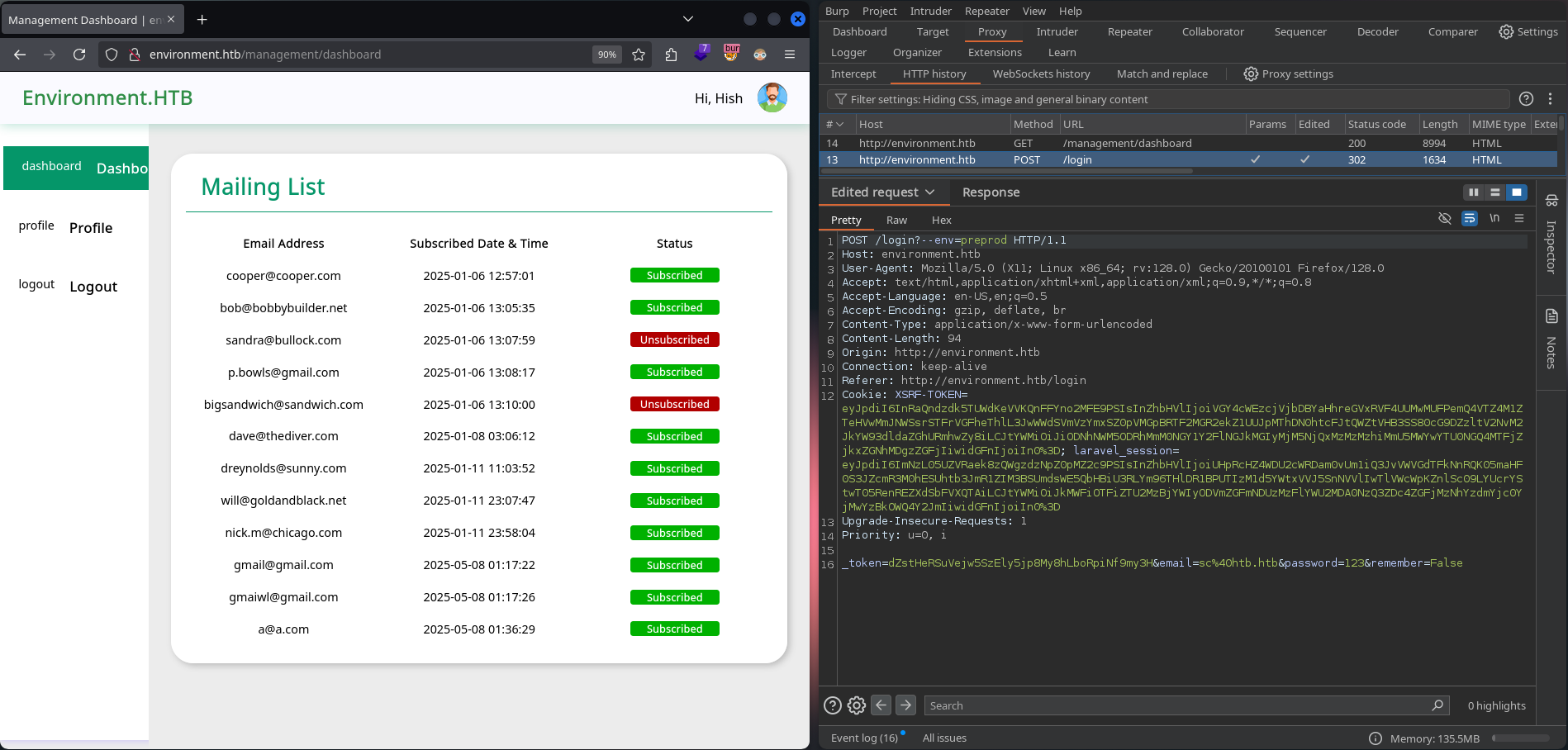
Afortunadamente la version de laravel 11.30.0 esta en el rango de versiones afectadas por el CVE-2024-52301. Esta vulnerabilidad permite realizar cambios en la variable de entorno de la aplicacion. Como unico requisito se muestra que register_argc_argv debe de estar habilitado. Se muestra en el PoC de Nyamort/CVE-2024-52301 que se puede inyectar directamente el valor en la direccion url: http://localhost?--env=local.
En nuestro caso al realizar una solicitud de autenticacion se haria a /login?--env=preprod.
Interceptamos y modificamos la solicitud.
|
|
Tras realizar la solicitud nos autenticamos dentro del dashboard como Hish.
En profile podemos realizar el cambio de imagen de perfil del usuario.
CVE-2024-21546
UniSharp Laravel Filemanager en versiones menores a 2.9.1 tiene una vulnerabilidad Code Injection que permite la subida de archivos PHP lo cual permitiria la Ejecucion Remota de Comandos. Para la subida de archivos exitosa se agrega un “mimetype” valido, como el de una imagen, en el nombre del archivo un punto al final, ej.: rce.php..
Intentamos realizar la explotacion agregando GIF89a al archivo y la ejecucion de whoami, tomamos el mimetype de gif: Content-Type: image/gif.
|
|
Subimos el archivo, interceptamos y modificamos el mimetype a image/gif.
|
|
Se observa que se realizo con exito el cambio.
Realizamos una solicitud al archivo y observamos que el comando se ejecuto correctamente.
|
|
User - www-data
Subimos una pequena webshell y con shells ejecutamos una shell inversa.
|
|
Logrando el acceso como www-data mediante una shell.
|
|
Database
Descubrimos la base de datos sqlite de la aplicacion.
|
|
Se observan tres usuarios con su respectiva hash de contrasena. Intentamos el crackeo de estas pero sin suerte.
|
|
www-data tiene acceso a el directorio de hish, logramos la lectura de la flag user.txt.
|
|
User - Hish
El usuario Hish tiene un archivo .gpg encriptado.
|
|
Tambien observamos claves privadas en el directorio .gnupg.
|
|
Decrypt gpg File
Para desencriptar el archivo copiamos la carpeta .gnupg a /dev/shm/ para luego modificar nuestra variable de entorno HOME.
|
|
Con lo anterior ejecutamos gpg con la flag para desencriptar el archivo keyvault.gpg logrando obtener el contenido de este.
|
|
Observamos lo que parecen ser credenciales para sitios web.
|
|
Shell
Ejecutamos su para hish, tras ingresar una de las contrasenas logramos el acceso a este usuario.
|
|
Privesc
Hish puede ejecutar systeminfo como sudo ademas la variable BASH_ENV se mantiene tras su ejecucion.
|
|
El archivo es un script que ejecuta una serie de comandos.
|
|
Este muestra informacion en pantalla.
|
|
BASH_ENV
Cuando la variable BASH_ENV esta definida y se ejecuta un archivo en modo ’no-interactivo’, se ejecuta el script/archivo definido en la sesion actual. Realizamos un test asignando a la variable un script con contenido de ejecucion de un echo.
|
|
Tras la ejecucion se observa que el script se ejecuto.
|
|
Shell
Generamos una clave privada para el usuario hish.
|
|
Agregamos el contenido de la clave publica al archivo authorized_keys del usuario root.
|
|
Realizamos la ejecucion.
|
|
Ingresamos como root por SSH localmente logrando acceder a este usuario y a la flag root.txt.
|
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
|
|