CTF collection Vol.1 es una serie de retos de Esteganografia, Reversing, Analisis de Codigo, OSINT like.
Room
| Titulo |
CTF collection Vol.1  |
| Descripción |
Sharpening up your CTF skill with the collection. The first volume is designed for beginner. |
| Puntos |
700 |
| Dificultad |
Facil |
| Maker |
DesKel  |
What does the base said?
Can you decode the following?
Reto:
1
|
VEhNe2p1NTdfZDNjMGQzXzdoM19iNDUzfQ==
|
Reto:
Solucion:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
➜ ctf_collection_vol1 exiftool Findme.jpg
ExifTool Version Number : 10.80
File Name : Findme.jpg
Directory : .
File Size : 34 kB
File Modification Date/Time : 2020:02:12 17:29:21-06:00
File Access Date/Time : 2020:02:12 17:29:54-06:00
File Inode Change Date/Time : 2020:02:12 17:29:49-06:00
File Permissions : rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
X Resolution : 96
Y Resolution : 96
Exif Byte Order : Big-endian (Motorola, MM)
Resolution Unit : inches
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
Flashpix Version : 0100
Owner Name : THM{... snip ...}
Comment : CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 60.
Image Width : 800
Image Height : 480
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 800x480
Megapixels : 0.384
➜ ctf_collection_vol1
|
Mon, are we going to be okay?
Something is hiding. That’s all you need to know.
Solucion:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
➜ ctf_collection_vol1 steghide info Extinction.jpg
"Extinction.jpg":
format: jpeg
capacity: 1.3 KB
Try to get information about embedded data ? (y/n)
➜ ctf_collection_vol1 steghide info Extinction.jpg
"Extinction.jpg":
format: jpeg
capacity: 1.3 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "Final_message.txt":
size: 79.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
➜ ctf_collection_vol1 steghide extract -sf Extinction.jpg
Enter passphrase:
wrote extracted data to "Final_message.txt".
➜ ctf_collection_vol1 cat Final_message.txt
It going to be over soon. Sleep my child.
THM{... snip ...}
➜ ctf_collection_vol1
|
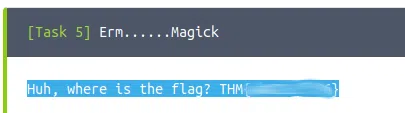
Erm……Magick
Huh, where is the flag?
Solucion:
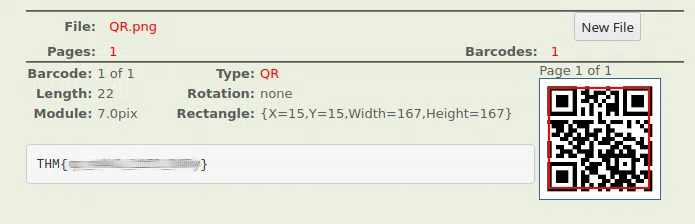
QRrrrr
Such technology is quite reliable.
Solucion:
Reverse it or read it?
Solucion:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
➜ ctf_collection_vol1 r2 hello.hello
[0x00001060]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze len bytes of instructions for references (aar)
[x] Analyze function calls (aac)
[x] Use -AA or aaaa to perform additional experimental analysis.
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[0x00001060]> afl
0x00001000 3 23 sym._init
0x00001030 1 6 sym.imp.puts
0x00001040 1 6 sym.imp.printf
0x00001050 1 6 sub.__cxa_finalize_248_50
0x00001060 1 43 entry0
0x00001090 3 33 sym.deregister_tm_clones
0x000010c0 3 50 sym.register_tm_clones
0x00001100 4 49 sym.__do_global_dtors_aux
0x00001140 1 5 entry1.init
0x00001145 1 24 sym.skip
0x0000115d 1 23 sym.main
0x00001180 4 93 sym.__libc_csu_init
0x000011e0 1 1 sym.__libc_csu_fini
0x000011e4 1 9 sym._fini
[0x00001060]> pdf @sym.skip
/ (fcn) sym.skip 24
| sym.skip ();
| 0x00001145 55 push rbp
| 0x00001146 4889e5 mov rbp, rsp
| 0x00001149 488d3db80e00. lea rdi, qword str.THM_345y_f1nd_345y_60 ; 0x2008 ; "THM{... snip ...}"
| 0x00001150 b800000000 mov eax, 0
| 0x00001155 e8e6feffff call sym.imp.printf ; int printf(const char *format)
| 0x0000115a 90 nop
| 0x0000115b 5d pop rbp
\ 0x0000115c c3 ret
[0x00001060]>
|
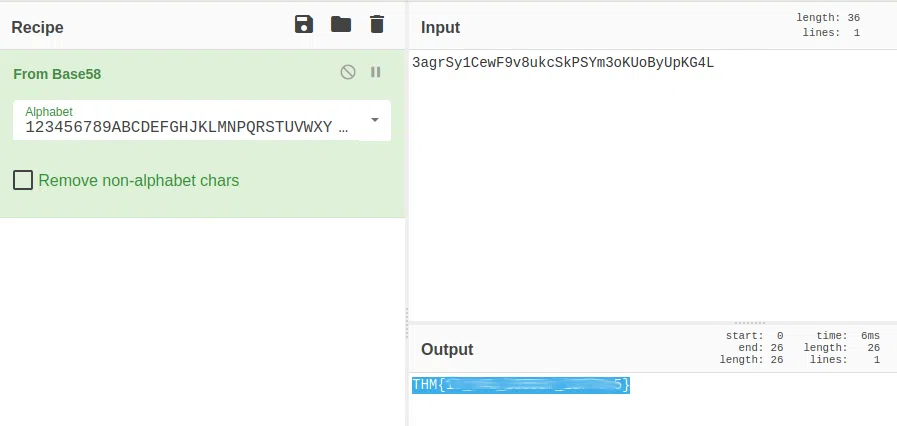
Another decoding stuff
Can you decode it?
Reto:
1
|
3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L
|
Solucion:
Left or right
Left, right, left, right… Rot 13 is too mainstream. Solve this
Reto:
Solucion:
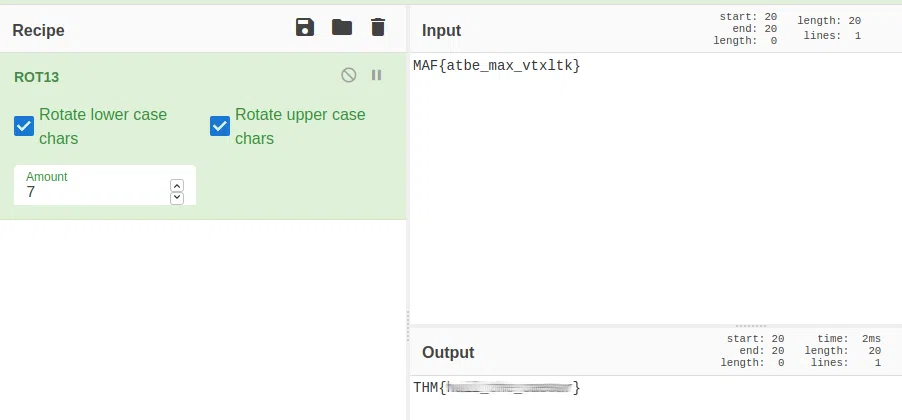
No downloadable file, no ciphered or encoded text. Huh …….
Solucion:
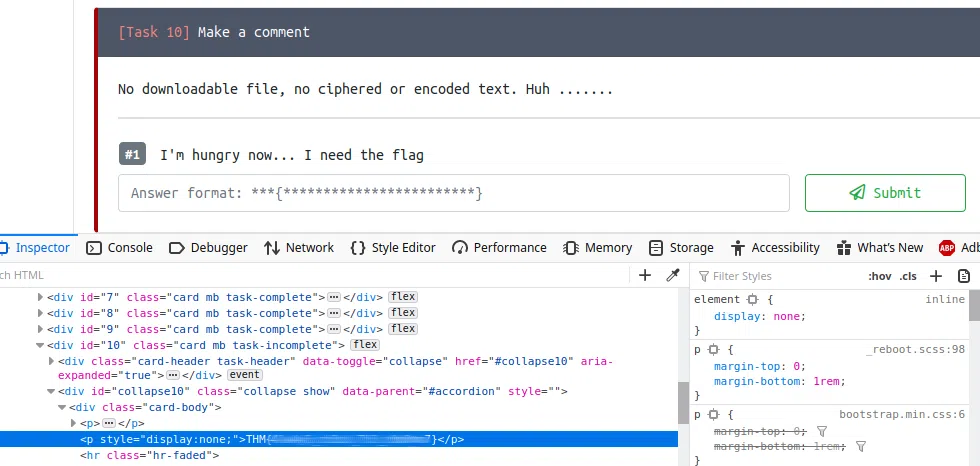
Can you fix it?
I accidentally messed up with this PNG file. Can you help me fix it? Thanks, ^^
Pasamos el archivo a Hexadecimal, editamos el archivo y reemplazamos la cantidad de “magic numbers” de un archivo PNG, luego de esto podemos obtener nuestra imagen renderizando la con CyberChef.
Reto:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
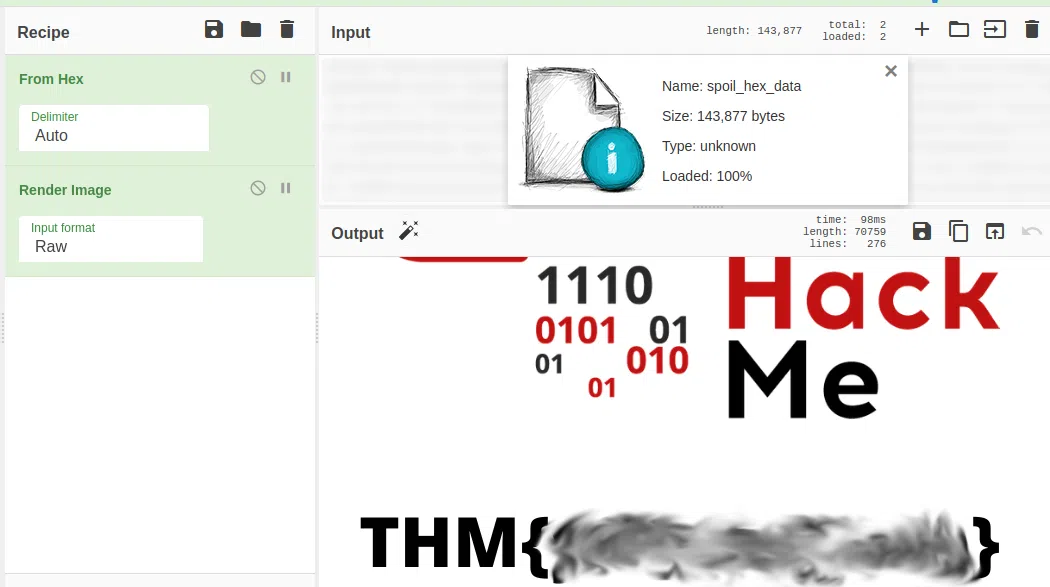
➜ ctf_collection_vol1 xxd -p spoil.png > spoil_hex_data
➜ ctf_collection_vol1 head spoil
head: cannot open 'spoil' for reading: No such file or directory
➜ ctf_collection_vol1 head spoil_hex_data
2333445f0d0a1a0a0000000d4948445200000320000003200806000000db
700668000000017352474200aece1ce9000000097048597300000ec40000
0ec401952b0e1b0000200049444154789cecdd799c9c559deff1cf799e5a
bb7a5f927477f640480209201150c420bba288a8805c19067c5d64c079e9
752e03ce38e30e8e2f75e63a23ea8c0ce8308e036470c191cd80880c4b20
0909184c42b64ed2e9f4bed7f23ce7fe51559dea4e27a4bbaaf7effbf5ea
57d2d5554f9daa7abafa7ceb9cf33bc65a6b1111111111111907ce443740
4444444444660e0510111111111119370a202222222222326e1440444444
444464dc28808888888888c8b8510011111111119171a300222222222222
e34601444444444444c68d028888888888888c1b0510111111111119370a
➜ ctf_collection_vol1 vim spoil_hex_data
➜ ctf_collection_vol1 head spoil_hex_data
89504E470D0A1A0A0000000d4948445200000320000003200806000000db
700668000000017352474200aece1ce9000000097048597300000ec40000
0ec401952b0e1b0000200049444154789cecdd799c9c559deff1cf799e5a
bb7a5f927477f640480209201150c420bba288a8805c19067c5d64c079e9
752e03ce38e30e8e2f75e63a23ea8c0ce8308e036470c191cd80880c4b20
0909184c42b64ed2e9f4bed7f23ce7fe51559dea4e27a4bbaaf7effbf5ea
57d2d5554f9daa7abafa7ceb9cf33bc65a6b1111111111111907ce443740
4444444444660e0510111111111119370a202222222222326e1440444444
444464dc28808888888888c8b8510011111111119171a300222222222222
e34601444444444444c68d028888888888888c1b0510111111111119370a
➜ ctf_collection_vol1
|
Solucion:
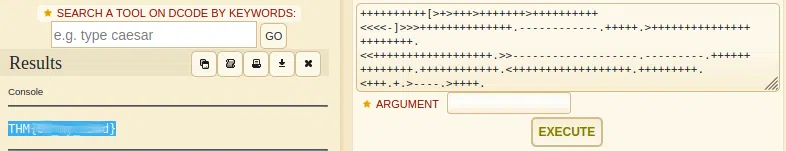
Read it
Some hidden flag inside Tryhackme social account.
Solucion:

Spin my head
What is this?
Reto:
1
|
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>++++++++++++++.------------.+++++.>+++++++++++++++++++++++.<<++++++++++++++++++.>>-------------------.---------.++++++++++++++.++++++++++++.<++++++++++++++++++.+++++++++.<+++.+.>----.>++++.
|
Solucion:
An exclusive!
Exclusive strings for everyone!
Reto:
1
2
|
S1: 44585d6b2368737c65252166234f20626d
S2: 1010101010101010101010101010101010
|
Solucion:
1
2
3
4
5
6
|
script.py
s1 = "44585d6b2368737c65252166234f20626d"
s2 = "1010101010101010101010101010101010"
a = hex(int(s1, 16) ^ int(s2, 16))[2:]
print(bytes.fromhex(a).decode('utf-8'))
|
Binary walk
Please exfiltrate my file :)
Solucion:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
➜ ctf_collection_vol1 binwalk hell.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.02
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
265845 0x40E75 Zip archive data, at least v2.0 to extract, uncompressed size: 69, name: hello_there.txt
266099 0x40F73 End of Zip archive, footer length: 22
➜ ctf_collection_vol1 binwalk hell.jpg -e
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.02
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
265845 0x40E75 Zip archive data, at least v2.0 to extract, uncompressed size: 69, name: hello_there.txt
266099 0x40F73 End of Zip archive, footer length: 22
➜ ctf_collection_vol1 ls
Extinction.jpg Findme.jpg _hell.jpg.extracted help.txt spoil_hex_data ti.py
Final_message.txt hell.jpg hello.hello img spoil.webp
➜ ctf_collection_vol1 ls _hell.jpg.extracted
40E75.zip hello_there.txt
➜ ctf_collection_vol1 cat _hell.jpg.extracted/hello_there.txt
Thank you for extracting me, you are the best!
THM{... snip ...}
➜ ctf_collection_vol1
|
Darkness
There is something lurking in the dark.
Solucion:
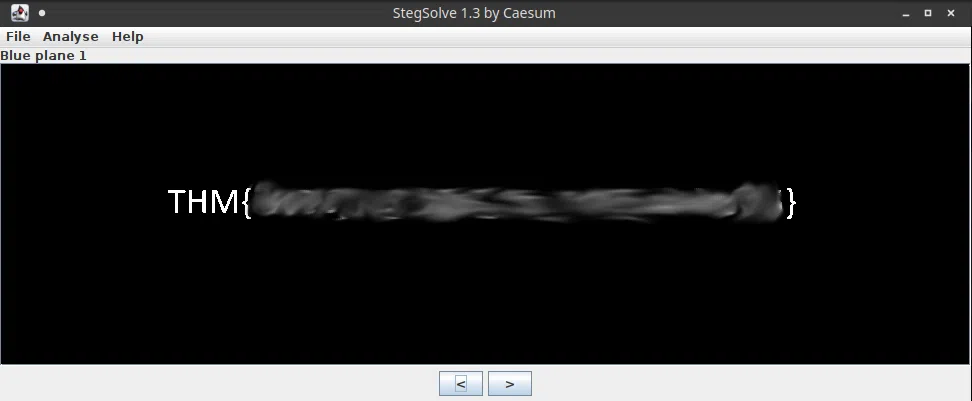
A sounding QR
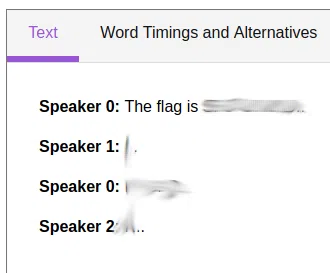
How good is your listening skill?
P/S: The flag formatted as THM{Listened Flag}, the flag should be in All CAPS
Solucion:
QR:
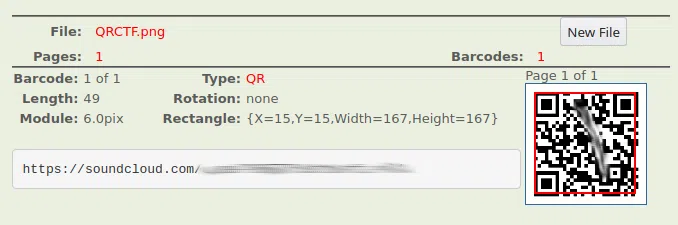
Descargamos el archivo de audio y utilizamos Speech to Text.
Dig up the past
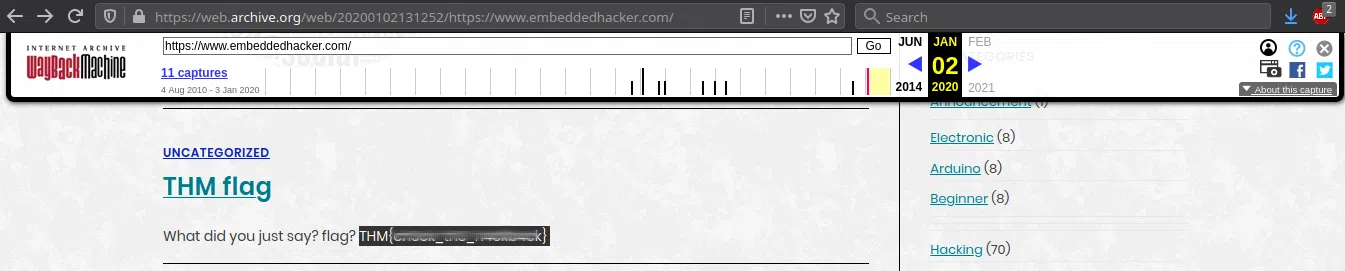
Sometimes we need a ‘machine’ to dig the past.
Reto:
1
2
|
Targetted website: https://www.embeddedhacker.com/
Targetted time: 2 January 2020
|
Utilizamos web.archive.org para obtener nuestra flag en la fecha descrita.
Solucion:
Uncrackable!
Can you solve the following? By the way, I lost the key. Sorry >.<
Reto:
1
2
3
|
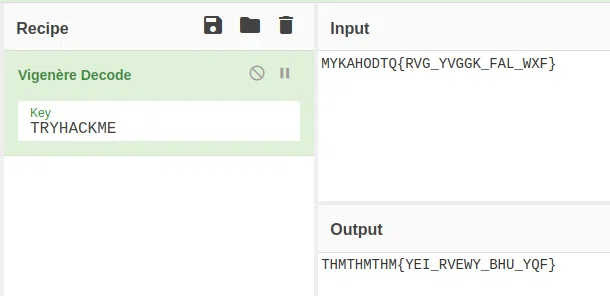
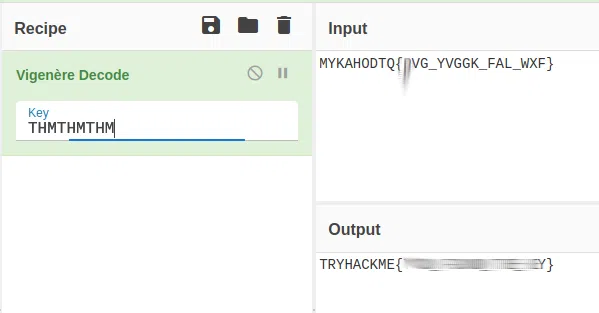
MYKAHODTQ{RVG_YVGGK_FAL_WXF}
Flag format: TRYHACKME{FLAG IN ALL CAP}
|
Utilizamos Vignere Decoder para obtener primero la KEY, utilizamos el formato del flag como KEY (TRYHACKME), luego de eso utilizamos el mismo formato de lo que obtuvimos.
Solucion:
Small bases
Decode the following text.
Reto:
1
|
581695969015253365094191591547859387620042736036246486373595515576333693
|
Solucion:
Decimal > Hex
Hex - Ascii
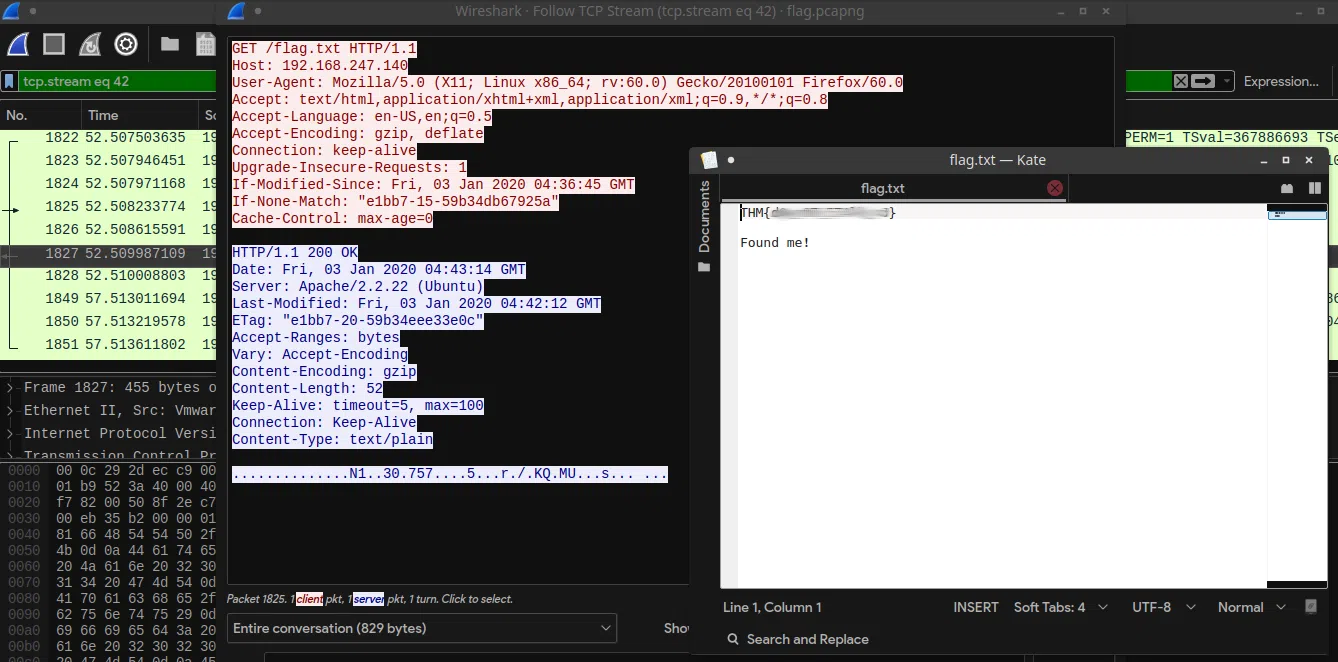
Read the packet
I just hacked my neighbor’s WiFi and try to capture some packet. He must be up to no good. Help me find it.
Solucion:
HTTP Wireshark.