Stealthcopter CTF Primer es una serie de retos de TryHackMe donde utilizamos distintas herramientas para resolver los retos.
Room
WEB
w.01
Revisa el codigo fuente de la pagina.
w.02
Repara el nombre del script en la cabecera del archivo HTML y revisa la consola (developmer tools).
w.03
Imagen base64 codificada.
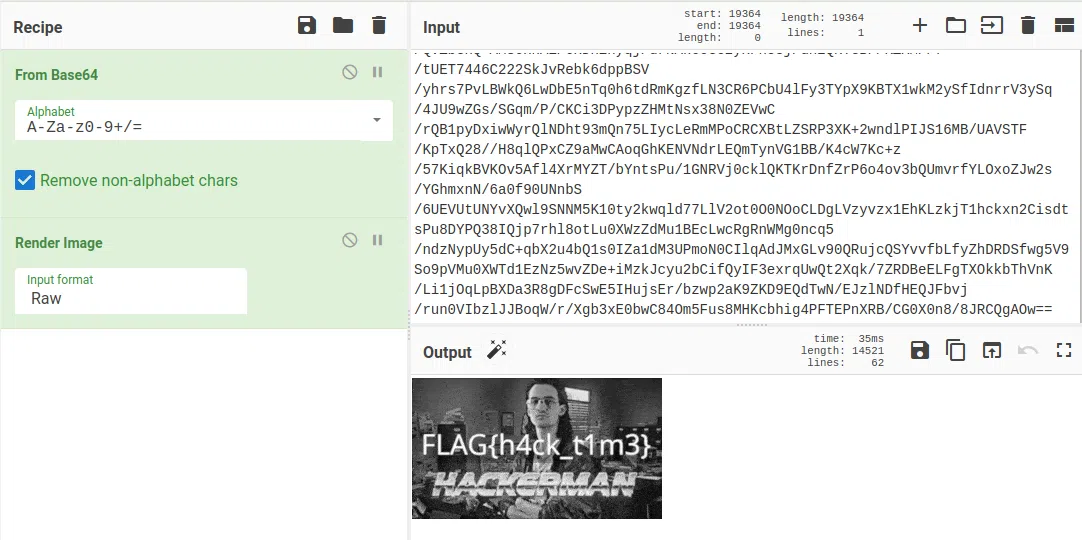
w.04
Elimina los // en el codigo fuente.
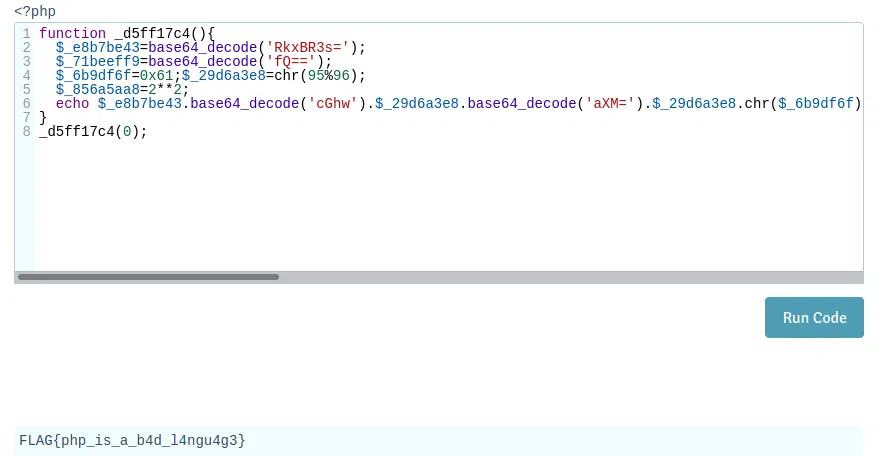
w.05
Key bruteforce o adivina ;).
1
2
3
4
5
|
sckull@uplifted:~/tmp/web$ php w.05.php 'key=7'
Key entered: 7
CipherText: T3FiSXVlOFYvVTJCRHRnRFdTRUZOeHplNVZpK0pQZUVUbWNmTHNCZUt5RT0=
PlainText: FLAG{n0t_s0_t0ugh}
sckull@uplifted:~/tmp/web$
|
w.06
Reto
1
|
var _0x550c=['HsOde8OyacKIw518XMKNPsO8SMO7w4JxwoPCugDCiwh4w43Cqw==','CcK3wq4='];(function(_0x1421f9,_0xa7900b){var _0x371c54=function(_0x5f2f93){while(--_0x5f2f93){_0x1421f9['push'](_0x1421f9['shift']());}};_0x371c54(++_0xa7900b);}(_0x550c,0x1e6));var _0x56ae=function(_0xec1512,_0x3f22ed){_0xec1512=_0xec1512-0x0;var _0x353971=_0x550c[_0xec1512];if(_0x56ae['wlUhtf']===undefined){(function(){var _0x353626=function(){var _0x1efe97;try{_0x1efe97=Function('return\x20(function()\x20'+'{}.constructor(\x22return\x20this\x22)(\x20)'+');')();}catch(_0x299503){_0x1efe97=window;}return _0x1efe97;};var _0x53087e=_0x353626();var _0x4b80a9='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';_0x53087e['atob']||(_0x53087e['atob']=function(_0x8b960b){var _0x584879=String(_0x8b960b)['replace'](/=+$/,'');for(var _0x38ec89=0x0,_0xcfc329,_0xd90795,_0x409b70=0x0,_0x429a24='';_0xd90795=_0x584879['charAt'](_0x409b70++);~_0xd90795&&(_0xcfc329=_0x38ec89%0x4?_0xcfc329*0x40+_0xd90795:_0xd90795,_0x38ec89++%0x4)?_0x429a24+=String['fromCharCode'](0xff&_0xcfc329>>(-0x2*_0x38ec89&0x6)):0x0){_0xd90795=_0x4b80a9['indexOf'](_0xd90795);}return _0x429a24;});}());var _0x4f002d=function(_0x5c44fa,_0x3f22ed){var _0x2dee1d=[],_0x17ee0=0x0,_0x4a4ac3,_0x41b3d2='',_0x329c74='';_0x5c44fa=atob(_0x5c44fa);for(var _0x2ee72b=0x0,_0x1f3f1d=_0x5c44fa['length'];_0x2ee72b<_0x1f3f1d;_0x2ee72b++){_0x329c74+='%'+('00'+_0x5c44fa['charCodeAt'](_0x2ee72b)['toString'](0x10))['slice'](-0x2);}_0x5c44fa=decodeURIComponent(_0x329c74);for(var _0xbc2d51=0x0;_0xbc2d51<0x100;_0xbc2d51++){_0x2dee1d[_0xbc2d51]=_0xbc2d51;}for(_0xbc2d51=0x0;_0xbc2d51<0x100;_0xbc2d51++){_0x17ee0=(_0x17ee0+_0x2dee1d[_0xbc2d51]+_0x3f22ed['charCodeAt'](_0xbc2d51%_0x3f22ed['length']))%0x100;_0x4a4ac3=_0x2dee1d[_0xbc2d51];_0x2dee1d[_0xbc2d51]=_0x2dee1d[_0x17ee0];_0x2dee1d[_0x17ee0]=_0x4a4ac3;}_0xbc2d51=0x0;_0x17ee0=0x0;for(var _0x4301cb=0x0;_0x4301cb<_0x5c44fa['length'];_0x4301cb++){_0xbc2d51=(_0xbc2d51+0x1)%0x100;_0x17ee0=(_0x17ee0+_0x2dee1d[_0xbc2d51])%0x100;_0x4a4ac3=_0x2dee1d[_0xbc2d51];_0x2dee1d[_0xbc2d51]=_0x2dee1d[_0x17ee0];_0x2dee1d[_0x17ee0]=_0x4a4ac3;_0x41b3d2+=String['fromCharCode'](_0x5c44fa['charCodeAt'](_0x4301cb)^_0x2dee1d[(_0x2dee1d[_0xbc2d51]+_0x2dee1d[_0x17ee0])%0x100]);}return _0x41b3d2;};_0x56ae['ZUnPBK']=_0x4f002d;_0x56ae['ffVsLy']={};_0x56ae['wlUhtf']=!![];}var _0x5e7cc1=_0x56ae['ffVsLy'][_0xec1512];if(_0x5e7cc1===undefined){if(_0x56ae['RhVTbi']===undefined){_0x56ae['RhVTbi']=!![];}_0x353971=_0x56ae['ZUnPBK'](_0x353971,_0x3f22ed);_0x56ae['ffVsLy'][_0xec1512]=_0x353971;}else{_0x353971=_0x5e7cc1;}return _0x353971;};function callme(){var _0x4b81bb=_0x56ae('0x0','E^eq');console[_0x56ae('0x1','X!jV')](_0x4b81bb);}
|
Ejecuta la funcion callme().
w.07
Key bruteforce o adivina ;).
sckull@uplifted:~/tmp/web$ php w.07.php 'key=1337'
Key entered: 1337
CipherText: QXhUQzVLYjJkU2dZOEhkbHQ3dXZ4NndoWlh1Y0hyeUpsVEhVYTFxT3lWbz0=
PlainText:
sckull@uplifted:~/tmp/web$ php w.07.php 'key=1338'
Key entered: 1338
CipherText: QXhUQzVLYjJkU2dZOEhkbHQ3dXZ4NndoWlh1Y0hyeUpsVEhVYTFxT3lWbz0=
PlainText: FLAG{4_l1ttl3_b4t_h4rd3r}
sckull@uplifted:~/tmp/web$
w.08
Reto
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MTIzNCwidXNlcm5hbWUiOiJhZG1pbiIsInBhc3N3b3JkIjoiRkxBR3tqd3RfdDBrM25zX2FyM19jMDBsX2IzNG56fSJ9.gNVX4fCIMvjLYZ0jUY0untMYbPmRNNFzZwXyU01bv-M
Json Web Token
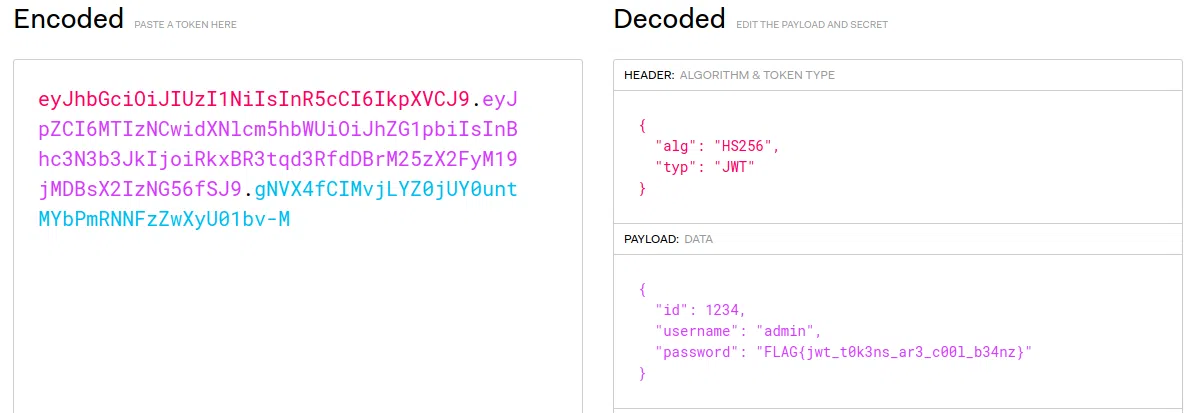
w.09
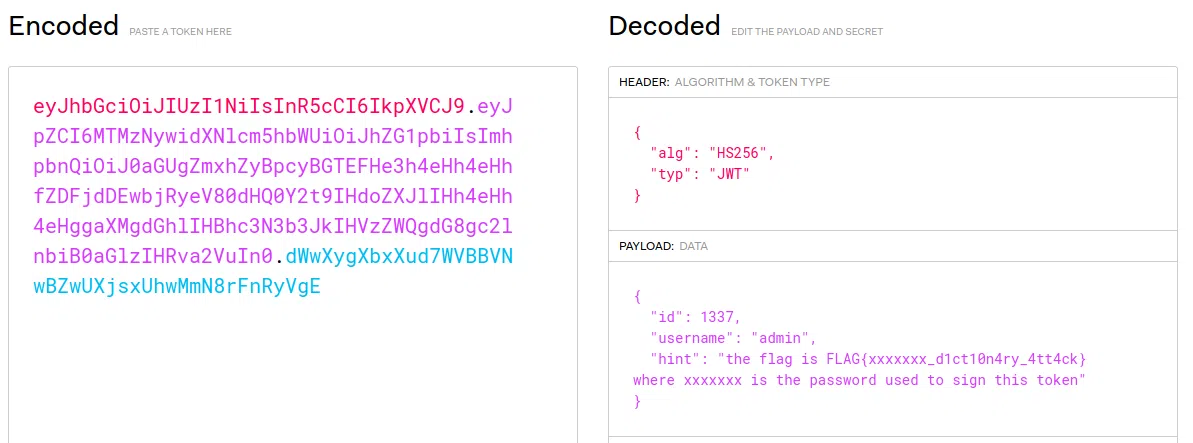
Reto
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MTMzNywidXNlcm5hbWUiOiJhZG1pbiIsImhpbnQiOiJ0aGUgZmxhZyBpcyBGTEFHe3h4eHh4eHhfZDFjdDEwbjRyeV80dHQ0Y2t9IHdoZXJlIHh4eHh4eHggaXMgdGhlIHBhc3N3b3JkIHVzZWQgdG8gc2lnbiB0aGlzIHRva2VuIn0#756c17ca05dbc57b9ded6541055370059c145e3b31521c0c98df2b1674725601
Utilizamos hashcat
sckull@uplifted:~/tmp/web$ /home/sckull/tools/hashcat/hashcat64.bin -m 16500 09web_jwt.txt /home/sckull/tools/rockyou.txt -o 09web_output.txt
hashcat (v5.1.0) starting...
* Device #1: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
nvmlDeviceGetFanSpeed(): Not Supported
OpenCL Platform #1: NVIDIA Corporation
======================================
* Device #1: GeForce MX130, 501/2004 MB allocatable, 3MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Watchdog: Temperature abort trigger set to 90c
Dictionary cache hit:
* Filename..: /home/sckull/tools/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Session..........: hashcat
Status...........: Cracked
Hash.Type........: JWT (JSON Web Token)
Hash.Target......: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MTMzNy...nRyVgE
Time.Started.....: Mon Mar 16 02:21:40 2020 (0 secs)
Time.Estimated...: Mon Mar 16 02:21:40 2020 (0 secs)
Guess.Base.......: File (/home/sckull/tools/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 6400.2 kH/s (8.23ms) @ Accel:512 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 98304/14344385 (0.69%)
Rejected.........: 0/98304 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 123456 -> Donovan
Hardware.Mon.#1..: Temp: 60c Util: 47% Core:1189MHz Mem:2505MHz Bus:4
Started: Mon Mar 16 02:21:29 2020
Stopped: Mon Mar 16 02:21:42 2020
sckull@uplifted:~/tmp/web$ cat 09web_output.txt
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MTMzNywidXNlcm5hbWUiOiJhZG1pbiIsImhpbnQiOiJ0aGUgZmxhZyBpcyBGTEFHe3h4eHh4eHhfZDFjdDEwbjRyeV80dHQ0Y2t9IHdoZXJlIHh4eHh4eHggaXMgdGhlIHBhc3N3b3JkIHVzZWQgdG8gc2lnbiB0aGlzIHRva2VuIn0.dWwXygXbxXud7WVBBVNwBZwUXjsxUhwMmN8rFnRyVgE:rockyou
sckull@uplifted:~/tmp/web$
w.10
La clave esta en el codigo fuente $key = hash( 'sha256', str(0x22C49FE9));
sckull@uplifted:~/tmp/web$ python
Python 2.7.17 (default, Nov 7 2019, 10:07:09)
[GCC 7.4.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> print 0x22C49FE9
583311337
>>>
sckull@uplifted:~/tmp/web$ php w.10.php 'key=583311337'
Key entered: 583311337
CipherText: OWVzUHhVVFNsM0t6NFhDb1FiT0RJaHNrWWYrM3VRMi9FNXcyTGhxbVV0aHpKUjdOcGRVcWtZcWc3djV5OFVxQw==
PlainText: FLAG{1_h0p3_y0u_d1dnt_brut3f0rc3_m3...LINE_16}
sckull@uplifted:~/tmp/web$
Cryptography
c.01
Reto:
RkxBR3sxc3RfdGltZV9sdWNreX0=
Base64
1
2
3
4
5
|
sckull@uplifted:~/tmp/crypto$ cat c.01
RkxBR3sxc3RfdGltZV9sdWNreX0=
sckull@uplifted:~/tmp/crypto$ cat c.01|base64 -d
FLAG{1st_time_lucky}
sckull@uplifted:~/tmp/crypto$
|
c.02
Reto:
VW10NFFsSXpjM3BqYlZKbVpFZHNkRnBZVG1aWlZqbHFZVWRHZVdKWU1EMD0=
Base64 X3
1
|
https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)&input=VlcxME5GRnNTWHBqTTNCcVlsWktiVnBGWkhOa1JuQlpWRzFhV2xacWJIRlpWV1JIWlZkS1dVMUVNRDA9
|
c.03
Reto:
SYNT{fgnoorq_va_gur_onpx}
ROT13
https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,13)&input=U1lOVHtmZ25vb3JxX3ZhX2d1cl9vbnB4fQ
c.04
Reto:
F5yd29CuXST7e5aMKaX4bnkV8xF8dKSMB7E14yWUU
Base58
https://gchq.github.io/CyberChef/#recipe=From_Base58('123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz',false)&input=RjV5ZDI5Q3VYU1Q3ZTVhTUthWDRibmtWOHhGOGRLU01CN0UxNHlXVVU
c.05
Reto:
\H�WPG^DCXET�EHAT�^W�T_RCHAEX^_�XB�I^CX_V;XE�B�EYT�STBE;�B^�BTRDCT;;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL;w}pvJI^CnXBnBDATCnBTRDCTL
1- XOR BruteForce (Key: 31)
2- XOR
https://gchq.github.io/CyberChef/#recipe=XOR_Brute_Force(1,100,0,'Standard',false,true,false,''/disabled)XOR(%7B'option':'Hex','string':'31'%7D,'Standard',false)&input=XEgRV1BHXkRDWEVUEUVIQVQRXlcRVF9SQ0hBRVheXxFYQhFJXkNYX1Y7WEUWQhFFWVQRU1RCRTsSQl4RQlRSRENUOzt3fXB2SkleQ25YQm5CREFUQ25CVFJEQ1RMO3d9cHZKSV5DblhCbkJEQVRDbkJUUkRDVEw7d31wdkpJXkNuWEJuQkRBVENuQlRSRENUTDt3fXB2SkleQ25YQm5CREFUQ25CVFJEQ1RMO3d9cHZKSV5DblhCbkJEQVRDbkJUUkRDVEw7d31wdkpJXkNuWEJuQkRBVENuQlRSRENUTDt3fXB2SkleQ25YQm5CREFUQ25CVFJEQ1RMO3d9cHZKSV5DblhCbkJEQVRDbkJUUkRDVEw7d31wdkpJXkNuWEJuQkRBVENuQlRSRENUTA
c.06
Reto:
Mlw Obkwgxvw vbtzxk mk t filahh gy xrukrtlbgk seilsuxxav mipm uc mlbry t lijbxw gy brlxkagoxr Utxwsk vmhaxvk, utwww hr lax pwmmijl hj s dxcohkh. Am xqhehck t ysjf hj hhecseilsuxxav lytlmmlnmmgg.
Ymjlm hwlvvauxh tr Zmgotr Ttmxalme Txepslh mf 1553, mai ubilwk bw wtlc lh nrvxkwltgh sgw meieiexgx, tnm ml kxwalmiv tep smmieimw lh uvwtd ml ngxae 1863, mljxx gwgmyjbxw dtmij. Mamk xtvfxw ml mai vxlgjbixahg pw vamxyki agwiuabjxktfdx (Yvwgvl xhk 'xzx brvxvmhaxvsuei ubilwk'). Fefr iigiei ztoi lkbiv mh meieiexgx wgvvqimmgg lgzxfik mael tki wllifmbeder Zazxrwkx gaiaijl. Br 1863, Xkbivkbgz Dtwaldm otl xzx ymjlm xg infdbll s zxrwktp exmlgw hj vxvmhaxvagz Zazxrwkx gaiaijl.
Br lax 19xz vxrlnkc lax wuaxqw ptw eblelmkmtnmiv mh Fdtbww wx Zazxrwkx (1523–1596), efw ls svjyakxh aml tjxlifm geex.
Rsmk ypsz bw txeso:
YEEY{vasuheelx_xgdtbvw}
Vigenere-cipher
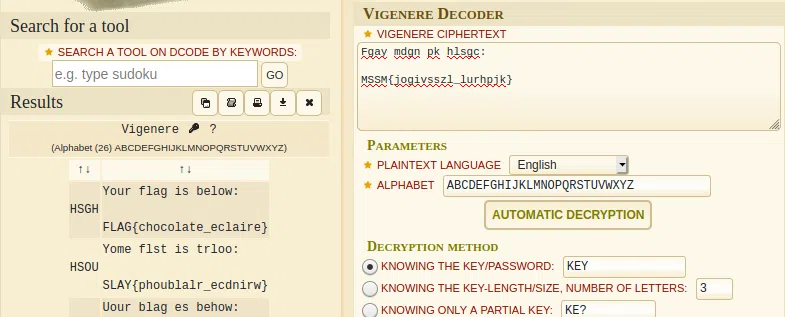
c.07
Reto:
-----BEGIN RSA PRIVATE KEY-----
MIIBOQIBAAJBALWyVLY0Yum5/589v9ECnrHDzDu1AyDP38Ajx6tcul9G2cFUFUMY
Iqf9Wm8BFxNxErdOWmhlJaw+q8rbaAyyRvUCAwEAAQJAWEYrodoRtDwJVPRLHOCI
+RSHRPrMakSUEGVRvI9wfJi654A0HYLyk8JZnf+CbeueI7KnN/2w4MPIkxK9Mjfk
gQIhAP878FR1Yo1X508REZ1YNVDKc6pl33Fm32LVSbz5s/RzAiEAtj3nQwJEgVG4
Bv2CIBZ1CRIGmILeZY3Cx54hGnB55PcCIGy/CgfCN+pHALvUZu/mTFkO2TdJzmkP
zq/adl94+K53AiAZ5PHXM5tIRLRBSgQTSx2WDFmjkfTHuTzT4EQT3ad0QQIgUPy3
p9QrcqBWnnHkTM+MjIjpRzQ2TMLx1e6dOxgYDl4=
-----END RSA PRIVATE KEY-----
openssl enc -in c.07.txt -out binarytext -d -a && openssl rsautl -decrypt -in binarytext -out flag07.txt -inkey c.07.key && cat flag07.txt
c.08
Reto:
hint: bacon
loloooolooololoololoooollollololloooolooloolooolllooloooololololoooooooollooloooloooloooolooooooooloollololloooooooollooooollooloooollooolloloooloooooollooooollloloooloooooolooolll
Bacon Cipher
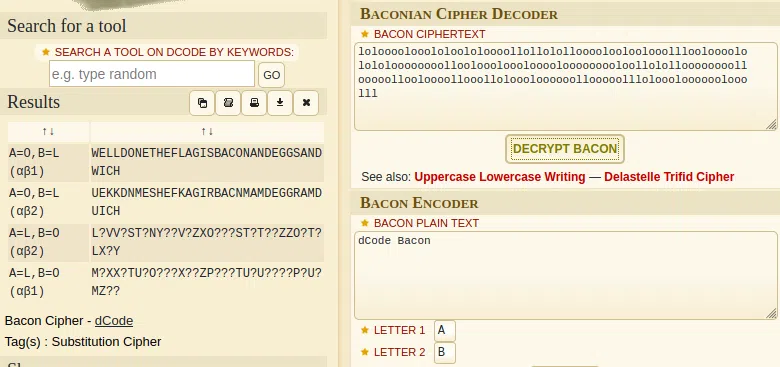
c.09
Reto:
WOPM PM ZG ZDJOZEYWPR MXEMWPWXWPHG RPJOYL VOYLY YZRO DYWWYL PM LYJDZRYT VPWO ZGHWOYL. WOY ZDJOZEYW PM ZERTYUIOPQSDFGHJKLMWXCVBNA. NHXL UDZI PM UDZI{YZMN_ZM_ZER_123}
1- Monoalphabetic Substitution
2- CyberChef - Monoalphabetic Substitution
https://gchq.github.io/CyberChef/#recipe=Substitute('PLAYFM','FLAGYB')&input=VEhJUyBJUyBBTiBBTERIQU1FVElDIFNVTVNUSVRVVElPTiBDSURIRVIgV0hFUkUgRUFDSCBMRVRURVIgSVMgUkVETEFDRUcgV0lUSCBBTk9USEVSLiBUSEUgQUxESEFNRVQgSVMgQU1DR0VQWUhJVlpMS05PREpSU1RVQldRRlguIEZPVVIgUExBWSBJUyBQTEFZe0VBU0ZfQVNfQU1DXzEyM30
FLAG{easy_as_abc_123}
c.10
Reto:
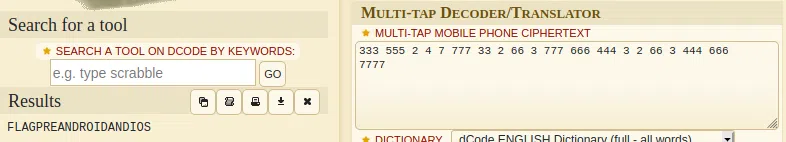
333 555 2 4 7 777 33 2 66 3 777 666 444 3 2 66 3 444 666 7777
Multitap abc Cipher
Forensics
f.01
1
2
3
|
sckull@uplifted:~/tmp/forensics$ cat f.01|grep FLAG
FLAG{here_i_am}
sckull@uplifted:~/tmp/forensics$
|
f.02.wav
Morse - Decoder Audio
f.03.jpg
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
|
sckull@uplifted:~/tmp/forensics$ exiftool f.03.jpg
ExifTool Version Number : 10.80
File Name : f.03.jpg
Directory : .
File Size : 103 kB
File Modification Date/Time : 2019:10:26 13:57:46-06:00
File Access Date/Time : 2019:10:26 13:57:46-06:00
File Inode Change Date/Time : 2020:03:10 18:52:40-06:00
File Permissions : rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Exif Byte Order : Little-endian (Intel, II)
X Resolution : 300
Y Resolution : 300
Resolution Unit : inches
Software : GIMP 2.10.8
Modify Date : 2019:10:20 20:43:54
GPS Latitude : 0 deg 0' 0.00"
GPS Longitude : 0 deg 0' 0.00"
GPS Altitude : 0 m
Compression : JPEG (old-style)
Photometric Interpretation : YCbCr
Samples Per Pixel : 3
Thumbnail Offset : 370
Thumbnail Length : 10424
XMP Toolkit : XMP Core 4.4.0-Exiv2
Digital Source Type : http://cv.iptc.org/newscodes/digitalsourcetype/digitalCapture
Document ID : gimp:docid:gimp:718367af-6e16-4bd5-859e-7d934e66fc4e
Instance ID : xmp.iid:4816adee-26e4-489c-9d9f-125d04d23c3b
Original Document ID : xmp.did:8ea562a1-efa5-4766-b216-6fd07e106c76
Model Release Status : None
Api : 2.0
Platform : Linux
Time Stamp : 1571600638600225
Version : 2.10.8
Format : image/jpeg
Creator Tool : GIMP 2.10
Location Created :
Location Shown :
Artwork Or Object :
Registry ID :
History Action : saved, saved
History Changed : /metadata, /
History Instance ID : xmp.iid:aad9dc17-4a47-49b9-a57f-540623e0091d, xmp.iid:d8a72d8c-5fd0-43b7-a097-16b682f31893
History Software Agent : Gimp 2.10 (Linux), Gimp 2.10 (Linux)
History When : +01:00, +01:00
Image Supplier :
Image Creator :
Copyright Owner :
Licensor :
Creator : type="Seq" FLAG{**********}
Image Width : 800
Image Height : 600
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 800x600
Megapixels : 0.480
Thumbnail Image : (Binary data 10424 bytes, use -b option to extract)
GPS Position : 0 deg 0' 0.00", 0 deg 0' 0.00"
sckull@uplifted:~/tmp/forensics$
|
f.04
1
2
3
4
5
|
sckull@uplifted:~/tmp/forensics$ file _f.04
_f.04: ASCII text
sckull@uplifted:~/tmp/forensics$ cat _f.04
FLAG{*******_****_engaged}
sckull@uplifted:~/tmp/forensics$
|
f.05.png
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
sckull@uplifted:~/tmp/forensics$ binwalk f.05.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1406 x 800, 8-bit/color RGB, non-interlaced
99 0x63 Zlib compressed data, default compression
2093725 0x1FF29D Zip archive data, at least v2.0 to extract, compressed size: 44, uncompressed size: 400, name: flag.txt
2093913 0x1FF359 End of Zip archive
sckull@uplifted:~/tmp/forensics$ binwalk -e f.05.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1406 x 800, 8-bit/color RGB, non-interlaced
99 0x63 Zlib compressed data, default compression
2093725 0x1FF29D Zip archive data, at least v2.0 to extract, compressed size: 44, uncompressed size: 400, name: flag.txt
2093913 0x1FF359 End of Zip archive
sckull@uplifted:~/tmp/forensics$ cd _f.05.png.extracted/
sckull@uplifted:~/tmp/forensics/_f.05.png.extracted$ ls
1FF29D.zip 63 63.zlib flag.txt
sckull@uplifted:~/tmp/forensics/_f.05.png.extracted$ cat flag.txt
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
flag{this_is_another_one_of_them_flags}
sckull@uplifted:~/tmp/forensics/_f.05.png.extracted$
|
f.06.png
1
2
3
4
5
6
7
8
9
10
11
12
13
|
sckull@uplifted:~/tmp/forensics$ xxd f.06.png |head
00000000: 8950 4e58 0d0a 1a0a 0000 000d 4948 4452 .PNX........IHDR
00000010: 0000 0640 0000 0429 0806 0000 0099 68c1 ...@...)......h.
00000020: 1c00 002d c07a 5458 7452 6177 2070 726f ...-.zTXtRaw pro
00000030: 6669 6c65 2074 7970 6520 6578 6966 0000 file type exif..
00000040: 78da ad9c 6992 2d37 8ea5 ff73 15b9 04ce x...i.-7...s....
00000050: c372 4090 34eb 1dd4 f2eb 3b1e 21a9 a4ac .r@.4.....;.!...
00000060: 2ab3 6e6b 3d65 46e8 be3b b813 c019 40f0 *.nk=eF..;....@.
00000070: 86fb 1fff e785 7ffd eb5f 29e6 1443 6d63 ........._)..Cmc
00000080: f6d5 7be4 9fba eaca c62f 33fe fcf3 f333 ..{....../3....3
00000090: c5fa fdff f70f bff6 df47 fff6 78c8 ebfb .........G..x...
sckull@uplifted:~/tmp/forensics$
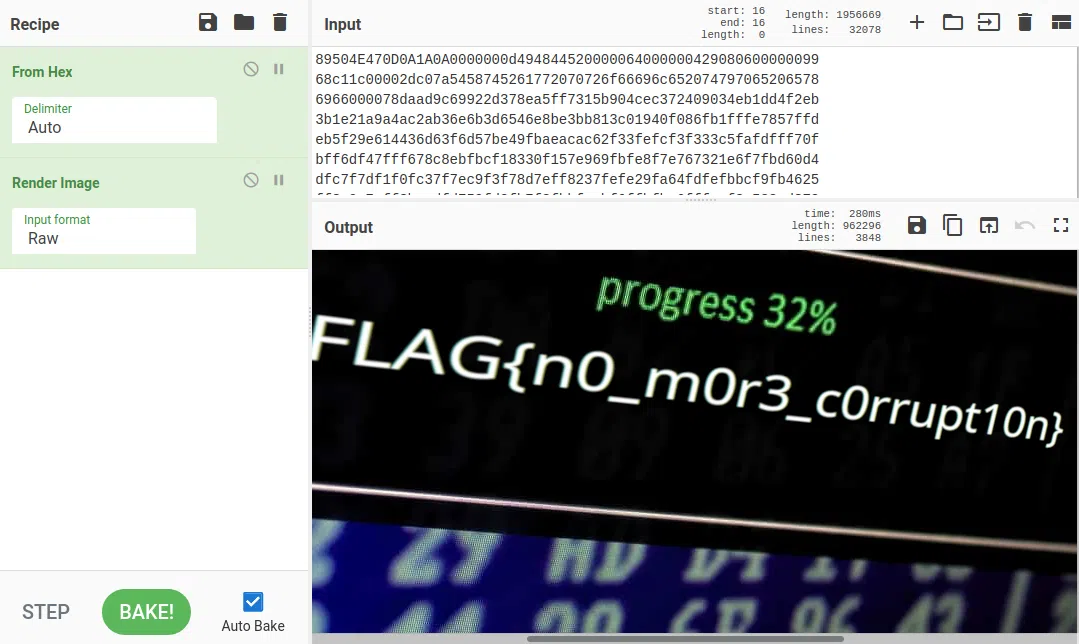
sckull@uplifted:~/tmp/forensics$ xxd -p f.06.png > hex_png06
|
BAD HEADER FILE MAGIC NUMBERS
List of File Signatures
1
2
|
89 50 4E 47 0D 0A 1A 0A
FLAG{n0_m0r3_c0rrupt10n}
|
f.07.zip
1
2
3
4
5
6
7
8
9
10
|
sckull@uplifted:~/tmp/forensics$ fcrackzip -D -u -p /home/sckull/tools/rockyou.txt f.07.zip
PASSWORD FOUND!!!!: pw == password1
sckull@uplifted:~/tmp/forensics$
sckull@uplifted:~/tmp/forensics$ unzip f.07.zip
Archive: f.07.zip
[f.07.zip] flag.txt password:
inflating: flag.txt
sckull@uplifted:~/tmp/forensics$ cat flag.txt
FLAG{zippy_zip_zip_zip}
sckull@uplifted:~/tmp/forensics$
|
f.08
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
sckull@uplifted:~/tmp/forensics$ file f.08
f.08: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, BuildID[sha1]=ea2b43595682667af187b0ac8db31207e9bf845f, for GNU/Linux 3.2.0, not stripped
sckull@uplifted:~/tmp/forensics$ chmod +x f.08
sckull@uplifted:~/tmp/forensics$ ./f.08
Hello, please enter the flag:
hello
Sorry the flag is incorrect
sckull@uplifted:~/tmp/forensics$ gdb -q ./f.08
Reading symbols from ./f.08...(no debugging symbols found)...done.
gdb-peda$ disas main
[... snip ...]
0x00000000000011d4 <+43>: mov BYTE PTR [rbp-0x73],0x46
0x00000000000011d8 <+47>: mov BYTE PTR [rbp-0x72],0x4c
0x00000000000011dc <+51>: mov BYTE PTR [rbp-0x71],0x41
0x00000000000011e0 <+55>: mov BYTE PTR [rbp-0x70],0x47
0x00000000000011e4 <+59>: mov BYTE PTR [rbp-0x6f],0x7b
0x00000000000011e8 <+63>: mov BYTE PTR [rbp-0x6e],0x69
0x00000000000011ec <+67>: mov BYTE PTR [rbp-0x6d],0x6e
0x00000000000011f0 <+71>: mov BYTE PTR [rbp-0x6c],0x63
0x00000000000011f4 <+75>: mov BYTE PTR [rbp-0x6b],0x6f
0x00000000000011f8 <+79>: mov BYTE PTR [rbp-0x6a],0x72
0x00000000000011fc <+83>: mov BYTE PTR [rbp-0x69],0x72
0x0000000000001200 <+87>: mov BYTE PTR [rbp-0x68],0x65
0x0000000000001204 <+91>: mov BYTE PTR [rbp-0x67],0x63
0x0000000000001208 <+95>: mov BYTE PTR [rbp-0x66],0x74
0x000000000000120c <+99>: mov BYTE PTR [rbp-0x65],0x7d
[... snip ...]
|
HEX
1
|
46 4c 41 47 7b 69 6e 63 6f 72 72 65 63 74 7d
|
FLAG
Con la frase correcta:
1
2
3
4
5
6
|
sckull@uplifted:~/tmp/forensics$ ./f.08
Hello, please enter the flag:
FLAG{incorrect}
Well done, you got the flag correct!!!
sckull@uplifted:~/tmp/forensics$
|
f.09
1
2
3
4
5
6
7
8
9
|
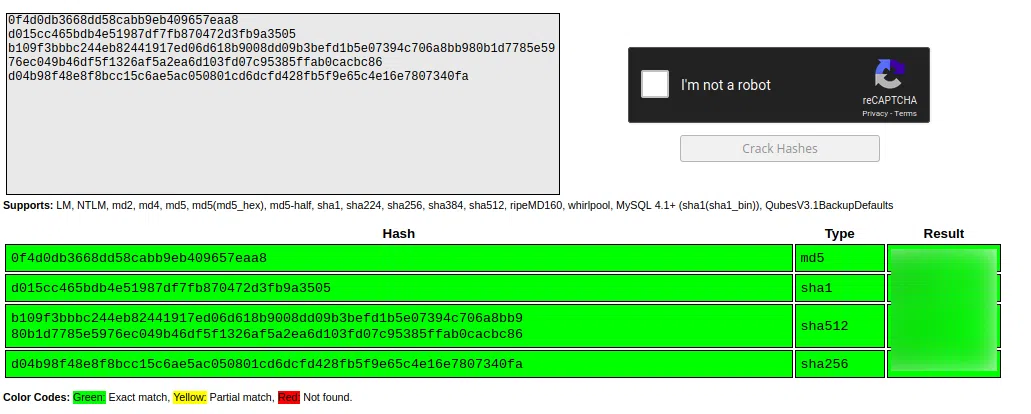
0f4d0db3668dd58cabb9eb409657eaa8
{
d015cc465bdb4e51987df7fb870472d3fb9a3505
_
_
b109f3bbbc244eb82441917ed06d618b9008dd09b3befd1b5e07394c706a8bb980b1d7785e5976ec049b46df5f1326af5a2ea6d103fd07c95385ffab0cacbc86
_
d04b98f48e8f8bcc15c6ae5ac050801cd6dcfd428fb5f9e65c4e16e7807340fa
}
|
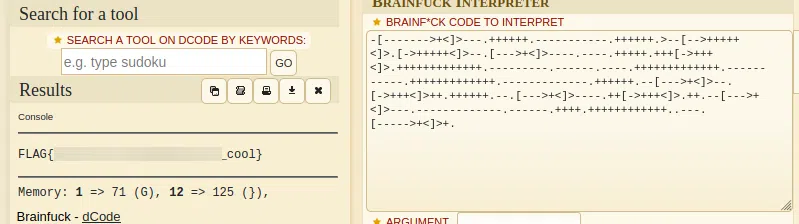
f.10
Brainfuck Language
Networking
n.01.pcap
Filtro: HTTP GET
FLAG{n0w_y0ur_g3tt1ng_1t}
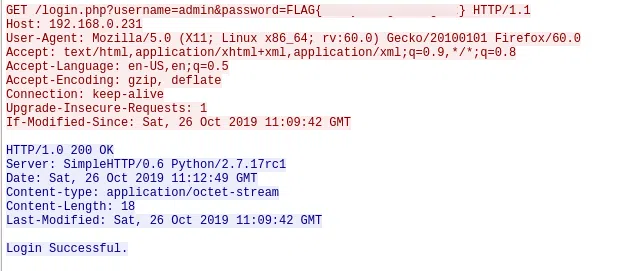
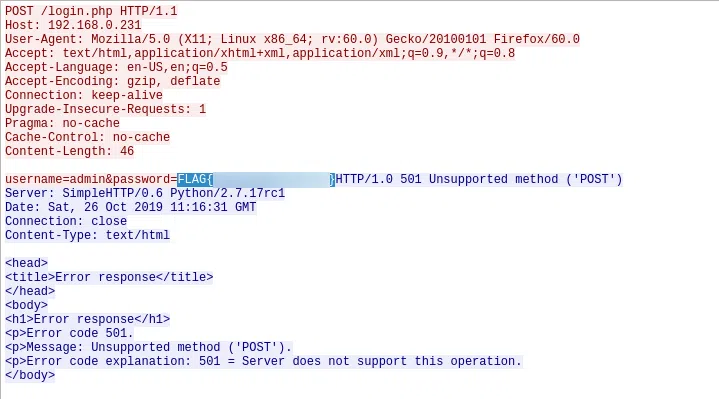
n.02.pcap
Filtro: HTTP POST
FLAG{1_am_th3_p0stm4n}
n.03.pcap
USER AGENT
FLAG{s3cr3t_ag3nt}
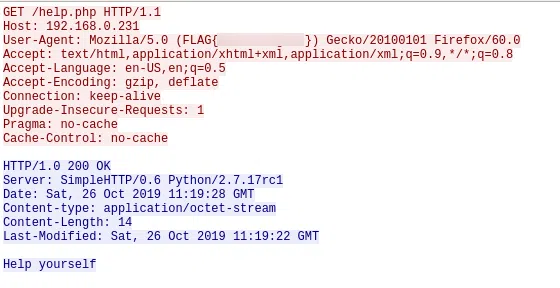
n.04.pcap
OBJECTS HTTP
FLAG{h3r3_1_am}
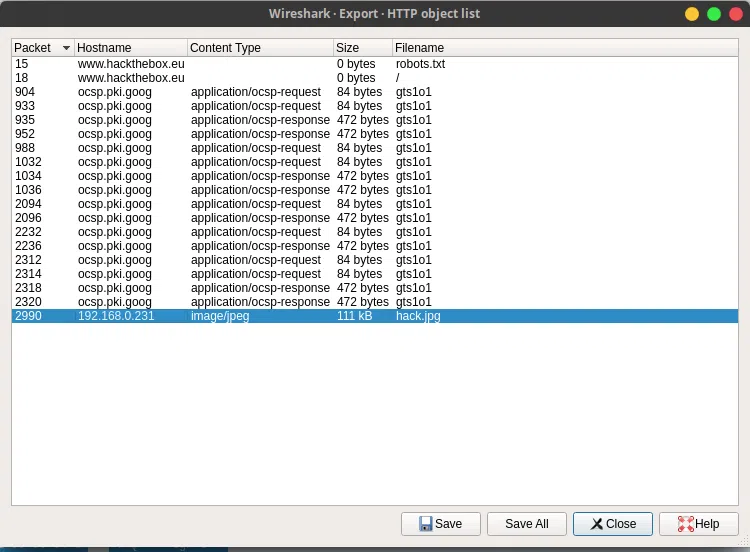

n.05.pcap
SMB
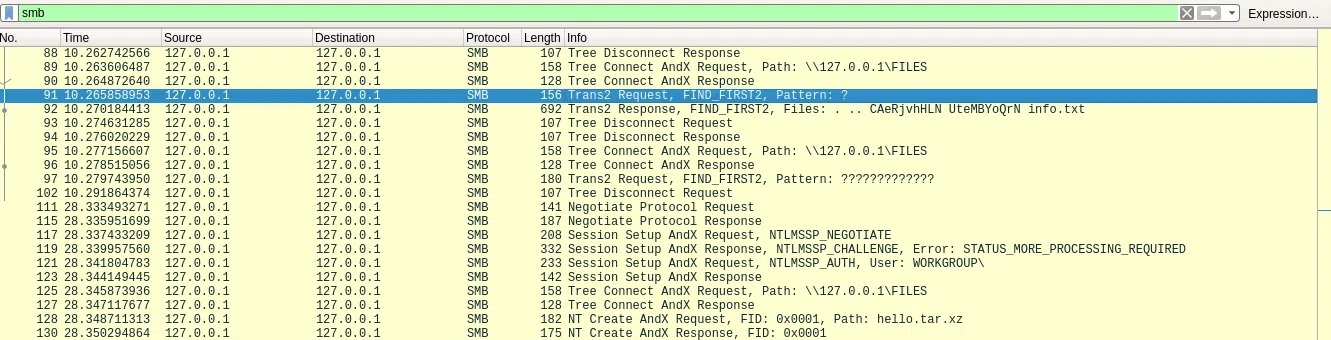
SMB OBJECT
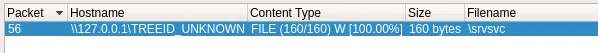
1
2
3
4
5
|
sckull@uplifted:~/tmp/networking$ tar -xvf smb_object05.tar
flag.txt
sckull@uplifted:~/tmp/networking$ cat flag.txt
FLAG{smb_smb_smb_smb_smb_smb}
sckull@uplifted:~/tmp/networking$
|
n.06.pcap
FTP
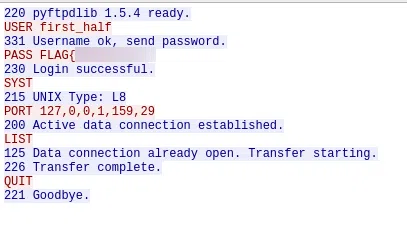
FLAG{1n3s3cur3_
TELNET
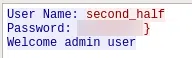
pr0t0c0ls}
FLAG{1n3s3cur3_pr0t0c0ls}
n.07.pcap
DNS
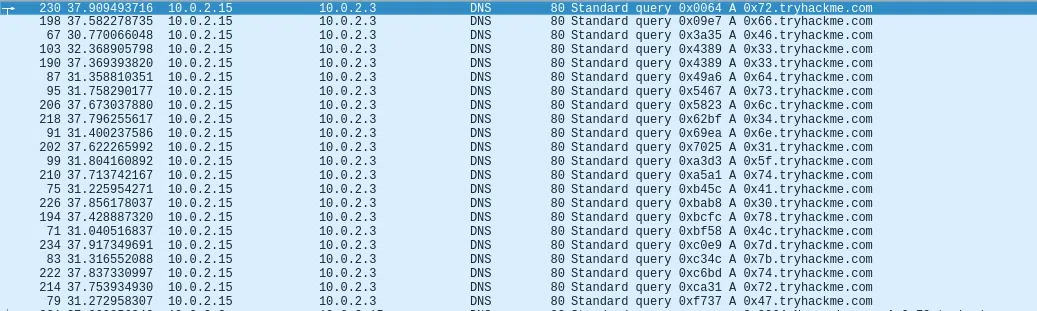
1
|
46 4c 41 47 7b 64 6e 73 5f 33 78 66 31 6c 74 72 34 74 30 72 7d
|
https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NDYgNGMgNDEgNDcgN2IgNjQgNmUgNzMgNWYgMzMgNzggNjYgMzEgNmMgNzQgNzIgMzQgNzQgMzAgNzIgN2Q
FLAG{dns_3xf1ltr4t0r}
n.08.pcap
tcp and data

FLAG{this is a hidden flag}
n.09
7z File
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
sckull@uplifted:~/tmp/networking$ file n.09
n.09: 7-zip archive data, version 0.3
sckull@uplifted:~/tmp/networking$ xxd n.09 | head
00000000: 377a bcaf 271c 0003 46c0 dcbf d40b 0000 7z..'...F.......
00000010: 0000 0000 2300 0000 0000 0000 cf09 fa64 ....#..........d
00000020: 0068 33be 1c86 3077 60f4 a484 2585 fa1c .h3...0w`...%...
00000030: 7627 82f2 9186 dc88 ca27 bae3 fb13 c5ff v'.......'......
00000040: 0e24 c288 d1b1 0114 695f 90fd b8ca a6d3 .$......i_......
00000050: 2f38 db8c 915e 7e32 f588 4d5c 3f35 4a84 /8...^~2..M\?5J.
00000060: 242d b5f0 8c96 a4e0 ce62 7105 5389 18f1 $-.......bq.S...
00000070: e946 8af0 1d2f a762 e91a 934b 32a6 7eb8 .F.../.b...K2.~.
00000080: 8322 16d1 2abc 32be 2107 1dae 03ac 6edf ."..*.2.!.....n.
00000090: e042 8551 7d12 e93f 57e4 fa2b 4f3d a993 .B.Q}..?W..+O=..
sckull@uplifted:~/tmp/networking$ mv n.09 n.09.7z
sckull@uplifted:~/tmp/networking$ 7z e n.09.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,8 CPUs Intel(R) Core(TM) i5-8250U CPU @ 1.60GHz (806EA),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3095 bytes (4 KiB)
Extracting archive: n.09.7z
--
Path = n.09.7z
Type = 7z
Physical Size = 3095
Headers Size = 198
Method = LZMA:23
Solid = +
Blocks = 1
Everything is Ok
Files: 2
Size: 26112
Compressed: 3095
sckull@uplifted:~/tmp/networking$
sckull@uplifted:~/tmp/networking$ strings *.msg| grep FL
FLAG\{sn41L_m41L\}
FLAG{sn41L_m41L}<br>
sckull@uplifted:~/tmp/networking$
|
n.10.pcap
SSL Certificate
SSL Wireshark: Edit > Preferences > Protocols > SSL > (Pre)-Master-Secret log filename > Select n.10.ssl.log
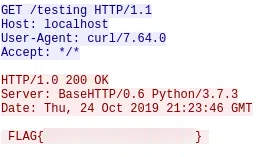
FLAG{y0u_ar3_c3rt1f13d_n0w}























