
En Previous identificamos una version de Next.JS vulnerable. En esta fue posible realizar bypass a filtros de acceso para acceder a la API y descargar archivos. Con la enumeracion de archivos logramos obtener credenciales de acceso para SSH. Finalmente escalamos privilegios con sudo y terraform.
| Nombre | Previous |
|---|---|
| OS | Linux |
| Puntos | 30 |
| Dificultad | Medium |
| Fecha de Salida | 2025-08-23 |
| IP | 10.10.11.83 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
|
|
Web Site
El sitio web nos redirige al dominio previous.htb el cual agregamos al archivo /etc/hosts.
|
|
El sitio presenta una tecnologia bajo el nombre PreviousJS.
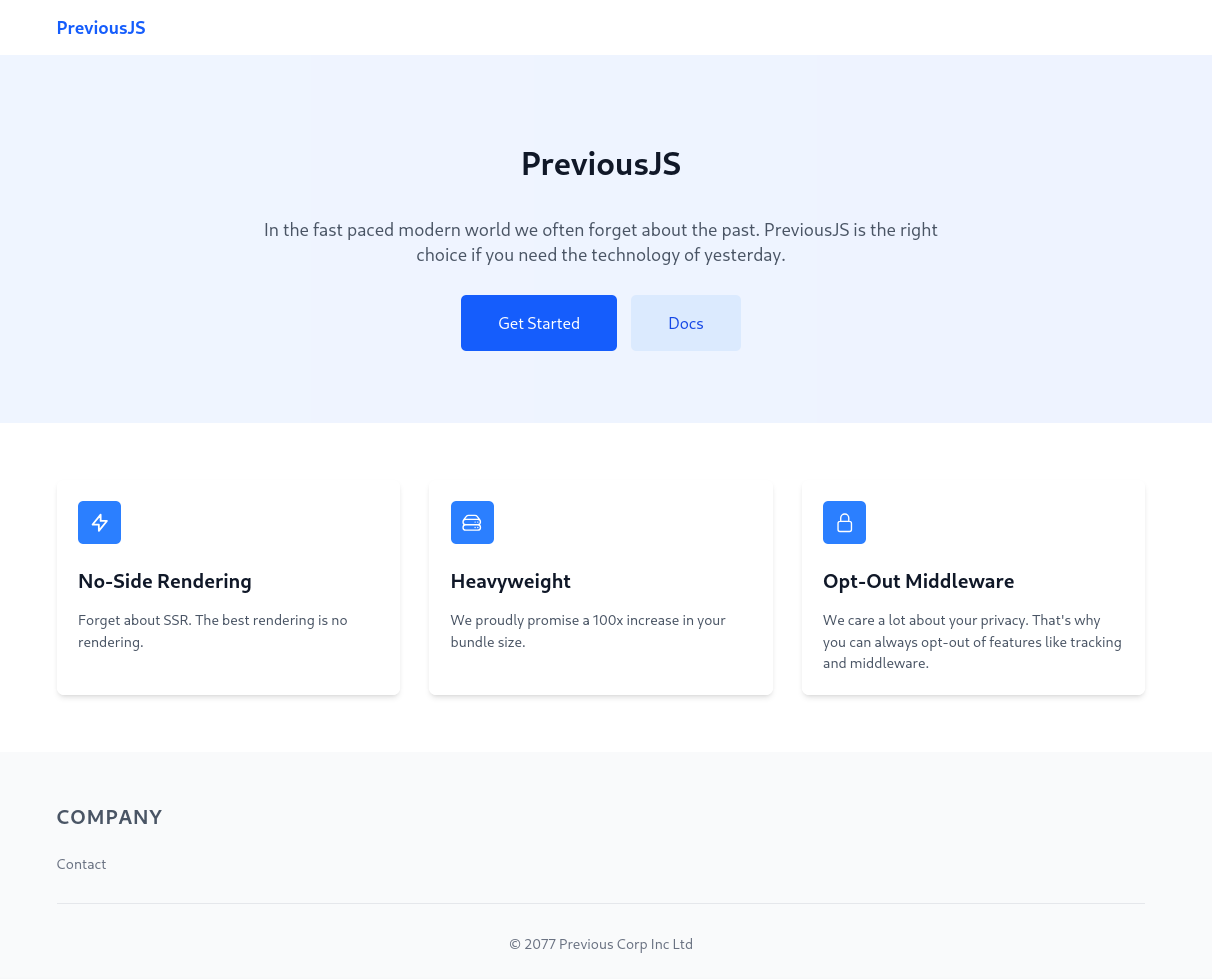
La documentacion es accesible con autenticacion.
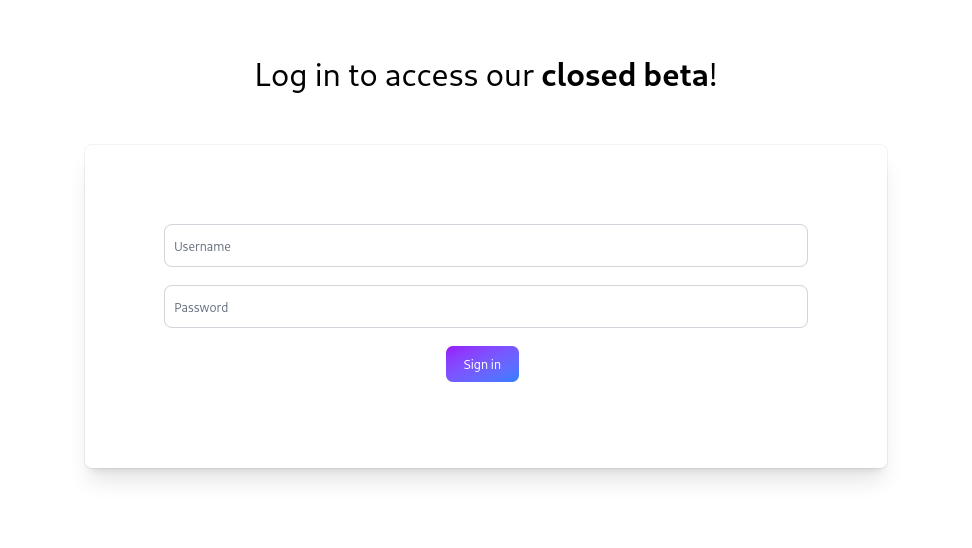
Web Tech
Los headers del sitio muestran que la tecnologia es Next.JS.
|
|
Wappalyzer muestra que la version es 15.2.2.

Directory Brute Forcing
feroxbuster muestra multiples rutas, archivos e incluso lo que parece una API.
|
|
CVE-2025-29927
La version de Next.js del sitio es vulnerable, es posible realizar bypass a filtros de autorizacion si esta ocurre por parte del middleware logrando a acceder a recursos como paginas de administracion, esto es posible tras agregar el header x-middleware-subrequest en las solicitudes.
Ejecutamos un PoC para esta vulnerabilidad la cual verifica y ’explota’ la vulnerabilidad.
|
|
Especificamos la url a la cual deseamos acceder, en este caso a la documentacion agregando la version de Next.js. Este muestra uno de los payloads que permite realizar el bypass guardando la solicitud en un archivo .html.
|
|
htmledit nos muestra el contenido html.
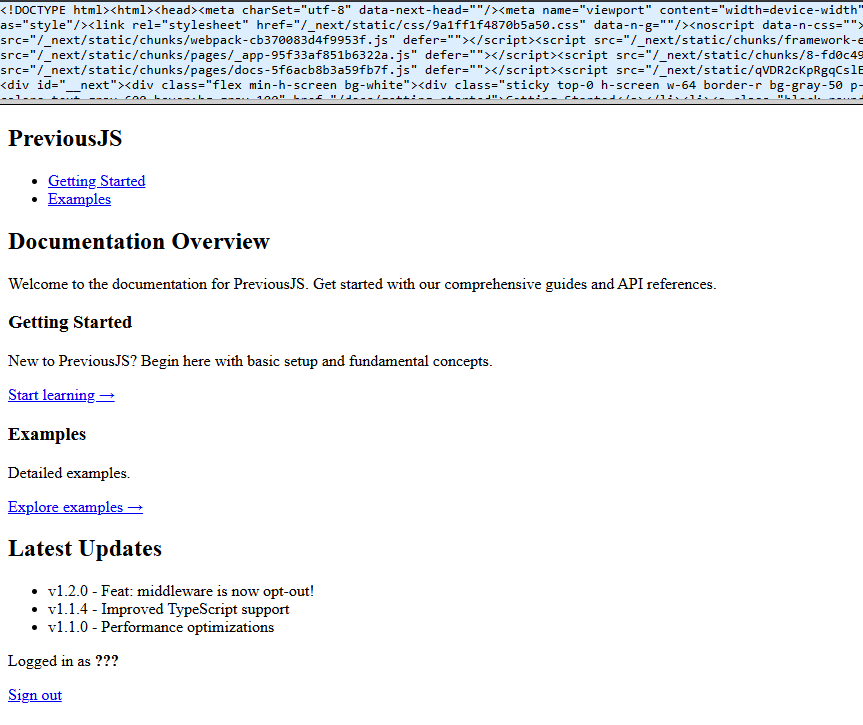
Path Traversal - Download Files
Utilizando Burpsuite agregamos el header a la solicitud logrando observar directamente desde el navegador el contenido.
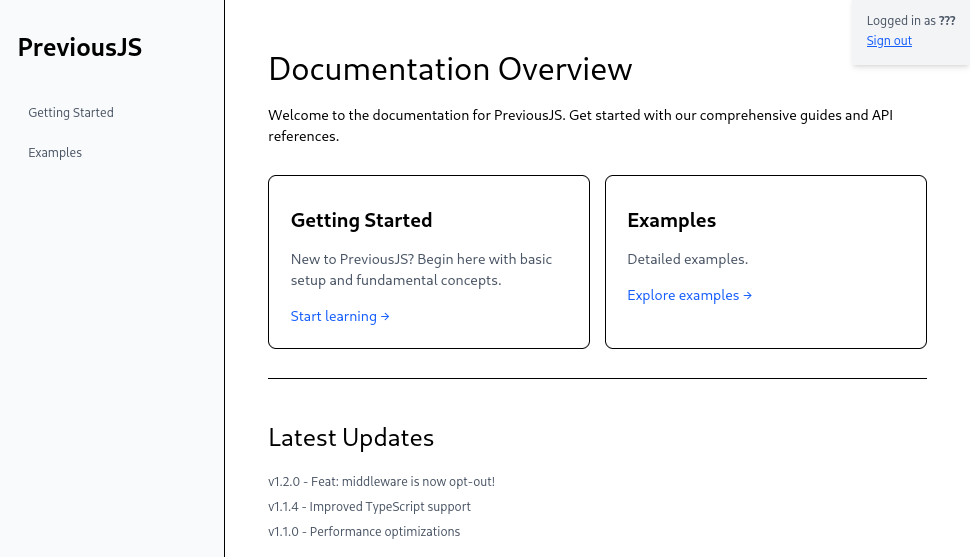
Vemos dos paginas nuevas en /docs/.
Una de estas muestra un ejemplo que se puede descargar a traves de la API.

Esta toma el nombre del archivo.
|
|
Logramos descargamos el archivo agregando el header.
|
|
Enumerating Files
Es posible descargar archivos del sistema.
|
|
Creamos un pequeno script para agregar el header.
|
|
Encontramos que la aplicacion esta corriendo dentro de un docker por la existencia del archivo .dockerenv.
|
|
Nos basamos de project-structure de nextjs para obtener informacion de la aplicacion, vemos la lectura del archivo package.json.
|
|
Encontramos el archivo server.js que contiene configuracion de nextjs. La aplicacion esta en /app, tambien se indica output en ‘standalone’ lo cual crearia archivos necesarios para la aplicacion en /.next.
|
|
Tras enumerar los archivos dentro de .next, required-server-files.json nos muestra multiples archivos entre ellos server/pages-manifest.json.
|
|
Esta especifica las paginas/rutas con los archivos javascript.
|
|
El archivo pages/api/auth/[...nextauth].js contiene “codigo” para la autenticacion de usuarios en la aplicacion.
|
|
beautifier formateo el codigo donde encontramos un par de credenciales.
|
|
User - Jeremy
Las credenciales son validas por SSH, logrando leer la flag user.txt.
|
|
Privesc
Jeremy puede ejecutar como root terraform con flags especificas.
|
|
Se especifica -chdir con el directorio /opt/examples donde observamos la configuracion a ejecutar: main.tf.
|
|
Se especifica el provider/plugin examples, el archivo /root/examples/hello-world.ts fuente y unicamente se muestra el directorio destino.
|
|
El archivo terraform.tfstate muestra el archivo destino en /home/jeremy/docker/previous/public/examples/
|
|
Jeremy tiene un archivo de configuracion para terraform en su directorio principal. Este especifica el directorio donde se encuentra el providier.
|
|
Si realizamos la ejecucion este muestra que no se encontraron cambios al archivo hello-world.ts.
|
|
Custom Provider
Creamos un script en bash bajo el mismo nombre del provider para ejecutar cat y crear el archivo /dev/shm/passwd.
|
|
Modificamos el archivo de configuracion .terraformrc agregando el directorio donde se encuentra el script.
|
|
Ejecutamos el terraform con sudo y observamos que se ejecuto el script.
|
|
Shell
Modificamos el script para realizar una copia de bash con permisos SUID.
|
|
Ejecutamos y verificamos que la copia fue realizada.
|
|
Ejecutamos bash con la flag -p logrando obtener acceso root y la flag root.txt.
|
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
|
|
