
Mirage inicia en el servicio NFS, donde se encontraron dos archivos que indican configuraciones, comandos y software utilizado. Se identifico una configuracion en el servidor DNS que permitia agregar registros, esto permitio la captura de credenciales para el servidor NATS donde posteriormente se extrajeron otro par de credenciales para recabar informacion para Bloodhound. Con el analisis en este ultimo se logro el acceso a diferentes usuarios a traves de grupos, usuarios y permisos. Finalmente, se logro identificar la configuracion y requisitos para explotar ESC10 para escalar privilegios.
| Nombre | Mirage 0 |
|---|---|
| OS | Windows |
| Puntos | Retired |
| Dificultad | Hard |
| Fecha de Salida | 2025-07-19 |
| IP | 10.10.11.78 |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: dns (53), kerberos (88), http (80), nfs (111), ldap (389), smb (445), winrm (5985), ntp (123).
|
|
Agregamos a nuestro archivo /etc/hosts los valores mirage.htb dc01.mirage.htb.
NFS
showmount muestra que existe un recurso compartido, puede acceder cualquiera.
|
|
Montamos el recurso localmente, se listan dos PDFs.
|
|
Missing DNS Record
El primer PDF (Incident_Report_Missing_DNS_Record_nats-svc.pdf) indica en un reporte que el subdominio nats-svc.mirage.htb, donde corre NATS messaging system no se encuentra disponible, la razon es ‘scavenging’, es una configuracion en el servidor DNS para eliminar registros con la configuracion por default.
Se muestra en una imagen el intento de autenticacion con este ultimo servicio ademas del nombre de usuario Dev_Account_A que por el nombre podria indicar algun tipo de “nomenclatura”.
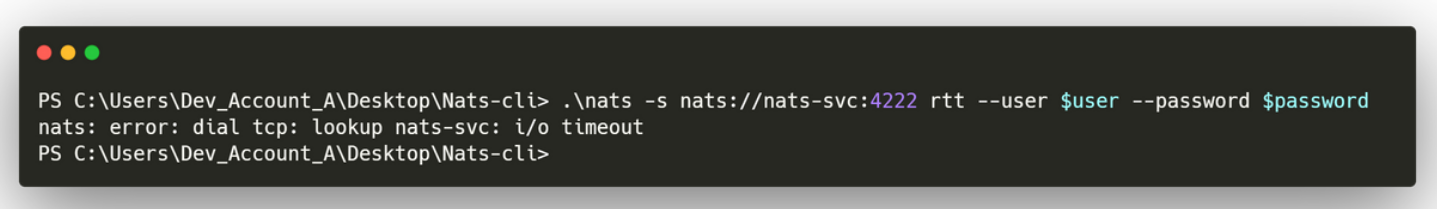
Se muestra la configuracion donde observamos que Dynamic Updates esta configurado a Nonsecure and secure lo cual permitiria a cualquier ‘usuario’ registrar/actualizar algun registro DNS. (Question about secure and unsecure DNS registration, Don’t Get Hijacked: Prevalence, Mitigation, and Impact of Non-Secure DNS Dynamic Updates).
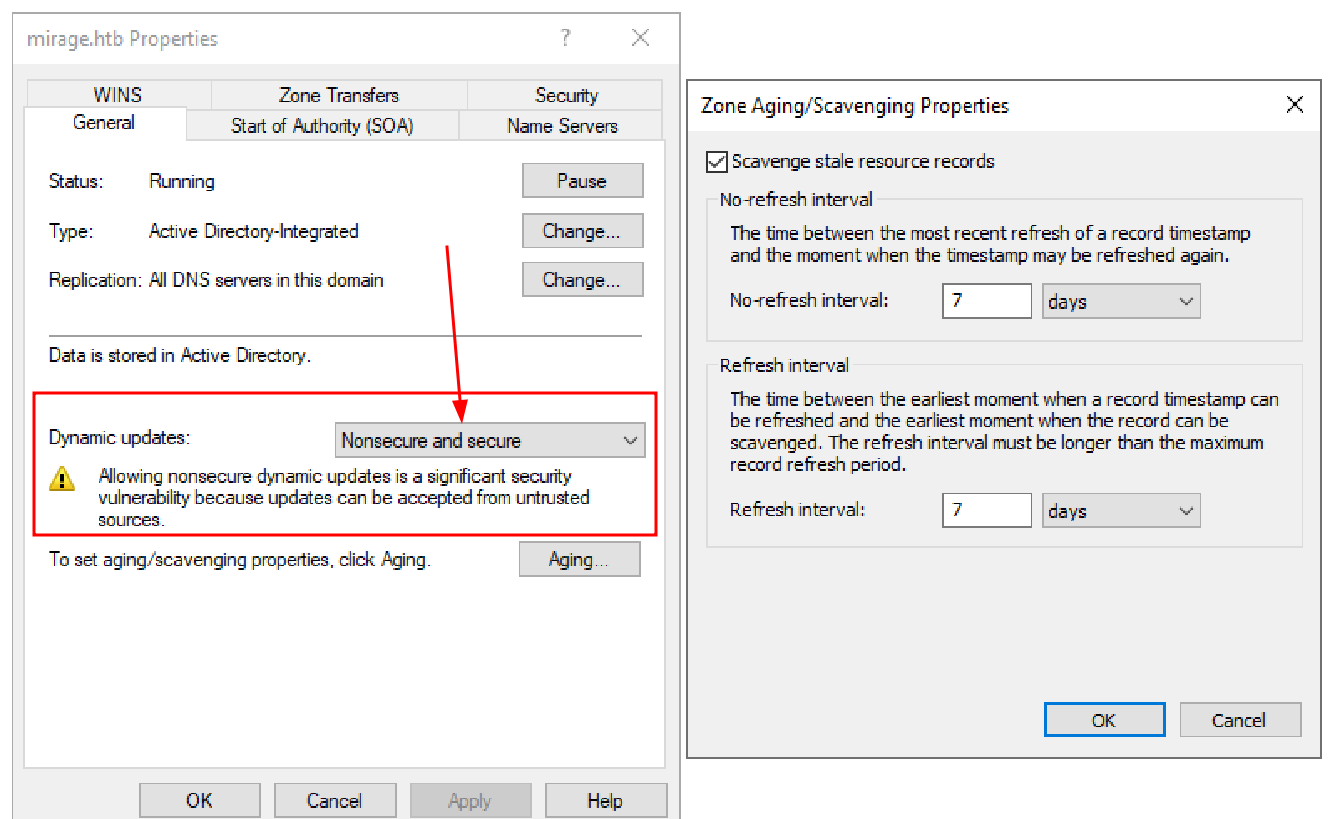
Finalmente se indica que nats-svc.mirage.htb “prodria” estar codificado en aplicaciones que aun puedan estar realizando algun tipo de conexion a este y de existir un secuestro a este subdominio podria exponer informacion.
Deprecated NTLM
El segundo PDF (Mirage_Authentication_Hardening_Report.pdf) principalmente menciona el uso de NTLM como un tipo de autenticacion obsoleta y que, Mirage esta “actualizando” a autenticacion por Kerberos. El objetivo es cambiar todo el dominio a este tipo de autenticacion para 2025.
Se observa un posible nombre de usuario al final ad-security.
Active Directory Security Team
IT Security Department – Mirage.htb
Contact: ad-security@mirage.htb
Enumerating Users
Basados en la informacion de la “nomenclatura” de usuarios en los PDFs y posibles usuarios creamos un wordlist con estos.
|
|
kerbrute muestra unicamente dos nombres de usuarios validos.
|
|
Usuario como contrasena no muestra ningun usuario valido.
|
|
DNS Update and Catching Credentials
El servidor DNS esta configurado para permitir actualizar/crear registros dns a cualquier usuario, utilizamos nsupdate para eliminar y agregar un nuevo registro en el servidor. Especificando el subdominio nats-svc.mirage.htb a nuestra direccion IP. La configuracion de nuestro archivo quedaria de la siguiente forma:
|
|
Tras especificar el archivo en nsupdate se verifica la existencia del registro.
|
|
El registro parece no estar registrado, tras ejecutar el update/registro y verificarlo con dig observamos que ahora nats-svc.mirage.htb apunta a nuestra IP.
|
|
NATS System Message
NATS corre en el puerto 4222, colocamos netcat a la escucha de este puerto tras el registro. Obtuvimos una solicitud desde el servidor.
|
|
Instalamos NATS server localmente para monitorear el trafico del puerto 4222.
|
|
Ejecutamos nats-server con la flag -V se muestra que existe autenticacion por parte de mirage con el usuario Dev_Account_A aunque no muestra la contrasena y muestra que TLS no es requerido.
|
|
Ejecutamos wireshark donde filtramos por el puerto 4222. Observamos una conexion donde se muestra la autenticacion con las credenciales de usuario.
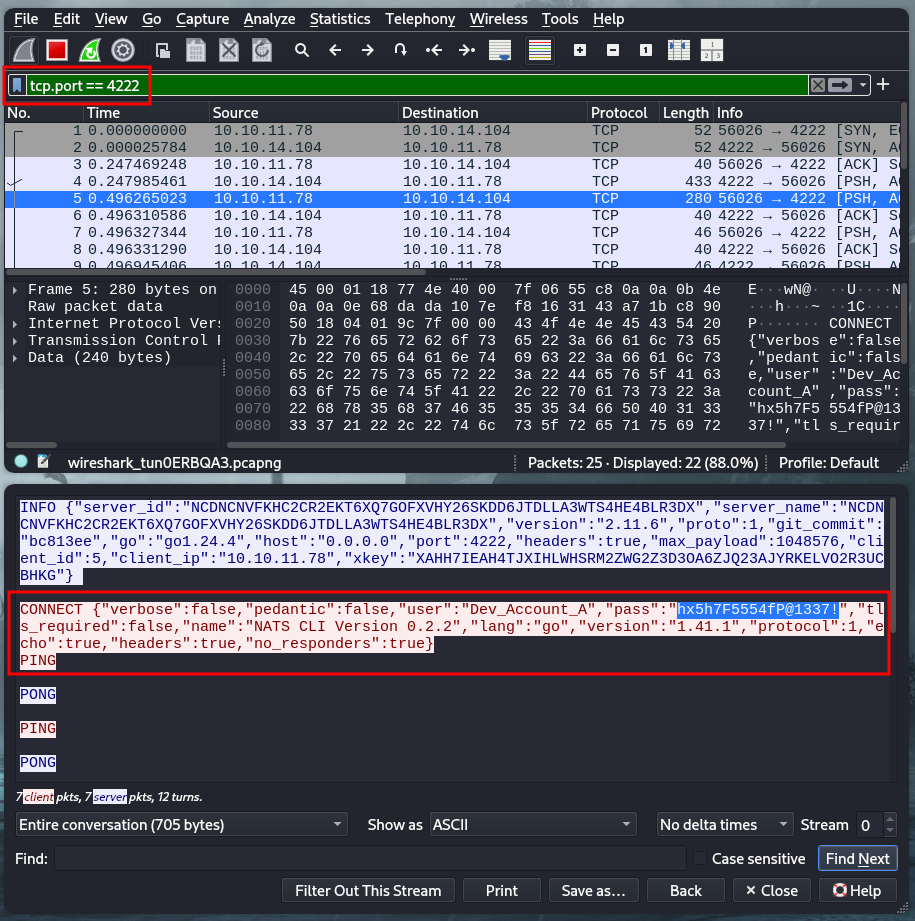
|
|
NATS streams
Con el cliente nats enumeramos los streams se lista el stream auth_logs.
|
|
Con view observamos los mensajes en el stream donde se muestran un par de credenciales.
|
|
|
|
User - david.jjackson
Kerbrute muestra el uusario como valido.
|
|
Este usuario tiene acceso por smb y ldap.
|
|
bloodhound
Ejecutamos el collector de bloodhound con netexec.
|
|
Users
Encontramos nueve cuentas dentro del grupo Domain Users.
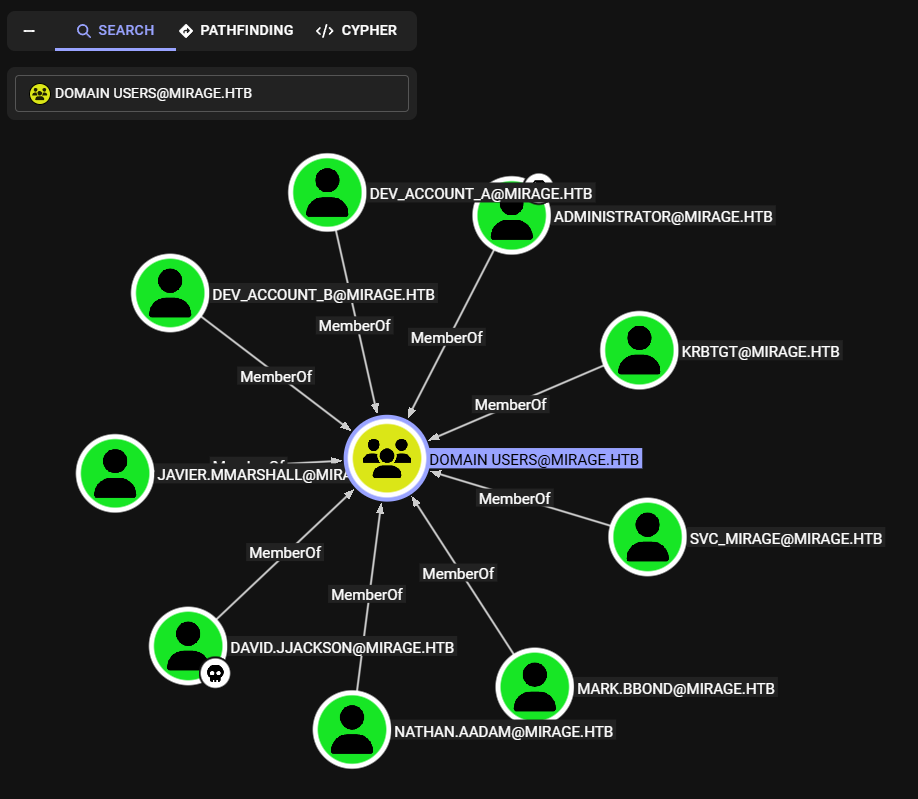
Nathan.Aadam
Nathan puede acceder por WinRM ademas, pertenece a dos grupos: Exchange_admins y IT_Admins.
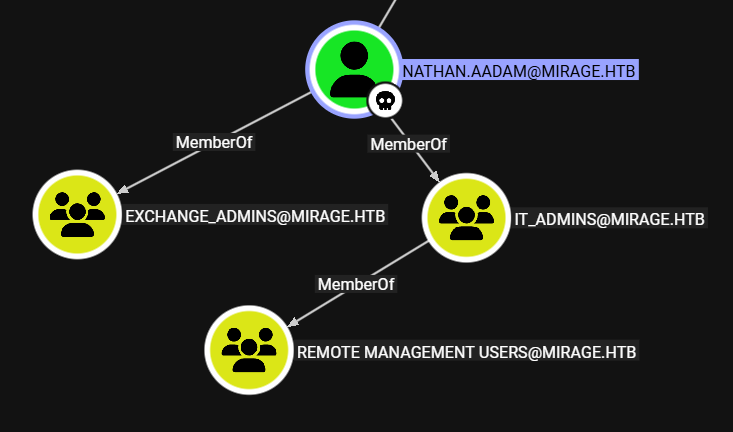
Tambien, se observa que es posible realizar Kerberoasting a este usuario.
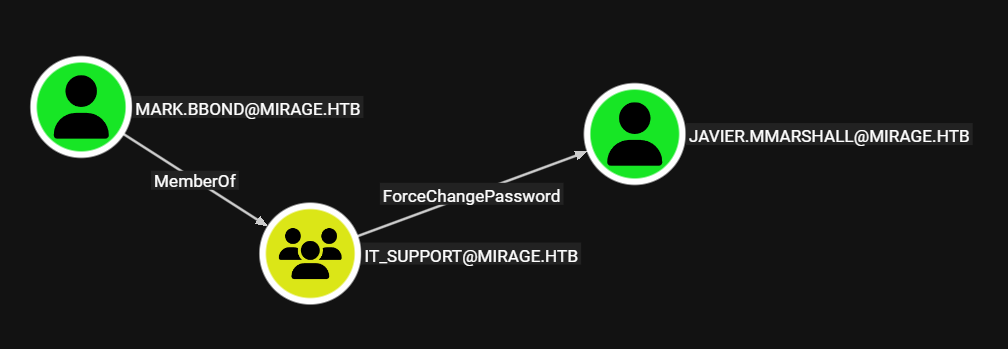
Mark.Bbond
Mark a traves del grupo IT_Support puede realizar el cambio de contrasena a Javier.Mmarshall.
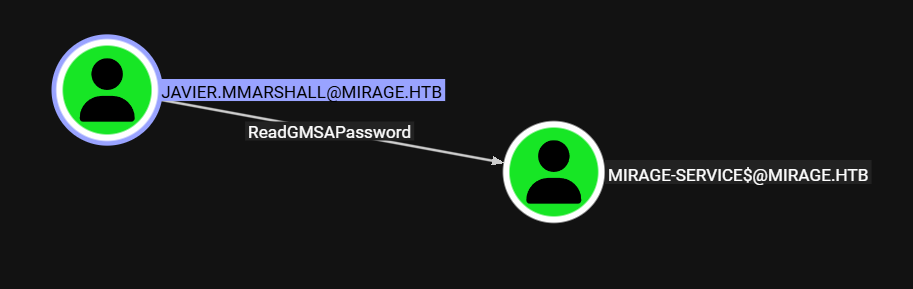
Javier.Mmarshall
Javier puede realizar la lectura de contrasena GMSA de Mirage-Service$.
Mirage-Service
Se muestra como miembro unico de Domain Computers.
User - nathan.aadam
A traves de las credenciales de david.jjackson ejecutamos kerberoasting con netexec logrando obtener el hash de nathan.aadam.
|
|
Cracking the Hash
Ejecutamos john con el wordlist rockyou.txt sobre el archivo de hash logrando obtener la contrasena.
|
|
Nathan tiene acceso por smb y ldap.
|
|
Shell WinRM
Nathan al pertenecer al grupo de Remote Managment Users puede acceder por WinRM. Generamos el archivo de configuracion krb5 con netexec para mirage.
|
|
Solicitamos un ticket con kinit.
|
|
Ejecutamos evil-winrm logrando una shell y la lectura de la flag user.txt.
|
|
En la configuracion de nats enocntramos otras credenciales para usuarios.
|
|
User - Mark.bbond -> javier.Mmarshall
Tras ejecutar WinPEAS este muestra un par de credenciales.
|
|
Estas permiten el acceso por smb y ldap.
|
|
Generamos un ticket para este usuario con getTGT.
|
|
Change Password javier.mmarshall
A traves de IT_Supoort mark puede cambiar la contrasena de javier.
|
|
Muestra KDC_ERR_CLIENT_REVOKED que indica que el usuario no puede autenticarse.
|
|
Si observamos el usuario no esta habilitado.
|
|
Tambien, vemos que mark tiene permisos sobre javier.
|
|
Enable User
Iniciamos obteniendo una shell como mark.bbond con RunasCs.
|
|
Ejecutamos Enable-ADAccount y javier ahora muestra que esta habilitado.
|
|
Tras habilitar el usuario este nos sigue mostrando el mismo error.
|
|
Intentamos a traves de RunasCs ahora muestra que el usuario tiene restriciones de tiempo para ingresar.
|
|
Logon Hours
Siguiendo el post How to set Logon Hours for Active Directory Users actualizamos el usuario javier.mmarshall a las horas que puede ingresar. Cambiamos las horas para el ingreso de este usuario.
|
|
RunasCS muestra que no es posible ingresar con este usuario.
|
|
Con la flag --remote-impersonation este logra una conexion pero muere al instante.
|
|
netexec muestra que tiene acceso por LDAP.
|
|
User - Mirage-Service$
Read GMSA Password
Javier puede realizar la lectura de la contrasena gmsa de mirage-service$, ejecutamos netexec con la flag --gmsa con las credenciales de javier.
|
|
Privesc
Obtuvimos un ticket para mirage-service.
|
|
Tras ejecutar certipy este no muestra ninguna plantilla vulnerable.
|
|
Se observa que mirage-service tiene permisos WRITE sobre mark.bbond.
|
|
Indagamos mas en los atributos y observamos que userPrincipalName se lista como WRITE.
|
|
ESC10
Certipy presenta distintos escenarios en la documentacion donde userPrincipalName es utilizado para abusar de plantillas vulnerables (ESCx). Sin embargo, la mayoria de estas se muestran en el output de certipy.
Uno de los escenarios es ESC10, el cual tiene como requisito la modificacion de UPN de un usuario (mark.bbond) y el valor 0x4 en el registro HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\, este ultimo se confirmo al realizar el query en el registro.
|
|
Hay que mencionar que ESC10 no es posible detectar a traves de certipy ya que es necesario acceso privilegiado para acceder a los registros.
Certipy does not directly detect ESC10 by querying the Schannel CertificateMappingMethods registry key on Domain Controllers or other target servers, as this typically requires privileged access (like local administrator rights) to those servers’ registries.
Exploit
Iniciamos cambiando userPrincipalName de mark.bbond como mirage-service a DC01$.
|
|
Como mark.bbond se obtiene un certificado de la plantilla User.
|
|
Se devuelve el valor original de UPN a mark.bbond.
|
|
Con el certificado obtenido autenticamos y obtenemos una “shell” ldap donde realizamos ejecutamos RBCD. Para ello: set_rbcd Target Controlled-Account.
|
|
- ref. ESC10
Solicitamos un service ticket para mirage-service especificando -impersonate DC01.
|
|
Finalmente con este ultimo ticket logramos obtener el hash de administrator.
|
|
Shell
Solicitamos un ticket con el hash.
|
|
Logrando una shell como administrator y la flag root.txt.
|
|
Dump Hashes
Realizamos un dump de las hashes con impacket-secretdumps.
|
|

